资料
-
OpenID Connect Tokens
-
Kubernetes 与 OpenID 集成 SSO 登录测试
-
Introducing OIDC identity provider authentication for Amazon EKS
-
Understanding Amazon Cognito user pool OAuth 2.0 grants
-
在 Kubernetes 中使用 Keycloak OIDC Provider 对用户进行身份验证
-
深入浅出的谈谈Amazon EKS的身份认证处理
-
https://github.com/int128/kubelogin
eks 的三种认证方式
- Service account tokens
- Webhook token authentication
- OpenID connect tokens
除开集成了AWS IAM的webhook身份认证,EKS还提供了另外一种集成OIDC协议身份池的身份认证。需要注意的是前面一节介绍的webhook认证方式是默认开启的,即使使用OIDC的认证方式,webhook的认证也会持续可用
这种OIDC身份认证方式是开源k8s原生的,与AWS IAM完全无关。让k8s集群将用户池管理完全托管给外部的OIDC兼容的身份池,当k8s需要给来自于外部身份池的user授予权限时,可以直接使用rolebinding的方式,将k8s内部的role权限授予这个外部的user
官方博客提供了两种实现
- 使用cognito创建用户池
- 自建oidc ipp(例如keycloak)
使用cognito创建用户池
整体的逻辑如下
- 创建oidc idp,将用户加入
- 配置kubectl工具完成访问
cognito本身是aws支持的服务,集成度较高
CLIENT_ID=702vqsrjicklgb7c5b7b50i1gc
ISSUER_URL=https://cognito-idp.us-west-2.amazonaws.com/us-west-2_re1u6bpRA
POOL_ID=us-west-2_re1u6bpRA
aws cognito-idp admin-create-user --user-pool-id $POOL_ID --username test@example.com --temporary-password password
aws cognito-idp admin-set-user-password --user-pool-id $POOL_ID --username test@example.com --password Blah123$ --permanent
aws cognito-idp create-group --group-name secret-reader --user-pool-id $POOL_ID
aws cognito-idp admin-add-user-to-group --user-pool-id $POOL_ID --username test@example.com --group-name secret-reader
aws cognito-idp admin-initiate-auth --auth-flow ADMIN_USER_PASSWORD_AUTH \
--client-id $CLIENT_ID \
--auth-parameters USERNAME=test@example.com,PASSWORD=Blah123$ \
--user-pool-id $POOL_ID \
--query 'AuthenticationResult.IdToken'
output:
{
"sub": "86f7130a-5605-4c05-b402-c970b27633ce",
"aud": "702vqsrjicklgb7c5b7b50i1gc",
"cognito:groups": [
"secret-reader"
],
"event_id": "aa0723aa-12f3-49f1-9a21-7a7d542129bd",
"token_use": "id",
"auth_time": 1612760751,
"iss": "https://cognito-idp.us-west-2.amazonaws.com/us-west-2_re1u6bpRA",
"cognito:username": "86f7130a-5605-4c05-b402-c970b27633ce",
"exp": 1612764351,
"iat": 1612760751,
"email": "test@example.com"
