概述
为了提高系统运维和故障排查的效率, 日志系统采用 ELK(Elasticsearch、Logstash、Kibana)技术栈,通过 FileBeats 作为日志收集器,将来自不同节点的日志数据汇总并存储在 Elasticsearch 中,最终通过 Kibana 进行可视化展示和分析。
系统配置包括 FileBeats 的收集规则、Logstash 的处理管道和 Elasticsearch 的索引设置。部署过程采用 Kubernetes 的 Helm Chart 实现,简化了安装和管理。
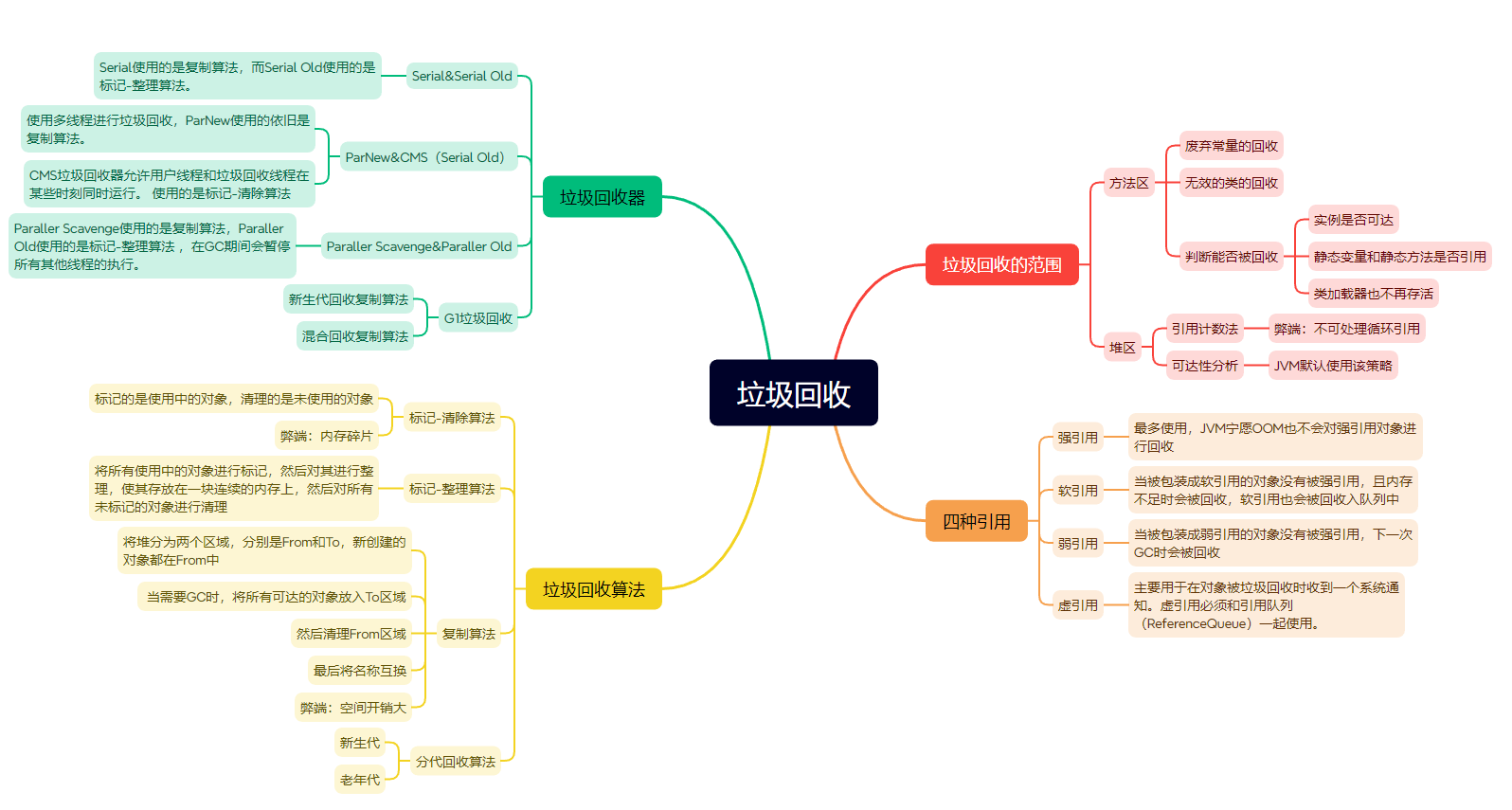
架构
FileBeats + Kafka + ELK
⚡️: 在不影响旧有日志系统运行的前提下,我们在现有的 ELK+Kafka 架构基础上,新增了 Filebeat 作为日志收集器,用于采集 Kubernetes 日志。

日志采集器Logstash其功能虽然强大,但是它依赖java、在数据量大的时候,Logstash进程会消耗过多的系统资源,这将严重影响业务系统的性能,而filebeat就是一个完美的替代者,它基于Go语言没有任何依赖,配置文件简单,格式明了,同时filebeat比logstash更加轻量级,所以占用系统资源极少,非常适合安装在生产机器上。这就是推荐使用filebeat,也是 ELK Stack 在 Agent 的第一选择。
此架构适合大型集群、海量数据的业务场景,它通过将前端Logstash Agent替换成filebeat,有效降低了收集日志对业务系统资源的消耗。同时,消息队列使用kafka集群架构,有效保障了收集数据的安全性和稳定性,而后端Logstash和Elasticsearch均采用集群模式搭建,从整体上提高了ELK系统的高效性、扩展性和吞吐量。我所在的项目组采用的就是这套架构,由于生产所需的配置较高,且涉及较多持久化操作,采用的都是性能高配的云主机搭建方式而非时下流行的容器搭建
部署
elasticsearch
安装方式:helm
安装版本:8.5.1
⚡️ helm安装8版本elastic默认开启ssl认证,我们这边禁用认证
开始前奏操作,生成secret
# 根据提供的 elastic-certificates.p12 将 pcks12 中的信息分离出来,写入文件
openssl pkcs12 -nodes -passin pass:'' -in elastic-certificates.p12 -out elastic-certificate.pem
添加证书和密码到集群
# 添加证书
kubectl create secret generic elastic-certificates --from-file=elastic-certificates.p12
kubectl create secret generic elastic-certificate-pem --from-file=elastic-certificate.pem
# 设置集群用户名密码,用户名不建议修改
##命令行
kubectl create secret generic elastic-credentials \
--from-literal=username=elastic --from-literal=password=123456
##yaml
apiVersion: v1
data:
password: MTIzNDU2
username: ZWxhc3RpYw==
kind: Secret
metadata:
name: elastic-credentials
namespace: elastic
type: Opaque
🏴 加油特种兵
先添加elasticsearch的helm仓库,并拉取对应版本的Charts并对其解压
[root@ycloud ~]# helm repo add elastic https://helm.elastic.co
"elastic" has been added to your repositories
[root@ycloud ~]# helm pull elastic/elasticsearch --version 8.5.1
[root@ycloud ~]# tar -zxvf elasticsearch-8.5.1.tgz
elasticsearch/Chart.yaml
elasticsearch/values.yaml
......
调整values
replicas: 2
minimumMasterNodes: 1
esMajorVersion: ""
# Allows you to add any config files in /usr/share/elasticsearch/config/
# such as elasticsearch.yml and log4j2.properties
# ==================安全配置========================
protocol: http
###挂在证书,这里用我们上面创建的证书
secretMounts:
- name: elastic-certificates
secretName: elastic-certificates
path: /usr/share/elasticsearch/config/certs
defaultMode: 0755
esConfig:
elasticsearch.yml: |
xpack.security.enabled: true
xpack.security.transport.ssl.enabled: true
xpack.security.transport.ssl.verification_mode: certificate
xpack.security.transport.ssl.keystore.path: /usr/share/elasticsearch/config/certs/elastic-certificates.p12
xpack.security.transport.ssl.truststore.path: /usr/share/elasticsearch/config/certs/elastic-certificates.p12
# key:
# nestedkey: value
# log4j2.properties: |
# key = value
## 关闭ssl认证
createCert: false
esJavaOpts: "-Xmx1g -Xms1g"
###指定elastic用户密码
extraEnvs:
- name: ELASTIC_USERNAME
valueFrom:
secretKeyRef:
name: elastic-credentials ###用我们创建的secret
key: username
- name: ELASTIC_PASSWORD
valueFrom:
secretKeyRef:
name: elastic-credentials ###用我们创建的secret
key: password
###true开启持久化
persistence:
enabled: true
kibana
安装方式:helm
安装版本:8.5.1
⚡️: 默认使用身份验证和TLS部署Kibana 8.5.1连接到Elasticsearch
🐤:重置kibana_system账户密码
[root@ycloud hub]# kubectl exec -it elasticsearch-master-0 -- bin/elasticsearch-reset-password -u kibana_system
Defaulted container "elasticsearch" out of: elasticsearch, configure-sysctl (init)
This tool will reset the password of the [kibana_system] user to an autogenerated value.
