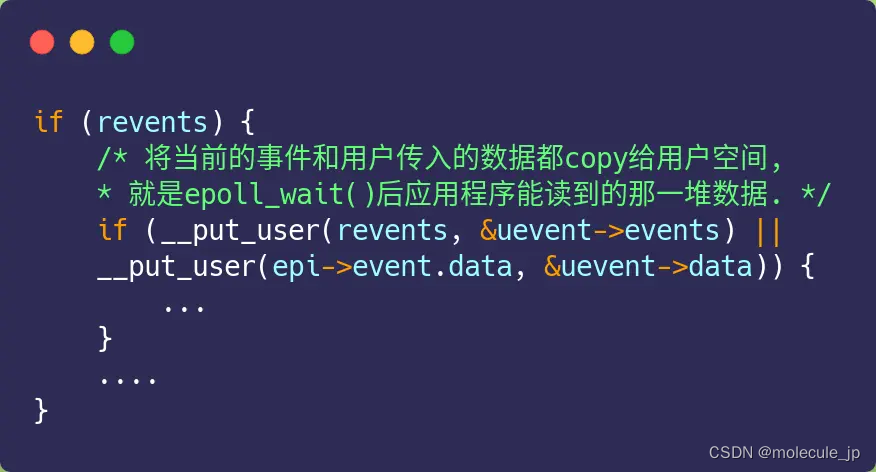
- 本来不打算放了,但是比赛打都打了留个纪念
- 社工有佬,与我无关,misc只会隐写
- 虽然我是逆向手,但因为队友tql,所以只留给我最后一道~~
- 我的wp向来以简述思路为主,习惯就好
Crypto
Hex?Hex!(初级)
- 十六进制转字符串
梦想是红色的 (初级)
- 社会主义核心价值观编码
原来你也玩原神 (初级)
- 原神文字,对照翻译
md5的破解
- 给了md5还是单位flag未知,随便爆破
yafu (中级)
- yafu分解rsa
factordb (中级)
- factordb分解rsa
(校外)我测你vva
c = 'HYEQJvPZ~X@+Bp'
for i in range(len(c)):
if i % 2 == 0:
print(chr(ord(c[i])-i),end='')
else:
print(chr(ord(c[i])+i), end='')
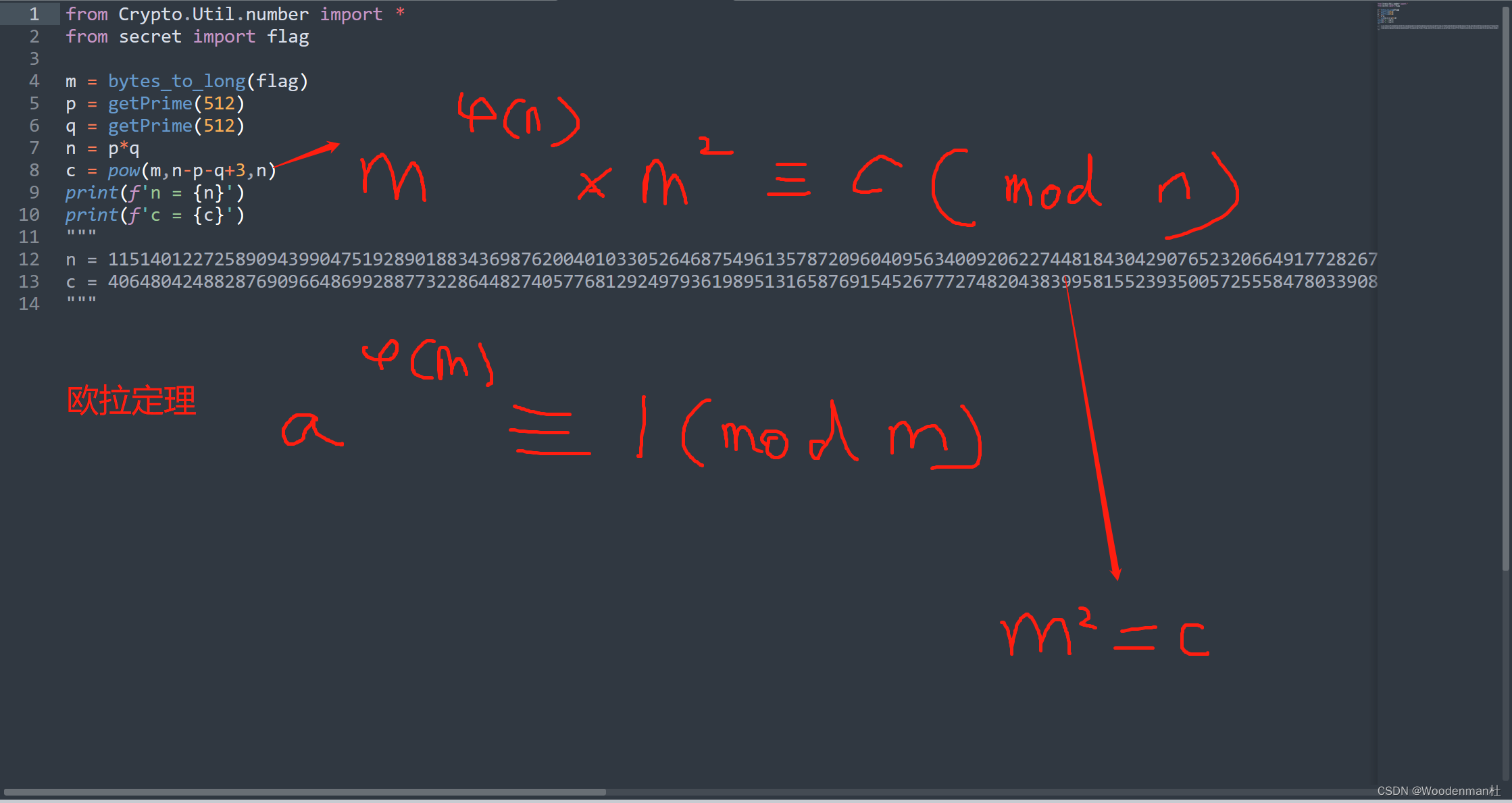
Euler
- 欧拉定理的简单利用
- phi = (p-1)*(q-1) = e-2,然后就能推到出开根就是结果
(校外)隐晦的聊天记录
- 密文和明文异或得到key,和另一个明文异或即可
a = [0x6c,0x73,0xd5,0x24,0x0a,0x94,0x8c,0x86,0x98,0x1b,0xc2,0x94,0x81,0x4d]
a1 = 'attack at dawn'
for i in range(len(a)):
print(a[i] ^ ord(a1[i]),end=',')
b1 = 'Monday or Thur'
print()
b = [13,7,161,69,105,255,172,231,236,59,166,245,246,35]
for i in range(len(a)):
print(hex(b[i] ^ ord(b1[i]))[2:],end=' ')
# 4068cf2108868c889e1bf29d8351
(校外)baby_xor
- c1 = p ^ m
- 根据已知明文m可以泄露p高位
- 然后高位攻击得到p
- 正常rsa解密
The same common divisor (高级)
- 两次加密rsa,n1、n2不相同且有公因数,直接gcd得到原p、q1、q2,然后正常rsa
import gmpy2
n1= 9852079772293301283705208653824307027320071498525390578148444258198605733768947108049676831872672654449631852459503049139275329796717506126689710613873813880735666507857022786447784753088176997374711523987152412069255685005264853118880922539048290400078105858759506186417678959028622484823376958194324034590514104266608644398160457382895380141070373685334979803658172378382884352616985632157233900719194944197689860219335238499593658894630966428723660931647038577670614850305719449893199713589368780231046895222526070730152875112477675102652862254926169713030701937231206405968412044029177246460558028793385980934233
n3= 4940268030889181135441311597961813780480775970170156650560367030148383674257975796516865571557828263935532335958510269356443566533284856608454193676600884849913964971291145182724888816164723930966472329604608512023988191536173112847915884014445539739070437180314205284883149421228744714989392788108329929896637182055266508625177260492776962915873036873839946591259443753924970795669864031580632650140641456386202636466624658715315856453572441182758855085077441336516178544978457053552156714181607801760605521338788424464551796638531143900048375037218585999440622490119344971822707261432953755569507740550277088437182
