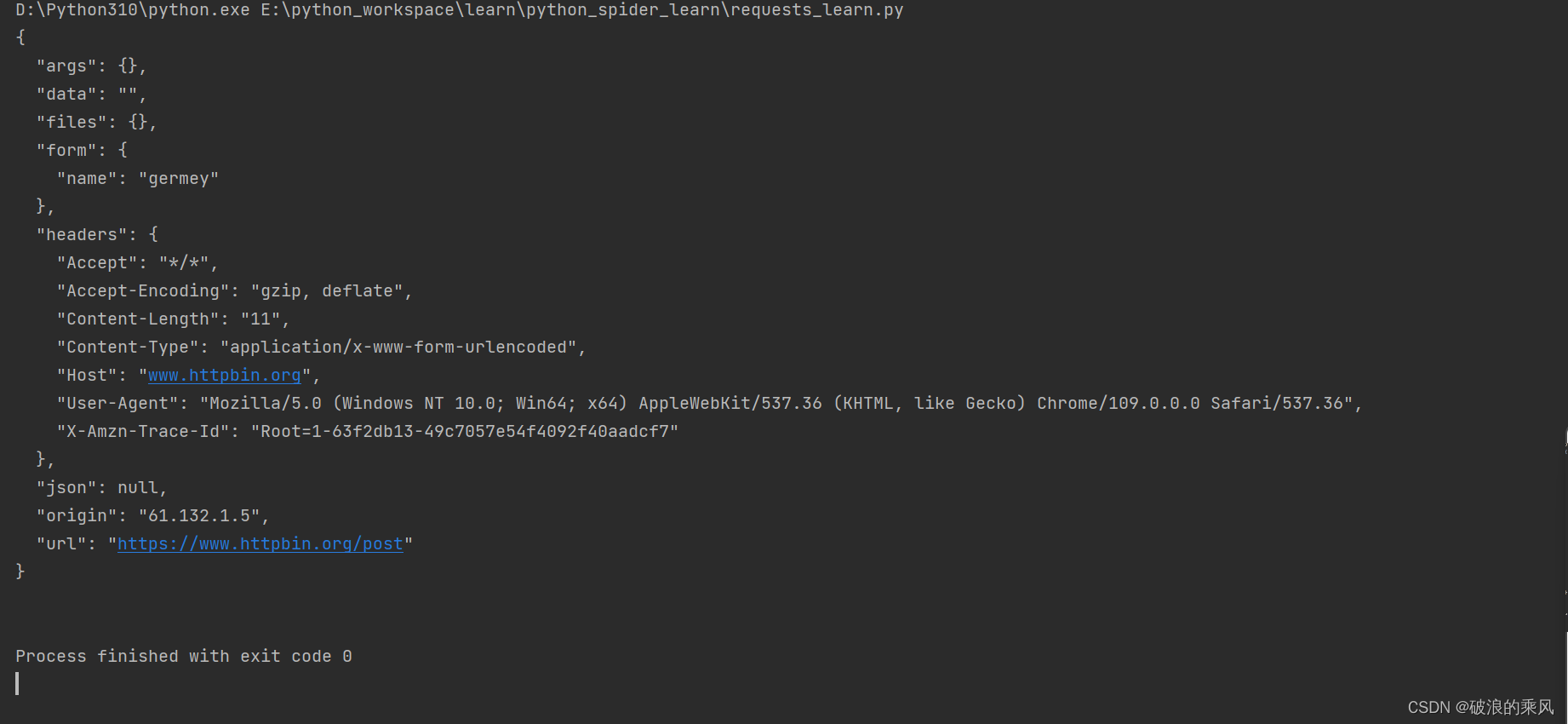
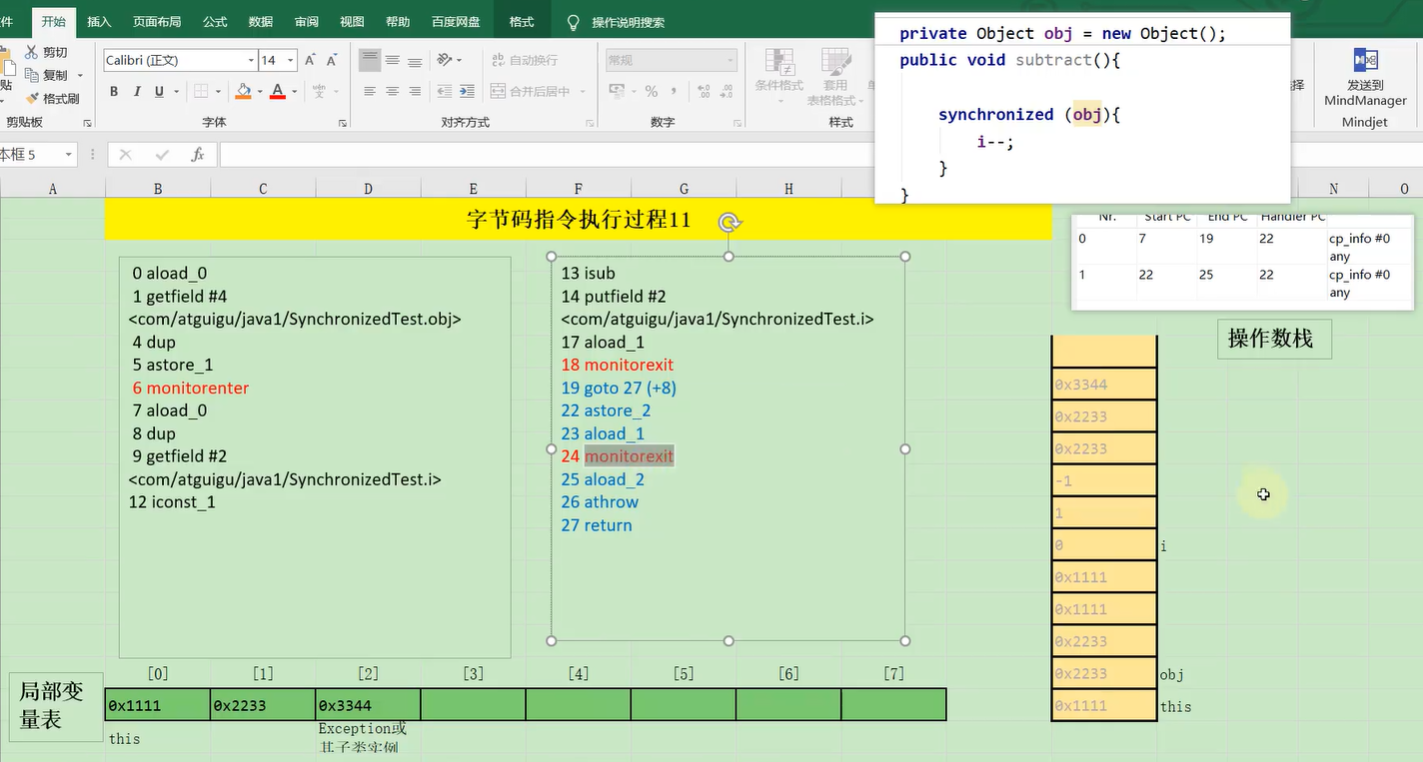
301、Drag and drop the virtual component from the left onto their descriptions on the right.
