mulesoft MCIA 破釜沉舟备考 2023.04.14.11
- 1. To implement predictive maintenance on its machinery equipment, ACME Tractors has installed thousands of IoT sensors that will send data for each machinery asset as sequences of JMS messages, in near real-time, to a JMS queue named SENSOR_DATA on a JMS server.
- 2. The ABC company has an Anypoint Runtime Fabric on VMs/Bare Metal (RTF-VM) appliance installed on its own customer-hosted AWS infrastructure.
- 3. When designing an upstream API and its implementation, the development team has been advised to not set timeouts when invoking downstream API.
- 4. An organization is creating a Mule application that will be deployed to CloudHub.
- 5. A company wants its users to log in to Anypoint Platform using the company's own internal user credentials.
- 6. Additional nodes are being added to an existing customer-hosted Mule runtime cluster to improve performance.
- 7. A new upstream API Is being designed to offer an SLA of 500 ms median and 800 ms maximum (99th percentile) response time.

1. To implement predictive maintenance on its machinery equipment, ACME Tractors has installed thousands of IoT sensors that will send data for each machinery asset as sequences of JMS messages, in near real-time, to a JMS queue named SENSOR_DATA on a JMS server.
The Mule application contains a JMS Listener operation configured to receive incoming messages from the JMS servers SENSOR_DATA JMS queue. The Mule application persists each received JMS message, then sends a transformed version of the corresponding Mule event to the machinery equipment back-end systems.
The Mule application will be deployed to a multi-node, customer-hosted Mule runtime cluster. Under normal conditions, each JMS message should be processed exactly once.
How should the JMS Listener be configured to maximize performance and concurrent message processing of the JMS queue?
A. Set numberOfConsumers = 1
Set primaryNodeOnly = false
B. Set numberOfConsumers = 1
Set primaryNodeOnly = true
C. Set numberOfConsumers to a value greater than one
Set primaryNodeOnly = true
D. Set numberOfConsumers to a value greater than one
Set primaryNodeOnly = false
Answer: D
2. The ABC company has an Anypoint Runtime Fabric on VMs/Bare Metal (RTF-VM) appliance installed on its own customer-hosted AWS infrastructure.
Mule applications are deployed to this RTF-VM appliance. As part of the company standards, the Mule application logs must be forwarded to an external log management tool (LMT).
Given the company’s current setup and requirements, what is the most idiomatic (used for its intended purpose) way to send Mule application logs to the external LMT?
A. In RTF-VM, install and configure the external LTM’s log-forwarding agent
B. In RTF-VM, edit the pod configuration to automatically install and configure an Anypoint Monitoring agent
C. In each Mule application, configure custom Log4j settings
D. In RTF-VM. configure the out-of-the-box external log forwarder
Answer: A
3. When designing an upstream API and its implementation, the development team has been advised to not set timeouts when invoking downstream API.
Because the downstream API has no SLA that can be relied upon. This is the only donwstream API dependency of that upstream API. Assume the downstream API runs uninterrupted without crashing.
What is the impact of this advice?
A. The invocation of the downstream API will run to completion without timing out.
B. An SLA for the upstream API CANNOT be provided.
C. A default timeout of 500 ms will automatically be applied by the Mule runtime in which the upstream API implementation executes.
D. A load-dependent timeout of less than 1000 ms will be applied by the Mule runtime in which the downstream API implementation executes.
Answer: B
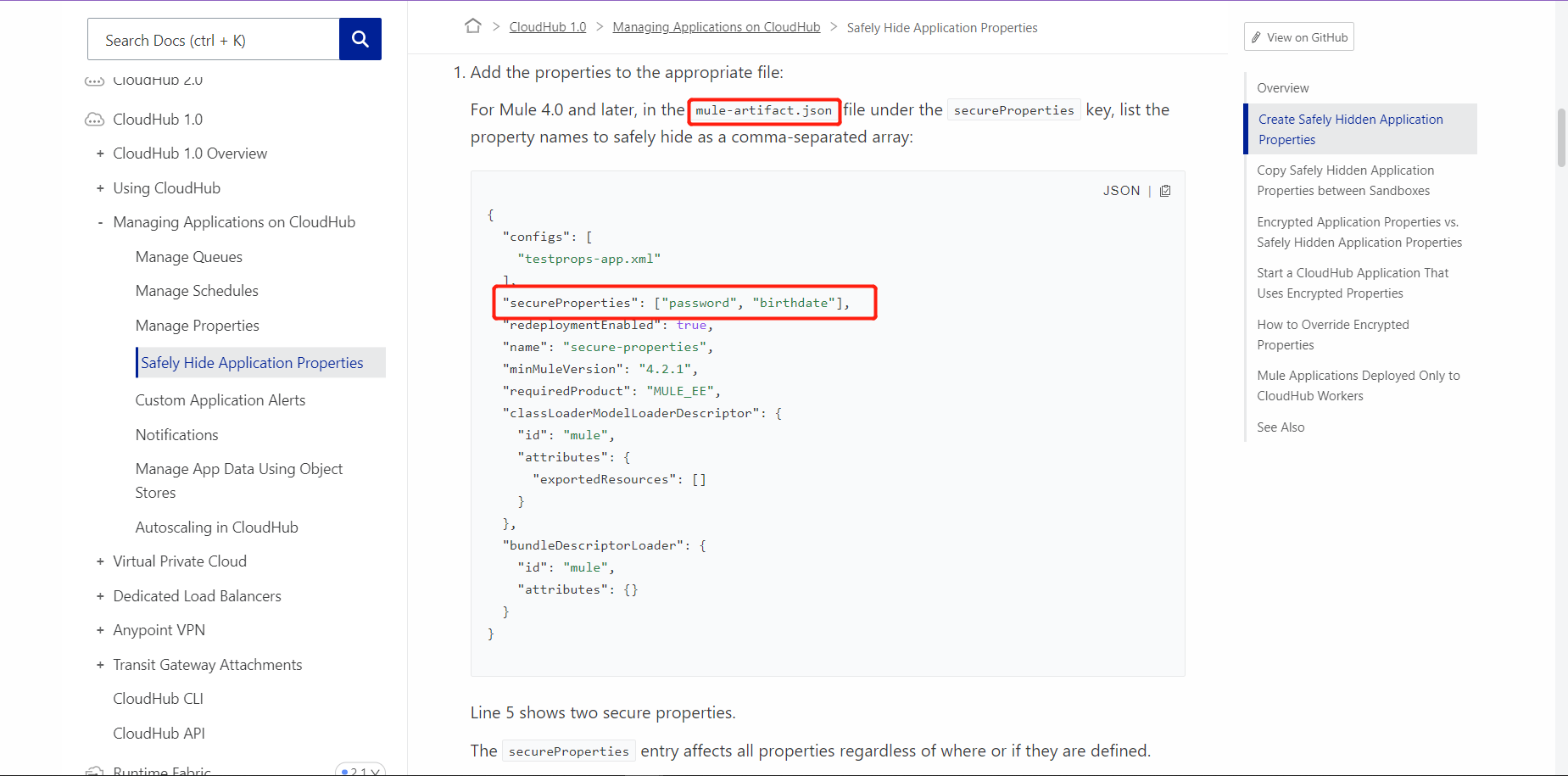
4. An organization is creating a Mule application that will be deployed to CloudHub.
The Mule application has a property named dbPassword that stores a database user’s password. The organization’s security standards indicate that the dbPassword property must be hidden from every Anypoint Platform user after the value is set in the Runtime Manager Properties tab.
What configuration in the Mule application helps hide the dbPassword property value in Runtime Manager?