c1= 7066425618980522033304943700150361912772559890076173881522840300333719222157667104461410726444725540513601550570478331917063911791020088865705346188662290524599499769112250751103647749860198318955619903728724860941709527724500004142950768744200491448875522031555564384426372047270359602780292587644737898593450148108629904854675417943165292922990980758572264063039172969633878015560735737699147707712154627358077477591293746136250207139049702201052305840453700782016480965369600667516646007546442708862429431724013679189842300429421340122052682391471347471758814138218632022564279296594279507382548264409296929401260
c2= 854668035897095127498890630660344701894030345838998465420605524714323454298819946231147930930739944351187708040037822108105697983018529921300277486094149269105712677374751164879455815185393395371001495146490416978221501351569800028842842393448555836910486037183218754013655794027528039329299851644787006463456162952383099752894635657833907958930587328480492546831654755627949756658554724024525108575961076341962292900510328611128404001877137799465932130220386963518903892403159969133882215092783063943679288192557384595152566356483424061922742307738886179947575613661171671781544283180451958232826666741028590085269
n2 = n3 ^ n1
p = gmpy2.gcd(n1, n2)
print(p)
assert (p != 1)
q1 = int(n1 // p)
q2 = int(n2 // p)
phi1 = (p-1) * (q1-1)
phi2 = (p-1) * (q2-1)
e = 65537
d1 = gmpy2.invert(e, phi1)
m1 = pow(c1, d1, n1)
print(m1)
from Crypto.Util.number import *
m1 = 45940908057800334992280176246569624084394175656577274619161848219023136326492308967132840820922928222674792554877
print(long_to_bytes(m1))
你是我的关键词(Keyworld) (初级)
- 关键词加密,密钥是YOU,网站即可
(校外)Virginia
- 词频分析得到密钥flag
- 然后已知凯撒,推规律
s = [86, 116, 128, 80, 98, 85, 139, 122, 134, 114, 125, 136, 117, 123, 129, 127, 128, 128, 142, 130, 140, 147, 127, 132, 131, 136, 151, 134, 152, 164]
h = [76,105,116,67,84,70,123] # 比对发现规律
cnt = 10
for i in s:
print(chr(i-cnt),end='')
cnt+=1
(校外)Where is P?
- e=3,先进行小明文攻击恢复P
import gmpy2
n = 24479907029118467064460793139240403258697681144532146836881997837526487637306591893357774423547391867013441147680031968367449693796015901951120514250935018725570026327610524687128709707340727799633444550317834481416507364804274266363478822257132586592232042108076935945436358397787891169163821061005102693505011197453089873909085170776511350713452580692963748763166981047023704528272230392479728897831538235554137129584665886878574314566549330671483636900134584707867654841021494106881794644469229030140144595938886437242375435914268001721437309283611088568191856208951867342004280893021653793820874747638264412653721
e = 3
res = 0
c = 22184346235325197613876257964606959796734210361241668065837491428527234174610482874427139453643569493268653377061231169173874401139203757698022691973395609028489121048788465356158531144787135876251872262389742175830840373281181905217510352227396545981674450409488394636498629147806808635157820030290630290808150235068140864601098322473572121965126109735529553247807211711005936042322910065304489093415276688746634951081501428768318098925390576594162098506572668709475140964400043947851427774550253257759990959997691631511262768785787474750441024242552456956598974533625095249106992723798354594261566983135394923063605
for i in range(200000000):
if gmpy2.iroot(c+n*i,3)[1] == 1:
res = gmpy2.iroot(c+n*i,3)[0]
print (res)
break
- 已知p高位,sage高位攻击
n = 24479907029118467064460793139240403258697681144532146836881997837526487637306591893357774423547391867013441147680031968367449693796015901951120514250935018725570026327610524687128709707340727799633444550317834481416507364804274266363478822257132586592232042108076935945436358397787891169163821061005102693505011197453089873909085170776511350713452580692963748763166981047023704528272230392479728897831538235554137129584665886878574314566549330671483636900134584707867654841021494106881794644469229030140144595938886437242375435914268001721437309283611088568191856208951867342004280893021653793820874747638264412653721
p = 66302204855869216148926460265779698576660998574555407124043768605865908069722142097621926304390549253688814246272903647124801382742681337653915017783954290069842646020090511605930590064443141710086879668946
p = p << 340
PR.<x> = PolynomialRing(Zmod(n))
f = x + p
roots = f.small_roots(X=2^340, beta = 0.4)
print(roots)
- 恢复p,正常rsa解密
p = 66302204855869216148926460265779698576660998574555407124043768605865908069722142097621926304390549253688814246272903647124801382742681337653915017783954290069842646020090511605930590064443141710086879668946
c = 6566517934961780069851397787369134601399136324586682773286046135297104713708615112015588908759927424841719937322574766875308296258325687730658550956691921018605724308665345526807393669538103819281108643141723589363068859617542807984954436567078438099854340705208503317269397632214274507740533638883597409138972287275965697689862321166613821995226000320597560745749780942467497435742492468670016480112957715214640939272457886646483560443432985954141177463448896521810457886108311082101521263110578485768091003174683555938678346359150123350656418123918738868598042533211541966786594006129134087145798672161268647536724
e = 65537
p = p << 340
p += 190359646620368037373858129269357427930662582059729745031738883187122682151344208537498381535001130363
if n % p == 0 :
print(1)
q = int(n // p)
