Vault从入门到精通系列之二:启动Vault服务器
- 一、启动开发服务器
- 二、设置环境变量
- 三、验证服务器正在运行
- 四、vault命令汇总
Vault 作为客户端-服务器应用程序运行。Vault 服务器是唯一与数据存储和后端交互的 Vault 架构。通过 Vault CLI 完成的所有操作都通过 TLS 连接与服务器交互。
在本篇博客中,启动以开发模式运行的 Vault 服务器并与之交互。
一、启动开发服务器
以开发模式(开发服务器)启动 Vault 服务器。开发服务器是一个内置的、预配置的服务器,它不是很安全,但对于在本地使用 Vault 很有用。
vault server -dev
输出如下所示:
vault server -dev
==> Vault server configuration:
Api Address: http://127.0.0.1:8200
Cgo: disabled
Cluster Address: https://127.0.0.1:8201
Environment Variables: CLASSPATH, FLINK_HOME, GODEBUG, HADOOP_HOME, HISTFILE, HISTSIZE, HISTTIMEFORMAT, HIVE_HOME, HOME, HOSTNAME, JAVA_HOME, LANG, LESSOPEN, LOGNAME, LS_COLORS, MAIL, MONGODB_HOME, MSSQL_HOME, PATH, PROMPT_COMMAND, PWD, PYTHON3_HOME, QT_GRAPHICSSYSTEM, QT_GRAPHICSSYSTEM_CHECKED, SHELL, SHLVL, SPARK_HOME, SUDO_COMMAND, SUDO_GID, SUDO_UID, SUDO_USER, TERM, TMOUT, USER, USERNAME, VAULT_ADDR, XDG_SESSION_ID, ZOOKEEP_HOME, _
Go Version: go1.20.4
Listener 1: tcp (addr: "127.0.0.1:8200", cluster address: "127.0.0.1:8201", max_request_duration: "1m30s", max_request_size: "33554432", tls: "disabled")
Log Level:
Mlock: supported: true, enabled: false
Recovery Mode: false
Storage: inmem
Version: Vault v1.13.3, built 2023-06-06T18:12:37Z
Version Sha: 3bedf816cbf851656ae9e6bd65dd4a67a9ddff5e
==> Vault server started! Log data will stream in below:
2023-06-19T13:14:08.399+0800 [INFO] proxy environment: http_proxy="" https_proxy="" no_proxy=""
2023-06-19T13:14:08.399+0800 [WARN] no `api_addr` value specified in config or in VAULT_API_ADDR; falling back to detection if possible, but this value should be manually set
2023-06-19T13:14:08.400+0800 [INFO] core: Initializing version history cache for core
2023-06-19T13:14:08.400+0800 [INFO] core: security barrier not initialized
2023-06-19T13:14:08.400+0800 [INFO] core: security barrier initialized: stored=1 shares=1 threshold=1
2023-06-19T13:14:08.401+0800 [INFO] core: post-unseal setup starting
2023-06-19T13:14:08.416+0800 [INFO] core: loaded wrapping token key
2023-06-19T13:14:08.416+0800 [INFO] core: successfully setup plugin catalog: plugin-directory=""
2023-06-19T13:14:08.416+0800 [INFO] core: no mounts; adding default mount table
2023-06-19T13:14:08.417+0800 [INFO] core: successfully mounted: type=cubbyhole version="v1.13.3+builtin.vault" path=cubbyhole/ namespace="ID: root. Path: "