A. Use secure::dbPassword as the property placeholder name and store the cleartext (unencrypted) value in a secure properties placeholder file
B. Use secure::dbPassword as the property placeholder name and store the property encrypted value in a secure properties placeholder file
C. Add the dbPassword property to the secureProperties section of the pom.xml file
D. Add the dbPassword property to the secureProperties section of the mule-artifact.json file
Answer: B
Reference: https://docs.mulesoft.com/runtime-manager/secure-application-properties
5. A company wants its users to log in to Anypoint Platform using the company’s own internal user credentials.
To achieve this, the company needs to integrate an external identity provider (IdP) with the
company’s Anypoint Platform master organization, but SAML 2.0 CANNOT be used.
Besides SAML 2.0, what single-sign-on standard can the company use to integrate the IdP with their Anypoint Platform master organization?
A. SAML 1.0
B. OAuth 2.0
C. Basic Authentication
D. OpenID Connect
Answer: D
Explanation:
As the Anypoint Platform organization administrator, you can configure identity management in Anypoint
Platform to set up users for single sign-on (SSO).
Configure identity management using one of the following single sign-on standards:
- OpenID Connect: End user identity verification by an authorization server including SSO
- SAML 2.0: Web-based authorization including cross-domain SSO
6. Additional nodes are being added to an existing customer-hosted Mule runtime cluster to improve performance.
Mule applications deployed to this cluster are invoked by API clients through a load
balancer.
What is also required to carry out this change?
A. A new load balancer must be provisioned to allow traffic to the new nodes in a round-robin fashion
B. External monitoring tools or log aggregators must be configured to recognize the new nodes
C. API implementations using an object store must be adjusted to recognize the new nodes and persist to them
D. New firewall rules must be configured to accommodate communication between API clients and the new nodes
Answer: B
Explanation:
- Clustering is a group of servers or mule runtime which acts as a single unit.
- Mulesoft Enterprise Edition supports scalable clustering to provide high availability for the Mulesoft application.
- In simple terms, virtual servers composed of multiple nodes and they communicate and share
information through a distributed shared memory grid. - By default, Mulesoft ensures the High availability of applications if clustering implemented.
- Let’s consider the scenario one of the nodes in cluster crashed or goes down and under maintenance. In such cases, Mulesoft will ensure that requests are processed by other nodes in the cluster. Mulesoft clustering also ensures that the request is load balanced between all the nodes in a cluster.
- Clustering is only supported by on-premise Mule runtime and it is not supported in Cloudhub.
Correct answer is External monitoring tools or log aggregators must be configured to recognize the new nodes - Rest of the options are automatically taken care of when a new node is added in cluster.
Reference: https://docs.mulesoft.com/runtime-manager/cluster-about
7. A new upstream API Is being designed to offer an SLA of 500 ms median and 800 ms maximum (99th percentile) response time.
The corresponding API implementation needs to sequentially invoke 3 downstream APIs of very similar complexity. The first of these downstream APIs offers the following SLA for its response time: median: 100 ms, 80th percentile: 500 ms, 95th percentile: 1000 ms.
If possible, how can a timeout be set in the upstream API for the invocation of the first downstream API to meet the new upstream API’s desired SLA?
A. Set a timeout of 100 ms; that leaves 400 ms for the other two downstream APIs to complete
B. Do not set a timeout; the Invocation of this API Is mandatory and so we must wait until it responds
C. Set a timeout of 50 ms; this times out more invocations of that API but gives additional room for retries
D. No timeout is possible to meet the upstream API’s desired SLA; a different SLA must be negotiated with the first downstream API or invoke an alternative API
Answer: D