编译运行
使用的是 ubuntu22.04
需要提前设置好网络
optee运行环境搭建:https://optee.readthedocs.io/en/latest/building/prerequisites.html
安装必要的库
sudo apt install -y \
adb \
acpica-tools \
autoconf \
automake \
bc \
bison \
build-essential \
ccache \
cpio \
cscope \
curl \
device-tree-compiler \
e2tools \
expect \
fastboot \
flex \
ftp-upload \
gdisk \
git \
gdb \
gdb-multiarch \
libattr1-dev \
libcap-ng-dev \
libfdt-dev \
libftdi-dev \
libglib2.0-dev \
libgmp3-dev \
libhidapi-dev \
libmpc-dev \
libncurses5-dev \
libpixman-1-dev \
libslirp-dev \
libssl-dev \
libtool \
libusb-1.0-0-dev \
make \
mtools \
netcat \
ninja-build \
python3-cryptography \
python3-pip \
python3-pyelftools \
python3-serial \
python-is-python3 \
rsync \
swig \
unzip \
uuid-dev \
wget \
xdg-utils \
xterm \
xz-utils \
zlib1g-dev
下载配置 repo,将~/bin/repo中首行的python修改为python3
mkdir ~/bin
curl https://mirrors.tuna.tsinghua.edu.cn/git/git-repo -o ~/bin/repo
chmod a+x ~/bin/repo
echo "PATH=~/bin:$PATH" >> ~/.bashrc
source ~/.bashrc
下载optee并编译
git config --global user.email "you@example.com"
git config --global user.name "Your Name"
mkdir optee && cd optee
repo init -u https://github.com/OP-TEE/manifest.git -m qemu_v8.xml
repo sync
cd build
make toolchains # 下载交叉编译工具
make run # 下载其他内容,编译,运行(需要的时间蛮长的)
在第一个窗口,输入c,continue,继续运行
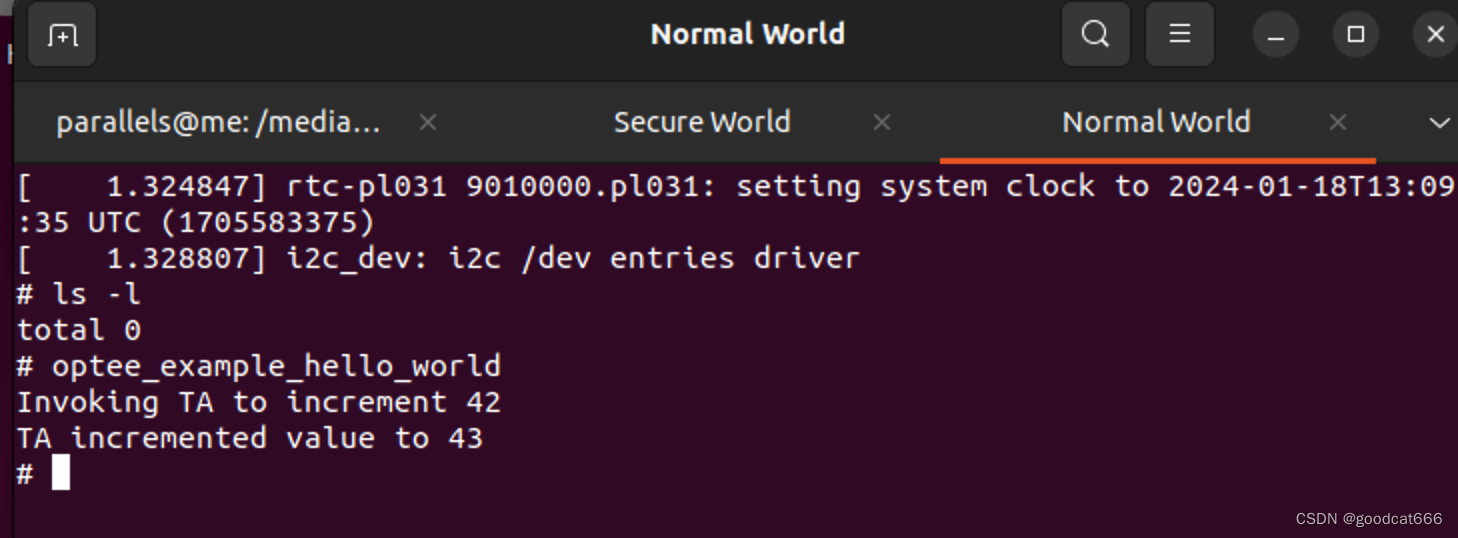
Normal world是linux系统,直接输入用户名root,就进入终端
Secure World是optee-os的日志输出
调试
make DEBUG=1 -f qemu_v8.mk all
make DEBUG=1 -f qemu_v8.mk run-only
去除TA和OPTEE-OS的地址ASLR
make DEBUG=1 CFG_CORE_ASLR=n CFG_TA_ASLR=n -f qemu_v8.mk run
sudo -E gdb-multiarch
set architecture aarch64
target remote :1234
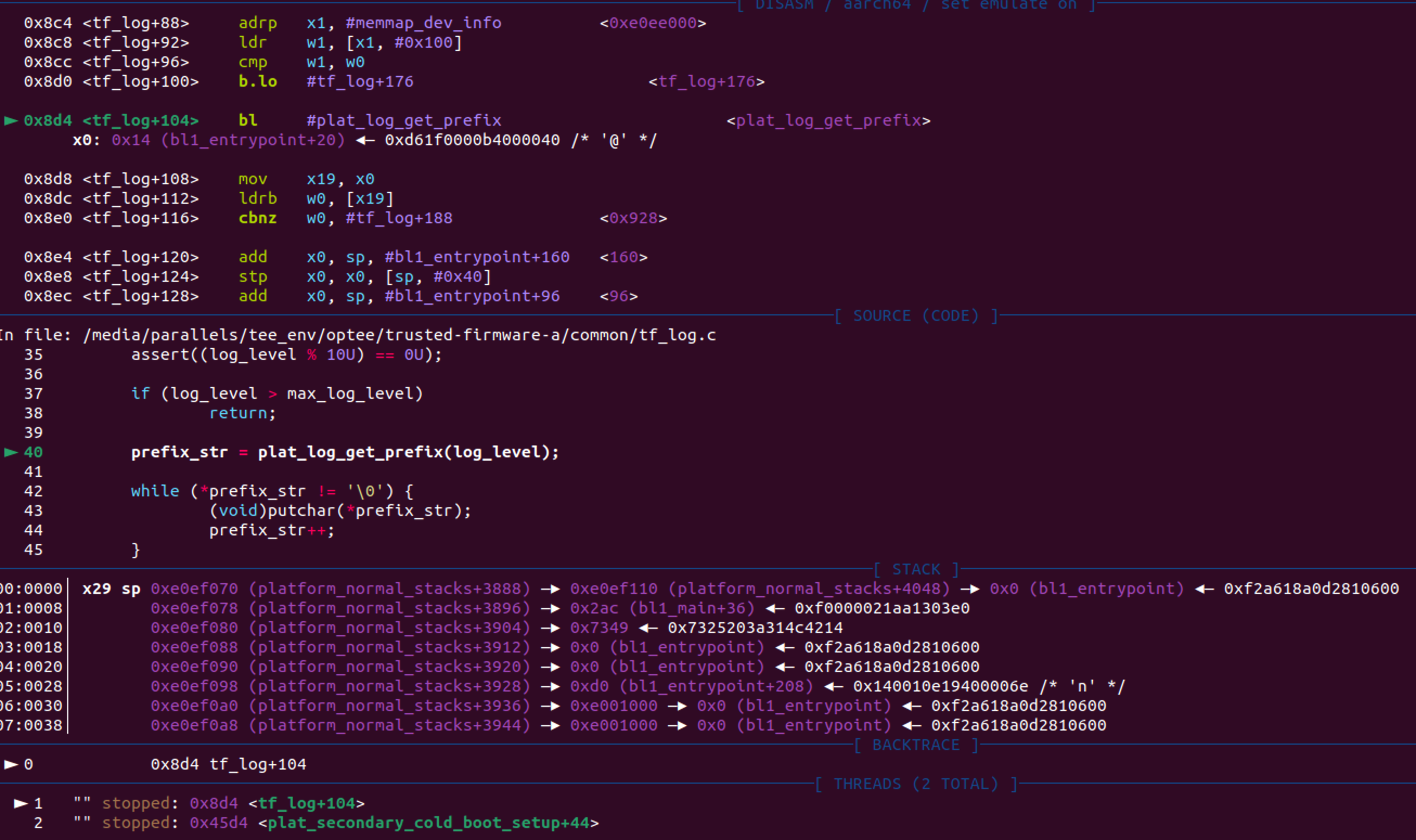
ATF调试
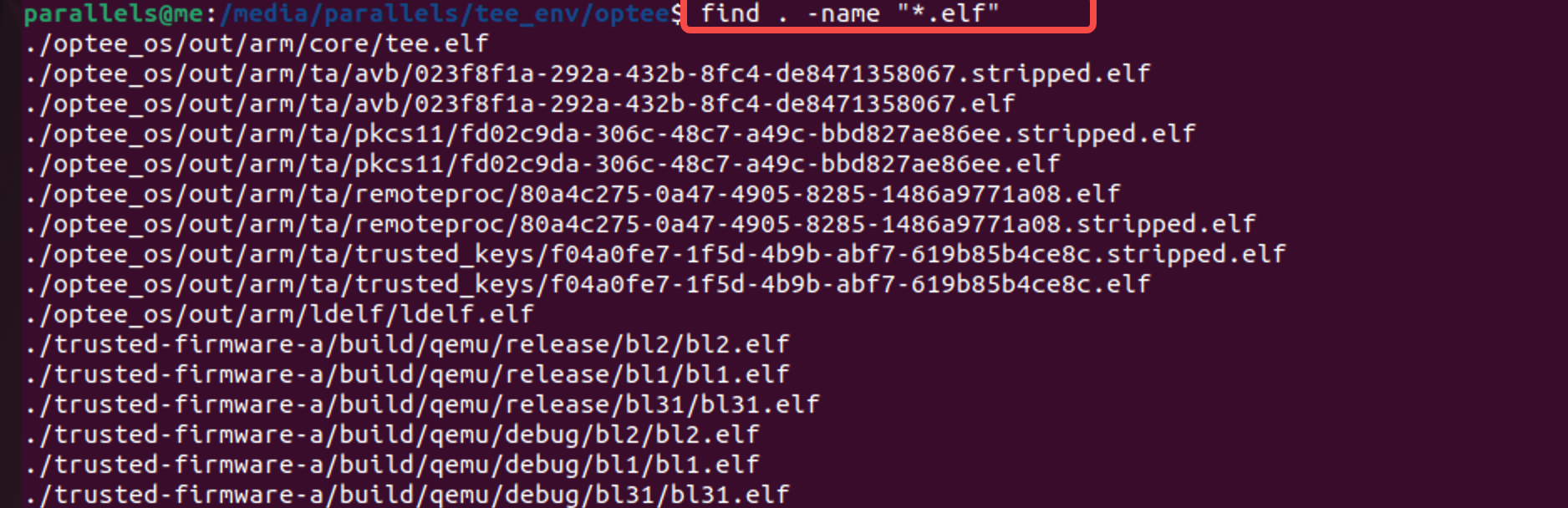
可以看到trusted-firmware-a生成了bl1,bl2,bl31等阶段的elf文件
下断点的時候注意,切换到对应的阶段之后再去 symbol-file xxx 加载符号
pwndbg> set architecture aarch64
The target architecture is set to "aarch64".
pwndbg> symbol-file ./trusted-firmware-a/build/qemu/debug/bl1/bl1.elf
Reading symbols from ./trusted-firmware-a/build/qemu/debug/bl1/bl1.elf...
pwndbg> b bl1_main
Breakpoint 1 at 0x288: file bl1/bl1_main.c, line 96.
pwndbg> target remote :1234
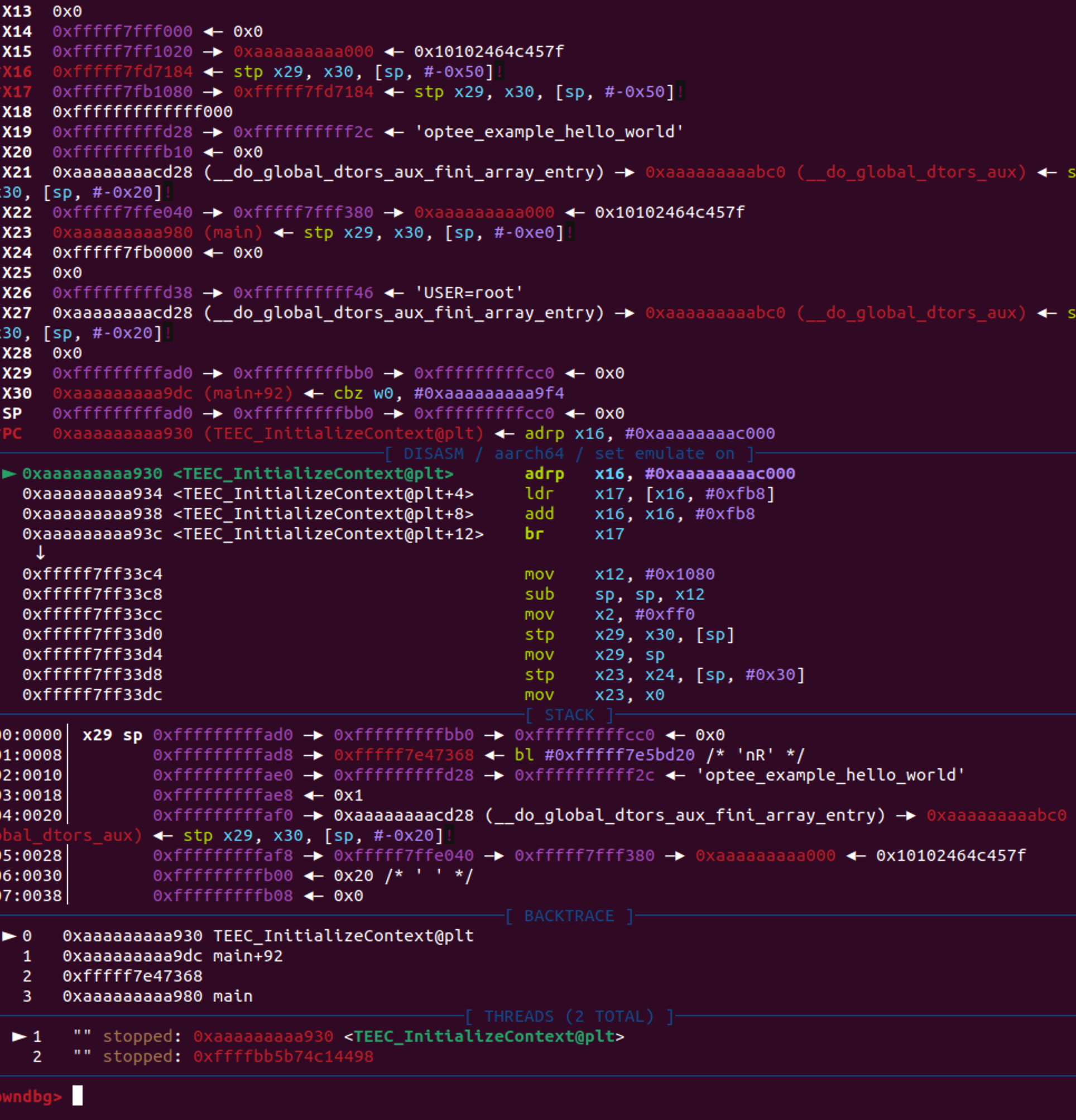
CA调试
cat /proc/sys/kernel/randomize_va_space
echo 0 > /proc/sys/kernel/randomize_va_space
由于已经去除了地址随机化,查看下一次执行app,elf加载地址在什么地方
head -n 1 /proc/self/maps
aaaaaaaaa000-aaaaaab72000 r-xp 00000000 00:02 1058 /bin/busybox
搜索optee_example_hello_world,找到未去除符号的optee_example_hello_world
$ find . -name "optee_example_hello_world"
./out-br/host/aarch64-buildroot-linux-gnu/sysroot/usr/bin/optee_example_hello_world
./out-br/target/usr/bin/optee_example_hello_world
./out-br/build/optee_examples_ext-1.0/hello_world/optee_example_hello_world
./out-br/per-package/optee_examples_ext/host/aarch64-buildroot-linux-gnu/sysroot/usr/bin/optee_example_hello_world
./out-br/per-package/optee_examples_ext/target/usr/bin/optee_example_hello_world
$ file ./out-br/build/optee_examples_ext-1.0/hello_world/optee_example_hello_world
./out-br/build/optee_examples_ext-1.0/hello_world/optee_example_hello_world: ELF 64-bit LSB pie executable, ARM aarch64, version 1 (SYSV), dynamically linked, interpreter /lib/ld-linux-aarch64.so.1, for GNU/Linux 3.7.0, with debug_info, not stripped
加载符号
pwndbg> add-symbol-file ./out-br/build/optee_examples_ext-1.0/hello_world/optee_example_hello_world -o aaaaaaaaa000
pwndbg> b TEEC_InitializeContext
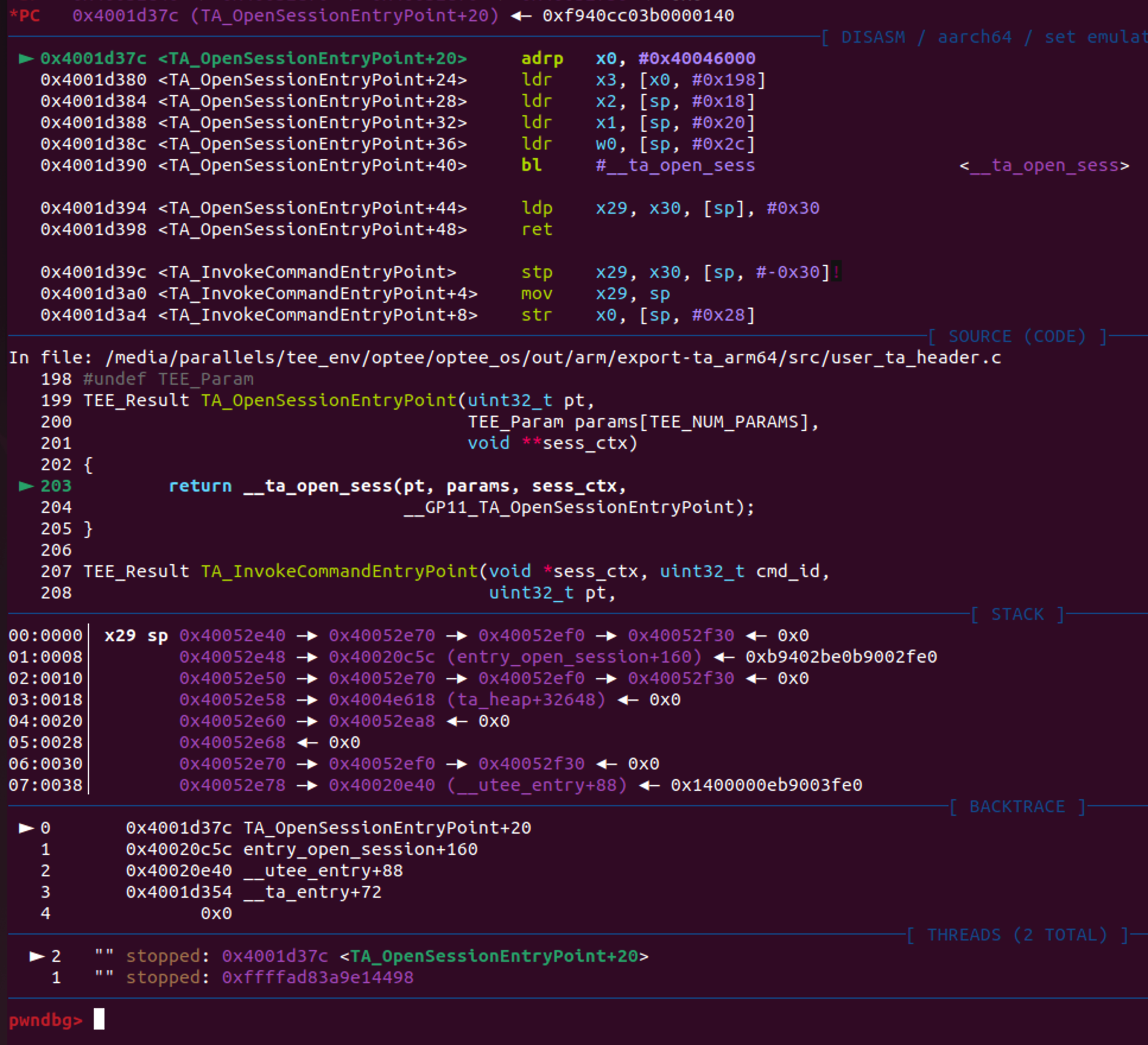
TA调试 && TEE-OS调试
调试TA
在normal侧执行
optee_example_hello_world
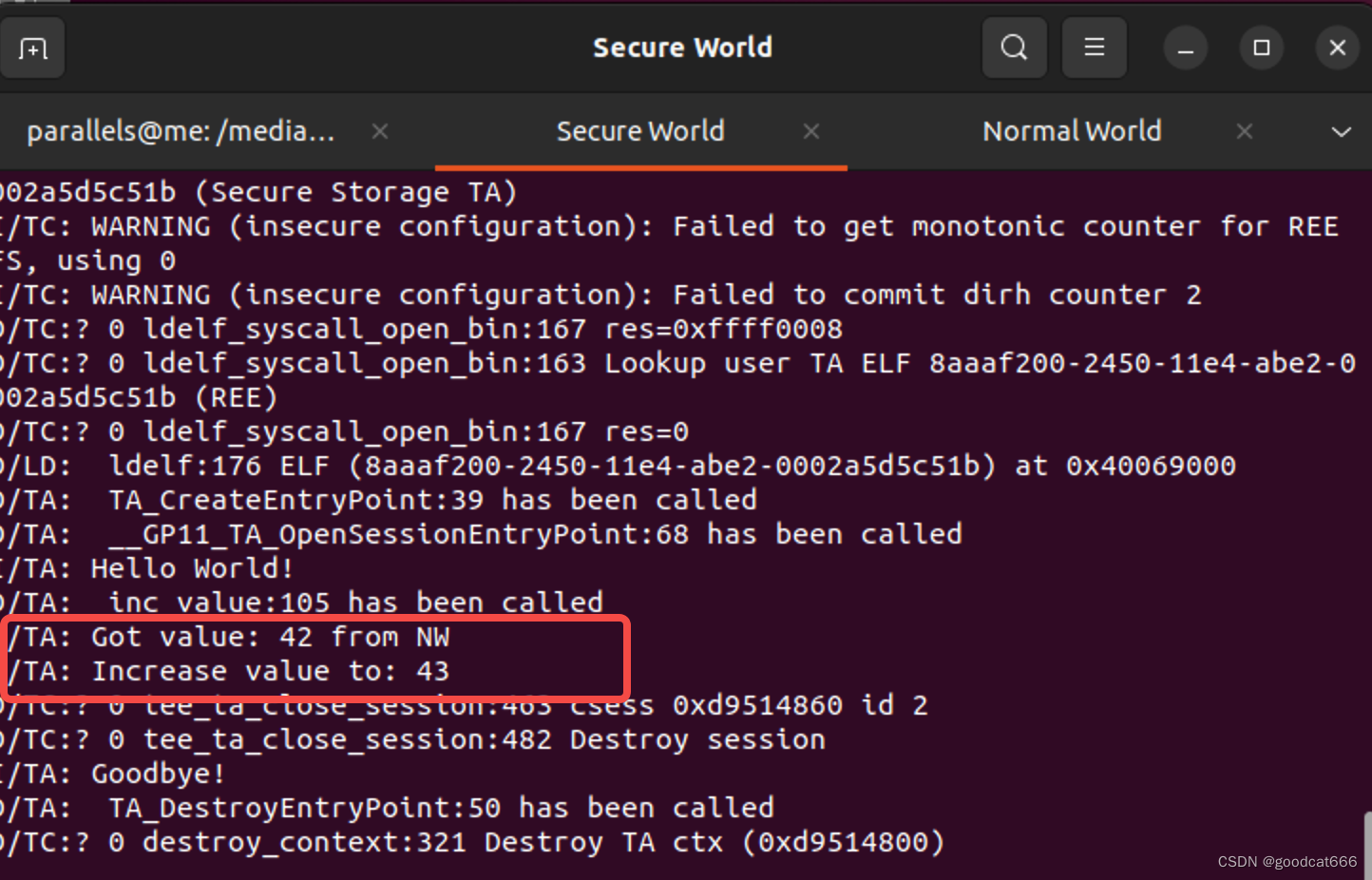
在secure侧查看对应的ta,以及加载地址
D/LD: ldelf:176 ELF (8aaaf200-2450-11e4-abe2-0002a5d5c51b) at 0x4001d000
在optee目录下,搜索有符号的ta
$ find . -name "8aaaf200-2450-11e4-abe2-0002a5d5c51b*"
./out-br/build/optee_examples_ext-1.0/hello_world/ta/out/8aaaf200-2450-11e4-abe2-0002a5d5c51b.elf
$ file ./out-br/build/optee_examples_ext-1.0/hello_world/ta/out/8aaaf200-2450-11e4-abe2-0002a5d5c51b.elf
./out-br/build/optee_examples_ext-1.0/hello_world/ta/out/8aaaf200-2450-11e4-abe2-0002a5d5c51b.elf: ELF 64-bit LSB pie executable, ARM aarch64, version 1 (SYSV), static-pie linked, with debug_info, not stripped
gdb加载符号
pwndbg> add-symbol-file ./out-br/build/optee_examples_ext-1.0/hello_world/ta/out/8aaaf200-2450-11e4-abe2-0002a5d5c51b.elf -o 0x4001d000
add symbol table from file "./out-br/build/optee_examples_ext-1.0/hello_world/ta/out/8aaaf200-2450-11e4-abe2-0002a5d5c51b.elf" with all sections offset by 0x4001d000
Reading symbols from ./out-br/build/optee_examples_ext-1.0/hello_world/ta/out/8aaaf200-2450-11e4-abe2-0002a5d5c51b.elf...
pwndbg> b TA_OpenSessionEntryPoint
Breakpoint 1 at 0x4001d37c: file /media/parallels/tee_env/optee/optee_os/out/arm/export-ta_arm64/src/user_ta_header.c, line 203.
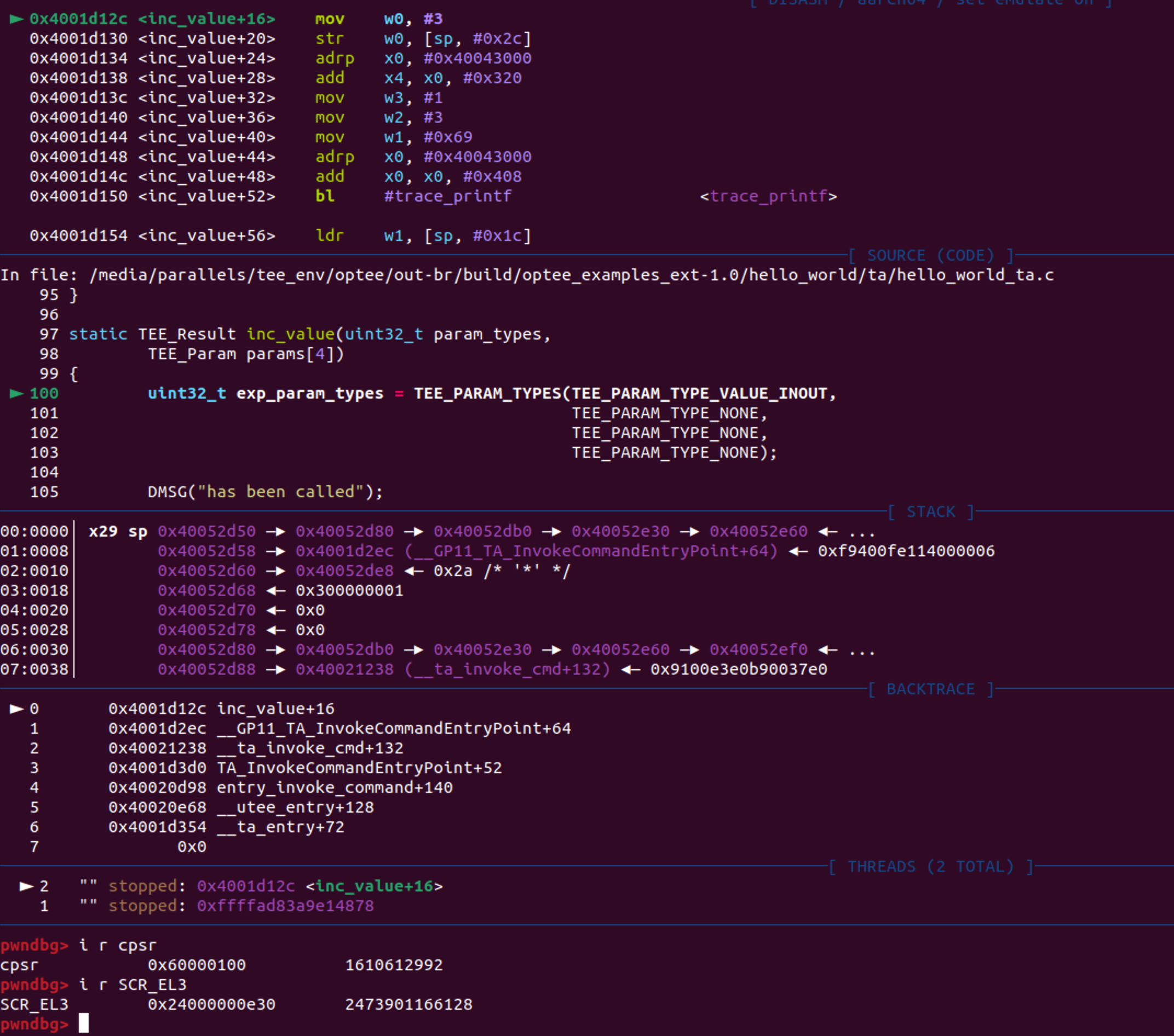
pwndbg> b inc_value
Breakpoint 2 at 0x4001d12c: file hello_world_ta.c, line 100.
pwndbg> b dec_value
Breakpoint 3 at 0x4001d1f4: file hello_world_ta.c, line 120.
pwndbg>
调试optee-os
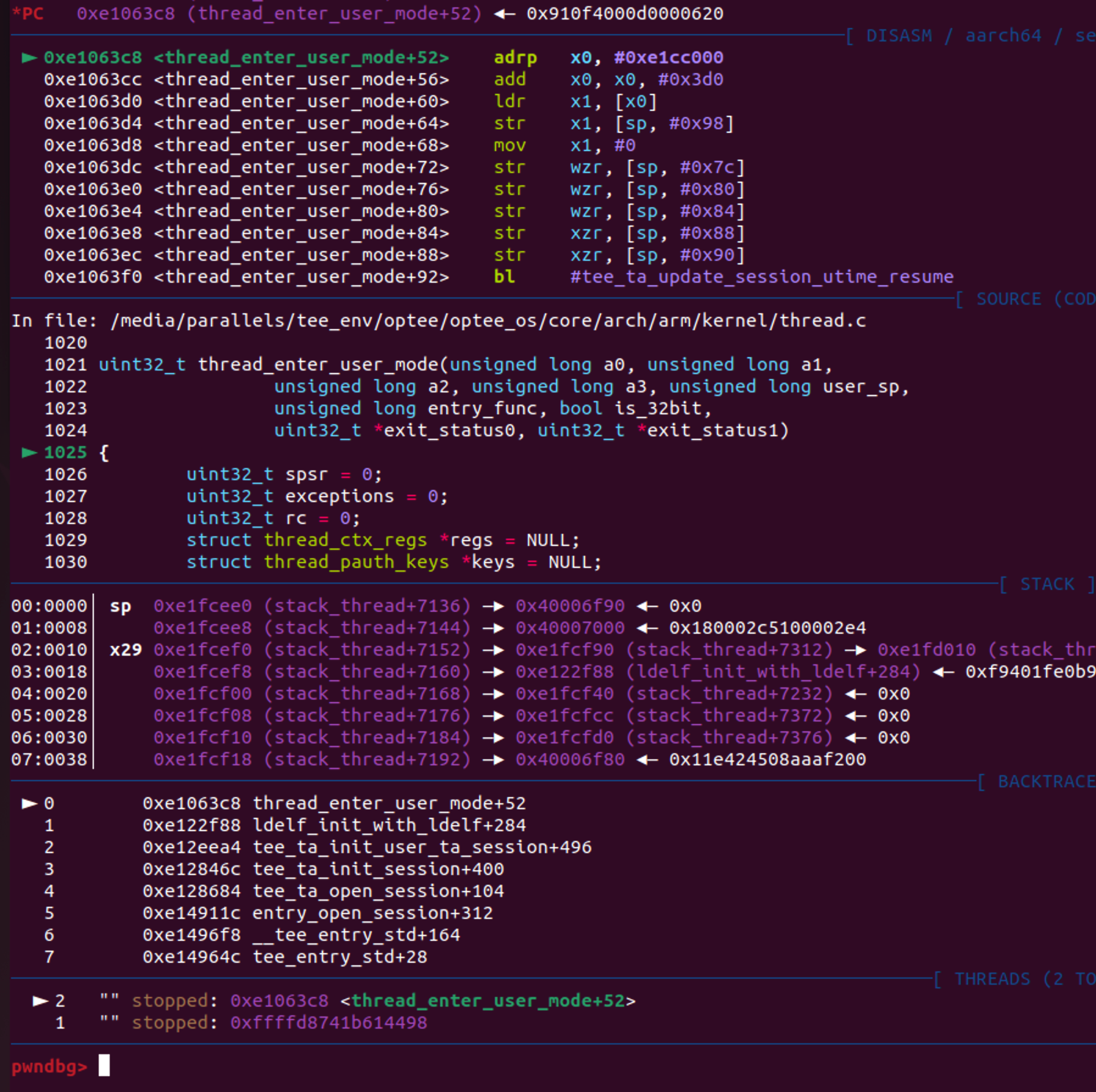
pwndbg> symbol-file ./optee_os/out/arm/core/tee.elf
Reading symbols from ./optee_os/out/arm/core/tee.elf...
pwndbg> b thread_enter_user_mode
Breakpoint 1 at 0xe1063c8: file core/arch/arm/kernel/thread.c, line 1025.
参考
https://teaclave.apache.org/trustzone-sdk-docs/debugging-optee-ta.md/
https://github.com/ForgeRock/optee-build/blob/master/docs/debug.md
https://www.cnblogs.com/han-guang-xue/p/17825453.html
https://o0xmuhe.github.io/2022/08/24/optee学习/