phi = (q-1) * (p-1)
d = gmpy2.invert(e,phi)
m = pow(c,d,n)
print(long_to_bytes(m))
(校外)babyLCG
- 线性同余,网上找脚本写就行
from Crypto.Util.number import *
def gcd(a,b):
if(b==0):
return a
else:
return gcd(b,a%b)
s = [699175025435513913222265085178805479192132631113784770123757454808149151697608216361550466652878, 193316257467202036043918706856603526262215679149886976392930192639917920593706895122296071643390, 1624937780477561769577140419364339298985292198464188802403816662221142156714021229977403603922943, 659236391930254891621938248429619132720452597526316230221895367798170380093631947248925278766506, 111407194162820942281872438978366964960570302720229611594374532025973998885554449685055172110829, 1415787594624585063605356859393351333923892058922987749824214311091742328340293435914830175796909, 655057648553921580727111809001898496375489870757705297406250204329094679858718932270475755075698, 1683427135823894785654993254138434580152093609545092045940376086714124324274044014654085676620851, 492953986125248558013838257810313149490245209968714980288031443714890115686764222999717055064509, 70048773361068060773257074705619791938224397526269544533030294499007242937089146507674570192265]
t = []
for i in range(9):
t.append(s[i]-s[i-1])
all_n = []
for i in range(7):
all_n.append(gcd((t[i+1]*t[i-1]-t[i]*t[i]), (t[i+2]*t[i]-t[i+1]*t[i+1])))
MMI = lambda A, n,s=1,t=0,N=0: (n < 2 and t%N or MMI(n, A%n, t, s-A//n*t, N or n),-1)[n<1] #逆元计算
for n in all_n:
n=abs(n)
if n==1:
continue
a=(s[2]-s[1])*MMI((s[1]-s[0]),n)%n
ani=MMI(a,n)
b=(s[1]-a*s[0])%n
seed = (ani*(s[0]-b))%n
plaintext=seed
print(long_to_bytes(plaintext))
easy_math (中级)
- 二元一次方程组,z3能爆破
from z3 import *
p = Real('p')
q = Real('q')
s = Solver()
s.add(p*q == 2230791374046346835775433548641067593691369485828070649075162141394476183565187654365131822111419512477883295758461313983481545182887415447403634720326639070667688614534290859200753589300443797)
s.add(p**3-q**5 == 392490868359411675557103683163021977774935163924606169241731307258226973701652855448542714274348304997416149742779376023311152228735117186027560227613656229190807480010615064372521942836446425717660375242197759811804760170129768647414717571386950790115746414735411766002368288743086845078803312201707960465419405926186622999423245762570917629351110970429987377475979058821154568001902541710817731089463915930932142007312230897818177067675996751110894377356758932)
print(s.check())
print(s.model())
- 得到pq正常rsa解密
import gmpy2
from Crypto.Util.number import *