The password will be printed in the console.
Please confirm that you would like to continue [y/N]y
Password for the [kibana_system] user successfully reset.
New value: nVUE*km=842x7duqB4TR
🐤:更新 elastic-credentials文件
# [root@ycloud hub]# echo nVUE*km=842x7duqB4TR|base64
blZVRSprbT04NDJ4N2R1cUI0VFIK
apiVersion: v1
data:
kibana_password: blZVRSprbT04NDJ4N2R1cUI0VFIK
kibana_username: a2liYW5hX3N5c3RlbQ==
password: MTIzNDU2
username: ZWxhc3RpYw==
kind: Secret
metadata:
name: elastic-credentials
namespace: elastic
type: Opaque
🏴 加油特种兵
先添加kibana的helm仓库,并拉取对应版本的Charts并对其解压
[root@ycloud ~]# helm repo add elastic https://helm.elastic.co
"elastic" has been added to your repositories
[root@ycloud ~]# helm pull elastic/kibana --version 8.5.1
[root@ycloud ~]# tar -zxvf kibana-8.5.1.tgz
kibana/Chart.yaml
kibana/values.yaml
......
调整template
# cd kibana/templates/ ; rm -rf post-delete-* pre-install-*
##删除deployment.yaml部分内容
---
- name: ELASTICSEARCH_SSL_CERTIFICATEAUTHORITIES
value: "{{ template "kibana.home_dir" . }}/config/certs/{{ .Values.elasticsearchCertificateAuthoritiesFile }}"
- name: ELASTICSEARCH_SERVICEACCOUNTTOKEN
valueFrom:
secretKeyRef:
name: {{ template "kibana.fullname" . }}-es-token
key: token
optional: false
---
readinessProbe:
{{ toYaml .Values.readinessProbe | indent 10 }}
exec:
command:
- bash
- -c
- |
#!/usr/bin/env bash -e
# Disable nss cache to avoid filling dentry cache when calling curl
# This is required with Kibana Docker using nss < 3.52
export NSS_SDB_USE_CACHE=no
http () {
local path="${1}"
set -- -XGET -s --fail -L
if [ -n "${ELASTICSEARCH_USERNAME}" ] && [ -n "${ELASTICSEARCH_PASSWORD}" ]; then
set -- "$@" -u "${ELASTICSEARCH_USERNAME}:${ELASTICSEARCH_PASSWORD}"
fi
STATUS=$(curl --output /dev/null --write-out "%{http_code}" -k "$@" "{{ .Values.protocol }}://localhost:{{ .Values.httpPort }}${path}")
if [[ "${STATUS}" -eq 200 ]]; then
exit 0
fi
echo "Error: Got HTTP code ${STATUS} but expected a 200"
exit 1
}
http "{{ .Values.healthCheckPath }}"
---
- name: elasticsearch-certs
secret:
secretName: {{ .Values.elasticsearchCertificateSecret }}
---
- name: elasticsearch-certs
mountPath: {{ template "kibana.home_dir" . }}/config/certs
readOnly: true
---
调整values
# cd kibana/templates/
# rm -rf post-delete-* pre-install-*
---
elasticsearchHosts: "http://elasticsearch-master:9200"
#elasticsearchCertificateSecret: elasticsearch-master-certs
#elasticsearchCertificateAuthoritiesFile: ca.crt
elasticsearchCredentialSecret: elastic-credentials
replicas: 1
extraEnvs:
- name: "NODE_OPTIONS"
value: "--max-old-space-size=1800"
- name: 'ELASTICSEARCH_USERNAME'
valueFrom:
secretKeyRef:
name: elastic-credentials
key: kibana_username
- name: 'ELASTICSEARCH_PASSWORD'
valueFrom:
secretKeyRef:
name: elastic-credentials
key: kibana_password
resources:
requests:
cpu: "1000m"
memory: "2Gi"
limits:
cpu: "1000m"
memory: "2Gi"
protocol: http
serverHost: "0.0.0.0"
healthCheckPath: "/app/kibana"
filebeat
⚡️: 详情见 Here
总结
日志系统已成功应用于多种业务场景。为了进一步提高系统的稳定性,后面我们在新的部署中采用 ClickHouse 作为日志存储解决方案。