一:系统版本
二:部署环境
节点名称
IP
部署组件及版本
配置文件路径
机器CPU
机器内存
机器存储
Ldap
10.10.10.111
self-service-password:latest
phpldapadmin:latest
openldap:latest
openldap:/data/openldap/config
phpldapadmin(只是web管理界面,数据依托openldap)
self-service-password:/data/self-service-password/data
2*16cores
64g
50g 系统
800g 数据盘
三:部署流程
(1)安装docker和docker-compose
apt-get install -y docker wget https://github.com/docker/compose/releases/download/1.29.2/docker-compose-Linux-x86_64 mv docker-compose-Linux-x86_64 /usr/bin/docker-compose(2)提前拉取需要用到的镜像
docker pull osixia/openldap:latest docker pull osixia/phpldapadmin:latest docker pull tiredofit/self-service-password:latest(3)准备应用要挂载的配置文件目录
mkdir -p /data/openldap/data mkdir -p /data/openldap/config mkdir -p /data/self-service-password/data mkdir -p /data/self-service-password/logs 备注:如遇到读取文件权限问题请使用 chmod 755 -R /data/self-service-password/data(4)所有组件的部署方式全部为docker-compose形式编排部署,docker-compose.yml文件所在路径/app/ldap_docker_compose/,编排内容:
~]# mkdir -p /app/ldap_docker_compose/ ~]# cat /app/ldap_docker_compose/docker-compose.yml version: '3' services: ## 安装openldap openldap: container_name: openldap image: osixia/openldap:latest restart: always environment: TZ: Asia/Shanghai LDAP_ORGANISATION: "Manager" LDAP_DOMAIN: "westhab.com" LDAP_ADMIN_PASSWORD: "admin123456" LDAP_CONFIG_PASSWORD: "admin123456" volumes: - /data/openldap/data:/var/lib/ldap - /data/openldap/config:/etc/ldap/slapd.d ports: - '389:389' ## 安装phpldapadmin