血的教训–kail系统免密centos7的坑【高版本ssh免密低版本ssh的坑】
最近下载了一个2023版本的kail系统,但是经过几次设置免密后,ssh过去一直让提供密码,所以就仔细的分析了一下,果然还是发现了点猫腻
接上一个博客,大家可以看看,ssh免密之间的坑
入侵redis之准备—linux之间的免密通信原来是这么的简单
ssh免密其实很简单,但是没想到还是有一些坑
出现免密失败的情况,我也是百度了好多,都是让更改目录的权限,但是都失败了,其实这跟权限有关系,但是我们基本上也不会动这些目录的权限,如果你的权限没有问题,那就可以往我这个方向考虑了,那就是高版本的ssh加密方式和低版本ssh啊hi见的加密方式不一样,大家知道最近ssh低于9版本有漏洞,所以ssh版本都升级到9以上了,但是部分还是9一下版本,这个就是免密失败的原因。
关键报错:
debug2: we did not send a packet, disable method
debug3: authmethod_lookup publickey
debug3: remaining preferred: keyboard-interactive,password
debug3: authmethod_is_enabled publickey
debug1: Next authentication method: publickey
debug1: Trying private key: /home/liushuai/.ssh/id_rsa
debug3: no such identity: /home/liushuai/.ssh/id_rsa: No such file or directory
debug1: Trying private key: /home/liushuai/.ssh/id_ecdsa
debug3: no such identity: /home/liushuai/.ssh/id_ecdsa: No such file or directory
debug1: Trying private key: /home/liushuai/.ssh/id_ecdsa_sk
debug3: no such identity: /home/liushuai/.ssh/id_ecdsa_sk: No such file or directory
debug1: Trying private key: /home/liushuai/.ssh/id_ed25519
debug3: no such identity: /home/liushuai/.ssh/id_ed25519: No such file or directory
debug1: Trying private key: /home/liushuai/.ssh/id_ed25519_sk
debug3: no such identity: /home/liushuai/.ssh/id_ed25519_sk: No such file or directory
debug1: Trying private key: /home/liushuai/.ssh/id_xmss
debug3: no such identity: /home/liushuai/.ssh/id_xmss: No such file or directory
debug2: we did not send a packet, disable method
debug3: authmethod_lookup password
debug3: remaining preferred: ,password
debug3: authmethod_is_enabled password
debug1: Next authentication method: password
废话不多说,直接开干
| 系统 | ip | 介绍 |
|---|---|---|
| kail系统 | 192.168.126.132 | 生成公钥,并推送到centos7上 |
| centos7 | 192.168.126.133 | 接受免密,实现kail往centos7方向免密 |
先按照老的免密方式搞一波
生成密钥
┌──(liushuai㉿bogon)-[~]
└─$ ssh-keygen -t dsa ###注意看,咱这边的加密方式是dsa,这个就是坑
Generating public/private dsa key pair.
Enter file in which to save the key (/home/liushuai/.ssh/id_dsa):
Created directory '/home/liushuai/.ssh'.
Enter passphrase (empty for no passphrase):
Enter same passphrase again:
Your identification has been saved in /home/liushuai/.ssh/id_dsa
Your public key has been saved in /home/liushuai/.ssh/id_dsa.pub
The key fingerprint is:
SHA256:k47VhY43db0GBtwHoUvZIVgnPDYui3QtT4vsGgBXewQ liushuai@bogon
The key's randomart image is:
+---[DSA 1024]----+
| E..==.=o |
| . o. BO..o |
| . . . .=+=+o .|
| o ..O.*o.. .|
| .. S %.. o |
| .= * + . |
| ..o |
| .. |
| .. |
+----[SHA256]-----+

拷贝密钥
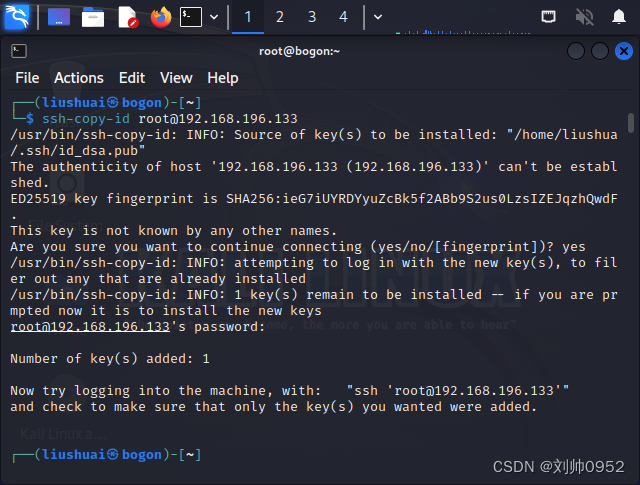
┌──(liushuai㉿bogon)-[~]
└─$ ssh-copy-id root@192.168.196.133
/usr/bin/ssh-copy-id: INFO: Source of key(s) to be installed: "/home/liushuai/.ssh/id_dsa.pub"
The authenticity of host '192.168.196.133 (192.168.196.133)' can't be established.
ED25519 key fingerprint is SHA256:ieG7iUYRDYyuZcBk5f2ABb9S2us0LzsIZEJqzhQwdFM.
This key is not known by any other names.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
/usr/bin/ssh-copy-id: INFO: attempting to log in with the new key(s), to filter out any that are already installed
/usr/bin/ssh-copy-id: INFO: 1 key(s) remain to be installed -- if you are prompted now it is to install the new keys
root@192.168.196.133's password:
Number of key(s) added: 1
Now try logging into the machine, with: "ssh 'root@192.168.196.133'"
and check to make sure that only the key(s) you wanted were added.
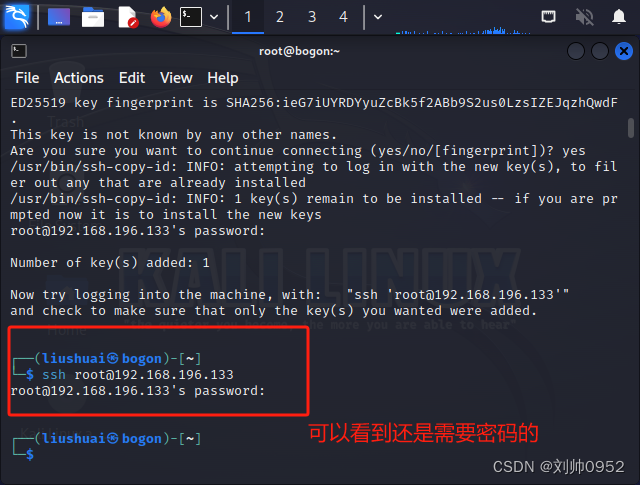
测试免密登录
┌──(liushuai㉿bogon)-[~]
└─$ ssh root@192.168.196.133
root@192.168.196.133's password: ####还是需要密码的,为什么的接着往下看
原因分析
经过排查,是因为两台主机的ssh版本问题
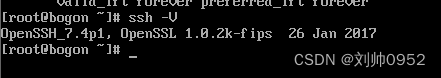
kail系统的版本:OpenSSH_9.3p2 Debian-1
┌──(liushuai㉿bogon)-[~]
└─$ ssh -V
OpenSSH_9.3p2 Debian-1, OpenSSL 3.0.10 1 Aug 2023

centos的版本:7.4P1
进一步分析
利用ssh -vvv的功能,查看问题出现在哪里
┌──(liushuai㉿bogon)-[~]
└─$ ssh root@192.168.196.133
root@192.168.196.133's password:
Last login: Wed Nov 29 07:52:35 2023
[root@bogon ~]# exit
logout
Connection to 192.168.196.133 closed.
┌──(liushuai㉿bogon)-[~]
└─$ ssh root@192.168.196.133 -vvv
OpenSSH_9.3p2 Debian-1, OpenSSL 3.0.10 1 Aug 2023
debug1: Reading configuration data /etc/ssh/ssh_config
debug1: /etc/ssh/ssh_config line 19: include /etc/ssh/ssh_config.d/*.conf matched no files
debug1: /etc/ssh/ssh_config line 21: Applying options for *
debug2: resolve_canonicalize: hostname 192.168.196.133 is address
debug3: expanded UserKnownHostsFile '~/.ssh/known_hosts' -> '/home/liushuai/.ssh/known_hosts'
debug3: expanded UserKnownHostsFile '~/.ssh/known_hosts2' -> '/home/liushuai/.ssh/known_hosts2'
debug3: ssh_connect_direct: entering
debug1: Connecting to 192.168.196.133 [192.168.196.133] port 22.
debug3: set_sock_tos: set socket 3 IP_TOS 0x10
debug1: Connection established.
debug1: identity file /home/liushuai/.ssh/id_rsa type -1
debug1: identity file /home/liushuai/.ssh/id_rsa-cert type -1
debug1: identity file /home/liushuai/.ssh/id_ecdsa type -1
debug1: identity file /home/liushuai/.ssh/id_ecdsa-cert type -1
debug1: identity file /home/liushuai/.ssh/id_ecdsa_sk type -1
debug1: identity file /home/liushuai/.ssh/id_ecdsa_sk-cert type -1
debug1: identity file /home/liushuai/.ssh/id_ed25519 type -1
debug1: identity file /home/liushuai/.ssh/id_ed25519-cert type -1
debug1: identity file /home/liushuai/.ssh/id_ed25519_sk type -1
debug1: identity file /home/liushuai/.ssh/id_ed25519_sk-cert type -1
debug1: identity file /home/liushuai/.ssh/id_xmss type -1
debug1: identity file /home/liushuai/.ssh/id_xmss-cert type -1
debug1: identity file /home/liushuai/.ssh/id_dsa type 1
debug1: identity file /home/liushuai/.ssh/id_dsa-cert type -1
debug1: Local version string SSH-2.0-OpenSSH_9.3p2 Debian-1
debug1: Remote protocol version 2.0, remote software version OpenSSH_7.4
debug1: compat_banner: match: OpenSSH_7.4 pat OpenSSH_7.4* compat 0x04000006
debug2: fd 3 setting O_NONBLOCK
debug1: Authenticating to 192.168.196.133:22 as 'root'
debug3: record_hostkey: found key type ED25519 in file /home/liushuai/.ssh/known_hosts:1
debug3: record_hostkey: found key type ECDSA in file /home/liushuai/.ssh/known_hosts:2
debug3: load_hostkeys_file: loaded 2 keys from 192.168.196.133
debug1: load_hostkeys: fopen /home/liushuai/.ssh/known_hosts2: No such file or directory
debug1: load_hostkeys: fopen /etc/ssh/ssh_known_hosts: No such file or directory
debug1: load_hostkeys: fopen /etc/ssh/ssh_known_hosts2: No such file or directory
debug3: order_hostkeyalgs: have matching best-preference key type ssh-ed25519-cert-v01@openssh.com, using HostkeyAlgorithms verbatim
debug3: send packet: type 20
debug1: SSH2_MSG_KEXINIT sent
debug3: receive packet: type 20
debug1: SSH2_MSG_KEXINIT received
debug2: local client KEXINIT proposal
debug2: KEX algorithms: sntrup761x25519-sha512@openssh.com,curve25519-sha256,curve25519-sha256@libssh.org,ecdh-sha2-nistp256,ecdh-sha2-nistp384,ecdh-sha2-nistp521,diffie-hellman-group-exchange-sha256,diffie-hellman-group16-sha512,diffie-hellman-group18-sha512,diffie-hellman-group14-sha256,ext-info-c
debug2: host key algorithms: ssh-ed25519-cert-v01@openssh.com,ecdsa-sha2-nistp256-cert-v01@openssh.com,ecdsa-sha2-nistp384-cert-v01@openssh.com,ecdsa-sha2-nistp521-cert-v01@openssh.com,sk-ssh-ed25519-cert-v01@openssh.com,sk-ecdsa-sha2-nistp256-cert-v01@openssh.com,rsa-sha2-512-cert-v01@openssh.com,rsa-sha2-256-cert-v01@openssh.com,ssh-ed25519,ecdsa-sha2-nistp256,ecdsa-sha2-nistp384,ecdsa-sha2-nistp521,sk-ssh-ed25519@openssh.com,sk-ecdsa-sha2-nistp256@openssh.com,rsa-sha2-512,rsa-sha2-256
debug2: ciphers ctos: chacha20-poly1305@openssh.com,aes128-ctr,aes192-ctr,aes256-ctr,aes128-gcm@openssh.com,aes256-gcm@openssh.com
debug2: ciphers stoc: chacha20-poly1305@openssh.com,aes128-ctr,aes192-ctr,aes256-ctr,aes128-gcm@openssh.com,aes256-gcm@openssh.com
debug2: MACs ctos: umac-64-etm@openssh.com,umac-128-etm@openssh.com,hmac-sha2-256-etm@openssh.com,hmac-sha2-512-etm@openssh.com,hmac-sha1-etm@openssh.com,umac-64@openssh.com,umac-128@openssh.com,hmac-sha2-256,hmac-sha2-512,hmac-sha1
debug2: MACs stoc: umac-64-etm@openssh.com,umac-128-etm@openssh.com,hmac-sha2-256-etm@openssh.com,hmac-sha2-512-etm@openssh.com,hmac-sha1-etm@openssh.com,umac-64@openssh.com,umac-128@openssh.com,hmac-sha2-256,hmac-sha2-512,hmac-sha1
debug2: compression ctos: none,zlib@openssh.com,zlib
debug2: compression stoc: none,zlib@openssh.com,zlib
debug2: languages ctos:
debug2: languages stoc:
debug2: first_kex_follows 0
debug2: reserved 0
debug2: peer server KEXINIT proposal
debug2: KEX algorithms: curve25519-sha256,curve25519-sha256@libssh.org,ecdh-sha2-nistp256,ecdh-sha2-nistp384,ecdh-sha2-nistp521,diffie-hellman-group-exchange-sha256,diffie-hellman-group16-sha512,diffie-hellman-group18-sha512,diffie-hellman-group-exchange-sha1,diffie-hellman-group14-sha256,diffie-hellman-group14-sha1,diffie-hellman-group1-sha1
debug2: host key algorithms: ssh-rsa,rsa-sha2-512,rsa-sha2-256,ecdsa-sha2-nistp256,ssh-ed25519
debug2: ciphers ctos: chacha20-poly1305@openssh.com,aes128-ctr,aes192-ctr,aes256-ctr,aes128-gcm@openssh.com,aes256-gcm@openssh.com,aes128-cbc,aes192-cbc,aes256-cbc,blowfish-cbc,cast128-cbc,3des-cbc
debug2: ciphers stoc: chacha20-poly1305@openssh.com,aes128-ctr,aes192-ctr,aes256-ctr,aes128-gcm@openssh.com,aes256-gcm@openssh.com,aes128-cbc,aes192-cbc,aes256-cbc,blowfish-cbc,cast128-cbc,3des-cbc
debug2: MACs ctos: umac-64-etm@openssh.com,umac-128-etm@openssh.com,hmac-sha2-256-etm@openssh.com,hmac-sha2-512-etm@openssh.com,hmac-sha1-etm@openssh.com,umac-64@openssh.com,umac-128@openssh.com,hmac-sha2-256,hmac-sha2-512,hmac-sha1
debug2: MACs stoc: umac-64-etm@openssh.com,umac-128-etm@openssh.com,hmac-sha2-256-etm@openssh.com,hmac-sha2-512-etm@openssh.com,hmac-sha1-etm@openssh.com,umac-64@openssh.com,umac-128@openssh.com,hmac-sha2-256,hmac-sha2-512,hmac-sha1
debug2: compression ctos: none,zlib@openssh.com
debug2: compression stoc: none,zlib@openssh.com
debug2: languages ctos:
debug2: languages stoc:
debug2: first_kex_follows 0
debug2: reserved 0
debug1: kex: algorithm: curve25519-sha256
debug1: kex: host key algorithm: ssh-ed25519
debug1: kex: server->client cipher: chacha20-poly1305@openssh.com MAC: <implicit> compression: none
debug1: kex: client->server cipher: chacha20-poly1305@openssh.com MAC: <implicit> compression: none
debug3: send packet: type 30
debug1: expecting SSH2_MSG_KEX_ECDH_REPLY
debug3: receive packet: type 31
debug1: SSH2_MSG_KEX_ECDH_REPLY received
debug1: Server host key: ssh-ed25519 SHA256:ieG7iUYRDYyuZcBk5f2ABb9S2us0LzsIZEJqzhQwdFM
debug3: record_hostkey: found key type ED25519 in file /home/liushuai/.ssh/known_hosts:1
debug3: record_hostkey: found key type ECDSA in file /home/liushuai/.ssh/known_hosts:2
debug3: load_hostkeys_file: loaded 2 keys from 192.168.196.133
debug1: load_hostkeys: fopen /home/liushuai/.ssh/known_hosts2: No such file or directory
debug1: load_hostkeys: fopen /etc/ssh/ssh_known_hosts: No such file or directory
debug1: load_hostkeys: fopen /etc/ssh/ssh_known_hosts2: No such file or directory
debug1: Host '192.168.196.133' is known and matches the ED25519 host key.
debug1: Found key in /home/liushuai/.ssh/known_hosts:1
debug3: send packet: type 21
debug2: ssh_set_newkeys: mode 1
debug1: rekey out after 134217728 blocks
debug1: SSH2_MSG_NEWKEYS sent
debug1: expecting SSH2_MSG_NEWKEYS
debug3: receive packet: type 21
debug1: SSH2_MSG_NEWKEYS received
debug2: ssh_set_newkeys: mode 0
debug1: rekey in after 134217728 blocks
debug3: ssh_get_authentication_socket_path: path '/tmp/ssh-6WK2JhuI1VHD/agent.1125'
debug1: get_agent_identities: bound agent to hostkey
debug1: get_agent_identities: ssh_fetch_identitylist: agent contains no identities
debug1: Skipping ssh-dss key /home/liushuai/.ssh/id_dsa - corresponding algo not in PubkeyAcceptedAlgorithms
debug1: Will attempt key: /home/liushuai/.ssh/id_rsa
debug1: Will attempt key: /home/liushuai/.ssh/id_ecdsa
debug1: Will attempt key: /home/liushuai/.ssh/id_ecdsa_sk
debug1: Will attempt key: /home/liushuai/.ssh/id_ed25519
debug1: Will attempt key: /home/liushuai/.ssh/id_ed25519_sk
debug1: Will attempt key: /home/liushuai/.ssh/id_xmss
debug2: pubkey_prepare: done
debug3: send packet: type 5
debug3: receive packet: type 7
debug1: SSH2_MSG_EXT_INFO received
debug1: kex_input_ext_info: server-sig-algs=<rsa-sha2-256,rsa-sha2-512>
debug3: receive packet: type 6
debug2: service_accept: ssh-userauth
debug1: SSH2_MSG_SERVICE_ACCEPT received
debug3: send packet: type 50
debug3: receive packet: type 51
debug1: Authentications that can continue: publickey,gssapi-keyex,gssapi-with-mic,password
debug3: start over, passed a different list publickey,gssapi-keyex,gssapi-with-mic,password
debug3: preferred gssapi-with-mic,publickey,keyboard-interactive,password
debug3: authmethod_lookup gssapi-with-mic
debug3: remaining preferred: publickey,keyboard-interactive,password
debug3: authmethod_is_enabled gssapi-with-mic
debug1: Next authentication method: gssapi-with-mic
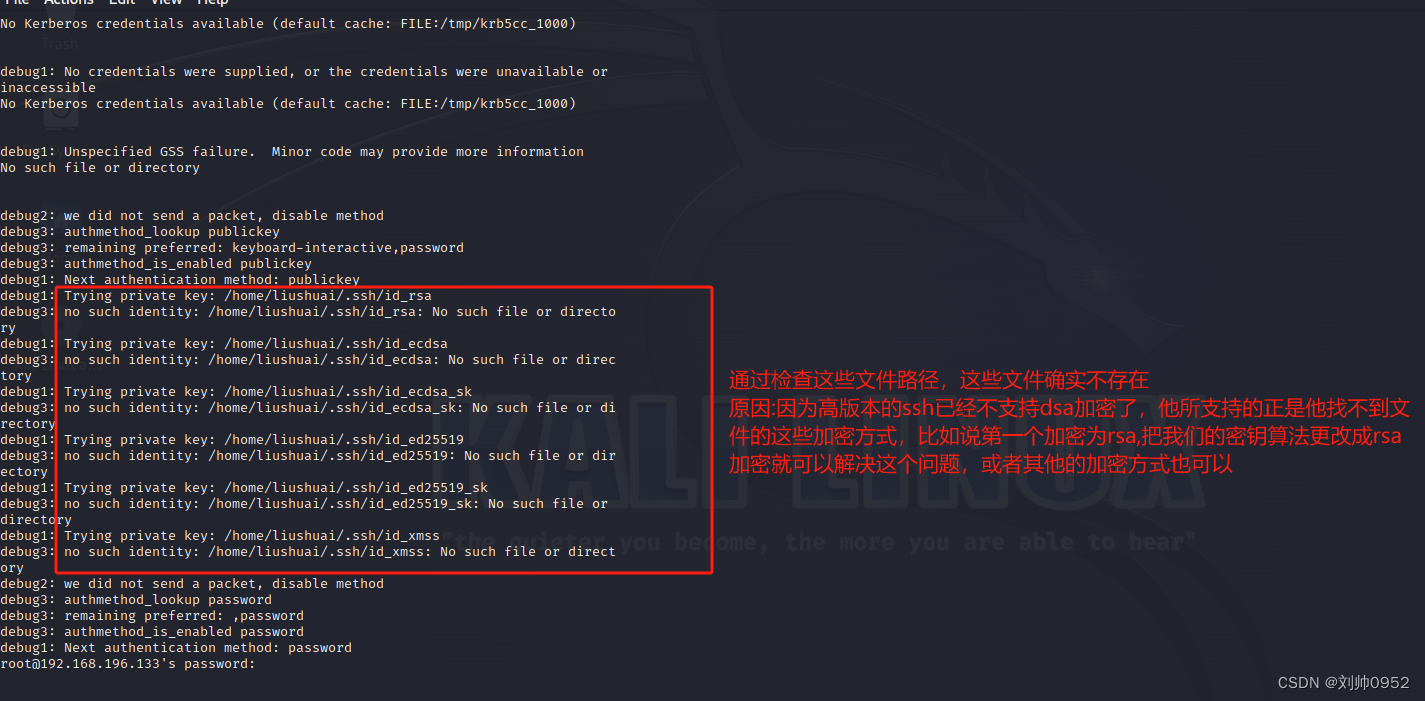
debug1: No credentials were supplied, or the credentials were unavailable or inaccessible
No Kerberos credentials available (default cache: FILE:/tmp/krb5cc_1000)
debug1: No credentials were supplied, or the credentials were unavailable or inaccessible
No Kerberos credentials available (default cache: FILE:/tmp/krb5cc_1000)
debug1: Unspecified GSS failure. Minor code may provide more information
No such file or directory
debug2: we did not send a packet, disable method
debug3: authmethod_lookup publickey
debug3: remaining preferred: keyboard-interactive,password
debug3: authmethod_is_enabled publickey
debug1: Next authentication method: publickey
debug1: Trying private key: /home/liushuai/.ssh/id_rsa ###出现找不到文件
debug3: no such identity: /home/liushuai/.ssh/id_rsa: No such file or directory
debug1: Trying private key: /home/liushuai/.ssh/id_ecdsa ###出现找不到文件
debug3: no such identity: /home/liushuai/.ssh/id_ecdsa: No such file or directory
debug1: Trying private key: /home/liushuai/.ssh/id_ecdsa_sk ###出现找不到文件
debug3: no such identity: /home/liushuai/.ssh/id_ecdsa_sk: No such file or directory
debug1: Trying private key: /home/liushuai/.ssh/id_ed25519 ###出现找不到文件
debug3: no such identity: /home/liushuai/.ssh/id_ed25519: No such file or directory
debug1: Trying private key: /home/liushuai/.ssh/id_ed25519_sk ###出现找不到文件
debug3: no such identity: /home/liushuai/.ssh/id_ed25519_sk: No such file or directory
debug1: Trying private key: /home/liushuai/.ssh/id_xmss ###出现找不到文件
debug3: no such identity: /home/liushuai/.ssh/id_xmss: No such file or directory
debug2: we did not send a packet, disable method
debug3: authmethod_lookup password
debug3: remaining preferred: ,password
debug3: authmethod_is_enabled password
debug1: Next authentication method: password
root@192.168.196.133's password:
更改加密方式为rsa
清理掉之前的密钥文件
──(liushuai㉿bogon)-[~]
└─$ cd .ssh
┌──(liushuai㉿bogon)-[~/.ssh]
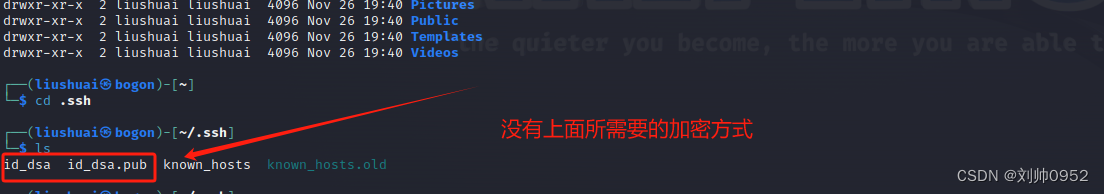
└─$ ls
id_dsa id_dsa.pub known_hosts known_hosts.old
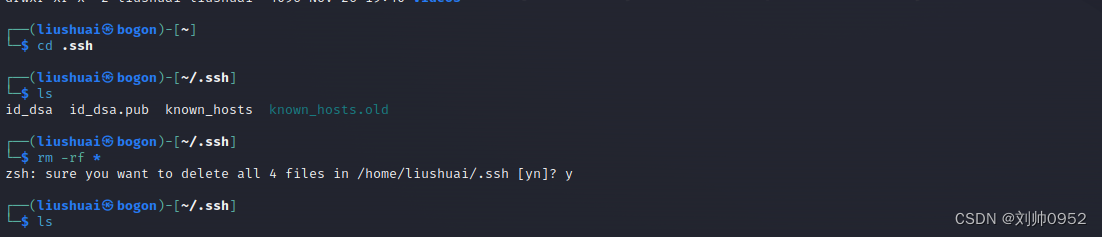
┌──(liushuai㉿bogon)-[~/.ssh] ###直接在.ssh目录下,清理即可,如有需要建议备份
└─$ rm -rf *
zsh: sure you want to delete all 4 files in /home/liushuai/.ssh [yn]? y
┌──(liushuai㉿bogon)-[~/.ssh]
└─$ ls
 ### 重新生成密钥
### 重新生成密钥
┌──(liushuai㉿bogon)-[~/.ssh]
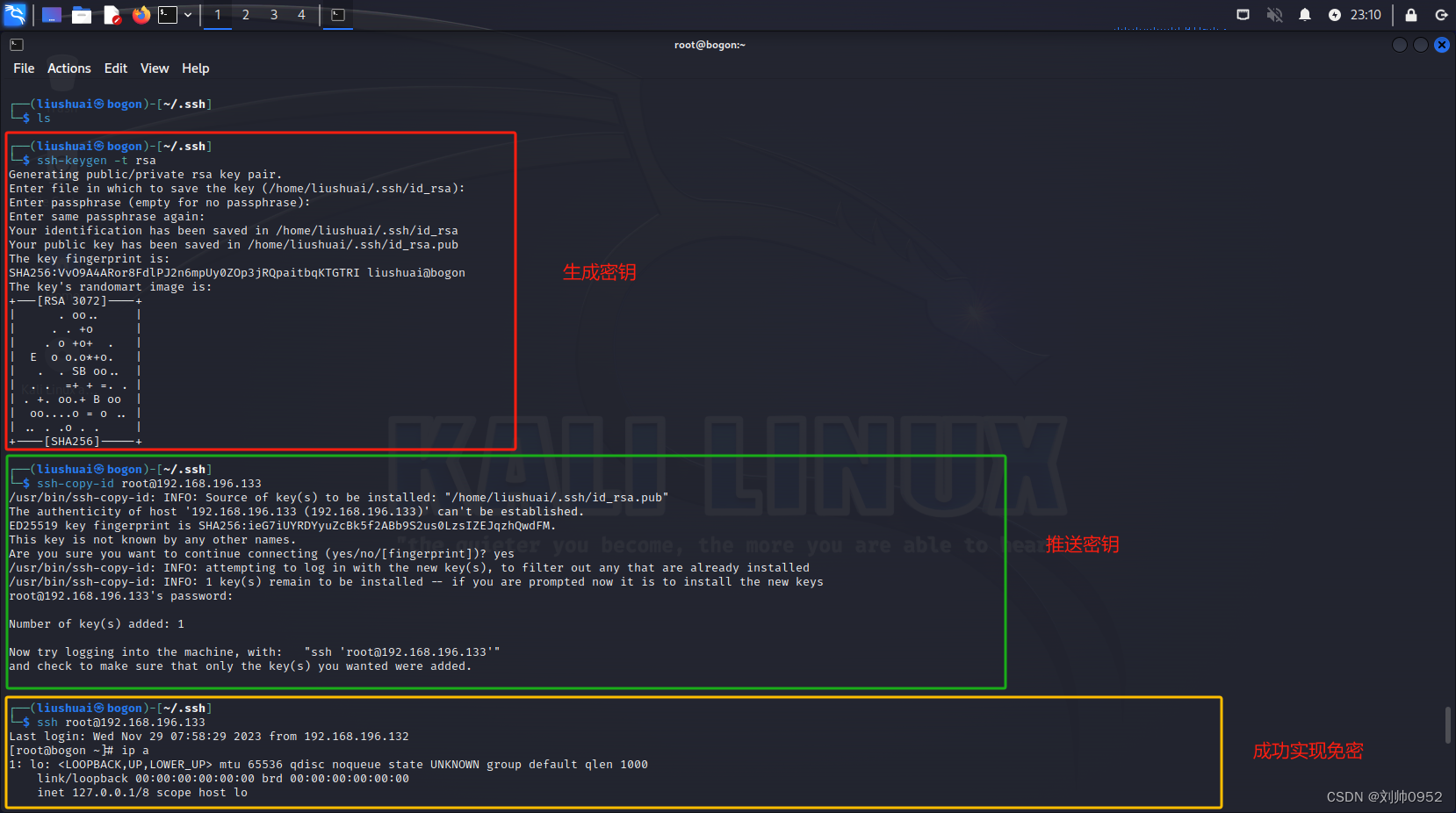
└─$ ssh-keygen -t rsa ##更换了加密算法为rsa
Generating public/private rsa key pair.
Enter file in which to save the key (/home/liushuai/.ssh/id_rsa):
Enter passphrase (empty for no passphrase):
Enter same passphrase again:
Your identification has been saved in /home/liushuai/.ssh/id_rsa
Your public key has been saved in /home/liushuai/.ssh/id_rsa.pub
The key fingerprint is:
SHA256:VvO9A4ARor8FdlPJ2n6mpUy0ZOp3jRQpaitbqKTGTRI liushuai@bogon
The key's randomart image is:
+---[RSA 3072]----+
| . oo.. |
| . . +o |
| . o +o+ . |
| E o o.o*+o. |
| . . SB oo.. |
| . . =+ + =. . |
| . +. oo.+ B oo |
| oo....o = o .. |
| .. . .o . . |
+----[SHA256]-----+
推送密钥
──(liushuai㉿bogon)-[~/.ssh]
└─$ ssh-copy-id root@192.168.196.133 ###推送方式不变
/usr/bin/ssh-copy-id: INFO: Source of key(s) to be installed: "/home/liushuai/.ssh/id_rsa.pub"
The authenticity of host '192.168.196.133 (192.168.196.133)' can't be established.
ED25519 key fingerprint is SHA256:ieG7iUYRDYyuZcBk5f2ABb9S2us0LzsIZEJqzhQwdFM.
This key is not known by any other names.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
/usr/bin/ssh-copy-id: INFO: attempting to log in with the new key(s), to filter out any that are already installed
/usr/bin/ssh-copy-id: INFO: 1 key(s) remain to be installed -- if you are prompted now it is to install the new keys
root@192.168.196.133's password:
Number of key(s) added: 1
Now try logging into the machine, with: "ssh 'root@192.168.196.133'"
and check to make sure that only the key(s) you wanted were added.
测试免密效果
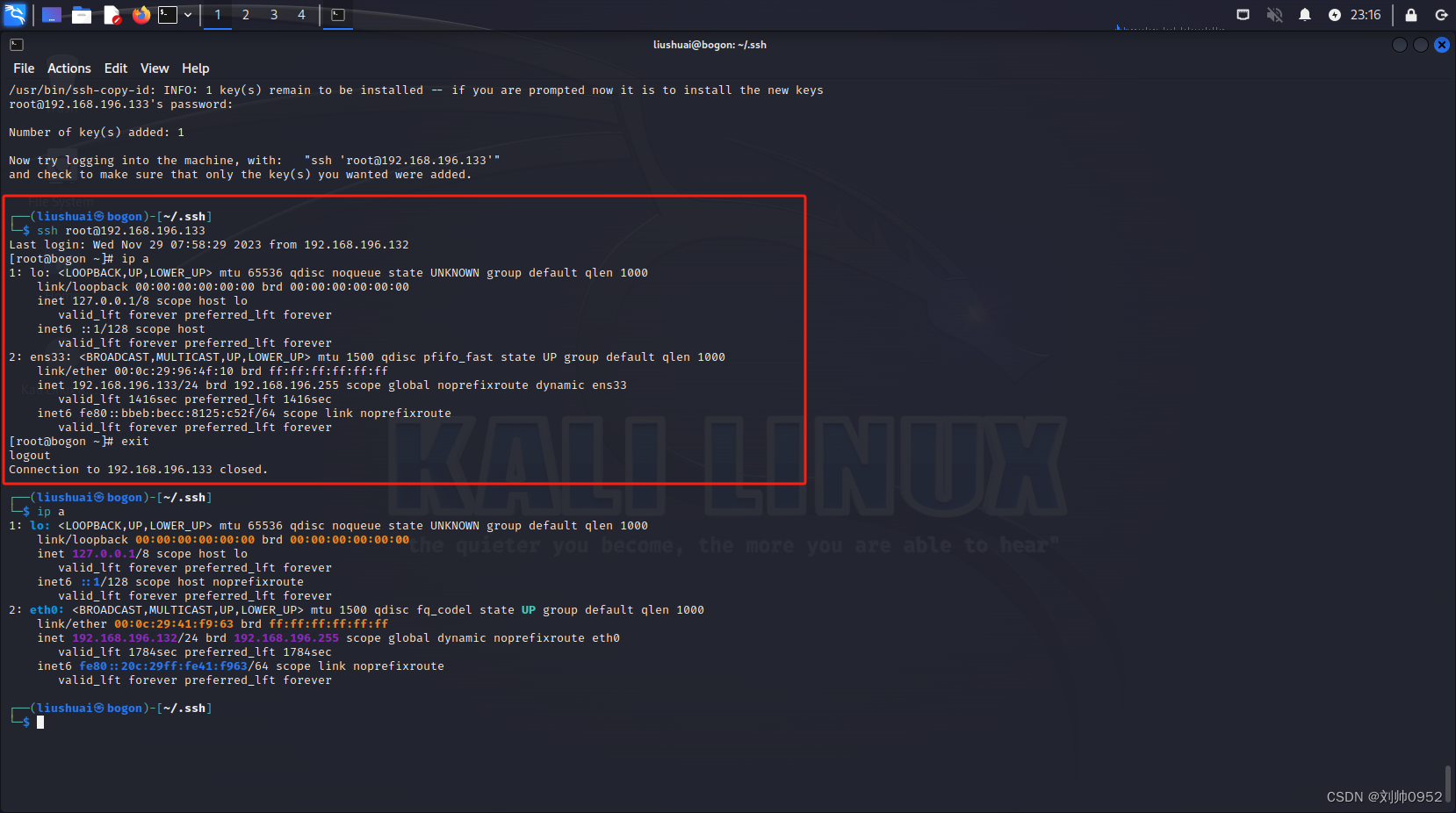
└─$ ssh root@192.168.196.133
Last login: Wed Nov 29 07:58:29 2023 from 192.168.196.132
[root@bogon ~]# ip a
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: ens33: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP group default qlen 1000
link/ether 00:0c:29:96:4f:10 brd ff:ff:ff:ff:ff:ff
inet 192.168.196.133/24 brd 192.168.196.255 scope global noprefixroute dynamic ens33
valid_lft 1416sec preferred_lft 1416sec
inet6 fe80::bbeb:becc:8125:c52f/64 scope link noprefixroute
valid_lft forever preferred_lft forever
[root@bogon ~]# exit
logout
Connection to 192.168.196.133 closed.
结束语
没有随随便便的成功,只有不断的努力