c = 2168563038335029902089976057856861885635845445863841607485310134441400500612435296818745930370268060353437465666224400129105788787423156958336380480503762222278722770240792709450637433509537280
p = 7321664971326604351487965655099805117568571010588695608389113791312918573783115429227542573780838065461696504325762281209452761930184231131129306271846427
q = 304683618109085947723284393392507415311
e = 65537
n = p*q
phi = (q-1) * (p-1)
d = gmpy2.invert(e,phi)
m = pow(c,d,n)
# m = 637558173724466425186024472873280955351137947957753869483412370269183338041518428156258150408573
print(long_to_bytes(m))
(校外)baby_xor
-
因为已知flag的一部分格式,所以可以通过m泄露p高位,然后再高位攻击出p
-
需要注意一下不要用bytes_to_long
可泄露的m位数是 7x8 = 56 ( LitCTF{ ) 所以需要补200位
Reverse
debase64
-
当然赛博厨子也能直接解
-
密文爆破
#include <bits/stdc++.h>
using namespace std;
string table = "ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789+/";
int main()
{
int key[4][3] = {0x46,0xed,0x18,0x96,0x56,0x9e,0xd2,0x72,0xb2,0xb3,0x80,0x70};
for(int cnt = 0; cnt < 4; cnt++){
for(int i = 0; i <= 62; i++){
for(int j = 0; j <= 62; j++){
for(int k = 0; k <= 62; k++){
for(int l = 0; l <= 62; l++){
int temp1 = ((4 * i) | (j >> 4) & 3) & 0xff;
int temp2 = ((16 * j) | (k >> 2)) & 0xff;
int temp3 = ((k << 6) | l) & 0xff;
if(temp1 == key[cnt][0] && temp2 == key[cnt][1] && temp3 == key[cnt][2]){
cout <<table[l] <<table[k] <<table[j] <<table[i];
break;
}
}}}}
}
}
Misc
Take me hand (初级)
- wirshark打开就有flag
这羽毛球怎么只有一半啊(恼 (初级)
- 半张图
- 010改一下图片高度即可
404notfound (初级)
- 010打开ctrl f就有flag
喜欢我的压缩包么 (初级)
- azpr爆破,114514
破损的图片(初级)
- 恢复文件头打开即可
两仪生四象 (中级)
_hash = {"111":"乾", "011":"兑", "101":"离" , "001":"震" , "110":"巽", "010":"坎" , "100":"艮", "000":"坤"}
_reverse_hash = {v: k for k, v in _hash.items()}
encoded_text = "坤乾兑艮兑坎坤坤巽震坤巽震艮兑坎坤震兑乾坤巽坤艮兑震巽坤巽艮坤巽艮艮兑兑艮震兑乾坤乾坤坤兑艮艮坤巽坤坤巽坎坤兑离坎震艮兑坤巽坎艮兑震坤震兑乾坤乾坎坤兑坎坤震艮离坤离乾艮震艮巽震离震坤巽兑艮兑坎坤震巽艮坤离乾艮坎离坤震巽坎坤兑坤艮兑震巽震巽坎坤巽坤艮兑兑坎震巽兑"
s = []
for i in encoded_text:
print(_reverse_hash[i],end='')
print()
s = '000111011100011010000000110001000110001100011010000001011111000110000100011001110000110100000110100100011011100001011111000111000000011100100000110000000110010000011101010001100011000110010100011001000001011111000111010000011010000001100101000101111100001100110001101001000110011100011010000001110100000101111100010101000001110010000011000100011001110001110010000110000100011011010001110011'
for i in range(0,len(s),10):
w = s[i:i+10]
w = '0b' + w
w = int(w,2)
print(chr(w),end='')
ssvvgg
-
base64解码保存jpg
-
010末尾看到hint
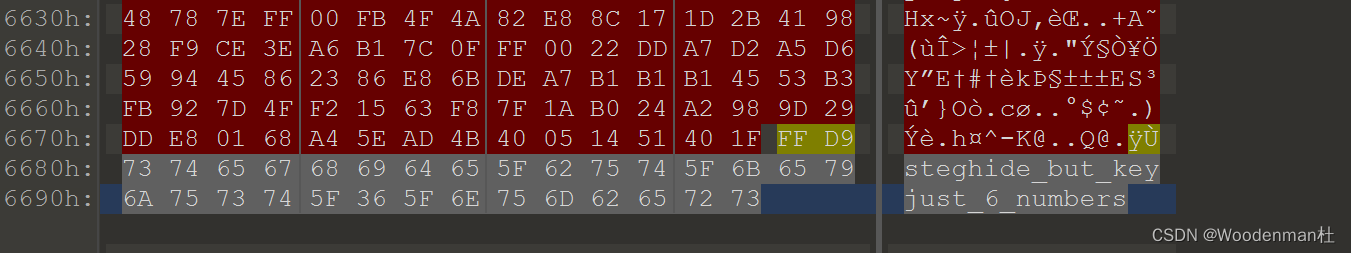
-
stegseek爆破


![[MYAQL / Mariadb] 数据库学习-数据导入导出](https://img-blog.csdnimg.cn/019f88f7a15746edb81eb54b4ca011a0.png)