phpldapadmin: container_name: phpldapadmin image: osixia/phpldapadmin:latest environment: PHPLDAPADMIN_LDAP_HOSTS: openldap PHPLDAPADMIN_HTTPS: "false" ports: - "30004:80" depends_on: - openldap ## 安装自助修改密码插件self-service-password change-ldap-password: container_name: self-service-password image: tiredofit/self-service-password:latest restart: always ports: - "8080:80" environment: - LDAP_SERVER=ldap://10.10.10.111:389 - LDAP_STARTTLS=false - LDAP_BINDDN=cn=admin,dc=westhab,dc=com - LDAP_BINDPASS=admin123456 - LDAP_BASE_SEARCH=dc=westhab,dc=com - LDAP_LOGIN_ATTRIBUTE=uid - LDAP_FULLNAME_ATTRIBUTE=cn # 邮箱配置模块 - MAIL_FROM=emis@skycloudsys.com - MAIL_FROM_NAME=账号自助服务平台 - SMTP_DEBUG=0 - SMTP_HOST=smtp.qiye.aliyun.com - SMTP_USER=emis@skycloudsys.com - SMTP_PASS=QUN3ZSQmNzQ1QkJjaQ== - SMTP_SECURE_TYPE=tls - SMTP_AUTOTLS=false - SMTP_AUTH_ON=true - NOTIFY_ON_CHANGE=true volumes: - /etc/localtime:/etc/localtime - /data/self-service-password/data:/www/ssp - /data/self-service-password/logs:/www/logs(5)启动服务
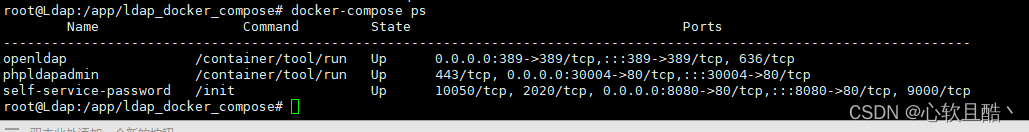
#开始部署 ~]# docker-compose up -d #停止运行的容器实例 ~]# docker-compose stop #单独启动容器 ~]# docker-compose up -d phpldapadmin #重启所有容器 ~]# docker-compose restart #查看服务状态 ~]# docker-compose ps(6)查看服务状态
(7) 功能测试
1、ldapadmin服务访问测试:(正常)
2、ldapadmin增删改查功能测试:(正常)
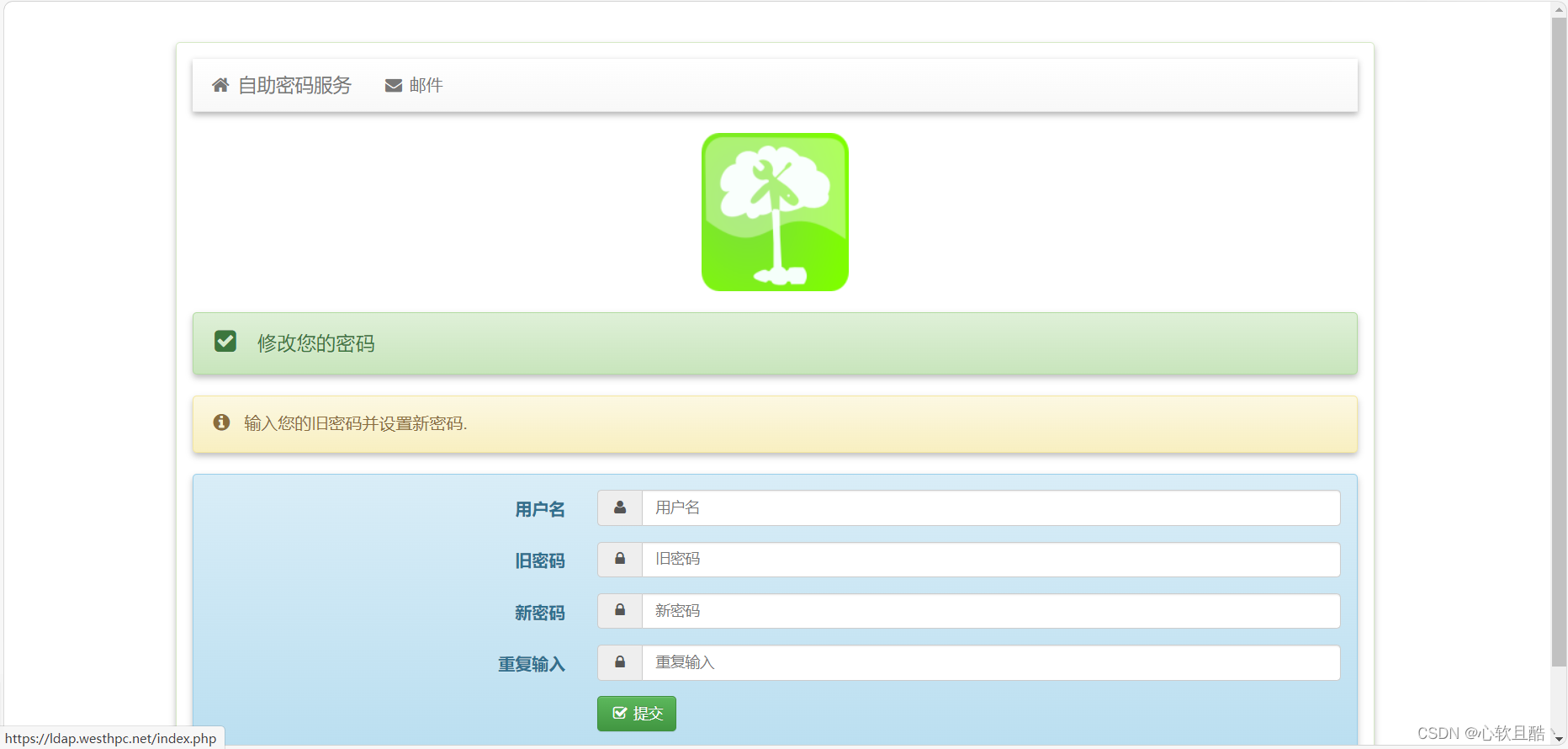
3、selfpasswd(自助密码修改服务)访问测试:(正常)
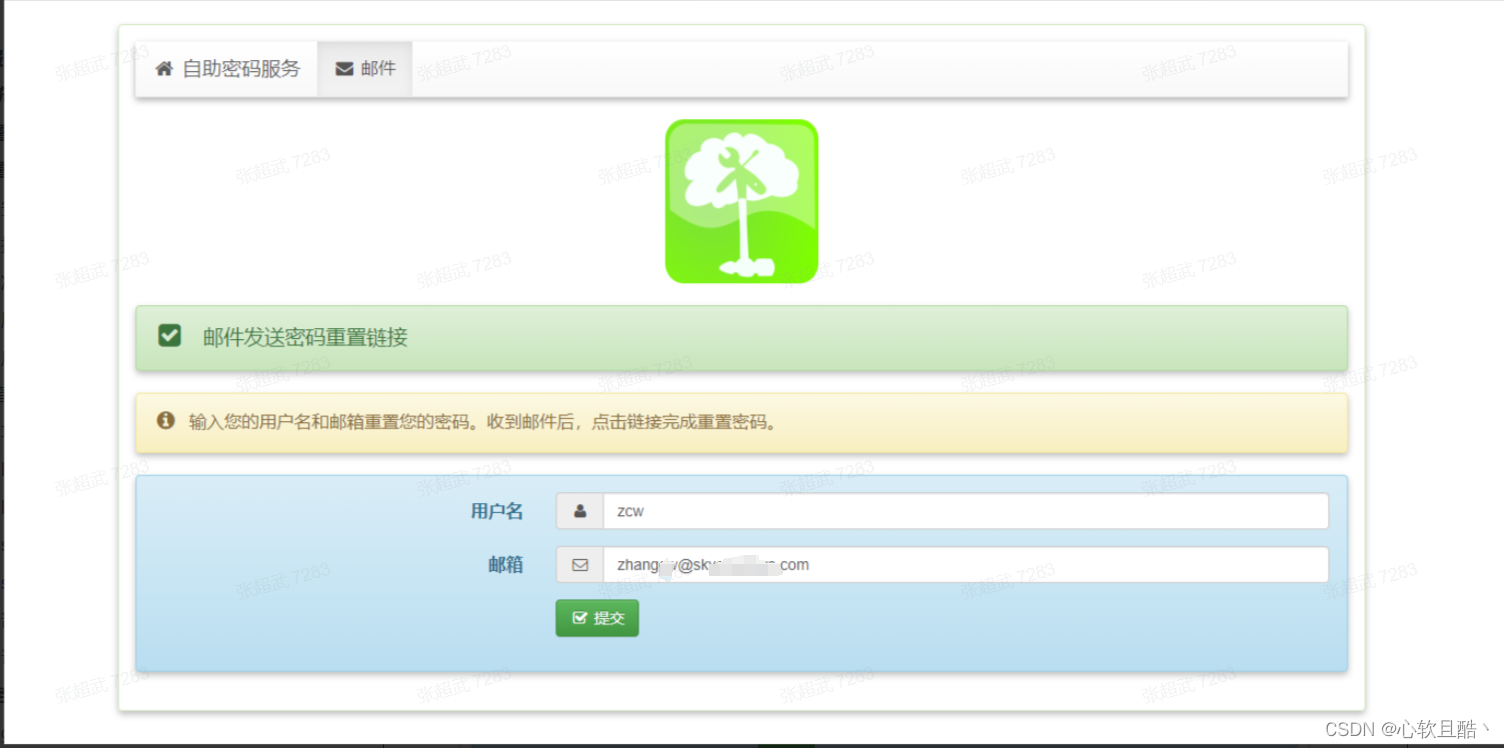
4、selfpasswd功能测试(原密码修改密码,忘记密码邮箱重置密码):(正常)
(8)部署过程遇到的问题总结:
问题1:由于使用的阿里云smtp服务密码"ACwe$&745BBci"存在连续特殊字符"$&",而docker-compose的yaml文件无法对连续的特殊字符做转义,尝试使用把密码以挂载env_file形式去传递到docker内部,但是测试此种方案发现没有生效。
解决办法:尝试对原密码进行base64位加密,然后去修改docker volume的服务器上的本地配置文件做base64的解码,以这种方式去规避连续特殊字符。(修改完之后需要重启docker服务生效 docker-compose restart)
在index.php中的email password 修改原配置为base64_decode($mail_smtp_pass);
在/data/self-service-password/data/conf/config.inc.php中的email password 修改原配置为 $mail_smtp_pass = base64_decode($mail_smtp_pass);
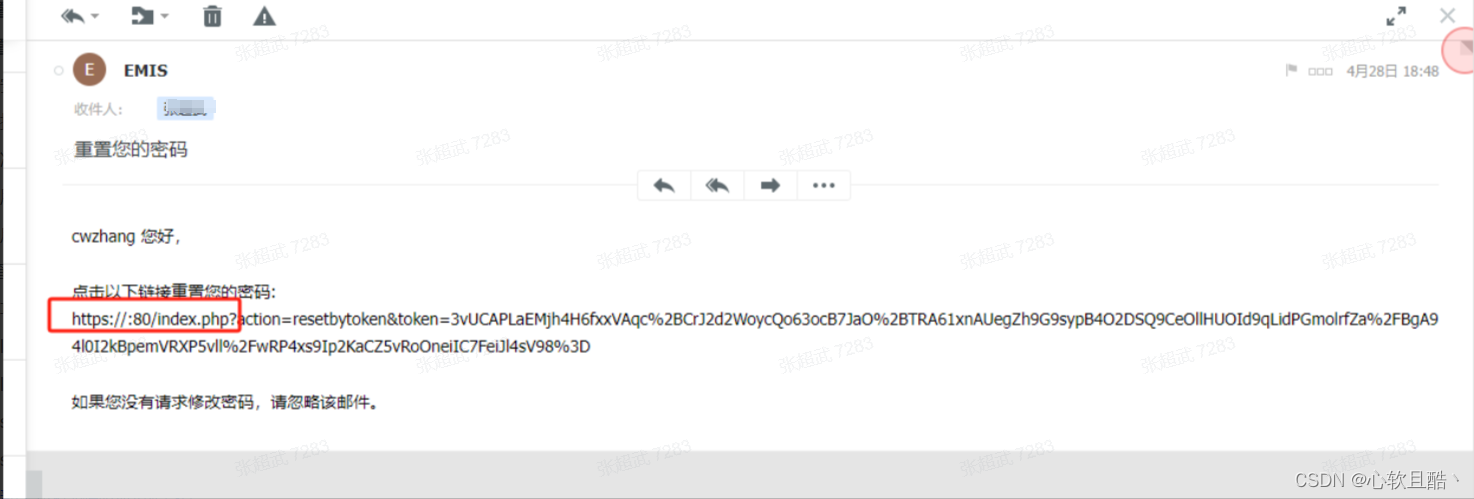
问题2:发现邮件重置密码时,重置链接不完整,缺少实际的ip或域名信息。
解决办法:在修改docker volume的服务器上的本地配置/data/self-service-password/data/conf/config.inc.php文件补全重置邮件链接的前缀换成域名信息。(修改完之后需要重启docker服务生效 docker-compose restart)
三:服务接入
关于要用到的ldap目录树的解释:
1. 基础 DN(Base DN): 作用: 基础 DN 是 LDAP 搜索操作的起始点,指定了搜索的根节点。 用途: 当执行 LDAP 搜索操作时,基础 DN 指定了搜索的起始位置,搜索将从该位置开始递归地向下搜索整个 LDAP 目录树。 示例: 基础 DN 可以是整个 LDAP 目录树的根节点,如 dc=example,dc=com,或者是特定组织单位(OU)的 DN。 2. 搜索 DN(Search DN): 作用: 搜索 DN 是用于执行 LDAP 搜索操作时的身份验证信息,用于访问 LDAP 目录中的数据。 用途: 在执行 LDAP 搜索操作时,需要提供搜索 DN 和相应的密码以进行身份验证,以便访问 LDAP 数据。 示例: 搜索 DN 可以是具有适当权限的用户或服务账户的 DN,用于执行 LDAP 搜索操作。(1)grafana对接ldap
1.在grafana.ini中启用ldap服务开关
enabled = true config_file = /etc/grafana/ldap.toml allow_sign_up = true # prevent synchronizing ldap users organization roles skip_org_role_sync = true
2.ldap.toml配置