302、Which two actions, when applied in the LAN network segment, will facilitate Layer 3 CAPWAP discovery for lightweight AP? (Choose two.)
A. Utilize DHCP option 43
B. Configure WLC IP address on LAN switch
C. Enable port security on the switch port.
D. Utilize DHCP option 17
E. Configure an ip helper-address on the router interface.
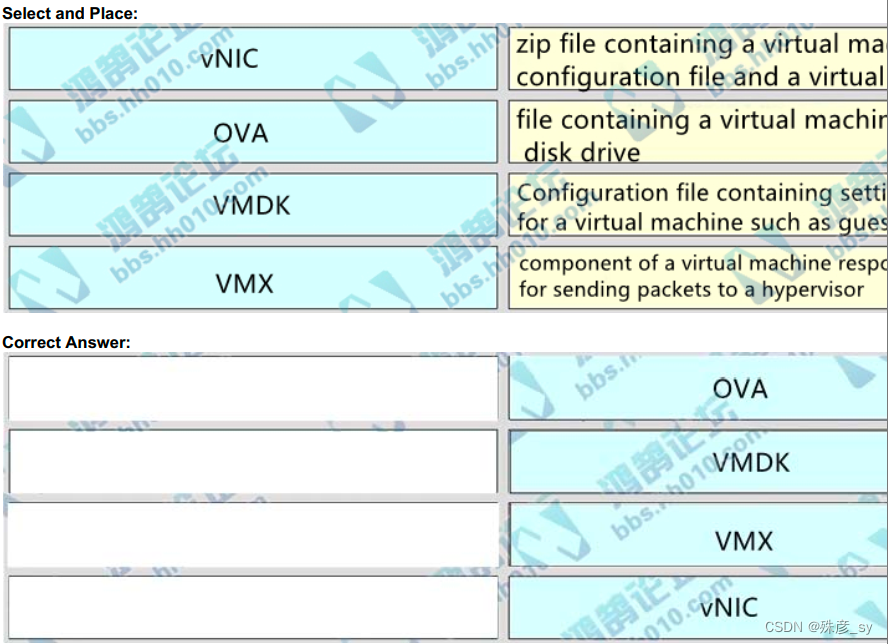
303、
Refer to the exhibit. What step resolves the authentication issue?
A. use basic authentication
B. change the port to 12446
C. target 192 168.100.82 in the URI
D. restart the vsmart host
304、 Which data is properly formatted with JSON?
A. {
"name": "Peter",
"age", "25",
"likesJson": true,
"characteristics": ["small","strong",18]
}
B. {
"name": "Peter",
"age": "25",
"likesJson": true,
"characteristics": ["small","strong","18"],
}
C. {
"name": Peter,
"age": 25,
"likesJson": true,
"characteristics": ["small","strong","18"],
}
D. {
"name":"Peter"
"age":"25"
"likesJson":true
"characteristics":["small","strong",18]
}
305、
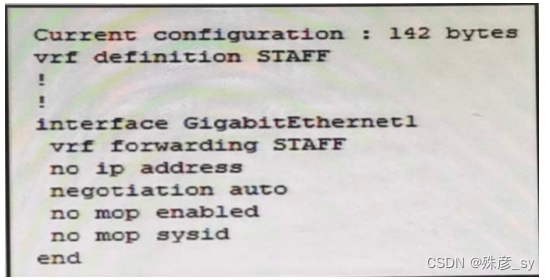
Refer to the exhibit. An engineer must assign an IP address of 192. 168.1.1/24 to the GigabitEthemnet interface. Which two commands must be.added to the existing configuration to accomplish this task?(Choose two.)
A. Router(config-if)#ip address 192.168.1.1 255.255.255.0
B. Router(config-if)#address-family ipv4
C. Router(config-vrf)#address-family ipv6
D. Router(config-vrf)#address-family ipv4
E. Router(config-vrf)#ip address 192.168.1.1 255.255.255.0
306、A company has an existing Cisco 5520 HA cluster using SSO. An engineer deploys a new single Cisco Catalyst 9800 WLC to test new features. The engineer successfully configures a mobility tunnel between the 5520 cluster and 9800 WLC.Clients connected to the corporate WLAN roam seamlessly between access points on the 5520 and 9800 WLC. After a failure on the primary 5520 WLC, all WLAN services remain functional;however, clients cannot roam between the 5520 and 9800 controllers without dropping their connection. Which feature must be configured to remedy the issue?
A. mobility MAC on the 5520 cluster
B. mobility MAC on the 9800 WLC
C. new mobility on the 5520 cluster
D. new mobility on the 9800 WLC
307、Which three methods does Cisco DNA Center use to discover devices? (Choose three.)
A. CDP
B. SNMP
C. LLDP
D. ping
E. NETCONF
F. a specified range of IP addresses
308、What is the difference between the MAC address table and TCAM?
A. The MAC address table supports partial matches. TCAM requires an exact match
B. TCAM is used to make L2 fonwarding decisions. CAM is used to build routing tables
C. The MAC address table is contained in TCAM. ACL and QoS information is stored in TCAM
D. Router prefix lookups happen in TCAM. MAC address table lookups happen in CAM
309、The following system log message is presented after a network administrator configures a GRE tunnel:%TUN-RECURDOWN Interface Tunnel 0 temporarily disabled due to recursive
routing
Why is Tunnel 0 disabled?
A. Because dynamic routing is not enabled
B. Because the tunnel cannot reach its tunnel destination.
C. Because the best path to the tunnel destination is through the tunnel itself
D. Because the router cannot recursively identify its egress forwarding interfac
310、

Refer to the exhibit. A network engineer must simplify the IPsec configuration by enabling IPsec over GRE
using IPsec profiles. Which two configuration changes accomplish this? (Choose two).
A. Remove the crypto map and modify the ACL to allow traffc between 10.10.0.0/24 to 10.20.0.0/24.
B. Create an IPsec profile, associate the transform-set ACL, and apply the profile to the tunnel interface.
C. Apply the crypto map to the tunnel interface and change the tunnel mode to tunnel mode ipsec ipv4
D. Remove all configuration related to crypto map from R1 and R2 and eliminate the ACL
E. Create an IPsec profile, associate the transform-set, and apply the profile to the tunnel interface.
311、
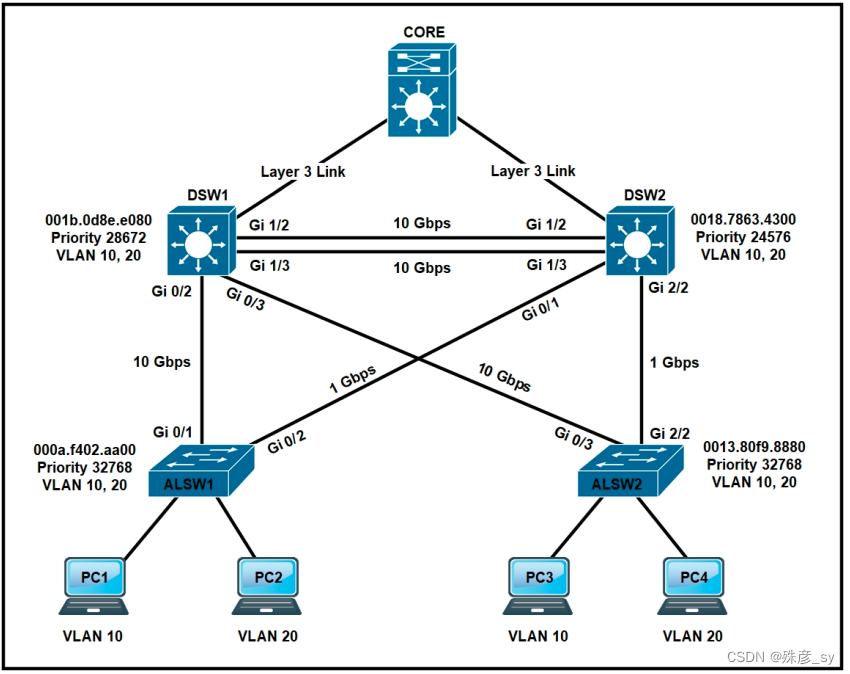
Refer to the exhibit. All switches are confiqured with the default port priority value. Which two commands ensure that traffic from PC1 is forwarded over the Gi1/3 trunk port between DSW1 and DSW2? (Choose two.)
A. DSW1 (config-if)#spanning-tree port-priority 0
B. DSW2(config-if)#spanning-tree port-priority 128
C. DSW2(config-if)#spanning-tree port-priority 16
D. DSW2(config)#interface gi1/3
E. DSW1(config)#interface gi1/3
312、Which encryption hashing algorithm does NTP use for authentication?
A. SSL
B. MD5
C. AES128
D. AES256
313、A customer has completed the installation of a Wi-Fi 6 greenfield deployment at their new campus. They want to leverage Wi-Fi 6 enhanced speeds.on the trusted employee WLAN. To configure the employee WLAN, which two Layer 2 security policies should be used? (Choose two.)
A. WPA (AES)
B. WEP
C. WPA2 (AES)
D. 802.1X
E. OPEN
314、

Refer to the exhibit. A network engineer configures OSPF and reviews the router confguration. Whichinterface or interfaces are able to establish OSPF adjacency?
A. GigabitEthernet0/1 and GigabitEthemnet0/1.40
B. only GigabitEthernet0/0
C. GigabitEthernet0/0 and GigabitEthernet0/1
D. only GigabitEthernet0/1
315、

Refer to the exhibit. Communication between London and New York is down. Which command set must be
applied to resolve this issue?
A. NewYork(config)int f0/1
NewYork(config)#switchport mode dynamic desirable
NewYork(config)end
NewYork#
B. NewYork(config)int f0/1
NewYork(config)switchport nonegotiate
NewYork(config)#end
NewYork#
C. NewYork(config)#int f0/1
NewYork(config)#switchport trunk encap dot1q
NewYork(config)#fend
NewYork#
D. NewYork(config)#int f0/1
NewYork(config)#switchport mode trunk
NewYork(config)#end
NewYork#
316、 What is YANG used for?
A. scraping data via CLI
B. processing SNMP read-only polls
C. describing data models
D. providing a transport for network configuration data between client and server
317、An engineer must configure a GRE tunnel interface in the default mode. The engineer has assigned an IPv4 address on the tunnel and sourced the tunnel from an Ethernet interface. Which additional configuration must be made on the tunnel interface?
A. (config-if)# tunnel destination <ip address>
B. (config-if)# keepalive <seconds retries>
C. (config-if)# ip tcp adjust-mss <value>
D. (config-if)# ip mtu svalue>
318、
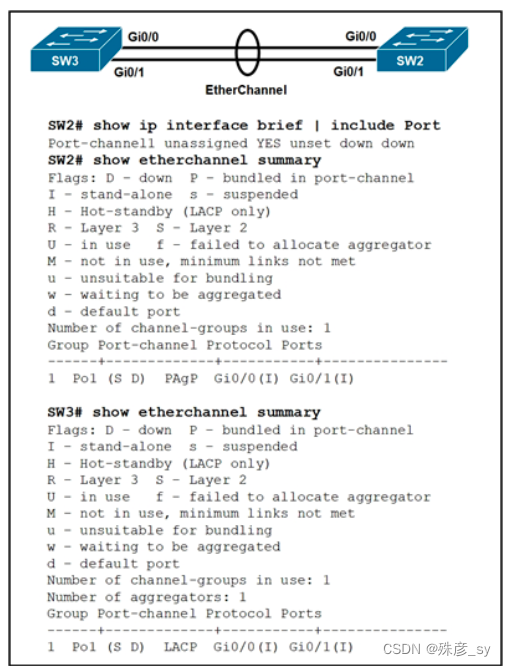
Refer to the exhibit. Which action resolves the EtherChannel issue between SW2 and SW3?
A. Configure channel-group 1 mode active on both interfaces
B. Configure switchport mode trunk on SW2
C. Configure switchport nonegotiate on SW3
D. Configure channel-group 1 mode desirable on both interfaces
319、Which two network problems indicate a need to implement QoS in a campus network? (Choose two.)
A. port flapping
B. excess jitter
C. misrouted network packets
D. duplicate IP addresses
E. bandwidth-related packet loss
320、

Refer to the exhibit Which configuration change ensures that R1 is the active gateway whenever it is in a functional state for the 172. 30.110.0/24 network?
A. R2
standby 1 priority 100
standby 1 preempt
B. R1
standby 1 preempt
R2
standby 1 priority 100
C. R1
standby 1 preempt
R2
standby 1 priority 90
D. R2
standby 1 priority 90
standby 1 preempt
321、In a Cisco SD-Access solution, what is the role of the Identity Services Engine?
A. It is leveraged for dynamic endpoint to group mapping and policy definition.
B. It provides GUI management and abstraction via apps that share context
C. It is used to analyze endpoint to app flows and monitor fabric status
D. It manages the LISP EID database.
322、Which two methods are used to reduce the AP coverage area? (Choose two.)
A. Reduce AP transmit power.
B. Reduce channel width from 40 MHz to 20 MHz.
C. Disable 2.4 GHz and use only 5 GHz.
D. Increase minimum mandatory data rate.
E. Enable Fastlane.
323、Which outcome is achieved with this Python code?client.connect (ip, port= 22, username= usr, password= pswd )stdin, stdout, stderr = client.exec_command ('show ip bgp 192.168.101.0
bestpathin')print (stdout)
A. connects to a Cisco device using SSH and exports the BGP table for the prefix
B. connects to a Cisco device using SSH and exports the routing table information
C. displays the output of the show command in a formatted way
D. connects to a Cisco device using Telnet and exports the routing table information
324、Which technology does VXLAN use to provide segmentation for Layer 2 and Layer 3 traffic?
A. VNI
B. VRF
C. bridge domain
D. VLAN
325、Based on the output below, which Python code shows the value of the "upTime" key?
{
"response": [{
"family": "Routers",
"type. "Cisco ASR 1001-X Router",
"errorCode": null
"location": null,macAddress" "00:c8:8b:80:bc:00",
"hostname": "asr1001-x abcinc","role": "BORDER ROUTER",
"lastUpdateTime": 1577391777128,
"serialNumber":"FXS1932Q2SE",
"softwareeVersion": "16.3.2",
"locationName": null,
"upTime":"49 days. 13:43:44:231",
"lastUpdated": "2019-12-22 14:55:23"
}]
}
A. json_data = json.loads(response text)
print(json_datalresponsel['family']['upTime'])
B. json_data = response.json()
print(json_data['response'][0]['upTime'])
C. json_data = response.json()
print(json_data)['response'][family]['upTime'])
D. json_data = response.json()
print(json_data['response'][0][upTime])
326、
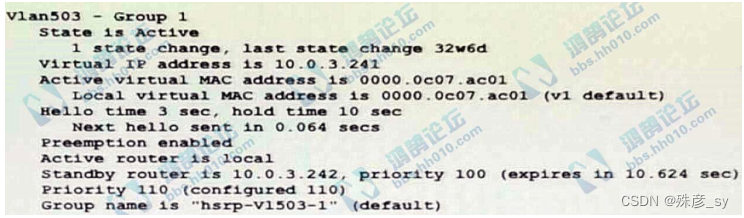
Refer to the exhibit. Which two facts does the device output confirm? (Choose two.)
A. The device's HSRP group uses the virtual IP address 10.0.3.242
B. The device is configured with the default HSRP priority.
C. The standby device is configured with the default HSRP priority.
D. The device is using the default HSRP hello timer.
E. The device sends unicast messages to its peers.
327、In a three-tier hierarchical campus network design, which action is a design best-practice for the core layer?A. provide QoS prioritization services such as marking, queueing, and classification for critical network traffic.
B. provide redundant Layer 3 point-to-point links between the core devices for more predictable and faster convergence
C. provide advanced network security features such as 802.1X. DHCP snooping, VACLs, and port security
D. provide redundant aggregation for access layer devices and first-hop redundancy protocols such as VRRP
328、What is a VPN in a Cisco SD-WAN deployment?
A. common exchange point between two different services
B. attribute to identify a set of services offered in specific places in the SD-WAN fabric
C. virtualized environment that provides traffic isolation and segmentation in the SD-WAN fabric
D. virtual channel used to carry control plane information
329、What is an emulated machine that has dedicated compute, memory, and storage resources and a fully installed operating system?
A. container
B. mainframe
C. host
D. virtual machine
330、Which entity is a Type 1 hypervisor?
A. Oracle VM VirtualBox
B. VMware server
C. Citrix XenServer
D. Microsoft Virtual PC
331、
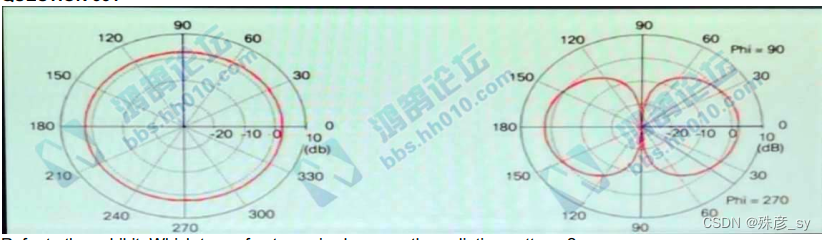
Refer to the exhibit. Which type of antenna is shown on the radiation patterns?
A. omnidirectional
B. Yagi
C. dipole
D. patch
332、

Refer to the exhibit. Which JSON syntax is derived from this data?
A. {[{'First Name': Johnny', "Last Name': 'Table', "Hobbies': [Running', Video games']}, {First Name' 'Billy, "Last Name': 'Smith', "Hobbies': ['Napping', 'Reading']}]}
B. {'Person': [{First Name': 'Johnny', 'Last Name': 'Table', "Hobbies: 'Running', 'Video games'}, {First Name': 'Billy', 'Last Name': 'Smith', "Hobbies": Napping', Reading'}]}
C. {[{'First Name': 'Johnny', "Last Name': 'Table', 'Hobbies': 'Running', 'Hobbies': 'Video games'}, {'First Name': 'Billy', 'Last Name': 'Smith','Hobbies': 'Napping', 'Hobbies': 'Reading'}]}
D. {'Person': {{'First Name': 'Johnny', 'Last Name': 'Table', 'Hobbies': ['Running', 'Video games']}, {'First Name': 'Billy', 'Last Name': 'Smith','Hobbies':['Napping', 'Reading']}]}
333、In a fabric-enabled wireless network, which device is responsible for maintaining the endpoint ID database?
A. fabric border node
B. fabric edge node
C. fabric wireless controller
D. control plane node
334、

Refer to the exhibit A network administrator confiqured RSPAN to troubleshoot an issue between switch1 and switch2. The switches are connected using interface GigabitEthernet 1/1. An external packet capture device is connected to swich2 interface GigabitEthernet1/2. Which two commands must be added to complete this confiquration? (Choose two.)
A. switch2(config)# monitor session 2 destination vlan 10
B. switch1(config)# interface GigabitEthernet 1/1
switch1(confia-if# switchport mode access
switch1(config-if)# switchport access vlan 10
switch2(config)# interface GigabitEthernet 1/1
switch2(config-if)# switchport mode access
switch2(config-if)# switchport access vlan 10
C. switch2(config)# monitor session 1 source remote vlan 70
switch2(config)# monitor session 1 destination interface GigabitEthernet1/1
D. switch2(config-if)# switchport trunk allowed vlan 10,20,30,40,50,60,70-80
E. switch2(config)# monitor session 1 source remote vlan 70
switch2(confia)# monitor session 1 destination interface GigabitEthernet1/2
335、What is the data policy in a Cisco SD-WAN deployment?
A. list of ordered statements that define node configurations and authentication used within the SDWAN overlay
B. Set of statements that defines how data is forwarded based on IP packet information and specific VPNs
C. detailed database mapping several kinds of addresses with their corresponding location
D. group of services tested to guarantee devices and links liveliness within the SD-WAN overlay
336、What ate two characteristics of Cisco SD-Access elements? (Choose two )
A. The border node is required for communication between fabric and nonfabric devices.
B. Fabric endpoints are connected directly to the border node
C. Traffic within the fabric always goes through the control plane node
D. The control plane node has the full RLOC-to-EID mapping database
E. The border node has the full RLOC-to-EID mapping database
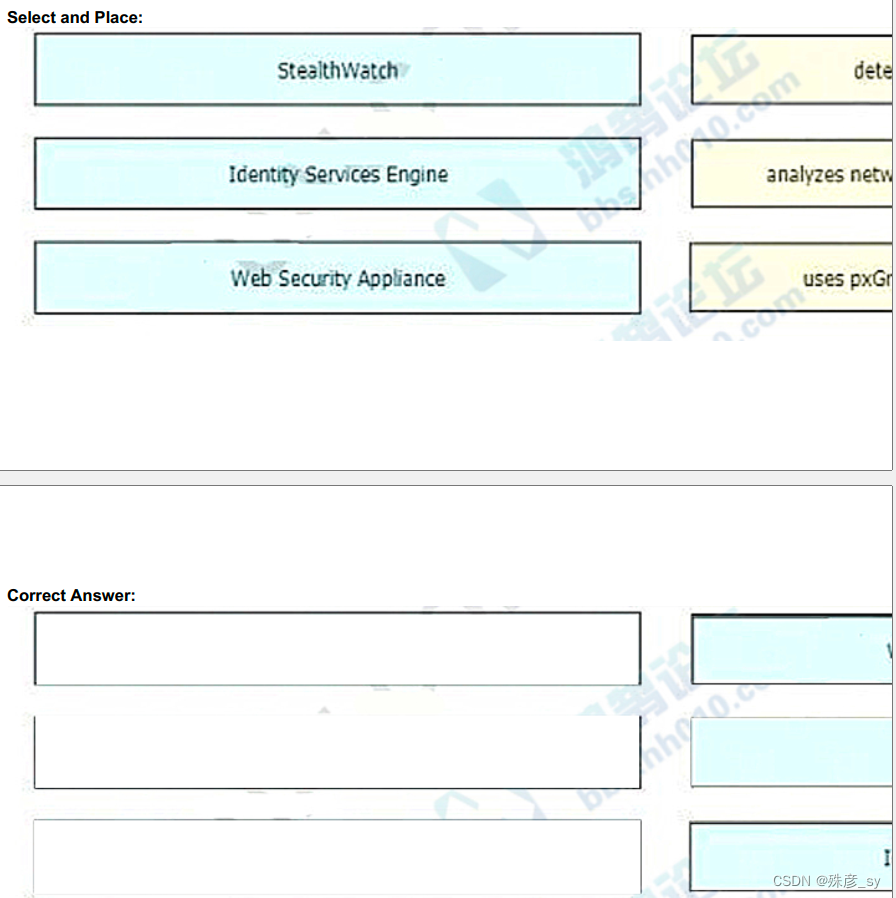
337、Drag and drop the solutions that comprise Cisco Cyber Threat Defense from the left onto the objectives they accomplish on the right.
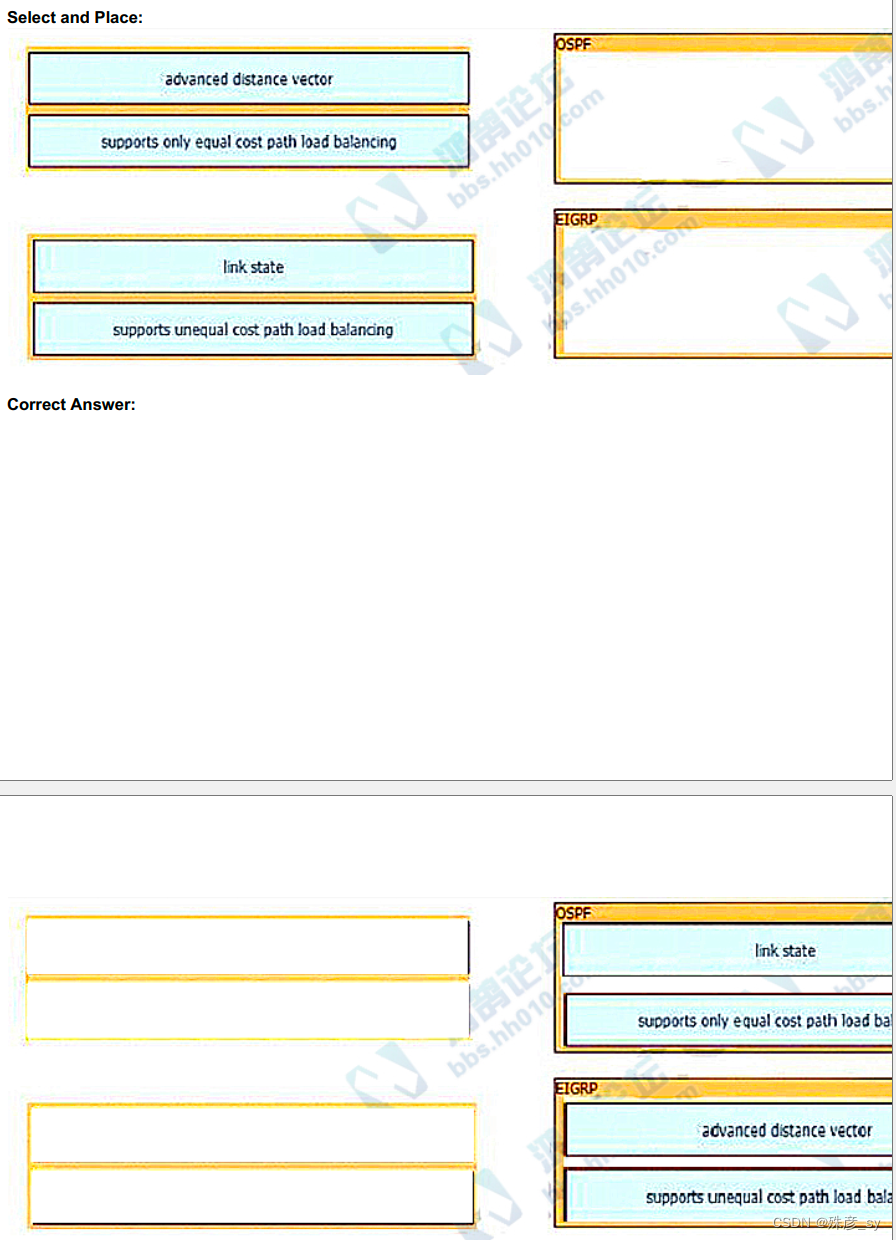
338、Drag and drop the descriptions from the left onto the routing protocol they describe on the right.
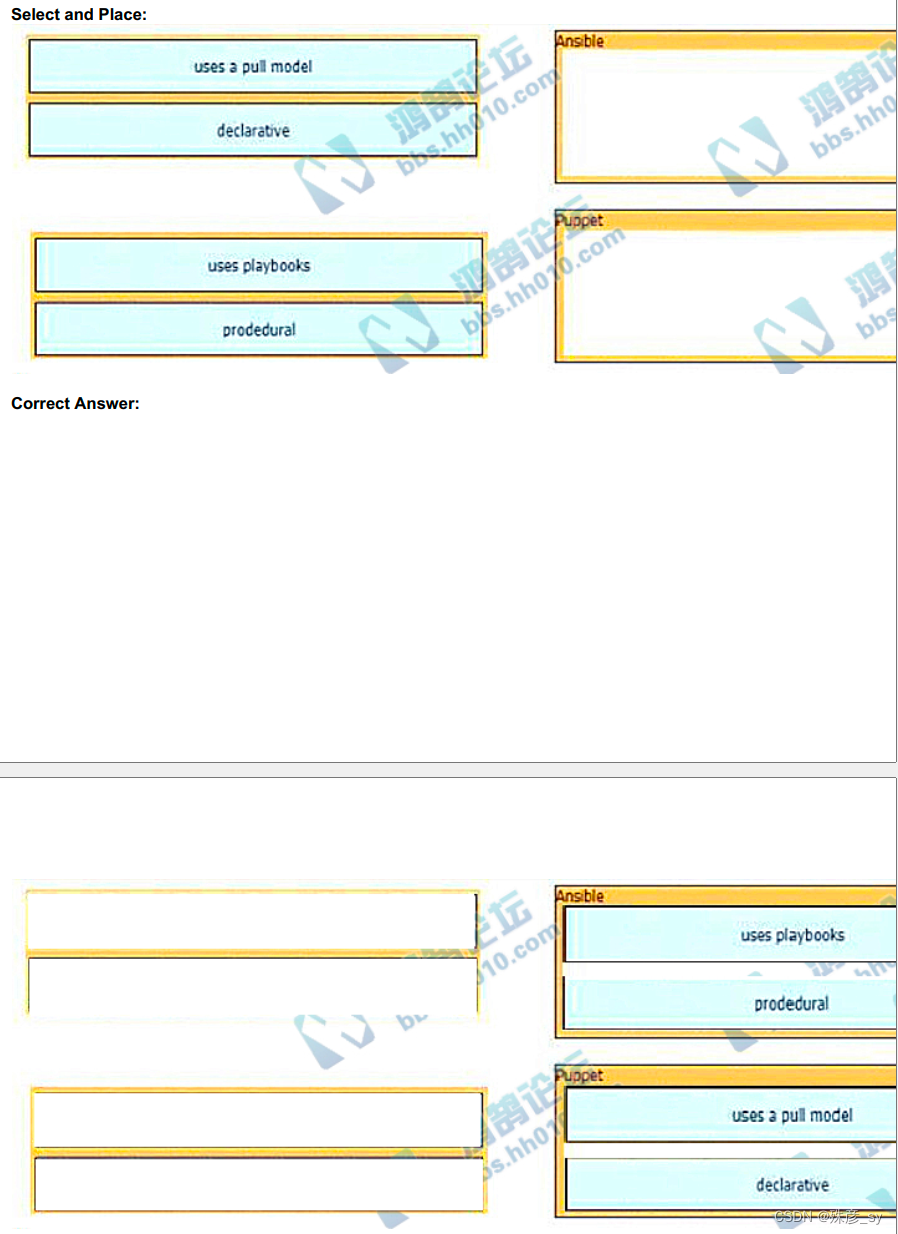
339、Drag and drop the characteristic from the left onto the orchestration tools that they describe on the right.
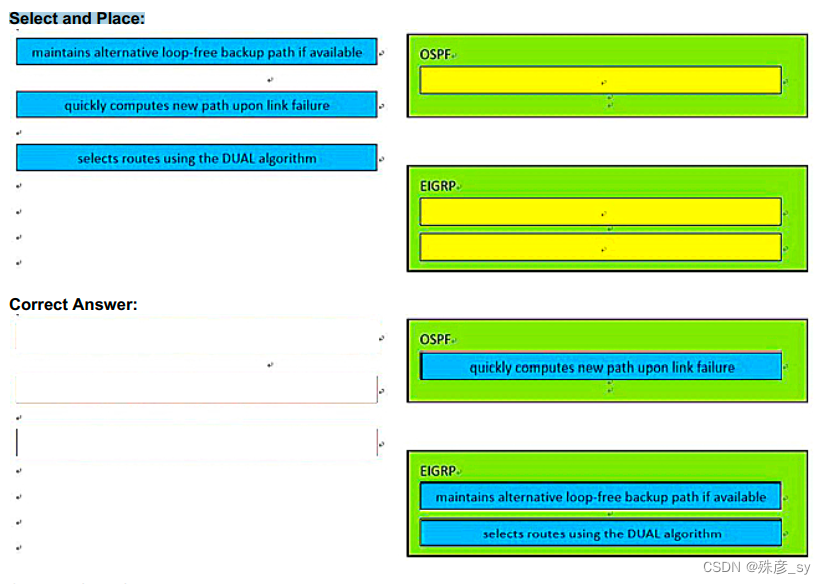
340、Drag and drop the characteristics from the left onto the routing protocols they describes on the right.
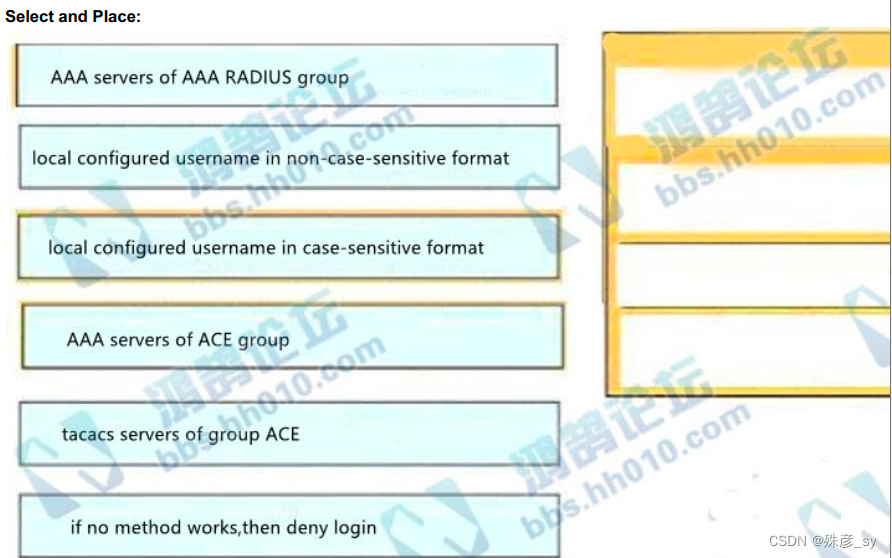
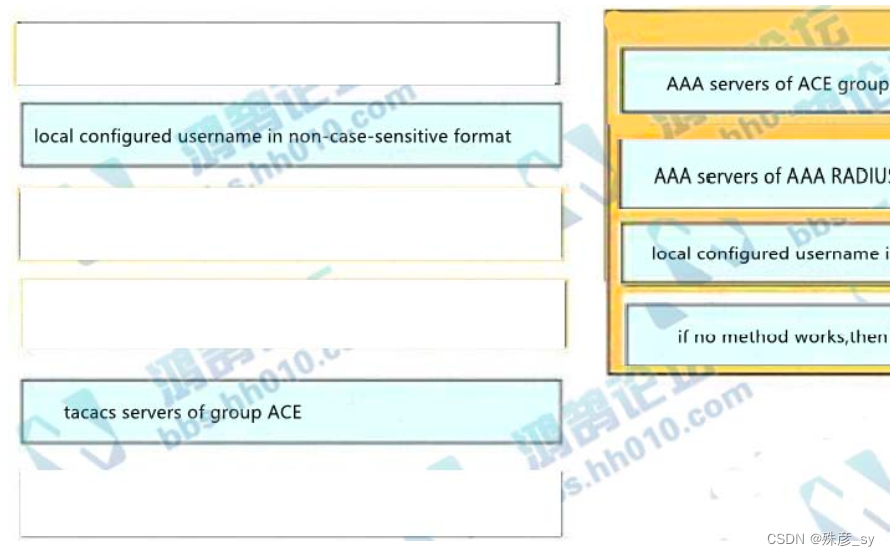
341、An engineer creates the configuration below. Drag and drop the authentication methods from the left into
the order of priority on the right. Not all options are used.
R1#show run | i aaa
aaa new-model
aaa authentication login default froup ACE group AAA_RADIUS local-case
aaa session-id common
R1#
342、What is a characteristic of a virtual machine?
A. It must be aware of other virtual machines, in order to allocate physical resource for
them
B. It is deployable without a hypervisor to host it
C. It must run the same operating system as its host
D. It relies on hypervisor to allocate computing resources for it
343、 How do stratum levels relate to the distance from a time source?
A. Stratum 0 devices are connected directly to an authoritative time source
B. Stratum 1 devices are connected directly to an authoritative time source
C. Stratum 15 devices are connected directly to an authoritative time source
D. Stratum 15 devices are an authoritative time source
344、What is the function of a fabric border node in a Cisco SD-Access environment?
A. To collect traffic flow information toward external networks
B. To connect the Cisco SD-Access fabric to another fabric or external Layer 3 networks
C. To attach and register clients to the fabric
D. To handle an ordered list of IP addresses and locations for endpoints in the fabric
345、Which AP mode allows an engineer to scan configured channels for rogue access
points?
A. sniffer
B. monitor
C. bridge
D. local
346、
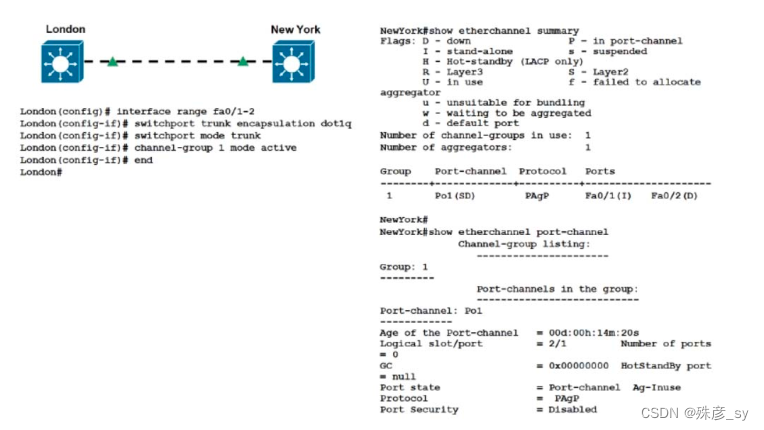
Refer to the exhibit. Communication between London and New York is down. Which
command set must be applied to the New York switch to resolve this issue?
A. NewYork(config)# no int po1
NewYork(config)# interface range fa-/1-2
NewYork(config-if)# channel-group 1 mode negotiate
NewYork(config)-if# end
NewYork#
B. NewYork(config)# no int po1
NewYork(config)# interface range fa-/1-2
NewYork(config-if)# channel-group 1 mode auto
NewYork(config)-if# end
NewYork#
C. NewYork(config)# no int po1
NewYork(config)# interface range fa-/1-2
NewYork(config-if)# channel-group 1 mode on
NewYork(config)-if# end
NewYork#
D. NewYork(config)# no int po1
NewYork(config)# interface range fa-/1-2
NewYork(config-if)# channel-group 1 mode passive
NewYork(config)-if# end
NewYork#
347、
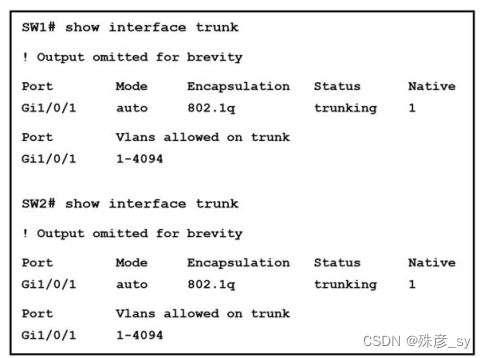
Refer to the exhibit. The trunk between Gig1/0/1 of switch SW2 and Gig1/0/1 of switch
SW1 is not operational.
Which action resolves this issue?
A. Configure both interfaces in dynamic auto DTP mode and ensure that the switches
are in the same VTP domain
B. Configure both interfaces in dynamic desirable DTP mode and ensure that the
switches are in the same VTP domain
C. Configure both interfaces in nonegotiate and ensure that the switches are in the
different VTP domain
D. Configure both interfaces in dynamic auto DTP mode and ensure that the switches
are in the different VTP domain
348、
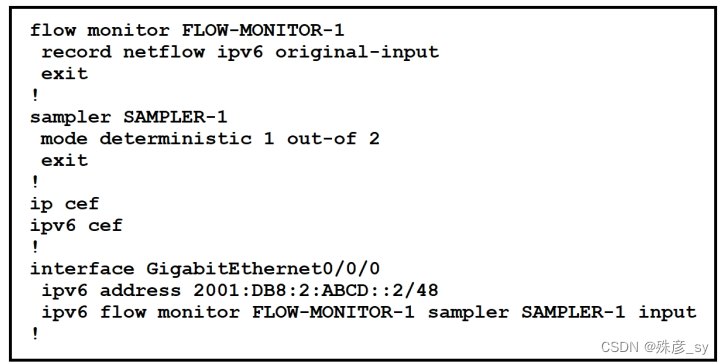
Refer to the exhibit. What is the effect of introducing the sampler feature into the FlexibleNetFlow configuration on the router?
A. NetFlow updates to the collector are sent 50% less frequently
B. Every second IPv4 packet is forward to the collector for inspection
C. CPU and memory utilization are reduced when compared with what is required for full
NetFlow
D. The resolution of sampling data increases, but it requires more performance from the
router
349、Which signal strength and noise values meet the minimum SNR for voice networks?
A. signal strength -69 dBm, noise 94 dBm
B. signal strength -67 dBm, noise 91 dBm
C. signal strength -68 dBm, noise 89 dBm
D. signal strength -66 dBm, noise 90 dBm
350、
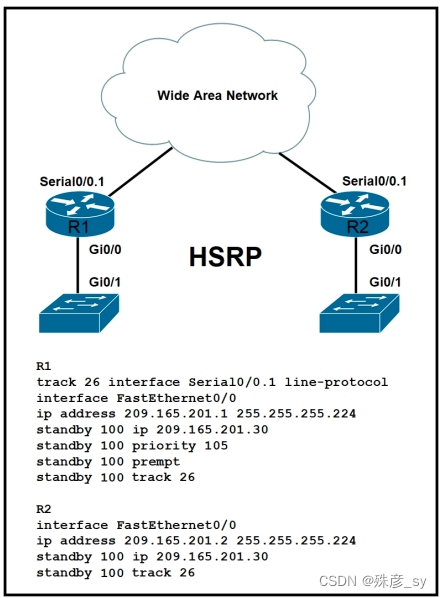
Refer to the exhibit. Which command must be added to enable R2 to take over as master
when Serial Interface 0/0.1 is down on R1?
A. R1# no standy 100 track 26
B. R2# no standy 100 track 26
C. R2# standy 100 preempt
D. R2# standy 100 priority 100