2023-06-19T13:14:08.418+0800 [INFO] core: successfully mounted: type=system version="v1.13.3+builtin.vault" path=sys/ namespace="ID: root. Path: "
2023-06-19T13:14:08.418+0800 [INFO] core: successfully mounted: type=identity version="v1.13.3+builtin.vault" path=identity/ namespace="ID: root. Path: "
2023-06-19T13:14:08.420+0800 [INFO] core: successfully mounted: type=token version="v1.13.3+builtin.vault" path=token/ namespace="ID: root. Path: "
2023-06-19T13:14:08.420+0800 [INFO] rollback: starting rollback manager
2023-06-19T13:14:08.423+0800 [INFO] core: restoring leases
2023-06-19T13:14:08.425+0800 [INFO] expiration: lease restore complete
2023-06-19T13:14:08.426+0800 [INFO] identity: entities restored
2023-06-19T13:14:08.426+0800 [INFO] identity: groups restored
2023-06-19T13:14:08.426+0800 [INFO] core: Recorded vault version: vault version=1.13.3 upgrade time="2023-06-19 05:14:08.426587913 +0000 UTC" build date=2023-06-06T18:12:37Z
2023-06-19T13:14:08.696+0800 [INFO] core: post-unseal setup complete
2023-06-19T13:14:08.696+0800 [INFO] core: root token generated
2023-06-19T13:14:08.696+0800 [INFO] core: pre-seal teardown starting
2023-06-19T13:14:08.697+0800 [INFO] rollback: stopping rollback manager
2023-06-19T13:14:08.697+0800 [INFO] core: pre-seal teardown complete
2023-06-19T13:14:08.697+0800 [INFO] core.cluster-listener.tcp: starting listener: listener_address=127.0.0.1:8201
2023-06-19T13:14:08.697+0800 [INFO] core.cluster-listener: serving cluster requests: cluster_listen_address=127.0.0.1:8201
2023-06-19T13:14:08.697+0800 [INFO] core: post-unseal setup starting
2023-06-19T13:14:08.697+0800 [INFO] core: loaded wrapping token key
2023-06-19T13:14:08.697+0800 [INFO] core: successfully setup plugin catalog: plugin-directory=""
2023-06-19T13:14:08.698+0800 [INFO] core: successfully mounted: type=system version="v1.13.3+builtin.vault" path=sys/ namespace="ID: root. Path: "
2023-06-19T13:14:08.698+0800 [INFO] core: successfully mounted: type=identity version="v1.13.3+builtin.vault" path=identity/ namespace="ID: root. Path: "
2023-06-19T13:14:08.698+0800 [INFO] core: successfully mounted: type=cubbyhole version="v1.13.3+builtin.vault" path=cubbyhole/ namespace="ID: root. Path: "
2023-06-19T13:14:08.699+0800 [INFO] core: successfully mounted: type=token version="v1.13.3+builtin.vault" path=token/ namespace="ID: root. Path: "
2023-06-19T13:14:08.699+0800 [INFO] rollback: starting rollback manager
2023-06-19T13:14:08.699+0800 [INFO] core: restoring leases
2023-06-19T13:14:08.700+0800 [INFO] identity: entities restored
2023-06-19T13:14:08.700+0800 [INFO] identity: groups restored
2023-06-19T13:14:08.700+0800 [INFO] expiration: lease restore complete
2023-06-19T13:14:08.700+0800 [INFO] core: post-unseal setup complete
2023-06-19T13:14:08.700+0800 [INFO] core: vault is unsealed
2023-06-19T13:14:08.703+0800 [INFO] core: successful mount: namespace="" path=secret/ type=kv version=""
WARNING! dev mode is enabled! In this mode, Vault runs entirely in-memory
and starts unsealed with a single unseal key. The root token is already
authenticated to the CLI, so you can immediately begin using Vault.
You may need to set the following environment variables:
$ export VAULT_ADDR='http://127.0.0.1:8200'
The unseal key and root token are displayed below in case you want to
seal/unseal the Vault or re-authenticate.
Unseal Key: jp2vzZPjYufsXNsJsEFTuKHMJzvx2FvnC5M3H6+y3vc=
Root Token: hvs.WNSdITpoYX5HvRZWYyGjvZaj
Development mode should NOT be used in production installations!
开发服务器将其所有数据存储在内存中(但仍然加密),在localhost没有 TLS 的情况下进行侦听,并自动解封并向您显示解封密钥和根访问密钥。
二、设置环境变量
启动一个新的终端会话。
export VAULT_ADDR …从终端输出复制并运行命令。这将配置 Vault 客户端与开发服务器对话。
export VAULT_ADDR='http://127.0.0.1:8200'
Vault CLI 使用环境变量确定哪些 Vault 服务器发送请求 VAULT_ADDR。
将解封密钥保存在某处。不要担心如何安全地保存它。现在,只需将它保存在任何地方。
将环境变量值VAULT_TOKEN设置为终端输出中显示的生成的根令牌值。
export VAULT_TOKEN="hvs.6j4cuewowBGit65rheNoceI7"
要与 Vault 交互,必须提供有效的令牌。设置此环境变量是一种通过 CLI 向 Vault 提供令牌的方法。在身份验证教程中,将学习使用vault login <token_value>命令对 Vault 进行身份验证。
三、验证服务器正在运行
通过运行命令验证服务器是否正在运行vault status。如果运行成功,输出应如下所示:
vault status
Key Value
--- -----
Seal Type shamir
Initialized true
Sealed false
Total Shares 1
Threshold 1
Version 1.13.3
Build Date 2023-06-06T18:12:37Z
Storage Type inmem
Cluster Name vault-cluster-488bbee6
Cluster ID 6fd0289e-dd56-af7f-c188-6f8ea08e3f2e
HA Enabled false
四、vault命令汇总
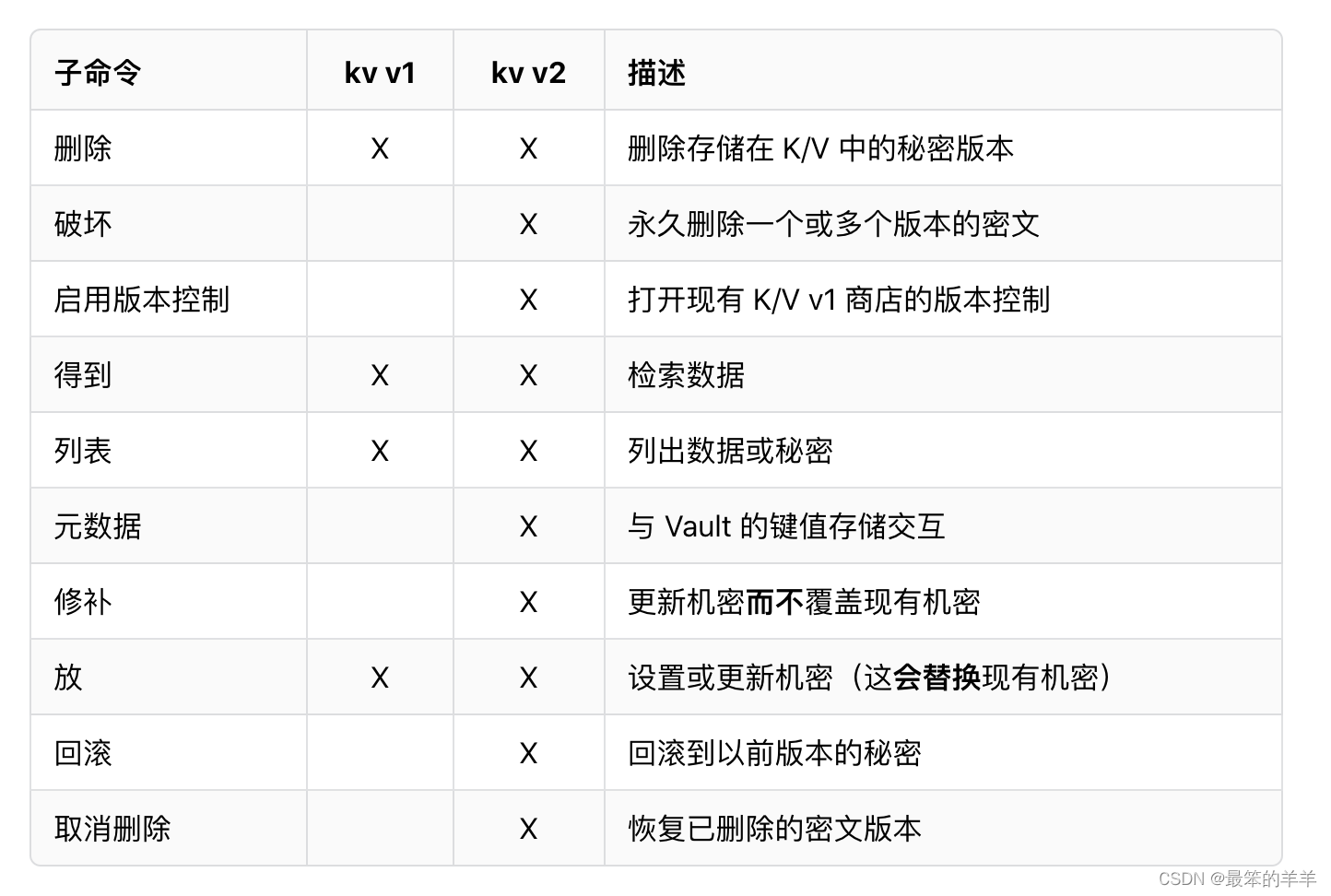
在开发模式下运行 Vault 时,Key/Value v2 机密引擎在 secret/ 路径下启用。Key/Value 机密引擎是一个通用的键值存储,用于在为 Vault 配置的物理存储中存储任意机密。写入 Vault 的秘密被加密,然后写入后端存储。因此,后端存储机制永远看不到未加密的值,也没有必要的手段在没有 Vault 的情况下对其进行解密。
Key/Value 机密引擎有版本 1 和 2。不同之处在于 v2 提供机密的版本控制,而 v1 不提供。
使用 vault kv [options] [args] 命令与 K/V 秘密引擎交互。
可用的子命令: