AndroGenshin:
rc4加密表,base64换表:

脚本梭就行
python
username = b"genshinimpact" base64_table = [125, 239, 101, 151, 77, 163, 163, 110, 58, 230, 186, 206, 84, 84, 189, 193, 30, 63, 104, 178, 130, 211, 164, 94, 75, 16, 32, 33, 193, 160, 120, 47, 30, 127, 157, 66, 163, 181, 177, 47, 0, 236, 106, 107, 144, 231, 250, 16, 36, 34, 91, 9, 188, 81, 5, 241, 235, 3, 54, 150, 40, 119, 202, 150] def rc4(key, data): S = list(range(256)) j = 0 out = [] for i in range(256): j = (j + S[i] + key[i % len(key)]) % 256 S[i], S[j] = S[j], S[i] i = j = 0 for t in data: i = (i + 1) % 256 j = (j + S[i]) % 256 S[i], S[j] = S[j], S[i] out.append(t^ S[(S[i] + S[j]) % 256]) return out import base64 def base64_custom_decode(data, custom_table): original_table = "ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789+/" decode_table = str.maketrans(custom_table, original_table) decoded_data = base64.b64decode(data.translate(decode_table)) return decoded_data retval = rc4(username, base64_table) new_table = "".join([chr(t) for t in retval]) enc_data = "YnwgY2txbE8TRyQecyE1bE8DZWMkMiRgJW1=" print(base64_custom_decode(enc_data, new_table))
SMC:
先来看主函数部分:
c
int __cdecl main(int argc, const char **argv, const char **envp)
{
DWORD *v3; // eax
v3 = (DWORD *)malloc(0x26u);
VirtualProtect(&sub_403040, 0x26u, 0x40u, v3);
puts("Please enter your flag:");
sub_401025("%s", data);
if ( NtCurrentPeb()->BeingDebugged )
{
MessageBoxA(0, "Debug Detected!", "Warning!", 0);
Sleep(0x1388u);
exit(0);
}
sub_401042();
if ( ((int (__cdecl *)(char *, void *))sub_403040)(data, &byte_403020) )
puts("Win!");
else
puts("Lose!");
return system("pause");
}
主函数比较简洁明了,就是sub_403040这个函数不知道,是由sub_401042这个函数解密而成的,看一下加密函数
c
char sub_401042()
{
int i; // ecx
char result; // al
for ( i = 0; i < 38; ++i )
{
result = byte_403068[i & 3];
sub_403040[i] ^= result;
}
return result;
}
接着动调把解密后的函数搞出来就行

可以直接set ip直接跳到目标函数处,patch掉反调试代码
解密函数如下:

就是异或再加5,直接梭脚本就行
python
data=[0x7C, 0x82, 0x75, 0x7B, 0x6F, 0x47, 0x61, 0x57, 0x53, 0x25,
0x47, 0x53, 0x25, 0x84, 0x6A, 0x27, 0x68, 0x27, 0x67, 0x6A,
0x7D, 0x84, 0x7B, 0x35, 0x35, 0x48, 0x25, 0x7B, 0x7E, 0x6A,
0x33, 0x71]
for i in data:
char=(i-5)^0x11
print(chr(char),end="")
Petals:
看主函数:
c
__int64 __fastcall main(int a1, char **a2, char **a3)
{
unsigned int v4; // [rsp+Ch] [rbp-4h]
puts("Here is a pack of flowers, to my best love --- you.");
puts("But I must check your identity, please input the right passwd");
__isoc99_scanf("%s", byte_4080);
v4 = strlen(byte_4080);
if ( strlen(byte_4080) != 25 )
{
puts("Please check your input's format!");
exit(-1);
}
((void (__fastcall *)(char *, _QWORD))loc_1209)(byte_4080, v4);
sub_160C(byte_4080, &unk_4020, v4);
printf("If you are succeed, the flag is flag{md5(your input)}");
return 0LL;
}
逻辑依旧比较清晰,看一下sub_160C函数
c
int __fastcall sub_160C(const void *a1, const void *a2, unsigned int a3)
{
if ( !memcmp(a1, a2, a3) )
return puts("I love you.");
else
return puts("I hate you!");
}
数据的判断语句,要判断的数据是
data=[ 0xD0, 0xD0, 0x85, 0x85, 0x80, 0x80, 0xC5, 0x8A, 0x93, 0x89,
0x92, 0x8F, 0x87, 0x88, 0x9F, 0x8F, 0xC5, 0x84, 0xD6, 0xD1,
0xD2, 0x82, 0xD3, 0xDE, 0x87]
再来看一下上一个函数log_1209:
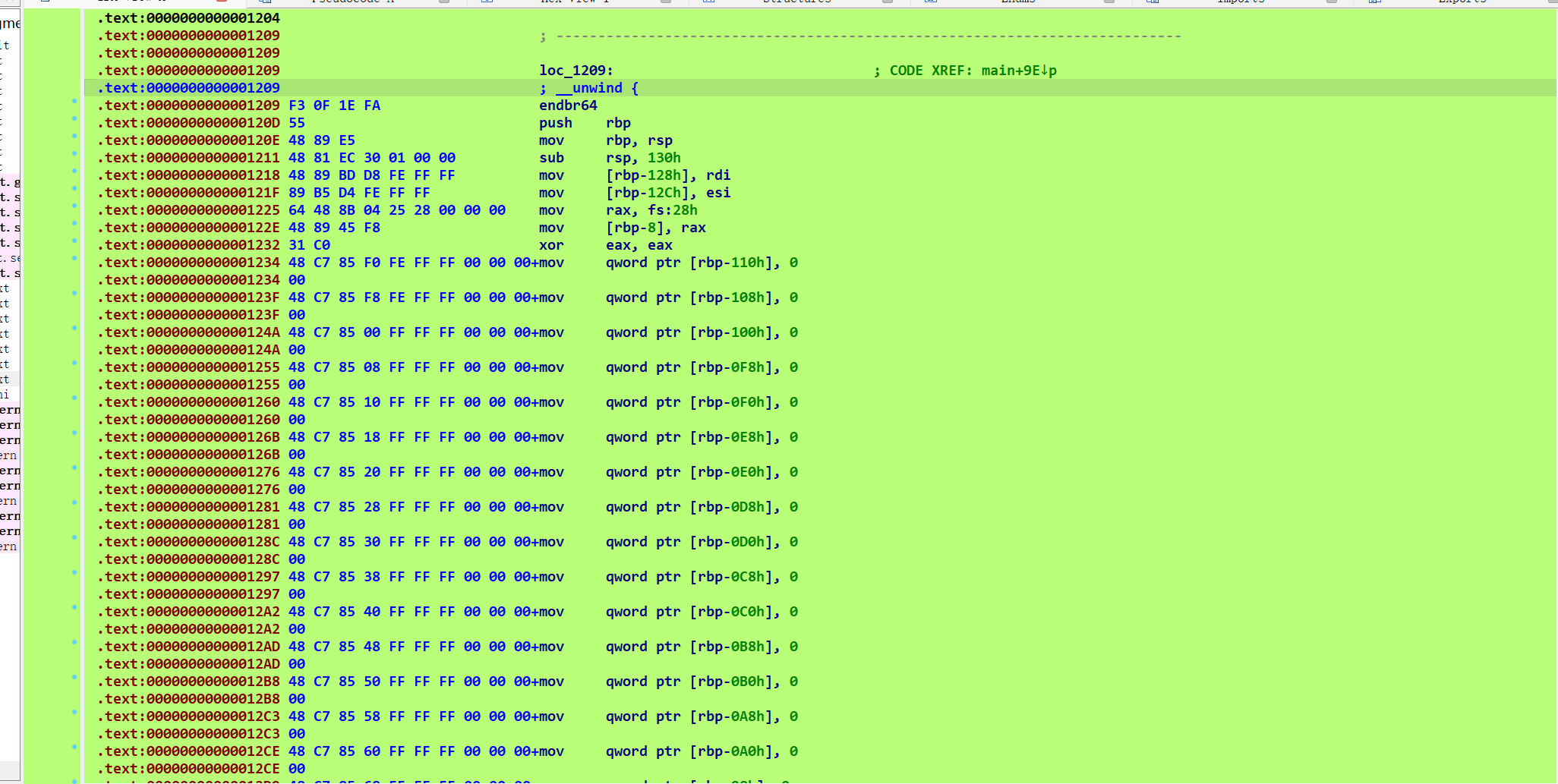
发现爆红。初步判断应该是加了花指令

果然,经典花指令,在call那里按u,然后将剩下的代码按c转化为代码即可
去花函数为
c
unsigned __int64 __fastcall sub_1209(__int64 a1, unsigned int a2)
{
int i; // [rsp+18h] [rbp-118h]
unsigned int j; // [rsp+1Ch] [rbp-114h]
__int64 v5[33]; // [rsp+20h] [rbp-110h] BYREF
unsigned __int64 v6; // [rsp+128h] [rbp-8h]
v6 = __readfsqword(0x28u);
memset(v5, 0, 256);
for ( i = 0; i <= 255; ++i )
*((_BYTE *)v5 + i) = ~(i ^ a2);
for ( j = 0; a2 > j; ++j )
*(_BYTE *)((int)j + a1) = *((_BYTE *)v5 + *(unsigned __int8 *)((int)j + a1));
return v6 - __readfsqword(0x28u);
}
其实加密过程很直接,第一个for循环生成密码表,然后再根据字符作为下标就行加密
就是在密码表中找对应的,然后下标就是加密前的数据。脚本如下:
python
data=[ 0xD0, 0xD0, 0x85, 0x85, 0x80, 0x80, 0xC5, 0x8A, 0x93, 0x89,
0x92, 0x8F, 0x87, 0x88, 0x9F, 0x8F, 0xC5, 0x84, 0xD6, 0xD1,
0xD2, 0x82, 0xD3, 0xDE, 0x87]
v5=[0]*256
for i in range(256):
v5[i]=~(i^25)&0xff
print(v5)
flag=""
for i in range(25):
flag+=v5.index(data[i])
print("\n")
import hashlib
md5=hashlib.md5()
md5.update(flag.encode())
result=md5.hexdigest()
print(result)
C?C++?:
c#编写的程序,dnspy打开即可

找到加密函数部分
c
// ConsoleApp1.Program
// Token: 0x06000001 RID: 1 RVA: 0x00002050 File Offset: 0x00000250
private static void Main(string[] args)
{
int num = 35;
int[] array = new int[]
{
68, 75, 66, 72, 99, 19, 19, 78, 83, 74,
91, 86, 35, 39, 77, 85, 44, 89, 47, 92,
49, 88, 48, 91, 88, 102, 105, 51, 76, 115,
-124, 125, 79, 122, -103
};
char[] array2 = new char[35];
int[] array3 = new int[35];
Console.Write("Input your flag: ");
string text = Console.ReadLine();
for (int i = 0; i < text.Length; i++)
{
array2[i] = text[i];
}
string text2 = "NEWSTAR";
for (int j = 0; j < num; j++)
{
char[] array4 = array2;
int num2 = j;
array4[num2] += (char)j;
char[] array5 = array2;
int num3 = j;
array5[num3] -= ' ';
}
for (int k = 0; k < 7; k++)
{
char[] array6 = array2;
int num4 = k;
array6[num4] += (char)(k ^ (int)(-(int)(text2[k] % '\u0004')));
char[] array7 = array2;
int num5 = k + 7;
array7[num5] += text2[k] % '\u0005';
char[] array8 = array2;
int num6 = k + 14;
array8[num6] += (char)(2 * k);
char[] array9 = array2;
int num7 = k + 21;
array9[num7] += (char)(k ^ 2);
char[] array10 = array2;
int num8 = k + 28;
array10[num8] += text2[k] / '\u0005' + '\n';
}
for (int l = 0; l < num; l++)
{
int num9 = (int)array2[l];
array3[l] = num9;
}
for (int m = 0; m < 35; m++)
{
bool flag = m == 34 && array3[m] == array[m];
if (flag)
{
Console.WriteLine("Right!");
}
bool flag2 = array3[m] == array[m];
if (!flag2)
{
Console.WriteLine("Wrong!");
break;
}
}
}
其实加密过程不复杂,就是加密过程很乱,慢慢分析一下即可
python
v6 = 35
j = 0
v10 = [68,75,66,72,99,19,19,78,83,74,91,86,35,39,77,85,44,89,47,92,49,88,48,91,88,102,105,51,76,115,-124,125,79,122,-103]
a2 = "NEWSTAR"
for j in range(7):
v10[j + 28] -= (ord(a2[j])//5) + 10
v10[j + 21] -= j ^ 2
v10[j + 14] -= 2 * j
v10[j + 7] -= ord(a2[j]) % 5
v10[j] -= j ^ -(ord(a2[j]) % 4)
for i in range(v6):
v10[i] -= i
v10[i] += 32
