事不一而理有定在,犹百川万折,必归于海。
——《容斋随笔》
1.查壳
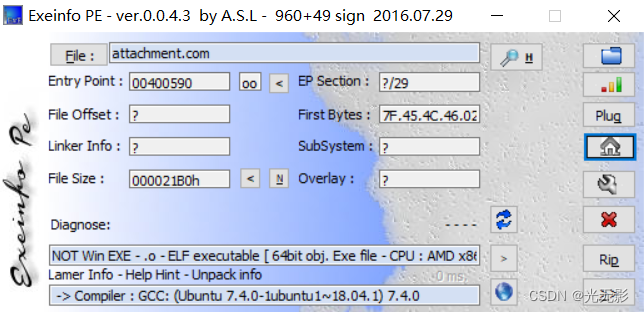
是一个64位像是ELF的文件
无壳子
2.拖入64位IDA
IDA分析失败
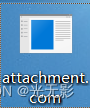
是一个.com文件
COM格式文件是一种简单的可执行文件。在迪吉多公司于20世纪70年代推出的操作系统中,.COM被用做包含操作系统支持命令的文本文件的拓展名(类似于Windows系统的.cmd文件)。随着引进CP/M的引进(微型计算机的操作系统),COM扩展相的文件改变为的可执行文件。该格式后来被结转到MS-DOS。虽然MS-DOS中已有更常见的.exe文件格式的,紧凑的COM文件仍然保持活力,并在MS-DOS频繁使用。
我们直接把文件后缀名改为elf

拖入64位IDA分析成功

反编译主函数
int __cdecl main(int argc, const char **argv, const char **envp)
{
signal(14, sig);
alarm(1u);
delay(6000000LL);
can_continue = 1337;
return 0;
}跟进这几个函数都没有发现什么,观察一下函数列表
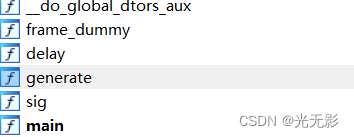
跟进generate函数,发现比较可疑
unsigned __int64 generate()
{
char s[131]; // [rsp+0h] [rbp-B0h] BYREF
char v2[14]; // [rsp+83h] [rbp-2Dh] BYREF
char v3[31]; // [rsp+91h] [rbp-1Fh] BYREF
*(_QWORD *)&v3[23] = __readfsqword(0x28u);
if ( can_continue == 1337 )
{
s[64] = 35;
s[65] = 60;
s[66] = 73;
s[67] = 100;
s[68] = 85;
s[69] = 46;
s[70] = 119;
s[71] = 32;
s[72] = 45;
s[73] = 115;
s[74] = 63;
s[75] = 125;
s[76] = 44;
s[77] = 56;
s[78] = 108;
s[79] = 83;
s[80] = 84;
s[81] = 42;
s[82] = 90;
s[83] = 106;
s[84] = 87;
s[85] = 58;
s[86] = 102;
s[87] = 94;
s[88] = 77;
s[89] = 54;
s[90] = 101;
s[91] = 110;
s[92] = 112;
s[93] = 104;
s[94] = 99;
s[95] = 47;
s[96] = 79;
s[97] = 118;
s[98] = 37;
s[99] = 75;
s[100] = 11;
s[101] = 52;
s[102] = 76;
s[103] = 82;
s[104] = 103;
s[105] = 96;
s[106] = 95;
s[107] = 69;
s[108] = 123;
s[109] = 114;
s[110] = 59;
s[111] = 126;
s[112] = 74;
s[113] = 10;
s[114] = 107;
s[115] = 113;
s[116] = 67;
s[117] = 36;
s[118] = 92;
s[119] = 40;
s[120] = 34;
s[121] = 64;
s[122] = 50;
s[123] = 68;
s[124] = 98;
s[125] = 80;
s[126] = 13;
s[127] = 38;
s[128] = 49;
s[129] = 55;
s[130] = 12;
qmemcpy(v2, "]y>=xaVYA[BF3", 13);
v2[13] = (unsigned __int8)&unk_400BB4;
strcpy(v3, "!tQHu0Xi5|\t9N+zmG)o");
strcpy(s, "watevr{3ncrytion_is_overrated_youtube.com/watch?v=OPf0YbXqDm0}");
puts(s);
}
return __readfsqword(0x28u) ^ *(_QWORD *)&v3[23];
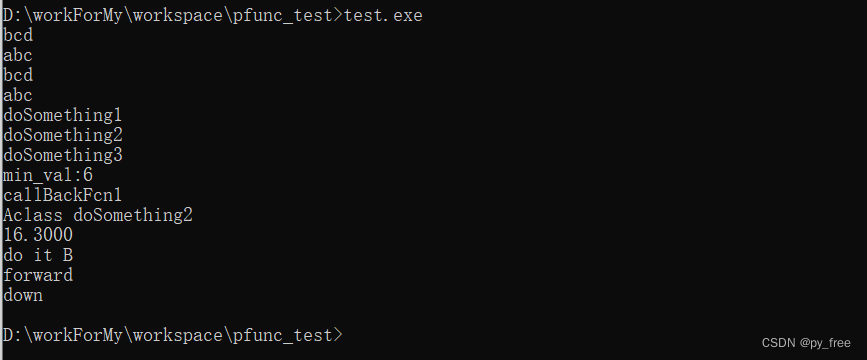
}发现一个疑似flag的字符串watevr{3ncrytion_is_overrated_youtube.com/watch?v=OPf0YbXqDm0}
提交验证,发现就是flag
flag{3ncrytion_is_overrated_youtube.com/watch?v=OPf0YbXqDm0}

![[标准库]STM32F103R8T6 高级定时器--PWM输出和带死区互补PWM输出](https://img-blog.csdnimg.cn/940aefb964ff4c7996064705d63c471a.png)