# To troubleshoot and get more log info enable ldap debug logging in grafana.ini # [log] # filters = ldap:debug [[servers]] # Ldap server host (specify multiple hosts space separated) host = "10.10.100.111" # Default port is 389 or 636 if use_ssl = true port = 389 # Set to true if LDAP server should use an encrypted TLS connection (either with STARTTLS or LDAPS) use_ssl = false # If set to true, use LDAP with STARTTLS instead of LDAPS start_tls = false # The value of an accepted TLS cipher. By default, this value is empty. Example value: ["TLS_AES_256_GCM_SHA384"]) # For a complete list of supported ciphers and TLS versions, refer to: https://go.dev/src/crypto/tls/cipher_suites.go tls_ciphers = [] # This is the minimum TLS version allowed. By default, this value is empty. Accepted values are: TLS1.1, TLS1.2, TLS1.3. min_tls_version = "" # set to true if you want to skip ssl cert validation ssl_skip_verify = false # set to the path to your root CA certificate or leave unset to use system defaults # root_ca_cert = "/path/to/certificate.crt" # Authentication against LDAP servers requiring client certificates # client_cert = "/path/to/client.crt" # client_key = "/path/to/client.key" # Search user bind dn bind_dn = "cn=admin,dc=westhpc,dc=com" # Search user bind password # If the password contains # or ; you have to wrap it with triple quotes. Ex """#password;""" bind_password = 'admin123456' # We recommend using variable expansion for the bind_password, for more info https://grafana.com/docs/grafana/latest/setup-grafana/configure-grafana/#variable-expansion # bind_password = '$__env{LDAP_BIND_PASSWORD}' # Timeout in seconds (applies to each host specified in the 'host' entry (space separated)) timeout = 10 # User search filter, for example "(cn=%s)" or "(sAMAccountName=%s)" or "(uid=%s)" search_filter = "(uid=%s)" # An array of base dns to search through search_base_dns = ["dc=westhap,dc=com"] ## For Posix or LDAP setups that does not support member_of attribute you can define the below settings ## Please check grafana LDAP docs for examples group_search_filter = "(&(objectClass=posixGroup)(memberUid=%s))" group_search_base_dns = ["dc=westhab,dc=com"] # group_search_filter_user_attribute = "uid" # Specify names of the ldap attributes your ldap uses [servers.attributes] name = "givenName" surname = "sn" username = "uid" member_of = "cn" email = "email" # Map ldap groups to grafana org roles [[servers.group_mappings]] group_dn = "cn=admins,ou=groups,dc=grafana,dc=org" org_role = "Admin" # To make user an instance admin (Grafana Admin) uncomment line below # grafana_admin = true # The Grafana organization database id, optional, if left out the default org (id 1) will be used # org_id = 1 [[servers.group_mappings]] group_dn = "cn=editors,ou=groups,dc=grafana,dc=org" org_role = "Editor" [[servers.group_mappings]] # If you want to match all (or no ldap groups) then you can use wildcard group_dn = "*" org_role = "Viewer"
3.重启服务生效
4.验证grafana和ldap是否对接成功docker-compose restart