}
kubectl config set-credentials cognito-user \
--auth-provider=oidc \
--auth-provider-arg=idp-issuer-url=$ISSUER_URL \
--auth-provider-arg=client-id=$CLIENT_ID \
--auth-provider-arg=refresh-token=<refresh_token> \
--auth-provider-arg=id-token=<id_token>
自建keycloak认证访问eks
关于keycloak配置sso访问aws可以参考之前的blog
官方博客给出的方案也使用了keycloak,和saml的配置类似,需要拿到issue url和client id
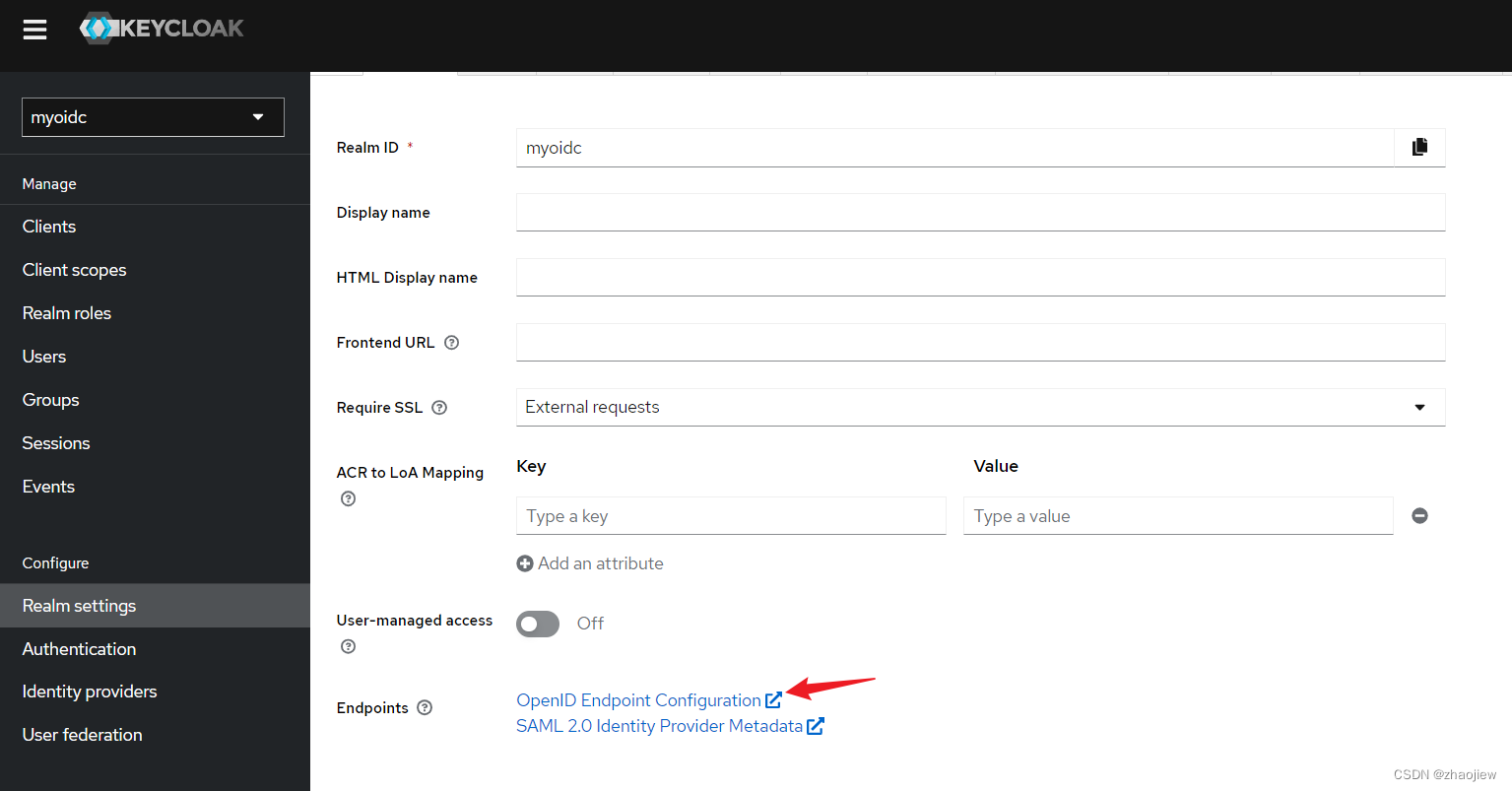
{
"issuer": "https://xxxxxxxx:8443/realms/myoidc",
"authorization_endpoint": "https://xxxxxxxx:8443/realms/myoidc/protocol/openid-connect/auth",
"token_endpoint": "https://xxxxxxxx:8443/realms/myoidc/protocol/openid-connect/token",
"introspection_endpoint": "https://xxxxxxxx:8443/realms/myoidc/protocol/openid-connect/token/introspect",
"userinfo_endpoint": "https://xxxxxxxx:8443/realms/myoidc/protocol/openid-connect/userinfo",
"end_session_endpoint": "https://xxxxxxxx:8443/realms/myoidc/protocol/openid-connect/logout",
"frontchannel_logout_session_supported": true,
"frontchannel_logout_supported": true,
"jwks_uri": "https://xxxxxxxx:8443/realms/myoidc/protocol/openid-connect/certs",
"check_session_iframe": "https://xxxxxxxx:8443/realms/myoidc/protocol/openid-connect/login-status-iframe.html",
"grant_types_supported": [
"authorization_code",
"implicit",
"refresh_token",
"password",
"client_credentials",
"urn:ietf:params:oauth:grant-type:device_code",
"urn:openid:params:grant-type:ciba"
],
}
但是执行以下命令关联会报错,查看issueUrl参数,必须使用域名,测试环境没有公开域名,无法继续以后再尝试吧
The URL of the OpenID identity provider that allows the API server to discover public signing keys for verifying tokens. The URL must begin with https:// and should correspond to the iss claim in the provider’s OIDC ID tokens. Per the OIDC standard, path components are allowed but query parameters are not. Typically the URL consists of only a hostname, like https://server.example.org or https://example.com . This URL should point to the level below .well-known/openid-configuration and must be publicly accessible over the internet.
aws eks associate-identity-provider-config \
--cluster-name worklearn \
--oidc identityProviderConfigName=awsoidc,issuerUrl=https://xxx:8443/realms/myoidc,clientId=awsoidc,groupsClaim=group,groupsPrefix=gid: \
--no-verify-ssl \
--region cn-north-1
创建完之后控制台结果
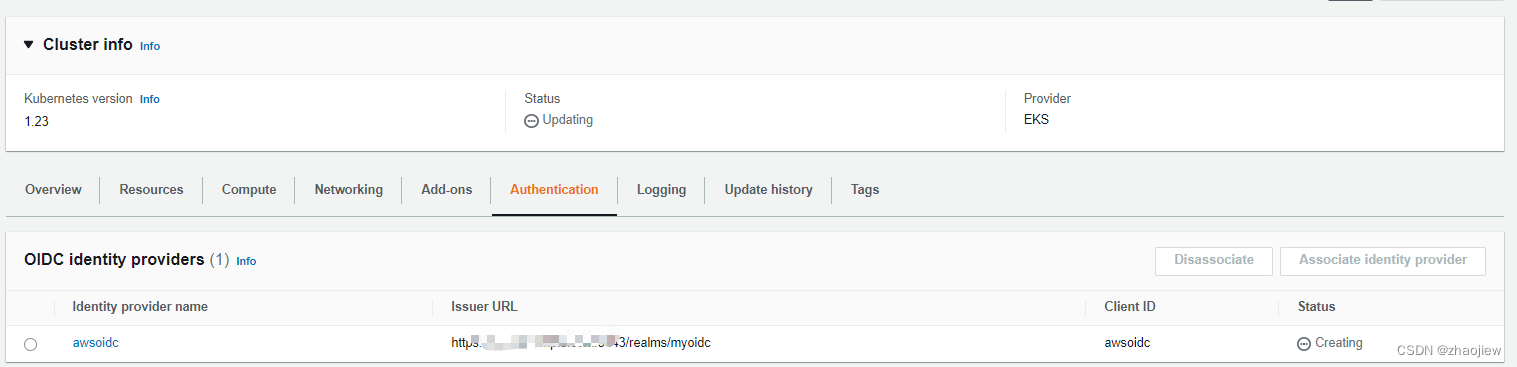
之后可以直接获取token访问apiserver,或者通过kubelogin等插件配置kubectl工具实现认证
curl -k --location --request POST 'https://<KEYCLOAK DOMAIN>/auth/realms/<REALM NAME>/protocol/openid-connect/token' \
--header 'Content-Type: application/x-www-form-urlencoded' \
--data-urlencode 'username=testuser' \
--data-urlencode 'password=<PASSWORD>' \
--data-urlencode 'grant_type=password' \
--data-urlencode 'client_secret=<CLIENT_SECRET>' \
--data-urlencode 'scope=profile openid' \
--data-urlencode 'client_id=<CLIENT ID>' | jq '.id_token' -r

![[附源码]计算机毕业设计springboot水果管理系统](https://img-blog.csdnimg.cn/957ee6822f544b5a8080e53da451e971.png)