print(chr(v10[i]%256), end='')
R4ndom:
主函数逻辑:
c
int __cdecl main(int argc, const char **argv, const char **envp)
{
char v3; // bl
int v4; // eax
int i; // [rsp+Ch] [rbp-94h]
__int64 s2[6]; // [rsp+10h] [rbp-90h] BYREF
__int16 v8; // [rsp+40h] [rbp-60h]
char data[8]; // [rsp+50h] [rbp-50h] BYREF
__int64 v10; // [rsp+58h] [rbp-48h]
__int64 v11; // [rsp+60h] [rbp-40h]
__int64 v12; // [rsp+68h] [rbp-38h]
__int64 v13; // [rsp+70h] [rbp-30h]
__int64 v14; // [rsp+78h] [rbp-28h]
__int16 v15; // [rsp+80h] [rbp-20h]
unsigned __int64 v16; // [rsp+88h] [rbp-18h]
v16 = __readfsqword(0x28u);
s2[0] = 0x3513AB8AB2D7E6EELL;
s2[1] = 0x2EEDBA9CB9C97B02LL;
s2[2] = 0x16E4F8C8EEFA4FBDLL;
s2[3] = 0x383014F4983B6382LL;
s2[4] = 0xEA32360C3D843607LL;
s2[5] = 42581LL;
v8 = 0;
puts("Can You Find the Secret?");
puts("Give me your flag");
*(_QWORD *)data = 0LL;
v10 = 0LL;
v11 = 0LL;
v12 = 0LL;
v13 = 0LL;
v14 = 0LL;
v15 = 0;
__isoc99_scanf("%s", data);
if ( strlen(data) != 42 )
exit(0);
for ( i = 0; i < strlen(data); ++i )
{
v3 = data[i];
v4 = rand();
data[i] = Table[(16 * ((unsigned __int8)(v3 + v4 % 255) >> 4) + 15) & (unsigned __int8)(v3 + v4 % 255)];
}
if ( !memcmp(data, s2, 0x2AuLL) )
puts("You get the Right Flag!!");
else
puts("Maybe your flag is Wrong o.O?");
return 0;
}
直接看最关键的代码逻辑
c
for ( i = 0; i < strlen(data); ++i )
{
v3 = data[i];
v4 = rand();
data[i] = Table[(16 * ((unsigned __int8)(v3 + v4 % 255) >> 4) + 15) & (unsigned __int8)(v3 + v4 % 255)];
}
if ( !memcmp(data, s2, 0x2AuLL) )
puts("You get the Right Flag!!");
else
puts("Maybe your flag is Wrong o.O?");
return 0;
}
这里data和s2进行判断,s2的数据上面已经给出了,for循环这里还有一个rand(),我们来看一下函数列表有没有srand函数,发现是有的,我们交叉引用到调用处

发现是这个b函数进行了调用,再来交叉引用一下发现是在init_array处进行调用,也就是在main函数前就已经设置好了随机数种子
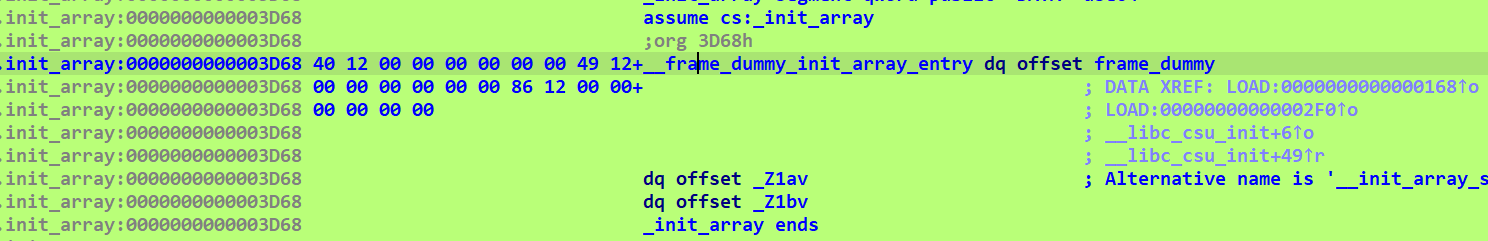
回到主函数这里,可以直接爆破求值就行,注意这是elf文件,需要在linux下编译运行
c
#include <stdio.h>
#include <stdint.h>
#include <stdlib.h>
int main() {
uint64_t s2[6];
s2[0] = 0x3513AB8AB2D7E6EELL;
s2[1] = 0x2EEDBA9CB9C97B02LL;
s2[2] = 0x16E4F8C8EEFA4FBDLL;
s2[3] = 0x383014F4983B6382LL;
s2[4] = 0xEA32360C3D843607LL;
s2[5] = 42581LL;
unsigned char* flag = (unsigned char*)s2;
unsigned char table[] =
{
0x63, 0x7C, 0x77, 0x7B, 0xF2, 0x6B, 0x6F, 0xC5, 0x30, 0x01,
0x67, 0x2B, 0xFE, 0xD7, 0xAB, 0x76, 0xCA, 0x82, 0xC9, 0x7D,
0xFA, 0x59, 0x47, 0xF0, 0xAD, 0xD4, 0xA2, 0xAF, 0x9C, 0xA4,
0x72, 0xC0, 0xB7, 0xFD, 0x93, 0x26, 0x36, 0x3F, 0xF7, 0xCC,
0x34, 0xA5, 0xE5, 0xF1, 0x71, 0xD8, 0x31, 0x15, 0x04, 0xC7,
0x23, 0xC3, 0x18, 0x96, 0x05, 0x9A, 0x07, 0x12, 0x80, 0xE2,
0xEB, 0x27, 0xB2, 0x75, 0x09, 0x83, 0x2C, 0x1A, 0x1B, 0x6E,
0x5A, 0xA0, 0x52, 0x3B, 0xD6, 0xB3, 0x29, 0xE3, 0x2F, 0x84,
0x53, 0xD1, 0x00, 0xED, 0x20, 0xFC, 0xB1, 0x5B, 0x6A, 0xCB,
0xBE, 0x39, 0x4A, 0x4C, 0x58, 0xCF, 0xD0, 0xEF, 0xAA, 0xFB,
0x43, 0x4D, 0x33, 0x85, 0x45, 0xF9, 0x02, 0x7F, 0x50, 0x3C,
0x9F, 0xA8, 0x51, 0xA3, 0x40, 0x8F, 0x92, 0x9D, 0x38, 0xF5,
0xBC, 0xB6, 0xDA, 0x21, 0x10, 0xFF, 0xF3, 0xD2, 0xCD, 0x0C,
0x13, 0xEC, 0x5F, 0x97, 0x44, 0x17, 0xC4, 0xA7, 0x7E, 0x3D,
0x64, 0x5D, 0x19, 0x73, 0x60, 0x81, 0x4F, 0xDC, 0x22, 0x2A,
0x90, 0x88, 0x46, 0xEE, 0xB8, 0x14, 0xDE, 0x5E, 0x0B, 0xDB,
0xE0, 0x32, 0x3A, 0x0A, 0x49, 0x06, 0x24, 0x5C, 0xC2, 0xD3,
0xAC, 0x62, 0x91, 0x95, 0xE4, 0x79, 0xE7, 0xC8, 0x37, 0x6D,
0x8D, 0xD5, 0x4E, 0xA9, 0x6C, 0x56, 0xF4, 0xEA, 0x65, 0x7A,
0xAE, 0x08, 0xBA, 0x78, 0x25, 0x2E, 0x1C, 0xA6, 0xB4, 0xC6,
0xE8, 0xDD, 0x74, 0x1F, 0x4B, 0xBD, 0x8B, 0x8A, 0x70, 0x3E,
0xB5, 0x66, 0x48, 0x03, 0xF6, 0x0E, 0x61, 0x35, 0x57, 0xB9,
0x86, 0xC1, 0x1D, 0x9E, 0xE1, 0xF8, 0x98, 0x11, 0x69, 0xD9,
0x8E, 0x94, 0x9B, 0x1E, 0x87, 0xE9, 0xCE, 0x55, 0x28, 0xDF,
0x8C, 0xA1, 0x89, 0x0D, 0xBF, 0xE6, 0x42, 0x68, 0x41, 0x99,
0x2D, 0x0F, 0xB0, 0x54, 0xBB, 0x16
};
unsigned int flags[42];
srand(1400333646);
for(int i = 0; i < 42; i++) {
int flag_char = flag[i];
int random = rand();
for(int num = 33; num < 127; num++) {
int found = 0;
for(int j = 0; j < 256; j++) {
if (flag_char == table[(16 * ((unsigned char)(num + random % 255) >> 4) + 15) & (unsigned char)(num + random % 255)]) {
flags[i] = num;
found = 1;
break;
}
}
if (found) {
break;
}
}
}
puts("\nDecrypted flag:");
for(int i = 0; i < 42; i++) {
printf("%c", flags[i]);
}
return 0;
}
easy_enc:
看主函数逻辑
c
__int64 sub_140016070()
{
char *v0; // rdi
__int64 i; // rcx
char v3[32]; // [rsp+0h] [rbp-20h] BYREF
char v4; // [rsp+20h] [rbp+0h] BYREF
__int64 v5[9]; // [rsp+28h] [rbp+8h]
char data[132]; // [rsp+70h] [rbp+50h] BYREF
int j; // [rsp+F4h] [rbp+D4h]
char Buf1[5]; // [rsp+120h] [rbp+100h] BYREF
char v9[127]; // [rsp+125h] [rbp+105h] BYREF
int v10; // [rsp+1A4h] [rbp+184h]
v0 = &v4;
for ( i = 106i64; i; --i )
{
*(_DWORD *)v0 = -858993460;
v0 += 4;
}
sub_14001135C(&unk_140021018);
v5[0] = (__int64)sub_1400113C5;
v5[1] = (__int64)sub_1400113CA;
v5[2] = (__int64)sub_1400113F2;
v5[3] = (__int64)sub_1400113ED;
memset(data, 0, 0x64ui64);
sub_14001118B("Input Your flag(format:A-Z a-z): ");
sub_1400113FC((__int64)&unk_140019C18, (__int64)data);
length = j_strlen(data);
for ( j = 0; j < 4; ++j )
((void (__fastcall *)(char *))v5[j])(data);
Buf1[0] = -24;
Buf1[1] = 0x80;
Buf1[2] = -124;
Buf1[3] = 8;
Buf1[4] = 24;
strcpy(v9, "<xh");
v9[4] = 112;
v9[5] = 124;
v9[6] = -108;
v9[7] = -56;
v9[8] = -32;
v9[9] = 16;
v9[10] = -20;
v9[11] = -76;
v9[12] = -84;
v9[13] = 104;
v9[14] = -88;
v9[15] = 12;
v9[16] = 28;
v9[17] = -112;
v9[18] = -52;
v9[19] = 84;
v9[20] = 60;
v9[21] = 20;
v9[22] = -36;
v9[23] = 48;
memset(&v9[24], 0, 0x47ui64);
v10 = 1;
if ( !j_memcmp(Buf1, data, length) )
sub_14001118B("Right!! flag is flag{your input}\n");
else
sub_14001118B("Wrong!!\n");
sub_1400112F3(v3, &unk_14001AA10);
return 0i64;
}
其实这里的加密是比较清晰的,只是数据比较那里那里有点小问题,这里buf1是包括v9的,所以比较的字符串长度为29
接着看一下四个加密函数即可
c
__int64 __fastcall sub_140015B80(__int64 a1)
{
__int64 result; // rax
int i; // [rsp+24h] [rbp+4h]
sub_14001135C(&unk_140021018);
for ( i = 0; ; ++i )
{
result = (unsigned int)length;
if ( i >= length )
break;
if ( *(unsigned __int8 *)(a1 + i) < (unsigned int)'A' || *(unsigned __int8 *)(a1 + i) > (unsigned int)'Z' )
{
if ( *(unsigned __int8 *)(a1 + i) < (unsigned int)'0' || *(unsigned __int8 *)(a1 + i) > (unsigned int)'9' )
{
if ( *(unsigned __int8 *)(a1 + i) >= (unsigned int)'a' && *(unsigned __int8 *)(a1 + i) <= (unsigned int)'z' )
*(_BYTE *)(a1 + i) = (*(unsigned __int8 *)(a1 + i) - 89) % 26 + 97;
}
else
{
*(_BYTE *)(a1 + i) = (*(unsigned __int8 *)(a1 + i) - 45) % 10 + 48;
}
}
else
{
*(_BYTE *)(a1 + i) = (*(unsigned __int8 *)(a1 + i) - 52) % 26 + 65;
}
}
return result;
}
c
__int64 __fastcall sub_140015CE0(__int64 a1)
{
char *v1; // rdi
__int64 i; // rcx
char v4[32]; // [rsp+0h] [rbp-20h] BYREF
char v5; // [rsp+20h] [rbp+0h] BYREF
char Str[44]; // [rsp+28h] [rbp+8h] BYREF
int j; // [rsp+54h] [rbp+34h]
__int64 v8; // [rsp+128h] [rbp+108h]
__int64 v9; // [rsp+130h] [rbp+110h]
size_t v10; // [rsp+138h] [rbp+118h]
v1 = &v5;
for ( i = 28i64; i; --i )
{
*(_DWORD *)v1 = -858993460;
v1 += 4;
}
sub_14001135C(&unk_140021018);
strcpy(Str, "NewStarCTF");
memset(&Str[11], 0, 9ui64);
for ( j = 0; j < length; ++j )
{
v8 = j;
v9 = j;
v10 = j_strlen(Str);
*(_BYTE *)(a1 + j) += Str[j % v10];
}
return sub_1400112F3(v4, &unk_14001A920);
}
c
__int64 __fastcall sub_140012B40(__int64 a1)
{
__int64 result; // rax
int i; // [rsp+24h] [rbp+4h]
sub_14001135C(&unk_140021018);
for ( i = 0; ; ++i )
{
result = (unsigned int)length;
if ( i >= length )
break;
*(_BYTE *)(a1 + i) = ~*(_BYTE *)(a1 + i);
}
return result;
}
c
__int64 __fastcall sub_140011830(__int64 a1)
{
__int64 result; // rax
int i; // [rsp+24h] [rbp+4h]
sub_14001135C(&unk_140021018);
for ( i = 0; ; ++i )
{
result = (unsigned int)length;
if ( i >= length )
break;
*(_BYTE *)(a1 + i) *= 52;
}
return result;
}
逆是不可能逆了,直接爆破
c
#include <stdio.h>
#include <string.h>
// 第一个加密函数
unsigned char encrypt_first(unsigned char data, int i) {
if ( data < (unsigned int)'A' || data > (unsigned int)'Z' )
{
if ( data < (unsigned int)'0' || data > (unsigned int)'9' )
{
if ( data >= (unsigned int)'a' && data <= (unsigned int)'z' )
data = (data - 89) % 26 + 97;
}
else
{
data = (data - 45) % 10 + 48;
}
}
else
{
data = (data - 52) % 26 + 65;
}