#!/bin/bash
# Define output file
current_date=$(date "+%Y%m%d") # Gets the current date in YYYYMMDD format
output_file="server_security_inspection_report_${current_date}.txt"
# Empty the file initially
echo '' > $output_file
# 获取巡检时间 (Get the inspection time)
inspection_time=$(date "+%Y-%m-%d %H:%M:%S")
# 获取主机IP地址 (Get the host IP address)
host_ip=$(hostname -I | awk '{print $1}')
# 获取最后六次Session记录 (Get the last six session records)
last_logins=$(last -n 6 -w)
echo "===============================================" > $output_file
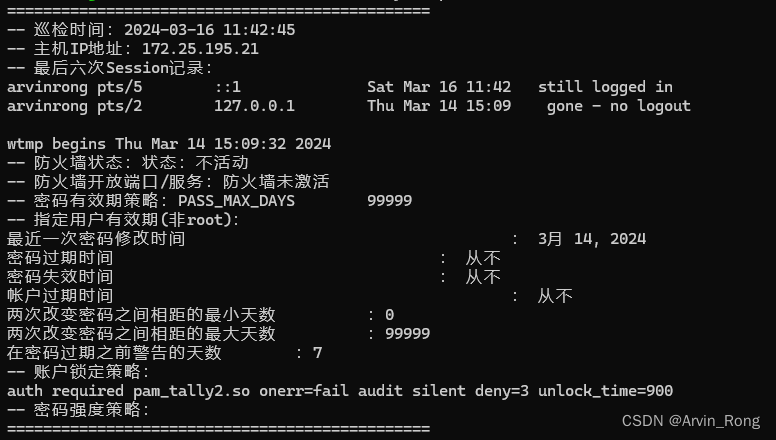
echo "-- 巡检时间:$inspection_time" >> $output_file
echo "-- 主机IP地址:$host_ip" >> $output_file
echo "-- 最后六次Session记录:" >> $output_file
echo "$last_logins" >> $output_file
# 获取防火墙状态 (Get the firewall status)
# UOS (Debian/Ubuntu-based) 通常使用 UFW,如果使用其他方式需要调整此部分脚本
firewall_status=$(ufw status | head -n 1)
echo "-- 防火墙状态:$firewall_status" >> $output_file
ufw_status=$(ufw status | grep Status | awk '{print $2}')
if [ "$ufw_status" != "active" ]; then
firewall_open_ports_and_service="防火墙未激活"
else
# 获取开放端口或服务, 逗号分隔
firewall_open_ports_and_service=$(ufw status | grep ALLOW | awk '{print $1}' | sort | uniq | paste -sd, - )
fi
echo "-- 防火墙开放端口/服务:$firewall_open_ports_and_service" >> $output_file
# 密码有效期策略,脚本中username即用户名需要根据实际使用进行修改
password_policy=$(chage -l username 2>/dev/null || echo "chage 命令执行失败,请检查是否修改脚本中指定用户名(默认username需要改为实际使用用户名)")
password_max_days=$(grep -w "PASS_MAX_DAYS" /etc/login.defs | grep -v ^#)
echo "-- 密码有效期策略:$password_max_days" >> $output_file
echo "-- 指定用户有效期(非root):" >> $output_file
echo "$password_policy" >> $output_file
# 账户锁定策略 (Account lockout policy)
echo "-- 账户锁定策略:" >> $output_file
grep "pam_tally2\|pam_faillock" /etc/pam.d/common-auth >> $output_file
# 密码强度策略 (Password strength policy)
echo "-- 密码强度策略:" >> "$output_file"
grep "pam_cracklib.so\|pam_pwquality.so" /etc/pam.d/common-password >> "$output_file"
echo "===============================================" >> $output_file
# 显示报告 (Display the report)
cat $output_file
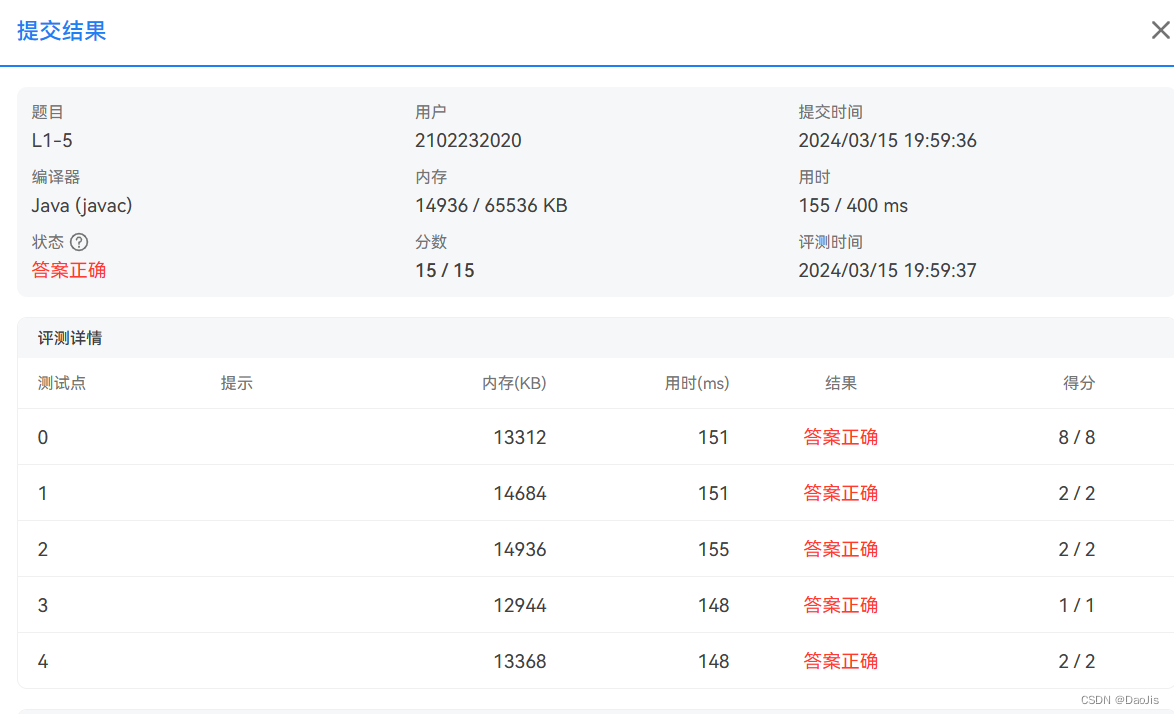
巡检结果输出样例: